SECURITY
Download as pptx, pdf0 likes191 views
This document describes a face recognition security system that uses PCA (principal component analysis) algorithm to authenticate users. The system extracts facial features from images to generate templates, which it compares to templates in a database. If a match is found, the user is validated and an alarm circuit is deactivated. Otherwise, the alarm sounds. It concludes that the system successfully identifies users from facial images and generates monthly attendance reports for employees.
1 of 18
Download to read offline











Ad
Recommended
Datamining
DataminingNeha Agrawal
Ěý
This document outlines a fruit classifier system that uses data mining techniques to predict fruit names based on their features. It describes the motivation, scope, dataset, features, algorithms, and technologies used. The system uses KNN, Naive Bayes, and decision tree algorithms to classify fruits, and it provides a comparison of their accuracies. It also discusses the preprocessing, cross validation strategy, and tools/techniques implemented, including Python libraries and algorithms like KNN, Naive Bayes, and decision trees.Andrew Bossy. Data Imputation Using Reverse ML
Andrew Bossy. Data Imputation Using Reverse MLLviv Startup Club
Ěý
This document discusses various methods for data imputation and restoration using reverse machine learning. It describes types of missing data and common imputation techniques like mean, median, mode, regression, KNN, and MICE. Advanced generative models for imputation including VAE, GAIN, MisGAN, and VIGAN are also covered. The document proposes training autoencoders with dropout and regularization as a reverse machine learning technique for data restoration, finding it achieves better accuracy than classical methods.Creating Your First Predictive Model In Python
Creating Your First Predictive Model In PythonRobert Dempsey
Ěý
This document outlines a step-by-step guide for creating a predictive model in Python, focusing on various aspects such as selecting the right modeling technique, preparing data, validating results, and implementing the model in production. Key topics include feature selection, training the model, and ensuring accuracy over time. It emphasizes the use of libraries like Scikit-learn and techniques like logistic regression, training/testing splits, and model serialization with pickle.Hardware softwareAgustin Frias
Ěý
El documento explica los componentes básicos de una computadora, incluyendo el hardware, software, CPU, memoria, perifĂ©ricos y sistemas operativos. Define hardware como los componentes fĂsicos como la CPU, memoria y perifĂ©ricos. Explica que el software son los programas y procesos que determinan las acciones de la máquina como Windows y aplicaciones. Luego describe cada componente principal como la CPU, memoria, perifĂ©ricos de entrada/salida y almacenamiento, y cĂłmo funciona básicamente una computadora.Principais diferenças entre ead e eol fĂłrum 4Rosa Serra
Ěý
O documento compara educação a distância (EAD) e educação on-line (EOL), explicando que EAD envolve ensino mediado por tecnologia com professores e alunos separados espacialmente, permitindo interação online e aulas presenciais, enquanto EOL se baseia em aprendizado via internet usando e-learning, videoconferência e teleconferência.ZacharyZahlResumeLinkedIn
ZacharyZahlResumeLinkedInZack Zahl
Ěý
This document is a resume for Zachary Zahl. It summarizes his experience as a sales professional, including 3 years at AppCard Inc. where he advanced from Sales Representative to Senior Success Manager. It also lists his education including a Bachelor of Science in Business and Spanish from University of Mary Washington, and highlights his skills in computer programs, Spanish fluency, and volunteer experience teaching ESL.Hitesh_resume
Hitesh_resumeHitesh Rathod
Ěý
Hitesh Premjibhai Rathod is applying for a position and provides his resume. He has a Bachelor of Commerce degree from Saurashtra University. He has over 8 years of work experience in roles involving retail sales, customer service, and PC hardware and software support. His technical skills include knowledge of computer hardware, troubleshooting, and experience working with laptops, desktops and printers. He is seeking to utilize and upgrade his knowledge and be a valuable contributor to a company.PresentaciĂłn conceptos generalesyensyloreee
Ěý
La comunicación en informática implica el intercambio de datos entre computadoras a través de conexiones y protocolos comunes. Los medios de comunicación transmiten mensajes de forma textual, sonora, visual o audiovisual. El trabajo colaborativo es una herramienta fundamental en educación y empresas para desarrollar actividades de manera efectiva. Las plataformas informáticas gestionan procesos organizacionales y evolucionan continuamente.Brief (1)
