SNA of M2M Organisations
Download as pptx, pdf0 likes442 views
This document discusses social network analysis (SNA) and its application to analyzing relationships between organizations in the machine-to-machine (M2M) sector. It defines key SNA concepts like nodes, ties, and centrality measures. It also outlines benefits of SNA like identifying influential actors, and limitations such as difficulties collecting all relationship data. Visualizations of sample M2M networks show operators have highest degree centrality while application providers have highest closeness centrality. SNA provides a framework for describing complex networks but has limitations like not capturing relationship attributes or motives.
1 of 8
Download to read offline

![Five things to first consider about SNA
3
1. The first endeavour should always be to define what the Nodes and Ties mean.[2] For
our M2M analysis, the nodes are organisations and ties are contractual relationships.
2. Nodes can have different weightings of importance, e.g.
ŌĆō Size (revenue/subscribers)
ŌĆō Geography
ŌĆō Track record
ŌĆō Associations
ŌĆō Other segmentation attributes
3. Ties have characteristics that matter when it comes to identifying things like leadership,
influence and strength e.g.
ŌĆō Direction (one-way, both)
ŌĆō Quantity
ŌĆō Contract date
ŌĆō Value
ŌĆō Frequency
4. Matrix, graphs and other visualization tools are important for analysis and measurement.
ŌĆō Tools like NodeXL will be required for any network of reasonable size
ŌĆō Considerable time is usually required to capture and keep the data up to date.
ŌĆō The M2M example in later slides shows just a few of the tens of thousands of Enterprises, 200+ Operators &
300+ Application Providers that Jasper, Vodafone & Ericsson have as M2M partners!
5. The perspective of the analysis can centre on the complete network (socio) or an
individuals personal network (ego).](https://image.slidesharecdn.com/snaofm2morganisations-130527190612-phpapp01/85/SNA-of-M2M-Organisations-3-320.jpg)
![Visualization[3] can also reveal positional relationships
ŌĆó Operators have the highest degree
centrality. AT&T is most central of the
operators and is the longest established
with largest customer base.
ŌĆó Application Providers have the highest
closeness centrality. They work with
multiple operators but rarely direct with
Enterprise customers.
ŌĆó Device/SIM and Platform Providers are
structurally equivalent nodes.
ŌĆó System Integrators are the most peripheral,
having the smallest number of connections.
ŌĆó Enterprise Customers has the highest
betweeness centrality providing the only
path to System Integrations
ŌĆó No groups of nodes are connected to each
other (cliques). However if the definition of
ties were extended beyond ŌĆścontractualŌĆÖ
then informal or personal relationships
would show all nodes in this extracted view
as being connected.
Operators
Enterprise Customers
Device/SIM
Application Providers
Platform
System Integrators
5](https://image.slidesharecdn.com/snaofm2morganisations-130527190612-phpapp01/85/SNA-of-M2M-Organisations-5-320.jpg)
![Benefits & Limitations of SNA
Benefits Limitations
Provides framework to describe any complex
network.
Collecting and maintaining source data can be
difficult
Identifies important individuals and the influence
they have
Does not describe meanings, motives or explain
why actions happen, e.g. why a contract was won.
A typological analysis is more suitable.
Can identify previously unrecognised sub-groups
through visual clusters
Little examination of important attributes such as
attitudes, opinions and behaviours that may be
helping or hindering relationships
Highlights areas for further inquiry and possible
improvement, e.g. gaps
More sensitive to data omissions than other
surveys. >75% sampling is required.[4]
Even weak ties may be revealed as important for
bridging disparate groups
Privacy can be ignored when views of others
contribute to the analysis.
Useful for track changes over time to reveal paths. Visualization can lead to over simplification and
misreading of results. E.g. Network measures such
as density can be easily misrepresented when
networks of different sizes are compared.
6](https://image.slidesharecdn.com/snaofm2morganisations-130527190612-phpapp01/85/SNA-of-M2M-Organisations-6-320.jpg)

![References
[1] Wellman B, Berkowitz SD (1977). Social structures: a network approach. Greenwich: JAI Press.
[2] Pinheiro, C. (2011). Social Network Analysis in Telecommunications. John Wiley & Sons.
[3] Based on Davies R (2011). Network Visualisation and Analysis, Cambridge.
[4] Borgatti, Carley & Krackhardt (2006).
8](https://image.slidesharecdn.com/snaofm2morganisations-130527190612-phpapp01/85/SNA-of-M2M-Organisations-8-320.jpg)
Ad
Recommended
Types of communication networks
Types of communication networksDamaashaad
╠²
The document discusses the history and evolution of computer networks from early standalone computers in the 1970s-80s to today's internet-connected world. It describes how the ARPANET in 1969 first linked two computers, pioneering network technology. Over time, networks expanded to connect people globally through the internet. The document then defines what a computer network is, describing the basic requirements of at least two connected computers, servers, clients, networking hardware and software. It also outlines common network types including LAN, WAN, VPN, MAN and CAN, as well as network topologies like star, bus, ring and tree configurations. Finally, it introduces the ISO/OSI 7-layer model for standardizing network communication.Subscriber Churn Prediction Model using Social Network Analysis In Telecommun...
