Searching
Download as ppt, pdf1 like93 views
The document discusses searching algorithms, focusing on sequential and binary search methods. Sequential search examines elements one by one and has a time complexity of O(n), while binary search is more efficient, with a time complexity of O(log n), as it divides the array into halves. Examples of both algorithms and their respective program logic are provided.
1 of 13
Downloaded 15 times





![SEQUENTIAL SEARCH pROGRAmSEQUENTIAL SEARCH pROGRAm
LOGICLOGIC
01/31/18 BY MS. SHAISTA QADIR 7
’éŚ PROGRAM LOGIC:
public int seqsearch(int [ ]arr, int x)
{
for(int i=0; i< arr.length; i++)
if(arr [ i ] == x)
return i;
return -1;
}
’éŚ Time Complexity of Sequential search algorithm is: O(n)3.](https://image.slidesharecdn.com/lecture6-180131100803/85/Searching-7-320.jpg)

![BINARY SEARCH pROGRAmBINARY SEARCH pROGRAm
lOGIClOGIC
01/31/18 BY MS. SHAISTA QADIR 12
’éŚ PROGRAM LOGIC:
public static int binarysearch(int[ ] a, int x) {
int lo = 0; int hi = a.length;
while (lo < hi) {
int i = (lo + hi) / 2;
if (a[i] == x)
return i;
else if (a[i] < x)
lo = i+1;
else hi = I; }
return -1; }
’éŚ Time Complexity of binary search algorithm is: O(logn)](https://image.slidesharecdn.com/lecture6-180131100803/85/Searching-12-320.jpg)

Ad
Recommended
Secondary Index Search in InnoDB
Secondary Index Search in InnoDBMIJIN AN
╠²
The document discusses secondary index searches in MySQL. It describes the process as starting with a search of the secondary index tree to find the primary key. The primary key is then added to an unsorted list. Once all secondary index searches are complete, the primary key list is sorted. The primary index tree is then searched sequentially using the sorted primary key list to retrieve the clustered data records. Finally, the clustered data records are accessed sequentially.4 heapsort pq
4 heapsort pqhasan Mohammad
╠²
This document discusses heapsort and priority queues implemented using binary heaps. Heapsort uses a max heap to sort an array in O(n log n) time by repeatedly extracting the maximum element and placing it in its sorted position. A priority queue uses a min heap to retrieve the minimum element in O(log n) time for insertions and deletions by keeping the minimum key at the root.Java - Collections
Java - CollectionsAmith jayasekara
╠²
This document provides information on Java collection frameworks like List, Set, and Map. It discusses the common implementations of each and their performance characteristics for different operations. Key points covered include the differences between ArrayList and LinkedList, when to use HashSet vs LinkedHashSet, and how HashMap performance is related to load factor. The document also mentions utility methods in Collections class and best practices like avoiding null returns.Deadlock Prevention in Operating System
Deadlock Prevention in Operating SystemZeeshan Iqbal
╠²
The document describes an experiment to simulate an algorithm for deadlock prevention in an operating system. It defines deadlock as when processes are blocked because each holds a resource needed by another. It explains resource allocation graphs (RAGs) that represent processes, resources, and their relationships. The algorithm aims to prevent deadlock by ordering resources and only allowing requests in increasing order to avoid cycles in the RAG. The program simulates this approach by tracking available resources, allocation, and need matrices to determine a safe process execution order or report an unsafe state.Big Data & Hadoop Data Analysis
Big Data & Hadoop Data AnalysisKoushik Mondal
╠²
This document provides an overview of big data, Hadoop, and Hive. It discusses big data characteristics, how Hadoop allows distributed storage and processing of big data, key Hadoop components and ecosystem tools, and features of Hive. It then describes a project analyzing airline data stored on Hadoop using Hive queries. The project involves querying airport, airline, and route data to analyze operating airports and airlines by country, routes by stops and code sharing, and highest airports by country.A Survey of Sequential Rule Mining Techniques
A Survey of Sequential Rule Mining Techniquesijsrd.com
╠²
This paper reviews existing sequential rule mining techniques, categorizing them into generate-and-test and pattern-growth frameworks while analyzing algorithm performance based on runtime and theory. Key approaches discussed include GSP and PrefixSpan, which differ in their methodology for discovering sequential patterns from databases. The authors conclude by noting the potential for improved mining efficiency through enhanced memory utilization and hint at developing a new algorithm for sequential association rules in future work.Ds chapter 2
Ds chapter 2Prof .Pragati Khade
╠²
An array allows storing a collection of homogeneous data elements in contiguous memory locations and provides random access to elements. It defines a variable with a name and fixed size, where all elements are of the same data type. Arrays are commonly used to store lists of values and perform operations like sorting and searching algorithms. Bubble sort is a simple sorting algorithm that compares adjacent elements and swaps them if they are in the wrong order until the list is fully sorted.Heap Sort in Design and Analysis of algorithms
Heap Sort in Design and Analysis of algorithmssamairaakram
╠²
The document provides a comprehensive overview of the heap sort algorithm, detailing its properties, structure, and the process of sorting using a binary heap. It includes explanations of binary trees, types of heaps, the heap sort algorithm, and its time complexity. The advantages and disadvantages of heap sort are also discussed, highlighting its efficiency and simplicity compared to other sorting methods.A novel algorithm for mining closed sequential patterns
A novel algorithm for mining closed sequential patternsIJDKP
╠²
This document presents a novel algorithm called NCSP for mining closed sequential patterns from large sequence databases, addressing the inefficiencies of existing algorithms that produce excessive sequential patterns. The proposed algorithm uses vertical bitmap representation to enhance support counting and outperforms the previously established method, Clospan, in both speed and efficiency. The article details the algorithm's structure, effectiveness through experimental results, and offers insights into the problem of closed sequential pattern mining.Fast Sequential Rule Mining
Fast Sequential Rule Miningijsrd.com
╠²
This paper proposes a novel method for fast sequential rule mining, which is more efficient than existing approaches by utilizing a pattern-growth method rather than a generate-candidate-and-test approach. The proposed algorithm identifies valuable sequential patterns through a systematic process involving itemset generation and support confidence calculation, ultimately demonstrating superior performance compared to previous algorithms. It highlights the application of sequential pattern mining in various fields, including business and biology, while addressing challenges related to large data sets.Linear search-and-binary-search
Linear search-and-binary-searchInternational Islamic University
╠²
This document provides an overview of linear search and binary search algorithms.