Brief (1)10reyaar
Ěý
This document outlines the requirements for a coursework assignment to design a new music magazine, which includes developing initial ideas, draft designs, taking original photographs, creating fictional music artists, and analyzing other music magazines. Students must create a front cover, contents page, and double page spread using only self-taken images and no stock photos. The completed project is due on February 5th, 2016.Mind + body = wellness
Mind + body = wellnessMaryalice Anderson
Ěý
The document discusses the relationship between mind, body, and wellness. It states that when the mind is healthy, the body will follow. It encourages motivating the mind through questioning, making new friends to aid social wellness, exercising to work the body, and eating well to stay healthy. References are provided to support the concepts discussed.Pasos para publicar en slideshareyensyloreee
Ěý
El documento proporciona 13 pasos para publicar un documento en şÝşÝߣShare. Estos incluyen registrarse en el sitio web de şÝşÝߣShare, cargar una foto de perfil, subir el documento en formato PowerPoint, agregar un tĂtulo, descripciĂłn y etiquetas clave, seleccionar una categorĂa, y guardar el documento para que quede publicado con un enlace Ăşnico que puede compartirse.MoliendaAndres fernandez.raigan@gmail.com
Ěý
La molienda es la Ăşltima etapa de reducciĂłn del tamaño de partĂculas del mineral para su concentraciĂłn. Se usan molinos para reducir el tamaño del mineral a menos de 200 mallas. La molienda implica controlar variables como la carga, agua, bolas y tiempo de molienda para lograr la finura deseada de manera eficiente.kitchen case study
kitchen case study azharkhan002
Ěý
The customer, Mr. Harris, wanted to complete the modern look of his newly renovated house with an open plan kitchen. He chose the German kitchen brand Schuller, which features matt anthracite doors that are balanced by cool white worksurfaces. The doors conceal a purpose-built, modern kitchen with clever storage solutions and an ergonomic design. Unlike other black kitchens that can appear cheap, the extension built for Mr. Harris's home provides natural light that shows off the anthracite doors in the minimalist setting he desired. Through consultation, LiebenDerKuche and the Schuller brand created a stunning kitchen that fulfilled Mr. Harris's brief of being minimalist and original.Separaciones por membranasRainier Maldonado Blanco
Ěý
Este documento trata sobre separaciones con membranas. Brevemente describe que una membrana es un material semipermeable que permite el paso selectivo de especies, y que la selectividad se debe al tamaño, forma, solubilidad, carga o polaridad de las moléculas. Luego presenta ejemplos de aplicaciones industriales como microfiltración, ultrafiltración, ósmosis inversa y diálisis. Finalmente, explica conceptos como permeabilidad, polarización de concentración y diferentes patrones de flujo en procesos con membranas.Nutrients deficiency symptoms in plants
Nutrients deficiency symptoms in plantsDr. MU Haq Yousufzai
Ěý
The document discusses various nutrient deficiencies that can occur in plants, including deficiencies of nitrogen, phosphorus, potassium, calcium, magnesium, sulfur, zinc, copper, iron, manganese, boron, molybdenum, chloride, and nickel. It notes that any deficiency of an essential nutrient can limit crop yields and advises farmers to identify nutrient deficiencies and protect crops from "hidden hunger" to ensure better yields. The document also discusses nutrient antagonism and synergism.Face recognization
Face recognizationleenak770
Ěý
This document provides an overview of face recognition technology. It discusses 2D and 3D facial recognition, how the technology works by measuring facial features to create a unique face print, hardware and software requirements, advantages like identifying repeat offenders, and applications in security, multimedia, and law enforcement. The conclusion states that while progress has been made, continued work is needed to develop more accurate systems.IRJET- Real-Time Face Tracking for Password Authentication
IRJET- Real-Time Face Tracking for Password AuthenticationIRJET Journal
Ěý
1. The document describes a real-time face tracking system for password authentication using an ARM controller.
2. The system uses a MATLAB algorithm to detect faces in real-time from a camera and compare it to registered images. If matched, it prompts the user to enter a password.