Subscriber Churn Prediction Model using Social Network Analysis In Telecommun...BAINIDA
╠²
The document discusses the application of social network analysis (SNA) in predicting subscriber churn in the telecommunications industry, emphasizing the need for understanding customer behavior through interconnected relationships. It outlines basic concepts of SNA, including the importance of identifying influential users within networks and various centrality measures. The presentation details how SNA can enhance traditional marketing approaches by analyzing information exchange dynamics among customers in social networks.An innovative approach to solve the network design problem concerning intelli...
An innovative approach to solve the network design problem concerning intelli...alienaimi
╠²
This research proposes a novel methodology for designing robust transportation networks that consider the vulnerabilities from intelligent adversaries seeking to exploit weak points. By incorporating a multi-level optimization approach that includes the designer, adversary, and users, the study demonstrates how strategic investment can enhance both network performance and safety against disruptions. Numerical experiments validate the proposed model's effectiveness in improving network resilience and system-wide performance measures.Graph Theoretic Model for Community Wireless Networks
Graph Theoretic Model for Community Wireless NetworksABDELAAL
╠²
This document proposes a graph theoretic model for analyzing and designing community wireless networks (CWNs). It models a CWN as two graphs: a social graph representing community stakeholders and their relationships, and a wireless graph representing the technical network. Node and edge attributes in these graphs capture social, economic, and technical factors. This allows quantification of stakeholder contributions and benefits, and informs decisions around network implementation and operation. The model provides a framework to study CWNs as complex socio-technical systems and solve related problems.Routing and Security Issues for Trust Based Framework in Mobile Ad Hoc Networks
Routing and Security Issues for Trust Based Framework in Mobile Ad Hoc Networksiosrjce
╠²
The document discusses the vulnerabilities and challenges of routing and security in Mobile Ad Hoc Networks (MANETs), emphasizing the importance of trust-based frameworks. It highlights issues such as the dynamic nature of nodes, the need for secure routing protocols, and the challenges in establishing trust among nodes without centralized authority. The paper reviews existing research and proposes the necessity for robust trust models to enhance the functionality and security of MANETs.Opportunistic mobile social networks: architecture, privacy, security issues ...
Opportunistic mobile social networks: architecture, privacy, security issues ...IJECEIAES
╠²
The document discusses opportunistic mobile social networks (OMSN), a technology that enables mobile users to communicate without the internet, highlighting its architecture, privacy, and security challenges. It contrasts OMSN with traditional mobile social networks, emphasizing the importance of addressing privacy and security issues, which remain inadequately solved. The paper also explores future research directions to enhance data routing security and manage user participation effectively.Intelligent Agents in Telecommunications
Intelligent Agents in TelecommunicationsIJCSIS Research Publications
╠²
The document discusses the application of intelligent agents in telecommunications, emphasizing their role in enhancing the operation and management of complex telecommunication networks. It highlights the need for automated systems to manage various network components without significant human intervention and reviews recent applications of Distributed Artificial Intelligence (DAI) in improving network design, control, and service management. Various case studies illustrate how DAI techniques have been implemented to address specific challenges in telecommunications, such as fault management and service provisioning.Comprehensive Analysis on the Vulnerability and Efficiency of P2P Networks un...
Comprehensive Analysis on the Vulnerability and Efficiency of P2P Networks un...ijp2p
╠²
The document analyzes the vulnerability and efficiency of peer-to-peer (P2P) networks under static failures and targeted attacks, emphasizing the necessity for resilience to faults and threats. It presents methods for evaluating P2P networks' reliability and robustness through simulation, focusing on their capacity to endure random and targeted node removals. The findings aim to enhance the understanding of P2P systems' structural integrity and propose strategies for maintaining performance during attacks or failures.Application Of Distributed AI And Cooperative Problem Solving To Telecommunic...
Application Of Distributed AI And Cooperative Problem Solving To Telecommunic...Claudia Acosta
╠²
This document discusses applying distributed artificial intelligence (DAI) and cooperative problem-solving approaches to telecommunications. It provides an overview of potential DAI applications in telecommunications, focusing on four systems in more detail. These include distributed traffic management and resolving service interactions in intelligent networks. The document argues that trends in the industry like converged networks require DAI approaches to integrate and coordinate existing AI systems and build distributed control systems with cooperative intelligent components.An Agent Future For Network Control
An Agent Future For Network ControlSara Alvarez
╠²
This document discusses the potential for using intelligent agent technology for network control and management. It notes that as networks become more complex and diverse, distributed autonomous control will become more necessary. Agent technology is proposed as a way to achieve more effective, robust and autonomous network control. The document provides an overview of current network trends driving interest in agent solutions and highlights some key areas like multi-provider environments, resource management and communications integration that could benefit from agent-based approaches.Testing Vitality Ranking and Prediction in Social Networking Services With Dy...