It explains that linear search sequentially searches through an array one element at a time to find a target value. It is simple to implement but has poor efficiency as the time scales linearly with the size of the input.
Binary search is more efficient by cutting the search space in half at each step. It works on a sorted array by comparing the target to the middle element and determining which half to search next. The time complexity of binary search is logarithmic rather than linear.IRJET- A Survey on Different Searching Algorithms
IRJET- A Survey on Different Searching AlgorithmsIRJET Journal
╠²
The document summarizes and compares several common search algorithms:
- Binary search has the best average time complexity of O(log n) but only works on sorted data. Linear search has average time complexity of O(n) and works on any data but is less efficient.
- Hybrid search combines linear and binary search to search unsorted arrays more efficiently than linear search. Interpolation search is an improvement on binary search that may search in different locations based on the search key value.
- Jump search works on sorted data by jumping in blocks of size sqrt(n) and doing a linear search within blocks. It has better average performance than linear search but only works on sorted data.Graph based Approach and Clustering of Patterns (GACP) for Sequential Pattern...
Graph based Approach and Clustering of Patterns (GACP) for Sequential Pattern...AshishDPatel1
╠²
The paper presents a new algorithm called GACP (Graph-Based Approach and Clustering of Patterns) for efficient sequential pattern mining, which improves upon traditional techniques by utilizing graph representation to minimize memory usage and I/O operations. GACP avoids recursive tree reconstruction and excessive database scans, employing clustering techniques to streamline pattern retrieval. The algorithm is designed to handle large data collections effectively, making it applicable in various fields such as web usage analysis and customer behavior studies.Mining Top-k Closed Sequential Patterns in Sequential Databases
Mining Top-k Closed Sequential Patterns in Sequential Databases IOSR Journals
╠²
This paper discusses the challenges of mining sequential patterns in databases, specifically the difficulty in setting a minimum support threshold and the exponential growth of generated patterns. It proposes a new algorithm for mining top-k closed sequential patterns with a minimum length constraint, which enhances efficiency by dynamically raising support and performing effective verification. The experimental results demonstrate the advantages of the top-k mining approach over existing methods, particularly in computational performance.Mining closed sequential patterns in large sequence databases
Mining closed sequential patterns in large sequence databasesIJDMS
╠²
The paper presents an efficient algorithm, called CSPAN, for mining closed sequential patterns in large sequence databases, utilizing a pruning method known as occurrence checking for early detection. CSPAN outperforms existing algorithms such as Clospan and CLASP by significantly improving performance on various datasets. The study emphasizes the importance of closed sequential pattern mining in reducing the number of generated patterns and enhancing mining efficiency across numerous applications.Aslam
AslamMuhammad Aslam
╠²
This document discusses algorithms for linear and binary search. It explains that linear search sequentially checks each element of a list to find a target value, while binary search divides the search space in half at each step to quickly locate a value. For linear search, the best case is when the target is first, average case is when it is in the middle, and worst case is when it is last. Binary search uses a midpoint calculation and comparison to recursively narrow the search range.A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETS
A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETSijcsa
╠²
The document presents a new optimization approach for extracting frequent 2-itemsets using a modified apriori algorithm to enhance data mining efficiency. It emphasizes the classification of items based on their purchase patterns, particularly in commercial settings, aiming to help store managers improve product arrangements based on frequent item correlations. The experimental results show that this method improves extraction time compared to traditional algorithms and facilitates better decision-making for item placements in stores.A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETS
A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETSijcsa
╠²
This document presents a new optimization approach for extracting frequent 2-itemsets from transactional databases. The approach sorts frequent 1-itemsets by support before generating 2-itemsets, aiming to discover association rules more quickly. Experiments show the proposed OPTI2I algorithm performs efficiently on weakly correlated data compared to APRIORI, PASCAL, CLOSE and MAX-MINER. The work also presents a model for side-by-side classification of items based on relationships between 2-itemsets, which could help arrange products in large stores.A New Extraction Optimization Approach to Frequent 2 Item sets
A New Extraction Optimization Approach to Frequent 2 Item setsijcsa
╠²
