TS/NOFORN
2 likes2,021 views
This document contains a summary of analysis of 5 malware suspects. Key details are provided on each suspect's files, compile times, command and control infrastructure, and behaviors. The analysis suggests the suspects originate from a French-speaking operator and involve use of Lua scripting. Attribution is difficult due to techniques like using commonly known bot names and hosting infrastructure in different countries.
1 of 42
Downloaded 17 times











![SUSPECTS #[2-4]
ŌĆóFILESIZE: 184320
ŌĆóCODESIZE: 139264
ŌĆóCOMPILETIME: 2010:02:16 18:05:54+01:00
ŌĆóFILESIZE: 184320
ŌĆóCODESIZE: 139264
ŌĆóCOMPILETIME: 2010:03:11 17:55:03+01:00
ŌĆóFILESIZE: 792064
ŌĆóCODESIZE: 583680
ŌĆóCOMPILETIME: 2011:10:2520:28:39+01:00](https://image.slidesharecdn.com/tsnoforn-141024170404-conversion-gate01/85/TS-NOFORN-17-320.jpg)




















Ad
Recommended
La Quadrature Du Cercle - The APTs That Weren't
La Quadrature Du Cercle - The APTs That Weren'tpinkflawd
╠²
This document discusses advanced persistent threats (APTs) and cyber espionage. It describes how APTs have evolved over time to target different platforms and avoid detection. Nation states are now engaging in industrial espionage and some commercial threat intelligence firms may be inadvertently aiding attackers by publishing detailed research on sophisticated government-backed malware. Attribution of APTs is challenging and not always necessary, but recognition of actor tools can help defenders. Overall it raises ethical questions around the public disclosure of nation state cyber operations.The A and the P of the T
The A and the P of the Tpinkflawd
╠²
This document discusses advanced persistent threats (APTs) and their evolution over time. It notes that early detection of threats was based on knowing binary signatures and behaviors, but APTs now use unique and regularly updated binaries, lack repetitive artifacts, are environmentally sensitive, use multiple persistence techniques, and employ consistent evasion methods to avoid detection. Examples of prominent APTs discussed include BlackEnergy, Havex, BlackPOS, and Evil Bunny malware families. The document emphasizes that attackers are constantly improving their techniques, making early detection and protection against APTs extremely challenging.How would you find what you can't see?
How would you find what you can't see?pinkflawd
╠²
The document contains a history of malware infections on a system over time, listing the malware name, registry key used, and date/time of infection. It also contains references to common cybersecurity terms like virus, worm, trojan, and APT, as well as URLs possibly related to the infections. The document appears to be a log of malicious activity on a system.Big Game Hunting - Peculiarities In Nation State Malware Research
Big Game Hunting - Peculiarities In Nation State Malware Researchpinkflawd
╠²
This document discusses various techniques used in malware analysis and attribution, including:
1) Analyzing malware samples and associated metadata to identify patterns in implementation traits, infrastructure, and custom features that can provide clues to the actor.
2) The challenges of attribution given issues like attribution indicators being faked, the influence of individual analysts and compilers, and denials from suspected groups.
3) How soft attribution based on analyzing similarities in malware is less definitive than hard attribution with confirmed links, and how both are interpreted by analysts.Catch Me If You Can
Catch Me If You Canpinkflawd
╠²
This document discusses various techniques used for malware analysis and anti-analysis. It describes levels of malware sophistication from mass to advanced. It also outlines methods used for static analysis, debugging, and bypassing anti-debugging techniques. The document provides references to papers on anti-debugging, anti-virtualization, and unpacking malware. It briefly describes examples of VB6 and C++ packers as well as sneaky exploits and payloads.Shooting
Shootingpinkflawd
╠²
This document contains information about several malware programs, including Bunny, Babar, NBOT, and Casper. It describes their technical capabilities such as evasion techniques, payloads, and command and control protocols. It also references additional documents and blogs that provide more in-depth analysis of these malware programs. Hashes are included for some of the malware binaries.Malware Most Wanted: Evil Bunny
Malware Most Wanted: Evil BunnyCyphort
╠²
The document details a presentation by security researcher Marion Marschalek on the 'EvilBunny' malware, highlighting its sophisticated features and the modern threat landscape. It discusses the malware's command and control capabilities, infection vectors, and the challenges it presents to security solutions, as well as its origins and connection to other malware. The presentation emphasizes the need for enhanced malware detection and response in the face of evolving cyber threats.Zeus' Not Dead Yet
Zeus' Not Dead Yetpinkflawd
╠²
Zeus is an old banking Trojan that steals user data. It has evolved over time, with new variants like Citadel and SpyEye emerging. Zeus uses various techniques to evade detection like hiding in system processes and changing its files frequently. It communicates with command and control servers to receive configuration updates and upload stolen information.News bytes Oct-2011
