??? ??? ????? ??????? ? ???????? ? ????????? ? ????? ???? ??????? ???? ??????? ??????? ?? ??????
- 1. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????? ????????????????? ???????????????? ????????? ?????? ??????? ??????/ ?????????????????? /?????????????????????? ???????? ???? ???? ???????? ????????????? ??????????? ?????? ???????? ???????????????? ???????: ??????? ???? ?????????????? ?????????? ????????????????????? ??????? ????????? ??????????? ??????? ???????? ???????????? ??????: ??????????????)??????? ?(??????????????)?????????? ?(?????????????? ?(????? ??????? ???? )????????????????? ?????? ???? ?????? ?????? ????????????? ??????? ??????? ?????? ?????? ????????? ??????? ???????? ?????????????? ???????? ????????? .?????????? ???????????????? ???????(????????? ????????? ?????¨C????????? ????????¨C??????????????? ????¨C ??????????)??????????(???????? ????????? ?????? ????¨C??????????¨C)??????????????? ????? ????????? ???????? ????? ?????? ?????? ????? ????? ?????? ???? ????????? ??????? ????? ????? ?????????? ????????? ????? ????? ???????? ??????? ???????????????????? ????? ?????? ???????? ??????/????????? ???????? ??????? ?????????? ??????? ??????? ???? ???????? ?????? ????????? ?????????? ???????? ???????? ?????? ???????? ???????? ?????? ????? ???????? ??????? ?????? ????? ???????? ????? ???????
- 2. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com : ??????? ???????? ?????? ???? ????? ????????? ????????? ?????? ?????? ?????? ?????
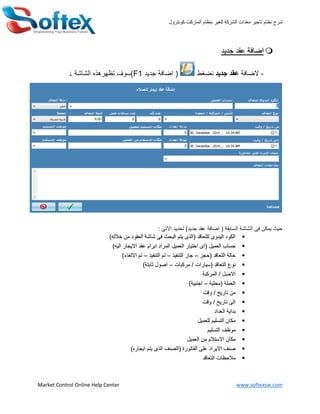
- 3. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ?????? ????????????? -?????????????????????????)?????? ???????F1???????? ????????? ?)????? ????????? ???????? ???? ?????? ?????): ??????? ??????? )?????? ????? ??????? ?????????? ???????? ???????)??????? ???? ???????? ?????? ???? ??????? ????? ?(????? ????????? ??????)?????? ????????? ????? ??????? ???????? ???????? ???????? ?(??? ?????????? ???????(????¨C????????? ?????¨C????????? ????¨C)????????? ???? ?????????? ??????(???????/????????¨C)??????? ?????? ????????/????????? ??????????(??????¨C)???????? ???????? ????/????? ???????? ?????/????? ????????? ??????? ????????? ????????? ?????? ?????????? ?????? ????????? ???? ?????????? ?????? ?)???????? ????? ?????? ?(?????? ?????????? ????? ????????? ????? ?????????? ?????????
- 4. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????? ????? ??????????????? ????? ????????????? ????????? ???????? ?????? ???? ???????? ???????? ?????? ???? ????? ???????? ????? ??????? :????????? ????? ????????? ???????? ???? ?(??????? ????????? ????? ????? ??????/???????/???? ?????? ????? ????? ??????? ????? ???? ????? )????? ????? ??????? ?????????????Right Click: ???????? ????????? ?????? ????? -)??????? ???????? ?????? ???? ????? ?????? ?(???? ????????? ????????
- 5. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com -???? ???????)??????? ???????? ?????? ???? ????? ????????? ??????? ?????? ?(???? ??????? -)????????? ????? ?????? ?(???? ????????? ?????
- 6. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com -????? ????? ?????????? ?????? ??????? ??????? ?????? ?????????(???? ????????? ????????? ????????) ???? ??????? ????????????? ????? ?????? ????? ????????? ????????? ???????? ??? ??????? ????? ??????? ???????? ??????? ??????? ???????? ???????????????? ????????? ???? ??????? ??? ??????? ???? ?????? ??? ?????????? ??????? ????? ?(???? ??????? ????? ???? ????? ) ?????? ???? ???????? ?????? -?????????????????????????)?????? ???????F1???????? ????????? ?)?????
- 7. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????)???? ??????? ????????? ?????? ????? ???? ??????? ??????? ???????? ?????? ?(????? ???????? ????? ?????? ????? ???????? ??????? ??????? ?????????????? ?????? ???????? ????? ???: ??????? ???????? ?????? ???? ?????
