Secure Socket Layer (SSL)
Download as PPT, PDF8 likes5,008 views
The document presents an overview of Secure Socket Layer (SSL) technology. It discusses how SSL establishes encrypted connections to provide security and integrity. It describes SSL architecture including certificates, hashing, asymmetric and symmetric data transfer, and the SSL handshake process. It also covers encryption algorithms like RC4, AES, Triple DES, and RSA that are used. Finally, it discusses asymmetric key cryptography algorithms like Diffie-Hellman and RSA, as well as symmetric key cryptography and the future scope of encryption standards.
1 of 18
Downloaded 249 times






Recommended
SSL



SSLBadrul Alam bulon
Ěý
The document discusses Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols for securing communications over a network. It explains that SSL uses certificates and keys to encrypt data between a client and server so only they can access it. It then describes the different versions of SSL, how SSL establishes encrypted connections, and provides diagrams of SSL and mutual authentication processes.Transport layer security (tls)



Transport layer security (tls)Kalpesh Kalekar
Ěý
Transport Layer Security (TLS) is a protocol that ensures privacy between communicating applications and their users on the Internet. When a server and client communicate, TLS ensures that no third party may eavesdrop or tamper with any message. TLS is the successor to the Secure Sockets Layer (SSL).Secure socket layer



Secure socket layerNishant Pahad
Ěý
SSL is a secure protocol that runs above TCP/IP and allows users to encrypt data and authenticate server and client identities securely. It uses public key encryption to generate a shared secret and establish an encrypted connection. The SSL handshake process verifies the server's identity and allows the client and server to agree on encryption algorithms before exchanging data. This helps prevent man-in-the-middle attacks by authenticating servers and encrypting the connection.SSL TLS Protocol



SSL TLS ProtocolDevang Badrakiya
Ěý
Brief explanation about TLS and SSL protocol handshake and message exchange process and its describe certificate validation.Introduction to Secure Sockets Layer



Introduction to Secure Sockets LayerNascenia IT
Ěý
Introduction to Secure Socket Layer (SSL) and Tunnel Layer Security (TLS). Shows basic principle of SSL and also little bit of practical applicability.Cryptography.ppt



Cryptography.pptUday Meena
Ěý
This document provides an overview of cryptography. It begins with basic definitions related to cryptography and a brief history of its use from ancient times to modern ciphers. It then describes different types of ciphers like stream ciphers, block ciphers, and public key cryptosystems. It also covers cryptography methods like symmetric and asymmetric algorithms. Common types of attacks on cryptosystems like brute force, chosen ciphertext, and frequency analysis are also discussed.Ssl (Secure Sockets Layer)



Ssl (Secure Sockets Layer)Asad Ali
Ěý
SSL is an acronym for Secure Sockets Layer. It is a protocol used for authenticating and encrypting web traffic. For web traffic to be authenticated means that your browser is able to verify the identity of the remote server.Secure Socket Layer



Secure Socket LayerNaveen Kumar
Ěý
SSL and TLS are security layers used below application layer of TCP/IP model. Structure and working of these layers are explained in the presentation. 2. public key cryptography and RSA



2. public key cryptography and RSADr.Florence Dayana
Ěý
Public Key Cryptography,Public-Key Cryptosystem,Rivest-Shamir-Adleman (RSA) Scheme,The Security of RSA,Optimal Asymmetric Encryption Padding (OAEP)
Ssl and tls



Ssl and tlsRana assad ali
Ěý
Transport Layer Security (TLS) is the successor to the Secure Sockets Layer (SSL) protocol. TLS ensures privacy and security between communicating applications and users on the internet by preventing eavesdropping, tampering, and message forgery. It works by having the client and server negotiate a cipher suite and protocol version to use to securely transmit encrypted messages. This establishes a secure channel over an unsecured network like the internet to provide confidentiality, integrity, and authentication of communications.DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg
Ěý
This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.Introduction to Cryptography



Introduction to CryptographySeema Goel
Ěý
The presentation covers the following:
Basic Terms
Cryptography
The General Goals of Cryptography
Common Types of Attacks
Substitution Ciphers
Transposition Cipher
Steganography- “Concealed Writing”
Symmetric Secret Key Encryption
Types of Symmetric Algorithms
Common Symmetric Algorithms
Asymmetric Secret Key Encryption
Common Asymmetric Algorithms
Public Key Cryptography
Hashing Techniques
Hashing Algorithms
Digital Signatures
Transport Layer Security
Public key infrastructure (PKI)
Email security



Email securityAhmed EL-KOSAIRY
Ěý
This document discusses email security threats and options to improve security. The main threats to email security are loss of confidentiality from emails being sent in clear text over open networks and stored on insecure systems, lack of integrity protection allowing emails to be altered, and lack of authentication and non-repudiation. Options to improve security include encrypting server-client connections using POP/IMAP over SSH or SSL, and end-to-end encryption using PGP. PGP provides encryption for confidentiality and digital signatures for authenticity and non-repudiation. The document also discusses email-based attacks and spam, as well as the algorithms and authentication process used by PGP.Secure Socket Layer (SSL)