This paper presents a new optimization approach for extracting frequent 2-itemsets using a modified apriori algorithm, enhancing the speed of discovery while focusing on association rules. The authors propose an efficient method by first calculating and filtering frequent 1-itemsets before generating 2-itemsets based on their supports, especially in the context of large databases and weakly correlated data. Experimental results show that this approach significantly improves extraction times compared to traditional methods, enabling better decision-making for item arrangements in retail environments.Review Over Sequential Rule Mining
Review Over Sequential Rule Miningijsrd.com
╠²
The document provides a comprehensive review of sequential rule mining, highlighting its significance in data mining for predictive purposes across various domains like stock analysis and weather observation. It discusses different algorithms for mining sequential rules, their advantages, limitations, and the changing methodologies over time, including the constraint-based approach to reduce uninteresting patterns. The paper concludes by emphasizing the need for efficient mining algorithms to handle large databases effectively.C# Arrays Presentation - Computer Science and Engineering Department
C# Arrays Presentation - Computer Science and Engineering DepartmentBhuvaneswaranB1
╠²
The document provides a comprehensive overview of arrays in C# programming, discussing their definition, types, and various methods associated with the 'System.Array' class. It outlines the syntax for creating arrays, iterating through them using for and foreach loops, and describes built-in methods such as indexOf, binarySearch, clear, resize, sort, reverse, copyTo, and clone. Additionally, it explains the differences between shallow and deep copies of arrays, as well as jagged versus multi-dimensional arrays.Algorithm 8th lecture linear & binary search(2).pptx
Algorithm 8th lecture linear & binary search(2).pptxAftabali702240
╠²
The document discusses linear and binary search algorithms. Linear search sequentially checks each element of an unsorted array to find a target value, resulting in O(n) time complexity in the worst case. Binary search works on a sorted array by comparing the target to the middle element and recursively searching half the array, resulting in O(log n) time complexity in the worst case, which is more efficient than linear search.Sequential Pattern Mining Methods: A Snap Shot
Sequential Pattern Mining Methods: A Snap ShotIOSR Journals
╠²
This document summarizes sequential pattern mining methods. It begins by defining sequential pattern mining as discovering time-related behaviors in sequence databases. It then reviews two main approaches for sequential pattern mining - Apriori-based methods and frequent pattern growth methods. For Apriori-based methods, it discusses GSP, SPADE, and SPAM algorithms. For frequent pattern growth methods, it discusses FreeSpan and PrefixSpan algorithms. It then presents experimental results comparing the performance of Apriori, PrefixSpan, and SPAM algorithms based on execution time, number of patterns found, and memory usage. Finally, it discusses limitations of traditional objective measures like support and confidence for determining pattern interestingness and proposes alternative measures like lift.Clustering and Visualisation using R programming
Clustering and Visualisation using R programmingNixon Mendez
╠²
The document outlines various clustering and visualization techniques for analyzing microarray data of yeast cell cycles, including Principal Component Analysis, Multidimensional Scaling, K-means clustering, Self-Organizing Maps, and Hierarchical Clustering. It discusses methodologies to visualize and interpret gene expression data, while emphasizing the effect of cyclins on gene regulation. The analysis provides practical R code examples for implementing these techniques and presents datasets for further exploration.Chapter three data structure and algorithms qaybta quee
Chapter three data structure and algorithms qaybta queehabdi203062
╠²
The document discusses arrays as a fundamental data structure, outlining key operations such as insertion, searching, and deletion, specifically focusing on ordered and unordered arrays. It highlights the efficiency of binary search on ordered arrays compared to linear search, and also explores object storage within arrays, big-oh notation for algorithm efficiency, and trade-offs between unordered and ordered arrays. Additionally, it gives insights into implementation strategies and the appendices indicate advanced data structures that offer improved performance for various operations.Sequential Pattern Tree Mining
Sequential Pattern Tree MiningIOSR Journals
╠²
The document discusses a novel approach to sequential pattern mining using a structured tree framework that stores both frequent and non-frequent items, allowing for efficient mining with a single database scan. This method reduces the time and space complexities associated with existing algorithms by avoiding the generation of intermediate candidate sequences and minimizing the need for repeated database scans. Performance analysis demonstrates that this new algorithm significantly outperforms established techniques like GSP, PrefixSpan, and tree-based mining methods.Algorithm - Mergesort & Quicksort
Algorithm - Mergesort & Quicksort Varendra University Rajshahi-bangladesh
╠²
1. The document discusses the merge sort and quicksort algorithms.
2. Merge sort works by dividing an array into two halves, sorting each half recursively, and then merging the sorted halves into a single sorted array.
