Security, you are also part of the game
0 likes1,001 views
The document discusses various aspects of cybersecurity, emphasizing the importance of password management and device security. It highlights vulnerabilities such as lost portable devices and methods of hacking, including social engineering and shoulder surfing. Practical tips are provided for creating strong passwords and securing sensitive data, alongside a reminder that users are the first line of defense in security.
1 of 41
Download to read offline









![Open solutions, smarter people
Time to crack a password
âĒ [[Guesses before string is found = 2H]]
âĒ This is.obviously a.bad passw0rd:-(
â 2230 = 1.72543659 Ã 1069
â 1000 guesses /s = 5.5 x 1058 years
âĒ PrXyc.N(n4k77#L!eVdAfp9
â 2151 = 2.85449539 Ã 1045
â 1000 guesses /s = 9 Ã 1034 years](https://image.slidesharecdn.com/securitybasic-120401082124-phpapp01/85/Security-you-are-also-part-of-the-game-21-320.jpg)












Ad
Recommended
Hack u intro
Hack u introhacku
Ėý
HackU is a 24-hour hackathon where participants have 24 hours to build a project in teams of up to 4 people. Participants will attend talks, have access to food/drinks, and support from other attendees. Projects can revolve around building, fixing, automating, or revolutionizing something. At the end, teams will have 90 seconds to demo their project and impress the judges. Yahoo and various websites provide resources and APIs to help participants build their projects. The hackathon kicks off with talks and then hacking begins the next day.Contribute or die
Contribute or dieBert Desmet
Ėý
The document discusses the Fedora Project and free/open source software. It summarizes that the Fedora Project adopts new technologies and releases them early to innovate rapidly. It also ensures long-term sustainability by committing to upstream developers. The document encourages participation in Fedora to influence future products and ensure needs are met. Studies show people prefer creativity over stability in jobs and that proprietary software limits innovation potential.So, You Want to Land a Job
So, You Want to Land a JobJohn Gallagher
Ėý
John Gallagher emphasizes that success in landing a job largely relies on people skills rather than technical knowledge, encouraging a positive attitude and integrity. He stresses the importance of being a problem solver, committing to lifelong learning, and managing personal priorities effectively. The ultimate goal, he suggests, is not just employment but making a meaningful difference.Cave Spring Knights Touchdown Club 2014
Cave Spring Knights Touchdown Club 2014John Gallagher
Ėý
The Touchdown Club last year was successful and this year the goal is to double membership. To do this, everyone needs to return and recruit one new person. The purpose of the club is to support the football team through fundraising and tailgating. The club has three membership levels - Black, Red, and White - with Red level including two season tickets and priority seating.Fedora 14 overview
Fedora 14 overviewBert Desmet
Ėý
Fedora 14 'Laughlin' is a new release of the Fedora operating system that is free, open source, and maintained by volunteers. Some key features and improvements in Fedora 14 include support for additional architectures, an improved virtual desktop interface using Spice, faster JPEG loading with Libjpegturbo, the new Gnome 3 desktop environment, improved security tools for servers on EC2 cloud computing platforms, and new development tools and languages like D programming and Python 2.7.How To Take Notes During Meetings
How To Take Notes During MeetingsRussel C. Arida
Ėý
The document provides guidance on how to effectively take notes during meetings. It recommends dividing your paper into three sections for the title, minutes, and key words/learning. It includes an example meeting notes page with the title of meeting, venue, time, list of attendees with their contact details and attributes. The minutes section would be used to record the discussions. The key words and learning section lists the main topics discussed and lessons learned from each attendee such as the relevance of slides in a presentation and how pictures can enhance explanation. Taking good meeting notes with these elements can help recall discussions and personalities.Climbing the Age & Ladder Chart
Climbing the Age & Ladder Chart Russel C. Arida
Ėý
The document discusses the concept of the 'Age & Ladder Chart' as a tool to assess career progression in relation to age and performance evaluations. It emphasizes the importance of establishing a Daily Management System (DMS) to effectively manage daily activities and enhance personal growth, ultimately leading to career advancement. The author provides actionable steps for implementing a DMS and reflects on the significance of dedicating time to skill mastery as it relates to promotions and professional development.ÐīÐūÐģаÐīÐļÐ―Ð°&ēđģūąč;ÐąÐĩÐŧÐūÐēа1
ÐīÐūÐģаÐīÐļÐ―Ð°&ēđģūąč;ÐąÐĩÐŧÐūÐēа1guestfb2102
Ėý
ÐÐūКŅОÐĩÐ―Ņ ÐūÐŋÐļŅŅÐēаÐĩŅ ÐūŅÐūÐąÐĩÐ―Ð―ÐūŅŅÐļ Ð―ÐūŅŅÐąŅКÐūÐē, ÐēКÐŧŅŅаŅ ÐļŅ
ÐļŅŅÐūŅÐļŅ, ŅŅÐ―ÐšŅÐļÐūÐ―Ð°ÐŧŅÐ―ŅÐĩ ÐēÐūзОÐūÐķÐ―ÐūŅŅÐļ Ðļ ÐŋаŅаОÐĩŅŅŅ, а ŅаКÐķÐĩ ÐŋŅÐļОÐĩÐ―ÐĩÐ―ÐļÐĩ Ðē ÐūÐąŅазÐūÐēÐ°Ð―ÐļÐļ. РаŅŅОаŅŅÐļÐēаŅŅŅŅ ÐēÐļÐīŅ Ð―ÐūŅŅÐąŅКÐūÐē, ÐļŅ
Ņ
аŅаКŅÐĩŅÐļŅŅÐļКÐļ Ðļ ŅŅÐūÐļОÐūŅŅŅ, а ŅаКÐķÐĩ ÐļŅ
ŅÐūÐŧŅ Ðē ŅŅÐĩÐąÐ―ÐūО ÐŋŅÐūŅÐĩŅŅÐĩ Ðļ ŅÐŋŅаÐēÐŧÐĩÐ―ÐļÐļ ÐūÐąŅазÐūÐēÐ°Ð―ÐļÐĩО. ÐĒаКÐķÐĩ ÐŋŅÐļÐēÐĩÐīÐĩÐ― ŅÐŋÐļŅÐūК КÐūОÐŋŅŅŅÐĩŅÐ―ŅŅ
ОаÐģазÐļÐ―ÐūÐē Ðē ÐĄÐ°Ð―ÐšŅ-ÐÐĩŅÐĩŅÐąŅŅÐģÐĩ, ÐģÐīÐĩ ОÐūÐķÐ―Ðū ÐŋŅÐļÐūÐąŅÐĩŅŅÐļ ÐīÐ°Ð―Ð―ŅÐĩ ŅŅŅŅÐūÐđŅŅÐēа.Boeing rocketdyne radical innovation case study
Boeing rocketdyne radical innovation case studyMuthu Kumaar Thangavelu
Ėý
