Seminar ppt on digital signature
Download as PPTX, PDF107 likes62,171 views
This document summarizes a seminar on digital signatures. It defines a digital signature as an encrypted hash value of a message that is unique to the document and verifies the identity of the owner. Digital signatures provide authenticity, integrity, and non-repudiation for electronic documents. The technology uses public and private key pairs, with the private key used to generate signatures and the public key used to verify signatures. Some challenges of digital signatures include the cost of certification authorities and ensuring private keys remain secure, but they enable secure e-commerce, e-governance and other applications.
1 of 19
Downloaded 4,534 times


![INTRODUCTION
’é┤The authenticity of many legal, financial, and other documents is
done by the presence or absence of an authorized handwritten
signature.
’é┤ŌĆ£Digital SignatureŌĆØ is the best solution for authenticity in various
fields.
’é┤A digital signature is nothing but an attachment to any piece of
electronic information, which represents the content of the
document and the identity of the owner of that document
uniquely[5].](https://image.slidesharecdn.com/seminar-151029231027-lva1-app6892/85/Seminar-ppt-on-digital-signature-3-320.jpg)


![BASIC REQUIREMENTSŌĆ”.
’é┤Private Key
The private key is one which is accessible only to the signer. It is
used to generate the digital signature which is then attached to the
message.[2]
’é┤Public Key
The public key is made available to all those who receive the signed
messages from the sender. It is used for verification of the received
message.[2]](https://image.slidesharecdn.com/seminar-151029231027-lva1-app6892/85/Seminar-ppt-on-digital-signature-6-320.jpg)
![BASIC REQUIREMENTSŌĆ”
’é┤ Digital Signature Certificate
’é┤A subscriber of the private key and public key pair makes the public
key available to all those who are intended to receive the signed
messages from the subscriber.[1]
’é┤ But in case of any dispute between the two sides, there must be some
entity with the receiver which will allow the receiver of the message
to prove that the message was sent by the subscriber of the key pair.
This can be done with the Digital Signature Certificate.[1]](https://image.slidesharecdn.com/seminar-151029231027-lva1-app6892/85/Seminar-ppt-on-digital-signature-7-320.jpg)





![DRAWBACKS
’é┤The private key must be kept in a secured manner.[3]
’é┤The process of generation and verification of digital signature
requires considerable amount of time.[3]
’é┤For using the digital signature the user has to obtain private and
public key, the receiver has to obtain the digital signature certificate
also.[3]](https://image.slidesharecdn.com/seminar-151029231027-lva1-app6892/85/Seminar-ppt-on-digital-signature-16-320.jpg)



Recommended
Digital signatures



Digital signaturesIshwar Dayal
╠²
Digital signatures provide authenticity, integrity, and non-repudiation for electronic documents and allow for secure e-governance and e-commerce using the internet. A digital signature is created using a private key to sign a message, and the signature can be verified using the corresponding public key. Digital signatures employ asymmetric cryptography and consist of key generation, signing, and verification algorithms. Hardware tokens like smart cards and USB tokens securely store private keys to generate digital signatures on documents. The Controller of Certifying Authorities licenses and regulates certification authorities in India to issue digital signature certificates.Digital Signature



Digital SignatureMohamed Talaat
╠²
This presentation provides an introduction to the digital signature topic, it also shows the desired properties and the related applications.Digital signature



Digital signatureFilipp Kolobov
╠²
Digital signatures use asymmetric cryptography to provide authentication, integrity and non-repudiation for electronic documents and communications. A digital signature is created using a private key and can be verified by anyone using the corresponding public key. This ensures the document was not altered and the sender cannot deny sending it. Private keys are protected using devices like smart cards or hardware tokens to keep them secure.Digital Signature ppt



Digital Signature pptOECLIB Odisha Electronics Control Library
╠²
The authenticity of many legal, financial, and other documents is determined by the presence or absence of an authorizes handwritten signatureDigital signature



Digital signatureAJAL A J
╠²
Digital signatures provide authentication, integrity, and non-repudiation for digital documents and messages. They work by using public key cryptography where a private key is used to sign a message hash and the corresponding public key can then verify that the signature is valid. Digital signatures are important for electronic transactions and communications where the identity of the sender and the integrity of the message need to be assured. However, digital signatures are only as secure as the private keys used to create them.Secure electronic transaction ppt



Secure electronic transaction pptSubhash Gupta
╠²
The document discusses Secure Electronic Transaction (SET), which is a protocol that aims to secure credit card transactions on the internet. It consists of a set of protocols to provide confidentiality, integrity, authentication, and non-repudiation. SET uses public key cryptography including digital signatures and certificates to authenticate parties and encrypt transaction information. The key steps in a SET transaction involve the customer sending encrypted order and payment information to the merchant, who then requests payment authorization from the payment gateway before fulfilling the order.Digital Signature



Digital Signaturesaurav5884
╠²
Digital signatures provide authentication and integrity for electronic documents and transactions. They use public key cryptography where a document is encrypted with the sender's private key and decrypted by the recipient's public key. A digital certificate issued by a certificate authority binds the signer's identity to their public key and is verified using the CA's digital signature. Common uses of digital signatures include software updates, financial transactions, and legally binding documents.Digital Signature



Digital SignatureAdarsh Kumar Yadav
╠²
This document summarizes a colloquium on digital signatures presented by Prashant Shekhar. It introduces digital signatures as a way to authenticate electronic documents through a mathematical scheme. It discusses how digital signatures work using public and private keys along with digital certificates from a certification authority. The document also outlines some applications of digital signatures like email, data storage, funds transfer, and software distribution. It concludes by noting advantages like authentication, integrity, and non-repudiation, as well as disadvantages such as expiration of certificates and costs of software.Digital signature



