Security services mind map
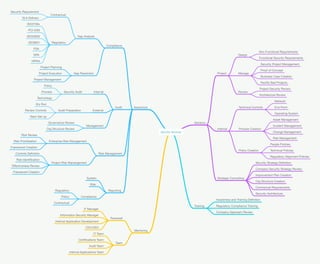
- 1. Security Services Assurance Compliance Gap Analysis Contractual Security Requirement SLA Delivery Regulatory ISO2700x PCI-DSS ISO20000 ISO9001 FSA DPA HIPAA Gap Resolution Project Planning Project Execution Project Management Audit InternalSecurity Audit Policy Process Technology ExternalAudit Preparation Dry Run Review Controls Team Set-up Management Governance Review Org Structure Review Risk Management Enterprise Risk Management Risk Review Risk Prioritisation Framework Creation Project Risk Manangement Controls De’¼ünition Risk Identi’¼ücation E’¼Ćectiveness Review Framework Creation Reporting System Risk Compliance Regulatory Policy Contractual Advisory Project Design Non Functional Requirements Functional Security Requirements Manage Security Project Management Proof of Concept Business Case Creation Rectify Bad Projects Review Project Security Review Architecture Review Internal Technical Controls Network End Point Operating System Process Creation Asset Management Incident Management Change Management Risk Management Policy Creation People Policies Technical Policies Regulatory Alignment Policies Strategic Consulting Security Strategy De’¼ünition Company Security Strategy Review Improvement Plan Creation Org Structure Creation Contractual Requirements Security Architecture Training Awareness and Training De’¼ünition Regulatory Compliance Training Company Approach Review Mentoring Personell IT Manager Information Security Manager Internal Application Development CIO/CISO Team IT Team Certi’¼ücations Team Audit Team Internal Applications Team