The document discusses a case study of radical innovation at Boeing-Rocketdyne without collocation. It summarizes the success of the VC3 (Virtual Cross Value Chain, Creative, Collaborative) team in designing a rocket engine thrust chamber in 10 months, compared to the traditional 6 years and higher costs. Some key practices that led to the VC3 team's success included establishing strategy and guidelines in advance, using collaborative technologies as knowledge management tools, and restructuring work processes without changing core creative needs. The implications discussed are for practice, research, and effective virtual team working.SESTINFO 2011 Apresentacao AndroidRafael Sakurai
Ėý
O documento ÃĐ uma apresentaçÃĢo sobre desenvolvimento na plataforma Android, abordando temas como a arquitetura do sistema, componentes de aplicaçÃĢo, e o ambiente de desenvolvimento. Inclui informaçÃĩes sobre o Android SDK, a criaçÃĢo de um projeto 'Hello World', e detalhes sobre serviços, recebedores de transmissÃĢo, e provedores de conteÚdo. A apresentaçÃĢo tambÃĐm discute a publicaçÃĢo de aplicaçÃĩes no Android Market e destaca nÚmeros relevantes sobre o uso do Android atÃĐ 2011.Social Training Project for Merchandisers
Social Training Project for MerchandisersRussel C. Arida
Ėý
The document discusses a social training project in the Philippines that aims to provide job opportunities and training to unemployed youth. The project partners the government, NGOs, and merchandising agencies. It provides a 2-day training program on merchandising skills to help trainees find employment in the merchandising sector. Feedback from past trainees showed they learned valuable skills that can be applied to their work and life. The training director can be contacted for more information about the program.Semantic web design for www.data.gov.sg - Technical Report
Semantic web design for www.data.gov.sg - Technical ReportMuthu Kumaar Thangavelu
Ėý
The document presents an eight step migrational framework for converting Singapore government data from legacy systems to linked data format. The framework was developed based on an analysis of Singapore's existing data ecosystem and two pilot datasets from the Urban Redevelopment Authority and Department of Statistics. Each step in the framework outlines objectives, issues identified, and recommended tools. The framework is intended to help the Infocomm Development Authority implement a linked data system for publishing and connecting government data. It aims to provide a customized approach based on Singapore's current data landscape.Why You Should Partner With Colonial Life
Why You Should Partner With Colonial Lifedonnadwyer
Ėý
This document summarizes how brokers can partner with Colonial Life to provide benefits counseling services to employers and their employees. It outlines how this differentiated service approach can help employees better understand and appreciate their benefits while saving employers money through lower payroll taxes and premiums. Specific voluntary benefits like life insurance, disability insurance, and cancer coverage are highlighted.Buckmann labs KM case study
Buckmann labs KM case studyMuthu Kumaar Thangavelu
Ėý
This document summarizes the key points from a case study about Buckman Laboratories' implementation of a knowledge management system called K'Netix. It describes Buckman's profile and problems encountered that led to the need for KM. Buckman launched K'Netix on the CompuServe platform in 1992, creating forums for knowledge sharing. While implementation faced initial challenges, results showed increased sales, spending, and associate engagement by 1994-1995. Future challenges included a drop in forum usage after switching platforms and building trust in virtual knowledge sharing.Human Capital Management
Human Capital ManagementMuthu Kumaar Thangavelu
Ėý
The document discusses the changing nature of corporations and work in the modern knowledge economy. It makes three key points:
1) In knowledge-based companies, employees invest their human capital and skills in the company, so they have a stake in the company's success beyond just their salary. This challenges the traditional view of employees as assets owned by shareholders.
2) As work becomes more professionalized, employees gain skills and change employers more often, staying in their profession. Companies benefit from training employees to retain them and increase the flexibility of their workforce.
3) Some companies are recognizing employees as a new class of investors in the company, in addition to financial shareholders, by giving employees ownership stakes or profit-Measures of corporate performance
Measures of corporate performanceSamahAdra
Ėý
This document discusses methods for measuring corporate performance, including the balanced scorecard and stakeholder measures. It outlines the advantages and limitations of each. The balanced scorecard takes a holistic view across four perspectives: learning and growth, internal business processes, customers, and financials. It aims to align business activities with organizational strategy but can fail if not properly communicated. Stakeholder measures evaluate performance based on key stakeholder groups' priorities but balancing different stakeholders' interests can be challenging. The document provides an in-depth examination of these two approaches to corporate performance assessment.Bp business and information strategy alignment
Bp business and information strategy alignmentMuthu Kumaar Thangavelu
Ėý
The document examines British Petroleum's (BP) information systems and technology alignment with business strategies using various theoretical frameworks, including the information systems strategy triangle and hypercompetition model. It emphasizes the importance of IT transformation, strategic outsourcing, and the evolution of BP's technology stack in enhancing operational efficiency and competitive advantage. The study concludes that successful organizational alignment between information systems and business strategy is crucial for achieving growth and sustainability in changing market conditions.Deja vu security Adam Cecchetti - Security is a Snapshot in Time BSidesPDX ...