Digital signaturePraseela R
╠²
This document discusses digital signatures and how they provide security services like secrecy, authentication, non-repudiation and integrity. It explains that digital signatures use asymmetric cryptography with a private key for signing and a public key for verification. The digital signature is created by hashing the message and signing it with the private key. When received, the message hash is verified using the public key to authenticate that the signature was created by the private key owner and that the message has not been altered. Digital signatures thus authenticate messages and ensure non-repudiation by binding the signer to the message in a way that can be verified.Digital signature



Digital signatureAJAL A J
╠²
Easy for the signer to sign a message
There is no point in having a digital signature scheme that involves the signer needing to use slow and complex operations to compute a digital signature.
Easy for anyone to verify a message
Similarly we would like the verification of a digital signature to be as efficient as possible.
Hard for anyone to forge a digital signature
It should be practically impossible for anyone who is not the legitimate signer to compute a digital signature on a message that appears to be valid. By ŌĆ£appears to be validŌĆØ we mean that anyone who attempts to verify the digital signature is led to believe that they have just successfully verified a valid digital signature on a message.Digital certificates & its importance



Digital certificates & its importancesvm
╠²
A digital certificate is a unique electronic document that identifies an individual or organization. It uses public key infrastructure (PKI) to allow secure data exchange over the internet. A digital certificate contains a public key and is digitally signed by a certificate authority (CA) that verifies the identity of the requester. When user A sends a message to user B, user B can verify user A's certificate by checking the CA's digital signature on the certificate using the CA's public key. Digital certificates are important for secure communication, online banking, expanding e-commerce, and protecting against online threats. The major types are SSL certificates for servers, code signing certificates for software, and client certificates for identifying individuals.public key infrastructure



public key infrastructurevimal kumar
╠²
This document summarizes a seminar presentation on public key infrastructure (PKI). It discusses key concepts of PKI including digital signatures, certificates, validation, revocation, and the roles of certification authorities. The presentation covers how asymmetric encryption, hashing, and digital signatures enable secure authentication and authorization in a PKI. It also examines the entities, operations, and technologies involved in implementing and managing a PKI, such as certificate authorities, registration authorities, key generation and storage, and certification revocation lists.Digital signature



Digital signatureHossain Md Shakhawat
╠²
Digital Signature, Electronic Signature, How digital signature works, Confidentiality of digital signature, Authenticity of digital signature, Integrity of digital signature, standard of digital signature, Algorithm of digital signature, Mathematical base of digital signature, parameters of digital signature, key computation of digital signature, key generation of digital signature, verification of of digital signatureDigital certificates



Digital certificatesBuddhika Karunanayaka
╠²
This document discusses the history and uses of cryptography and digital certificates. It provides an overview of how public key infrastructure (PKI) uses public and private key pairs to securely exchange information over networks. A certification authority (CA) is responsible for issuing digital certificates which contain a public key and verify identity. PKI and digital certificates are used for applications like encryption, digital signatures, authentication, and secure communication protocols.Digital signature



Digital signatureAbdullah Khosa
╠²
The document discusses digital signatures, including what they are, how they work, and their use and importance for organizations. A digital signature is a small block of encrypted data attached to an electronic document that verifies the signer's identity and ensures the document has not been altered. For organizations, digital signatures can save significant time and costs compared to physical signatures by allowing remote signing of documents without printing or delivery. While some prefer the personal connection of handwritten signatures, digital signatures are more secure and efficient and will likely replace physical signatures as the technology becomes more advanced and widely used.Digital certificates



Digital certificatesSimmi Kamra
╠²
Digital signatures use asymmetric cryptography to authenticate digital messages. They allow a recipient to verify the identity of the sender and confirm the message has not been altered. A digital signature scheme involves key generation, signing, and verification algorithms. Digital signatures provide authentication, integrity, and non-repudiation and are commonly used for software distribution, financial transactions, and other cases requiring detection of forgery or tampering. They offer advantages over traditional ink signatures like inability to forge or erase the signature.Introduction to Digital signatures



Introduction to Digital signaturesRohit Bhat
╠²
This document provides an introduction to digital signatures, including an overview of encryption, hashing, digital signature creation and verification, and different digital signature schemes like RSA, ElGamal, and Schnorr. It also discusses the legal aspects and advantages/disadvantages of digital signatures.Digital signature



Digital signatureMohanasundaram Nattudurai
╠²
This PPT provides an complete reference of "DIGITAL SIGNATURE". It gives "how the digital signature are works?" and "why we need a digital signature?". And also I include some Digital signature algorithm in a Diagrammatic format.Digital Signature



Digital Signaturenayakslideshare
╠²
Digital signatures provide authenticity, integrity and non-repudiation to electronic documents by using public key infrastructure. Under PKI, each individual has a public/private key pair, and certification authorities verify and certify individuals' public keys. Digital signatures are generated by encrypting a document hash with an individual's private key and can be verified by decrypting with the corresponding public key.cryptography



cryptographyswatihans
╠²
Cryptography involves converting plain text into cipher text to secure communication. There are two main types: private/symmetric key cryptography uses a single shared key for encryption and decryption, while public/asymmetric key cryptography uses two keys - a public key to encrypt and a private key to decrypt. Private key cryptography is faster but requires secure key exchange, while public key allows communication without pre-shared keys and enables authentication and digital signatures.Digital signature 2



Digital signature 2Ankita Dave
╠²
The document discusses digital signatures and the process for obtaining a digital signature certificate in India. It defines digital signatures and compares them to paper signatures. It outlines the different classes of digital signature certificates (1, 2, and 3) and explains that a class 3 certificate is needed for individuals for legally valid purposes. The steps to obtain a class 3 certificate involve downloading root certificates, selecting a certification authority, visiting their website, selecting the certificate type, and submitting an online request to generate a key pair.DIGITAL SIGNATURE



