Secure routing in DSR
Download as PPTX, PDF1 like602 views
This presentation helps you to understand how routing works in DSR Protocol in Ad-Hoc Networks. DSR protocols is used in Mobile Ad-hoc network.
1 of 17
Downloaded 30 times











Recommended
"Underrepresented" is not just a buzzword: A closer look at the lack of ethni...



"Underrepresented" is not just a buzzword: A closer look at the lack of ethni...Robyn Dahl
Ěý
Talk given at GSA Annual Meeting.
For abstract and details: https://gsa.confex.com/gsa/2016AM/webprogram/Paper284916.html
For more on these topics: www.robynmdahl.com/blogImproved dsr algo routing in manet



Improved dsr algo routing in manetmadhavsolanki
Ěý
This document summarizes a research paper on designing an energy routing protocol called EPAR to optimize power consumption in mobile ad hoc networks (MANETs). EPAR aims to minimize total transmission energy and maximize network lifetime. It calculates the battery power for each path and selects the path with the maximum lowest hop energy. Simulation results show that EPAR outperforms the original DSR protocol by 65% and achieves higher throughput than DSR and another protocol called MTPR in different network scenarios. EPAR and MTPR also produce longer network lifetimes than DSR when considering factors like packet delivery ratio.DSR Protocol



DSR Protocol@zenafaris91
Ěý
The Dynamic Source Routing protocol (DSR) is a simple and efficient routing protocol designed for use in wireless ad-hoc networks without existing infrastructure. DSR allows networks to self-organize and self-configure. It uses two main mechanisms: route discovery determines the optimal transmission path between nodes, while route maintenance ensures the path stays optimal and loop-free as network conditions change.DYNAMIC SOURCE ROUTING (DSR)



DYNAMIC SOURCE ROUTING (DSR)Shankha Subhra Ghosh
Ěý
Dynamic Source Routing uses route discovery to find routes between nodes. When a node receives a route request (RREQ) message, if it is the destination it returns a route reply (RREP) with the accumulated route record to the sender. If it is an intermediate node, it discards the RREQ if it has the same ID or finds its own address in the route, otherwise it appends its address to the route record and propagates the RREQ to neighbors to continue finding a path to the destination.Dynamic source routing



Dynamic source routingAshraf Uddin
Ěý
DSR is a source routing protocol for wireless ad hoc networks. It uses source routing whereby the source specifies the complete path to the destination in the packet header. Route discovery is done through route request broadcasts, and routes are cached for future use. Route maintenance is done through acknowledgements; if a link breaks, a route error is sent back to the source. Simulation results showed high packet delivery ratios even with high node mobility. DSR performs well for dynamic wireless networks.Database security



Database securityBirju Tank
Ěý
Database security involves protecting a database from unauthorized access, modification, or deletion. It aims to ensure the confidentiality, integrity, and availability of data through various mechanisms like access controls, encryption, firewalls, and authorization levels. These controls regulate how data flows between systems and users, prevent indirect data inferences, and restrict access to only authorized users and operations. The goal is to safeguard sensitive information in databases from both intentional and accidental security threats.Vulnerabilities in Android



Vulnerabilities in AndroidBirju Tank
Ěý
The document discusses vulnerabilities in the Android operating system. It begins by noting the dominance of Android and iOS in the smartphone market and the need for privacy awareness as malicious codes are increasingly reported. It then defines vulnerability as a weakness or soft spot, and lists some common types of vulnerabilities like invalidated inputs, broken access control, and SQL injection. The document also covers Android security features like encryption, sandboxing, and permissions, as well as current issues around mobile security including malicious apps, unsafe websites, and data security problems. It concludes that while Android utilizes sandboxing and permissions, optional permission assignments can still leave security loopholes.Blackhole Attck detection in AODV Protocol



Blackhole Attck detection in AODV ProtocolBirju Tank
Ěý
Covers black hole attck detection in AODV routing protocol of MANET. You can find method to detect the black hole attck and method to prevent it.5 g technology