Testing Vitality Ranking and Prediction in Social Networking Services With Dy...reshma reshu
╠²
The document discusses a project aimed at ranking users in social networking services based on their vitality through dynamic analyzing of interactions, addressing technical challenges inherent in large-scale data. It proposes algorithms for user vitality measurement and ranking, contrasting with existing influence-focused methods, and highlights the potential benefits to advertising and user engagement. Additionally, it outlines system requirements and provides an overview of modules, algorithms, and user interface components involved in the project.Social Friend Overlying Communities Based on Social Network Context
Social Friend Overlying Communities Based on Social Network ContextIRJET Journal
╠²
This document discusses algorithms for detecting overlapping communities in social networks. It begins with an introduction to social networks and community detection. It then reviews various algorithms that have been proposed for detecting overlapping communities, including clique percolation methods, fuzzy detection algorithms, agent-based and dynamic algorithms, and more. It also discusses using these algorithms to recommend friends and locations to users based on their behaviors and communities within social networks. The document presents results from applying these algorithms and concludes by discussing opportunities for future work improving recommendation performance.Recommendation System for Information Services Adapted, Over Terrestrial Digi...
Recommendation System for Information Services Adapted, Over Terrestrial Digi...CSEIJJournal
╠²
The document outlines the development of a recommendation system for information services using digital terrestrial television (DTT) in Colombia, integrating technologies such as social networks and user data. It describes the architectural design of an interactive application that adapts services based on user interactions and preferences, involving various user and device profiles. Key aspects such as user interface design, technical aspects of implementation, and the use of web services for data management are also discussed.A MALICIOUS USERS DETECTING MODEL BASED ON FEEDBACK CORRELATIONS
A MALICIOUS USERS DETECTING MODEL BASED ON FEEDBACK CORRELATIONSIJCNC
╠²
This paper presents a trust and reputation framework designed to identify malicious users in peer-to-peer (P2P) streaming systems. It addresses challenges such as dishonest feedback and strategic altering behaviors by utilizing a two-layered overlay model that captures peer behavior and evaluates trust correlations. Simulation results indicate that this framework successfully filters out dishonest feedback and defends against security threats, thereby enhancing the efficiency of P2P streaming systems.Do4301690695
Do4301690695IJERA Editor
╠²
The document discusses vulnerabilities in multicast routing protocols for multihop wireless networks, particularly focusing on insider (byzantine) attacks from compromised nodes. It introduces BSMR, a novel secure multicast routing protocol designed to resist such attacks without requiring special hardware, and presents simulation results demonstrating its effectiveness. The protocol employs a reliability metric to avoid adversarial links and includes mechanisms for route discovery, activation, and maintenance to ensure robust multicast communication.Dv31821825
Dv31821825IJERA Editor
╠²
The document discusses the analysis of social networks, focusing on the emergence of domain-equivalent user groups and collective behavior patterns within these networks. It explores the 'six degrees of separation' theory, utilizing large-scale social media data for verification and analysis, while also addressing the challenges posed by network complexity and size. The authors propose a model for collective behavior learning, highlighting the importance of extracting social dimensions and implementing effective algorithms for managing and predicting user interactions in these networks.Determine Best Fit Topology unit-2.pptx
Determine Best Fit Topology unit-2.pptxnahomtilahun29
╠²
The document outlines the process for determining user needs and establishing requirements for optimal network topology. It discusses methods for assessing user needs, defining functional, performance, security, and cost requirements, as well as the importance of network segmentation for managing different user groups and application types. Key considerations include user interviews, surveys, traffic analysis, bandwidth allocation, and creating specific segments to enhance network performance and security.IRJET- Private Social Media and Data Security
IRJET- Private Social Media and Data SecurityIRJET Journal
╠²
This document discusses the development of a private social media application called Ping Meee using the Ruby on Rails framework. It begins with an introduction that outlines the benefits of private social media over public platforms for organizations, such as better control over data and interactions. The document then reviews relevant literature on social media security challenges and cyber attacks. Finally, it provides a brief overview of how the Ping Meee application works using the Ruby on Rails framework.Safe Drinking Water In Bangladesh Essay
Safe Drinking Water In Bangladesh EssaySusan Cox
╠²
1. Coordination across agencies - As threats evolve, the DHS will need to continue strengthening coordination between its various sub-agencies as well as other federal, state, and local partners.
2. Technology and information sharing - Advances in technology and the ability to share timely intelligence across organizations will be vital. The DHS must adapt to emerging technologies.