3. If the correct password is entered, a relay is activated to open a shutter, simulating a cash withdrawal from an ATM. The system aims to improve ATM security beyond just PIN numbers.IRJET - Face Detection and Recognition System
IRJET - Face Detection and Recognition SystemIRJET Journal
Ěý
The document describes a face detection and recognition system that uses machine learning algorithms. It analyzes facial structures in images and compares them to a dataset of facial models to identify matches. The system performs background subtraction, face detection, face recognition, and tracking. It was created to provide quick, accurate and contactless biometric security but could also be used for applications like attendance tracking. The system architecture includes modules for motion detection, face detection, face recognition and tracking a detected face. It was designed to be easily adaptable and allow additional functionality to be added.Security by user through application to lock/unlock machine by face detection
Security by user through application to lock/unlock machine by face detectionIRJET Journal
Ěý
This document describes a proposed system for providing security to laptops and mobile devices using face detection and authentication. The system would use a laptop's camera to capture an image of anyone attempting to unlock the laptop. That image and a notification would then be sent to the owner's smartphone app. The app would allow the owner to remotely lock the laptop, retrieve data, log the user out, or take other security actions. The document discusses the system architecture, scope, algorithms used including eigenfaces for face detection and REST for communication. It provides details on how face detection and eigenfaces work to identify faces and compares them to stored images for authentication. The proposed system is intended to provide improved security over password-only systems by verifying theUbiquitious Computing system : Integrating RFID with Face Recognition systems
Ubiquitious Computing system : Integrating RFID with Face Recognition systemsShahryar Ali
Ěý
This document describes a student attendance system that integrates RFID and face recognition technologies. RFID tags are used to record when students enter the classroom, while a camera and face recognition software verify students' identities. The system aims to automate attendance tracking and prevent illegal use of RFID cards. It discusses the components, workings, and standards of RFID systems as well as an overview of face recognition using principal component analysis. MATLAB is used to implement a prototype that detects faces in images and recognizes students with over 95% accuracy based on a real-time face database. The integrated system aims to provide efficient, secure, and error-free attendance tracking.Improved Approach for Eigenface Recognition
Improved Approach for Eigenface RecognitionBRNSSPublicationHubI
Ěý
This document describes research on an improved approach for eigenface recognition. The key points are:
- Eigenface recognition is a common method for face recognition that uses principal component analysis to define a face space from a training set of faces.
- The proposed improved eigenface approach aims to achieve better accuracy than existing approaches. It uses MATLAB to design and develop the algorithm.
- The methodology involves loading training images, constructing the face space using mean images and eigenvectors, and classifying new images by comparing them to existing face classes.
- Experimental results show the improved eigenface approach provides better performance than existing methods for face recognition.Criminal Detection System
Criminal Detection SystemIntrader Amit
Ěý
The document outlines the development of a Criminal Detection System that utilizes facial recognition algorithms to identify individuals from images. It details the motivation, methodologies, and technologies used, focusing on neural networks and various algorithms like PCA and MPCA-LDA to enhance accuracy in face detection under diverse conditions. The approach aims to create a robust and user-friendly system for security applications in high-traffic environments.Pattern recognition facial recognition
Pattern recognition facial recognitionMazin Alwaaly
Ěý
The document discusses facial recognition technology, which identifies individuals in digital images by analyzing facial features. It covers the history, applications, types of comparisons, components, and techniques used in face recognition, highlighting its use in security, banking, and social media. Additionally, it presents the advantages and disadvantages of this technology, including cost-effectiveness and issues related to accuracy.Face Recognition Proposal Presentation
Face Recognition Proposal PresentationMd. Atiqur Rahman
Ěý
This document outlines a project on face recognition. It discusses biometrics and why face recognition was chosen over other methods. Applications of face recognition are presented for law enforcement, security, immigration, residential security, banking, and mobile unlocking. The working process of face recognition involves inputting an image, detecting the face, and recognizing the face by matching it to a database. The current progress includes detecting faces and face parts using a modified Viola-Jones algorithm. Future work will involve matching detected faces to images in a created database for recognition. Advantages of face recognition include convenience and limitations include inability to distinguish identical twins.Face recognization 1