3. Quicksort works by selecting a pivot element and partitioning the array into two halves based on element values relative to the pivot.A survey paper on sequence pattern mining with incremental
A survey paper on sequence pattern mining with incrementalAlexander Decker
╠²
This document summarizes four algorithms for sequential pattern mining: GSP, ISM, FreeSpan, and PrefixSpan. GSP is an Apriori-based algorithm that incorporates time constraints. ISM extends SPADE to incrementally update patterns after database changes. FreeSpan uses frequent items to recursively project databases and grow subsequences. PrefixSpan also uses projection but claims to not require candidate generation. It recursively projects databases based on short prefix patterns. The document concludes by stating the goal was to find an efficient scheme for extracting sequential patterns from transactional datasets.Chapter - 2 introduction to Computer Organization.pdf
Chapter - 2 introduction to Computer Organization.pdfShaista Qadir
╠²
The document provides an overview of computer system organization, detailing the components such as the central processing unit (CPU), memory unit, and input/output devices. It explains the roles of the CPU, including the control unit and arithmetic logic unit, and describes different types of memory, including RAM, ROM, cache memory, and secondary storage devices like hard disks and solid-state drives. Additionally, exercises are included to reinforce understanding of the concepts presented.Chapter - 1 Introduction to Computer Science.pdf
Chapter - 1 Introduction to Computer Science.pdfShaista Qadir
╠²
The document provides an introduction to computer science, defining a computer as an electronic device that processes data into information. It outlines the information processing cycle, advantages and disadvantages of computers, and their classification based on size, purpose, and hardware design. Key points include the fast speed and reliability of computers, health risks associated with usage, and classifications such as supercomputers, mainframes, and microcomputers.More Related Content
Similar to Searching (20)
A novel algorithm for mining closed sequential patterns
A novel algorithm for mining closed sequential patternsIJDKP
╠²
This document presents a novel algorithm called NCSP for mining closed sequential patterns from large sequence databases, addressing the inefficiencies of existing algorithms that produce excessive sequential patterns. The proposed algorithm uses vertical bitmap representation to enhance support counting and outperforms the previously established method, Clospan, in both speed and efficiency. The article details the algorithm's structure, effectiveness through experimental results, and offers insights into the problem of closed sequential pattern mining.Fast Sequential Rule Mining
Fast Sequential Rule Miningijsrd.com
╠²
This paper proposes a novel method for fast sequential rule mining, which is more efficient than existing approaches by utilizing a pattern-growth method rather than a generate-candidate-and-test approach. The proposed algorithm identifies valuable sequential patterns through a systematic process involving itemset generation and support confidence calculation, ultimately demonstrating superior performance compared to previous algorithms. It highlights the application of sequential pattern mining in various fields, including business and biology, while addressing challenges related to large data sets.Linear search-and-binary-search
Linear search-and-binary-searchInternational Islamic University
╠²
This document provides an overview of linear search and binary search algorithms.
It explains that linear search sequentially searches through an array one element at a time to find a target value. It is simple to implement but has poor efficiency as the time scales linearly with the size of the input.
Binary search is more efficient by cutting the search space in half at each step. It works on a sorted array by comparing the target to the middle element and determining which half to search next. The time complexity of binary search is logarithmic rather than linear.IRJET- A Survey on Different Searching Algorithms
IRJET- A Survey on Different Searching AlgorithmsIRJET Journal
╠²
The document summarizes and compares several common search algorithms:
- Binary search has the best average time complexity of O(log n) but only works on sorted data. Linear search has average time complexity of O(n) and works on any data but is less efficient.
- Hybrid search combines linear and binary search to search unsorted arrays more efficiently than linear search. Interpolation search is an improvement on binary search that may search in different locations based on the search key value.
- Jump search works on sorted data by jumping in blocks of size sqrt(n) and doing a linear search within blocks. It has better average performance than linear search but only works on sorted data.Graph based Approach and Clustering of Patterns (GACP) for Sequential Pattern...
