Top Level Cyber Security Strategy
- 1. Top Level Cyber Security Strategy John M. Gilligan jgilligan@gilligangroupinc.com www.gilligangroupinc.com
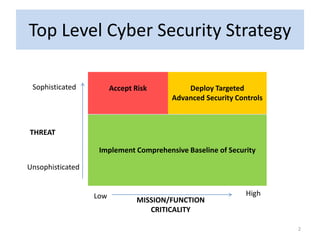
- 2. Top Level Cyber Security Strategy Sophisticated Unsophisticated MISSION/FUNCTION CRITICALITY Implement Comprehensive Baseline of Security THREAT Low High Deploy Targeted Advanced Security Controls Accept Risk 2
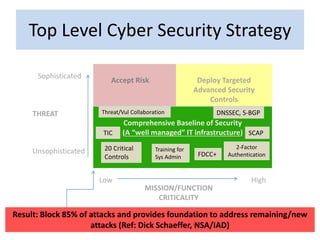
- 3. Top Level Cyber Security Strategy Sophisticated Unsophisticated MISSION/FUNCTION CRITICALITY Comprehensive Baseline of Security (A ŌĆ£well managedŌĆØ IT infrastructure) THREAT Low High Deploy Targeted Advanced Security Controls Accept Risk 3 TIC Training for Sys Admin 2-Factor Authentication 20 Critical Controls FDCC+ SCAP Result: Block 85% of attacks and provides foundation to address remaining/new attacks (Ref: Dick Schaeffer, NSA/IAD) DNSSEC, S-BGPThreat/Vul Collaboration