DIGITAL SIGNATUREravijain90
╠²
Digital signatures provide authenticity, integrity, and non-repudiation for electronic documents. They use asymmetric cryptography with a private key for signing and public key for verification. The signer uses their private key to encrypt a hash of the message, creating a digital signature. The recipient can then decrypt the signature with the signer's public key to verify the message has not been altered. Hardware tokens like smart cards and USB tokens store private keys securely. The Controller of Certifying Authorities licenses and monitors Certifying Authorities in India that issue digital signature certificates.Digital signature



Digital signatureYash Karanke
╠²
The document discusses digital signatures, including how they work, their history, applications, and legal status in India. A digital signature uses public and private keys to authenticate a message sender's identity and verify that the message was not altered. It explains how digital signature certificates are issued by certified authorities and associate an individual's identity with their public and private keys. The document also addresses frequently asked questions about digital signatures, such as how they provide security, who issues them, how long they are valid for, and their legal standing.Seminar presentation on digital signature ppt



Seminar presentation on digital signature pptRavi Ranjan
╠²
This document discusses digital signatures. It begins by introducing digital signatures as an electronic equivalent to handwritten signatures for authenticating documents. It then explains that a digital signature is created by encrypting a document's hash value with the sender's private key. The digital signature and public key allow any recipient to verify the sender's identity and confirm the document has not been altered. The document outlines the basic requirements for digital signatures like private and public keys and digital certificates. It also describes how the technology works and some common applications as well as challenges and drawbacks of digital signatures.Digital signature & certificate



Digital signature & certificateNetGains Technologies Pvt. Ltd.
╠²
This document summarizes key aspects of digital signatures and encryption. It explains that digital signatures use public/private key pairs to encrypt messages for authentication, integrity and non-repudiation. A certificate authority acts as a trusted third party by issuing digital certificates that contain a user's public key and identity information signed with the CA's private key. The document also compares features of paper signatures to digital signatures.Computer forensic ppt



Computer forensic pptPriya Manik
╠²
Computer forensics is a branch of digital forensic science involving the legal investigation and analysis of evidence found in computers and digital storage media. The objectives are to recover, analyze, and preserve digital evidence in a way that can be presented in a court of law, and to identify evidence and assess the identity and intent of perpetrators in a timely manner. Computer forensics techniques include acquiring, identifying, evaluating, and presenting digital evidence found in files, databases, audio/video files, websites, and other locations on computers, as well as analyzing deleted files, network activity, and detecting steganography.Digital signature(Cryptography)



Digital signature(Cryptography)Soham Kansodaria
╠²
The document provides an overview of digital signatures, including their history, theory, workings, and importance. Digital signatures were first proposed in 1976 and use public key cryptography to validate the authenticity and integrity of electronic documents and messages. They work by encrypting a hash of the message with the sender's private key, which can later be decrypted and verified by the recipient using the sender's public key. This allows the recipient to confirm the message has not been tampered with and was signed by the proper sender. Digital signatures provide security benefits like non-repudiation and are legally recognized in many countries and applications.Introduction to Cryptography



Introduction to CryptographyMd. Afif Al Mamun
╠²
Cryptography is the practice of securing communication and information by converting plaintext into ciphertext. The document provides an introduction to cryptography including its history from ancient times to the present. It discusses terminology like plaintext, encryption, ciphertext, decryption, and keys. Symmetric key cryptography uses a single key for encryption and decryption while asymmetric key cryptography uses two different keys. Examples of symmetric methods are DES, 3DES, AES, and RC4, while RSA is a common asymmetric method. Applications of cryptography include ATMs, email passwords, e-payments, e-commerce, electronic voting, defense services, securing data, and access control.Digital Signature.pptx



Digital Signature.pptxMd. AManullah Galib
╠²
This document provides an overview of digital signatures, including what they are, why they are used, how the technology works, and some challenges. A digital signature is a hash of a message encrypted with a private key, allowing the authenticity and integrity of electronic documents and messages to be verified using the corresponding public key. Digital signatures provide authentication, integrity, and non-repudiation for electronic communications and help enable the internet as a secure medium for transactions, though key security and certification costs present challenges. The document also reviews digital signature algorithms, applications, and drawbacks.csedigitalsignatureppt-170420041737.pdf



csedigitalsignatureppt-170420041737.pdfMehediHasanShaon1
╠²
This document discusses digital signatures. It begins by introducing digital signatures as an electronic equivalent to handwritten signatures for authenticating documents. It then explains that a digital signature is created by encrypting a document's hash value with the sender's private key. The digital signature and public key allow any recipient to verify the sender's identity and confirm the document has not been altered. The document outlines the basic requirements for digital signatures like private/public key pairs and digital certificates. It also describes how the technology works and some common applications as well as challenges like costs and ensuring private keys stay secure. In conclusion, it notes digital signatures may be difficult for the public to understand and trust due to involvement of organizations they may be wary of.More Related Content
What's hot (20)
Digital signature



Digital signaturePraseela R
╠²
This document discusses digital signatures and how they provide security services like secrecy, authentication, non-repudiation and integrity. It explains that digital signatures use asymmetric cryptography with a private key for signing and a public key for verification. The digital signature is created by hashing the message and signing it with the private key. When received, the message hash is verified using the public key to authenticate that the signature was created by the private key owner and that the message has not been altered. Digital signatures thus authenticate messages and ensure non-repudiation by binding the signer to the message in a way that can be verified.Digital signature



Digital signatureAJAL A J
╠²
Easy for the signer to sign a message
There is no point in having a digital signature scheme that involves the signer needing to use slow and complex operations to compute a digital signature.
Easy for anyone to verify a message
Similarly we would like the verification of a digital signature to be as efficient as possible.
Hard for anyone to forge a digital signature
It should be practically impossible for anyone who is not the legitimate signer to compute a digital signature on a message that appears to be valid. By ŌĆ£appears to be validŌĆØ we mean that anyone who attempts to verify the digital signature is led to believe that they have just successfully verified a valid digital signature on a message.Digital certificates & its importance



