Spoofing Techniques
- 1. SPOOFINGATTACKPRESENTED BY: S.M RAZA SAJJAD
- 2. AgendaSpoofingTypes of Spoofing IP Spoofing
- 3. URL spoofing
- 6. E-mail Address SpoofingSpoofingIn the context of network security, a spoofing attack is a situation in which one person or program successfully masquerades as another by falsifying data and thereby gaining an illegitimate advantage.An attacker alters his identity so that some one thinks he is some one else
- 7. Types of SpoofingIP SpoofingURL spoofingReferrer spoofingCaller ID spoofingE-mail Address Spoofing
- 8. IP SpoofingDefinition:Attacker spoofs the address of another machine and inserts itself between the attacked machine and the spoofed machine to intercept repliesthus gaining access to all messages in both directions without the trouble of any cryptanalytic effort. The attacker must monitor the packets sent from Alice to Bob and then guess the sequence number of the packets. Then the attacker knocks out Alice and injects his own packets, claiming to have the address of Alice.From Address: 10.10.20.30To Address: 10.10.5.5Attacker intercepts packetsas they go to 10.10.20.30Replies sent back to 10.10.20.30John10.10.5.5Attacker10.10.50.50
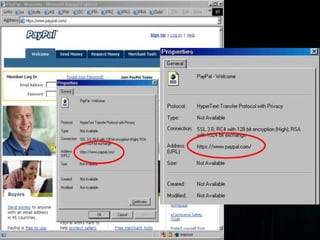
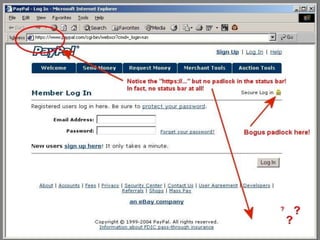
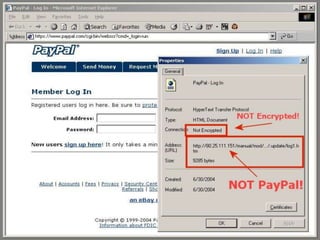
- 9. URL Spoofing and PhishingAnother kind of spoofing is "webpage spoofing," also known as phishing. In this attack, a legitimate web page such as a bank's site is reproduced in "look and feel" on another server under control of the attacker. The main intent is to fool the users into thinking that they are connected to a trusted site, for instance to harvest user names and passwords.This attack is often performed with the aid of URL spoofing, which exploits web browser bugs in order to display incorrect URLs in the browsers location bar; in order to direct the user away from the legitimate site and to the fake one. Once the user puts in their password, the attack-code reports a password error, then redirects the user back to the legitimate site.
- 13. Referrer SpoofingReferrer spoofing or ref tar spoofing is the sending of incorrect referrer information in an HTTP request, sometimes with the aim of gaining unauthorized access to a web site. It is also used to improve the privacy of an individual using a web browser to view World Wide Web sites, by replacing valid referrer data with incorrect data, though most users simply suppress their web browser from sending referrer data, and may also modify other HTTP headers.
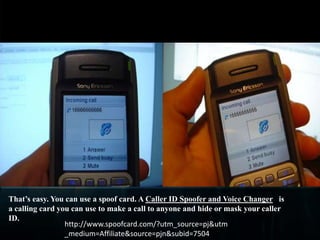
- 14. Caller ID SpoofingIn public telephone networks, it has for a long while been possible to find out who is calling you by looking at the Caller ID information that is transmitted with the call. There are technologies that transmit this information on landlines, on cell phones and also with VoIP. Unfortunately, there are now technologies (especially associated with VoIP) that allow callers to lie about their identity, and present false names and numbers, which could of course be used as a tool to defraud or harass. Because there are services and gateways that interconnect VoIP with other public phone networks, these false Caller IDs can be transmitted to any phone on the planet, which makes the whole Caller ID information now next to useless
- 15. That’s easy. You can use a spoof card. A Caller ID Spoofer and Voice Changeris a calling card you can use to make a call to anyone and hide or mask your caller ID.http://www.spoofcard.com/?utm_source=pj&utm_medium=Affiliate&source=pjn&subid=7504
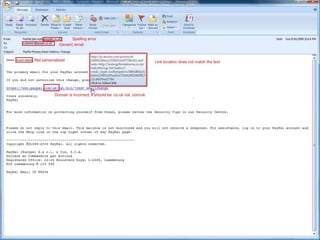
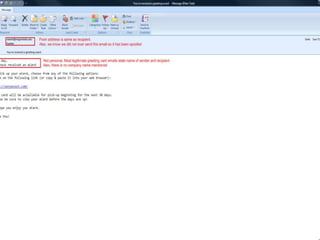
- 16. E-mail Address SpoofingThe sender information shown in e-mails (the "From" field) can be spoofed easily. This technique is commonly used by spammers to hide the origin of their e-mails and leads to problems such as misdirected bounces (i.e. e-mail spam backscatter).E-mail spoofing is a term used to describe (usually fraudulent) e-mail activity in which the sender address and other parts of the e-mail header are altered to appear as though the e-mail originated from a different source.By changing certain properties of the e-mail, such as the From, Return-Path and Reply-To fields (which can be found in the message header), ill-intentioned users can make the e-mail appear to be from someone other than the actual sender. The result is that, although the e-mail appears to come from the address indicated in the From field (found in the e-mail headers), it actually comes from another source.
- 19. ConclusionsComputer Security is a continuous battleAs computer security gets tighter hackers are getting smarter