Simple ams slidedeck
Download as pptx, pdf0 likes268 views
The document outlines Radware's Attack Mitigation System (AMS) and its capabilities in preventing various DDoS and application-layer attacks. It highlights features such as ASIC-based engines for high-volume attack protection, deep inspection, and behavioral analysis, along with support from a dedicated Security Operations Center. Radware's portfolio includes products designed for network and server attack prevention as well as web application firewalls.
1 of 11
Downloaded 13 times





Ad
Recommended
He m¨±rere me te haumarutanga
He m¨±rere me te haumarutangaranginui
?
This document discusses various computer hacking and security terms in te reo M¨ˇori, including:
1. M¨±rere - refers to hacking or a hacker. Several types of attacks are mentioned such as whakaeke p¨±reirei engaenga which is a buffer overflow attack.
2. Haumarutanga - security. The document notes how security can be breached through techniques like whakah¨tuhi whakawhiti pae or cross-site scripting.
3. Other terms discussed include whakakore ratonga (denial of service attack), p¨±kahatanga p¨ˇpori (social engineering), and hinu nakKaspersky security for virtualization light agent launch presentation
Kaspersky security for virtualization light agent launch presentationShapeBlue
?
Kaspersky Security for Virtualization - Light Agent provides antivirus and network protection for virtual environments like Microsoft Hyper-V and Citrix Xen without impacting performance. It uses a lightweight agent and separate security virtual machine to deeply scan individual VMs for malware while being scalable. A single license covers protection for both Hyper-V and Xen VMs through flexible per-machine or per-core licensing options.Refense Security Risk Briefing July 2009
Refense Security Risk Briefing July 2009apompliano
?
Refense provides vulnerability management and compliance checking for network infrastructure devices such as routers, switches, firewalls, and wireless access points. It uses a non-intrusive, agentless approach to conduct in-depth analysis of devices and identify vulnerabilities, configuration issues, and deviations from security policies. Refense offers both on-premise appliance and managed service options that are scalable, easy to implement, and provide comprehensive reporting and risk mitigation intelligence.DDoS Falcon_Tech_Specs-Haltdos
DDoS Falcon_Tech_Specs-HaltdosHaltdos
?
Haltdos Falcon is a high-performance DDoS protection solution utilizing AI for real-time attack detection and mitigation, significantly outperforming traditional hardware with latency under 60 microseconds. It provides comprehensive, multi-layered security against diverse DDoS attack types while ensuring seamless integration without requiring extensive IT expertise. Available in various deployment modes and featuring 24/7 support, Haltdos Falcon is designed to maintain business continuity and safeguard online services from increasingly sophisticated cyber threats.9 Steps For Fighting Against a DDos Attack in real-time
9 Steps For Fighting Against a DDos Attack in real-time Haltdos
?
The document outlines nine steps to combat DDoS attacks effectively in real-time, emphasizing the importance of identifying the attack type, prioritizing critical applications, and using IP whitelisting. It highlights advanced measures like blocking malicious IP addresses and enhancing application-level security, along with public relations strategies if the attack is publicly known. Organizations are urged to stay prepared for ongoing DDoS threats in the digital age.Radware Hybrid Cloud Web Application Firewall and DDoS Protection
Radware Hybrid Cloud Web Application Firewall and DDoS ProtectionAndy Ellis
?
The document describes Radware's hybrid cloud WAF service, which provides fully-managed web application and DDoS protection for enterprises with applications in both cloud and on-premise environments. The service uses Radware's security technologies to integrate cloud and on-premise defenses, providing comprehensive detection and mitigation of web attacks, SQL injections, cross-site scripting, and DDoS attacks across hybrid infrastructures. It offers three service tiers with varying levels of protection and management features to suit different customer needs.Introducing Kaspersky Security for Virtualization - Light Agent
Introducing Kaspersky Security for Virtualization - Light AgentKaspersky
?
The document discusses Kaspersky Security for Virtualization, detailing its role in protecting virtual environments by utilizing a light agent approach. It highlights the benefits of virtualization, common misconceptions about security in virtualized settings, and the comprehensive protection features offered by Kaspersky's solution. The solution aims to provide high-quality security management for enterprises and service providers within multi-hypervisor infrastructures, ensuring both performance and effective malware prevention.F5 - BigIP ASM introduction
F5 - BigIP ASM introductionJimmy Saigon
?
1) Traditional network security devices are limited in protecting applications from attacks, with web application firewalls (WAFs) like BIG-IP ASM providing more comprehensive protection against a wide range of vulnerabilities and attacks.
2) BIG-IP ASM protects applications from the OWASP top 10 vulnerabilities like injection, XSS, CSRF, and more, with features like automatic DOS detection and PCI compliance reporting.
3) The solution provides visibility into applications through monitoring and reporting on server latency and other metrics to help optimize performance and security.Trend micro v2
Trend micro v2JD Sherry
?
This document discusses how Trend Micro's Deep Security product provides virtualization and cloud security through an integrated platform. It offers agentless and agent-based security across physical, virtual, and cloud environments from a single management console. This consolidated security model maximizes performance and ROI while simplifying management and strengthening protection across platforms.AGILE SECURITY? Security for the Real World
AGILE SECURITY? Security for the Real WorldCisco Russia
?
