Spam TV
Download as ppt, pdf2 likes877 views
Web 1.0 allowed users to freely share and upload content online. As user-generated content grew in popularity with Web 2.0, spam has expanded from email to now include unsolicited audio and video content that could soon appear on popular video sharing websites, following the model of spam expanding from email to various online platforms. Research from the University of California San Diego found that spammers had to send 350 million spam messages to generate only 28 sales of male enhancement products, demonstrating the inefficiency of spam tactics.
1 of 12
Download to read offline










Ad
Recommended
Thewww
ThewwwMelissa Davis
╠²
1) In the late 1950s and 1960s, the US government established ARPA (Advanced Research Projects Agency) in response to the Soviet launch of Sputnik. ARPA funded the creation of ARPANET, one of the first wide-area networks connecting government and university sites.
2) ARPANET used new technologies like packet switching and interface message processors to connect different computer networks. It served as the basis for further networking research and the eventual development of the Internet.
3) In the 1970s and 1980s, networking expanded through the development of protocols like TCP and the rise of personal computers and email. The World Wide Web was created in the early 1990s, allowing for easy navigation of onlineEmpowerment Technology Lesson 2
Empowerment Technology Lesson 2alicelagajino
╠²
Here is a draft social media post for your "Think Before You Click" campaign ad/poster:
#ThinkBeforeYouClick
One click can change everything. Help keep yourself and others safe online by pausing to consider what you share and where you surf. Your privacy and security are important - be mindful of protecting personal information. Use technology to empower yourself through knowledge and connection, not endanger yourself through haste or deception. This message brought to you by the #EmpowermentTechnology campaign. Think before you click!Cyber Security for 5th and 6th Graders
Cyber Security for 5th and 6th GradersStephen Thomas, CISSP
╠²
This document provides an agenda and overview for a cyber security workshop for 5th and 6th graders. The agenda includes introductions to cyber security, secure passwords, social engineering, privacy practices, and an interactive cyber security jeopardy game. Key topics covered are defining cyber security and common threats, creating strong and unique passwords, protecting personal information when online, and practicing safe internet usage. A discussion of specific security and privacy strategies helps students learn how to protect themselves in the digital world.Moss Adams 2007 Personal Financial Planning Practice Study
Moss Adams 2007 Personal Financial Planning Practice Studyhilldor
╠²
The document summarizes a study on CPA financial planning practices. It finds that CPA financial planning practices are growing faster than the broader financial planning industry, averaging 34.9% annual growth. Most successful firms develop formal plans and goals, monitor performance of their financial planning services, formalize compensation systems, and devote time to marketing. The study provides insights into the structures, registrations, challenges and opportunities for CPA financial planning practices.Research paper powerpoint presentation for public viewing
Research paper powerpoint presentation for public viewingKnuckles McGuire
╠²
Malware can have negative effects on computers. It is software designed to harm systems or gain unauthorized access. Examples include viruses, spyware, and botnets. A brief history of malware outlines some of the earliest known viruses from the 1970s to the present. Today, malware constantly evolves to exploit new computer capabilities. Victims experience issues like decreased performance and unexpected programs/ads. Users can take precautions like antivirus software, but experts worry future malware may increasingly endanger systems since attacks evolve while defenses must catch up.Arrott Htcia St Johns 101020
Arrott Htcia St Johns 101020Anthony Arrott
╠²
The document discusses the triple challenge of changing IT security landscape, cybercrime, and protection methods. It notes that information now comes from outside rather than inside enterprises, cybercrime has evolved from simple crimes to organized crime for profit, and protection now relies on cloud-based querying rather than installing updates on individual computers. Traditional antivirus methods are overwhelmed by the volume of new threats. Effective protection requires multiple layers of reputation services that inspect sources and file contents.The ŌĆśLove BugŌĆÖ or the so-called 'Iloveyou virus'