Graph based Approach and Clustering of Patterns (GACP) for Sequential Pattern...AshishDPatel1
╠²
The paper presents a new algorithm called GACP (Graph-Based Approach and Clustering of Patterns) for efficient sequential pattern mining, which improves upon traditional techniques by utilizing graph representation to minimize memory usage and I/O operations. GACP avoids recursive tree reconstruction and excessive database scans, employing clustering techniques to streamline pattern retrieval. The algorithm is designed to handle large data collections effectively, making it applicable in various fields such as web usage analysis and customer behavior studies.Mining Top-k Closed Sequential Patterns in Sequential Databases
Mining Top-k Closed Sequential Patterns in Sequential Databases IOSR Journals
╠²
This paper discusses the challenges of mining sequential patterns in databases, specifically the difficulty in setting a minimum support threshold and the exponential growth of generated patterns. It proposes a new algorithm for mining top-k closed sequential patterns with a minimum length constraint, which enhances efficiency by dynamically raising support and performing effective verification. The experimental results demonstrate the advantages of the top-k mining approach over existing methods, particularly in computational performance.Mining closed sequential patterns in large sequence databases
Mining closed sequential patterns in large sequence databasesIJDMS
╠²
The paper presents an efficient algorithm, called CSPAN, for mining closed sequential patterns in large sequence databases, utilizing a pruning method known as occurrence checking for early detection. CSPAN outperforms existing algorithms such as Clospan and CLASP by significantly improving performance on various datasets. The study emphasizes the importance of closed sequential pattern mining in reducing the number of generated patterns and enhancing mining efficiency across numerous applications.Aslam
AslamMuhammad Aslam
╠²
This document discusses algorithms for linear and binary search. It explains that linear search sequentially checks each element of a list to find a target value, while binary search divides the search space in half at each step to quickly locate a value. For linear search, the best case is when the target is first, average case is when it is in the middle, and worst case is when it is last. Binary search uses a midpoint calculation and comparison to recursively narrow the search range.A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETS
A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETSijcsa
╠²
The document presents a new optimization approach for extracting frequent 2-itemsets using a modified apriori algorithm to enhance data mining efficiency. It emphasizes the classification of items based on their purchase patterns, particularly in commercial settings, aiming to help store managers improve product arrangements based on frequent item correlations. The experimental results show that this method improves extraction time compared to traditional algorithms and facilitates better decision-making for item placements in stores.A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETS
A NEW EXTRACTION OPTIMIZATION APPROACH TO FREQUENT 2 ITEMSETSijcsa
╠²
This document presents a new optimization approach for extracting frequent 2-itemsets from transactional databases. The approach sorts frequent 1-itemsets by support before generating 2-itemsets, aiming to discover association rules more quickly. Experiments show the proposed OPTI2I algorithm performs efficiently on weakly correlated data compared to APRIORI, PASCAL, CLOSE and MAX-MINER. The work also presents a model for side-by-side classification of items based on relationships between 2-itemsets, which could help arrange products in large stores.A New Extraction Optimization Approach to Frequent 2 Item sets
A New Extraction Optimization Approach to Frequent 2 Item setsijcsa
╠²
This paper presents a new optimization approach for extracting frequent 2-itemsets using a modified apriori algorithm, enhancing the speed of discovery while focusing on association rules. The authors propose an efficient method by first calculating and filtering frequent 1-itemsets before generating 2-itemsets based on their supports, especially in the context of large databases and weakly correlated data. Experimental results show that this approach significantly improves extraction times compared to traditional methods, enabling better decision-making for item arrangements in retail environments.Review Over Sequential Rule Mining
Review Over Sequential Rule Miningijsrd.com
╠²
The document provides a comprehensive review of sequential rule mining, highlighting its significance in data mining for predictive purposes across various domains like stock analysis and weather observation. It discusses different algorithms for mining sequential rules, their advantages, limitations, and the changing methodologies over time, including the constraint-based approach to reduce uninteresting patterns. The paper concludes by emphasizing the need for efficient mining algorithms to handle large databases effectively.C# Arrays Presentation - Computer Science and Engineering Department
C# Arrays Presentation - Computer Science and Engineering DepartmentBhuvaneswaranB1
╠²
The document provides a comprehensive overview of arrays in C# programming, discussing their definition, types, and various methods associated with the 'System.Array' class. It outlines the syntax for creating arrays, iterating through them using for and foreach loops, and describes built-in methods such as indexOf, binarySearch, clear, resize, sort, reverse, copyTo, and clone. Additionally, it explains the differences between shallow and deep copies of arrays, as well as jagged versus multi-dimensional arrays.Algorithm 8th lecture linear & binary search(2).pptx
Algorithm 8th lecture linear & binary search(2).pptxAftabali702240
╠²
The document discusses linear and binary search algorithms. Linear search sequentially checks each element of an unsorted array to find a target value, resulting in O(n) time complexity in the worst case. Binary search works on a sorted array by comparing the target to the middle element and recursively searching half the array, resulting in O(log n) time complexity in the worst case, which is more efficient than linear search.Sequential Pattern Mining Methods: A Snap Shot
Sequential Pattern Mining Methods: A Snap ShotIOSR Journals
╠²
This document summarizes sequential pattern mining methods. It begins by defining sequential pattern mining as discovering time-related behaviors in sequence databases. It then reviews two main approaches for sequential pattern mining - Apriori-based methods and frequent pattern growth methods. For Apriori-based methods, it discusses GSP, SPADE, and SPAM algorithms. For frequent pattern growth methods, it discusses FreeSpan and PrefixSpan algorithms. It then presents experimental results comparing the performance of Apriori, PrefixSpan, and SPAM algorithms based on execution time, number of patterns found, and memory usage. Finally, it discusses limitations of traditional objective measures like support and confidence for determining pattern interestingness and proposes alternative measures like lift.Clustering and Visualisation using R programming
Clustering and Visualisation using R programmingNixon Mendez
╠²
The document outlines various clustering and visualization techniques for analyzing microarray data of yeast cell cycles, including Principal Component Analysis, Multidimensional Scaling, K-means clustering, Self-Organizing Maps, and Hierarchical Clustering. It discusses methodologies to visualize and interpret gene expression data, while emphasizing the effect of cyclins on gene regulation. The analysis provides practical R code examples for implementing these techniques and presents datasets for further exploration.Chapter three data structure and algorithms qaybta quee
Chapter three data structure and algorithms qaybta queehabdi203062
╠²
The document discusses arrays as a fundamental data structure, outlining key operations such as insertion, searching, and deletion, specifically focusing on ordered and unordered arrays. It highlights the efficiency of binary search on ordered arrays compared to linear search, and also explores object storage within arrays, big-oh notation for algorithm efficiency, and trade-offs between unordered and ordered arrays. Additionally, it gives insights into implementation strategies and the appendices indicate advanced data structures that offer improved performance for various operations.Sequential Pattern Tree Mining
Sequential Pattern Tree MiningIOSR Journals
╠²
The document discusses a novel approach to sequential pattern mining using a structured tree framework that stores both frequent and non-frequent items, allowing for efficient mining with a single database scan. This method reduces the time and space complexities associated with existing algorithms by avoiding the generation of intermediate candidate sequences and minimizing the need for repeated database scans. Performance analysis demonstrates that this new algorithm significantly outperforms established techniques like GSP, PrefixSpan, and tree-based mining methods.Algorithm - Mergesort & Quicksort