Secure Socket Layer (SSL)Samip jain
Ěý
SSL is an internet protocol for secure exchange of information between a web browser and a web server.Transport layer security



Transport layer securityHrudya Balachandran
Ěý
TLS is an IETF standard similar to SSL that provides cryptographic security and secure connections between parties through the establishment of a secure session. It aims to securely transmit data via record layer encapsulation and encryption, using techniques like cryptographic computations, MACs, and the generation of secrets through pseudorandom functions and data expansion. TLS supports various cipher suites, certificate types, and alert codes while making some changes compared to SSL in areas like record formatting, PRF usage, and handshake messaging.Cryptography



CryptographyKalyani Government Engineering College
Ěý
This document presents an overview of cryptography including its definition, history, basic terms, classifications, techniques, advantages, disadvantages, and applications. Cryptography is defined as the art and science of achieving security by encoding messages. The earliest evidence of cryptography dates back 4000 years to ancient Egypt. Techniques covered include symmetric and asymmetric encryption, transposition ciphers, substitution ciphers, block ciphers, stream ciphers, hashing, and steganography. Advantages of cryptography include confidentiality, authentication, data integrity, and non-repudiation, while disadvantages include reduced accessibility and inability to ensure high availability. Cryptography has applications in defense, e-commerce, business transactions, internet payments, user identification, and data security.IPSec (Internet Protocol Security) - PART 1



IPSec (Internet Protocol Security) - PART 1Shobhit Sharma
Ěý
What is IPSec? What is Internet Protocol Security?
Presentation By Shobhit Sharma (ScriptKKiddie)
Read More At : https://www.technical0812.comPublic Key Cryptography



Public Key CryptographyGopal Sakarkar
Ěý
Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key aloneTLS - Transport Layer Security



TLS - Transport Layer SecurityByronKimani
Ěý
TLS (Transport Layer Security) is a cryptographic protocol that provides encryption and security for data sent over the internet. It is used by HTTPS to encrypt communication between web browsers and servers. TLS 1.2, the previous standard, had security flaws in how it exchanged encryption keys. TLS 1.3 improves security by using Diffie-Hellman key exchange so keys are not sent directly over the network. To upgrade a website from HTTP to HTTPS, an SSL certificate must be purchased and installed, all links on the site must be changed to HTTPS, and HTTP traffic should be redirected to HTTPS.Kerberos



KerberosSutanu Paul
Ěý
This document provides an overview of Kerberos, including:
- Kerberos is an authentication protocol that uses symmetric encryption and timestamps to allow nodes communicating over an insecure network to verify each other's identity securely.
- It works by having a client first authenticate with an authentication server to obtain a ticket-granting ticket, then uses that ticket to obtain additional tickets for access to other services.
- Kerberos addresses the need for secure authentication in distributed network environments where the workstations themselves cannot be fully trusted.SYMMETRIC CRYPTOGRAPHY 



SYMMETRIC CRYPTOGRAPHY Santosh Naidu
Ěý
SYMMETRIC CRYPTOGRAPHY
TOPICS TO BE COVERED:
Symmetric Cryptography
Symmetric encryption principles, Cryptography, Cryptanalysis, types of attacks on encryption messages, Feistel’s Cipher structure, block ciphers, Overview of DES, 3DES, AES, algorithms. Stream cipher structure, RC4 algorithm, Cipher block modes of operation, location of encryption devices, key distribution, Message Authentication, MAC, Secure hash and HMAC, SHA-1, MD5, applications of symmetric cryptography and hash functions.
S/MIME & E-mail Security (Network Security)



S/MIME & E-mail Security (Network Security)Prafull Johri
Ěý
This document discusses email security and encryption. It explains that email travels through unprotected networks and is exposed to attacks. It describes how email privacy aims to protect email from unauthorized access. Some remedies discussed are encrypting communication between servers using TLS and SASL authentication. The document also discusses using public-key cryptography for email encryption with tools like PGP and S/MIME, which can encrypt email content and add digital signatures for authentication. S/MIME is described as a security enhancement to the MIME email standard that provides encrypted and signed data functionality.Symmetric Cipher Model, Substitution techniques, Transposition techniques, St...