The ŌĆśLove BugŌĆÖ or the so-called 'Iloveyou virus'johannesgetu60
╠²
The 'ILOVEYOU' virus, one of the most notorious computer viruses, spread through email in May 2000, causing an estimated $15 billion in damages. It infected millions of computers by enticing users with romantic messages, leading to data loss, service disruptions, and reputational damage for affected organizations. This incident highlighted the importance of cybersecurity, prompting increased awareness and the implementation of various protective measures.Ransomware hostage rescue manual
Ransomware hostage rescue manualRoel Palmaers
╠²
The document is a ransomware hostage rescue manual that explains what ransomware is, how to identify if you're infected, and the steps to take if infected. It covers infection methods, response strategies, and preventive measures, emphasizing the importance of backups and security awareness. Additionally, it provides insights into Bitcoin and the use of the Tor network by hackers for anonymity.When web 2.0 sneezes, everyone gets sick
When web 2.0 sneezes, everyone gets sickStefan Tanase
╠²
The document discusses the vulnerabilities and threats posed by Web 2.0 technologies, particularly in relation to social networking platforms. It highlights the rise of malware like the Koobface worm, which utilizes social engineering tactics to spread through various networks. Additionally, it underscores the potential for targeted attacks, privacy issues, and data leakage within social media contexts, stressing the ongoing evolution of cybersecurity challenges in this domain.radhika.pdf
radhika.pdfdharmendra321361
╠²
Computer viruses and worms replicate themselves by inserting copies into other programs or documents. Viruses are pieces of code that piggyback on other programs, while worms are self-contained and use network vulnerabilities to spread. Notable examples include the Morris worm of 1988, which was the first to gain widespread attention, and the MyDoom virus of 2004, which caused major internet disruptions through distributed denial of service attacks. Prevention methods against viruses, worms, and other malware include software updates, antivirus programs, and more secure operating systems.Living In Hi-Tech, Hi-Touch World
Living In Hi-Tech, Hi-Touch WorldCheryl Engle
╠²
The document outlines the evolution of web tools and technologies from first to third generation, emphasizing their applications in enhancing interactivity and collaboration. It discusses various tools, such as email, wikis, and immersive environments, while providing insights into their advantages and limitations. The American Red Cross's vision of utilizing these technologies to streamline service delivery with personal interaction is highlighted throughout the overview.News Bytes by Jaskaran Narula - Null Meet Bhopal
News Bytes by Jaskaran Narula - Null Meet Bhopal Jaskaran Narula
╠²
The document provides a summary of recent hacking and cybersecurity news. It discusses hacks of the NSA and a Ukrainian government customs database that stole classified data. It also mentions the rise of ransomware attacks, a hacking tool called USB Kill that can destroy computers, and issues with the mobile game Pokemon Go accessing locations deemed sacred in some religions. The document provides links to additional information on these and other topics like exploited Linux vulnerabilities and tips for secure Python coding.The Internet
The InternetHugo Antonio
╠²
The document provides an overview of the history and uses of the Internet. It discusses how the Internet was created in the 1960s as a network to share information between computers called ARPANET. It then describes common uses of the Internet like accessing information, entertainment, social networking, and commerce. It also outlines some important websites and programs used to browse the Internet.Features Of The Internet
Features Of The Internetkimromero
╠²
The document provides an overview of several key features and functions of the Internet, including chatting, email, file transfer protocol (FTP), newsgroups, social networking, and telnet. It discusses how chatting allows real-time communication between users, how email is one of the most used functions and can be sent to multiple addresses, and common problems with email like spam and viruses. It also outlines that FTP is used to transfer files, newsgroups are public message boards on specific topics, social networking focuses on online communities, and telnet formerly allowed remote computer access.Information Security - A Discussion
Information Security - A DiscussionKaushik Patra
╠²