3. Addressing new and evolving threats - As threats change, the DHS needs flexibility to take on new responsibilities and tackle threats such as cybersecurity that have become more prominent.
Other issuesIMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...
IMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...IJCSEA Journal
╠²
The document presents a hybrid model for measuring dynamic coupling in distributed object-oriented software systems, addressing limitations of traditional static coupling measures. It outlines a three-step process involving instrumentation, post-processing, and dynamic measurement, aiming for improved predictive accuracy in software quality models. The significance of dynamic coupling is emphasized due to its relevance in handling polymorphism and inheritance within distributed systems.IMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...
IMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...IJCSEA Journal
╠²
This document summarizes a research paper that proposes a method for dynamically measuring coupling in distributed object-oriented software systems. The method involves three steps: instrumentation of the Java Virtual Machine to trace method calls, post-processing of the trace files to merge information, and calculation of coupling metrics based on the dynamic traces. The implementation results show that the proposed approach can effectively measure coupling metrics dynamically by accounting for polymorphism and dynamic binding, overcoming limitations of traditional static coupling analysis.IRJET- An Overview on Cloud Computing and Challenges
IRJET- An Overview on Cloud Computing and ChallengesIRJET Journal
╠²
This document discusses cloud computing, including its various models and challenges. It begins by defining cloud computing as the delivery of computing services over the internet. It then discusses the three main service models of cloud computing: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). The document also outlines the different types of cloud models based on location and service, including public, private, hybrid, community, and federated clouds. Finally, it discusses some of the key challenges of adopting cloud computing such as security, loss of control, vendor lock-in, and lack of skills.Network Effects
Network Effectsa16z
╠²
The document discusses network effects, which occur when a product or service becomes more valuable as more users join, creating barriers to entry and exit within markets. It outlines various properties of networks, such as node similarity, connection types, and unique characteristics of certain platforms like Facebook and Airbnb, showcasing how these companies leveraged network effects for growth. Additionally, the document emphasizes the importance of understanding network dynamics and strategies for building user engagement and critical mass.Booysen machine 2012
Booysen machine 2012Sreekrishna Das
╠²
This document discusses machine-to-machine (M2M) communications in vehicular networks. It begins with an overview of M2M communications and architectures, highlighting areas where M2M is being applied such as smart grids, home networking, and healthcare. The document then explores how M2M principles can enhance vehicular networks by supporting large-scale deployment, cross-platform networking, autonomous monitoring and control, visualization, and security. Several challenges for applying M2M to vehicular networks are also identified, including standardization and data security management.MCPL2013 - Social network analyses in organizations: challenges and approache...
MCPL2013 - Social network analyses in organizations: challenges and approache...Vagner Santana
╠²
This document summarizes a study on social network analysis in organizations. The study analyzed work networks at a large IT service organization using data from 108,050 support tickets over 10 months. Four features were considered for each of the 315 sysadmins: work shift, department, customer, and problem severity. Networks were built connecting sysadmins based on similarity across these features. The results showed distinct networks emerged for each feature combination, such as separate networks for sysadmins based on similarity in service lines vs shift or severity. The document concludes that network analysis is a promising approach to uncover relationships in complex work environments and more research is needed on methods for very large multi-edge networks.Current issues - International Journal of Network Security & Its Applications...
Current issues - International Journal of Network Security & Its Applications...IJNSA Journal
╠²
The document surveys the concept of autonomic networks, focusing on various self-organizing functions such as self-configuration, self-optimization, self-repair, self-protection, and self-cure. It discusses the architectural framework necessary for integrating these functions with telecommunications protocols to enhance network management and user experience, while addressing challenges in quality of service and operational efficiency. The paper highlights techniques for anomaly detection and the role of policies in guiding autonomous elements towards achieving defined goals.B1802030511
B1802030511IOSR Journals
╠²
This document provides a review of simulation techniques for parallel and distributed computing. It discusses several key topics:
1) It defines parallel computing, distributed computing, and parallel and distributed computing systems. Various classification schemes for parallel and distributed systems are also described.
2) It examines several modeling techniques for parallel and distributed systems including system modeling, network modeling, performance modeling, and mathematical modeling. It provides details on parallel discrete event simulation.
3) It reviews several simulation software tools used for modeling parallel and distributed systems including SimOS, SimJava, and MicroGrid.
4) It concludes with a focused discussion on cloud computing as the latest development in parallel and distributed computing.A Survey of MAC Layer Issues and Application layer Protocols for Machine-to-M...
A Survey of MAC Layer Issues and Application layer Protocols for Machine-to-M...IRJET Journal
╠²
This document discusses challenges at the MAC layer for machine-to-machine (M2M) communications. It first describes issues around efficient, scalable and fair channel access for large numbers of M2M devices. It then discusses application layer protocols used to connect devices and applications to the internet, including CoAP, MQTT, and WebSocket. Finally, it analyzes MAC layer issues for a smart home example using M2M for power management, security and assisted living for the elderly. Key challenges include supporting diverse quality of service needs, large numbers of devices sharing channels, energy efficiency needs, and low-cost hardware requirements.FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.More Related Content
Similar to SNA of M2M Organisations (20)
Application Of Distributed AI And Cooperative Problem Solving To Telecommunic...