Sourcefire provides an agile security solution through its network and endpoint security products. It offers comprehensive visibility across the network from devices to applications to threats. Sourcefire's adaptive security infrastructure includes the Sourcefire Defense Center for centralized management and the FireSIGHT technology which provides real-time awareness and automation. This intelligence enables automated tuning of defenses and efficient response to security events.What You Need To Know About The New PCI Cloud Guidelines
What You Need To Know About The New PCI Cloud GuidelinesCloudPassage
?
This document discusses key considerations for achieving PCI DSS compliance in public cloud environments. It outlines the scope of responsibility between cloud service providers (CSPs) and their customers, providing an example breakdown. It also provides a basic checklist for PCI compliance in the cloud and suggestions for limiting the scope of PCI controls. Incident response procedures and securing data throughout its lifecycle in the cloud are also addressed.RSA 2012 Virtualization Security February 2012
RSA 2012 Virtualization Security February 2012Symantec
?
Symantec and VMware have announced integrations to enhance security for virtual and cloud environments, addressing traditional and emerging risks such as targeted malware and poor visibility. The solutions include orchestrated prevention of data loss, improved compliance via centralized risk visibility, and comprehensive security measures that extend beyond antivirus. Key offerings include several Symantec products, real-time threat telemetry, and API integrations to bolster infrastructure and information security.HaltDos DDoS Protection Solution
HaltDos DDoS Protection SolutionHaltdos
?
Haltdos is India's first comprehensive DDoS mitigation solution designed to ensure that websites remain online and accessible amidst increasing cyber threats. It utilizes multi-layered protection and anomaly detection, differentiating itself from traditional firewalls and IPS by adapting automatically to various types of DDoS attacks without the need for human intervention. The startup, founded by a team with extensive security expertise, offers real-time metrics, customizable settings, and is geared towards maintaining business operations continuously.Preparing for the Imminent Terabit DDoS Attack
Preparing for the Imminent Terabit DDoS AttackImperva
?
The document discusses the growing threat of DDoS attacks and the need for resilient network protection. It notes that average attack sizes have grown to 10Gbps in 2013 and many recent attacks have exceeded 40Gbps. While botnets and open resolvers have not increased significantly, attackers are able to generate high volumes of traffic using a small number of "super resources." The document argues a terabit-level attack could occur within the next 1-3 years. It advocates for a cloud-based, scalable architecture with visibility across different asset types and rapid response capabilities. The document presents Incapsula as a solution offering application protection, DNS protection, and infrastructure protection against DDoS attacks.APARATO GENITAL MASCULINOOmar Calzada
?
El documento describe la anatom¨Şa y funci¨®n del aparato reproductor masculino. Incluye una descripci¨®n de los test¨Şculos, las v¨Şas esperm¨˘ticas como el epid¨Şdimo y los conductos deferentes, las gl¨˘ndulas anexas como las ves¨Şculas seminales y la pr¨®stata, y el pene. Explica que los test¨Şculos producen espermatozoides y la hormona testosterona, y que las estructuras asociadas almacenan y transportan los espermatozoides y fluidos durante la eyaculaci¨®n.Scarlet hope rev lb2 no video embed
Scarlet hope rev lb2 no video embedJoyBKY
?
Scarlet Hope is a mission that aims to bring hope and love of Jesus to women in the sex industry. It was started by Rachelle Starr who felt called by God to minister to those in a spiritually and physically difficult place. The sex industry is a massive global business that employs millions, often exploiting vulnerable people, especially women and children. Scarlet Hope delivers food to strip clubs weekly and helps women access resources to escape the industry by providing housing, education, childcare and other support.9935019
9935019chobits505
?
±ľĆÚÖĐ×÷ҵµÄÖ÷ĚâĘÇą«Ô°Ł¬ĚÖÂŰÁËą«Ô°Ŕď¸÷ŔŕČ˵ĻŁ¬°üŔ¨ŔĎČˡ˘ÄęÇáČËşÍСş˘µÄČŐłŁ»Ą¶ŻˇŁĂżÎ»łÉÔ±¶ĽÓиöČËÖ÷Ě⣬˛ĚÄݶ÷רעÓÚŔĎČËČşĚ塣Afghanistan telecompolicy english
Afghanistan telecompolicy englishmjaihu
?
The document provides Afghanistan's national telecommunications and internet policy. It aims to rapidly develop the country's telecommunications infrastructure through private sector participation, competition, and adoption of modern technologies. Key points include establishing an independent regulatory authority, corporatizing the state-owned telecom into Afghan Telecom with plans for privatization, introducing competition through additional licenses, and developing policies around licensed and unlicensed spectrum use. The overall goal is to stimulate economic growth and improve social services through affordable and widespread communications access.Miscellaneous legal terms domestic and foregin copy
Miscellaneous legal terms domestic and foregin copybearister2746
?
This document provides an overview of various legal business structures and terms used domestically and internationally. It discusses corporations, partnerships, limited liability companies, and other structures under U.S. law as well as civil law systems in countries like France and Germany. Key points covered include how corporations provide liability protection for shareholders, the different types of corporations, and similarities and differences in business structures and taxation between the U.S. and civil law countries.Connect & Create
Connect & CreateConnect & Create
?