The document discusses various aspects of information security in the high-tech era, emphasizing the vulnerabilities of technology, such as hacking, phishing, and social engineering. It highlights the importance of personal responsibility in safeguarding sensitive information and passwords, as well as the effectiveness of technology in creating security measures. Ultimately, the document concludes that security is only as strong as its weakest link and calls for awareness and proactive measures against emerging threats.The malware effects
The malware effectsViral Parmar
╠²
Viral Parmar discusses the history and types of malware, including viruses, trojans, ransomware, and scareware. Some notable ransomware strains described are CryptoLocker, Cryptowall, Locky, and WannaCry. The document also outlines how to create ransomware-as-a-service using the "Tox" kit and provides steps to remove ransomware infections along with decryption tools.10 Worst Computer Viruses of all time
10 Worst Computer Viruses of all timeAlefyaM
╠²
The document lists and describes the 10 worst computer viruses of all time. It discusses viruses such as Melissa, ILOVEYOU, Code Red, Nimda, MyDoom, Sasser, Netsky, Leap-A/Oompa-A, and the number one worst virus, Storm Worm. The viruses caused billions in damages and disrupted systems worldwide by spreading through email and files and exploiting software vulnerabilities.Computer Worms
Computer Wormssadique_ghitm
╠²
This document discusses computer worms, including how they work, types of worms, and examples of major worms. It defines worms as programs that replicate themselves across a network by exploiting security vulnerabilities. The document covers worm target discovery, propagation, activation methods, payloads, examples like Morris worm, Code Red, Nimda, SQL Slammer, and Sobig.f, as well as prevention techniques and current research focus areas.What is a virus and anti virus
What is a virus and anti virusLeonor Costa
╠²
The document discusses viruses and anti-virus software. It provides a 9 point lesson plan on viruses, including what they are, how they spread, their evolution timeline from 1983-2007, statistics on known viruses, the differences between crackers and hackers, and the main types of viruses such as boot viruses, time bombs, worms, and Trojan horses. The goals are to increase knowledge on preventing and combating viruses through behavioral changes.ppt on antivirus and computer virus
ppt on antivirus and computer virusNaveen Goyal
╠²
Computer viruses are software programs that spread from computer to computer and interfere with operations. They are often spread through email attachments and downloads. Viruses operate by slowing computers down, disabling applications, and displaying unusual messages or icons. Two notorious viruses from the late 90s/early 2000s were Melissa and ILOVEYOU, which caused billions in damages and saw their creators prosecuted. Antivirus software detects and removes viruses using virus definitions and behavior analysis, and must be regularly updated as new viruses emerge daily.Today's malware aint what you think
Today's malware aint what you thinkNathan Winters
╠²
This document provides background on Roger Grimes, an InfoWorld contributing editor and security columnist. It then summarizes Grimes' presentation on malware trends, including a brief history of early malware from the 1960s-1980s and trends through the 2000s. It notes that today, malware is primarily trojans and is often spread through deceptive means rather than exploits, as people are tricked into intentionally installing malicious programs. Key points include that many legitimate websites are compromised to spread malware, and that fake anti-virus programs remain a highly effective deception tactic for cybercriminals.Cyber Crime & Security
Cyber Crime & SecurityAnchit Rajawat
╠²
This document discusses cyber crime and security. It begins with an introduction to cyber crime, defining it as criminal acts involving computers. It then covers the history and categories of cyber crime, as well as common types like hacking, cyber terrorism, and denial of service attacks. The document also discusses cyber security, noting its role in preventing online attacks and the importance of keeping software updated. Safety tips are provided, along with statistics on cyber attacks.Video in a Web 2.0 World
Video in a Web 2.0 WorldReligion Communicators Council
╠²
1. The document describes how in 1517, Martin Luther posted his 95 theses criticizing the Catholic Church to the door of the Castle Church in Wittenberg, hoping to spark academic debate.
2. Two friends, Rolf and Stein, see the posting and Stein gets the idea to make hundreds of copies using the new printing press to distribute Luther's ideas more widely.