Face recognization 1leenak770
Ěý
This document provides an overview of facial recognition technology. It discusses how facial recognition works by measuring distinguishing features of the face. It covers 2D and 3D facial recognition, with 3D providing more accuracy. The document outlines the basic steps 3D facial recognition systems use to verify identity, including acquiring an image, determining head position/size, measuring facial curves to create a template, and matching templates. It also discusses the technology's advantages in identification, current and future applications, and some disadvantages regarding variations in poses, lighting and privacy issues.More Related Content
Viewers also liked (12)
ZacharyZahlResumeLinkedIn
ZacharyZahlResumeLinkedInZack Zahl
Ěý
This document is a resume for Zachary Zahl. It summarizes his experience as a sales professional, including 3 years at AppCard Inc. where he advanced from Sales Representative to Senior Success Manager. It also lists his education including a Bachelor of Science in Business and Spanish from University of Mary Washington, and highlights his skills in computer programs, Spanish fluency, and volunteer experience teaching ESL.Hitesh_resume
Hitesh_resumeHitesh Rathod
Ěý
Hitesh Premjibhai Rathod is applying for a position and provides his resume. He has a Bachelor of Commerce degree from Saurashtra University. He has over 8 years of work experience in roles involving retail sales, customer service, and PC hardware and software support. His technical skills include knowledge of computer hardware, troubleshooting, and experience working with laptops, desktops and printers. He is seeking to utilize and upgrade his knowledge and be a valuable contributor to a company.PresentaciĂłn conceptos generalesyensyloreee
Ěý
La comunicación en informática implica el intercambio de datos entre computadoras a través de conexiones y protocolos comunes. Los medios de comunicación transmiten mensajes de forma textual, sonora, visual o audiovisual. El trabajo colaborativo es una herramienta fundamental en educación y empresas para desarrollar actividades de manera efectiva. Las plataformas informáticas gestionan procesos organizacionales y evolucionan continuamente.Brief (1)
Brief (1)10reyaar
Ěý
This document outlines the requirements for a coursework assignment to design a new music magazine, which includes developing initial ideas, draft designs, taking original photographs, creating fictional music artists, and analyzing other music magazines. Students must create a front cover, contents page, and double page spread using only self-taken images and no stock photos. The completed project is due on February 5th, 2016.Mind + body = wellness
Mind + body = wellnessMaryalice Anderson
Ěý
The document discusses the relationship between mind, body, and wellness. It states that when the mind is healthy, the body will follow. It encourages motivating the mind through questioning, making new friends to aid social wellness, exercising to work the body, and eating well to stay healthy. References are provided to support the concepts discussed.Pasos para publicar en slideshareyensyloreee
Ěý
El documento proporciona 13 pasos para publicar un documento en şÝşÝߣShare. Estos incluyen registrarse en el sitio web de şÝşÝߣShare, cargar una foto de perfil, subir el documento en formato PowerPoint, agregar un tĂtulo, descripciĂłn y etiquetas clave, seleccionar una categorĂa, y guardar el documento para que quede publicado con un enlace Ăşnico que puede compartirse.MoliendaAndres fernandez.raigan@gmail.com
Ěý
La molienda es la Ăşltima etapa de reducciĂłn del tamaño de partĂculas del mineral para su concentraciĂłn. Se usan molinos para reducir el tamaño del mineral a menos de 200 mallas. La molienda implica controlar variables como la carga, agua, bolas y tiempo de molienda para lograr la finura deseada de manera eficiente.kitchen case study
kitchen case study azharkhan002
Ěý
The customer, Mr. Harris, wanted to complete the modern look of his newly renovated house with an open plan kitchen. He chose the German kitchen brand Schuller, which features matt anthracite doors that are balanced by cool white worksurfaces. The doors conceal a purpose-built, modern kitchen with clever storage solutions and an ergonomic design. Unlike other black kitchens that can appear cheap, the extension built for Mr. Harris's home provides natural light that shows off the anthracite doors in the minimalist setting he desired. Through consultation, LiebenDerKuche and the Schuller brand created a stunning kitchen that fulfilled Mr. Harris's brief of being minimalist and original.Separaciones por membranasRainier Maldonado Blanco
Ěý
Este documento trata sobre separaciones con membranas. Brevemente describe que una membrana es un material semipermeable que permite el paso selectivo de especies, y que la selectividad se debe al tamaño, forma, solubilidad, carga o polaridad de las moléculas. Luego presenta ejemplos de aplicaciones industriales como microfiltración, ultrafiltración, ósmosis inversa y diálisis. Finalmente, explica conceptos como permeabilidad, polarización de concentración y diferentes patrones de flujo en procesos con membranas.Nutrients deficiency symptoms in plants