Application Of Distributed AI And Cooperative Problem Solving To Telecommunic...Claudia Acosta
╠²
This document discusses applying distributed artificial intelligence (DAI) and cooperative problem-solving approaches to telecommunications. It provides an overview of potential DAI applications in telecommunications, focusing on four systems in more detail. These include distributed traffic management and resolving service interactions in intelligent networks. The document argues that trends in the industry like converged networks require DAI approaches to integrate and coordinate existing AI systems and build distributed control systems with cooperative intelligent components.An Agent Future For Network Control
An Agent Future For Network ControlSara Alvarez
╠²
This document discusses the potential for using intelligent agent technology for network control and management. It notes that as networks become more complex and diverse, distributed autonomous control will become more necessary. Agent technology is proposed as a way to achieve more effective, robust and autonomous network control. The document provides an overview of current network trends driving interest in agent solutions and highlights some key areas like multi-provider environments, resource management and communications integration that could benefit from agent-based approaches.Testing Vitality Ranking and Prediction in Social Networking Services With Dy...
Testing Vitality Ranking and Prediction in Social Networking Services With Dy...reshma reshu
╠²
The document discusses a project aimed at ranking users in social networking services based on their vitality through dynamic analyzing of interactions, addressing technical challenges inherent in large-scale data. It proposes algorithms for user vitality measurement and ranking, contrasting with existing influence-focused methods, and highlights the potential benefits to advertising and user engagement. Additionally, it outlines system requirements and provides an overview of modules, algorithms, and user interface components involved in the project.Social Friend Overlying Communities Based on Social Network Context
Social Friend Overlying Communities Based on Social Network ContextIRJET Journal
╠²
This document discusses algorithms for detecting overlapping communities in social networks. It begins with an introduction to social networks and community detection. It then reviews various algorithms that have been proposed for detecting overlapping communities, including clique percolation methods, fuzzy detection algorithms, agent-based and dynamic algorithms, and more. It also discusses using these algorithms to recommend friends and locations to users based on their behaviors and communities within social networks. The document presents results from applying these algorithms and concludes by discussing opportunities for future work improving recommendation performance.Recommendation System for Information Services Adapted, Over Terrestrial Digi...
Recommendation System for Information Services Adapted, Over Terrestrial Digi...CSEIJJournal
╠²
The document outlines the development of a recommendation system for information services using digital terrestrial television (DTT) in Colombia, integrating technologies such as social networks and user data. It describes the architectural design of an interactive application that adapts services based on user interactions and preferences, involving various user and device profiles. Key aspects such as user interface design, technical aspects of implementation, and the use of web services for data management are also discussed.A MALICIOUS USERS DETECTING MODEL BASED ON FEEDBACK CORRELATIONS
A MALICIOUS USERS DETECTING MODEL BASED ON FEEDBACK CORRELATIONSIJCNC
╠²
This paper presents a trust and reputation framework designed to identify malicious users in peer-to-peer (P2P) streaming systems. It addresses challenges such as dishonest feedback and strategic altering behaviors by utilizing a two-layered overlay model that captures peer behavior and evaluates trust correlations. Simulation results indicate that this framework successfully filters out dishonest feedback and defends against security threats, thereby enhancing the efficiency of P2P streaming systems.Do4301690695
Do4301690695IJERA Editor
╠²
The document discusses vulnerabilities in multicast routing protocols for multihop wireless networks, particularly focusing on insider (byzantine) attacks from compromised nodes. It introduces BSMR, a novel secure multicast routing protocol designed to resist such attacks without requiring special hardware, and presents simulation results demonstrating its effectiveness. The protocol employs a reliability metric to avoid adversarial links and includes mechanisms for route discovery, activation, and maintenance to ensure robust multicast communication.Dv31821825
Dv31821825IJERA Editor
╠²
The document discusses the analysis of social networks, focusing on the emergence of domain-equivalent user groups and collective behavior patterns within these networks. It explores the 'six degrees of separation' theory, utilizing large-scale social media data for verification and analysis, while also addressing the challenges posed by network complexity and size. The authors propose a model for collective behavior learning, highlighting the importance of extracting social dimensions and implementing effective algorithms for managing and predicting user interactions in these networks.Determine Best Fit Topology unit-2.pptx
Determine Best Fit Topology unit-2.pptxnahomtilahun29
╠²
The document outlines the process for determining user needs and establishing requirements for optimal network topology. It discusses methods for assessing user needs, defining functional, performance, security, and cost requirements, as well as the importance of network segmentation for managing different user groups and application types. Key considerations include user interviews, surveys, traffic analysis, bandwidth allocation, and creating specific segments to enhance network performance and security.IRJET- Private Social Media and Data Security
IRJET- Private Social Media and Data SecurityIRJET Journal
╠²
This document discusses the development of a private social media application called Ping Meee using the Ruby on Rails framework. It begins with an introduction that outlines the benefits of private social media over public platforms for organizations, such as better control over data and interactions. The document then reviews relevant literature on social media security challenges and cyber attacks. Finally, it provides a brief overview of how the Ping Meee application works using the Ruby on Rails framework.Safe Drinking Water In Bangladesh Essay
Safe Drinking Water In Bangladesh EssaySusan Cox
╠²
1. Coordination across agencies - As threats evolve, the DHS will need to continue strengthening coordination between its various sub-agencies as well as other federal, state, and local partners.