5 g technologyBirju Tank
Ěý
This document provides an overview of 5G technology presented by students at GTU PG School, BISAG, GANDHINAGAR. 5G is described as the next major phase of mobile telecommunication that will offer transmission speeds up to 1 Gbps, making it 10 times faster than current technologies. The objectives of 5G include providing superior quality of service and user experience, reliable connectivity, and the ability to handle exponential growth in network capacity. The document traces the evolution of mobile technologies from 1G to 5G and concludes that 5G will revolutionize the world by 2020 and beyond through new concepts, innovations, and spectrums.Literature review report



Literature review reportBirju Tank
Ěý
This Document will help to understand how literature review done in MANET. This explains Security Issues in MANET.J2ME Mobile app



J2ME Mobile appBirju Tank
Ěý
This presentation may help you to understand how J2ME Application works. It contains different examples of J2ME Application.Android vs iOS encryption systems



Android vs iOS encryption systemsBirju Tank
Ěý
This will help you to understand the encryption system in Android and iOS. This presentation also contain comparison of encryption in both OS.Software prototyping



Software prototypingBirju Tank
Ěý
Basics about software prototyping. You may clearly understand how software prototyping is useful their pros and cons. Different types of software prototyping also there in presentation.Secure lab setup for cyber security



Secure lab setup for cyber securityBirju Tank
Ěý
This document outlines plans for setting up a secure cybersecurity lab with three main goals: 1) Support both Windows and Linux systems to emulate a real-world environment, 2) Be able to isolate the lab network from the campus network for exercises, and 3) Provide a mixed-use space for both security exercises and general usage. Key aspects of the lab setup include using virtual machines on physical systems to lower costs, purchasing a managed switch to isolate student workstations, and configuring older or vulnerable operating systems on student systems to simulate real-world targets.Data mining



Data miningBirju Tank
Ěý
The document provides an introduction to the concept of data mining, defining it as the extraction of useful patterns from large data sources through automatic or semi-automatic means. It discusses common data mining tasks like classification, clustering, prediction, and association rule mining. Examples of data mining applications are also given such as marketing, fraud detection, and scientific data analysis.Android operating system



Android operating systemBirju Tank
Ěý
Android is a software platform and operating system for mobile devices based on the Linux kernel. It was developed by Andy Rubin, Rich Miner, Nick Sears and Chris White and was later acquired by Google in 2005. Key features of Android include support for various wireless networks, an interface better than previous touchscreen mobiles, and the ability to access millions of applications. Android uses the Java programming language and allows developers to write once and deploy across many different devices.Virtualization



VirtualizationBirju Tank
Ěý
Virtualization allows multiple operating systems to run simultaneously on the same hardware. It provides benefits such as reduced costs, increased hardware utilization, and isolation of virtual machines. Popular virtualization providers include VMware, Red Hat, and Citrix, with VMware's Workstation, GSX Server, and ESX Server being useful virtualization products. Virtualization offers advantages like testing flexibility and disaster recovery benefits.Mobile Broadband Wireless Access



Mobile Broadband Wireless AccessBirju Tank
Ěý
The document summarizes the IEEE 802.20 standard for mobile broadband wireless access. Key points include:
- IEEE 802.20 defines the PHY and MAC layers for mobile broadband networks to provide data rates over 1 Mbps with support for vehicular mobility.
- It aims to fill the gap between cellular and wireless local area networks by providing greater coverage and mobility than WiFi but with higher data rates than 2G and 3G cellular networks.
- The standard supports applications requiring high-speed data access like video and VoIP through efficient packet-based transmission optimized for IP services. It also defines enhancements for conformance testing, system performance, management information, and bridging of 802.20 networks.Process management



Process managementBirju Tank
Ěý
The document discusses process management in operating systems. It defines a process as a program during execution, which requires resources like memory and CPU registers. The document outlines the life cycle of a process, including the different states a process can be in like ready, running, waiting, blocked. It describes process creation and termination. The process control block (PCB) contains information needed to control and monitor each process. Context switching allows the CPU to switch between processes. Scheduling determines which process enters the running state. The document lists some common process control system calls and discusses advantages and disadvantages of process management.Project Manager | Integrated Design Expert