Deja vu security Adam Cecchetti - Security is a Snapshot in Time BSidesPDX ...adamdeja
Ėý
Adam Cecchetti discusses the evolving landscape of security, emphasizing that security is a snapshot in time and the importance of constantly adapting to modern threats. He highlights the challenges of hacker activity related to outdated practices and the rising complexity of technology, which leads to potential vulnerabilities. The presentation advocates for a proactive approach to security that combines awareness, detailed understanding, and cooperative effort to build a more secure future.Learn Hacking
Learn Hackinghackingtraining
Ėý
This document provides an overview of hackers and hacker culture. It defines different types of hackers such as white hats, grey hats, and black hats. It discusses what motivates hackers and the rules or ethic of the hacker community, which includes rejecting hierarchies, mistrusting authority, promoting decentralization, sharing information, and serving their community. The document aims to give a broad understanding of hackers, their motivations, and culture.E Crime Mid Year Meeting London
E Crime Mid Year Meeting LondonHartj
Ėý
This document discusses password security and hacking techniques. It begins with legal disclaimers about obtaining permission before scanning systems or cracking passwords. It then outlines accepted security principles and introduces the "third age of hacking" which focuses on gaining passwords. Various password hacking techniques are presented such as password surfing, metadata mining, and social engineering. The document argues that the solution is to implement two-factor authentication using something a user knows plus something they have to uniquely identify the user each time they log in.Shannon Morris PDLM presentation
Shannon Morris PDLM presentationshannoncmorris
Ėý
The document discusses promoting safe and responsible use of technology through developing students' understanding of ethical and security issues related to technology. It provides examples of security threats like hacking school networks to change grades, spreading malware through instant messages that can lead to identity theft, and infecting computers with ads for profit. The document emphasizes the importance of educating students on network security best practices like using strong passwords, backing up data, and knowing how to identify and avoid security risks online in order to protect schools and individuals from cyber threats.Bar Camp 11 Oct09 Hacking
Bar Camp 11 Oct09 HackingBarcamp Kerala
Ėý
This document discusses hacking and provides an overview of ethical hacking. It begins by defining what a hacker is, noting that historically it referred to an enthusiastic computer hobbyist rather than a criminal. It discusses the evolution of hacking and open source culture. It then discusses ethical hacking and penetration testing, noting it involves authorized attempts to breach systems to test security. It provides an example case study of a large hadron collider being hacked. It also discusses the importance of security given the rise in internet users and potential for attacks on critical networks.Hushcon 2016 Keynote: Test for Echo
Hushcon 2016 Keynote: Test for EchoDeja vu Security
Ėý
Adam Cecchetti's keynote at Hushcon 2016 discusses the critical state of cybersecurity, emphasizing the need for awareness and innovative thinking to address inherited security issues in software. He highlights the pervasive influence of technology on everyday life, urging a shift in user behavior towards more secure practices. The talk underscores the importance of collaboration and understanding diverse perspectives in improving security and achieving impactful technological solutions.Passwords
PasswordsKevin OBrien
Ėý
The document discusses the importance of secure password practices and the threats posed by hackers utilizing social engineering techniques. It emphasizes the need for unique and complex passwords for important sites, and recommends using salted hashes and password managers like LastPass or KeePassX to generate and store strong passwords. The limitations of current encryption methods and the potential future threats from quantum computing are also highlighted.Frontier Secure: Handout for small business leaders on "How to be Secure"
Frontier Secure: Handout for small business leaders on "How to be Secure" Frontier Small Business
Ėý
The document outlines the essential cybersecurity measures small businesses must adopt to protect against various threats, including phishing, spam, and malware, which can result in significant financial losses. It emphasizes the importance of firewalls, antivirus software, and employee education on internet safety. Additionally, the document provides social media security tips and best practices to mitigate risks associated with online platforms.Computer Security
Computer Securitytonik
Ėý
Computer security involves protecting information from threats like malware, hacking, and social engineering. Malware like viruses, trojans, bots, and spyware can disrupt systems or steal private information. Social engineering tricks people into sharing confidential details. To stay safe, use strong, unique passwords, avoid suspicious emails and links, and practice cybersecurity best practices like keeping software updated.So whats in a password
So whats in a passwordRob Gillen
Ėý
The presentation discusses recent real-world password attacks on various systems, highlighting significant breaches such as the Adobe hack affecting 153 million accounts and other incidents resulting in the exposure of personal data. It emphasizes the importance of understanding the vulnerabilities associated with password security, including algorithm weaknesses and common attack methods like brute-force and dictionary attacks. Additionally, it provides recommendations for improving password security, including the use of strong, unique passwords and secure hashing techniques.A journey through an INFOSEC labyrinth
A journey through an INFOSEC labyrinthAvÄdÄnei Andrei
Ėý
Andrei AvÄdÄnei presented on his journey in information security and entrepreneurship. Some key points included:
1. He founded the security conference DefCamp in 2011 and the Cyber Security Research Center in Romania (CCSIR) to promote the local security community and industry.
2. Through DefCamp, he aimed to connect smart security professionals in Romania and worldwide through informal talks, competitions, and networking events.
3. His lessons emphasized an offensive security mindset, iterating on ideas through failures, building honeypots and backups, and staying responsive to feedback to improve.
