1 of 7
Download to read offline







Recommended
GeneticAlgorithms_AND_CuttingWoodAlgorithm 



GeneticAlgorithms_AND_CuttingWoodAlgorithm kinan keshkeh
Ěý
Genetic Algorithms _AND_ Cutting Wood AlgorithmA NEW PROPOSED SYMMETRIC KEY ALGORITHM FOR MODERN CRYPTOGRAPHIC



A NEW PROPOSED SYMMETRIC KEY ALGORITHM FOR MODERN CRYPTOGRAPHICijsrd.com
Ěý
This document describes a new proposed symmetric key encryption algorithm. It begins with background on cryptography and then describes the new algorithm. The algorithm encrypts text by taking the ASCII value of each character, reversing the 8-bit binary representation, dividing this by a 4-digit key, and storing the remainder in the first 3 digits and quotient in the next 5 digits to form the ciphertext. It provides an example of encrypting the character 'T' using this process. The document suggests this algorithm is easy to implement and more secure than existing algorithms due to using a reversal operation during encryption.Elementry Cryptography



Elementry CryptographyTata Consultancy Services
Ěý
Basic of Elementry Cryptography. Types of cryptography & broad categorization of Encryption algorithmFundamentals of cryptography



Fundamentals of cryptographyHossain Md Shakhawat
Ěý
Introduction to Cryptography, Fundamentals of cryptography, Encryption, Decryption, Plaintext, Ciphertext, Public key cryptography, Secret key cryptography, steam cipher, block cipher, transposition cipher, security of cryptographic algorithm, cipher attack,8051 microcontroller lecture ppt by Tarun Khaneja ( 9034406598 )



8051 microcontroller lecture ppt by Tarun Khaneja ( 9034406598 )Tarun Khaneja
Ěý
The document discusses the 8051 microcontroller. It describes the basic components of the 8051 including 4K bytes of internal ROM, 128 bytes of internal RAM, four 8-bit I/O ports, two 16-bit timers/counters, and one serial interface. It provides a block diagram of the 8051 and discusses important pins such as the I/O ports, PSEN, ALE, EA, RXD, TXD, and XTAL1 and XTAL2. It also gives examples of how the 8051 is used in embedded systems and describes methods for connecting an external clock source to the 8051.Idea (international data encryption algorithm)



Idea (international data encryption algorithm)Arofiah Hidayati
Ěý
Idea (international data encryption algorithm)Caesar cipher



Caesar cipherRamadhi Irawan
Ěý
The Caesar cipher is one of the earliest known substitution ciphers. It works by shifting each letter in a plaintext message by a set number of positions (the key) in the alphabet to encrypt it. For example, with a key of 3, A would be replaced by D, B by E, and so on. Decryption simply requires shifting letters in the opposite direction by the same key. While simple, the Caesar cipher has some mathematical properties and was allegedly used by Julius Caesar to communicate with his army. However, it is also easy to break through brute force by trying all 26 possible keys.Idea(international data encryption algorithm)



Idea(international data encryption algorithm)SAurabh PRajapati
Ěý
The document discusses the International Data Encryption Algorithm (IDEA). It was developed in 1990 as a replacement for the Data Encryption Standard. IDEA is a symmetric block cipher that uses a 128-bit key to encrypt 64-bit blocks of plaintext into ciphertext. The key is divided into 52 subkeys that are used in 8 rounds of encryption/decryption operations involving XOR, addition, and multiplication. IDEA was used in PGP v2.0 and can encrypt sensitive data for applications like financial services, broadcasting, and government use.Cipher techniques



Cipher techniquesMohd Arif
Ěý
The document provides an overview of cipher techniques including:
- Classical techniques like transposition ciphers, substitution ciphers including the Caesar and Playfair ciphers, and polyalphabetic ciphers like the Vigenere cipher.
- Modern techniques like stream ciphers which encrypt bits one at a time using a pseudorandom keystream, and block ciphers which encrypt blocks of text.
- It also discusses cryptanalysis techniques for analyzing ciphers and discusses how to build more secure systems using techniques like the one-time pad or combining multiple ciphers.Cryptography