Algorithm - Mergesort & Quicksort Varendra University Rajshahi-bangladesh
╠²
1. The document discusses the merge sort and quicksort algorithms.
2. Merge sort works by dividing an array into two halves, sorting each half recursively, and then merging the sorted halves into a single sorted array.
3. Quicksort works by selecting a pivot element and partitioning the array into two halves based on element values relative to the pivot.A survey paper on sequence pattern mining with incremental
A survey paper on sequence pattern mining with incrementalAlexander Decker
╠²
This document summarizes four algorithms for sequential pattern mining: GSP, ISM, FreeSpan, and PrefixSpan. GSP is an Apriori-based algorithm that incorporates time constraints. ISM extends SPADE to incrementally update patterns after database changes. FreeSpan uses frequent items to recursively project databases and grow subsequences. PrefixSpan also uses projection but claims to not require candidate generation. It recursively projects databases based on short prefix patterns. The document concludes by stating the goal was to find an efficient scheme for extracting sequential patterns from transactional datasets.More from Shaista Qadir (8)
Chapter - 2 introduction to Computer Organization.pdf
Chapter - 2 introduction to Computer Organization.pdfShaista Qadir
╠²
The document provides an overview of computer system organization, detailing the components such as the central processing unit (CPU), memory unit, and input/output devices. It explains the roles of the CPU, including the control unit and arithmetic logic unit, and describes different types of memory, including RAM, ROM, cache memory, and secondary storage devices like hard disks and solid-state drives. Additionally, exercises are included to reinforce understanding of the concepts presented.Chapter - 1 Introduction to Computer Science.pdf
Chapter - 1 Introduction to Computer Science.pdfShaista Qadir
╠²
The document provides an introduction to computer science, defining a computer as an electronic device that processes data into information. It outlines the information processing cycle, advantages and disadvantages of computers, and their classification based on size, purpose, and hardware design. Key points include the fast speed and reliability of computers, health risks associated with usage, and classifications such as supercomputers, mainframes, and microcomputers.Lecture 4
Lecture 4Shaista Qadir
╠²
This document discusses stacks, a linear data structure accessed from one end, operating on a Last In First Out (LIFO) basis. It covers various operations performed on stacks, including pushing and popping elements, as well as applications such as evaluating arithmetic expressions using infix, postfix, and prefix notations. Additionally, it provides algorithms for manipulating stacks and converting between different expression notations.Lecture 1
Lecture 1Shaista Qadir
╠²
The document provides an overview of different data structures and their types. It discusses linear data structures like arrays, linked lists, stacks and queues as well as non-linear structures like trees and graphs. Common operations on different data structures are also mentioned. The document further describes abstract data types and how they define the operations that can be performed on data without specifying implementation details.Sorting
SortingShaista Qadir
╠²
The document presents an overview of various sorting algorithms, including insertion sort, selection sort, bubble sort, and merge sort. It details each algorithm's methodology, advantages, disadvantages, and complexity in terms of best and worst-case scenarios. The content also includes code examples for implementing these sorting algorithms.Queue
QueueShaista Qadir
╠²
Chapter 5 discusses queues, which are FIFO data structures where elements are added to the rear and removed from the front. It covers operations like enqueue, dequeue, and checks for empty or clear status, as well as applications of queues in real-world scenarios. The chapter also introduces priority queues, which allow elements to be processed based on priority rather than strictly in order of arrival.linked list
linked listShaista Qadir
╠²
The document presents an overview of linked lists, including singly linked lists, doubly linked lists, and circular linked lists, detailing their structure and functions. It outlines algorithms for insertion, deletion, and searching within these lists, illustrated with class definitions and operations for singly and doubly linked lists. Additionally, specific methods for adding and removing nodes are provided, alongside descriptions of how these structures can be utilized in programming.Complexity Analysis
Complexity Analysis Shaista Qadir
╠²
Chapter 2 discusses complexity analysis of algorithms, covering properties of algorithms, computational complexity, time and space efficiency, and asymptotic notations like big-oh, omega, and theta. It emphasizes the importance of measuring an algorithm's efficiency and provides illustrative examples for understanding space and time requirements. The chapter concludes with examples on analyzing the complexity of various algorithms to determine their performance.Ad
Recently uploaded (20)
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
╠²
A presentation at Internetware 2025.2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
╠²
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
¤æŗ Introducing Data Contracts: An agreement between data producers and consumers
¤ōØ Data Contracts key components: Understanding a contract and its purpose
¤¦æŌĆŹ¤Ä© Writing your first contract: How to create your own contracts in OpenMetadata
¤”Š An OpenMetadata MCP Server update!