Project Manager | Integrated Design ExpertBARBARA BIANCO
Ěý
Barbara Bianco
Project Manager and Project Architect, with extensive experience in managing and developing complex projects from concept to completion. Since September 2023, she has been working as a Project Manager at MAB Arquitectura, overseeing all project phases, from concept design to construction, with a strong focus on artistic direction and interdisciplinary coordination.
Previously, she worked at Progetto CMR for eight years (2015-2023), taking on roles of increasing responsibility: initially as a Project Architect, and later as Head of Research & Development and Competition Area (2020-2023).
She graduated in Architecture from the University of Genoa and obtained a Level II Master’s in Digital Architecture and Integrated Design from the INArch Institute in Rome, earning the MAD Award. In 2009, she won First Prize at Urban Promo Giovani with the project "From Urbanity to Humanity", a redevelopment plan for the Maddalena district of Genoa focused on the visual and perceptive rediscovery of the city.
Experience & Projects
Barbara has developed projects for major clients across various sectors (banking, insurance, real estate, corporate), overseeing both the technical and aesthetic aspects while coordinating multidisciplinary teams. Notable projects include:
The Sign Business District for Covivio, Milan
New L'Oréal Headquarters in Milan, Romolo area
Redevelopment of Via C. Colombo in Rome for Prelios, now the PWC headquarters
Interior design for Spark One & Spark Two, two office buildings in the Santa Giulia district, Milan (Spark One: 53,000 m²) for In.Town-Lendlease
She has also worked on international projects such as:
International Specialized Hospital of Uganda (ISHU) – Kampala
Palazzo Milano, a residential building in Taiwan for Chonghong Construction
Chua Lang Street Building, a hotel in Hanoi
Manjiangwan Masterplan, a resort in China
Key Skills
✔️ Integrated design: managing and developing projects from concept to completion
✔️ Artistic direction: ensuring aesthetic quality and design consistency
✔️ Project management: coordinating clients, designers, and multidisciplinary consultants
✔️ Software proficiency: AutoCAD, Photoshop, InDesign, Office Suite
✔️ Languages: Advanced English, Basic French
✔️ Leadership & problem-solving: ability to lead teams and manage complex processes in dynamic environmentsPrivilege Escalation Techniques and methodology.pdf



Privilege Escalation Techniques and methodology.pdfharshvikramshahi2
Ěý
Consolidated 40 different ways to escalate privilege Water Industry Process Automation & Control Monthly - April 2025



Water Industry Process Automation & Control Monthly - April 2025Water Industry Process Automation & Control
Ěý
Welcome to the April 2025 edition of WIPAC Monthly, the magazine brought to you by the LInkedIn Group Water Industry Process Automation & Control.
In this month's issue, along with all of the industries news we have a number of great articles for your edification
The first article is my annual piece looking behind the storm overflow numbers that are published each year to go into a bit more depth and look at what the numbers are actually saying.
The second article is a taster of what people will be seeing at the SWAN Annual Conference next month in Berlin and looks at the use of fibre-optic cable for leak detection and how its a technology we should be using more of
The third article, by Rob Stevens, looks at what the options are for the Continuous Water Quality Monitoring that the English Water Companies will be installing over the next year and the need to ensure that we install the right technology from the start.
Hope you enjoy the current edition,
OliverProduction Planning & Control and Inventory Management.pptx



Production Planning & Control and Inventory Management.pptxVirajPasare
Ěý
Production Planning and Control : Importance, Objectives and Functions . Inventory Management - Meaning, Types , Objectives, Selective Inventory Control : ABC AnalysisAirport Components Part2 ppt.pptx-Apron,Hangers,Terminal building