Nutrients deficiency symptoms in plantsDr. MU Haq Yousufzai
Ěý
The document discusses various nutrient deficiencies that can occur in plants, including deficiencies of nitrogen, phosphorus, potassium, calcium, magnesium, sulfur, zinc, copper, iron, manganese, boron, molybdenum, chloride, and nickel. It notes that any deficiency of an essential nutrient can limit crop yields and advises farmers to identify nutrient deficiencies and protect crops from "hidden hunger" to ensure better yields. The document also discusses nutrient antagonism and synergism.Similar to SECURITY (20)
Face recognization
Face recognizationleenak770
Ěý
This document provides an overview of face recognition technology. It discusses 2D and 3D facial recognition, how the technology works by measuring facial features to create a unique face print, hardware and software requirements, advantages like identifying repeat offenders, and applications in security, multimedia, and law enforcement. The conclusion states that while progress has been made, continued work is needed to develop more accurate systems.IRJET- Real-Time Face Tracking for Password Authentication
IRJET- Real-Time Face Tracking for Password AuthenticationIRJET Journal
Ěý
1. The document describes a real-time face tracking system for password authentication using an ARM controller.
2. The system uses a MATLAB algorithm to detect faces in real-time from a camera and compare it to registered images. If matched, it prompts the user to enter a password.
3. If the correct password is entered, a relay is activated to open a shutter, simulating a cash withdrawal from an ATM. The system aims to improve ATM security beyond just PIN numbers.IRJET - Face Detection and Recognition System
IRJET - Face Detection and Recognition SystemIRJET Journal
Ěý
The document describes a face detection and recognition system that uses machine learning algorithms. It analyzes facial structures in images and compares them to a dataset of facial models to identify matches. The system performs background subtraction, face detection, face recognition, and tracking. It was created to provide quick, accurate and contactless biometric security but could also be used for applications like attendance tracking. The system architecture includes modules for motion detection, face detection, face recognition and tracking a detected face. It was designed to be easily adaptable and allow additional functionality to be added.Security by user through application to lock/unlock machine by face detection
Security by user through application to lock/unlock machine by face detectionIRJET Journal
Ěý
This document describes a proposed system for providing security to laptops and mobile devices using face detection and authentication. The system would use a laptop's camera to capture an image of anyone attempting to unlock the laptop. That image and a notification would then be sent to the owner's smartphone app. The app would allow the owner to remotely lock the laptop, retrieve data, log the user out, or take other security actions. The document discusses the system architecture, scope, algorithms used including eigenfaces for face detection and REST for communication. It provides details on how face detection and eigenfaces work to identify faces and compares them to stored images for authentication. The proposed system is intended to provide improved security over password-only systems by verifying theUbiquitious Computing system : Integrating RFID with Face Recognition systems
Ubiquitious Computing system : Integrating RFID with Face Recognition systemsShahryar Ali
Ěý
This document describes a student attendance system that integrates RFID and face recognition technologies. RFID tags are used to record when students enter the classroom, while a camera and face recognition software verify students' identities. The system aims to automate attendance tracking and prevent illegal use of RFID cards. It discusses the components, workings, and standards of RFID systems as well as an overview of face recognition using principal component analysis. MATLAB is used to implement a prototype that detects faces in images and recognizes students with over 95% accuracy based on a real-time face database. The integrated system aims to provide efficient, secure, and error-free attendance tracking.Improved Approach for Eigenface Recognition
Improved Approach for Eigenface RecognitionBRNSSPublicationHubI
Ěý
This document describes research on an improved approach for eigenface recognition. The key points are:
- Eigenface recognition is a common method for face recognition that uses principal component analysis to define a face space from a training set of faces.
- The proposed improved eigenface approach aims to achieve better accuracy than existing approaches. It uses MATLAB to design and develop the algorithm.
- The methodology involves loading training images, constructing the face space using mean images and eigenvectors, and classifying new images by comparing them to existing face classes.