Digital certificates & its importancesvm
╠²
A digital certificate is a unique electronic document that identifies an individual or organization. It uses public key infrastructure (PKI) to allow secure data exchange over the internet. A digital certificate contains a public key and is digitally signed by a certificate authority (CA) that verifies the identity of the requester. When user A sends a message to user B, user B can verify user A's certificate by checking the CA's digital signature on the certificate using the CA's public key. Digital certificates are important for secure communication, online banking, expanding e-commerce, and protecting against online threats. The major types are SSL certificates for servers, code signing certificates for software, and client certificates for identifying individuals.public key infrastructure



public key infrastructurevimal kumar
╠²
This document summarizes a seminar presentation on public key infrastructure (PKI). It discusses key concepts of PKI including digital signatures, certificates, validation, revocation, and the roles of certification authorities. The presentation covers how asymmetric encryption, hashing, and digital signatures enable secure authentication and authorization in a PKI. It also examines the entities, operations, and technologies involved in implementing and managing a PKI, such as certificate authorities, registration authorities, key generation and storage, and certification revocation lists.Digital signature



Digital signatureHossain Md Shakhawat
╠²
Digital Signature, Electronic Signature, How digital signature works, Confidentiality of digital signature, Authenticity of digital signature, Integrity of digital signature, standard of digital signature, Algorithm of digital signature, Mathematical base of digital signature, parameters of digital signature, key computation of digital signature, key generation of digital signature, verification of of digital signatureDigital certificates



Digital certificatesBuddhika Karunanayaka
╠²
This document discusses the history and uses of cryptography and digital certificates. It provides an overview of how public key infrastructure (PKI) uses public and private key pairs to securely exchange information over networks. A certification authority (CA) is responsible for issuing digital certificates which contain a public key and verify identity. PKI and digital certificates are used for applications like encryption, digital signatures, authentication, and secure communication protocols.Digital signature



Digital signatureAbdullah Khosa
╠²
The document discusses digital signatures, including what they are, how they work, and their use and importance for organizations. A digital signature is a small block of encrypted data attached to an electronic document that verifies the signer's identity and ensures the document has not been altered. For organizations, digital signatures can save significant time and costs compared to physical signatures by allowing remote signing of documents without printing or delivery. While some prefer the personal connection of handwritten signatures, digital signatures are more secure and efficient and will likely replace physical signatures as the technology becomes more advanced and widely used.Digital certificates



Digital certificatesSimmi Kamra
╠²
Digital signatures use asymmetric cryptography to authenticate digital messages. They allow a recipient to verify the identity of the sender and confirm the message has not been altered. A digital signature scheme involves key generation, signing, and verification algorithms. Digital signatures provide authentication, integrity, and non-repudiation and are commonly used for software distribution, financial transactions, and other cases requiring detection of forgery or tampering. They offer advantages over traditional ink signatures like inability to forge or erase the signature.Introduction to Digital signatures



Introduction to Digital signaturesRohit Bhat
╠²
This document provides an introduction to digital signatures, including an overview of encryption, hashing, digital signature creation and verification, and different digital signature schemes like RSA, ElGamal, and Schnorr. It also discusses the legal aspects and advantages/disadvantages of digital signatures.Digital signature



Digital signatureMohanasundaram Nattudurai
╠²
This PPT provides an complete reference of "DIGITAL SIGNATURE". It gives "how the digital signature are works?" and "why we need a digital signature?". And also I include some Digital signature algorithm in a Diagrammatic format.Digital Signature



Digital Signaturenayakslideshare
╠²
Digital signatures provide authenticity, integrity and non-repudiation to electronic documents by using public key infrastructure. Under PKI, each individual has a public/private key pair, and certification authorities verify and certify individuals' public keys. Digital signatures are generated by encrypting a document hash with an individual's private key and can be verified by decrypting with the corresponding public key.cryptography



cryptographyswatihans
╠²
Cryptography involves converting plain text into cipher text to secure communication. There are two main types: private/symmetric key cryptography uses a single shared key for encryption and decryption, while public/asymmetric key cryptography uses two keys - a public key to encrypt and a private key to decrypt. Private key cryptography is faster but requires secure key exchange, while public key allows communication without pre-shared keys and enables authentication and digital signatures.Digital signature 2



Digital signature 2Ankita Dave
╠²
The document discusses digital signatures and the process for obtaining a digital signature certificate in India. It defines digital signatures and compares them to paper signatures. It outlines the different classes of digital signature certificates (1, 2, and 3) and explains that a class 3 certificate is needed for individuals for legally valid purposes. The steps to obtain a class 3 certificate involve downloading root certificates, selecting a certification authority, visiting their website, selecting the certificate type, and submitting an online request to generate a key pair.DIGITAL SIGNATURE



DIGITAL SIGNATUREravijain90
╠²
Digital signatures provide authenticity, integrity, and non-repudiation for electronic documents. They use asymmetric cryptography with a private key for signing and public key for verification. The signer uses their private key to encrypt a hash of the message, creating a digital signature. The recipient can then decrypt the signature with the signer's public key to verify the message has not been altered. Hardware tokens like smart cards and USB tokens store private keys securely. The Controller of Certifying Authorities licenses and monitors Certifying Authorities in India that issue digital signature certificates.Digital signature



Digital signatureYash Karanke
╠²
The document discusses digital signatures, including how they work, their history, applications, and legal status in India. A digital signature uses public and private keys to authenticate a message sender's identity and verify that the message was not altered. It explains how digital signature certificates are issued by certified authorities and associate an individual's identity with their public and private keys. The document also addresses frequently asked questions about digital signatures, such as how they provide security, who issues them, how long they are valid for, and their legal standing.Seminar presentation on digital signature ppt