CryptographyDarshini Parikh
Ěý
Cryptography is the practice and study of securing communication through techniques like encryption. It has evolved through manual, mechanical, and modern eras using computers. Cryptography aims to achieve goals like authentication, confidentiality, integrity, and non-repudiation. Common attacks include brute force, chosen plaintext, and differential power analysis. Symmetric cryptography uses a shared key while asymmetric uses public/private key pairs. Digital signatures and watermarks can authenticate documents. DRM and watermarks control digital content distribution.Cryptography



CryptographySidharth Mohapatra
Ěý
Cryptography is the science of using mathematics to encrypt and decrypt data.
Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anyone except the intended recipient.
Cryptography



CryptographyShivanand Arur
Ěý
This PPT explains about the term "Cryptography - Encryption & Decryption". This PPT is for beginners and for intermediate developers who want to learn about Cryptography. I have also explained about the various classes which .Net provides for encryption and decryption and some other terms like "AES" and "DES".Cryptography.ppt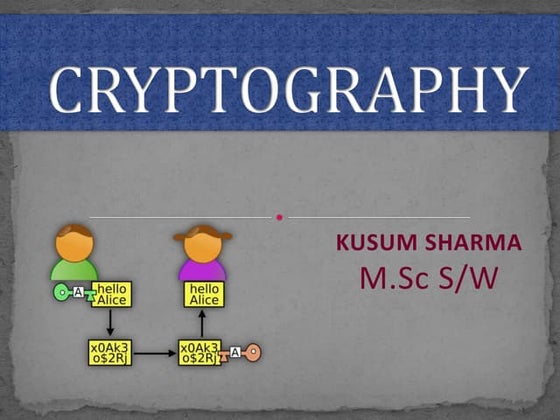



Cryptography.pptkusum sharma
Ěý
This document provides an overview of cryptography. It defines cryptography as the science of securing messages from attacks. It discusses basic cryptography terms like plain text, cipher text, encryption, decryption, and keys. It describes symmetric key cryptography, where the same key is used for encryption and decryption, and asymmetric key cryptography, which uses different public and private keys. It also covers traditional cipher techniques like substitution and transposition ciphers. The document concludes by listing some applications of cryptography like e-commerce, secure data, and access control.Computer Application in Business (commerce)



Computer Application in Business (commerce)Sudar Sudar
Ěý
The main objectives
1. To introduce the concept of computer and its various parts. 2. To explain the concept of data base management system and Management information system.
3. To provide insight about networking and basics of internet
Recall various terms of computer and its part
Understand the meaning of software, operating system, programming language and its features
Comparing Data Vs Information and its management system Understanding about various concepts of management information system
Explain about networking and elements based on internet
1. Recall the various concepts relating to computer and its various parts
2 Understand the meaning of software’s, operating system etc
3 Understanding the meaning and utility of database management system
4 Evaluate the various aspects of management information system
5 Generating more ideas regarding the use of internet for business purpose Database population in Odoo 18 - Odoo slides



Database population in Odoo 18 - Odoo slidesCeline George
Ěý
In this slide, we’ll discuss the database population in Odoo 18. In Odoo, performance analysis of the source code is more important. Database population is one of the methods used to analyze the performance of our code. Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1...



Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1...pinkdvil200
Ěý
Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1 2024 Research & Research Methods: Basic Concepts and Types.pptx



Research & Research Methods: Basic Concepts and Types.pptxDr. Sarita Anand
Ěý
This ppt has been made for the students pursuing PG in social science and humanities like M.Ed., M.A. (Education), Ph.D. Scholars. It will be also beneficial for the teachers and other faculty members interested in research and teaching research concepts.How to Configure Restaurants in Odoo 17 Point of Sale



How to Configure Restaurants in Odoo 17 Point of SaleCeline George
Ěý
Odoo, a versatile and integrated business management software, excels with its robust Point of Sale (POS) module. This guide delves into the intricacies of configuring restaurants in Odoo 17 POS, unlocking numerous possibilities for streamlined operations and enhanced customer experiences.How to Setup WhatsApp in Odoo 17 - Odoo şÝşÝߣs



How to Setup WhatsApp in Odoo 17 - Odoo şÝşÝߣsCeline George
Ěý
Integrate WhatsApp into Odoo using the WhatsApp Business API or third-party modules to enhance communication. This integration enables automated messaging and customer interaction management within Odoo 17.Blind Spots in AI and Formulation Science Knowledge Pyramid (Updated Perspect...



Blind Spots in AI and Formulation Science Knowledge Pyramid (Updated Perspect...Ajaz Hussain
Ěý
This presentation delves into the systemic blind spots within pharmaceutical science and regulatory systems, emphasizing the significance of "inactive ingredients" and their influence on therapeutic equivalence. These blind spots, indicative of normalized systemic failures, go beyond mere chance occurrences and are ingrained deeply enough to compromise decision-making processes and erode trust.
Historical instances like the 1938 FD&C Act and the Generic Drug Scandals underscore how crisis-triggered reforms often fail to address the fundamental issues, perpetuating inefficiencies and hazards.
The narrative advocates a shift from reactive crisis management to proactive, adaptable systems prioritizing continuous enhancement. Key hurdles involve challenging outdated assumptions regarding bioavailability, inadequately funded research ventures, and the impact of vague language in regulatory frameworks.
The rise of large language models (LLMs) presents promising solutions, albeit with accompanying risks necessitating thorough validation and seamless integration.
Tackling these blind spots demands a holistic approach, embracing adaptive learning and a steadfast commitment to self-improvement. By nurturing curiosity, refining regulatory terminology, and judiciously harnessing new technologies, the pharmaceutical sector can progress towards better public health service delivery and ensure the safety, efficacy, and real-world impact of drug products.How to Configure Flexible Working Schedule in Odoo 18 Employee



How to Configure Flexible Working Schedule in Odoo 18 EmployeeCeline George
Ěý
In this slide, we’ll discuss on how to configure flexible working schedule in Odoo 18 Employee module. In Odoo 18, the Employee module offers powerful tools to configure and manage flexible working schedules tailored to your organization's needs.The Constitution, Government and Law making bodies .



The Constitution, Government and Law making bodies .saanidhyapatel09
Ěý
This PowerPoint presentation provides an insightful overview of the Constitution, covering its key principles, features, and significance. It explains the fundamental rights, duties, structure of government, and the importance of constitutional law in governance. Ideal for students, educators, and anyone interested in understanding the foundation of a nation’s legal framework.
Essentials of a Good PMO, presented by Aalok Sonawala



Essentials of a Good PMO, presented by Aalok SonawalaAssociation for Project Management
Ěý
APM event hosted by the South Wales and West of England Network (SWWE Network)
Speaker: Aalok Sonawala
The SWWE Regional Network were very pleased to welcome Aalok Sonawala, Head of PMO, National Programmes, Rider Levett Bucknall on 26 February, to BAWA for our first face to face event of 2025. Aalok is a member of APM’s Thames Valley Regional Network and also speaks to members of APM’s PMO Interest Network, which aims to facilitate collaboration and learning, offer unbiased advice and guidance.
Tonight, Aalok planned to discuss the importance of a PMO within project-based organisations, the different types of PMO and their key elements, PMO governance and centres of excellence.
PMO’s within an organisation can be centralised, hub and spoke with a central PMO with satellite PMOs globally, or embedded within projects. The appropriate structure will be determined by the specific business needs of the organisation. The PMO sits above PM delivery and the supply chain delivery teams.
For further information about the event please click here.FESTIVAL: SINULOG & THINGYAN-LESSON 4.pptx