Airport Components Part2 ppt.pptx-Apron,Hangers,Terminal buildingPriyanka Dange
Ěý
Apron,Hangers,Terminal buildingUnit-03 Cams and Followers in Mechanisms of Machines.pptx



Unit-03 Cams and Followers in Mechanisms of Machines.pptxKirankumar Jagtap
Ěý
Unit-03 Cams and Followers.pptxWhy the Engineering Model is Key to Successful Projects



Why the Engineering Model is Key to Successful ProjectsMaadhu Creatives-Model Making Company
Ěý
In this PDF document, the importance of engineering models in successful project execution is discussed. It explains how these models enhance visualization, planning, and communication. Engineering models help identify potential issues early, reducing risks and costs. Ultimately, they improve collaboration and client satisfaction by providing a clear representation of the project.UHV UNIT-3 HARMONY IN THE FAMILY AND SOCIETY.pptx



UHV UNIT-3 HARMONY IN THE FAMILY AND SOCIETY.pptxariomthermal2031
Ěý
HARMONY IN THE FAMILY AND SOCIETY More Related Content
More from Birju Tank (11)
5 g technology



5 g technologyBirju Tank
Ěý
This document provides an overview of 5G technology presented by students at GTU PG School, BISAG, GANDHINAGAR. 5G is described as the next major phase of mobile telecommunication that will offer transmission speeds up to 1 Gbps, making it 10 times faster than current technologies. The objectives of 5G include providing superior quality of service and user experience, reliable connectivity, and the ability to handle exponential growth in network capacity. The document traces the evolution of mobile technologies from 1G to 5G and concludes that 5G will revolutionize the world by 2020 and beyond through new concepts, innovations, and spectrums.Literature review report



Literature review reportBirju Tank
Ěý
This Document will help to understand how literature review done in MANET. This explains Security Issues in MANET.J2ME Mobile app



J2ME Mobile appBirju Tank
Ěý
This presentation may help you to understand how J2ME Application works. It contains different examples of J2ME Application.Android vs iOS encryption systems



Android vs iOS encryption systemsBirju Tank
Ěý
This will help you to understand the encryption system in Android and iOS. This presentation also contain comparison of encryption in both OS.Software prototyping



Software prototypingBirju Tank
Ěý
Basics about software prototyping. You may clearly understand how software prototyping is useful their pros and cons. Different types of software prototyping also there in presentation.Secure lab setup for cyber security



Secure lab setup for cyber securityBirju Tank
Ěý
This document outlines plans for setting up a secure cybersecurity lab with three main goals: 1) Support both Windows and Linux systems to emulate a real-world environment, 2) Be able to isolate the lab network from the campus network for exercises, and 3) Provide a mixed-use space for both security exercises and general usage. Key aspects of the lab setup include using virtual machines on physical systems to lower costs, purchasing a managed switch to isolate student workstations, and configuring older or vulnerable operating systems on student systems to simulate real-world targets.Data mining



Data miningBirju Tank
Ěý
The document provides an introduction to the concept of data mining, defining it as the extraction of useful patterns from large data sources through automatic or semi-automatic means. It discusses common data mining tasks like classification, clustering, prediction, and association rule mining. Examples of data mining applications are also given such as marketing, fraud detection, and scientific data analysis.Android operating system



Android operating systemBirju Tank
Ěý
Android is a software platform and operating system for mobile devices based on the Linux kernel. It was developed by Andy Rubin, Rich Miner, Nick Sears and Chris White and was later acquired by Google in 2005. Key features of Android include support for various wireless networks, an interface better than previous touchscreen mobiles, and the ability to access millions of applications. Android uses the Java programming language and allows developers to write once and deploy across many different devices.Virtualization



VirtualizationBirju Tank
Ěý
Virtualization allows multiple operating systems to run simultaneously on the same hardware. It provides benefits such as reduced costs, increased hardware utilization, and isolation of virtual machines. Popular virtualization providers include VMware, Red Hat, and Citrix, with VMware's Workstation, GSX Server, and ESX Server being useful virtualization products. Virtualization offers advantages like testing flexibility and disaster recovery benefits.Mobile Broadband Wireless Access