Seminar presentation on digital signature pptRavi Ranjan
╠²
This document discusses digital signatures. It begins by introducing digital signatures as an electronic equivalent to handwritten signatures for authenticating documents. It then explains that a digital signature is created by encrypting a document's hash value with the sender's private key. The digital signature and public key allow any recipient to verify the sender's identity and confirm the document has not been altered. The document outlines the basic requirements for digital signatures like private and public keys and digital certificates. It also describes how the technology works and some common applications as well as challenges and drawbacks of digital signatures.Digital signature & certificate



Digital signature & certificateNetGains Technologies Pvt. Ltd.
╠²
This document summarizes key aspects of digital signatures and encryption. It explains that digital signatures use public/private key pairs to encrypt messages for authentication, integrity and non-repudiation. A certificate authority acts as a trusted third party by issuing digital certificates that contain a user's public key and identity information signed with the CA's private key. The document also compares features of paper signatures to digital signatures.Computer forensic ppt



Computer forensic pptPriya Manik
╠²
Computer forensics is a branch of digital forensic science involving the legal investigation and analysis of evidence found in computers and digital storage media. The objectives are to recover, analyze, and preserve digital evidence in a way that can be presented in a court of law, and to identify evidence and assess the identity and intent of perpetrators in a timely manner. Computer forensics techniques include acquiring, identifying, evaluating, and presenting digital evidence found in files, databases, audio/video files, websites, and other locations on computers, as well as analyzing deleted files, network activity, and detecting steganography.Digital signature(Cryptography)



Digital signature(Cryptography)Soham Kansodaria
╠²
The document provides an overview of digital signatures, including their history, theory, workings, and importance. Digital signatures were first proposed in 1976 and use public key cryptography to validate the authenticity and integrity of electronic documents and messages. They work by encrypting a hash of the message with the sender's private key, which can later be decrypted and verified by the recipient using the sender's public key. This allows the recipient to confirm the message has not been tampered with and was signed by the proper sender. Digital signatures provide security benefits like non-repudiation and are legally recognized in many countries and applications.Introduction to Cryptography



Introduction to CryptographyMd. Afif Al Mamun
╠²
Cryptography is the practice of securing communication and information by converting plaintext into ciphertext. The document provides an introduction to cryptography including its history from ancient times to the present. It discusses terminology like plaintext, encryption, ciphertext, decryption, and keys. Symmetric key cryptography uses a single key for encryption and decryption while asymmetric key cryptography uses two different keys. Examples of symmetric methods are DES, 3DES, AES, and RC4, while RSA is a common asymmetric method. Applications of cryptography include ATMs, email passwords, e-payments, e-commerce, electronic voting, defense services, securing data, and access control.Similar to Seminar ppt on digital signature (20)
Digital Signature.pptx



Digital Signature.pptxMd. AManullah Galib
╠²
This document provides an overview of digital signatures, including what they are, why they are used, how the technology works, and some challenges. A digital signature is a hash of a message encrypted with a private key, allowing the authenticity and integrity of electronic documents and messages to be verified using the corresponding public key. Digital signatures provide authentication, integrity, and non-repudiation for electronic communications and help enable the internet as a secure medium for transactions, though key security and certification costs present challenges. The document also reviews digital signature algorithms, applications, and drawbacks.csedigitalsignatureppt-170420041737.pdf



csedigitalsignatureppt-170420041737.pdfMehediHasanShaon1
╠²
This document discusses digital signatures. It begins by introducing digital signatures as an electronic equivalent to handwritten signatures for authenticating documents. It then explains that a digital signature is created by encrypting a document's hash value with the sender's private key. The digital signature and public key allow any recipient to verify the sender's identity and confirm the document has not been altered. The document outlines the basic requirements for digital signatures like private/public key pairs and digital certificates. It also describes how the technology works and some common applications as well as challenges like costs and ensuring private keys stay secure. In conclusion, it notes digital signatures may be difficult for the public to understand and trust due to involvement of organizations they may be wary of.DIGITAL SIGNATURE PPT



DIGITAL SIGNATURE PPTRajanGoyal16
╠²
This document discusses digital signatures, which provide authenticity, integrity, and non-repudiation for electronic documents. A digital signature is a mathematical scheme that uses public key encryption to verify that a digital message was created by a known sender and was not altered in transit. The document outlines the basic requirements of private and public keys, and how the technology works. It compares digital and paper signatures, and lists some applications of digital signatures such as electronic mail, data storage, and software distribution.digital signature ppt



digital signature pptNitesh Dubey
╠²
Power point Presentation on the digital signature and in this presentation cover mostly all the points and effectively mannerDigital signturue



Digital signturueSanjeevsharma620
╠²
The document discusses digital signatures, which are used to authenticate the sender of an electronic document. Digital signatures provide authenticity, integrity, and non-repudiation to electronic documents by using public and private key cryptography. They allow identification of the signer, detection of any changes to data, and prevention of impersonation. While digital signatures enable secure e-commerce and e-governance, they also have disadvantages like reliance on certificates and verification software that require costs and have limited lifespans.Digital signatur



Digital signaturRuwandi Madhunamali
╠²
Digital signatures provide authentication, integrity, and non-repudiation for electronic documents. They work by using public key cryptography - a signer encrypts a hash of a message with their private key, which can be verified by anyone using the signer's public key. Major milestones in digital signatures include the invention of the RSA algorithm in 1977 and laws passed in 2000 and 2008 that gave digital signatures legal standing. While they provide security, key security and processing times are challenges.Digital Signature Agency



Digital Signature AgencyDigital Signature Agency
╠²
Welcome to digital signature agency, we are introduce our self, we are the best digital signature service provider in Delhi, India. We are authorised signatory of Vsing deals in Franchise, Agency, DSP, RA, RAA, LRA, Partner, Associates, Reseller, Dealer Account in all over india. We provide of Class 3 digital signatures, DGFT Signature and Docuemnt Signer DSC with complete paperless and quick process We offer vsign digital Signature at very low price.Digital Signature Certificate



