Software testing methodolgy with the control flow analysis
- 1. SOFTWARE TESTING METHODOLGY WITH THE CONTROL FLOW ANALYSIS WEN-CHANG PAI, CHI-MING CHUNG, CHING-TANG HSIEH, CHUN- CHIA WANG, AND YING-HONG WANG
- 2. PRESENTED BY: REEMA QAISER KHAN MS(SE)-2
- 3. ŌĆó This paper provides a method for analyzing the control-flow of a program. ŌĆó The authors define a number of command types and test data generating rules based on the control-flow of the program. ŌĆó An algorithm to scan program and analysis testing paths is provided. ŌĆó This will allow testers to recover the programŌĆÖs design, understand the software structure, and assist software maintenance.
- 4. AN OVERVIEW OF PROGRAM TESTING ŌĆó In a program P, we say a statement block B = (s1, s2, ŌĆ”, sn) is a maximal subset of contiguous statements of P such that statement si is the unique successor of si-1 and si-1 is the unique predecessor of si, for all i = 1, 2, ŌĆ”, n. ŌĆó A program graph G = {nodes, edges} contains a set of nodes and edges
- 5. ŌĆó A node without a predecessor is a start node. ŌĆó A node without a successor is an exit node. ŌĆó A complete path is a path whose initial node is the start node of G and whose final node is an exit node of G. ŌĆó A well known logic coverage criterion is decision coverage or branch coverage. Examples of branch or decision statements are IF statements, WHILE statements, and SWITCH statement. ŌĆó This criterion states that each branch direction must be traversed at least once.
- 6. ŌĆó In software testing technologies, boundary testing (or boundary value analysis; BVA) is a good test case design. It selects test data at the boundary of the input domain. ŌĆó Experience shows that test data selected with BVA have a higher payoff than other data. ŌĆó More errors tend to occur at the boundaries of the input domain.
- 7. AUTOMATICALLY GENERATING TEST DATA ŌĆó The steps involved in the method are described in the following: 1) Choosing Adequacy Testing Criteria: The branch coverage criterion is adopted in this paper to generate test data for testing a program. 2) Defining Command Types: We define three typical statement types in a program: (1) sequential commands, (2)conditional commands, and (3) loop commands. Each command type essentially corresponding to a block or some blocks in a program. In this paper, we will generate test data for each of the command types to enter every branch of a program.
- 8. 3) Scanning the Program and Generating Test Data: The test data are generated from the input domain, which is derived through boundary value analysis with the Branch coverage criterion. 4) Analyzing Test Paths and Testing : Finally, testers analyze the testing paths and test the program with the results obtained in step 3.
- 9. TEST DATA GENERATING RULES ŌĆó Type 1. Sequential Command Set : ŌĆó The Sequential commands, such as OPEN, READ, WRITE, and CLOSE statements, are usually written in the form ŌĆó ŌĆśC1; C2ŌĆÖ,
- 10. Rule 4.1 : The set S1, S2, ŌĆ”, Sn is a contiguous sequence of statements of a program P, such that a corresponding block B exists in P. A node N also exists in the program graph G.
- 11. ŌĆó Type 2. Conditional Command Set : ŌĆó A conditional command, such as an If-Then-End statement, If-Then-Else-End statement, Switch-Case-With- Default statement, or Switch-Case-Without-Default statement, has a number of subcommands, from which exactly one is chosen to be executed. Conditional commands typically have the form ŌĆó If CON1 then B1 Else if CON2 then B2 ŌĆ” else if CONn then Bn end if
- 12. Rule 4.2 : Set SŌĆ▓ is a set of Switch statements of a program P, such that a number of corresponding blocks B1, B2, ŌĆ”, Bk exist in SŌĆ▓. A number of nodes S, N1, N2, ŌĆ”, Nk, and E also exist in the program graph G.
- 13. ŌĆó Type 3. Loop Command Set : ŌĆó Loop commands, such as For-loop statements, While-loop statements, and Repeat- loop statements, have a number of subcommands that are executed repeatedly until some conditions are true. Loop commands typically have the form While CON do B End while OR Repeat B Until CON
- 14. Rule 4.3 : Set SŌĆ▓ is a Loop statement s of a program P, such that a corresponding block B exists in P. A number of nodes, S, N, and E, also exist in the program graph G.
- 15. TEST PATH ANALYSIS ALGORITHM ŌĆó The algorithm analyzes the path to search for the command types and the apply rules 4.1 to 4.3 accordingly. ŌĆó We can transform each statement of a program to its corresponding flow. The paths are analyzed and test data are generated after the program has been completely scanned.