Symmetric Cipher Model, Substitution techniques, Transposition techniques, St...JAINAM KAPADIYA
Ěý
1) The document discusses symmetric encryption techniques including the symmetric cipher model, substitution techniques like the Caesar cipher and transposition techniques like the rail fence cipher.
2) It also covers the one-time pad cipher and its requirements for security as well as steganography techniques for hiding messages.
3) Cryptanalysis methods like brute force attacks and cryptanalytic attacks are explained for analyzing encryption algorithms.Transport Layer Security (TLS)



Transport Layer Security (TLS)Arun Shukla
Ěý
It is an IETF standardization initiative whose goal is to come out with an Internet standard Version of SSL. The presentation discusses all. Happy Learning. :)
SSL/TLS



SSL/TLSDr Anjan Krishnamurthy
Ěý
The document discusses SSL/TLS (Secure Sockets Layer/Transport Layer Security), which are cryptographic protocols that provide secure communication over the internet. It covers SSL/TLS concepts like handshaking, encryption, authentication. It also describes JSSE (Java Secure Socket Extension), the Java implementation of SSL/TLS, including its architecture, classes and configuration. The document provides references for further reading on SSL/TLS and JSSE.Email security



Email securityIndrajit Sreemany
Ěý
Electronic mail security requires confidentiality, authentication, integrity, and non-repudiation. Privacy Enhanced Mail (PEM) and Pretty Good Privacy (PGP) provide these security services for email. PEM uses canonical conversion, digital signatures, encryption, and base64 encoding. PGP provides authentication via digital signatures and confidentiality through symmetric encryption of messages with randomly generated session keys. Secure/Multipurpose Internet Mail Extensions (S/MIME) also supports signed and encrypted email to provide security.Transport Layer Security



Transport Layer SecurityChhatra Thapa
Ěý
Transport Layer Security (TLS) was designed to provide security at the transport layer and was derived from Secure Sockets Layer (SSL). TLS operates at the transport layer of the internet model and consists of four protocols: the handshake protocol for authentication and key exchange, the change cipher spec protocol for transitioning to the negotiated cryptographic settings, the alert protocol for transmitting error messages, and the record protocol for encapsulation of higher level protocols.Email security



Email securityBaliram Yadav
Ěý
This document discusses email security and the threats posed by unauthorized access and modification of emails. It outlines common threats like message interception, modification, false messages, and replay attacks. It emphasizes the importance of confidentiality, integrity, and availability for secure email. The document recommends steps for security at the sender's side like using incognito mode and avoiding public computers. It also suggests checking email headers and avoiding unknown attachments for security at the receiver's side. Finally, it describes PGP and S/MIME as methods for securely transmitting emails through encryption.Secure Socket Layer



Secure Socket Layerdwitigajab
Ěý
This presentation summarizes Secure Socket Layer (SSL) technology. It discusses how SSL uses encryption to provide security and integrity for data transmission. The presentation covers SSL architecture, including the certificate and hashing components. It also describes the SSL handshake process and how symmetric and asymmetric encryption algorithms are used to securely transfer data. Common algorithms like RSA, Diffie-Hellman, DES, and AES are also mentioned.Secure socket layer working



Secure socket layer workingSanjeevsharma620
Ěý
This document discusses SSL (Secure Sockets Layer) and the process of establishing an encrypted connection between a client and server. It covers topics such as SSL architecture, certificates, hashing, asymmetric and symmetric encryption used in SSL handshaking, and encryption algorithms like RSA, Diffie-Hellman, DES, Triple DES, and AES. Diagrams show the SSL design and workflow of a session, including the handshaking, change cipher, and alert protocols used to negotiate encryption settings and securely transfer application data over the encrypted connection.More Related Content
What's hot (20)
2. public key cryptography and RSA



2. public key cryptography and RSADr.Florence Dayana
Ěý
Public Key Cryptography,Public-Key Cryptosystem,Rivest-Shamir-Adleman (RSA) Scheme,The Security of RSA,Optimal Asymmetric Encryption Padding (OAEP)
Ssl and tls



Ssl and tlsRana assad ali
Ěý
Transport Layer Security (TLS) is the successor to the Secure Sockets Layer (SSL) protocol. TLS ensures privacy and security between communicating applications and users on the internet by preventing eavesdropping, tampering, and message forgery. It works by having the client and server negotiate a cipher suite and protocol version to use to securely transmit encrypted messages. This establishes a secure channel over an unsecured network like the internet to provide confidentiality, integrity, and authentication of communications.DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg
Ěý
This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.Introduction to Cryptography



Introduction to CryptographySeema Goel
Ěý
The presentation covers the following:
Basic Terms
Cryptography
The General Goals of Cryptography
Common Types of Attacks
Substitution Ciphers
Transposition Cipher
Steganography- “Concealed Writing”
Symmetric Secret Key Encryption
Types of Symmetric Algorithms
Common Symmetric Algorithms
Asymmetric Secret Key Encryption
Common Asymmetric Algorithms
Public Key Cryptography
Hashing Techniques
Hashing Algorithms
Digital Signatures
Transport Layer Security
Public key infrastructure (PKI)
Email security