- Experimental results show the improved eigenface approach provides better performance than existing methods for face recognition.Criminal Detection System
Criminal Detection SystemIntrader Amit
Ěý
The document outlines the development of a Criminal Detection System that utilizes facial recognition algorithms to identify individuals from images. It details the motivation, methodologies, and technologies used, focusing on neural networks and various algorithms like PCA and MPCA-LDA to enhance accuracy in face detection under diverse conditions. The approach aims to create a robust and user-friendly system for security applications in high-traffic environments.Pattern recognition facial recognition
Pattern recognition facial recognitionMazin Alwaaly
Ěý
The document discusses facial recognition technology, which identifies individuals in digital images by analyzing facial features. It covers the history, applications, types of comparisons, components, and techniques used in face recognition, highlighting its use in security, banking, and social media. Additionally, it presents the advantages and disadvantages of this technology, including cost-effectiveness and issues related to accuracy.Face Recognition Proposal Presentation
Face Recognition Proposal PresentationMd. Atiqur Rahman
Ěý
This document outlines a project on face recognition. It discusses biometrics and why face recognition was chosen over other methods. Applications of face recognition are presented for law enforcement, security, immigration, residential security, banking, and mobile unlocking. The working process of face recognition involves inputting an image, detecting the face, and recognizing the face by matching it to a database. The current progress includes detecting faces and face parts using a modified Viola-Jones algorithm. Future work will involve matching detected faces to images in a created database for recognition. Advantages of face recognition include convenience and limitations include inability to distinguish identical twins.Face recognization 1
Face recognization 1leenak770
Ěý
This document provides an overview of facial recognition technology. It discusses how facial recognition works by measuring distinguishing features of the face. It covers 2D and 3D facial recognition, with 3D providing more accuracy. The document outlines the basic steps 3D facial recognition systems use to verify identity, including acquiring an image, determining head position/size, measuring facial curves to create a template, and matching templates. It also discusses the technology's advantages in identification, current and future applications, and some disadvantages regarding variations in poses, lighting and privacy issues.A novel approach for performance parameter estimation of face recognition bas...
A novel approach for performance parameter estimation of face recognition bas...IJMER
Ěý
This document presents a novel approach for face recognition based on clustering, shape detection, and corner detection. The approach first clusters face key points and applies shape and corner detection methods to detect the face boundary and corners. It then performs both face identification and recognition on a large face database. The method achieves lower false acceptance rates, false rejection rates, and equal error rates compared to previous works, and also calculates recognition time. It provides a concise 3-sentence summary of the key aspects of the document.International Journal of Engineering Research and Development
International Journal of Engineering Research and DevelopmentIJERD Editor
Ěý
The document presents a proposal for enhancing security at automated teller machines (ATMs) using a face recognition system based on the eigen face approach. It discusses the challenges of face recognition, including illumination conditions and occlusions, and outlines the implementation of a system that includes cash withdrawal and balance inquiry, requiring users to verify their identity through facial recognition alongside traditional card and PIN methods. Experimental results indicate potential difficulties in face differentiation as the subject pool increases, highlighting the need for further enhancements in facial feature recognition.D1061825
D1061825IJERD Editor
Ěý
This document summarizes a research paper that proposes using face recognition with the eigenface approach for security at automated teller machines (ATMs). It discusses how current ATM systems have security issues and the eigenface approach could help with identification. The document outlines the eigenface algorithm methodology and implementation steps. It provides examples of screenshots from a prototype system. In conclusion, it discusses how the system could improve security at ATMs and help identify criminals, while future work may enhance the face recognition performance.Face Recognition Home Security System
Face Recognition Home Security SystemSuman Mia
Ěý
The document outlines a project report for a face recognition home security system developed by a team of computer science students, supervised by a professor. The system utilizes biometric technology to identify known individuals and automate access to homes, emphasizing high accuracy, speed, and user-friendly design. The implementation involves several software components, hardware, and deep learning techniques to detect and recognize faces effectively, though challenges such as lighting conditions and liveness detection are noted.IRJET- Implementation of Attendance System using Face Recognition