Ō×Ģ And More!Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software
╠²
Managing airport and airspace data is no small task, especially when youŌĆÖre expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts ŌĆō all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results ŌĆō streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FMEŌĆÖs AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
╠²
ū×ū©ūøū¢ ūóūÖūæūĢūōūÖūØ ū¬ūóū®ūÖūÖū¬ūÖ ūæūóū£ 3/4/5 ū”ūÖū©ūÖūØ, ūóūō 22 ūöūŚū£ūżūĢū¬ ūøū£ūÖūØ ūóūØ ūøū£ ūÉūżū®ū©ūĢūÖūĢū¬ ūöūóūÖūæūĢūō ūöūōū©ūĢū®ūĢū¬.╠²ūæūóū£ ū®ūśūŚ ūóūæūĢūōūö ūÆūōūĢū£ ūĢū×ūŚū®ūæ ūĀūĢūŚ ūĢū¦ū£ ū£ūöūżūóū£ūö ūæū®ūżūö ūöūóūæū©ūÖū¬/ū©ūĢūĪūÖū¬/ūÉūĀūÆū£ūÖū¬/ūĪūżū©ūōūÖū¬/ūóū©ūæūÖū¬ ūĢūóūĢūō..
ū×ūĪūĢūÆū£ ū£ūæū”ūó ūżūóūĢū£ūĢū¬ ūóūÖūæūĢūō ū®ūĢūĀūĢū¬ ūöū×ū¬ūÉūÖū×ūĢū¬ ū£ūóūĀūżūÖūØ ū®ūĢūĀūÖūØ: ū¦ūÖūōūĢūŚ ūÉūĀūøūÖ, ūÉūĢūżū¦ūÖ, ūĀūÖūĪūĢū©, ūĢūøū©ūĪūĢūØ ūÉūĀūøūÖ.Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...Josef Weingand
╠²
IBM LTO10FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptx
FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: New Data: Passkey Adoption in the WorkforceCoordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the SameWar_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdf
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdfbiswajitbanerjee38
╠²
Russia is one of the most aggressive nations when it comes to state coordinated cyberattacksŌĆŖŌĆöŌĆŖand Ukraine has been at the center of their crosshairs for 3 years. This report, provided the State Service of Special Communications and Information Protection of Ukraine contains an incredible amount of cybersecurity insights, showcasing the coordinated aggressive cyberwarfare campaigns of Russia against Ukraine.
It brings to the forefront that understanding your adversary, especially an aggressive nation state, is important for cyber defense. Knowing their motivations, capabilities, and tactics becomes an advantage when allocating resources for maximum impact.
Intelligence shows Russia is on a cyber rampage, leveraging FSB, SVR, and GRU resources to professionally target UkraineŌĆÖs critical infrastructures, military, and international diplomacy support efforts.
The number of total incidents against Ukraine, originating from Russia, has steadily increased from 1350 in 2021 to 4315 in 2024, but the number of actual critical incidents has been managed down from a high of 1048 in 2022 to a mere 59 in 2024ŌĆŖŌĆöŌĆŖshowcasing how the rapid detection and response to cyberattacks has been impacted by UkraineŌĆÖs improved cyber resilience.
Even against a much larger adversary, Ukraine is showcasing outstanding cybersecurity, enabled by strong strategies and sound tactics. There are lessons to learn for any enterprise that could potentially be targeted by aggressive nation states.
Definitely worth the read!"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
╠²
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of DeepfakesImproving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...
Improving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...Safe Software
╠²
Utilities and water companies play a key role in the creation of clean drinking water. The creation and maintenance of clean drinking water is becoming a critical problem due to pollution and pressure on the environment. A lot of data is necessary to create clean drinking water. For fieldworkers, two types of data are key: Asset data in an asset management system (EAM for example) and Geographic data in a GIS (ArcGIS Utility Network ). Keeping this type of data up to date and in sync is a challenge for many organizations, leading to duplicating data and creating a bulk of extra attributes and data to keep everything in sync. Using FME, it is possible to synchronize Enterprise Asset Management (EAM) data with the ArcGIS Utility Network in real time. Changes (creation, modification, deletion) in ArcGIS Pro are relayed to EAM via FME, and vice versa. This ensures continuous synchronization of both systems without daily bulk updates, minimizes risks, and seamlessly integrates with ArcGIS Utility Network services. This presentation focuses on the use of FME at a Dutch water company, to create a sync between the asset management and GIS.The Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu
╠²
A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
╠²
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionLessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash
╠²
Lessons Learned from Developing Secure AI WorkflowsYou are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
Ad
Searching
- 1. Chapter 6Chapter 6 searChingsearChing 01/31/18 BY MS. SHAISTA QADIR 1 PRESENTED BY Shaista Qadir Lecturer king khalid university
- 2. COntentsCOntents ’üČ searChing ’üČ seQUentiaL searCh ’üČ exampLe ’üČ aLgOrithm ’üČ prOgram LOgiC ’üČ BinarY searCh ’üČ exampLe ’üČ aLgOrithm ’üČ prOgram LOgiC 01/31/18 BY MS. SHAISTA QADIR 2
- 3. searChingsearChing 01/31/18 BY MS. SHAISTA QADIR 3 ’éŚ Computer systems are often used to store large amounts of data. ’éŚ Sometimes data must be retrieved from storage based on a searching criteria. ’éŚ Efficient storage of data to facilitate fast searching.