2. Technology and information sharing - Advances in technology and the ability to share timely intelligence across organizations will be vital. The DHS must adapt to emerging technologies.
3. Addressing new and evolving threats - As threats change, the DHS needs flexibility to take on new responsibilities and tackle threats such as cybersecurity that have become more prominent.
Other issuesIMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...
IMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...IJCSEA Journal
╠²
The document presents a hybrid model for measuring dynamic coupling in distributed object-oriented software systems, addressing limitations of traditional static coupling measures. It outlines a three-step process involving instrumentation, post-processing, and dynamic measurement, aiming for improved predictive accuracy in software quality models. The significance of dynamic coupling is emphasized due to its relevance in handling polymorphism and inheritance within distributed systems.IMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...
IMPLEMENTATION OF DYNAMIC COUPLING MEASUREMENT OF DISTRIBUTED OBJECT ORIENTED...IJCSEA Journal
╠²
This document summarizes a research paper that proposes a method for dynamically measuring coupling in distributed object-oriented software systems. The method involves three steps: instrumentation of the Java Virtual Machine to trace method calls, post-processing of the trace files to merge information, and calculation of coupling metrics based on the dynamic traces. The implementation results show that the proposed approach can effectively measure coupling metrics dynamically by accounting for polymorphism and dynamic binding, overcoming limitations of traditional static coupling analysis.IRJET- An Overview on Cloud Computing and Challenges
IRJET- An Overview on Cloud Computing and ChallengesIRJET Journal
╠²
This document discusses cloud computing, including its various models and challenges. It begins by defining cloud computing as the delivery of computing services over the internet. It then discusses the three main service models of cloud computing: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). The document also outlines the different types of cloud models based on location and service, including public, private, hybrid, community, and federated clouds. Finally, it discusses some of the key challenges of adopting cloud computing such as security, loss of control, vendor lock-in, and lack of skills.Network Effects
Network Effectsa16z
╠²
The document discusses network effects, which occur when a product or service becomes more valuable as more users join, creating barriers to entry and exit within markets. It outlines various properties of networks, such as node similarity, connection types, and unique characteristics of certain platforms like Facebook and Airbnb, showcasing how these companies leveraged network effects for growth. Additionally, the document emphasizes the importance of understanding network dynamics and strategies for building user engagement and critical mass.Booysen machine 2012
Booysen machine 2012Sreekrishna Das
╠²
This document discusses machine-to-machine (M2M) communications in vehicular networks. It begins with an overview of M2M communications and architectures, highlighting areas where M2M is being applied such as smart grids, home networking, and healthcare. The document then explores how M2M principles can enhance vehicular networks by supporting large-scale deployment, cross-platform networking, autonomous monitoring and control, visualization, and security. Several challenges for applying M2M to vehicular networks are also identified, including standardization and data security management.MCPL2013 - Social network analyses in organizations: challenges and approache...
MCPL2013 - Social network analyses in organizations: challenges and approache...Vagner Santana
╠²
This document summarizes a study on social network analysis in organizations. The study analyzed work networks at a large IT service organization using data from 108,050 support tickets over 10 months. Four features were considered for each of the 315 sysadmins: work shift, department, customer, and problem severity. Networks were built connecting sysadmins based on similarity across these features. The results showed distinct networks emerged for each feature combination, such as separate networks for sysadmins based on similarity in service lines vs shift or severity. The document concludes that network analysis is a promising approach to uncover relationships in complex work environments and more research is needed on methods for very large multi-edge networks.Current issues - International Journal of Network Security & Its Applications...
Current issues - International Journal of Network Security & Its Applications...IJNSA Journal
╠²
The document surveys the concept of autonomic networks, focusing on various self-organizing functions such as self-configuration, self-optimization, self-repair, self-protection, and self-cure. It discusses the architectural framework necessary for integrating these functions with telecommunications protocols to enhance network management and user experience, while addressing challenges in quality of service and operational efficiency. The paper highlights techniques for anomaly detection and the role of policies in guiding autonomous elements towards achieving defined goals.B1802030511
B1802030511IOSR Journals
╠²
This document provides a review of simulation techniques for parallel and distributed computing. It discusses several key topics:
1) It defines parallel computing, distributed computing, and parallel and distributed computing systems. Various classification schemes for parallel and distributed systems are also described.