3. Rolf worries this could start something uncontrollable, like sparking broader debate and societal change, but Stein decides to put the posting back rather than start something they can't control.0926182320 Sophos[1]
0926182320 Sophos[1]guest043f27
╠²
The document summarizes key findings from a 2008 security threat report. It found that malware continues to grow significantly, with over 20,000 new suspicious files detected daily. Spam volumes have declined but remain financially motivated. Phishing now targets social networks in addition to financial information. The web poses the largest threat through SQL injection attacks and compromised websites, which number over 16,000 new pages daily. While malware for Apple and Linux is still low, their market share growth makes them potential future targets. Proactive detection is critical to address evolving threats to users and corporate reputations across all platforms.WhatŌĆÖS All The Buzzafsme
WhatŌĆÖS All The BuzzafsmeMichael Amick
╠²
The document discusses the rapid evolution of technology and its implications for online education, job markets, and information overload. It highlights the exponential growth of knowledge and the importance of adapting to new technologies such as wikis, blogs, and podcasts. Additionally, it emphasizes the need for future job preparedness as 80% of jobs for today's kindergarteners do not currently exist.Web 2.0 Licensed to Kill
Web 2.0 Licensed to KillMike Thornburg
╠²
Web 2.0 allows for increased participation and sharing of information online through things like social media and user-generated content. Real estate is embracing these new technologies, with things like real estate blogs and mashups that combine real estate data from different sources. As bandwidth increases further with Web 3.0, real estate will continue to be reshaped by more immersive experiences online and more intelligent applications. The consumer is driving these changes in how business is done.How spam change the world
How spam change the world Farhaan Bukhsh
╠²
Spam has significantly impacted the world through its role in cybercrime and data breaches. It is used primarily to disseminate malware through malicious emails and is a huge vector for cybercrime. Spammers financially benefit through money, reputation, and in some cases their lives. They utilize botnets, which are networks of infected internet devices, to carry out distributed denial-of-service (DDoS) attacks, send spam emails, and recruit more devices to expand their botnets. Antispam companies try to counter spammers but they are not always successful due to the evolving nature of spam and cybercrime.Kushagra comp ppt.pptx
Kushagra comp ppt.pptxKushagraPal5
╠²
The document provides an introduction to a computer class on internet services. It discusses key terms related to the internet like internet services, why the internet is important for daily life, and common terms like internet, botnet, virus. It includes questions to test understanding of where internet comes from, how botnets are formed, and examples of dangerous viruses. Videos are also mentioned to provide further information on internet, botnets, and viruses."Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.More Related Content
Similar to Spam TV (20)
When web 2.0 sneezes, everyone gets sick
When web 2.0 sneezes, everyone gets sickStefan Tanase
╠²
The document discusses the vulnerabilities and threats posed by Web 2.0 technologies, particularly in relation to social networking platforms. It highlights the rise of malware like the Koobface worm, which utilizes social engineering tactics to spread through various networks. Additionally, it underscores the potential for targeted attacks, privacy issues, and data leakage within social media contexts, stressing the ongoing evolution of cybersecurity challenges in this domain.radhika.pdf
radhika.pdfdharmendra321361
╠²
Computer viruses and worms replicate themselves by inserting copies into other programs or documents. Viruses are pieces of code that piggyback on other programs, while worms are self-contained and use network vulnerabilities to spread. Notable examples include the Morris worm of 1988, which was the first to gain widespread attention, and the MyDoom virus of 2004, which caused major internet disruptions through distributed denial of service attacks. Prevention methods against viruses, worms, and other malware include software updates, antivirus programs, and more secure operating systems.Living In Hi-Tech, Hi-Touch World
Living In Hi-Tech, Hi-Touch WorldCheryl Engle
╠²
The document outlines the evolution of web tools and technologies from first to third generation, emphasizing their applications in enhancing interactivity and collaboration. It discusses various tools, such as email, wikis, and immersive environments, while providing insights into their advantages and limitations. The American Red Cross's vision of utilizing these technologies to streamline service delivery with personal interaction is highlighted throughout the overview.News Bytes by Jaskaran Narula - Null Meet Bhopal