4. He believes the black hat/white hat distinction is oversimplified and professionals can create positive impactHuman/User-Centric Security
Human/User-Centric SecurityShujun Li
Ėý
The document discusses user-centric security approaches, particularly focusing on password management and the challenges of balancing security and usability. It highlights various password cracking methods over the decades and presents potential solutions including password checkers, managers, and multi-factor authentication. The overall message advocates for improving user education and tools to enhance security without blaming users for vulnerabilities.More Related Content
Viewers also liked (10)
ÐīÐūÐģаÐīÐļÐ―Ð°&ēđģūąč;ÐąÐĩÐŧÐūÐēа1
ÐīÐūÐģаÐīÐļÐ―Ð°&ēđģūąč;ÐąÐĩÐŧÐūÐēа1guestfb2102
Ėý
ÐÐūКŅОÐĩÐ―Ņ ÐūÐŋÐļŅŅÐēаÐĩŅ ÐūŅÐūÐąÐĩÐ―Ð―ÐūŅŅÐļ Ð―ÐūŅŅÐąŅКÐūÐē, ÐēКÐŧŅŅаŅ ÐļŅ
ÐļŅŅÐūŅÐļŅ, ŅŅÐ―ÐšŅÐļÐūÐ―Ð°ÐŧŅÐ―ŅÐĩ ÐēÐūзОÐūÐķÐ―ÐūŅŅÐļ Ðļ ÐŋаŅаОÐĩŅŅŅ, а ŅаКÐķÐĩ ÐŋŅÐļОÐĩÐ―ÐĩÐ―ÐļÐĩ Ðē ÐūÐąŅазÐūÐēÐ°Ð―ÐļÐļ. РаŅŅОаŅŅÐļÐēаŅŅŅŅ ÐēÐļÐīŅ Ð―ÐūŅŅÐąŅКÐūÐē, ÐļŅ
Ņ
аŅаКŅÐĩŅÐļŅŅÐļКÐļ Ðļ ŅŅÐūÐļОÐūŅŅŅ, а ŅаКÐķÐĩ ÐļŅ
ŅÐūÐŧŅ Ðē ŅŅÐĩÐąÐ―ÐūО ÐŋŅÐūŅÐĩŅŅÐĩ Ðļ ŅÐŋŅаÐēÐŧÐĩÐ―ÐļÐļ ÐūÐąŅазÐūÐēÐ°Ð―ÐļÐĩО. ÐĒаКÐķÐĩ ÐŋŅÐļÐēÐĩÐīÐĩÐ― ŅÐŋÐļŅÐūК КÐūОÐŋŅŅŅÐĩŅÐ―ŅŅ
ОаÐģазÐļÐ―ÐūÐē Ðē ÐĄÐ°Ð―ÐšŅ-ÐÐĩŅÐĩŅÐąŅŅÐģÐĩ, ÐģÐīÐĩ ОÐūÐķÐ―Ðū ÐŋŅÐļÐūÐąŅÐĩŅŅÐļ ÐīÐ°Ð―Ð―ŅÐĩ ŅŅŅŅÐūÐđŅŅÐēа.Boeing rocketdyne radical innovation case study
Boeing rocketdyne radical innovation case studyMuthu Kumaar Thangavelu
Ėý
The document discusses a case study of radical innovation at Boeing-Rocketdyne without collocation. It summarizes the success of the VC3 (Virtual Cross Value Chain, Creative, Collaborative) team in designing a rocket engine thrust chamber in 10 months, compared to the traditional 6 years and higher costs. Some key practices that led to the VC3 team's success included establishing strategy and guidelines in advance, using collaborative technologies as knowledge management tools, and restructuring work processes without changing core creative needs. The implications discussed are for practice, research, and effective virtual team working.SESTINFO 2011 Apresentacao AndroidRafael Sakurai
Ėý
O documento ÃĐ uma apresentaçÃĢo sobre desenvolvimento na plataforma Android, abordando temas como a arquitetura do sistema, componentes de aplicaçÃĢo, e o ambiente de desenvolvimento. Inclui informaçÃĩes sobre o Android SDK, a criaçÃĢo de um projeto 'Hello World', e detalhes sobre serviços, recebedores de transmissÃĢo, e provedores de conteÚdo. A apresentaçÃĢo tambÃĐm discute a publicaçÃĢo de aplicaçÃĩes no Android Market e destaca nÚmeros relevantes sobre o uso do Android atÃĐ 2011.Social Training Project for Merchandisers
Social Training Project for MerchandisersRussel C. Arida
Ėý
The document discusses a social training project in the Philippines that aims to provide job opportunities and training to unemployed youth. The project partners the government, NGOs, and merchandising agencies. It provides a 2-day training program on merchandising skills to help trainees find employment in the merchandising sector. Feedback from past trainees showed they learned valuable skills that can be applied to their work and life. The training director can be contacted for more information about the program.Semantic web design for www.data.gov.sg - Technical Report
Semantic web design for www.data.gov.sg - Technical ReportMuthu Kumaar Thangavelu
Ėý
The document presents an eight step migrational framework for converting Singapore government data from legacy systems to linked data format. The framework was developed based on an analysis of Singapore's existing data ecosystem and two pilot datasets from the Urban Redevelopment Authority and Department of Statistics. Each step in the framework outlines objectives, issues identified, and recommended tools. The framework is intended to help the Infocomm Development Authority implement a linked data system for publishing and connecting government data. It aims to provide a customized approach based on Singapore's current data landscape.Why You Should Partner With Colonial Life
Why You Should Partner With Colonial Lifedonnadwyer
Ėý
This document summarizes how brokers can partner with Colonial Life to provide benefits counseling services to employers and their employees. It outlines how this differentiated service approach can help employees better understand and appreciate their benefits while saving employers money through lower payroll taxes and premiums. Specific voluntary benefits like life insurance, disability insurance, and cancer coverage are highlighted.Buckmann labs KM case study
Buckmann labs KM case studyMuthu Kumaar Thangavelu
Ėý
This document summarizes the key points from a case study about Buckman Laboratories' implementation of a knowledge management system called K'Netix. It describes Buckman's profile and problems encountered that led to the need for KM. Buckman launched K'Netix on the CompuServe platform in 1992, creating forums for knowledge sharing. While implementation faced initial challenges, results showed increased sales, spending, and associate engagement by 1994-1995. Future challenges included a drop in forum usage after switching platforms and building trust in virtual knowledge sharing.Human Capital Management
Human Capital ManagementMuthu Kumaar Thangavelu
Ėý
The document discusses the changing nature of corporations and work in the modern knowledge economy. It makes three key points:
1) In knowledge-based companies, employees invest their human capital and skills in the company, so they have a stake in the company's success beyond just their salary. This challenges the traditional view of employees as assets owned by shareholders.