News bytes Oct-2011Ashwin Patil, GCIH, GCIA, GCFE
╠²
This document summarizes recent cybersecurity news and events in the information security field. It discusses several security conferences that recently occurred including Brucon, Derbycon, and HITB as well as the arrest of members of the hacker group Lulzsec. It also covers recent vulnerabilities including a chosen plaintext attack against AES in SSL/TLS, the compromise of the mysql.com website, and an Apache reverse proxy bypass issue. Lastly, it mentions new security tools releases, recent malware activity including new Android threats, and recommended security reading materials.News Bytes - December 2015
News Bytes - December 2015n|u - The Open Security Community
╠²
An Instagram researcher hacked the Instagram server and accessed employee credentials. Juniper firewalls contained an unauthorized code backdoor since 2012. A 19-year-old hacked an airline's website and stole $150,000 by selling fake tickets. 13 million MacKeeper users had their data exposed in an unsecured database. Anonymous declared war on Donald Trump by DDoSing his websites. A Linux vulnerability allowed hacking by pressing backspace 28 times to exploit the Grub2 bootloader.The Enemy Within: Organizational Insight Through the Eyes of a Webserver
The Enemy Within: Organizational Insight Through the Eyes of a WebserverRamece Cave
╠²
The document discusses insights into organizational security through the lens of web servers, highlighting the ongoing threats they face due to outdated services and vulnerabilities. It covers the evolution of web servers, various malicious campaigns, and the potential risks associated with compromised servers being used for malicious purposes. Key recommendations include keeping servers patched, upgrading as needed, and maintaining diligence in security practices.ECrime presentation - A few bits about malware
ECrime presentation - A few bits about malwareMichael Hendrickx
╠²
This document discusses malware attacks and provides information about different types of malware like RATs, viruses, trojans, and ransomware. It describes the two main stages of a malware attack - infection and persistence. Common infection methods include exploiting software bugs, spear phishing, waterhole attacks, and inserting malware via USB devices. The persistence stage ensures the malware remains active by hiding from antivirus software and maintaining connections to command and control servers. Remediation involves improving user awareness, tightening endpoint controls, and regularly scanning with antivirus and malware detection tools.Next Generation Firewalls
Next Generation FirewallsThe eCore Group
╠²
Next generation firewalls aim to provide integrated threat protection through consolidation of gateway functions in virtual appliances with enterprise-class features for all segments. They aim to keep up with evolving intelligence-based threats by providing end-to-end policy compliance across all devices, including mobile, and virtualization capabilities for multi-tenant environments. Firewalls have evolved over 25 years from basic packet filtering to deep packet inspection to address more sophisticated threats that can bypass policies by posing as legitimate traffic.What is the Cybersecurity plan for tomorrow?
What is the Cybersecurity plan for tomorrow?Samvel Gevorgyan
╠²
This document discusses cybersecurity challenges and provides an overview of key concepts. It covers the CIA security model of confidentiality, integrity and availability. It also discusses identification, authentication and authorization. Additional sections outline cybersecurity elements like people, processes, technology and policies. Cybersecurity statistics on data breaches and spending are presented. Common security threats like SQL injection, password attacks, phishing and ransomware are analyzed. Approaches for both reacting to and avoiding security problems are proposed. The document promotes the services of Cyber Gates for cyber defense.Days of the Honeynet: Attacks, Tools, Incidents
Days of the Honeynet: Attacks, Tools, IncidentsAnton Chuvakin
╠²
This document summarizes attacks on a Linux honeypot connected to the internet over time. It describes common exploits attempted including longstanding vulnerabilities in RPC statd and WU-FTPD. It also outlines payloads left by attackers like rootkits and tools and provides examples of infiltration incidents where attackers used compromised systems for IRC bots, flooding attacks, and expanding attacks to other systems.Modern Web Security, Lazy but Mindful Like a Fox
Modern Web Security, Lazy but Mindful Like a FoxC4Media
╠²
The document discusses modern web security strategies showcased at QCon San Francisco 2016, emphasizing the importance of knowledge and innovation in software development. It covers various security vulnerabilities, bounty programs, and defenses employed by major tech companies like Facebook and Uber, along with insights into risk management and application security. The presentation also highlights practical security measures and advocates for effective communication of security contexts.RSA 2005 H&T: Die Script Kiddie! Die, Die, Die!