Email securityAhmed EL-KOSAIRY
Ěý
This document discusses email security threats and options to improve security. The main threats to email security are loss of confidentiality from emails being sent in clear text over open networks and stored on insecure systems, lack of integrity protection allowing emails to be altered, and lack of authentication and non-repudiation. Options to improve security include encrypting server-client connections using POP/IMAP over SSH or SSL, and end-to-end encryption using PGP. PGP provides encryption for confidentiality and digital signatures for authenticity and non-repudiation. The document also discusses email-based attacks and spam, as well as the algorithms and authentication process used by PGP.Secure Socket Layer (SSL)



Secure Socket Layer (SSL)Samip jain
Ěý
SSL is an internet protocol for secure exchange of information between a web browser and a web server.Transport layer security



Transport layer securityHrudya Balachandran
Ěý
TLS is an IETF standard similar to SSL that provides cryptographic security and secure connections between parties through the establishment of a secure session. It aims to securely transmit data via record layer encapsulation and encryption, using techniques like cryptographic computations, MACs, and the generation of secrets through pseudorandom functions and data expansion. TLS supports various cipher suites, certificate types, and alert codes while making some changes compared to SSL in areas like record formatting, PRF usage, and handshake messaging.Cryptography



CryptographyKalyani Government Engineering College
Ěý
This document presents an overview of cryptography including its definition, history, basic terms, classifications, techniques, advantages, disadvantages, and applications. Cryptography is defined as the art and science of achieving security by encoding messages. The earliest evidence of cryptography dates back 4000 years to ancient Egypt. Techniques covered include symmetric and asymmetric encryption, transposition ciphers, substitution ciphers, block ciphers, stream ciphers, hashing, and steganography. Advantages of cryptography include confidentiality, authentication, data integrity, and non-repudiation, while disadvantages include reduced accessibility and inability to ensure high availability. Cryptography has applications in defense, e-commerce, business transactions, internet payments, user identification, and data security.IPSec (Internet Protocol Security) - PART 1



IPSec (Internet Protocol Security) - PART 1Shobhit Sharma
Ěý
What is IPSec? What is Internet Protocol Security?
Presentation By Shobhit Sharma (ScriptKKiddie)
Read More At : https://www.technical0812.comPublic Key Cryptography



Public Key CryptographyGopal Sakarkar
Ěý
Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key aloneTLS - Transport Layer Security



TLS - Transport Layer SecurityByronKimani
Ěý
TLS (Transport Layer Security) is a cryptographic protocol that provides encryption and security for data sent over the internet. It is used by HTTPS to encrypt communication between web browsers and servers. TLS 1.2, the previous standard, had security flaws in how it exchanged encryption keys. TLS 1.3 improves security by using Diffie-Hellman key exchange so keys are not sent directly over the network. To upgrade a website from HTTP to HTTPS, an SSL certificate must be purchased and installed, all links on the site must be changed to HTTPS, and HTTP traffic should be redirected to HTTPS.Kerberos



KerberosSutanu Paul
Ěý
This document provides an overview of Kerberos, including:
- Kerberos is an authentication protocol that uses symmetric encryption and timestamps to allow nodes communicating over an insecure network to verify each other's identity securely.
- It works by having a client first authenticate with an authentication server to obtain a ticket-granting ticket, then uses that ticket to obtain additional tickets for access to other services.
- Kerberos addresses the need for secure authentication in distributed network environments where the workstations themselves cannot be fully trusted.SYMMETRIC CRYPTOGRAPHY 



SYMMETRIC CRYPTOGRAPHY Santosh Naidu
Ěý
SYMMETRIC CRYPTOGRAPHY
TOPICS TO BE COVERED:
Symmetric Cryptography
Symmetric encryption principles, Cryptography, Cryptanalysis, types of attacks on encryption messages, Feistel’s Cipher structure, block ciphers, Overview of DES, 3DES, AES, algorithms. Stream cipher structure, RC4 algorithm, Cipher block modes of operation, location of encryption devices, key distribution, Message Authentication, MAC, Secure hash and HMAC, SHA-1, MD5, applications of symmetric cryptography and hash functions.
S/MIME & E-mail Security (Network Security)



S/MIME & E-mail Security (Network Security)Prafull Johri
Ěý
This document discusses email security and encryption. It explains that email travels through unprotected networks and is exposed to attacks. It describes how email privacy aims to protect email from unauthorized access. Some remedies discussed are encrypting communication between servers using TLS and SASL authentication. The document also discusses using public-key cryptography for email encryption with tools like PGP and S/MIME, which can encrypt email content and add digital signatures for authentication. S/MIME is described as a security enhancement to the MIME email standard that provides encrypted and signed data functionality.Symmetric Cipher Model, Substitution techniques, Transposition techniques, St...