Jeff S. Turnbull emphasizes the importance of authentic storytelling in creating connections and value, advocating for marketing strategies that are grassroots and unconventional. He highlights the role of personal touch and clear communication in effective marketing across various platforms, including social media. Turnbull invites others to collaborate and share stories to enhance their messaging strategies.µÚĘ®¶ţ˝M ¸ĐśyŃbÖĂ
µÚĘ®¶ţ˝M ¸ĐśyŃbÖĂchobits505
?
¸ĂÎĵµĂčĘöÁËŇ»¸öąĹĹ̽ĎŐÓÎĎ·µÄÁ÷łĚŁ¬É漰ͨąýĘÓƵ·ÖÎöŔ´˝âËřĎä×ÓşÍĂĹŇÔĚÓÍѡŁÍćĽŇĐčҪѡÔńŐýČ·µÄŃŐÉ«şÍĘý×ÖŁ¬ŇÔĽ°ÔÚ±ľ×ÓÉĎ»ć»ŇÔ»ńµĂÎďĆ·ˇŁ×îÖŐÄż±ęĘÇËłŔűÍęłÉĚÓÍѡŁ9935019
9935019chobits505
?
¸ĂÎĵµĘǶÔÓÚ¶Ż»±íŃÝĆÚÖĐ×÷ҵµÄ˝éÉÜŁ¬ÍŶÓÖ÷ĚâÎŞą«Ô°Ł¬ąŰ˛ěÁËą«Ô°ÄÚ˛»Í¬ČËČşµÄ»î¶ŻˇŁÍŶӳÉÔ±°üŔ¨ÁÖÂüćᢲĚÄݶ÷ˇ˘Ŕµ˛ŞÔ¨ˇ˘·¶Ü°ÓčşÍÁÖąÚÓÓˇŁ˛ĚÄݶ÷µÄ¸öČËÖ÷ĚâרעÓÚŔĎÄęČˡŁDSS ITSEC Conference 2012 - Radware - Protection from SSL DDOS Attacks
DSS ITSEC Conference 2012 - Radware - Protection from SSL DDOS AttacksAndris Soroka
?
This document discusses modern DDoS and SSL attacks and how Radware's Attack Mitigation System (AMS) protects against them. It summarizes that AMS can protect against network floods, SSL floods, and application floods through techniques like SYN cookies, signatures, and SSL mitigation. AMS also enables legal users to continue working during attacks by authenticating sources through techniques like TCP cookies and encrypted web cookie challenges. The system can mitigate SSL DDoS attacks without using legal SSL certificates. Case studies show AMS has successfully protected banks, retailers, and other organizations against multi-vector attacks.S series presentation
S series presentationSergey Marunich
?
This document discusses HP TippingPoint's IPS and virtualization security solutions for data centers. It provides an overview of the modern threat landscape facing applications, and introduces HP TippingPoint's IPS platform and product lines. Key details include the platform's performance capabilities, available models in the S-Series and N-Series, and the TippingPoint 1200N embedded IPS module for HP switches. Virtualization security solutions are also briefly mentioned.Cat6500 Praesentation
Cat6500 PraesentationSophan_Pheng
?
The document discusses the Cisco Catalyst 6500 and Firewall Services Module (FWSM). It notes the importance of data center security and protecting servers from attacks. The Cisco Catalyst 6500 delivers security through features like network admission control, identity-based networking, and intrusion prevention. It can consolidate security functions to reduce power consumption. The FWSM integrates firewall capabilities into the Cisco Catalyst 6500 and 7600 series switches in a high-performance module.CRENNO Technologies Network Consultancy & Session Border Controller Solut...
CRENNO Technologies Network Consultancy & Session Border Controller Solut...Erol TOKALACOGLU
?
CRENNO Technologies provides network security consultancy and sells Acme-Packet session border controllers (SBCs). The document outlines CRENNO's capabilities, including SBC components that provide denial of service protection, access control, topology hiding, fraud prevention, monitoring and reporting. It also summarizes CRENNO's consultancy and on-demand solutions, and concludes that as a telecommunications software company, CRENNO has expertise in both network infrastructure and software development using SBCs.Radware DefenseFlow-The SDN Application That Programs Networks for DoS Security
Radware DefenseFlow-The SDN Application That Programs Networks for DoS Security Radware
?
DDoS attacks are a significant threat to businesses, with many organizations experiencing multiple attacks annually. The document compares traditional NetFlow-based mitigation solutions with Radware's DefenseFlow, an SDN application that offers immediate attack detection and low-cost provisioning. DefenseFlow provides a scalable and efficient method for DDoS protection by diverting suspicious traffic and utilizing a streamlined detection process.Security model-of-sip-d2-05 at kishore
Security model-of-sip-d2-05 at kishoreAT Kishore
?
The document discusses the pervasive need for security, particularly within the Session Initiation Protocol (SIP) framework, highlighting Alcatel-Lucent's leadership in security innovations and its establishment of a CIA (Confidentiality, Integrity, Availability) model. It outlines various security trends, challenges, and specific measures for enhancing SIP security, including advanced encryption techniques and prioritization methods for message processing. The importance of maintaining an 'always on' security model for effective communication systems is emphasized throughout the discussion.Trend Micro - Targeted attacks: Have you found yours?