Digital Signature CertificateDigitalcertificate
╠²
A Digital Signature Certificate Helps to provides you Individual and organization dsc for all purspose just like Income TAx, ROC, Trademark, E-Tenders, DGFT Etc. We offer all type of Digital Signature Certificate like Class2, Class3, DGFT as per your request. DGFT Signature and Docuemnt Signer DSC with complete paperless and quick process We offer vsign digital Signature at very low price and Our team provides the best servics of any other .
Difference between digital signature and digital certificate.pdf



Difference between digital signature and digital certificate.pdfefiling24
╠²
A digital signature and a digital certificate are both crucial in ensuring secure electronic communications, but they serve different purposes. A digital signature is an electronic equivalent of a handwritten signature, providing a way to verify the authenticity and integrity of a digital message or document. It ensures that the content has not been altered and confirms the identity of the signer. On the other hand, a digital certificate is an electronic document issued by a trusted authority (such as a Certificate Authority) that links the identity of the certificate holder, The certificate is used to establish the legitimacy of the holder's public key, enabling secure data exchanges, encryption, and the validation of digital signatures.Digital signature by mohsin iftikhar 



Digital signature by mohsin iftikhar Mohsin Ali
╠²
The document discusses digital signatures and encryption. It defines encryption as converting data into cipher text. There are two main types of encryption - private key encryption where each computer has a secret key, and public key encryption which uses a combination of private and public keys. A digital signature mathematically validates the authenticity and integrity of a message to prevent tampering. It serves as an electronic equivalent of a handwritten signature. The document then discusses the history and applications of digital signatures, and how digital signature certificates work by associating an identity with a public/private key pair.Dsc ppt



Dsc pptEarnlogicconsultants
╠²
Digital signature certificates provide security and authentication for electronic documents. When a digital signature is applied to a document, unique identification information is encrypted and embedded that allows the signature and document to be verified. This ensures the document content has not been altered and validates the signer's identity. Digital signature certificates come in classes for different use cases, with higher classes providing greater security for tasks involving sensitive information or large financial transactions. Proper implementation of digital signatures protects documents and identities from tampering or fraudulent actions.Digital Signature in Indian Evidence act .pptx



Digital Signature in Indian Evidence act .pptx9jz8vgkshv
╠²
Digital signatures provide a secure way to authenticate digital documents and messages. They use asymmetric encryption and digital certificates to verify identity and ensure document integrity. A digital signature is created by encrypting a hash of the message with the sender's private key, and can be verified by decrypting the signature with the sender's public key. This allows the recipient to confirm the identity of the sender and that the message content was not altered after signature. Digital signatures have legal standing and provide benefits like authentication, non-repudiation, and ensuring documents have not been tampered with.Digital Signatdsbuisduifhudosffdosfure.pptx



Digital Signatdsbuisduifhudosffdosfure.pptxMuthuvasanSR
╠²
Digital signatures provide a secure way to authenticate digital documents and messages. They use asymmetric encryption and digital certificates to verify identity and ensure document integrity. A digital signature is created by encrypting a hash of the message with the sender's private key, and can be verified by decrypting the signature with the sender's public key. This allows the recipient to confirm the identity of the sender and that the message content was not altered after signature.Digital signature



Digital signaturedhivyakesavan3
╠²
Digital signatures provide authentication and integrity for messages. A digital signature is formed by taking the hash of a message and encrypting it with the sender's private key. This guarantees the source and ensures the message has not been altered. Digital signatures can use direct signing between parties or an arbitrated approach involving a third party. The arbitrated method provides advantages in that no information is shared beforehand to prevent fraud and no incorrectly dated messages can be sent.Digital Signature provider in Delhi



Digital Signature provider in DelhiDigital Signature Agency
╠²
Vsign digital signature Agency Website is one of the best service provider in Delhi we provider all types of digital signature Individual and organization dsc for all purspose at very low priceDigital signature



Digital signatureJanani S
╠²
This document discusses digital signatures, including their basic requirements, working technology, and applications. Digital signatures provide authenticity, integrity, and non-repudiation for electronic documents by using public/private key pairs. The private key is used to generate a digital signature for a message, and anyone can verify the signature using the corresponding public key. Common uses of digital signatures include email, data storage, funds transfer, software distribution, and smart cards. GnuPG is an open source tool that can be used to generate key pairs, exchange keys, encrypt/decrypt files, and make/verify digital signatures.Electronic signature



Electronic signatureMelwin Mathew
╠²
Difference between electronic signature and digital signature, electronic signature vendors, agencies etc.Digital Signature in Gurgaon



Digital Signature in GurgaonDigitalSignatureGurg
╠²
Welcome to Digital Signature Gurgaon, Haryana. We are introduce our website in Digital
Signature Certificate. Here we are providing all solution of Digital signature
certificate. we Provides you Individual and organization dsc for for All Purspose GST
Filling, MCA, ROC E-filling, Provident Fund, Income Tax Return Filling and E-tender.
At very low price for any other Digital signature Gurgaon is the one of the best Digital
signature Provider in Gurgaon
Presentation on digital signatures & digital certificates



Presentation on digital signatures & digital certificatesVivaka Nand
╠²
Digital signatures and digital certificates use public key cryptography to authenticate users and verify the integrity of digital documents. A digital signature is created by encrypting a document with a user's private key. Anyone can then decrypt the signature using the signer's public key to verify that the document came from the correct user and has not been altered. Digital certificates contain a user's public key and identification information, and are digitally signed by a Certificate Authority to validate the certificate. Common uses of digital signatures and certificates include encrypting messages, authenticating users, and facilitating secure online transactions.Digital_signature_ppt.pptx