RSA 2005 H&T: Die Script Kiddie! Die, Die, Die!Dan Houser
╠²
Humorous yet serious look at means of messing with low-intensity hackers who are attempting to fingerprint the estate and determine your technology stack.
RSA 2005 - Houser & RockwoodFirewalls (Distributed computing)
Firewalls (Distributed computing)Sri Prasanna
╠²
The document discusses various methods that can be used to gain unauthorized access to a vault or protected computer systems and networks. It describes techniques like trying combinations, exploiting design flaws, observing others, social engineering, software exploits, malware, phishing, spoofing addresses, and session hijacking. It also notes the risks of buggy software and mistakes that introduce vulnerabilities.Web Hacking
Web HackingInformation Technology
╠²
The document discusses various vulnerabilities in web servers and web applications. It covers popular web servers like IIS, Apache, and others. It then discusses attacking vulnerabilities in web servers like sample files, source code disclosure, canonicalization, and buffer overflows. It also discusses vulnerabilities in web applications like cross-site scripting, SQL injection, cross-site request forgery, and HTTP response splitting. It provides examples of exploits and recommendations for countermeasures to secure web servers and applications.Introduction To ICT Security Audit OWASP Day Malaysia 2011
Introduction To ICT Security Audit OWASP Day Malaysia 2011Linuxmalaysia Malaysia
╠²
This document outlines an agenda for an IT audit and assessment event. It discusses identifying risks like outdated patches, weak passwords, open ports, and phishing. It provides resources for monitoring vulnerabilities and cracking passwords. Labs are suggested to practice tasks like patching, password cracking, port scanning, and network monitoring. The objective is to harden systems against common threats by finding vulnerabilities and ensuring regular security reviews are performed. Participants are encouraged to get involved to improve the security of their organization.Insecurity-In-Security version.1 (2010)
Insecurity-In-Security version.1 (2010)Abhishek Kumar
╠²
The document discusses various cybersecurity vulnerabilities and risks associated with user accounts, web services, and data security. It highlights the importance of implementing strict security measures, such as encryption, secure log-ins, and firewalls, as well as recognizing the ongoing nature of security maintenance rather than achieving complete security. The conclusion emphasizes vigilance against constantly evolving threats and the need to monitor vulnerabilities and patch systems accordingly.News bytes Sept-2011
News bytes Sept-2011Ashwin Patil, GCIH, GCIA, GCFE
╠²
This document provides a summary of recent cybersecurity news and announcements from August and September 2011. It covers topics like announcements for security conferences Malcon 2011 and Nullcon 2012. It also discusses the DigiNotar certificate authority breach, the Comodohacker attack, doppelganger domains collecting email, the Morto RDP worm, Android mobile phone monitoring services, the Linux kernel source code breach, and new malware like Mebromi and Spyeyetrojan. It provides an overview of security tools like OWASP GoatDroid and updates to existing tools. Finally, it lists some security reading materials.Advanced Malware Analysis
Advanced Malware AnalysisPrathan Phongthiproek
╠²
The document discusses security challenges posed by modern malware and web-based attacks. It provides examples of next-generation malware that bypass antivirus detection using techniques like embedding malicious code in Office documents or PDF files. It also discusses how web-based malware has evolved from defacements and DDoS tools to more advanced drive-by download attacks using exploit kits. The document aims to demonstrate malware analysis techniques and how to detect web server backdoors through tools and manual source code reviews. It concludes with a challenge to practice security skills safely.AtlSecCon 2016
AtlSecCon 2016Earl Carter
╠²
The document discusses emerging cybersecurity threats such as exploit kits, ransomware, and phishing scams. It provides an overview of the Angler exploit kit and how it has evolved, targeting vulnerabilities in Adobe Flash, Internet Explorer, and Silverlight. It also examines the CryptoWall ransomware version 4 and how it encrypts files and communicates with command and control servers. Additionally, it analyzes the SamSam ransomware attacks targeting healthcare organizations and the Rombertik malware which uses layers of obfuscation and anti-analysis techniques to propagate via spam and steal user credentials.Ransomware: History, Analysis, & Mitigation
Ransomware: History, Analysis, & MitigationWhiskeyNeon
╠²
The document provides an overview and analysis of ransomware, including its history, technical details, trends, and mitigation techniques. It discusses how ransomware has evolved from early variants like AIDS to modern cryptoware like CryptoLocker and Locky. The document also analyzes the infection process, command and control infrastructure, and outlines strategies organizations can take to help prevent and recover from ransomware attacks, such as backups, patching, and isolation of critical systems.Cyber Espionage Against Georgia (Georbot)
Cyber Espionage Against Georgia (Georbot)DataExchangeAgency
╠²