Trend Micro - Targeted attacks: Have you found yours?Global Business Events
?
The document discusses advanced persistent threats and how traditional security methods are insufficient for dealing with them. It introduces Trend Micro's Deep Discovery and custom defense solutions, which use specialized threat detection, deep analysis, threat intelligence, and adaptive security updates to detect and block targeted attacks. This is done by monitoring networks for malicious content and communications, analyzing behaviors, and gaining insights to rapidly respond to and remediate threats.Cisco tec chris young - security intelligence operations
Cisco tec chris young - security intelligence operationsCisco Public Relations
?
Cisco's Security Intelligence Operations (SIO) uses a global network of sensors and security researchers to detect threats. The SIO detects threats through analyzing data from over 1.6 million globally deployed devices and 75 terabytes of data received daily. It maintains a database called SensorBase that contains threat intelligence and telemetry data to provide context around potential threats. The SIO can then issue dynamic updates to security policies and signatures across Cisco's product line to block emerging threats in real-time.More Related Content
What's hot (6)
Trend micro v2
Trend micro v2JD Sherry
?
This document discusses how Trend Micro's Deep Security product provides virtualization and cloud security through an integrated platform. It offers agentless and agent-based security across physical, virtual, and cloud environments from a single management console. This consolidated security model maximizes performance and ROI while simplifying management and strengthening protection across platforms.AGILE SECURITY? Security for the Real World
AGILE SECURITY? Security for the Real WorldCisco Russia
?
Sourcefire provides an agile security solution through its network and endpoint security products. It offers comprehensive visibility across the network from devices to applications to threats. Sourcefire's adaptive security infrastructure includes the Sourcefire Defense Center for centralized management and the FireSIGHT technology which provides real-time awareness and automation. This intelligence enables automated tuning of defenses and efficient response to security events.What You Need To Know About The New PCI Cloud Guidelines
What You Need To Know About The New PCI Cloud GuidelinesCloudPassage
?
This document discusses key considerations for achieving PCI DSS compliance in public cloud environments. It outlines the scope of responsibility between cloud service providers (CSPs) and their customers, providing an example breakdown. It also provides a basic checklist for PCI compliance in the cloud and suggestions for limiting the scope of PCI controls. Incident response procedures and securing data throughout its lifecycle in the cloud are also addressed.RSA 2012 Virtualization Security February 2012
RSA 2012 Virtualization Security February 2012Symantec
?
Symantec and VMware have announced integrations to enhance security for virtual and cloud environments, addressing traditional and emerging risks such as targeted malware and poor visibility. The solutions include orchestrated prevention of data loss, improved compliance via centralized risk visibility, and comprehensive security measures that extend beyond antivirus. Key offerings include several Symantec products, real-time threat telemetry, and API integrations to bolster infrastructure and information security.HaltDos DDoS Protection Solution
HaltDos DDoS Protection SolutionHaltdos
?
Haltdos is India's first comprehensive DDoS mitigation solution designed to ensure that websites remain online and accessible amidst increasing cyber threats. It utilizes multi-layered protection and anomaly detection, differentiating itself from traditional firewalls and IPS by adapting automatically to various types of DDoS attacks without the need for human intervention. The startup, founded by a team with extensive security expertise, offers real-time metrics, customizable settings, and is geared towards maintaining business operations continuously.Preparing for the Imminent Terabit DDoS Attack
Preparing for the Imminent Terabit DDoS AttackImperva
?
The document discusses the growing threat of DDoS attacks and the need for resilient network protection. It notes that average attack sizes have grown to 10Gbps in 2013 and many recent attacks have exceeded 40Gbps. While botnets and open resolvers have not increased significantly, attackers are able to generate high volumes of traffic using a small number of "super resources." The document argues a terabit-level attack could occur within the next 1-3 years. It advocates for a cloud-based, scalable architecture with visibility across different asset types and rapid response capabilities. The document presents Incapsula as a solution offering application protection, DNS protection, and infrastructure protection against DDoS attacks.Viewers also liked (8)
APARATO GENITAL MASCULINOOmar Calzada
?
El documento describe la anatom¨Şa y funci¨®n del aparato reproductor masculino. Incluye una descripci¨®n de los test¨Şculos, las v¨Şas esperm¨˘ticas como el epid¨Şdimo y los conductos deferentes, las gl¨˘ndulas anexas como las ves¨Şculas seminales y la pr¨®stata, y el pene. Explica que los test¨Şculos producen espermatozoides y la hormona testosterona, y que las estructuras asociadas almacenan y transportan los espermatozoides y fluidos durante la eyaculaci¨®n.Scarlet hope rev lb2 no video embed
Scarlet hope rev lb2 no video embedJoyBKY
?
Scarlet Hope is a mission that aims to bring hope and love of Jesus to women in the sex industry. It was started by Rachelle Starr who felt called by God to minister to those in a spiritually and physically difficult place. The sex industry is a massive global business that employs millions, often exploiting vulnerable people, especially women and children. Scarlet Hope delivers food to strip clubs weekly and helps women access resources to escape the industry by providing housing, education, childcare and other support.9935019
9935019chobits505
?