Symmetric Cipher Model, Substitution techniques, Transposition techniques, St...JAINAM KAPADIYA
Ěý
1) The document discusses symmetric encryption techniques including the symmetric cipher model, substitution techniques like the Caesar cipher and transposition techniques like the rail fence cipher.
2) It also covers the one-time pad cipher and its requirements for security as well as steganography techniques for hiding messages.
3) Cryptanalysis methods like brute force attacks and cryptanalytic attacks are explained for analyzing encryption algorithms.Transport Layer Security (TLS)



Transport Layer Security (TLS)Arun Shukla
Ěý
It is an IETF standardization initiative whose goal is to come out with an Internet standard Version of SSL. The presentation discusses all. Happy Learning. :)
SSL/TLS



SSL/TLSDr Anjan Krishnamurthy
Ěý
The document discusses SSL/TLS (Secure Sockets Layer/Transport Layer Security), which are cryptographic protocols that provide secure communication over the internet. It covers SSL/TLS concepts like handshaking, encryption, authentication. It also describes JSSE (Java Secure Socket Extension), the Java implementation of SSL/TLS, including its architecture, classes and configuration. The document provides references for further reading on SSL/TLS and JSSE.Email security



Email securityIndrajit Sreemany
Ěý
Electronic mail security requires confidentiality, authentication, integrity, and non-repudiation. Privacy Enhanced Mail (PEM) and Pretty Good Privacy (PGP) provide these security services for email. PEM uses canonical conversion, digital signatures, encryption, and base64 encoding. PGP provides authentication via digital signatures and confidentiality through symmetric encryption of messages with randomly generated session keys. Secure/Multipurpose Internet Mail Extensions (S/MIME) also supports signed and encrypted email to provide security.Transport Layer Security



Transport Layer SecurityChhatra Thapa
Ěý
Transport Layer Security (TLS) was designed to provide security at the transport layer and was derived from Secure Sockets Layer (SSL). TLS operates at the transport layer of the internet model and consists of four protocols: the handshake protocol for authentication and key exchange, the change cipher spec protocol for transitioning to the negotiated cryptographic settings, the alert protocol for transmitting error messages, and the record protocol for encapsulation of higher level protocols.Email security



Email securityBaliram Yadav
Ěý
This document discusses email security and the threats posed by unauthorized access and modification of emails. It outlines common threats like message interception, modification, false messages, and replay attacks. It emphasizes the importance of confidentiality, integrity, and availability for secure email. The document recommends steps for security at the sender's side like using incognito mode and avoiding public computers. It also suggests checking email headers and avoiding unknown attachments for security at the receiver's side. Finally, it describes PGP and S/MIME as methods for securely transmitting emails through encryption.Similar to Secure Socket Layer (SSL) (20)
Secure Socket Layer



Secure Socket Layerdwitigajab
Ěý
This presentation summarizes Secure Socket Layer (SSL) technology. It discusses how SSL uses encryption to provide security and integrity for data transmission. The presentation covers SSL architecture, including the certificate and hashing components. It also describes the SSL handshake process and how symmetric and asymmetric encryption algorithms are used to securely transfer data. Common algorithms like RSA, Diffie-Hellman, DES, and AES are also mentioned.Secure socket layer working



Secure socket layer workingSanjeevsharma620
Ěý
This document discusses SSL (Secure Sockets Layer) and the process of establishing an encrypted connection between a client and server. It covers topics such as SSL architecture, certificates, hashing, asymmetric and symmetric encryption used in SSL handshaking, and encryption algorithms like RSA, Diffie-Hellman, DES, Triple DES, and AES. Diagrams show the SSL design and workflow of a session, including the handshaking, change cipher, and alert protocols used to negotiate encryption settings and securely transfer application data over the encrypted connection.SSLtalk



SSLtalkMatthew Aylard
Ěý
The document discusses the history and purpose of TLS/SSL, including how it uses asymmetric and symmetric cryptography. It describes how TLS/SSL works, including the handshake and record layers, cipher suites, and public key infrastructure (PKI). It notes that TLS/SSL secures communications between applications and transport layers in the OSI model. Examples of exploits like session hijacking and man-in-the-middle attacks are provided to illustrate the importance of encryption.Data encryption algorithm(edit)



Data encryption algorithm(edit)Hussain Almohammadi
Ěý
The document discusses data encryption algorithms and their importance for securing communications. It describes several common algorithms such as DES, 3DES, AES, Blowfish, and RSA. These algorithms encrypt data to make it secure during transmission and storage. The document also differentiates between symmetric and asymmetric encryption algorithms, and discusses factors like key size, encryption speed, and security level. It concludes that data encryption algorithms provide critical security and ensure availability of data.Ciphers



CiphersAhtesham Husain Shaikh
Ěý
This document provides an introduction to cipher suites used in TLS/SSL network protocols. It discusses the key components of a cipher suite, including the key exchange algorithm, authentication algorithm, bulk encryption algorithm, and message authentication code algorithm. An example cipher suite is provided to illustrate these components. Vulnerabilities related to cipher suites like SWEET32, POODLE, and BEAST are also mentioned. The document concludes by stating the importance of understanding SSL and TLS to prevent server vulnerabilities from being exploited.Basic Cryptography unit 4 CSS