2) As work becomes more professionalized, employees gain skills and change employers more often, staying in their profession. Companies benefit from training employees to retain them and increase the flexibility of their workforce.
3) Some companies are recognizing employees as a new class of investors in the company, in addition to financial shareholders, by giving employees ownership stakes or profit-Measures of corporate performance
Measures of corporate performanceSamahAdra
Ėý
This document discusses methods for measuring corporate performance, including the balanced scorecard and stakeholder measures. It outlines the advantages and limitations of each. The balanced scorecard takes a holistic view across four perspectives: learning and growth, internal business processes, customers, and financials. It aims to align business activities with organizational strategy but can fail if not properly communicated. Stakeholder measures evaluate performance based on key stakeholder groups' priorities but balancing different stakeholders' interests can be challenging. The document provides an in-depth examination of these two approaches to corporate performance assessment.Bp business and information strategy alignment
Bp business and information strategy alignmentMuthu Kumaar Thangavelu
Ėý
The document examines British Petroleum's (BP) information systems and technology alignment with business strategies using various theoretical frameworks, including the information systems strategy triangle and hypercompetition model. It emphasizes the importance of IT transformation, strategic outsourcing, and the evolution of BP's technology stack in enhancing operational efficiency and competitive advantage. The study concludes that successful organizational alignment between information systems and business strategy is crucial for achieving growth and sustainability in changing market conditions.Similar to Security, you are also part of the game (20)
Deja vu security Adam Cecchetti - Security is a Snapshot in Time BSidesPDX ...
Deja vu security Adam Cecchetti - Security is a Snapshot in Time BSidesPDX ...adamdeja
Ėý
Adam Cecchetti discusses the evolving landscape of security, emphasizing that security is a snapshot in time and the importance of constantly adapting to modern threats. He highlights the challenges of hacker activity related to outdated practices and the rising complexity of technology, which leads to potential vulnerabilities. The presentation advocates for a proactive approach to security that combines awareness, detailed understanding, and cooperative effort to build a more secure future.Learn Hacking
Learn Hackinghackingtraining
Ėý
This document provides an overview of hackers and hacker culture. It defines different types of hackers such as white hats, grey hats, and black hats. It discusses what motivates hackers and the rules or ethic of the hacker community, which includes rejecting hierarchies, mistrusting authority, promoting decentralization, sharing information, and serving their community. The document aims to give a broad understanding of hackers, their motivations, and culture.E Crime Mid Year Meeting London
E Crime Mid Year Meeting LondonHartj
Ėý
This document discusses password security and hacking techniques. It begins with legal disclaimers about obtaining permission before scanning systems or cracking passwords. It then outlines accepted security principles and introduces the "third age of hacking" which focuses on gaining passwords. Various password hacking techniques are presented such as password surfing, metadata mining, and social engineering. The document argues that the solution is to implement two-factor authentication using something a user knows plus something they have to uniquely identify the user each time they log in.Shannon Morris PDLM presentation
Shannon Morris PDLM presentationshannoncmorris
Ėý
The document discusses promoting safe and responsible use of technology through developing students' understanding of ethical and security issues related to technology. It provides examples of security threats like hacking school networks to change grades, spreading malware through instant messages that can lead to identity theft, and infecting computers with ads for profit. The document emphasizes the importance of educating students on network security best practices like using strong passwords, backing up data, and knowing how to identify and avoid security risks online in order to protect schools and individuals from cyber threats.Bar Camp 11 Oct09 Hacking
Bar Camp 11 Oct09 HackingBarcamp Kerala
Ėý
This document discusses hacking and provides an overview of ethical hacking. It begins by defining what a hacker is, noting that historically it referred to an enthusiastic computer hobbyist rather than a criminal. It discusses the evolution of hacking and open source culture. It then discusses ethical hacking and penetration testing, noting it involves authorized attempts to breach systems to test security. It provides an example case study of a large hadron collider being hacked. It also discusses the importance of security given the rise in internet users and potential for attacks on critical networks.Hushcon 2016 Keynote: Test for Echo
Hushcon 2016 Keynote: Test for EchoDeja vu Security
Ėý
Adam Cecchetti's keynote at Hushcon 2016 discusses the critical state of cybersecurity, emphasizing the need for awareness and innovative thinking to address inherited security issues in software. He highlights the pervasive influence of technology on everyday life, urging a shift in user behavior towards more secure practices. The talk underscores the importance of collaboration and understanding diverse perspectives in improving security and achieving impactful technological solutions.Passwords
PasswordsKevin OBrien
Ėý
The document discusses the importance of secure password practices and the threats posed by hackers utilizing social engineering techniques. It emphasizes the need for unique and complex passwords for important sites, and recommends using salted hashes and password managers like LastPass or KeePassX to generate and store strong passwords. The limitations of current encryption methods and the potential future threats from quantum computing are also highlighted.Frontier Secure: Handout for small business leaders on "How to be Secure"
Frontier Secure: Handout for small business leaders on "How to be Secure" Frontier Small Business
Ėý
The document outlines the essential cybersecurity measures small businesses must adopt to protect against various threats, including phishing, spam, and malware, which can result in significant financial losses. It emphasizes the importance of firewalls, antivirus software, and employee education on internet safety. Additionally, the document provides social media security tips and best practices to mitigate risks associated with online platforms.Computer Security
Computer Securitytonik
Ėý
Computer security involves protecting information from threats like malware, hacking, and social engineering. Malware like viruses, trojans, bots, and spyware can disrupt systems or steal private information. Social engineering tricks people into sharing confidential details. To stay safe, use strong, unique passwords, avoid suspicious emails and links, and practice cybersecurity best practices like keeping software updated.So whats in a password
So whats in a passwordRob Gillen
Ėý
The presentation discusses recent real-world password attacks on various systems, highlighting significant breaches such as the Adobe hack affecting 153 million accounts and other incidents resulting in the exposure of personal data. It emphasizes the importance of understanding the vulnerabilities associated with password security, including algorithm weaknesses and common attack methods like brute-force and dictionary attacks. Additionally, it provides recommendations for improving password security, including the use of strong, unique passwords and secure hashing techniques.A journey through an INFOSEC labyrinth
A journey through an INFOSEC labyrinthAvÄdÄnei Andrei
Ėý
Andrei AvÄdÄnei presented on his journey in information security and entrepreneurship. Some key points included:
1. He founded the security conference DefCamp in 2011 and the Cyber Security Research Center in Romania (CCSIR) to promote the local security community and industry.