The document summarizes a cyber espionage attack against the Georgian government discovered in March 2011. Advanced malware was collecting sensitive security documents from Georgian and American systems and uploading them to command and control servers linked to Russian security agencies. The sophisticated malware infected over 390 computers, 70% of which were in Georgia, through compromised Georgian news websites. It was able to fully control infected machines, search for sensitive words, and record audio and video. After extensive analysis of command and control servers and malware files, Georgian authorities determined that the Russian government was behind the attack.G3t R00t at IUT
G3t R00t at IUTNahidul Kibria
╠²
The document outlines various roles in information security, including penetration testers, malware analysts, and forensic analysts, detailing necessary skills and methodologies for each. It emphasizes the importance of community collaboration within OWASP to enhance application security and provides information about tools and resources for security professionals. The document also describes a Capture the Flag (CTF) event aimed at testing participants' skills in computer security, alongside rules and criteria for judging their performance.Hacker Halted 2014 - Post-Exploitation After Having Remote Access
Hacker Halted 2014 - Post-Exploitation After Having Remote AccessEC-Council
╠²
The document details a hacking approach to bypass security measures of high-security remote desktop environments, focusing on malware deployment, privilege escalation, and circumventing application whitelisting. It emphasizes techniques for remote code execution, using simulated user interaction, and methods for bypassing hardware firewalls. The document also provides insights for red teams, blue teams, and policy makers regarding vulnerabilities in security implementations.Complete University of Calculus :: 2nd edition
Complete University of Calculus :: 2nd editionShabista Imam
╠²
Master the language of change with the Complete Guidance Book of CalculusŌĆöyour comprehensive resource for understanding the core concepts and applications of differential and integral calculus. Designed for high school, college, and self-study learners, this book takes a clear, intuitive approach to a subject often considered challenging.More Related Content
Similar to TS/NOFORN (20)
News bytes Oct-2011
News bytes Oct-2011Ashwin Patil, GCIH, GCIA, GCFE
╠²
This document summarizes recent cybersecurity news and events in the information security field. It discusses several security conferences that recently occurred including Brucon, Derbycon, and HITB as well as the arrest of members of the hacker group Lulzsec. It also covers recent vulnerabilities including a chosen plaintext attack against AES in SSL/TLS, the compromise of the mysql.com website, and an Apache reverse proxy bypass issue. Lastly, it mentions new security tools releases, recent malware activity including new Android threats, and recommended security reading materials.News Bytes - December 2015
News Bytes - December 2015n|u - The Open Security Community
╠²
An Instagram researcher hacked the Instagram server and accessed employee credentials. Juniper firewalls contained an unauthorized code backdoor since 2012. A 19-year-old hacked an airline's website and stole $150,000 by selling fake tickets. 13 million MacKeeper users had their data exposed in an unsecured database. Anonymous declared war on Donald Trump by DDoSing his websites. A Linux vulnerability allowed hacking by pressing backspace 28 times to exploit the Grub2 bootloader.The Enemy Within: Organizational Insight Through the Eyes of a Webserver
The Enemy Within: Organizational Insight Through the Eyes of a WebserverRamece Cave
╠²
The document discusses insights into organizational security through the lens of web servers, highlighting the ongoing threats they face due to outdated services and vulnerabilities. It covers the evolution of web servers, various malicious campaigns, and the potential risks associated with compromised servers being used for malicious purposes. Key recommendations include keeping servers patched, upgrading as needed, and maintaining diligence in security practices.ECrime presentation - A few bits about malware
ECrime presentation - A few bits about malwareMichael Hendrickx
╠²
This document discusses malware attacks and provides information about different types of malware like RATs, viruses, trojans, and ransomware. It describes the two main stages of a malware attack - infection and persistence. Common infection methods include exploiting software bugs, spear phishing, waterhole attacks, and inserting malware via USB devices. The persistence stage ensures the malware remains active by hiding from antivirus software and maintaining connections to command and control servers. Remediation involves improving user awareness, tightening endpoint controls, and regularly scanning with antivirus and malware detection tools.Next Generation Firewalls
Next Generation FirewallsThe eCore Group
╠²
Next generation firewalls aim to provide integrated threat protection through consolidation of gateway functions in virtual appliances with enterprise-class features for all segments. They aim to keep up with evolving intelligence-based threats by providing end-to-end policy compliance across all devices, including mobile, and virtualization capabilities for multi-tenant environments. Firewalls have evolved over 25 years from basic packet filtering to deep packet inspection to address more sophisticated threats that can bypass policies by posing as legitimate traffic.What is the Cybersecurity plan for tomorrow?