Mobile Broadband Wireless AccessBirju Tank
Ěý
The document summarizes the IEEE 802.20 standard for mobile broadband wireless access. Key points include:
- IEEE 802.20 defines the PHY and MAC layers for mobile broadband networks to provide data rates over 1 Mbps with support for vehicular mobility.
- It aims to fill the gap between cellular and wireless local area networks by providing greater coverage and mobility than WiFi but with higher data rates than 2G and 3G cellular networks.
- The standard supports applications requiring high-speed data access like video and VoIP through efficient packet-based transmission optimized for IP services. It also defines enhancements for conformance testing, system performance, management information, and bridging of 802.20 networks.Process management



Process managementBirju Tank
Ěý
The document discusses process management in operating systems. It defines a process as a program during execution, which requires resources like memory and CPU registers. The document outlines the life cycle of a process, including the different states a process can be in like ready, running, waiting, blocked. It describes process creation and termination. The process control block (PCB) contains information needed to control and monitor each process. Context switching allows the CPU to switch between processes. Scheduling determines which process enters the running state. The document lists some common process control system calls and discusses advantages and disadvantages of process management.Recently uploaded (20)
Project Manager | Integrated Design Expert



Project Manager | Integrated Design ExpertBARBARA BIANCO
Ěý
Barbara Bianco
Project Manager and Project Architect, with extensive experience in managing and developing complex projects from concept to completion. Since September 2023, she has been working as a Project Manager at MAB Arquitectura, overseeing all project phases, from concept design to construction, with a strong focus on artistic direction and interdisciplinary coordination.
Previously, she worked at Progetto CMR for eight years (2015-2023), taking on roles of increasing responsibility: initially as a Project Architect, and later as Head of Research & Development and Competition Area (2020-2023).
She graduated in Architecture from the University of Genoa and obtained a Level II Master’s in Digital Architecture and Integrated Design from the INArch Institute in Rome, earning the MAD Award. In 2009, she won First Prize at Urban Promo Giovani with the project "From Urbanity to Humanity", a redevelopment plan for the Maddalena district of Genoa focused on the visual and perceptive rediscovery of the city.
Experience & Projects
Barbara has developed projects for major clients across various sectors (banking, insurance, real estate, corporate), overseeing both the technical and aesthetic aspects while coordinating multidisciplinary teams. Notable projects include:
The Sign Business District for Covivio, Milan
New L'Oréal Headquarters in Milan, Romolo area
Redevelopment of Via C. Colombo in Rome for Prelios, now the PWC headquarters
Interior design for Spark One & Spark Two, two office buildings in the Santa Giulia district, Milan (Spark One: 53,000 m²) for In.Town-Lendlease
She has also worked on international projects such as:
International Specialized Hospital of Uganda (ISHU) – Kampala
Palazzo Milano, a residential building in Taiwan for Chonghong Construction
Chua Lang Street Building, a hotel in Hanoi
Manjiangwan Masterplan, a resort in China
Key Skills
✔️ Integrated design: managing and developing projects from concept to completion
✔️ Artistic direction: ensuring aesthetic quality and design consistency
✔️ Project management: coordinating clients, designers, and multidisciplinary consultants
✔️ Software proficiency: AutoCAD, Photoshop, InDesign, Office Suite
✔️ Languages: Advanced English, Basic French
✔️ Leadership & problem-solving: ability to lead teams and manage complex processes in dynamic environmentsPrivilege Escalation Techniques and methodology.pdf



Privilege Escalation Techniques and methodology.pdfharshvikramshahi2
Ěý
Consolidated 40 different ways to escalate privilege Water Industry Process Automation & Control Monthly - April 2025