- 8. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ???????? ??????????????????? ?????????????????? ???????? ?????? -?????? ??????????????? ????????/.?????????? ????????? ??????? ????? ???????????? ????????????? ??????( ??????????????? ????????????????? ?(????? ???? ????? )????????? ????????(??????? ) ????????????????? ?????? ???? ????? )?
- 9. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com -?????? ??????(????? ??????????????????????????????? ?????? ???? ????? )??????????? ?????? ????? ??????? ?????????????? ???????????)?????? ???????F1????? ????????? ????? )??????
- 10. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com : ??????? ??????? ????? ) ???????? ?????? ???? ?????? ????? ?(?????? ???????? ????? ???? ?)??????????? ???? ????????? ????????? ( ??????? ????? ?)?????????? ?????? ???? ????????? ?????? ???????? ??????? ( ?????????? ??????? ?????????? ???????? ?????????? ???????)?????????? ?????? ???? ????????? ?(????? ?)?????????? ?????? ???? ????????? ?(????? ????????? ??????? ?????????? ??????? ??????????? ????????? ???????? -??????? ????????? ???????? -???????? ?????? -% ????????? ????????? -???????? ??????? -????????? ??????? ??????? ??????? ????????? ????????? ?????? ?(???? ????????? ???????) ???????? ???????? ??? -?????? ????? -???????? ????? ?) ??????? ???? ??????? ???? ?????? ?(??? ??????? ??????? ?????? ??????/????? ?????? ?????? ????? ???? ??????? ???? ??????????? ????? ??????? ?(?????? ??????? ????? ) ??????? ??????????????? ?????)????????? ?(??????????? ???????????? ???? ????? ??????? ?????????
- 11. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ???????? ?????????????.?????????????????????????????? ???????? ??????????? ?????????????????/????????? ??????( ??????????????? ?????????????????(?? ).?(??????? ???? ????? )?????????? ????????? ??????????? ?????????????????? ?????? ???? ????? )?
- 12. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com -???????? ?????? ???? ????? )??????????? ?????????? ?(??????? ?????? ?????? ??????
- 13. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ???????? ???????/?????????????? ????????????????/????? ?????????????????)?????? ???????F1????????? ????? ) ????????? : ??????? ??????? ????? ) ??????? ??????? ?(?????? ???????? ????? ???? ?????????? ????? ??????????? ??????? ?????????? ????? ???????? ?????
- 14. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ?????????? ????? ??????????? ????? ????????? ????? ?????????? ????? ????????? ??????? ????????? ????? ?????????? ??????? ??????? ????? ???? ????????? ??????? ?????? ??????/????? ?????? ????????????? ????????????????????? ???????? ?????? ???? ??????
- 15. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????? ????????????????? ??????????????? ???????? ??????????????????????? ???????? ??? ??????????????????? ???? ??????? ???????????????? ?????? ??????????????? ????? ????: ???????? ???????? ?????/?????????? ???????? ?????????????)??????? ?(??????????????)?????????? ?(?????) ?????????? ?(??????? ??????? ???? ???????? ?????? ???? ?????? ???????? ?????? ???? ????? ?????????? ???????? ?????? ?????? ??????
- 16. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com : ??????? ??????? ????? ) ???????? ?(??????? ????????? ????? ???? ????????? ?????) ????????? ??????? ???? ????????? ?(???? ????????? ??????)???????? ????? ??????? ????? ?????? ( ??????????? ?????? ?) ??????? ??????? ???? ??????????? ????? ???????? ?(?????? ??????????? ?????????? ??????? ???? ????? ????????? ?????????????? ??????? ??????? ????? ????????? ?????????(???????/?????? ????????? ??????? ???? ????????? ????? )????? ???????? ??????????: ??????????????(????????)?????????????????? ?????? ?????????????)?????????? ??????? ?(????????????? ???? )????????? ????????? ????????? ???? ????????? ?(?????????????? ?????? ???? ??????
- 17. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ?????? ?????? ?????(????????? ??????): ??????? ???????? ?????? ???? ????? ???????? ?????? ???????? ???? ?????? ????? ???????????? ??????? ????????? ?????? ???????? ????????? ??????? ????? ????????? ????? ????? ?(????????? ?????????/??????? ???????? ?????? ???? ????? )???????