Basic Cryptography unit 4 CSSDr. SURBHI SAROHA
Ěý
The document discusses various topics related to public key cryptography including:
1) Public key cryptography uses key pairs (public/private keys) to encrypt and decrypt messages securely. Private keys are kept secret while public keys can be openly distributed.
2) RSA is a commonly used public key cryptosystem that uses large prime numbers to encrypt data. It is considered secure if a large enough key is used.
3) Digital signatures authenticate messages by encrypting a hash of the message with the sender's private key, allowing verification with their public key.Cryptography



Cryptographyokolo chukwudumebi prince
Ěý
The document discusses various cryptographic concepts and algorithms. It begins with basic terms in cryptography like plain text, cipher text, encryption, decryption, and keys. It then explains symmetric and asymmetric key cryptography. Specific algorithms discussed include MD5, SHA-1, SHA-256, RIPEMD-160, and crypt. Code examples are provided to demonstrate generating hashes using these algorithms.SSL/TLS Handshake



SSL/TLS HandshakeArpit Agarwal
Ěý
This presentation gives a detailed understanding of SSL/TLS handshake and the basic idea of POODLE attackEncryption in Cryptography



Encryption in CryptographyUttara University
Ěý
Encryption is a fundamental concept in cryptography that involves the process of converting plaintext (readable and understandable data) into ciphertext (encoded and unintelligible data) using a mathematical algorithm and an encryption key. The primary purpose of encryption is to ensure the confidentiality and privacy of sensitive information during transmission or storage.
In the encryption process:
1. **Plaintext:** This is the original, readable data that is to be protected. It could be a message, a file, or any form of digital information.
2. **Encryption Algorithm:** An encryption algorithm is a set of mathematical rules and procedures that transform the plaintext into ciphertext. Common encryption algorithms include Advanced Encryption Standard (AES), RSA, and Triple DES.
3. **Encryption Key:** The encryption key is a piece of information used by the encryption algorithm to perform the transformation. The key determines the specific pattern and method by which the plaintext is converted into ciphertext. The strength of the encryption often depends on the length and randomness of the key.
4. **Ciphertext:** This is the result of the encryption process—the transformed and encoded data that appears random and is indecipherable without the corresponding decryption key.
Encryption serves several important purposes in the field of cryptography:
- **Confidentiality:** The primary goal of encryption is to keep information confidential and secure from unauthorized access. Even if an unauthorized party intercepts the ciphertext, they should be unable to understand or decipher it without the correct decryption key.
- **Integrity:** Encryption helps ensure the integrity of data by providing a means to detect any unauthorized modifications. If the ciphertext is altered, the decryption process will produce incorrect results, alerting the recipient to potential tampering.
- **Authentication:** In some encryption scenarios, the use of digital signatures or authenticated encryption helps verify the origin and authenticity of the encrypted data.
- **Secure Communication:** Encryption is widely used to secure communication over networks, such as the internet. Protocols like HTTPS (HTTP Secure) use encryption to protect the confidentiality of data transmitted between a web browser and a web server.
- **Data-at-Rest Protection:** Encryption is applied to data stored on devices or servers, ensuring that even if physical access is gained, the data remains protected from unauthorized viewing.
In summary, encryption is a crucial tool in the field of cryptography, providing a means to safeguard the confidentiality, integrity, and authenticity of sensitive information in various digital environments.CRYPTOGRAPHY_DOS_Symmetric-Key Cryptography.pptx



CRYPTOGRAPHY_DOS_Symmetric-Key Cryptography.pptxSVENISHA
Ěý
The same key is used for both encryption and decryption, meaning both sender and receiver must have access to the key.
Symmetric-key algorithms are generally faster than asymmetric-key algorithms, making them suitable for encrypting large amounts of data.
Common examples include AES, DES, and Blowfish, which are widely used in various applications.LEARN CRYPTOGRAPHY: What do they use? Series 2 of 3



LEARN CRYPTOGRAPHY: What do they use? Series 2 of 3Mark Morris
Ěý
Cryptography helps the world operate securely. Cryptography drives economies, armies, freedom, and BLOCKCHAIN. Learn about cryptography as Mark Morris takes you on an exciting tour of cryptography in use today.
Learn how cryptography is employed in blockchain technologies like Hyperledger, Ethereum, and Bitcoin and where they may be headed.
Understand the looming threats. Grasp how easy it is to employ and protect your assets with open source cryptography software.
In his second session of three, Mark will go over the cryptography utilized in leading blockhain platforms and cryptocurrencies; including zero-knowledge and homomorphic technology.
Mark Morris is the presenter and creator of the cryptographic series. Mark is an independent technology consultant and software design and development contractor, specializing in complex systems integration and advanced technology design and development for business and government.Ch11 Basic Cryptography