News Bytes by Jaskaran Narula - Null Meet Bhopal Jaskaran Narula
╠²
The document provides a summary of recent hacking and cybersecurity news. It discusses hacks of the NSA and a Ukrainian government customs database that stole classified data. It also mentions the rise of ransomware attacks, a hacking tool called USB Kill that can destroy computers, and issues with the mobile game Pokemon Go accessing locations deemed sacred in some religions. The document provides links to additional information on these and other topics like exploited Linux vulnerabilities and tips for secure Python coding.The Internet
The InternetHugo Antonio
╠²
The document provides an overview of the history and uses of the Internet. It discusses how the Internet was created in the 1960s as a network to share information between computers called ARPANET. It then describes common uses of the Internet like accessing information, entertainment, social networking, and commerce. It also outlines some important websites and programs used to browse the Internet.Features Of The Internet
Features Of The Internetkimromero
╠²
The document provides an overview of several key features and functions of the Internet, including chatting, email, file transfer protocol (FTP), newsgroups, social networking, and telnet. It discusses how chatting allows real-time communication between users, how email is one of the most used functions and can be sent to multiple addresses, and common problems with email like spam and viruses. It also outlines that FTP is used to transfer files, newsgroups are public message boards on specific topics, social networking focuses on online communities, and telnet formerly allowed remote computer access.Information Security - A Discussion
Information Security - A DiscussionKaushik Patra
╠²
The document discusses various aspects of information security in the high-tech era, emphasizing the vulnerabilities of technology, such as hacking, phishing, and social engineering. It highlights the importance of personal responsibility in safeguarding sensitive information and passwords, as well as the effectiveness of technology in creating security measures. Ultimately, the document concludes that security is only as strong as its weakest link and calls for awareness and proactive measures against emerging threats.The malware effects
The malware effectsViral Parmar
╠²
Viral Parmar discusses the history and types of malware, including viruses, trojans, ransomware, and scareware. Some notable ransomware strains described are CryptoLocker, Cryptowall, Locky, and WannaCry. The document also outlines how to create ransomware-as-a-service using the "Tox" kit and provides steps to remove ransomware infections along with decryption tools.10 Worst Computer Viruses of all time
10 Worst Computer Viruses of all timeAlefyaM
╠²
The document lists and describes the 10 worst computer viruses of all time. It discusses viruses such as Melissa, ILOVEYOU, Code Red, Nimda, MyDoom, Sasser, Netsky, Leap-A/Oompa-A, and the number one worst virus, Storm Worm. The viruses caused billions in damages and disrupted systems worldwide by spreading through email and files and exploiting software vulnerabilities.Computer Worms
Computer Wormssadique_ghitm
╠²
This document discusses computer worms, including how they work, types of worms, and examples of major worms. It defines worms as programs that replicate themselves across a network by exploiting security vulnerabilities. The document covers worm target discovery, propagation, activation methods, payloads, examples like Morris worm, Code Red, Nimda, SQL Slammer, and Sobig.f, as well as prevention techniques and current research focus areas.What is a virus and anti virus
What is a virus and anti virusLeonor Costa
╠²
The document discusses viruses and anti-virus software. It provides a 9 point lesson plan on viruses, including what they are, how they spread, their evolution timeline from 1983-2007, statistics on known viruses, the differences between crackers and hackers, and the main types of viruses such as boot viruses, time bombs, worms, and Trojan horses. The goals are to increase knowledge on preventing and combating viruses through behavioral changes.ppt on antivirus and computer virus
ppt on antivirus and computer virusNaveen Goyal
╠²
Computer viruses are software programs that spread from computer to computer and interfere with operations. They are often spread through email attachments and downloads. Viruses operate by slowing computers down, disabling applications, and displaying unusual messages or icons. Two notorious viruses from the late 90s/early 2000s were Melissa and ILOVEYOU, which caused billions in damages and saw their creators prosecuted. Antivirus software detects and removes viruses using virus definitions and behavior analysis, and must be regularly updated as new viruses emerge daily.Today's malware aint what you think
