Syscloud Release Notes - Q1, 2017
- 1. Syscloud Release Notes Q1, 2017
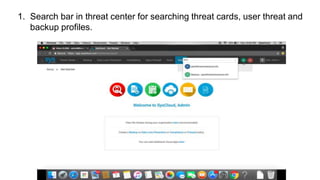
- 2. 1. Search bar in threat center for searching threat cards, user threat and backup profiles.
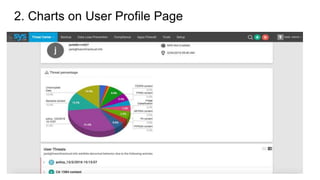
- 3. 2. Charts on User Profile Page
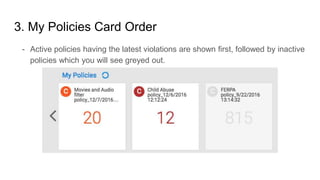
- 4. 3. My Policies Card Order - Active policies having the latest violations are shown first, followed by inactive policies which you will see greyed out.
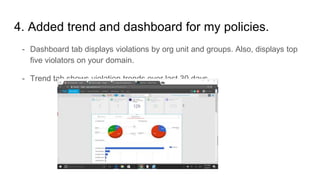
- 5. 4. Added trend and dashboard for my policies. - Dashboard tab displays violations by org unit and groups. Also, displays top five violators on your domain. - Trend tab shows violation trends over last 30 days.
- 6. 5. Play/Pause Changes for Threat Cards Policies - Changed play/pause to toggle button with Red and green colors. - Toggle buttons are always visible . if any policy is active, protected (green) is shown , else all are deactivated . - Next to toggle button a clickable count of number of policies is displayed. Click on the count redirects to policy creation/modification page. - Removed Policies and Incidents tab as all details are moved to Threat details page.
- 7. 6. Additional Notes - File level auto encryption is now supported. - The file will be automatically encrypted again after modification. The file owner has the option to select if they would like the file to remain encrypted upon decrypting. - New card introduced to show unencrypted sensitive documents under Syscloud recommends - Overriding the end user settings for custom admins - Custom admins privileges will override end user privileges. - Trash folder backup for drive.