±ľĆÚÖĐ×÷ҵµÄÖ÷ĚâĘÇą«Ô°Ł¬ĚÖÂŰÁËą«Ô°Ŕď¸÷ŔŕČ˵ĻŁ¬°üŔ¨ŔĎČˡ˘ÄęÇáČËşÍСş˘µÄČŐłŁ»Ą¶ŻˇŁĂżÎ»łÉÔ±¶ĽÓиöČËÖ÷Ě⣬˛ĚÄݶ÷רעÓÚŔĎČËČşĚ塣Afghanistan telecompolicy english
Afghanistan telecompolicy englishmjaihu
?
The document provides Afghanistan's national telecommunications and internet policy. It aims to rapidly develop the country's telecommunications infrastructure through private sector participation, competition, and adoption of modern technologies. Key points include establishing an independent regulatory authority, corporatizing the state-owned telecom into Afghan Telecom with plans for privatization, introducing competition through additional licenses, and developing policies around licensed and unlicensed spectrum use. The overall goal is to stimulate economic growth and improve social services through affordable and widespread communications access.Miscellaneous legal terms domestic and foregin copy
Miscellaneous legal terms domestic and foregin copybearister2746
?
This document provides an overview of various legal business structures and terms used domestically and internationally. It discusses corporations, partnerships, limited liability companies, and other structures under U.S. law as well as civil law systems in countries like France and Germany. Key points covered include how corporations provide liability protection for shareholders, the different types of corporations, and similarities and differences in business structures and taxation between the U.S. and civil law countries.Connect & Create
Connect & CreateConnect & Create
?
Jeff S. Turnbull emphasizes the importance of authentic storytelling in creating connections and value, advocating for marketing strategies that are grassroots and unconventional. He highlights the role of personal touch and clear communication in effective marketing across various platforms, including social media. Turnbull invites others to collaborate and share stories to enhance their messaging strategies.µÚĘ®¶ţ˝M ¸ĐśyŃbÖĂ
µÚĘ®¶ţ˝M ¸ĐśyŃbÖĂchobits505
?
¸ĂÎĵµĂčĘöÁËŇ»¸öąĹĹ̽ĎŐÓÎĎ·µÄÁ÷łĚŁ¬É漰ͨąýĘÓƵ·ÖÎöŔ´˝âËřĎä×ÓşÍĂĹŇÔĚÓÍѡŁÍćĽŇĐčҪѡÔńŐýČ·µÄŃŐÉ«şÍĘý×ÖŁ¬ŇÔĽ°ÔÚ±ľ×ÓÉĎ»ć»ŇÔ»ńµĂÎďĆ·ˇŁ×îÖŐÄż±ęĘÇËłŔűÍęłÉĚÓÍѡŁ9935019
9935019chobits505
?
¸ĂÎĵµĘǶÔÓÚ¶Ż»±íŃÝĆÚÖĐ×÷ҵµÄ˝éÉÜŁ¬ÍŶÓÖ÷ĚâÎŞą«Ô°Ł¬ąŰ˛ěÁËą«Ô°ÄÚ˛»Í¬ČËČşµÄ»î¶ŻˇŁÍŶӳÉÔ±°üŔ¨ÁÖÂüćᢲĚÄݶ÷ˇ˘Ŕµ˛ŞÔ¨ˇ˘·¶Ü°ÓčşÍÁÖąÚÓÓˇŁ˛ĚÄݶ÷µÄ¸öČËÖ÷ĚâרעÓÚŔĎÄęČˡŁAd
Similar to Simple ams slidedeck (20)
DSS ITSEC Conference 2012 - Radware - Protection from SSL DDOS Attacks
DSS ITSEC Conference 2012 - Radware - Protection from SSL DDOS AttacksAndris Soroka
?
This document discusses modern DDoS and SSL attacks and how Radware's Attack Mitigation System (AMS) protects against them. It summarizes that AMS can protect against network floods, SSL floods, and application floods through techniques like SYN cookies, signatures, and SSL mitigation. AMS also enables legal users to continue working during attacks by authenticating sources through techniques like TCP cookies and encrypted web cookie challenges. The system can mitigate SSL DDoS attacks without using legal SSL certificates. Case studies show AMS has successfully protected banks, retailers, and other organizations against multi-vector attacks.S series presentation
S series presentationSergey Marunich
?
This document discusses HP TippingPoint's IPS and virtualization security solutions for data centers. It provides an overview of the modern threat landscape facing applications, and introduces HP TippingPoint's IPS platform and product lines. Key details include the platform's performance capabilities, available models in the S-Series and N-Series, and the TippingPoint 1200N embedded IPS module for HP switches. Virtualization security solutions are also briefly mentioned.Cat6500 Praesentation
Cat6500 PraesentationSophan_Pheng
?
The document discusses the Cisco Catalyst 6500 and Firewall Services Module (FWSM). It notes the importance of data center security and protecting servers from attacks. The Cisco Catalyst 6500 delivers security through features like network admission control, identity-based networking, and intrusion prevention. It can consolidate security functions to reduce power consumption. The FWSM integrates firewall capabilities into the Cisco Catalyst 6500 and 7600 series switches in a high-performance module.CRENNO Technologies Network Consultancy & Session Border Controller Solut...
CRENNO Technologies Network Consultancy & Session Border Controller Solut...Erol TOKALACOGLU
?