FESTIVAL: SINULOG & THINGYAN-LESSON 4.pptxDanmarieMuli1
Ěý
Sinulog Festival of Cebu City, and Thingyan Festival of Myanmar.More Related Content
Viewers also liked (8)
Caesar cipher



Caesar cipherRamadhi Irawan
Ěý
The Caesar cipher is one of the earliest known substitution ciphers. It works by shifting each letter in a plaintext message by a set number of positions (the key) in the alphabet to encrypt it. For example, with a key of 3, A would be replaced by D, B by E, and so on. Decryption simply requires shifting letters in the opposite direction by the same key. While simple, the Caesar cipher has some mathematical properties and was allegedly used by Julius Caesar to communicate with his army. However, it is also easy to break through brute force by trying all 26 possible keys.Idea(international data encryption algorithm)



Idea(international data encryption algorithm)SAurabh PRajapati
Ěý
The document discusses the International Data Encryption Algorithm (IDEA). It was developed in 1990 as a replacement for the Data Encryption Standard. IDEA is a symmetric block cipher that uses a 128-bit key to encrypt 64-bit blocks of plaintext into ciphertext. The key is divided into 52 subkeys that are used in 8 rounds of encryption/decryption operations involving XOR, addition, and multiplication. IDEA was used in PGP v2.0 and can encrypt sensitive data for applications like financial services, broadcasting, and government use.Cipher techniques



Cipher techniquesMohd Arif
Ěý
The document provides an overview of cipher techniques including:
- Classical techniques like transposition ciphers, substitution ciphers including the Caesar and Playfair ciphers, and polyalphabetic ciphers like the Vigenere cipher.
- Modern techniques like stream ciphers which encrypt bits one at a time using a pseudorandom keystream, and block ciphers which encrypt blocks of text.
- It also discusses cryptanalysis techniques for analyzing ciphers and discusses how to build more secure systems using techniques like the one-time pad or combining multiple ciphers.Cryptography



CryptographyDarshini Parikh
Ěý
Cryptography is the practice and study of securing communication through techniques like encryption. It has evolved through manual, mechanical, and modern eras using computers. Cryptography aims to achieve goals like authentication, confidentiality, integrity, and non-repudiation. Common attacks include brute force, chosen plaintext, and differential power analysis. Symmetric cryptography uses a shared key while asymmetric uses public/private key pairs. Digital signatures and watermarks can authenticate documents. DRM and watermarks control digital content distribution.Cryptography



CryptographySidharth Mohapatra
Ěý
Cryptography is the science of using mathematics to encrypt and decrypt data.
Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anyone except the intended recipient.
Cryptography



CryptographyShivanand Arur
Ěý
This PPT explains about the term "Cryptography - Encryption & Decryption". This PPT is for beginners and for intermediate developers who want to learn about Cryptography. I have also explained about the various classes which .Net provides for encryption and decryption and some other terms like "AES" and "DES".Cryptography.ppt



Cryptography.pptkusum sharma
Ěý
This document provides an overview of cryptography. It defines cryptography as the science of securing messages from attacks. It discusses basic cryptography terms like plain text, cipher text, encryption, decryption, and keys. It describes symmetric key cryptography, where the same key is used for encryption and decryption, and asymmetric key cryptography, which uses different public and private keys. It also covers traditional cipher techniques like substitution and transposition ciphers. The document concludes by listing some applications of cryptography like e-commerce, secure data, and access control.Recently uploaded (20)
Computer Application in Business (commerce)