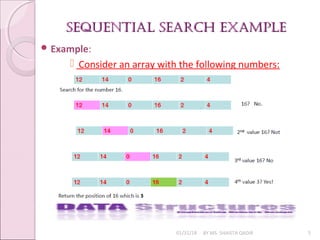
- 4. seQUentiaL searChseQUentiaL searCh 01/31/18 BY MS. SHAISTA QADIR 4 ’éŚ The sequential search (also called the Linear Search) is the simplest search algorithm. ’éŚ It is also the least efficient. ’éŚ It simply examines each element sequentially, starting with the first element, until it finds the ’éŚ key element or it reaches the end of the array. ’éŚ Application: To search a person in the train
- 5. SEQUENTIAL SEARCH ExAmpLESEQUENTIAL SEARCH ExAmpLE 01/31/18 BY MS. SHAISTA QADIR 5 ’éŚ Example: ’é¢ Consider an array with the following numbers:
- 6. SEQUENTIAL SEARCHSEQUENTIAL SEARCH ALGORITHmALGORITHm 01/31/18 BY MS. SHAISTA QADIR 6 ’éŚ ALGORITHM: (Postcondition: either the index i is returned where si = x, or ŌĆō1 is returned.) 1. Repeat steps 2ŌĆō3, for i = 0 to n ŌĆō 1. 2. If si = x, return i . 3. Return ŌĆō1.
- 7. SEQUENTIAL SEARCH pROGRAmSEQUENTIAL SEARCH pROGRAm LOGICLOGIC 01/31/18 BY MS. SHAISTA QADIR 7 ’éŚ PROGRAM LOGIC: public int seqsearch(int [ ]arr, int x) { for(int i=0; i< arr.length; i++) if(arr [ i ] == x) return i; return -1; } ’éŚ Time Complexity of Sequential search algorithm is: O(n)3.
- 8. BINARY SEARCHBINARY SEARCH 01/31/18 BY MS. SHAISTA QADIR 8 ’éŚ The binary search is the standard algorithm for searching through a sorted sequence. ’éŚ It is much more efficient than the sequential search. ’éŚ It repeatedly divides the sequence in two, each time restricting the search to the half that would contain the element ’éŚ Application: Binary search is used to search a word in a dictionary.
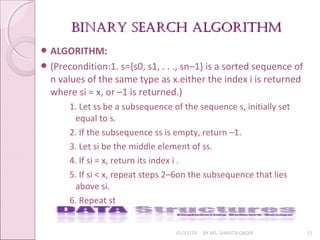
- 9. BINARY SEARCH ExAmplEBINARY SEARCH ExAmplE 01/31/18 BY MS. SHAISTA QADIR 9 ’éŚ Example: Condition : The array must be sorted. ’éŚ Consider an array with the following numbers: ’éŚ Divide-and-Conquer Strategy ’é¢ Search for the number 16. ’é¢ Calculate: mid=(First + last)/2
- 10. BINARY SEARCH ExAmplEBINARY SEARCH ExAmplE 01/31/18 BY MS. SHAISTA QADIR 10 ’éŚ Example: Condition : The array must be sorted. ’éŚ Return the position of 16 which is 3
- 11. BINARY SEARCH AlGORITHmBINARY SEARCH AlGORITHm 01/31/18 BY MS. SHAISTA QADIR 11 ’éŚ ALGORITHM: ’éŚ (Precondition:1. s={s0, s1, . . ., snŌĆō1} is a sorted sequence of n values of the same type as x.either the index i is returned where si = x, or ŌĆō1 is returned.) 1. Let ss be a subsequence of the sequence s, initially set equal to s. 2. If the subsequence ss is empty, return ŌĆō1. 3. Let si be the middle element of ss. 4. If si = x, return its index i . 5. If si < x, repeat steps 2ŌĆō6on the subsequence that lies above si. 6. Repeat st
- 12. BINARY SEARCH pROGRAmBINARY SEARCH pROGRAm lOGIClOGIC 01/31/18 BY MS. SHAISTA QADIR 12 ’éŚ PROGRAM LOGIC: public static int binarysearch(int[ ] a, int x) { int lo = 0; int hi = a.length; while (lo < hi) { int i = (lo + hi) / 2; if (a[i] == x) return i; else if (a[i] < x) lo = i+1; else hi = I; } return -1; } ’éŚ Time Complexity of binary search algorithm is: O(logn)
- 13. 01/31/18 BY MS. SHAISTA QADIR 13 THANK YOUTHANK YOU