Sdh alarm presentation
- 1. Defect and Failure 1. A defect is a detection of an alarm such as loss of signals, loss of frames, AIS and Excessive Errors 2. A failure is a defect that persists beyond a maximum time allocated. It is used to access to integrate Automatic Protection Switching ( APS ). 57/1
- 2. LOS : Loss of Signal 1. This alarm is raised when the STM-N level drops below the threshold at which a BER of 10-3 or worse is detected 2. It could be due to cut cable, excessive attenuation of the signal or an equipment fault 3. The LOS state will clear when 2 consecutive framing patterns are received and no LOS condition is detected 58/1
- 3. OOF : Out of frame 1. This situation occurs when 5 consecutive SDH frames are received with invalid framing patterns(A1 and A2 bytes) 2. The maximum time to detect OOF is therefore 625ÂĩSec 3. The OOF clears when consecutive SDH frames are received with valid framing patterns 59/1
- 4. LOF : loss of frame 1. The LOF occurs when the OOF state exists for a 3 mSec. 2. If OOFs are intermittent, the timer is not reset to zero until an âin frameâ state persists continuously for specified time in msecs 3. As the framing bytes are there in Regenerator section overhead (RSOH), this alarm is sometimes known as RS-LOF 60/1
- 5. LOP : loss of Pointer 1. The LOP state occurs when ânâ consecutive invalid pointers are received or ânâ New Data Flags (NDF) are received (other than in a concatenation indicator), where n >8 2. The LOP state is cleared when 3 equal valid pointers or 3 consecutive AIS indications are received. 61/1
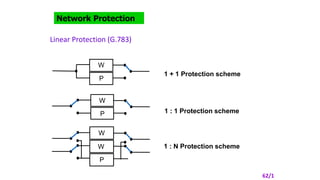
- 6. Network Protection Linear Protection (G.783) W P W P W W P 1 + 1 Protection scheme 1 : 1 Protection scheme 1 : N Protection scheme 62/1
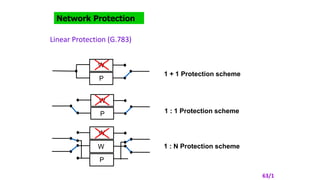
- 7. W P W P W W P 1 + 1 Protection scheme 1 : 1 Protection scheme 1 : N Protection scheme Network Protection Linear Protection (G.783) 63/1
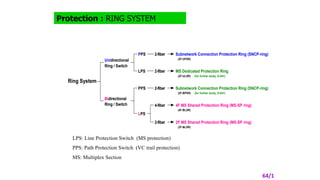
- 8. Protection : RING SYSTEM Ring System Unidirectional Ring / Switch Bidirectional Ring / Switch PPS LPS PPS LPS 2-fiber 2-fiber 2-fiber 4-fiber 2-fiber Subnetwork Connection Protection Ring (SNCP-ring) (2F-UPSR) MS Dedicated Protection Ring (2F-ULSR) (for further study, G.841) Subnetwork Connection Protection Ring (SNCP-ring) (2F-BPSR) (for further study, G.841) 4F MS Shared Protection Ring (MS-SP ring) (4F-BLSR) 2F MS Shared Protection Ring (MS-SP ring) (2F-BLSR) LPS: Line Protection Switch (MS protection) PPS: Path Protection Switch (VC trail protection) MS: Multiplex Section 64/1
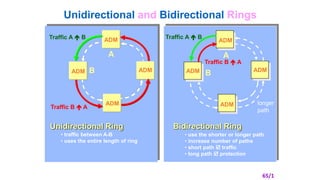
- 9. Unidirectional and Bidirectional Rings ADM ADM ADM A ADM B Traffic A ïĐ B Traffic B ïĐ A Unidirectional Ring âĒ traffic between A-B âĒ uses the entire length of ring B -> A Bidirectional Ring A B longer path ADM ADM ADM ADM âĒ use the shorter or longer path âĒ increase number of paths âĒ short path ïū traffic âĒ long path ïū protection Traffic A ïĐ B Traffic B ïĐ A 65/1
Editor's Notes
- #9: Ring systems are classified into five types based on employed switching method combination (unidirectional or bidirectional switch and path or line switch), (and fiber number (2 or 4 fibers). Theoretically any combination between switching and routing direction is possible. But in the ring system, above uni-uni and bi-bi combination is used. SNCP-ring (Unidirectional) 3.1 Also called 2-fiber Unidirectional Path Protection Switch Ring (2F-UPSR) 3.2 No switching protocol is required. This is a simple and fast switching scheme. MS Dedicated Protection Ring 4.1 2-fiber Unidirectional Line protection Switch Ring (2F-ULSR) 4.2 Protocol by K1 and K2 in MSOH is required and it is not standardized yet by ITU-T. SNCP-ring (Bidirectional) 5.1 2-fiber Bidirectional Path protection Switch Ring (2F-BPSR) 5.2 Ring must be controlled at a path level and protocol by K3 or K4 in POH is required. It is not standardized yet by ITU-T. 4F MS-SP ring 6.1 4-fiber Bidirectional Line protection Switch Ring (4F-BLSR) 6.2 Protocol by K1 and K2 in MSOH is required. 2F MS-SP ring 7.1 2-fiber Bidirectional Line protection Switch Ring (2F-BLSR) 7.2 Protocol by K1 and K2 in MSOH is required. There are two different algorithm in 4/2F MS-SP ring, the terrestrial application and the transoceanic application.