Today's malware aint what you thinkNathan Winters
╠²
This document provides background on Roger Grimes, an InfoWorld contributing editor and security columnist. It then summarizes Grimes' presentation on malware trends, including a brief history of early malware from the 1960s-1980s and trends through the 2000s. It notes that today, malware is primarily trojans and is often spread through deceptive means rather than exploits, as people are tricked into intentionally installing malicious programs. Key points include that many legitimate websites are compromised to spread malware, and that fake anti-virus programs remain a highly effective deception tactic for cybercriminals.Cyber Crime & Security
Cyber Crime & SecurityAnchit Rajawat
╠²
This document discusses cyber crime and security. It begins with an introduction to cyber crime, defining it as criminal acts involving computers. It then covers the history and categories of cyber crime, as well as common types like hacking, cyber terrorism, and denial of service attacks. The document also discusses cyber security, noting its role in preventing online attacks and the importance of keeping software updated. Safety tips are provided, along with statistics on cyber attacks.Video in a Web 2.0 World
Video in a Web 2.0 WorldReligion Communicators Council
╠²
1. The document describes how in 1517, Martin Luther posted his 95 theses criticizing the Catholic Church to the door of the Castle Church in Wittenberg, hoping to spark academic debate.
2. Two friends, Rolf and Stein, see the posting and Stein gets the idea to make hundreds of copies using the new printing press to distribute Luther's ideas more widely.
3. Rolf worries this could start something uncontrollable, like sparking broader debate and societal change, but Stein decides to put the posting back rather than start something they can't control.0926182320 Sophos[1]
0926182320 Sophos[1]guest043f27
╠²
The document summarizes key findings from a 2008 security threat report. It found that malware continues to grow significantly, with over 20,000 new suspicious files detected daily. Spam volumes have declined but remain financially motivated. Phishing now targets social networks in addition to financial information. The web poses the largest threat through SQL injection attacks and compromised websites, which number over 16,000 new pages daily. While malware for Apple and Linux is still low, their market share growth makes them potential future targets. Proactive detection is critical to address evolving threats to users and corporate reputations across all platforms.WhatŌĆÖS All The Buzzafsme
WhatŌĆÖS All The BuzzafsmeMichael Amick
╠²
The document discusses the rapid evolution of technology and its implications for online education, job markets, and information overload. It highlights the exponential growth of knowledge and the importance of adapting to new technologies such as wikis, blogs, and podcasts. Additionally, it emphasizes the need for future job preparedness as 80% of jobs for today's kindergarteners do not currently exist.Web 2.0 Licensed to Kill
Web 2.0 Licensed to KillMike Thornburg
╠²
Web 2.0 allows for increased participation and sharing of information online through things like social media and user-generated content. Real estate is embracing these new technologies, with things like real estate blogs and mashups that combine real estate data from different sources. As bandwidth increases further with Web 3.0, real estate will continue to be reshaped by more immersive experiences online and more intelligent applications. The consumer is driving these changes in how business is done.How spam change the world
How spam change the world Farhaan Bukhsh
╠²
Spam has significantly impacted the world through its role in cybercrime and data breaches. It is used primarily to disseminate malware through malicious emails and is a huge vector for cybercrime. Spammers financially benefit through money, reputation, and in some cases their lives. They utilize botnets, which are networks of infected internet devices, to carry out distributed denial-of-service (DDoS) attacks, send spam emails, and recruit more devices to expand their botnets. Antispam companies try to counter spammers but they are not always successful due to the evolving nature of spam and cybercrime.Kushagra comp ppt.pptx
Kushagra comp ppt.pptxKushagraPal5
╠²
The document provides an introduction to a computer class on internet services. It discusses key terms related to the internet like internet services, why the internet is important for daily life, and common terms like internet, botnet, virus. It includes questions to test understanding of where internet comes from, how botnets are formed, and examples of dangerous viruses. Videos are also mentioned to provide further information on internet, botnets, and viruses.Recently uploaded (20)
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of Deepfakes9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd.