IRJET- Implementation of Attendance System using Face RecognitionIRJET Journal
Ěý
This document describes a study that implemented an attendance tracking system using face recognition. The system aims to automatically record students' attendance during lectures using facial recognition technology instead of manual methods. It discusses existing manual and computer-based attendance systems and proposes a system that uses PCA (Principal Component Analysis) face recognition techniques to detect and recognize students' faces from images captured during lectures in order to mark their attendance automatically. The system architecture involves enrolling students by taking their images and extracting features, then acquiring new images during lectures, enhancing them, detecting and recognizing faces to mark attendance on a server database. The study implemented this system using Visual Studio 2010 and MS SQL Server 2008 and found it could successfully recognize faces and record attendance.Face Recognition System
Face Recognition SystemStudentRocks
Ěý
This document presents a project on a face recognition system. It provides an abstract describing the use of biometric security systems like face detection and recognition to provide verification and identification capabilities. It then outlines the various sections that will be included in the report, such as introduction, methodology, tools/technologies, applications and future scope. The methodology section describes using an Agile development approach and details the requirements analysis, data modeling, and process modeling steps. Computer vision, image processing and machine learning tools and technologies are also listed.Automated attendance system based on facial recognition
Automated attendance system based on facial recognitionDhanush Kasargod
Ěý
The document outlines a project for developing an automated attendance system using facial recognition technology. It describes the objectives, methodology involving the Viola-Jones algorithm and eigenface approach, and the results of implementing the system in a classroom setting. The project successfully marks attendance in real-time and saves the data in an Excel sheet, with future plans to create an online database for attendance tracking.Facial Recognition System
Facial Recognition SystemArun ACE
Ěý
Facial recognition systems have advanced significantly since first being developed in the 1960s. The software measures distinguishing landmarks on faces such as distance between eyes, nose width, and jawline to create a unique "faceprint". Emerging 3D facial recognition is more accurate as it can recognize faces from different angles. Current uses include law enforcement matching faces in crowds and at borders. Future applications may include employee time tracking and prison visitor screening.HUMAN FACE RECOGNITION USING IMAGE PROCESSING PCA AND NEURAL NETWORK
HUMAN FACE RECOGNITION USING IMAGE PROCESSING PCA AND NEURAL NETWORKijiert bestjournal
Ěý
The document discusses a face recognition system using image processing, principal component analysis (PCA), and neural networks, highlighting its potential for security and authentication. It outlines the system's approach to face detection, feature extraction, and classification, emphasizing its ability to tolerate variations in facial expressions. The proposed system aims to improve recognition accuracy by utilizing important facial features, thus offering a more robust solution compared to existing methods.Face Recognition Technology
Face Recognition TechnologyShravan Halankar
Ěý
The document provides an overview of face recognition technology, detailing its importance in biometric user identification and authentication. It describes the operational process, strengths, and weaknesses of face recognition systems, along with various feature extraction methods such as PCA and EBGM. Additionally, the document discusses the potential applications of face recognition in security and networking services, highlighting its growing significance in electronic transactions.Ad
SECURITY
- 2. INTRODUCTION • Face recognition is a process of scanning a face and matching it against a library of known faces. • Facial features of an image are extracted and a template is generated. • While matching, the features of the input image is extracted and a template is generated. • The template is compared against all the templates in the database.
- 3. • If the match is found then the user is acknowledged as a valid user and the alarm circuit is deactivated. • In enhancement of the project ie attendance management system for employees, once the user is validated as an authorised user he will be marked as present else absent. • We are also generating an attendance report.
- 4. Problem Statement • To build an efficient security system which uses face recognition technique. • Authenticating users based on their facial images which are compared against those present in the database. • An alarm circuit that will be activated as soon as an intruder tries to break through the system.
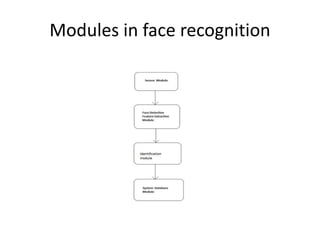
- 5. Modules in face recognition
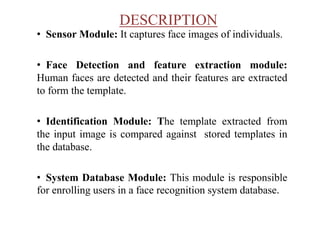
- 6. DESCRIPTION • Sensor Module: It captures face images of individuals. • Face Detection and feature extraction module: Human faces are detected and their features are extracted to form the template. • Identification Module: The template extracted from the input image is compared against stored templates in the database. • System Database Module: This module is responsible for enrolling users in a face recognition system database.