CRENNO Technologies provides network security consultancy and sells Acme-Packet session border controllers (SBCs). The document outlines CRENNO's capabilities, including SBC components that provide denial of service protection, access control, topology hiding, fraud prevention, monitoring and reporting. It also summarizes CRENNO's consultancy and on-demand solutions, and concludes that as a telecommunications software company, CRENNO has expertise in both network infrastructure and software development using SBCs.Radware DefenseFlow-The SDN Application That Programs Networks for DoS Security
Radware DefenseFlow-The SDN Application That Programs Networks for DoS Security Radware
?
DDoS attacks are a significant threat to businesses, with many organizations experiencing multiple attacks annually. The document compares traditional NetFlow-based mitigation solutions with Radware's DefenseFlow, an SDN application that offers immediate attack detection and low-cost provisioning. DefenseFlow provides a scalable and efficient method for DDoS protection by diverting suspicious traffic and utilizing a streamlined detection process.Security model-of-sip-d2-05 at kishore
Security model-of-sip-d2-05 at kishoreAT Kishore
?
The document discusses the pervasive need for security, particularly within the Session Initiation Protocol (SIP) framework, highlighting Alcatel-Lucent's leadership in security innovations and its establishment of a CIA (Confidentiality, Integrity, Availability) model. It outlines various security trends, challenges, and specific measures for enhancing SIP security, including advanced encryption techniques and prioritization methods for message processing. The importance of maintaining an 'always on' security model for effective communication systems is emphasized throughout the discussion.Trend Micro - Targeted attacks: Have you found yours?
Trend Micro - Targeted attacks: Have you found yours?Global Business Events
?
The document discusses advanced persistent threats and how traditional security methods are insufficient for dealing with them. It introduces Trend Micro's Deep Discovery and custom defense solutions, which use specialized threat detection, deep analysis, threat intelligence, and adaptive security updates to detect and block targeted attacks. This is done by monitoring networks for malicious content and communications, analyzing behaviors, and gaining insights to rapidly respond to and remediate threats.Cisco tec chris young - security intelligence operations
Cisco tec chris young - security intelligence operationsCisco Public Relations
?
Cisco's Security Intelligence Operations (SIO) uses a global network of sensors and security researchers to detect threats. The SIO detects threats through analyzing data from over 1.6 million globally deployed devices and 75 terabytes of data received daily. It maintains a database called SensorBase that contains threat intelligence and telemetry data to provide context around potential threats. The SIO can then issue dynamic updates to security policies and signatures across Cisco's product line to block emerging threats in real-time.Ixia anue maximum roi from your existing toolsets
Ixia anue maximum roi from your existing toolsetsresponsedatacomms
?
The Anue 5200 Net Tool Optimizer from Ixia helps maximize ROI from existing network monitoring tools by improving network visibility, optimizing tool utilization, and boosting staff productivity. It extends network monitoring coverage and scales to high-density and 40G networks while allowing expensive tools to monitor faster links. This reduces tool costs and overhead while simplifying monitoring. It also adds security by controlling access between core devices and tools.Ixia anue maximum roi from your existing toolsets
Ixia anue maximum roi from your existing toolsetsresponsedatacomms
?
The Anue 5200 Net Tool Optimizer from Ixia provides:
1) Increased network visibility for security and monitoring tools by addressing lack of SPAN ports and network segments.
2) Reduced tool costs by allowing expensive tools to monitor high speed networks and eliminating duplicate tools.
3) Increased staff productivity by simplifying monitoring setup and reducing troubleshooting time.Targeted Attacks: Have you found yours?
Targeted Attacks: Have you found yours?Trend Micro (EMEA) Limited
?
The document discusses the inadequacy of traditional security measures against advanced and targeted attacks on enterprise networks, where over 90% contain active malware. It highlights the importance of a customized defense approach using advanced threat detection methods, real-time analysis, and contextual threat intelligence. The document also emphasizes the need for organizations to adopt a layered security strategy to effectively prevent and respond to sophisticated cyber threats.Securing UC Borders with Acme Packet
Securing UC Borders with Acme PacketAcmePacket
?
The document discusses the security challenges and threats associated with unified communications (UC), specifically focusing on the vulnerabilities of IP networks which have become significant targets for cybercrime. It emphasizes the need for robust security measures, such as Session Border Controllers (SBC), to protect against various attacks like fraud, service theft, and eavesdropping, while ensuring interoperability and compliance. The summary concludes with a holistic approach to security, encompassing physical, data, host security, disaster recovery, and internal controls to safeguard communication infrastructures.Next Generation Security
Next Generation Securityneoma329
?
Next Generation Security
- Evolution of network security technologies from basic firewalls to next generation firewalls (NGFW) and next generation intrusion prevention systems (NGIPS) that provide advanced capabilities like application awareness, user awareness, and context awareness.
- NGFWs provide integrated firewall, IPS, and other features to control access at the application and user level rather than just the network/port level. NGIPS builds on IPS with application/context awareness to more accurately assess and respond to threats.
- Context awareness in particular enhances security by providing additional network intelligence and situational awareness to make better response decisions with fewer false alarms. The future of security emphasizes continued convergence through features like expanded awareness capabilities and centralized managementEndpoint Protection
Endpoint ProtectionSophos
?