╠²
Artificial Intelligence (AI) is rapidly changing the face of cybersecurity across the globe. In Nepal, the shift is already underway. Vice President of the Information Security Response Team Nepal (npCERT) and Information Security Consultant at One Cover Pvt. Ltd., Sudan Jha, recently presented an in-depth workshop on how AI can strengthen national security and digital defenses.FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
╠²
FIDO Seminar: Perspectives on Passkeys & Consumer Adoptioncnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
╠²
ū×ū©ūøū¢ ūóūÖūæūĢūōūÖūØ ū¬ūóū®ūÖūÖū¬ūÖ ūæūóū£ 3/4/5 ū”ūÖū©ūÖūØ, ūóūō 22 ūöūŚū£ūżūĢū¬ ūøū£ūÖūØ ūóūØ ūøū£ ūÉūżū®ū©ūĢūÖūĢū¬ ūöūóūÖūæūĢūō ūöūōū©ūĢū®ūĢū¬.╠²ūæūóū£ ū®ūśūŚ ūóūæūĢūōūö ūÆūōūĢū£ ūĢū×ūŚū®ūæ ūĀūĢūŚ ūĢū¦ū£ ū£ūöūżūóū£ūö ūæū®ūżūö ūöūóūæū©ūÖū¬/ū©ūĢūĪūÖū¬/ūÉūĀūÆū£ūÖū¬/ūĪūżū©ūōūÖū¬/ūóū©ūæūÖū¬ ūĢūóūĢūō..
ū×ūĪūĢūÆū£ ū£ūæū”ūó ūżūóūĢū£ūĢū¬ ūóūÖūæūĢūō ū®ūĢūĀūĢū¬ ūöū×ū¬ūÉūÖū×ūĢū¬ ū£ūóūĀūżūÖūØ ū®ūĢūĀūÖūØ: ū¦ūÖūōūĢūŚ ūÉūĀūøūÖ, ūÉūĢūżū¦ūÖ, ūĀūÖūĪūĢū©, ūĢūøū©ūĪūĢūØ ūÉūĀūøūÖ.Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
╠²
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...Edge AI and Vision Alliance
╠²
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/key-requirements-to-successfully-implement-generative-ai-in-edge-devices-optimized-mapping-to-the-enhanced-npx6-neural-processing-unit-ip-a-presentation-from-synopsys/
Gordon Cooper, Principal Product Manager at Synopsys, presents the ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOptimized Mapping to the Enhanced NPX6 Neural Processing Unit IPŌĆØ tutorial at the May 2025 Embedded Vision Summit.
In this talk, Cooper discusses emerging trends in generative AI for edge devices and the key role of transformer-based neural networks. He reviews the distinct attributes of transformers, their advantages over conventional convolutional neural networks and how they enable generative AI.