2. Through DefCamp, he aimed to connect smart security professionals in Romania and worldwide through informal talks, competitions, and networking events.
3. His lessons emphasized an offensive security mindset, iterating on ideas through failures, building honeypots and backups, and staying responsive to feedback to improve.
4. He believes the black hat/white hat distinction is oversimplified and professionals can create positive impactHuman/User-Centric Security
Human/User-Centric SecurityShujun Li
Ėý
The document discusses user-centric security approaches, particularly focusing on password management and the challenges of balancing security and usability. It highlights various password cracking methods over the decades and presents potential solutions including password checkers, managers, and multi-factor authentication. The overall message advocates for improving user education and tools to enhance security without blaming users for vulnerabilities.How to Become a Hacker?
How to Become a Hacker?removed_e10bf3fe21ff4e6e6a55bdd2c09fcb15
Ėý
This document provides lessons on how to become a hacker. It discusses preparing for a long journey, finding mentors, distinguishing yourself, going interactive, holding your hands, playing instead of just commenting, starting now and restarting often. It also discusses getting a computing and free software culture through writing and reading. The document encourages fixing your email, marrying your text editor, mastering version control and TODO lists, learning to make bug reports, scratching your own and others' itches, learning a programming language, understanding users' environments, and learning to test and write English. It concludes by discussing getting involved in a free software community.presentation on hacking
presentation on hackingAyush Upadhyay
Ėý
This document discusses hacking and the history of notable hacker Robert Tappan Morris. It defines hacking as gaining unauthorized access to a computer system without intending harm. Hackers are classified as white hat, gray hat, or black hat based on their motives. Morris created the first internet worm in 1988 while studying at Cornell, which disrupted many computers and led to him being the first person convicted under the Computer Fraud and Abuse Act. The document outlines the details of Morris' worm and criminal case, as well as his later career in computer science.Introduction to security
Introduction to securityMostafa Elgamala
Ėý
This document discusses various cybersecurity threats and issues. It covers hacking of government and private systems, the scope of hacking (devices, networks, etc.), common cyber attacks and their motives, potential results of attacks, and levels of security. It also provides examples of famous viruses and outlines guidelines, measures, and security procedures to help protect against various threats like identity theft, social engineering, mobile device risks, and network attacks. The key message is that security awareness is the first step to improving protection.Hacking,History Of Hacking,Types of Hacking,Types Of Hackers,Cyber Laws for ...
Hacking,History Of Hacking,Types of Hacking,Types Of Hackers,Cyber Laws for ...Qazi Anwar
Ėý
The document discusses the history and types of hacking, highlighting famous hackers and the evolution of hacking practices since the late 19th century. It also covers ethical hacking, cyber laws in Pakistan, prevention methods against hacking, and the role of vulnerability scanners, password cracking, and rootkits. Additionally, it emphasizes the demand for ethical hackers to combat cybercrime and outlines best practices for maintaining computer and internet security.Drooger, jack cyber security
Drooger, jack cyber securityHagerstown Chamber Business Expo
Ėý
This document discusses self defense for cybersecurity and protecting personal and organizational assets from cyber threats. It provides examples of common cyber attacks like hacking and phishing. It also outlines traditional security fixes like firewalls, antivirus software, and password best practices. Throughout it provides scenarios of past security breaches at companies to illustrate the risks and impacts of attacks. The key messages are that social engineering, weak passwords, and lack of backups leave both personal and business systems vulnerable to cyber criminals. Regular security updates, strong unique passwords, and backing up important data are recommended for protection.OCITA 2012: Opening Up to Open Source Software for Government
OCITA 2012: Opening Up to Open Source Software for GovernmentJillmz
Ėý
The document discusses the opportunities and challenges of adopting open source solutions in government sectors, emphasizing the cost benefits, flexibility, and potential for innovation, while also addressing concerns regarding security and support. Successful case studies from various government projects illustrate the practical application of open source software. It concludes with resources and steps to create an effective open source policy within local governments.Lkw Security Part 1_MVPs Azra & Sanjay
Lkw Security Part 1_MVPs Azra & SanjayQuek Lilian
Ėý
This document summarizes a presentation on information security and protecting privacy with Windows 7. It discusses why security is important, common security misconceptions like thinking antivirus is enough, emerging threats from social media and mobile devices, and how to strengthen security through practices like using strong passwords and keeping software updated. It also provides tips for securely using public networks and storing mobile data to help protect privacy and information.Software security (vulnerabilities) and physical security
Software security (vulnerabilities) and physical securityNicholas Davis
Ėý
The document discusses various types of software vulnerabilities including:
1. Vulnerabilities can result from weak passwords, software bugs, viruses, or insecure user input.
2. Common causes of vulnerabilities are password management flaws, operating system design flaws, software bugs, and unchecked user input.