Digital_signature_ppt.pptxMIRZATABISHHASAN1
╠²
Disgital Signature Algorithm which is used Hash value of a message when encrypted with the private key of a person is his digital signature on that e-Document.
Digital Signature of a person therefore varies from document to document thus ensuring authenticity of each word of that document.
As the public key of the signer is known, anybody can verify the message and the digital signature.
Recently uploaded (20)
Multi objective genetic approach with Ranking



Multi objective genetic approach with Rankingnamisha18
╠²
Multi objective genetic approach with Ranking Turbocor Product and Technology Review.pdf



Turbocor Product and Technology Review.pdfTotok Sulistiyanto
╠²
High Efficiency Chiller System in HVACEnv and Water Supply Engg._Dr. Hasan.pdf



Env and Water Supply Engg._Dr. Hasan.pdfMahmudHasan747870
╠²
Core course, namely Environment and Water Supply Engineering. Full lecture notes are in book format for the BSc in Civil Engineering program. US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
╠²
Preface: The ReGenX Generator innovation operates with a US Patented Frequency Dependent Load
Current Delay which delays the creation and storage of created Electromagnetic Field Energy around
the exterior of the generator coil. The result is the created and Time Delayed Electromagnetic Field
Energy performs any magnitude of Positive Electro-Mechanical Work at infinite efficiency on the
generator's Rotating Magnetic Field, increasing its Kinetic Energy and increasing the Kinetic Energy of
an EV or ICE Vehicle to any magnitude without requiring any Externally Supplied Input Energy. In
Electricity Generation applications the ReGenX Generator innovation now allows all electricity to be
generated at infinite efficiency requiring zero Input Energy, zero Input Energy Cost, while producing
zero Greenhouse Gas Emissions, zero Air Pollution and zero Nuclear Waste during the Electricity
Generation Phase. In Electric Motor operation the ReGen-X Quantum Motor now allows any
magnitude of Work to be performed with zero Electric Input Energy.
Demonstration Protocol: The demonstration protocol involves three prototypes;
1. Protytpe #1, demonstrates the ReGenX Generator's Load Current Time Delay when compared
to the instantaneous Load Current Sine Wave for a Conventional Generator Coil.
2. In the Conventional Faraday Generator operation the created Electromagnetic Field Energy
performs Negative Work at infinite efficiency and it reduces the Kinetic Energy of the system.
3. The Magnitude of the Negative Work / System Kinetic Energy Reduction (in Joules) is equal to
the Magnitude of the created Electromagnetic Field Energy (also in Joules).
4. When the Conventional Faraday Generator is placed On-Load, Negative Work is performed and
the speed of the system decreases according to Lenz's Law of Induction.
5. In order to maintain the System Speed and the Electric Power magnitude to the Loads,
additional Input Power must be supplied to the Prime Mover and additional Mechanical Input
Power must be supplied to the Generator's Drive Shaft.
6. For example, if 100 Watts of Electric Power is delivered to the Load by the Faraday Generator,
an additional >100 Watts of Mechanical Input Power must be supplied to the Generator's Drive
Shaft by the Prime Mover.
7. If 1 MW of Electric Power is delivered to the Load by the Faraday Generator, an additional >1
MW Watts of Mechanical Input Power must be supplied to the Generator's Drive Shaft by the
Prime Mover.
8. Generally speaking the ratio is 2 Watts of Mechanical Input Power to every 1 Watt of Electric
Output Power generated.
9. The increase in Drive Shaft Mechanical Input Power is provided by the Prime Mover and the
Input Energy Source which powers the Prime Mover.
10. In the Heins ReGenX Generator operation the created and Time Delayed Electromagnetic Field
Energy performs Positive Work at infinite efficiency and it increases the Kinetic Energy of the
system.
How to Build a Maze Solving Robot Using Arduino



How to Build a Maze Solving Robot Using ArduinoCircuitDigest
╠²
Learn how to make an Arduino-powered robot that can navigate mazes on its own using IR sensors and "Hand on the wall" algorithm.
This step-by-step guide will show you how to build your own maze-solving robot using Arduino UNO, three IR sensors, and basic components that you can easily find in your local electronics shop.The Golden Gate Bridge a structural marvel inspired by mother nature.pptx



The Golden Gate Bridge a structural marvel inspired by mother nature.pptxAkankshaRawat75
╠²
The Golden Gate Bridge is a 6 lane suspension bridge spans the Golden Gate Strait, connecting the city of San Francisco to Marin County, California.
It provides a vital transportation link between the Pacific Ocean and the San Francisco Bay.
Frankfurt University of Applied Science urkunde



Frankfurt University of Applied Science urkundeLisa Emerson
╠²
Duplicate Frankfurt University of Applied Science urkunde, make a Frankfurt UAS degree.Introduction to Safety, Health & Environment



Introduction to Safety, Health & Environmentssuserc606c7
╠²
Introduction to
Safety, Health &EnvironmentG8 mini project for alcohol detection and engine lock system with GPS tracki...



G8 mini project for alcohol detection and engine lock system with GPS tracki...sahillanjewar294
╠²
b.tech final year projects report for cseWater Industry Process Automation & Control Monthly - March 2025.pdf



Water Industry Process Automation & Control Monthly - March 2025.pdfWater Industry Process Automation & Control
╠²
Welcome to the March 2025 issue of WIPAC Monthly the magazine brought to you by the LinkedIn Group WIPAC Monthly.
In this month's edition, on top of the month's news from the water industry we cover subjects from the intelligent use of wastewater networks, the use of machine learning in water quality as well as how, we as an industry, need to develop the skills base in developing areas such as Machine Learning and Artificial Intelligence.
Enjoy the latest edition15. Smart Cities Big Data, Civic Hackers, and the Quest for a New Utopia.pdf



