MitM on USB -- Introduction of USBProxy --
- 1. MitM on USB Introduction of USBProxy ĪĪĪĪĪĪż½żķż▄(kalab1998{e}) 2014─Ļ10į┬31╚š Ą┌22╗žĪĖź═ź├ź╚ź’®`ź»źčź▒ź├ź╚ż“šiżÓ╗߯©üóŻ®Ī╣ 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 1
- 2. Self Introduction Ī± An engineer of a software company in Aizuwakamatsu (until next Feb., and will not update) Ī± I'm looking for a next job very hard. Ī± I will found an independent researcher Ī░KA-LABĪ▒ (It's the second choice if no one employ me). Ī± I have no released open source software. Ī± I have two projects on github as follows. ©C USBProxy is forked from dominicgs/USBProxy ©C Żļalas is a BLAS on GPGPU for Huge MatrixĪĪ 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 2
- 3. Is USB a computer network? YES! USB is a computer network 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 3
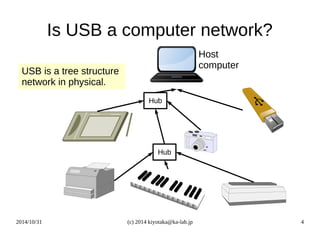
- 4. Is USB a computer network? Hub Hub USB is a tree structure network in physical. Host computer 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 4
- 5. Is USB a computer networkŻ┐ USB is one by one connections from the host to each device in logical. Host computer 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 5
- 6. How to communicate on USB? Case: Device to Host 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 6
- 7. How to communicate on USB? Case: Host to Device 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 7
- 8. Where is the host computer? Now a days, increasing such connections. Are there host computers? Ī∙Vector Graphics has copyright of this navigation icon. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 8
- 9. Which devices are the host? hhoosstt host Ī∙Vector Graphics has copyright of this navigation icon. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 9
- 10. We have an important problem. How do we investigate vulnerabilities of such devices without any laptop? Ī± Hack devices such cameras, printers, navigators, smartphones and so on. ?It's usually very difficult. Ī± Electrical tap on the USB cable. ?Next slides. Ī± Develop a USB Man in the Middle device. ?Main theme for this presentation. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 10
- 11. Electrical tapping on USB http://hackaday.com/2011/03/16/usb-man-in-the-middle-adapter/ 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 11
- 12. Electrical tapping on USB It's very easy, but it has some big problems. Ī± Conflicting signals Ī± Not enough electric power on signal lines Ī± Very weak against electrical noises Ī± Not running on USB2.0 by that specification 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 12
- 13. dominicgs/USBProxy Ī± The device must have two USB ports. ©C One is for connecting a host. ©C Another is for connecting a device. Ī± Software relaying Ī± Connectable USB2.0 Ī± Sniffable / Filterable / Injectable Ī± Very cheap, BeagleBone Black is about $60.0 Ī± https://github.com/dominicgs/USBProxy 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 13
- 14. USBProxy Structure 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 14
- 15. How to relay? Ī± USBProxy makes 6 kinds of threads runninng. ©C Reader for Input EP, ©C Reader for output EP, ©C Writer for Input EP, ©C Writer for Output EP, ©C Injection, ©C Filter 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 15
- 16. Connection Reader and Writer 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 16
- 17. Relay from device to host Ī± Reader for Input EP always requests data to the Endpoint on the device. Ī± Reader for Input EP send data to Writer for Input EP when it got data. Ī± Writer for Input EP sends data to the host. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 17
- 18. Relay from host to device Ī± Reader for Output EP always wait a request and data from the host. Ī± Reader for Output EP send data to Writer for Output EP when it got data. Ī± Writer for Output EP sends data to the Endpoint on the device. That's it. Very rough. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 18
- 19. Notification! Ī± USBProxy does not simulate the USB line. Ī± It just simulates endpoints on only one device. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 19
- 20. We have problems yet Ī± We want to simulate more devices. Ī± In many cases, it fail to simulate a device. Ī± It can't handle some complex devices yet. Ī± Linux lose endpoints on a device sometimes. Ī± It can't notice reset signal from a device. Ī± Very slow. ©C Original speed is 30.7MB/s, ©C USBProxy relay speed is 1,9MB/s. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 20
- 21. Other solutions Ī± If you want to just snif on USB, you can use USB protocol analizer such the Beagle USB480 Power. Ī± If you are interesting in deep side, maybe you will fall in darkness. 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 21
- 22. Beagle USB480 Power Ī± Easy to use Ī± Very fast, 29.8MB/s Ī± Cheap, just $2250.0 Ī± Another device is enable USB3.0, just $3600.0 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 22
- 23. Do you want to fall in darkness? Ī± Kali Linux NetHunter "Bad USB" MITM Attack Ī± http://vimeo.com/106065667 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 23
- 24. White page 2014/10/31 (c) 2014 kiyotaka@ka-lab.jp 24