Water Industry Process Automation & Control Monthly - April 2025Water Industry Process Automation & Control
Ěý
Welcome to the April 2025 edition of WIPAC Monthly, the magazine brought to you by the LInkedIn Group Water Industry Process Automation & Control.
In this month's issue, along with all of the industries news we have a number of great articles for your edification
The first article is my annual piece looking behind the storm overflow numbers that are published each year to go into a bit more depth and look at what the numbers are actually saying.
The second article is a taster of what people will be seeing at the SWAN Annual Conference next month in Berlin and looks at the use of fibre-optic cable for leak detection and how its a technology we should be using more of
The third article, by Rob Stevens, looks at what the options are for the Continuous Water Quality Monitoring that the English Water Companies will be installing over the next year and the need to ensure that we install the right technology from the start.
Hope you enjoy the current edition,
OliverProduction Planning & Control and Inventory Management.pptx



Production Planning & Control and Inventory Management.pptxVirajPasare
Ěý
Production Planning and Control : Importance, Objectives and Functions . Inventory Management - Meaning, Types , Objectives, Selective Inventory Control : ABC AnalysisAirport Components Part2 ppt.pptx-Apron,Hangers,Terminal building



Airport Components Part2 ppt.pptx-Apron,Hangers,Terminal buildingPriyanka Dange
Ěý
Apron,Hangers,Terminal buildingUnit-03 Cams and Followers in Mechanisms of Machines.pptx



Unit-03 Cams and Followers in Mechanisms of Machines.pptxKirankumar Jagtap
Ěý
Unit-03 Cams and Followers.pptxWhy the Engineering Model is Key to Successful Projects



Why the Engineering Model is Key to Successful ProjectsMaadhu Creatives-Model Making Company
Ěý
In this PDF document, the importance of engineering models in successful project execution is discussed. It explains how these models enhance visualization, planning, and communication. Engineering models help identify potential issues early, reducing risks and costs. Ultimately, they improve collaboration and client satisfaction by providing a clear representation of the project.UHV UNIT-3 HARMONY IN THE FAMILY AND SOCIETY.pptx



UHV UNIT-3 HARMONY IN THE FAMILY AND SOCIETY.pptxariomthermal2031
Ěý
HARMONY IN THE FAMILY AND SOCIETY e-health to improve the effectiveness of the Healthcare system



e-health to improve the effectiveness of the Healthcare systemDr INBAMALAR T M
Ěý
e-health to improve the effectiveness of the Healthcare system, Telehealth technology – A new horizon in health care, Telemedicine, E-healthapplicationof differential equation.pptx



applicationof differential equation.pptxPPSTUDIES
Ěý
irst-order differential equations find applications in modeling various phenomena, including growth and decay processes, Newton's law of cooling, electrical circuits, falling body problems, and mixing problems. Artificial intelligence and Machine learning in remote sensing and GIS



Artificial intelligence and Machine learning in remote sensing and GISamirthamm2083
Ěý
Artificial intelligence and Machine learning in remote sensing and GIS Virtual Power plants-Cleantech-Revolution



Virtual Power plants-Cleantech-RevolutionAshoka Saket
Ěý
VPPs are virtual aggregations of distributed energy resources, such as energy storage, solar panels, and wind turbines, that can be controlled and optimized in real-time to provide grid services.SIMULATION OF FIR FILTER BASED ON CORDIC ALGORITHM



SIMULATION OF FIR FILTER BASED ON CORDIC ALGORITHMVLSICS Design
Ěý
Coordinate Rotation Digital Computer (CORDIC) discovered by Jack E Volder. It is a shift-add operation and iterative algorithm. CORDIC algorithm has wide area for several applications like digital signal processing, biomedical processing, image processing, radar signal processing, 8087 math coprocessor, the HP-35 calculator, Discrete Fourier, Discrete Hartley and Chirp-Z transforms, filtering, robotics, real time navigational system and also in communication systems. In this paper, we discussed about the CORDIC algorithm and CORDIC algorithm based finite impulse response low pass & high pass filter. We have generated the M-code for the CORDIC Algorithm and CORDIC Algorithm based FIR filter with the help of MATLAB 2010a.We also discussed about the frequency response characteristics of FIR filter.
"Introduction to VLSI Design: Concepts and Applications"