Cooper then covers key requirements that must be met for neural processing units (NPU) to support transformers and generative AI in edge device applications. He uses transformer-based generative AI examples to illustrate the efficient mapping of these workloads onto the enhanced Synopsys ARC NPX NPU IP family.Powering Multi-Page Web Applications Using Flow Apps and FME Data Streaming
Powering Multi-Page Web Applications Using Flow Apps and FME Data StreamingSafe Software
╠²
Unleash the potential of FME Flow to build and deploy advanced multi-page web applications with ease. Discover how Flow Apps and FMEŌĆÖs data streaming capabilities empower you to create interactive web experiences directly within FME Platform. Without the need for dedicated web-hosting infrastructure, FME enhances both data accessibility and user experience. Join us to explore how to unlock the full potential of FME for your web projects and seamlessly integrate data-driven applications into your workflows.From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
╠²
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnŌĆÖt yielding any results, so I expanded my search to second-hand dealer sitesŌĆöonly to realise that periodically checking each one was going to be tedious. ThatŌĆÖs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformŌĆÖs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IŌĆÖll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canŌĆÖt buy a car for youŌĆöyetŌĆöit can certainly help you find the one youŌĆÖre after!PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.Crypto Super 500 - 14th Report - June2025.pdf
Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod
╠²
This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash
╠²
Lessons Learned from Developing Secure AI WorkflowsCapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdf
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdfbiswajitbanerjee38
╠²
Russia is one of the most aggressive nations when it comes to state coordinated cyberattacksŌĆŖŌĆöŌĆŖand Ukraine has been at the center of their crosshairs for 3 years. This report, provided the State Service of Special Communications and Information Protection of Ukraine contains an incredible amount of cybersecurity insights, showcasing the coordinated aggressive cyberwarfare campaigns of Russia against Ukraine.
It brings to the forefront that understanding your adversary, especially an aggressive nation state, is important for cyber defense. Knowing their motivations, capabilities, and tactics becomes an advantage when allocating resources for maximum impact.
Intelligence shows Russia is on a cyber rampage, leveraging FSB, SVR, and GRU resources to professionally target UkraineŌĆÖs critical infrastructures, military, and international diplomacy support efforts.
The number of total incidents against Ukraine, originating from Russia, has steadily increased from 1350 in 2021 to 4315 in 2024, but the number of actual critical incidents has been managed down from a high of 1048 in 2022 to a mere 59 in 2024ŌĆŖŌĆöŌĆŖshowcasing how the rapid detection and response to cyberattacks has been impacted by UkraineŌĆÖs improved cyber resilience.
Even against a much larger adversary, Ukraine is showcasing outstanding cybersecurity, enabled by strong strategies and sound tactics. There are lessons to learn for any enterprise that could potentially be targeted by aggressive nation states.
Definitely worth the read!Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
╠²
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd.
╠²
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...Edge AI and Vision Alliance
╠²
Ad
Spam TV
- 1. Spam TV: Coming soon to a popular Web 2.0 video site near you
- 2. Web 1.0 In the beginning, we had email
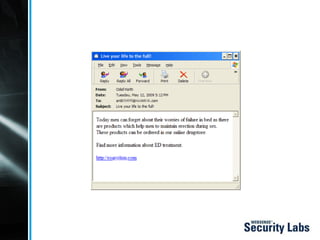
- 3. Web 1.0 Then, we had unsolicited email. Commonly known as spam
- 4. ╠²
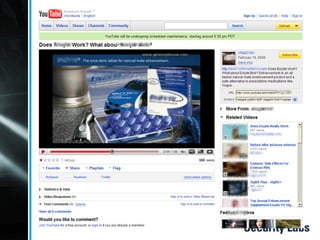
- 5. Web 2.0 In the beginning, we had sites where anybody could comment on anything, share anything, and upload anything to their heartŌĆÖs desire. http://en.wikipedia.org/wiki/User-generated_content
- 6. Web 2.0 Then, came ŌĆ”
- 7. Web 2.0 Then, came ŌĆ”
- 8. Web 2.0 Then, came ŌĆ”
- 9. Spam 2.0 Now, in audio and video!
- 10. Websense ThreatSeeker Network detected this scouring the blogosphere for malicious content
- 11. Spam as a business: win/loss ratio To land just 28 sales of various ŌĆ£male-enhancementŌĆØ products, spammers had to send 350 million spam See Univ. Calif. San Diego research for more info: http://www.cs.ucsd.edu/~savage/papers/CCS08Conversion.pdf
- 12. DonŌĆÖt be that 1 out of 28 who subjects 350 million others to spam! ’üŖ