Computer Application in Business (commerce)Sudar Sudar
Ěý
The main objectives
1. To introduce the concept of computer and its various parts. 2. To explain the concept of data base management system and Management information system.
3. To provide insight about networking and basics of internet
Recall various terms of computer and its part
Understand the meaning of software, operating system, programming language and its features
Comparing Data Vs Information and its management system Understanding about various concepts of management information system
Explain about networking and elements based on internet
1. Recall the various concepts relating to computer and its various parts
2 Understand the meaning of software’s, operating system etc
3 Understanding the meaning and utility of database management system
4 Evaluate the various aspects of management information system
5 Generating more ideas regarding the use of internet for business purpose Database population in Odoo 18 - Odoo slides



Database population in Odoo 18 - Odoo slidesCeline George
Ěý
In this slide, we’ll discuss the database population in Odoo 18. In Odoo, performance analysis of the source code is more important. Database population is one of the methods used to analyze the performance of our code. Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1...



Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1...pinkdvil200
Ěý
Lesson Plan M1 2024 Lesson Plan M1 2024 Lesson Plan M1 2024 Research & Research Methods: Basic Concepts and Types.pptx



Research & Research Methods: Basic Concepts and Types.pptxDr. Sarita Anand
Ěý
This ppt has been made for the students pursuing PG in social science and humanities like M.Ed., M.A. (Education), Ph.D. Scholars. It will be also beneficial for the teachers and other faculty members interested in research and teaching research concepts.How to Configure Restaurants in Odoo 17 Point of Sale



How to Configure Restaurants in Odoo 17 Point of SaleCeline George
Ěý
Odoo, a versatile and integrated business management software, excels with its robust Point of Sale (POS) module. This guide delves into the intricacies of configuring restaurants in Odoo 17 POS, unlocking numerous possibilities for streamlined operations and enhanced customer experiences.How to Setup WhatsApp in Odoo 17 - Odoo şÝşÝߣs



How to Setup WhatsApp in Odoo 17 - Odoo şÝşÝߣsCeline George
Ěý
Integrate WhatsApp into Odoo using the WhatsApp Business API or third-party modules to enhance communication. This integration enables automated messaging and customer interaction management within Odoo 17.Blind Spots in AI and Formulation Science Knowledge Pyramid (Updated Perspect...



Blind Spots in AI and Formulation Science Knowledge Pyramid (Updated Perspect...Ajaz Hussain
Ěý
This presentation delves into the systemic blind spots within pharmaceutical science and regulatory systems, emphasizing the significance of "inactive ingredients" and their influence on therapeutic equivalence. These blind spots, indicative of normalized systemic failures, go beyond mere chance occurrences and are ingrained deeply enough to compromise decision-making processes and erode trust.
Historical instances like the 1938 FD&C Act and the Generic Drug Scandals underscore how crisis-triggered reforms often fail to address the fundamental issues, perpetuating inefficiencies and hazards.
The narrative advocates a shift from reactive crisis management to proactive, adaptable systems prioritizing continuous enhancement. Key hurdles involve challenging outdated assumptions regarding bioavailability, inadequately funded research ventures, and the impact of vague language in regulatory frameworks.
The rise of large language models (LLMs) presents promising solutions, albeit with accompanying risks necessitating thorough validation and seamless integration.
Tackling these blind spots demands a holistic approach, embracing adaptive learning and a steadfast commitment to self-improvement. By nurturing curiosity, refining regulatory terminology, and judiciously harnessing new technologies, the pharmaceutical sector can progress towards better public health service delivery and ensure the safety, efficacy, and real-world impact of drug products.How to Configure Flexible Working Schedule in Odoo 18 Employee



How to Configure Flexible Working Schedule in Odoo 18 EmployeeCeline George
Ěý
In this slide, we’ll discuss on how to configure flexible working schedule in Odoo 18 Employee module. In Odoo 18, the Employee module offers powerful tools to configure and manage flexible working schedules tailored to your organization's needs.The Constitution, Government and Law making bodies .