"Introduction to VLSI Design: Concepts and Applications"GtxDriver
Ěý
This document offers a detailed exploration of VLSI (Very Large-Scale Integration) design principles, techniques, and applications. Topics include transistor-level design, digital circuit integration, and optimization strategies for modern electronics. Ideal for students, researchers, and professionals seeking a comprehensive guide to VLSI technology.Floating Offshore Wind in the Celtic Sea



Floating Offshore Wind in the Celtic Seapermagoveu
Ěý
Floating offshore wind (FLOW) governance arrangements in the Celtic Sea case are changing and innovating in response to different drivers including domestic political priorities (e.g. net-zero, decarbonization, economic growth) and external shocks that emphasize the need for energy security (e.g. the war in Ukraine).
To date, the rules of the game that guide floating wind in the UK have evolved organically rather than being designed with intent, which has created policy incoherence and fragmented governance arrangements. Despite this fragmentation, the UK has a well-established offshore wind sector and is positioning itself to become a global leader in floating wind.
Marine governance arrangements are in a state of flux as new actors, resources, and rules of the game are being introduced to deliver on this aspiration. However, the absence of a clear roadmap to deliver on ambitious floating wind targets by 2030 creates uncertainty for investors, reduces the likelihood that a new floating wind sector will deliver economic and social value to the UK, and risks further misalignment between climate and nature goals.Telehealth technology – A new horizon in health care



Telehealth technology – A new horizon in health careDr INBAMALAR T M
Ěý
Telehealth technology – A new horizon in health care, Telemedicine, E-healthWater Industry Process Automation & Control Monthly - April 2025



Water Industry Process Automation & Control Monthly - April 2025Water Industry Process Automation & Control
Ěý
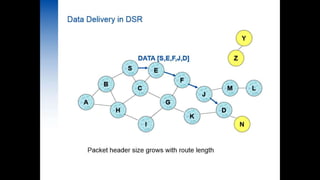
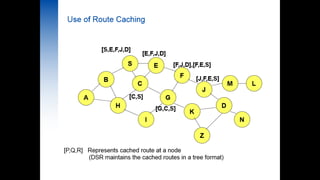
Secure routing in DSR
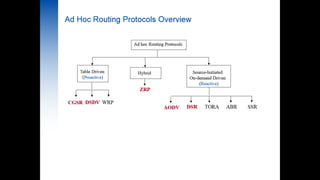
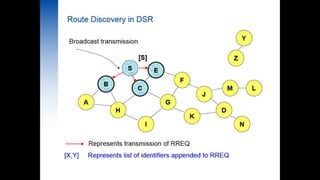
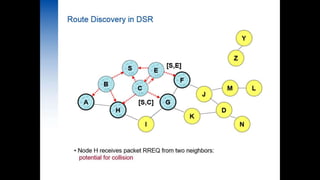
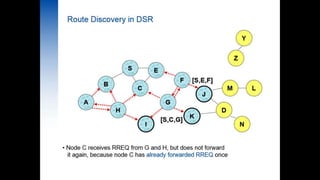
- 1. Secure Routing in DSR BY GROUP 4: Riya Chauhan(141060753016) Birju Tank((141060753017) Naman Vaishnav((141060753018) Dhara Patel((141060753019) Okasha Mahi((141060753020) DATE:17/04/2015 GTU PG SCHOOL – IEEE PRESENTATION
- 16. Attacks On DSR • Warm-Hole Attacks • Black-Hole Attack . .
- 17. References • “An Efficient Secure Route Discovery Protocol for DSR”Kulasekaran A. Sivakumar and Mahalingam Ramkumar Department of Computer Science and Engineering Mississippi State University, MS., 2007 IEEE, • “ASSOCIATION BETWEEN NODES TO COMBAT BLACKHOLE ATTACK IN DSR BASED MANET” N.Bhalaji, Dr.A.Shanmugam,Anna University Coimbatore,Tamilnadu, India