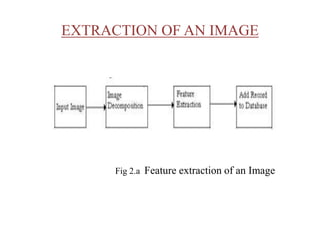
- 7. EXTRACTION OF AN IMAGE Fig 2.a Feature extraction of an Image
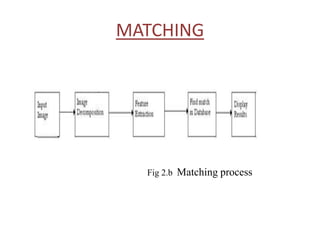
- 8. MATCHING Fig 2.b Matching process
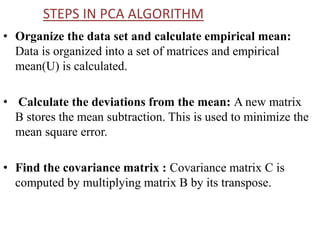
- 9. STEPS IN PCA ALGORITHM • Organize the data set and calculate empirical mean: Data is organized into a set of matrices and empirical mean(U) is calculated. • Calculate the deviations from the mean: A new matrix B stores the mean subtraction. This is used to minimize the mean square error. • Find the covariance matrix : Covariance matrix C is computed by multiplying matrix B by its transpose.
- 10. • Find the eigenvectors and eigen values of the covariance matrix: The diagonal matrix D is calculated of the covariance matrix C. • Rearrange the eigenvectors and eigen values : The eigen vector matrix V and eigen value matrix D is sorted in the order of decreasing eigen weights.
- 11. • Select a subset of the eigenvectors as basis vectors: Save the first L columns of V as the M × L matrix W: • Convert the source data to z-scores (optional): Create an M × 1 standard deviation vector s from the square root of each element along the main diagonal of the diagonalized covariance matrix C. • Project the z-scores of the data onto the new basis:
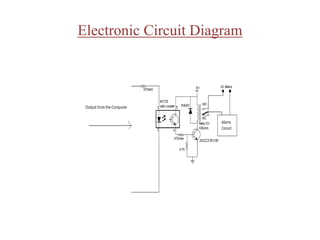
- 13. WORKING • IC mct2e receives the output from the computer via its First and Second pins. • If the computer sends a high output i.e. +5Volts when the face does not match the LED inside the IC glows. • This illumination of the LED is detected by the transistor which inturn sends the signal to the relay and turns it into an ON state. • When low signal is sent by the computer then the low signal(0 Voltage) is sent by the computer to the IC mct2e and the Relay is switched off.
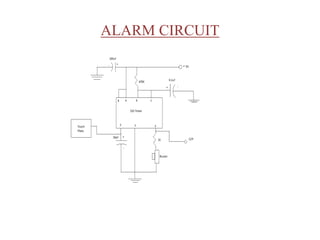
- 14. ALARM CIRCUIT
- 15. WORKING • When the Relay is on the current flows through the timer and the alarm circuit is active. • If anyone touches the touch plate the buzzer rings and the intruder is detected. • When the Relay is off the 555 timer is disconnected from the power supply and the circuit is deactivated.
- 16. CONCLUSION • Using Principle component analysis the face recognition was implemented using c# with the help of small set of images. • The system performance depends on the images stored in the database and the input image provided by the user. • This system identifies the users based on any facial images. • The monthly attendance report for the employees was successfully generated.
- 17. FUTURE SCOPE • Techniques like 3-D modelling, neural networks can be used. • Different circuits like door circuit, vibrator sensor circuit can be integrated with face recognition to fulfill different security objectives.
- 18. REFERENCES • http://encyclopedia.jrank.org/articles/pages/6741/Face -Recognition.html • http://www.electronicsforyou.com • http://www.howstuffworks.com • http://www.nec.com/global/solutions/security/technol ogies/face-recognition.html