3. There is debate around how vulnerabilities should be disclosed, with options including full disclosure, responsible disclosure, and limited disclosure.Frontier Secure: Handout for small business leaders on "How to be Secure"
Frontier Secure: Handout for small business leaders on "How to be Secure" Frontier Small Business
Ėý
Ad
Recently uploaded (20)
OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
Ėý
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...
Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...janeliewang985
Ėý
the slides of the MP selection approach CMPSFrom Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
Ėý
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnât yielding any results, so I expanded my search to second-hand dealer sitesâonly to realise that periodically checking each one was going to be tedious. Thatâs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformâs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, Iâll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canât buy a car for youâyetâit can certainly help you find the one youâre after!AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
Ėý
AI VIDEO MAGAZINE - r/aivideo community newsletter â Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash
Ėý
Lessons Learned from Developing Secure AI WorkflowsEIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science
Ėý
As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AIĖý- Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AIĖý- How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systemsĖý- How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignmentĖý- Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether youâre modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
Ėý
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
ð Introducing Data Contracts: An agreement between data producers and consumers
ð Data Contracts key components: Understanding a contract and its purpose
ð§âðĻ Writing your first contract: How to create your own contracts in OpenMetadata
ðĶū An OpenMetadata MCP Server update!
â And More!WebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect
Ėý
In todayâs dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging Seleniumâs broad browser support and WDIOâs modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
Ėý
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
Ėý
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic
Ėý
Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55
Ėý
CurieTech AI in Action â Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AIâs purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samplesâ95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specificationsâspeeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10Ã productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflowâletting you focus on innovation, not repetition.Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
Ėý
The SQLExecutor is one of FMEâs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation âValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash
Ėý
Cracking the Code - Unveiling Synergies Between Open Source Security and AI"Scaling in space and time with Temporal", Andriy Lupa.pdf
"Scaling in space and time with Temporal", Andriy Lupa.pdfFwdays
Ėý
Design patterns like Event Sourcing and Event Streaming have long become standards for building real-time analytics systems. However, when the system load becomes nonlinear with fast and often unpredictable spikes, it's crucial to respond quickly in order not to lose real-time operating itself.
In this talk, Iâll share my experience implementing and using a tool like Temporal.io. We'll explore the evolution of our system for maintaining real-time report generation and discuss how we use Temporal both for short-lived pipelines and long-running background tasks.AI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
Ėý
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
Ėý
ŨŨĻŨŨ ŨĒŨŨŨŨŨŨ ŨŠŨĒŨĐŨŨŨŠŨ ŨŨĒŨ 3/4/5 ŨĶŨŨĻŨŨ, ŨĒŨ 22 ŨŨŨŨĪŨŨŠ ŨŨŨŨ ŨĒŨ ŨŨ ŨŨĪŨĐŨĻŨŨŨŨŠ ŨŨĒŨŨŨŨ ŨŨŨĻŨŨĐŨŨŠ.ĖýŨŨĒŨ ŨĐŨŨ ŨĒŨŨŨŨ ŨŨŨŨ ŨŨŨŨĐŨ Ũ ŨŨ ŨŨ§Ũ ŨŨŨĪŨĒŨŨ ŨŨĐŨĪŨ ŨŨĒŨŨĻŨŨŠ/ŨĻŨŨĄŨŨŠ/ŨŨ ŨŨŨŨŠ/ŨĄŨĪŨĻŨŨŨŠ/ŨĒŨĻŨŨŨŠ ŨŨĒŨŨ..
ŨŨĄŨŨŨ ŨŨŨĶŨĒ ŨĪŨĒŨŨŨŨŠ ŨĒŨŨŨŨ ŨĐŨŨ ŨŨŠ ŨŨŨŠŨŨŨŨŨŠ ŨŨĒŨ ŨĪŨŨ ŨĐŨŨ ŨŨ: Ũ§ŨŨŨŨ ŨŨ ŨŨ, ŨŨŨĪŨ§Ũ, Ũ ŨŨĄŨŨĻ, ŨŨŨĻŨĄŨŨ ŨŨ ŨŨ.PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
Ėý
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
Ėý
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.Ad
Security, you are also part of the game
- 1. Open solutions, smarter people Security You are also part of the game This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License.
- 2. Open solutions, smarter people Who is that guy? âĒ Bert Desmet âĒ 23 years old âĒ Fedora â Ambassador, mentor, packager âĒ Loadays â Co organizer âĒ Numius â System Engineer, Consultant âĒ Devnox â Developer, System Engineer
- 3. Open solutions, smarter people Today's topics âĒ I'm a good hacker. âĒ Why I love USB sticks. âĒ Remember your password? âĒ Shhhhhhht!
- 4. Open solutions, smarter people I am a good hacker.
- 5. Open solutions, smarter people No tech hacking?
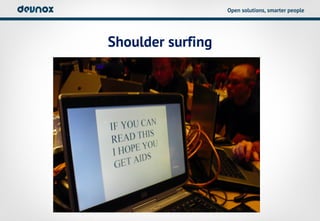
- 6. Open solutions, smarter people Shoulder surfing
- 7. Open solutions, smarter people Dumpster diving
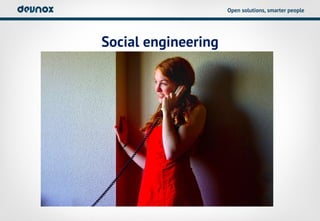
- 8. Open solutions, smarter people Social engineering
- 9. Open solutions, smarter people Taking pictures
- 10. Open solutions, smarter people Why I love USB sticks.