Ch11 Basic CryptographyInformation Technology
Ěý
Security+ Guide to Network Security Fundamentals, 3rd Edition, by Mark Ciampa
Knowledge and skills required for Network Administrators and Information Technology professionals to be aware of security vulnerabilities, to implement security measures, to analyze an existing network environment in consideration of known security threats or risks, to defend against attacks or viruses, and to ensure data privacy and integrity. Terminology and procedures for implementation and configuration of security, including access control, authorization, encryption, packet filters, firewalls, and Virtual Private Networks (VPNs).
CNIT 120: Network Security
http://samsclass.info/120/120_S09.shtml#lecture
Policy: http://samsclass.info/policy_use.htm
Many thanks to Sam Bowne for allowing to publish these presentations.Cryptography summary



Cryptography summaryNi
Ěý
Cryptography is used to protect information from unauthorized access by encrypting data. It involves the use of algorithms and keys to encrypt plain text into cipher text. There are two main types: symmetric cryptography which uses the same key to encrypt and decrypt, and asymmetric cryptography which uses a public/private key pair. Cryptography is applied in technologies like digital certificates, RSA, SSL, and digital signatures to securely transmit data, verify identities, and ensure integrity of communications.Introduction To PKI Technology



Introduction To PKI TechnologySylvain Maret
Ěý
The document provides an overview of a course on PKI (Public Key Infrastructure) technology. It outlines the topics that will be covered over two days, including secret key cryptography algorithms like AES and RSA, digital certificates, certificate authorities, and practical PKI applications like S/MIME, SSL, and IPSEC. The objectives of the course are to understand cryptographic fundamentals, public key infrastructure elements and how they interact, and why PKI is useful for enabling e-commerce and enhancing security.Web cryptography javascript



Web cryptography javascriptJose Manuel Ortega Candel
Ěý
The document discusses introducing cryptography concepts from a developer perspective using JavaScript. It covers authentication and encryption methods like AES, RSA, and hashing algorithms. It also discusses browser storage, the Web Cryptography API, cryptography libraries for JavaScript like CryptoJS, encrypting data on servers with Node.js, and tools for analyzing encryption. Practical examples are provided on implementing cryptography in apps.The Time-Consuming Task Of Preparing A Data Set For...



The Time-Consuming Task Of Preparing A Data Set For...Kimberly Thomas
Ěý
The document discusses preparing data sets for analysis in data mining and privacy preserving techniques. It states that preparing data sets is a time-consuming task that requires complex SQL queries, joining tables, and aggregating columns. Significant manual effort is needed to build data sets in a horizontal layout. It also discusses the need for privacy-preserving algorithms to protect sensitive data during the data mining process. The document proposes using case, pivot and SPJ methods to horizontally aggregate data, then employing a homomorphic encryption scheme to preserve privacy during the aggregations. Homomorphic encryption allows computations on encrypted data to produce an encrypted result that matches the result of operations on plaintext.Secrity project keyvan



Secrity project keyvanitrraincity
Ěý
1. Cryptography is used to provide security in electronic commerce by ensuring privacy, authenticity, and preventing forgery, alteration, eavesdropping and tracing of messages.
2. There are two main types of cryptography - symmetric which uses the same key for encryption and decryption, and asymmetric (public key) which uses different keys for encryption and decryption.
3. Common symmetric algorithms are DES and AES while RSA is an example of an asymmetric algorithm commonly used for digital signatures and encryption.Sw prezen3pdf



Sw prezen3pdfs1190088
Ěý
Encryption is used to secure private information such as credit card details, bank account information, and personal correspondence from unauthorized access. There are different types of encryption including symmetric key encryption where both parties use the same secret key, public key encryption which uses separate keys for encryption and decryption, and TLS which provides security for communications through protocols like SSL. Hash functions are also used for encryption through computing hash values from inputs and incorporating them into algorithms to detect tampering of data.Encryption Primer por Cathy Nolan



Encryption Primer por Cathy NolanJoao Galdino Mello de Souza
Ěý
The document provides an overview of encryption:
1) Encryption is the process of encoding information to prevent unauthorized access. It involves transforming plain text into ciphertext using cryptographic algorithms and encryption keys.
2) There are two main types of encryption - symmetric which uses the same key for encryption and decryption, and asymmetric which uses a public/private key pair.
3) When implementing encryption, organizations must determine what data needs protection, how it will be encrypted both in transit and at rest, and how encryption keys will be managed. Failure to properly manage keys could result in permanent data loss.Sw2 prezen3pdf