The Constitution, Government and Law making bodies .saanidhyapatel09
Ěý
This PowerPoint presentation provides an insightful overview of the Constitution, covering its key principles, features, and significance. It explains the fundamental rights, duties, structure of government, and the importance of constitutional law in governance. Ideal for students, educators, and anyone interested in understanding the foundation of a nation’s legal framework.
Essentials of a Good PMO, presented by Aalok Sonawala



Essentials of a Good PMO, presented by Aalok SonawalaAssociation for Project Management
Ěý
APM event hosted by the South Wales and West of England Network (SWWE Network)
Speaker: Aalok Sonawala
The SWWE Regional Network were very pleased to welcome Aalok Sonawala, Head of PMO, National Programmes, Rider Levett Bucknall on 26 February, to BAWA for our first face to face event of 2025. Aalok is a member of APM’s Thames Valley Regional Network and also speaks to members of APM’s PMO Interest Network, which aims to facilitate collaboration and learning, offer unbiased advice and guidance.
Tonight, Aalok planned to discuss the importance of a PMO within project-based organisations, the different types of PMO and their key elements, PMO governance and centres of excellence.
PMO’s within an organisation can be centralised, hub and spoke with a central PMO with satellite PMOs globally, or embedded within projects. The appropriate structure will be determined by the specific business needs of the organisation. The PMO sits above PM delivery and the supply chain delivery teams.
For further information about the event please click here.FESTIVAL: SINULOG & THINGYAN-LESSON 4.pptx



FESTIVAL: SINULOG & THINGYAN-LESSON 4.pptxDanmarieMuli1
Ěý
Sinulog Festival of Cebu City, and Thingyan Festival of Myanmar.SOCIAL CHANGE(a change in the institutional and normative structure of societ...



SOCIAL CHANGE(a change in the institutional and normative structure of societ...DrNidhiAgarwal
Ěý
This PPT is showing the effect of social changes in human life and it is very understandable to the students with easy language.in this contents are Itroduction, definition,Factors affecting social changes ,Main technological factors, Social change and stress , what is eustress and how social changes give impact of the human's life.Principle and Practices of Animal Breeding || Boby Basnet



Principle and Practices of Animal Breeding || Boby BasnetBoby Basnet
Ěý
Principle and Practices of Animal Breeding Full Note
|| Assistant Professor Boby Basnet ||IAAS || AFU || PU || FUHow to attach file using upload button Odoo 18



How to attach file using upload button Odoo 18Celine George
Ěý
In this slide, we’ll discuss on how to attach file using upload button Odoo 18. Odoo features a dedicated model, 'ir.attachments,' designed for storing attachments submitted by end users. We can see the process of utilizing the 'ir.attachments' model to enable file uploads through web forms in this slide.Rass MELAI : an Internet MELA Quiz Finals - El Dorado 2025



Rass MELAI : an Internet MELA Quiz Finals - El Dorado 2025Conquiztadors- the Quiz Society of Sri Venkateswara College
Ěý
Finals of Rass MELAI : a Music, Entertainment, Literature, Arts and Internet Culture Quiz organized by Conquiztadors, the Quiz society of Sri Venkateswara College under their annual quizzing fest El Dorado 2025. QuickBooks Desktop to QuickBooks Online How to Make the Move



QuickBooks Desktop to QuickBooks Online How to Make the MoveTechSoup
Ěý
If you use QuickBooks Desktop and are stressing about moving to QuickBooks Online, in this webinar, get your questions answered and learn tips and tricks to make the process easier for you.
Key Questions:
* When is the best time to make the shift to QuickBooks Online?
* Will my current version of QuickBooks Desktop stop working?
* I have a really old version of QuickBooks. What should I do?
* I run my payroll in QuickBooks Desktop now. How is that affected?
*Does it bring over all my historical data? Are there things that don't come over?
* What are the main differences between QuickBooks Desktop and QuickBooks Online?
* And moreRass MELAI : an Internet MELA Quiz Finals - El Dorado 2025



Rass MELAI : an Internet MELA Quiz Finals - El Dorado 2025Conquiztadors- the Quiz Society of Sri Venkateswara College
Ěý