15. Smart Cities Big Data, Civic Hackers, and the Quest for a New Utopia.pdfNgocThang9
╠²
Smart Cities Big Data, Civic Hackers, and the Quest for a New UtopiaUS Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
╠²
Water Industry Process Automation & Control Monthly - March 2025.pdf



Water Industry Process Automation & Control Monthly - March 2025.pdfWater Industry Process Automation & Control
╠²
Seminar ppt on digital signature
- 1. Seminar on Digital Signature Prepared By: Jinkal Patel Enrollment No: 140580702005 Guide By : Prof. Ramesh Prajapati Saraswati College of Engineering Gujarat Technological University & Technology
- 2. Content ŌĆó Introduction ŌĆó What is Digital Signature??? ŌĆó Why Digital Signature??? ŌĆó Basic RequirementsŌĆ”. ŌĆó How the Technology Works ŌĆó Approaches ŌĆó Algorithm of Digital Signature ŌĆó Challenges and Opportunities ŌĆó Application ŌĆó Drawbacks ŌĆó Conclusion
- 3. INTRODUCTION ’é┤The authenticity of many legal, financial, and other documents is done by the presence or absence of an authorized handwritten signature. ’é┤ŌĆ£Digital SignatureŌĆØ is the best solution for authenticity in various fields. ’é┤A digital signature is nothing but an attachment to any piece of electronic information, which represents the content of the document and the identity of the owner of that document uniquely[5].
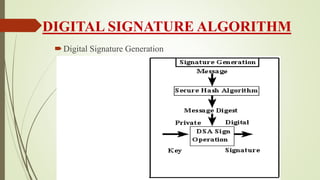
- 4. What is digital signature ’é┤Hash value of a message when encrypted with the private key of a person is his digital signature on that e-Document. ’é┤Digital Signature of a person therefore varies from document to document thus ensuring authenticity of each word of that document. ’é┤As the public key of the signer is known, anybody can verify the message and the digital signature.
- 5. Why Digital Signatures??? ’é┤To provide Authenticity, Integrity and Non-repudiation to electronic documents. ’é┤To use the Internet as the safe and secure medium for e-Commerce and e-Governance
- 6. BASIC REQUIREMENTSŌĆ”. ’é┤Private Key The private key is one which is accessible only to the signer. It is used to generate the digital signature which is then attached to the message.[2] ’é┤Public Key The public key is made available to all those who receive the signed messages from the sender. It is used for verification of the received message.[2]
- 7. BASIC REQUIREMENTSŌĆ” ’é┤ Digital Signature Certificate ’é┤A subscriber of the private key and public key pair makes the public key available to all those who are intended to receive the signed messages from the subscriber.[1] ’é┤ But in case of any dispute between the two sides, there must be some entity with the receiver which will allow the receiver of the message to prove that the message was sent by the subscriber of the key pair. This can be done with the Digital Signature Certificate.[1]
- 8. HOW THE TECHNOLOGY WORKS??
- 9. DIGITAL SIGNATURE ALGORITHM ’é┤Digital Signature Generation
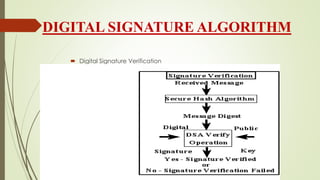
- 10. DIGITAL SIGNATURE ALGORITHM ’é┤ Digital Signature Verification
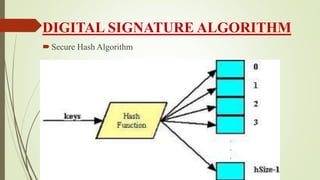
- 11. DIGITAL SIGNATURE ALGORITHM ’é┤Secure Hash Algorithm
- 12. Digital Signatures ’é┤I agree Efcc61c1c03db8d8ea8569545c073c814a0ed755 ’é┤My place of birth is at Gwalior. fe1188eecd44ee23e13c4b6655edc8cd5cdb6f25 ’é┤I am 62 years old. 0e6d7d56c4520756f59235b6ae981cdb5f9820a0 ’é┤I am an Engineer. ea0ae29b3b2c20fc018aaca45c3746a057b893e7 ’é┤I am a Engineer. 01f1d8abd9c2e6130870842055d97d315dff1ea3 ’é┤ These are digital signatures of same person on different documents
- 13. Paper Signatures v/s Digital Signatures Parameter Paper Electronic Authenticity May be forged Can not be copied Integrity Signature independent of the document Signature depends on the contents of the document Non- repudiation a. Handwriting expert needed b. Error prone a. Any computer user b. Error free
- 14. Challenges and Opportunities ’é┤ Institutional overhead: The cost of establishing and utilizing certification authorities, repositories, and other important services, as well as assuring quality in the performance of their functions. ’é┤Subscriber and Relying Party Costs: A digital signer will require software, and will probably have to pay a certification authority some price to issue a certificate. Hardware to secure the subscriber's private key may also be advisable.
- 15. APPLICATIONS ŌĆ”.. ’é┤ Electronic Mail ’é┤ Data storage ’é┤ Electronic funds transfer ’é┤ Software Distribution ’é┤ Smart Cards ’é┤ MITRENET ’é┤ ISDN ’é┤ Time Stamped Signature ’é┤ Blind Signatures
- 16. DRAWBACKS ’é┤The private key must be kept in a secured manner.[3] ’é┤The process of generation and verification of digital signature requires considerable amount of time.[3] ’é┤For using the digital signature the user has to obtain private and public key, the receiver has to obtain the digital signature certificate also.[3]
- 17. CONCLUSION Digital signatures are difficult to understand. Digital signatures will be championed by many players that the public distrusts, including national security agencies, law enforcement agencies, and consumer marketing companies.
- 18. References 1. https://en.m.wikipedia.org/wiki/Digital_Signature 2. www.google.com 3. www.computerfun4u.blogspot.com 4. www.slideshare.net 5. Cryptography & Network Security : Principal & Practise ,William Stallings