2) It examines several modeling techniques for parallel and distributed systems including system modeling, network modeling, performance modeling, and mathematical modeling. It provides details on parallel discrete event simulation.
3) It reviews several simulation software tools used for modeling parallel and distributed systems including SimOS, SimJava, and MicroGrid.
4) It concludes with a focused discussion on cloud computing as the latest development in parallel and distributed computing.A Survey of MAC Layer Issues and Application layer Protocols for Machine-to-M...
A Survey of MAC Layer Issues and Application layer Protocols for Machine-to-M...IRJET Journal
╠²
This document discusses challenges at the MAC layer for machine-to-machine (M2M) communications. It first describes issues around efficient, scalable and fair channel access for large numbers of M2M devices. It then discusses application layer protocols used to connect devices and applications to the internet, including CoAP, MQTT, and WebSocket. Finally, it analyzes MAC layer issues for a smart home example using M2M for power management, security and assisted living for the elderly. Key challenges include supporting diverse quality of service needs, large numbers of devices sharing channels, energy efficiency needs, and low-cost hardware requirements.Recently uploaded (20)
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
╠²
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the Same"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash
╠²
10 Key Challenges for AI within the EU Data Protection FrameworkCapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.UserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40
╠²
VMwareŌĆÖs pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include ScopesŌĆöand Datacenter is now officially part of the equation. In this session, weŌĆÖll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. YouŌĆÖll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiencyŌĆöall without migrating to the cloud. WeŌĆÖll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance
╠²
FIDO Seminar: Evolving Landscape of Post-Quantum CryptographyUsing the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...Josef Weingand
╠²
IBM LTO10FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptx
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptxFIDO Alliance
╠²
FIDO Seminar: Authentication for a Billion Consumers - AmazonConnecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
╠²
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
╠²
ū×ū©ūøū¢ ūóūÖūæūĢūōūÖūØ ū¬ūóū®ūÖūÖū¬ūÖ ūæūóū£ 3/4/5 ū”ūÖū©ūÖūØ, ūóūō 22 ūöūŚū£ūżūĢū¬ ūøū£ūÖūØ ūóūØ ūøū£ ūÉūżū®ū©ūĢūÖūĢū¬ ūöūóūÖūæūĢūō ūöūōū©ūĢū®ūĢū¬.╠²ūæūóū£ ū®ūśūŚ ūóūæūĢūōūö ūÆūōūĢū£ ūĢū×ūŚū®ūæ ūĀūĢūŚ ūĢū¦ū£ ū£ūöūżūóū£ūö ūæū®ūżūö ūöūóūæū©ūÖū¬/ū©ūĢūĪūÖū¬/ūÉūĀūÆū£ūÖū¬/ūĪūżū©ūōūÖū¬/ūóū©ūæūÖū¬ ūĢūóūĢūō..
ū×ūĪūĢūÆū£ ū£ūæū”ūó ūżūóūĢū£ūĢū¬ ūóūÖūæūĢūō ū®ūĢūĀūĢū¬ ūöū×ū¬ūÉūÖū×ūĢū¬ ū£ūóūĀūżūÖūØ ū®ūĢūĀūÖūØ: ū¦ūÖūōūĢūŚ ūÉūĀūøūÖ, ūÉūĢūżū¦ūÖ, ūĀūÖūĪūĢū©, ūĢūøū©ūĪūĢūØ ūÉūĀūøūÖ.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowSecuring Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of DeepfakesYou are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
Ad
SNA of M2M Organisations
- 1. Module: 55-7626-00N-A-20123 ŌĆō Social Media Use in Organisations (A-2012/3) Social Network Analysis of M2M Organisations Lee James Cox B0049872 MA in Technical Communication 1
- 2. First some definitions Social Network Analysis (SNA) is the study of structure1. It is the mapping and measuring of relationships and flows (ties) between members (nodes) within a network. Machine to Machine (M2M) refers to the technology that connects: a. a device (such as a sensor or meter) to capture an event (such as temperature, inventory level, etc.) b. which is relayed through a network (wireless, wired) c. to an application (software program), that translates the captured event into meaningful information (for example, items need to be restocked). M2M Organisations include device, network and application providers; as well as: ŌĆó Enterprise Customers: provide the services to end-users, e.g. Coca Cola, British Gas ŌĆó Platform Providers: equipment and solution providers to operators and others ŌĆó System Integrators: build solutions to join up incompatible systems 2 Node Node Tie
- 3. Five things to first consider about SNA 3 1. The first endeavour should always be to define what the Nodes and Ties mean.[2] For our M2M analysis, the nodes are organisations and ties are contractual relationships. 2. Nodes can have different weightings of importance, e.g. ŌĆō Size (revenue/subscribers) ŌĆō Geography ŌĆō Track record ŌĆō Associations ŌĆō Other segmentation attributes 3. Ties have characteristics that matter when it comes to identifying things like leadership, influence and strength e.g. ŌĆō Direction (one-way, both) ŌĆō Quantity ŌĆō Contract date ŌĆō Value ŌĆō Frequency 4. Matrix, graphs and other visualization tools are important for analysis and measurement. ŌĆō Tools like NodeXL will be required for any network of reasonable size ŌĆō Considerable time is usually required to capture and keep the data up to date. ŌĆō The M2M example in later slides shows just a few of the tens of thousands of Enterprises, 200+ Operators & 300+ Application Providers that Jasper, Vodafone & Ericsson have as M2M partners! 5. The perspective of the analysis can centre on the complete network (socio) or an individuals personal network (ego).