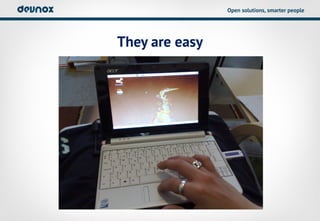
- 11. Open solutions, smarter people They are easy
- 12. Open solutions, smarter people And small
- 13. Open solutions, smarter people They are easily.. âĒ Forgotten âĒ Stolen
- 14. Open solutions, smarter people Some thoughts about it âĒ Encrypt your sensitive data âĒ Never put passwords on your system âĒ Use the intranet âĒ Never leave your portable gear alone âĒ Never forget your gear
- 15. Open solutions, smarter people Some statistics âĒ 53% of UK workers lost portable devices â >50% at a drinking venue âĒ Taxis and public transport âĒ 1 lost data record cost more than $187 â 70% indirect cost âĒ Lost costumers
- 16. Open solutions, smarter people Remember your password?
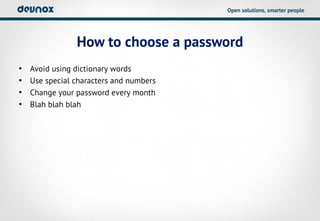
- 17. Open solutions, smarter people How to choose a password âĒ Avoid using dictionary words âĒ Use special characters and numbers âĒ Change your password every month âĒ Blah blah blah
- 18. Open solutions, smarter people How to choose a password âĒ Avoid using dictionary words âĒ Use special characters and numbers âĒ Change your password every month âĒ Blah blah blah
- 19. Open solutions, smarter people Entropy âĒ H : Entropy âĒ N : Possible symbols âĒ Length of string H= Lâlog2 N
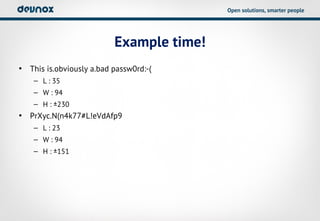
- 20. Open solutions, smarter people Example time! âĒ This is.obviously a.bad passw0rd:-( â L : 35 â W : 94 â H : Âą230 âĒ PrXyc.N(n4k77#L!eVdAfp9 â L : 23 â W : 94 â H : Âą151
- 21. Open solutions, smarter people Time to crack a password âĒ [[Guesses before string is found = 2H]] âĒ This is.obviously a.bad passw0rd:-( â 2230 = 1.72543659 Ã 1069 â 1000 guesses /s = 5.5 x 1058 years âĒ PrXyc.N(n4k77#L!eVdAfp9 â 2151 = 2.85449539 Ã 1045 â 1000 guesses /s = 9 Ã 1034 years
- 22. Open solutions, smarter people Password Strenght
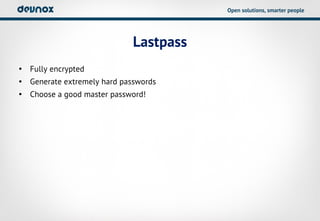
- 23. Open solutions, smarter people Lastpass âĒ Fully encrypted âĒ Generate extremely hard passwords âĒ Choose a good master password!
- 24. Open solutions, smarter people Some tips âĒ Never store passwords on pc âĒ Never use autologin
- 25. Open solutions, smarter people Shhhhhhhht!
- 26. Open solutions, smarter people I want you to shut up!
- 27. Open solutions, smarter people Security through obscurity âĒ Don't tell anyone âĒ Security based on secrecy
- 28. Open solutions, smarter people Kerckhoffs' doctrine âĒ Security can't depend on secrecy
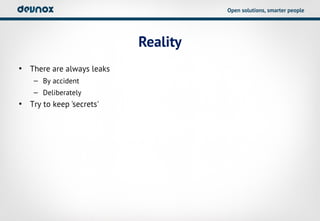
- 29. Open solutions, smarter people Reality âĒ There are always leaks â By accident â Deliberately âĒ Try to keep 'secrets'
- 30. Open solutions, smarter people Wait! There is more!
- 31. Open solutions, smarter people In a perfect world..
- 32. Open solutions, smarter people There is always a hole.
- 33. Open solutions, smarter people I like onions
- 34. Open solutions, smarter people Multi Level Security âĒ Multiple systems âĒ Building fort Knox âĒ You are the first line of defense
- 35. Open solutions, smarter people Extra! Extra!
- 36. Open solutions, smarter people Something you have..
- 37. Open solutions, smarter people Yubikey
- 38. Open solutions, smarter people I preach. And I practice.
- 39. Open solutions, smarter people Questions? âĒ Bert Desmet âĒ Security, you are also part of the game âĒ Mail: Bert@devnox.eu âĒ Twitter: @bdesmet_ âĒ Website: http://blog.bdesmet.be âĒ Website: http://www.devnox.eu âĒ This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License.
- 40. Open solutions, smarter people Sources âĒ Chess game: http://www.flickr.com/photos/seeminglee/1479932683/ âĒ Closed vault: http://www.flickr.com/photos/mstyne/3654056683/ âĒ Open vault: http://www.flickr.com/photos/spotsgot/156025944/ âĒ Onion: http://www.flickr.com/photos/inferis/107293622/ âĒ Laptop + usb stick: http://www.flickr.com/photos/wstryder/2780310027/ âĒ New York Public Library: http://www.flickr.com/photos/paul_lowry/2616820493/ âĒ Statistics on loosing gear: http://www.securestix.com/bad_news.php âĒ Shoulder surfing: http://www.flickr.com/photos/bonzoesc/209474964/ âĒ Dumpster: http://www.flickr.com/photos/urbanjacksonville/1803065217/ âĒ Telephone call: http://www.flickr.com/photos/lst1984/994531885/ âĒ Taking pictures: http://www.flickr.com/photos/glenpooh/708845839/ âĒ Xkcd joke: http://xkcd.com/936/ âĒ Shut up: http://www.flickr.com/photos/lorenia/934705558/ âĒ 3way handhake: http://media.photobucket.com/image/3%20way%20handshake/Haley_Bug/Mission%20Trip%20Choir%20Tour%202006/100_0087.jpg?o=1 âĒ Yubikey: http://www.flickr.com/photos/thofle/3206443137/ âĒ Special thanks to: Johnny Long
- 41. Open solutions, smarter people