Sw2 prezen3pdfs1190088
Ěý
This document discusses different types of encryption used to secure information. It introduces symmetric key encryption, which uses the same key to encrypt and decrypt, and public key encryption, which uses separate keys. It also mentions TLS/SSL protocols for secure communication and hash functions, which are incorporated into algorithms to detect tampering and enable faster data processing and comparison.Secure Socket Layer (SSL)
- 1. “ Secure Socket Layer” Project Presentation by: Dwiti Gajab Mihir Trivedi Aman Chaurasia
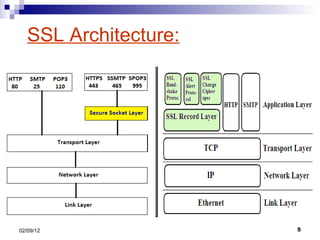
- 2. Contents: Cryptography and Secure Socket Layer (SSL) Establishment of Secured connection for “Encryption” Briefing on Asymmetric Encryption algorithms
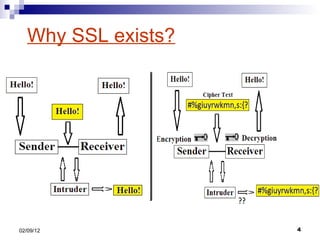
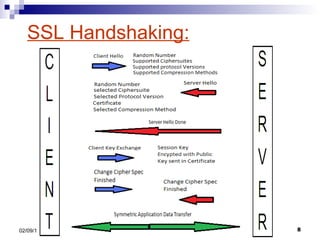
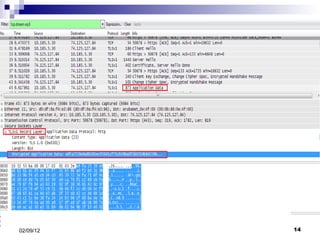
- 3. Cryptography: Security and Integrity Encryption helps in achieving this. SSL is one such type of protocols. Its two main functions are: Encryption Identification
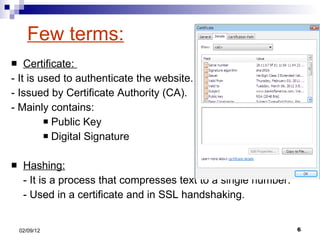
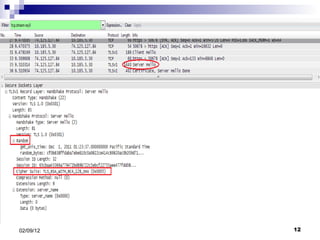
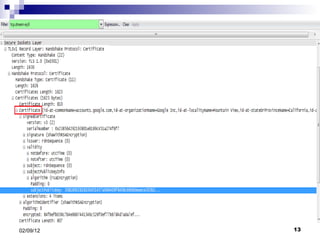
- 6. Few terms: Certificate: - It is used to authenticate the website. - Issued by Certificate Authority (CA). - Mainly contains: Public Key Digital Signature Hashing: - It is a process that compresses text to a single number. - Used in a certificate and in SSL handshaking.
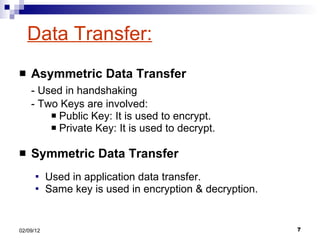
- 7. Data Transfer: Asymmetric Data Transfer - Used in handshaking - Two Keys are involved: Public Key: It is used to encrypt. Private Key: It is used to decrypt. Symmetric Data Transfer Used in application data transfer. Same key is used in encryption & decryption.
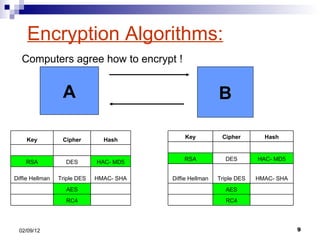
- 9. Encryption Algorithms: A B Computers agree how to encrypt ! Ěý RC4 Ěý Ěý AES Ěý HMAC- SHA Triple DES Diffie Hellman HAC- MD5 DES RSA Ěý Ěý Ěý Hash Cipher Key Ěý RC4 Ěý Ěý AES Ěý HMAC- SHA Triple DES Diffie Hellman HAC- MD5 DES RSA Ěý Ěý Ěý Hash Cipher Key
- 10. Ěý
- 11. Ěý
- 12. Ěý
- 13. Ěý
- 14. Ěý
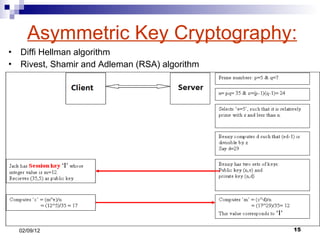
- 15. Asymmetric Key Cryptography: Diffi Hellman algorithm Rivest, Shamir and Adleman (RSA) algorithm
- 16. Symmetric key Cryptography: Used for encryption of data. Substitution/Transposition/Simple round ciphers. Modern round ciphers: DES, Triple DES, AES
- 17. Future Scope: Development of RSA algorithm for better security. References: Data communication and Networking, 4E, by Behrouz A. Forouzan Computer Networks by Ross & Kurose Network Security IOS by CISCO. http:// en.wikipedia.org/wiki/Secure_Sockets_Layer http://httpd.apache.org/docs/2.0/ssl/ssl_intro.html
- 18. Any Questions??? Thank łŰ´ÇłÜ…