- 16. ŌĆó Algorithm PATH_ANALYSIS ŌĆó begin ŌĆó get PROGRAM ŌĆó set START_NODE ŌĆó set NEW_NODE ŌĆó move POINTER to NEW_NODE ŌĆó while not END_OF_PROGRAM ŌĆó read next INSTRUCTION ŌĆó search INSTRUCTION_TABLE ŌĆó switch (INSTRUCTION) ŌĆó case ŌĆ£Switch Statement SetŌĆØ ŌĆó set NEW_NODE (or NODES) /* according to the rule 4.2 */ ŌĆó move POINTER to NEW_NODE /* according to the rule 4.2 */ ŌĆó case ŌĆ£Loop Statement SetŌĆØ ŌĆó set NEW_NODE (or NODES) /* according to the rule 4.3 */ ŌĆó move POINTER to NEW_NODE /* according to the rule 4.3 */ ŌĆó case ŌĆ£Sequence Statement SetŌĆØ /* according to the rule 4.1 */ ŌĆó skip ŌĆó end {switch} ŌĆó end {while} ŌĆó set END_NODE ŌĆó end {PATH_ANALYSIS}
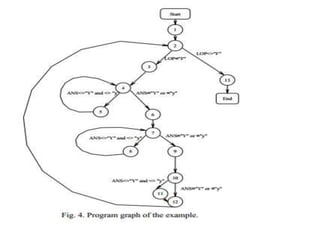
- 17. AN EXAMPLE
- 18. TEST CASES USING BOUNDARY VALUE ANALYSIS ŌĆó We have three loop commands, and one conditional command. ŌĆó Test Cases for the first Loop Command (WHILE LOP=ŌĆ£FŌĆØ) using boundary value analysis: 1- Test Case with test data of character F, to check input domain LOP=ŌĆ£FŌĆØ. 2- Test Case with test data can be any character except F, to check input domain LOP<>ŌĆ£FŌĆØ e.g. LOP=ŌĆ£AŌĆØ,LOP=ŌĆ£BŌĆØ, etc.
- 19. ŌĆó Test Cases for the Second Loop Command (WHILE ANS<> ŌĆ£YŌĆØ and ANS<> ŌĆ£yŌĆØ) using boundary value analysis: 1- Test Case with test data can be any character except ŌĆ£YŌĆØ or ŌĆ£yŌĆØ, to check input domain ANS<> ŌĆ£YŌĆØ and ANS<> ŌĆ£yŌĆØ, e.g. ANS=ŌĆ£AŌĆØ or ANS=ŌĆ£aŌĆØ, ANS=ŌĆ£BŌĆØor ANS=ŌĆ£bŌĆØ, etc. 2- Test Case with test data ŌĆ£YŌĆØ and ŌĆ£yŌĆØ , to check input domain ANS=ŌĆ£YŌĆØ or ANS=ŌĆ£yŌĆØ.
- 20. ŌĆó Test Cases for the Third Loop Command (WHILE ANS<> ŌĆ£YŌĆØ and ANS<> ŌĆ£yŌĆØ) using boundary value analysis: 1- Test Case with test data can be any character except ŌĆ£YŌĆØ or ŌĆ£yŌĆØ, to check input domain ANS<> ŌĆ£YŌĆØ and ANS<> ŌĆ£yŌĆØ, e.g. ANS=ŌĆ£AŌĆØ or ANS=ŌĆ£aŌĆØ, ANS=ŌĆ£BŌĆØor ANS=ŌĆ£bŌĆØ, etc. 2- Test Case with test data ŌĆ£YŌĆØ and ŌĆ£yŌĆØ , to check input domain ANS=ŌĆ£YŌĆØ or ANS=ŌĆ£yŌĆØ.
- 21. ŌĆó Test Cases for the First Conditional Command (IF ANS<> ŌĆ£YŌĆØ and ANS<> ŌĆ£yŌĆØ) using boundary value analysis: 1- Test Case with test data can be any character except ŌĆ£YŌĆØ or ŌĆ£yŌĆØ, to check input domain ANS<> ŌĆ£YŌĆØ and ANS<> ŌĆ£yŌĆØ, e.g. ANS=ŌĆ£AŌĆØ or ANS=ŌĆ£aŌĆØ, ANS=ŌĆ£BŌĆØor ANS=ŌĆ£bŌĆØ, etc. 2- Test Case with test data ŌĆ£YŌĆØ and ŌĆ£yŌĆØ , to check input domain ANS=ŌĆ£YŌĆØ or ANS=ŌĆ£yŌĆØ.
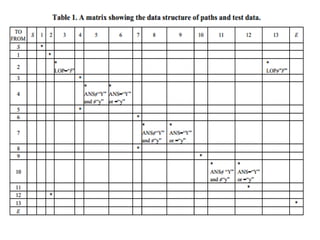
- 24. ŌĆó From Table 1, we have the following testing paths: ŌĆó <S, 1, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 5, 4, 6, 7, 8, 7, 9, 10, 11, 12, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 5, 4, 6, 7, 8, 7, 9, 10, 12, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 6, 7, 8, 7, 9, 10, 11, 12, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 6, 7, 8, 7, 9, 10, 12, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 5, 4, 6, 7, 9, 10, 11, 12, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 5, 4, 6, 7, 9, 10, 12, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 6, 7, 9, 10, 11, 12, 2, 13, E> ŌĆó <S, 1, 2, 3, 4, 6, 7, 9, 10, 12, 2, 13, E>
- 25. CONCLUSION ŌĆó The researchers have defined a number of command types flows and given some test data generation rules. These have been derived based on a branch coverage testing path selection criterion and boundary value analysis. We have also provided an algorithm and used an example to illustrate the methodology and show that it is practicable. ŌĆó The proposed methodology allows maintainers to recover a programŌĆÖs structure and conduct software maintenance. The method proposed in this paper can help testers recognize and test programs more efficiently.
- 26. REFERENCE ŌĆó http://www.iis.sinica.edu.tw/page/jise/2005/ 200511_07.pdf
- 27. THANKYOU