This document summarizes the key endpoint protection capabilities provided by Sophos, including:
- Securing endpoints against threats like malware, ransomware and data loss across applications, web, email and devices.
- Active protection technologies that use machine learning to identify emerging threats in real-time.
- Features like intrusion prevention, firewall, encryption and patch management to harden security.
- Centralized management console for deploying and maintaining protection across all endpoints and platforms with minimal complexity and user impact.Get the Most From Your Firewall
Get the Most From Your FirewallSophos
?
The document discusses the evolution and current capabilities of firewalls in response to changing technology, threats, and work environments. It emphasizes the importance of Unified Threat Management (UTM) solutions, like those offered by Sophos, to provide comprehensive protection across various areas such as endpoint, web, and email security. Additionally, it highlights the need for modern firewalls to address emerging security challenges while maintaining visibility and control over data protection.Targeted Attacks: Have you found yours?
Targeted Attacks: Have you found yours?Trend Micro (EMEA) Limited
?
The document discusses advanced persistent threats and how traditional security methods are insufficient for dealing with them. It introduces Deep Discovery as a solution that provides specialized threat detection across the attack sequence through analyzing malicious content, suspect communications, and attack behaviors. Deep Discovery uses automated analysis, threat intelligence, and sandboxing to detect customized attacks and provides security updates, attack analysis and intelligence, and context-relevant views to guide rapid remediation responses.PCTY 2012, Threat landscape and Security Intelligence v. Michael Andersson
PCTY 2012, Threat landscape and Security Intelligence v. Michael AnderssonIBM Danmark
?
IBM's X-Force research team analyzes security threats and develops new technologies to address emerging challenges, such as the rise of targeted attacks and mobile malware. The document highlights findings from IBM's 2011 X-Force Trend and Risk Report, including increases in shell command injection and SSH brute forcing attacks as well as growth in phishing-based malware. It also introduces IBM's Advanced Threat Protection Platform for integrated security intelligence through solutions like the QRadar SIEM and IBM Security Network IPS powered by X-Force research.DSS ITSEC Conference 2012 - SIEM Q1 Labs IBM Security Systems Intelligence
DSS ITSEC Conference 2012 - SIEM Q1 Labs IBM Security Systems IntelligenceAndris Soroka
?
IBM Security Systems provides innovative security solutions from leading technology vendors in over 10 countries. They specialize in security consulting, testing, auditing, integration, training and support. They were the first certified partner of Q1 Labs in the Baltics, and now work with IBM's security portfolio. The document discusses the need for security intelligence solutions that integrate log management, security information and event management, risk management, network activity monitoring, and other capabilities to provide comprehensive security insights.Mcafee ips nsp-2011
Mcafee ips nsp-2011Luluk Kristiawan
?
The document discusses McAfee's Global Network Protection and Network Intrusion Prevention capabilities. It introduces McAfee's Network Security Platform, which provides cutting-edge network IPS, integration with McAfee's security portfolio, and vulnerability-based threat protection. The platform offers benefits such as best-in-class protection, high performance for networks up to 10Gbps, and scalability to protect global networks.Arrow ECS IBM Partner Jam - Security Update - Vicki Cooper - IBM
Arrow ECS IBM Partner Jam - Security Update - Vicki Cooper - IBMArrow ECS UK
?
IBM Security Systems provides concise summaries of security-related documents in 3 sentences or less:
IBM Security Systems hosted an event on July 17th 2012 to discuss the changing security landscape with security leaders and IBM's vision and products for threat protection. The document outlines IBM's approach to holistic security through intelligence and outlines the business partner program to help partners identify, sell, and fulfill security opportunities. It provides an overview of IBM's security portfolio breadth and expertise in research, integration, and management to help organizations address a complex security environment.Ad
Recently uploaded (20)
AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
?
AI VIDEO MAGAZINE - r/aivideo community newsletter ¨C Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdf
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdfbiswajitbanerjee38
?
Russia is one of the most aggressive nations when it comes to state coordinated cyberattacks?ˇŞ?and Ukraine has been at the center of their crosshairs for 3 years. This report, provided the State Service of Special Communications and Information Protection of Ukraine contains an incredible amount of cybersecurity insights, showcasing the coordinated aggressive cyberwarfare campaigns of Russia against Ukraine.
It brings to the forefront that understanding your adversary, especially an aggressive nation state, is important for cyber defense. Knowing their motivations, capabilities, and tactics becomes an advantage when allocating resources for maximum impact.
Intelligence shows Russia is on a cyber rampage, leveraging FSB, SVR, and GRU resources to professionally target UkraineˇŻs critical infrastructures, military, and international diplomacy support efforts.
The number of total incidents against Ukraine, originating from Russia, has steadily increased from 1350 in 2021 to 4315 in 2024, but the number of actual critical incidents has been managed down from a high of 1048 in 2022 to a mere 59 in 2024?ˇŞ?showcasing how the rapid detection and response to cyberattacks has been impacted by UkraineˇŻs improved cyber resilience.
Even against a much larger adversary, Ukraine is showcasing outstanding cybersecurity, enabled by strong strategies and sound tactics. There are lessons to learn for any enterprise that could potentially be targeted by aggressive nation states.
