Say No To Dependency Hell
- 1. Say No to the Dependency Hell: Proper Management of Software Dependencies IVAN PASHCHENKO Trento - 2019
- 2. whoami 2 Ivan Pashchenko • PhD candidate in Information Security at the University of Trento • Former Intern at SAP Security Research • Former Leading Security Engineer at Bashneft, Russia • Snowboarder, hiker, volleyball player
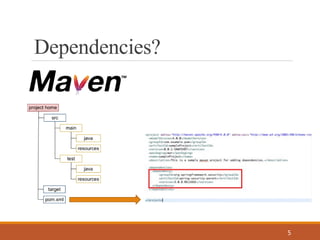
- 4. Nowadays software projects are highly interconnected 4 • Own code • Dependencies Own code Dependencies Software project
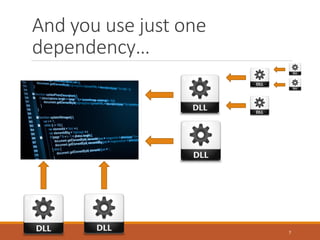
- 6. You are writing code… This is a typical functionality, I do not want to invent a wheel – I will use already developed functionality. 6
- 7. And you use just one dependency… 7
- 8. 8 Welcome to the Dependency Hell
- 10. 10
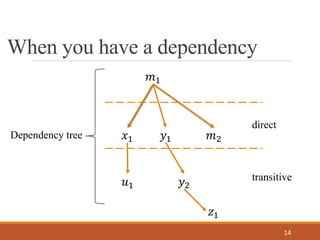
- 14. When you have a dependency 14 ùëö1 ùëö2ùë¶1ùë•1 ùë¶2ùë¢1 ùëß1 direct transitive Dependency tree
- 15. Current dependency analysis 15 0. Follow the updates in your software dependencies manually - Subscribe to mailing lists of your dependencies - Telegram channels - Analyze changelogs of the new releases - Receive a lot of spam…
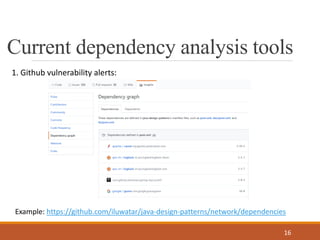
- 16. Current dependency analysis tools 16 1. Github vulnerability alerts: Example: https://github.com/iluwatar/java-design-patterns/network/dependencies
- 17. Current dependency analysis tools 17 1. Github vulnerability alerts: Listing the packages that a repository depends on: https://help.github.com/articles/listing-the-packages-that-a-repository-depends-on/ Viewing and updating vulnerable dependencies in your repository: https://help.github.com/articles/viewing-and-updating-vulnerable-dependencies-in-your- repository/ About security alerts for vulnerable dependencies: https://help.github.com/articles/about-security-alerts-for-vulnerable-dependencies/
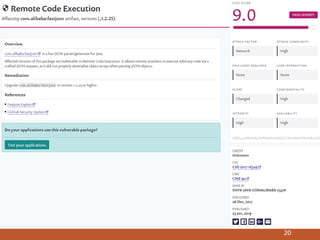
- 18. Current dependency analysis tools 18 2. Snyk.io: Home page: https://snyk.io/ Introduction video: https://youtu.be/4ng5usM6fd8
- 19. Current dependency analysis tools 19 2. Snyk.io – Vulnerability DB:
- 20. Current dependency analysis tools 20 2. Snyk.io – Vulnerability DB:
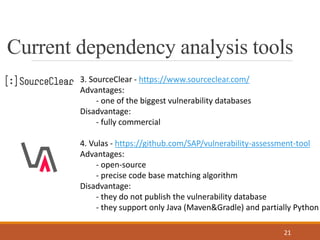
- 21. Current dependency analysis tools 21 3. SourceClear - https://www.sourceclear.com/ Advantages: - one of the biggest vulnerability databases Disadvantage: - fully commercial 4. Vulas - https://github.com/SAP/vulnerability-assessment-tool Advantages: - open-source - precise code base matching algorithm Disadvantage: - they do not publish the vulnerability database - they support only Java (Maven&Gradle) and partially Python
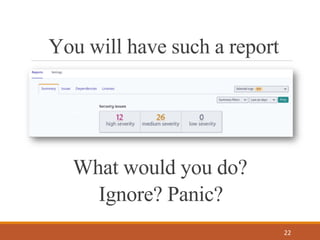
- 22. You will have such a report 22 What would you do? Ignore? Panic?
