Steganography
- 2. PRESENTED BY Presented To Teacher Name University Name Name 1 161-15-0000 Name 2 161-15-0001 Name 3 161-15-0002 Name 4 161-15-0003 Name 5 161-15-0004 Name 6 161-15-0005
- 3. WHAT IS STEGANOGRAPHY? Steganography is data hidden within data. Steganography is an encryption technique that can be used along with cryptography as an extra-secure method in which to protect data.
- 4. MAIN CONCEPT OF STEGANOGRAPHY Cover File (image, video or audio) Data to hide (text, image, video, audio, etc.) Stego Application Stego File
- 5. TYPES OF STEGANOGRAPHY ïAudio Steganography ïVideo Steganography ïText Steganography ïImage Steganography
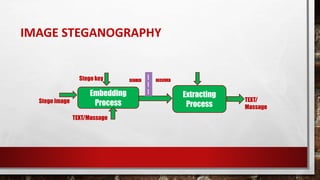
- 10. Embedding Process Extracting ProcessStego Image TEXT/Massage Stego key TEXT/ Massage | | | SENDER RECEIVER IMAGE STEGANOGRAPHY
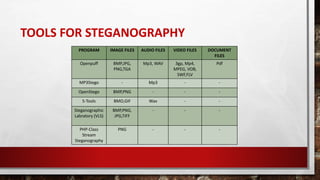
- 11. PROGRAM IMAGE FILES AUDIO FILES VIDEO FILES DOCUMENT FILES Openpuff BMP,JPG, PNG,TGA Mp3, WAV 3gp, Mp4, MPEG, VOB, SWF,FLV Pdf MP3Stego - Mp3 - - OpenStego BMP,PNG - - - S-Tools BMO,GIF Wav - - Steganographic Labratory (VLS) BMP,PNG, JPG,TIFF - - - PHP-Class Stream Steganography PNG - - - TOOLS FOR STEGANOGRAPHY
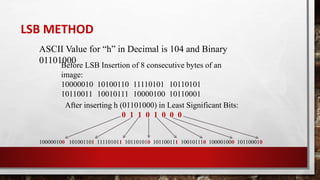
- 12. LSB METHOD ASCII Value for âhâ in Decimal is 104 and Binary 01101000Before LSB Insertion of 8 consecutive bytes of an image: 10000010 10100110 11110101 10110101 10110011 10010111 10000100 10110001 After inserting h (01101000) in Least Significant Bits: 0 1 1 0 1 0 0 0 100000100 101001101 111101011 101101010 101100111 100101110 100001000 101100010
- 13. ADVANTAGES ïķ It is used in the way of hiding not the information but the password to reach that information. ïķ Difficult to detect. Only receiver can detect. ïķ Can be applied differently in digital image, audio and video file. ïķ It can be done faster with the large number of software's.
- 14. DISADVANTAGES ïķ Huge number of data, huge file size, so someone can suspect about it. ïķ If this technique is gone in the wrong hands like hackers, terrorist, criminals then this can be very much dangerous for all.
- 15. Steganalys is DETECTING THE SECRET MESSAGE
- 16. CONCLUSION ïķ Though Steganography is not implemented in wider ways but it can be the best security tool. ïķ The main problem of todayâs world is to secure their data confidentially, the techniques used currently are not considered the best which can only be replaced by Steganography.
- 17. ANY QUESTION ? ? ?