Definitely worth the read!Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
?
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.Crypto Super 500 - 14th Report - June2025.pdf
Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod
?
This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance
?
FIDO Seminar: Evolving Landscape of Post-Quantum CryptographySecuring Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
?
Securing Account Lifecycles in the Age of DeepfakesFrom Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
?
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnˇŻt yielding any results, so I expanded my search to second-hand dealer sitesˇŞonly to realise that periodically checking each one was going to be tedious. ThatˇŻs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformˇŻs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IˇŻll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canˇŻt buy a car for youˇŞyetˇŞit can certainly help you find the one youˇŻre after!Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
?
şÝşÝߣ deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025The Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu
?
A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!Techniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash
?
Techniques for Automatic Device Identification and Network AssignmentSecurity Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
?
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash
?
10 Key Challenges for AI within the EU Data Protection FrameworkYou are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
?
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
?
?????:???? ???? & ????? ???? ?????? ??? ???> https://pcprocore.com/ ??
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itˇŻs no wonder why aspiring videographers are turning to this software for their projects.PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
?
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table."Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
?
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
?
Coordinated Disclosure for ML - What's Different and What's the SameYou are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
?
Simple ams slidedeck
- 1. ˇ.the most effective Attack Mitigation System ?A Short intro to AMS and DefensePro
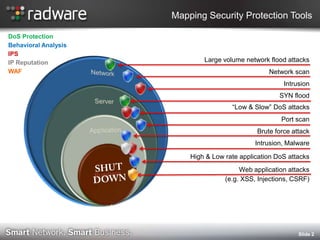
- 2. Mapping Security Protection Tools DoS Protection Behavioral Analysis IPS IP Reputation Large volume network flood attacks WAF Network scan Intrusion SYN flood ˇ°Low & Slowˇ± DoS attacks Port scan Brute force attack Intrusion, Malware High & Low rate application DoS attacks Web application attacks (e.g. XSS, Injections, CSRF) şÝşÝߣ 2
- 3. Introducing Radware Attack Mitigation System
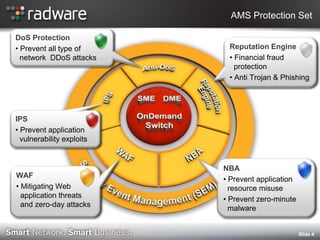
- 4. AMS Protection Set DoS Protection ? Prevent all type of Reputation Engine network DDoS attacks ? Financial fraud protection ? Anti Trojan & Phishing IPS ? Prevent application vulnerability exploits NBA WAF ? Prevent application ? Mitigating Web resource misuse application threats ? Prevent zero-minute and zero-day attacks malware şÝşÝߣ 4
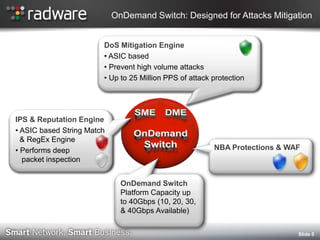
- 5. OnDemand Switch: Designed for Attacks Mitigation DoS Mitigation Engine ? ASIC based ? Prevent high volume attacks ? Up to 25 Million PPS of attack protection IPS & Reputation Engine ? ASIC based String Match & RegEx Engine ? Performs deep NBA Protections & WAF packet inspection OnDemand Switch Platform Capacity up to 40Gbps (10, 20, 30, & 40Gbps Available) şÝşÝߣ 5
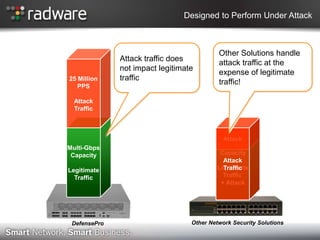
- 6. Designed to Perform Under Attack Other Solutions handle Attack traffic does attack traffic at the not impact legitimate expense of legitimate 25 Million traffic PPS traffic! Attack Traffic Attack Attack Multi-Gbps Multi-Gbps Capacity Capacity Attack Legitimate Legitimate Traffic Traffic Traffic + Attack DefensePro Other Network Security Solutions
- 7. DefensePro Layers of Defense DME Multi Purpose Multi Cores CPUˇŻs L7 Regex DDoS Mitigation Engine Acceleration ASIC (Up to 40 Gbps) (25M PPS) & Reputation Engine Behavioral-based protections Hardware Architecture ¨C Tailored for Attack Mitigation şÝşÝߣ
- 8. Radware AMS & ERT/SOC ? Security Operations Center (SOC) ¨C Provides weekly and emergency signature updates ¨C Maintains on-going application vulnerability protection ? Emergency Response Team (ERT) ¨C Provide 24x7 service for customers under attack ¨C Neutralize DoS/DDoS attacks and malware outbreaks şÝşÝߣ 8
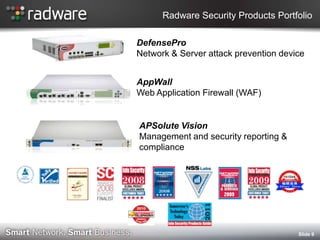
- 9. Radware Security Products Portfolio DefensePro Network & Server attack prevention device AppWall Web Application Firewall (WAF) APSolute Vision Management and security reporting & compliance şÝşÝߣ 9
- 10. PayPal proof şÝşÝߣ 10