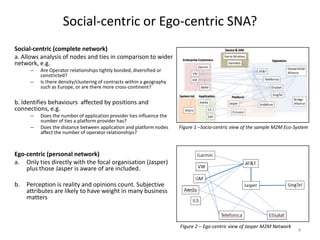
- 4. Social-centric or Ego-centric SNA? Social-centric (complete network) a. Allows analysis of nodes and ties in comparison to wider network, e.g. ŌĆō Are Operator relationships tightly bonded, diversified or constricted? ŌĆō Is there density/clustering of contracts within a geography such as Europe, or are there more cross-continent? b. Identifies behaviours affected by positions and connections, e.g. ŌĆō Does the number of application provider ties influence the number of ties a platform provider has? ŌĆō Does the distance between application and platform nodes affect the number of operator relationships? Ego-centric (personal network) a. Only ties directly with the focal organisation (Jasper) plus those Jasper is aware of are included. b. Perception is reality and opinions count. Subjective attributes are likely to have weight in many business matters 4 Figure 1 ŌĆōSocio-centric view of the sample M2M Eco-System Figure 2 ŌĆō Ego-centric view of Jasper M2M Network
- 5. Visualization[3] can also reveal positional relationships ŌĆó Operators have the highest degree centrality. AT&T is most central of the operators and is the longest established with largest customer base. ŌĆó Application Providers have the highest closeness centrality. They work with multiple operators but rarely direct with Enterprise customers. ŌĆó Device/SIM and Platform Providers are structurally equivalent nodes. ŌĆó System Integrators are the most peripheral, having the smallest number of connections. ŌĆó Enterprise Customers has the highest betweeness centrality providing the only path to System Integrations ŌĆó No groups of nodes are connected to each other (cliques). However if the definition of ties were extended beyond ŌĆścontractualŌĆÖ then informal or personal relationships would show all nodes in this extracted view as being connected. Operators Enterprise Customers Device/SIM Application Providers Platform System Integrators 5
- 6. Benefits & Limitations of SNA Benefits Limitations Provides framework to describe any complex network. Collecting and maintaining source data can be difficult Identifies important individuals and the influence they have Does not describe meanings, motives or explain why actions happen, e.g. why a contract was won. A typological analysis is more suitable. Can identify previously unrecognised sub-groups through visual clusters Little examination of important attributes such as attitudes, opinions and behaviours that may be helping or hindering relationships Highlights areas for further inquiry and possible improvement, e.g. gaps More sensitive to data omissions than other surveys. >75% sampling is required.[4] Even weak ties may be revealed as important for bridging disparate groups Privacy can be ignored when views of others contribute to the analysis. Useful for track changes over time to reveal paths. Visualization can lead to over simplification and misreading of results. E.g. Network measures such as density can be easily misrepresented when networks of different sizes are compared. 6
- 7. Other take away learningŌĆÖs from SNA 1. Social Network Analysis is not necessarily restricted to connections from tools such as Facebook or LinkedIn. SNA can be applied to a wide range of network subjects, such as how diseases spread, mapping films and interaction of characters, influence of language throughout the world, etc. 2. SNA focusses on relationships rather than attributes of the ŌĆśnodesŌĆÖ for their own sake, or the ideation behind the relationship. 3. A Social Network does not in itself encourage co-operation or collective action. Community tools such as Online Forums lend themselves better to co-ordination of action. 4. Connections within business networks often reveal companies tied to competitors. This has implications for trust and potential leaks within a social network. 7
- 8. References [1] Wellman B, Berkowitz SD (1977). Social structures: a network approach. Greenwich: JAI Press. [2] Pinheiro, C. (2011). Social Network Analysis in Telecommunications. John Wiley & Sons. [3] Based on Davies R (2011). Network Visualisation and Analysis, Cambridge. [4] Borgatti, Carley & Krackhardt (2006). 8
