The Art of War - Hacking Lifecycle
- 2. 2
- 3. 3 ╩╝ėŗ Waging war (ū„æ) Strategic attack (ų\╣ź) Disposition of the army (▄Ŗą╬) Forces (▒°ä▌) Weaknesses and strengths (╠ōīŹ) Military manoeuvres (▄ŖĀÄ) Variations and adaptability (Š┼ūā) Movement and development of troops (ąą▄Ŗ) Terrain (Ąžą╬) The nine battlegrounds (Š┼Ąž) Attacking with fire (╗╣ź) Intelligence and espionage (ė├ķg)
- 4. 4
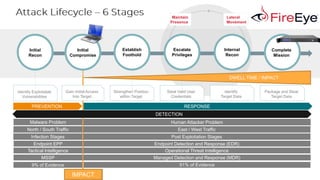
- 5. BREACHIMPACT Infection Stages Post Exploitation Stages Strengthen Position within Target Establish Foothold Package and Steal Target Data Complete Mission Initial Compromise Lateral Movement Maintain Presence Initial Recon Steal Valid User Credentials Escalate Privileges Identify Target Data Internal Recon Identify Exploitable Vulnerabilities Gain Initial Access Into Target PREVENTION DWELL TIME / IMPACT RESPONSE DETECTION Malware Problem Human Attacker Problem Endpoint EPP Endpoint Detection and Response (EDR) Tactical Intelligence Operational Threat Intelligence MSSP Managed Detection and Response (MDR) North / South Traffic East / West Traffic 9% of Evidence 18% 7% 52% 14%91% of Evidence
- 6. 6
- 7. 7 ? ? ? ?
- 8. 8
- 9. 9
- 10. 10
- 11. 11
- 12. 12
- 13. 13
- 15. 15