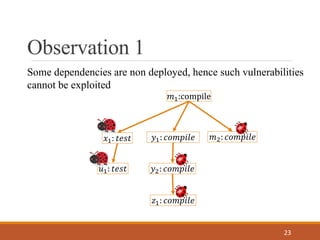
- 23. Observation 1 23 Some dependencies are non deployed, hence such vulnerabilities cannot be exploited ùëö1:compile ùëö2: ùëêùëúùëöùëùùëñùëôùëíùë¶1: ùëêùëúùëöùëùùëñùëôùëíùë•1: ùë°ùëíùë†ùë° ùë¶2: ùëêùëúùëöùëùùëñùëôùëíùë¢1: ùë°ùëíùë†ùë° ùëß1: ùëêùëúùëöùëùùëñùëôùëí
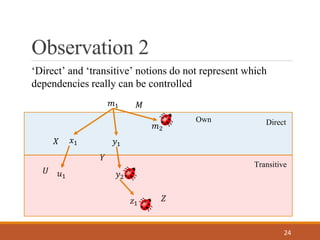
- 24. Observation 2 24 ùëö1 ùëö2 ùë¶1ùë•1 ùë¶2ùë¢1 ùëß1 ùëÄ ùëå ùëã ùëà ùëç Direct ‚ÄòDirect‚Äô and ‚Äòtransitive‚Äô notions do not represent which dependencies really can be controlled Transitive Own
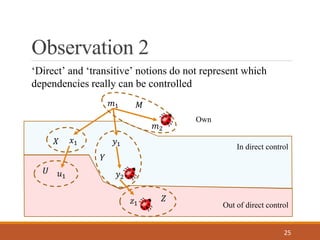
- 25. Observation 2 25 ùëö1 ùëö2 ùë¶1ùë•1 ùë¶2ùë¢1 ùëß1 ùëÄ ùëå ùëã ùëà ùëç ‚ÄòDirect‚Äô and ‚Äòtransitive‚Äô notions do not represent which dependencies really can be controlled Own In direct control Out of direct control
- 26. Observation 3 26 ùëö1 ùë•1 ùë¢1 ùë£1 ùë£2 ùë£1 ùë£1 ùë£2 ùë£3 ùë°0 ùë°1 There would be no version of x1: 1) to fix vulnerability in x1 2) adopt fixed version of u1 Fixing such a dependency would require a software company either to contribute to the halted library (make a new release) or maintain an own copy of the library Some libraries may become halted
- 27. Counting dependencies 27 Build dependency tree Maven goals: dependency:tree and dependency:resolve Filter non-deployed dependencies Exclude test and provided scopes Group dependencies by projects Group all GAVs with the same groupId within one path and substitute them in the path with the GAV, closest to the vulnerable GAV Identify halted dependencies ‚Ä¢ùêøùëéùë†ùë° ùëüùëíùëôùëíùëéùë†ùëí ùëñùëõùë°ùëíùëüùë£ùëéùëô = ùõº œÉùëñ=0 ùëõ { 1 ‚àí ùõº ùëñ ‚àó ùëÖùëíùëôùëíùëéùë†ùëí ùë°ùëñùëöùëí ùëõ‚àíùëñ} ‚Ä¢ùê∏ùë•ùëùùëíùëêùë°ùëíùëë ùëüùëíùëôùëíùëéùë†ùëí ùëëùëéùë°ùëí = ùêøùëéùë†ùë° ùëüùëíùëôùëíùëéùë†ùëí + ùêøùëéùë†ùë° ùëüùëíùëôùëíùëéùë†ùëí ùëñùëõùë°ùëíùëüùë£ùëéùëô ‚Ä¢ùê∏ùë•ùëùùëíùëêùë°ùëíùëë ùëüùëíùëôùëíùëéùë†ùëí ùëëùëéùë°ùëí < ùëáùêºùëÄùê∏ ‚áí ùêøùëñùëèùëüùëéùëüùë¶ ùëñùë† ‚Ñéùëéùëôùë°ùëíùëë Map with known vulnerable GA S. E. Ponta, H. Plate, and A. Sabetta. Beyond metadata: Code-centric and usage based analysis of known vulnerabilities in open-source software. In Proc. of ICSME-18, 2018
- 28. Effects Filtering non-deployed Dependency grouping “Is halted” analysis 28 20% less false alerts to check Developers may have fixed 82% of vulns in their dependencies (45% increase) 14% of dependencies are halted, hence would not be fixed
- 29. Following our approach you will have the following report 29 A bit more clear what to do, isn’t it?
- 30. An example of our report 30
- 31. 31 We are looking for your experience More details about our research are here: http://bit.ly/vuln-research-trento "Dependencies as you see it" (what the problems are, why people could, should, or won't update etc.). This can be a brief Skype/Hangout/etc interview at your convenience.
- 32. We bring order to the dependency hell 32
- 33. 33 For any questions or suggestions do not hesitate to contact me: E-mail: ivan.pashchenko@unitn.it Skype: ivanpashchenko Web-site: http://disi.unitn.it/~pashchenko Let’s say No to the Dependency Hell Information about our research is here: http://bit.ly/vuln-research-trento