The World's First Cyber Weapon - Stuxnet
- 1. The World’s First Cyber Weapon – Stuxnet Sean Xie Apr 2019 SET SAVE = L 6.1 L 1 T DB888.DBW614 L *IN0 L 30 ***I JCN M001 A DBX 696.3 JCN M002 L 146
- 2. Discovery Of the First Cyber Weapon ①Target Specific SCADA System Siemens WinCC & Step 7 U.S. & Israel Operation Olympic Games • Discovered in Jun 2010 by VirusBlokAda in Belarus • Named by Symantec Revealed in 2012 by The New York Times ④Purpose: Sabotage Iran’s Nuclear Program by Physically Damage Centrifuges ③Target Iran’s Uranium Enrichment Process at Natanz Fuel Enrichment Plant ②Target Specific Programmable Logic Controllers (PLC) S7-400 S7-300 Gas Centrifuge
- 3. High Level Architecture Overview Of The Target 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Cascade 164 Centrifuges PLC S7-315 PLC S7-415 WinCCWinCC Step7 IT Network Layer Industrial Control Layer Highly secure and isolated network behind multiple Firewalls without Internet connection Plant Layer Feed To waste Stage Exhaust Valves Product Tail Stage Fuel Enrichment Process Production Scheduling & Control Plant Supervisory & Direct Control S C A D A Monitors in the Cascade Hall Field Level Frequency Converter Communication ProcessorsPROFIBUS Network…… Pressure Transducers/Sensors Isolation Valves/Control Valves …… …… …… Pressure Controller…… …… Feed Product Tail • There are three cascade modules installed at Natanz • Each cascade module consists of 18 cascades • Six cascades (984 centrifuges) constitute a sub-unit sharing one feed, one production, and one tails Cascade Module
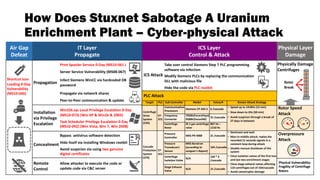
- 4. ICS Layer Control & Attack Air Gap Defeat IT Layer Propagate How Does Stuxnet Sabotage A Uranium Enrichment Plant – Cyber-physical Attack Win32k.sys Local Privilege Escalation 0-Day (MS10-073) (Win XP & Win2k & 2003) Task Scheduler Privilege Escalation 0-Day (MS10-092) (Win Vista, Win 7, Win 2008) Installation via Privilege Escalation Propagate via network shares Peer-to-Peer communication & update Print Spooler Service 0-Day (MS10-061 ) Server Service Vulnerability (MS08-067) Propagation Infect Siemens WinCC via hardcoded DB password Bypass antivirus software detection Hide itself via installing Windows rootkit Avoid suspicion via using two genuine digital certificates Concealment Remote Control Allow attacker to execute the code or update code via C&C server PLC Attack Modify Siemens PLCs by replacing the communication DLL with malicious file Hide the code via PLC rootkit ICS Attack Take over control Siemens Step 7 PLC programming software via infection Target PLC Sub Controller Model Value/# Known Attack Strategy Centrifuge Drive System (CDS) S7- 315 Communication Processors Siemens CP-342-5 6 /cascade • Speed up to 1410Hz (15 min) • Slow down to 2Hz (50 min) • Avoid suspicion through a break of 27 days in between Frequency Converter 7050h(FararoPaya) 9500h(VaconNX) 31 /cascade Centrifuge Rotor IR-1 gas centrifuge rotor 807 Hz – 1210 Hz Cascade Protection System (CPS) S7- 415 Pressure Controller MKS PR-4000 21 /cascade • Dominant and wait • Man-in-middle attack: replay the recorded 21 seconds signals in a constant loop during attack • Disable manual shutdown of the system • Close isolation valves of the first two and last two enrichment stages • Close stage exhaust valves affecting 110 centrifuges out of 164/cascade • Avoid catastrophic damage Pressure Transducer/ Sensor MKS Baratron (according to Langner’s Report) 164 /cascade Centrifuge Isolation Valve N/A 164 * 3 /cascade Stage Exhaust Valve N/A 15 /cascade Shortcut Icon Loading 0-Day Vulnerability (MS10-046) Physical Layer Damage Physically Damage Centrifuges Overpressure Attack Rotor Speed Attack Rotor Break Physical Vulnerability: Fragility of Centrifuge Rotors
- 5. Summary • First computer worm to attack SCADA system • First computer worm to attack PLC devices • First computer worm to exploit multiple 0-day vulnerabilities • First computer worm to use genuine digital certificates (compromised) • First computer worm to cause industrial devices physical damage • Opens new era of Cyber War • Demonstrates a method to attack a hard target by breaking through air-gap • Demonstrates a methodology for cyber-physical attack “A textbook example of Cyber Warfare” – Ralph Langner
- 6. References 1. Falliere, N., Murchu, L. O., & Chien, E. (February 2011). W32.Stuxnet Dossier. Synamtec Security Response Paper. 2. Langner, R. (November 2013). To Kill a Centrifuge. The Langner Group. 3. Gibney, A. (Director). (2016). Zero Days [Documentary Film]. 4. Sanger, D. E. (2012, June 1). Obama Order Sped Up Wave of Cyberattacks Against Iran. Retrieved from The New York Times: https://www.nytimes.com/2012/06/01/world/middleeast/obama-ordered-wave-of- cyberattacks-against-iran.html 5. Sanger, D. E. (2012). Confront and Conceal: Obama's Secret Wars and Surprising Use of American Power. Penguin Random House LLC. 6. GReAT. (2014, November 11). Stuxnet: Zero victims. Retrieved from Securelist | Kaspersky Lab's cyberthreat research and reports: https://securelist.com/stuxnet-zero-victims/67483/ 7. Albright, D., Brannan, P., & Walrond, C. (February 16, 2011). Stuxnet Malware and Natanz: Update of ISIS December 22, 2010 Report. Institute for Science and International Security. 8. Gross, M. J. (2011, March 2). A Declaration of Cyber-War. Retrieved from Vanity Fair: https://www.vanityfair.com/news/2011/03/stuxnet-201104?verso=true





![References
1. Falliere, N., Murchu, L. O., & Chien, E. (February 2011). W32.Stuxnet Dossier. Synamtec Security
Response Paper.
2. Langner, R. (November 2013). To Kill a Centrifuge. The Langner Group.
3. Gibney, A. (Director). (2016). Zero Days [Documentary Film].
4. Sanger, D. E. (2012, June 1). Obama Order Sped Up Wave of Cyberattacks Against Iran. Retrieved from
The New York Times: https://www.nytimes.com/2012/06/01/world/middleeast/obama-ordered-wave-of-
cyberattacks-against-iran.html
5. Sanger, D. E. (2012). Confront and Conceal: Obama's Secret Wars and Surprising Use of American Power.
Penguin Random House LLC.
6. GReAT. (2014, November 11). Stuxnet: Zero victims. Retrieved from Securelist | Kaspersky Lab's
cyberthreat research and reports: https://securelist.com/stuxnet-zero-victims/67483/
7. Albright, D., Brannan, P., & Walrond, C. (February 16, 2011). Stuxnet Malware and Natanz: Update of ISIS
December 22, 2010 Report. Institute for Science and International Security.
8. Gross, M. J. (2011, March 2). A Declaration of Cyber-War. Retrieved from Vanity Fair:
https://www.vanityfair.com/news/2011/03/stuxnet-201104?verso=true](https://image.slidesharecdn.com/worldsfirstcyberweaponseanxie-190428230408/85/The-World-s-First-Cyber-Weapon-Stuxnet-6-320.jpg)