- 18. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ????????????????? ??????? ?????? :????? ?????????????? ????????? ?????? ???? ?????? ????????? ?????: -???????(??? ????????? ?????????? ?????? ???? )???????? ?(???????? ??????????? )?????????? ??????? ????? ???????? ?????? ???? ????? ) ????????? ????????? ????????? ???? ????????? ???? ?(?????? ????????
- 19. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????? ????????????????????????????????? ????????? ?????? ????????????? ???? ?????????? ????????? ???????????? ????? ??????: ????? ????? ???????? ???? ?????????? ?????????? ????????? ?????? ???????? ???????? ??????????????)??????? ?(??????????????)?????????? ?(?????????????? ?(????? ??????? ???? )????????????????? ?????? ???? ?????? ?????? ?????? ?????: ??????? ???????? ?????? ???? ????? ????????? ????????? ??????
- 20. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com : ??????? ???????? ?????? ???? ????? )????????? ????????? ?(????? ??????? ????? ?????? ??????? ???????? ?????? ???? ????? ?????????? ??????? ?????? ?????? ?????
- 21. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com : ???????? ?????????? ???????? ?????? ?????????? ???????(???????/???????/???????/)??????? ?????????? ??????(???????/)??????? ?????? ????????/????????? ????????? ????? ?????????? ?????? : ??????? ???????? ?????? ???? ????? ????????? ?????? ?????
- 22. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ?????? ????????????????? ???????????????? ?????? ??????????????? ??????????? ???? ?????? ??????????????)?????? ?(????????????????) ????????? ?????? ???????? ?(?????????? ????? ???????? ???????
- 23. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????? ???????? ?????? ???? ????? ????????? ?????? ?????? ????? ????????? ???? ????????????? ???? ???????? ????? ???????? : ??????? ???????? ?????? ???? ????? ??????????? ?????? ?????
- 24. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ?????? ?????????????????? ?????? ???????? ??????? : ??????? ???????? ?????? ???? ????? ????????? ?????? ????? ????????? ???????? ???????? ?????? ???????? ??????????????)?????? ?(????????????????) ????????? ?????? ???????? ?(?????????? ????? ???????? ???????
- 25. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????? ???????? ?????? ???? ????? ????????? ?????? ?????? ????? ????????? ???? ????????????? ???? ???????? ????? ????????
- 26. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com : ??????? ???????? ?????? ???? ????? ??????????? ?????? ????? ????? ??????: ??????? ???????? ?????? ???? ????? ???????? ?????? ????? ????(?????????? ????????? ??????? ????? ?????? ???? ????? ?????¨C??????????????¨C)????????? ?????? ??????? ???????? ?????? ???? ????? ??????? ????? ???? ?????? ???? ????????
- 27. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ?????? ?????????????????? ?????? ???????? ??????? ??????? ???????? ?????? ???? ????? ????????? ??????? ??????? ????? ????????? ?????? ????????/???? ?????????? ??????????????)?????? ?(????????????????) ????????? ?????? ???????? ?(?????????? ????? ???????? ???????
- 28. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ??????? ???????? ?????? ???? ????? ????????? ?????? ?????? ????? ????? ????????? ?????? ???????? ?(?????? ???????? )?????????? ????????? ?(?????? ??????? ????? ?????? : ??????? ???????? ?????? ???? ????? )??????? ?????????
- 29. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ????????? ???? ????????????? ???? ???????? ????? ???????? ??? ?????? ???? ????? ??????????? ?????? ?????: ??????? ??????? ????? ??????: ??????? ???????? ?????? ???? ????? ???????? ?????? ?????
- 30. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ????(?????????? ????????? ??????? ????? ?????? ???? ????? ?????¨C????????? ?????¨C)????????? ?????? ??????? ???????? ?????? ???? ????? ??????? ????? ???? ?????? ???? ???????? ??????? ???????? ?????? ???? ????? ????????? ???????
- 31. ???????????? ???????? ??????? ??????? ??????????????? ????????? ??????? Market Control Online Help Center www.softexsw.com ????? ????????? ?????? ???? ??????????? ???? ?????????????? ??????? ?????????????? ???????? ??? ERP-control-http://softexsw.com/ar/market ????????? ???? ??????? ??????????????? ?????????????? ??????????????? ????? sales@softexsw.com ??????????? ??? ????????? ??????? ??????? ??????? ????? ???? support@softexsw.com ????? ?????????? ???? ??????? ????????? ???????? ???????? ??????? ???????? ???????? ??????? ??????? ????? w.comwww.softexs ???????? ???? ????????? ????????? ?????? ??????????? ??????