What is the Cybersecurity plan for tomorrow?Samvel Gevorgyan
╠²
This document discusses cybersecurity challenges and provides an overview of key concepts. It covers the CIA security model of confidentiality, integrity and availability. It also discusses identification, authentication and authorization. Additional sections outline cybersecurity elements like people, processes, technology and policies. Cybersecurity statistics on data breaches and spending are presented. Common security threats like SQL injection, password attacks, phishing and ransomware are analyzed. Approaches for both reacting to and avoiding security problems are proposed. The document promotes the services of Cyber Gates for cyber defense.Days of the Honeynet: Attacks, Tools, Incidents
Days of the Honeynet: Attacks, Tools, IncidentsAnton Chuvakin
╠²
This document summarizes attacks on a Linux honeypot connected to the internet over time. It describes common exploits attempted including longstanding vulnerabilities in RPC statd and WU-FTPD. It also outlines payloads left by attackers like rootkits and tools and provides examples of infiltration incidents where attackers used compromised systems for IRC bots, flooding attacks, and expanding attacks to other systems.Modern Web Security, Lazy but Mindful Like a Fox
Modern Web Security, Lazy but Mindful Like a FoxC4Media
╠²
The document discusses modern web security strategies showcased at QCon San Francisco 2016, emphasizing the importance of knowledge and innovation in software development. It covers various security vulnerabilities, bounty programs, and defenses employed by major tech companies like Facebook and Uber, along with insights into risk management and application security. The presentation also highlights practical security measures and advocates for effective communication of security contexts.RSA 2005 H&T: Die Script Kiddie! Die, Die, Die!
RSA 2005 H&T: Die Script Kiddie! Die, Die, Die!Dan Houser
╠²
Humorous yet serious look at means of messing with low-intensity hackers who are attempting to fingerprint the estate and determine your technology stack.
RSA 2005 - Houser & RockwoodFirewalls (Distributed computing)
Firewalls (Distributed computing)Sri Prasanna
╠²
The document discusses various methods that can be used to gain unauthorized access to a vault or protected computer systems and networks. It describes techniques like trying combinations, exploiting design flaws, observing others, social engineering, software exploits, malware, phishing, spoofing addresses, and session hijacking. It also notes the risks of buggy software and mistakes that introduce vulnerabilities.Web Hacking
Web HackingInformation Technology
╠²
The document discusses various vulnerabilities in web servers and web applications. It covers popular web servers like IIS, Apache, and others. It then discusses attacking vulnerabilities in web servers like sample files, source code disclosure, canonicalization, and buffer overflows. It also discusses vulnerabilities in web applications like cross-site scripting, SQL injection, cross-site request forgery, and HTTP response splitting. It provides examples of exploits and recommendations for countermeasures to secure web servers and applications.Introduction To ICT Security Audit OWASP Day Malaysia 2011
Introduction To ICT Security Audit OWASP Day Malaysia 2011Linuxmalaysia Malaysia
╠²
This document outlines an agenda for an IT audit and assessment event. It discusses identifying risks like outdated patches, weak passwords, open ports, and phishing. It provides resources for monitoring vulnerabilities and cracking passwords. Labs are suggested to practice tasks like patching, password cracking, port scanning, and network monitoring. The objective is to harden systems against common threats by finding vulnerabilities and ensuring regular security reviews are performed. Participants are encouraged to get involved to improve the security of their organization.Insecurity-In-Security version.1 (2010)
Insecurity-In-Security version.1 (2010)Abhishek Kumar
╠²
The document discusses various cybersecurity vulnerabilities and risks associated with user accounts, web services, and data security. It highlights the importance of implementing strict security measures, such as encryption, secure log-ins, and firewalls, as well as recognizing the ongoing nature of security maintenance rather than achieving complete security. The conclusion emphasizes vigilance against constantly evolving threats and the need to monitor vulnerabilities and patch systems accordingly.News bytes Sept-2011
News bytes Sept-2011Ashwin Patil, GCIH, GCIA, GCFE
╠²
This document provides a summary of recent cybersecurity news and announcements from August and September 2011. It covers topics like announcements for security conferences Malcon 2011 and Nullcon 2012. It also discusses the DigiNotar certificate authority breach, the Comodohacker attack, doppelganger domains collecting email, the Morto RDP worm, Android mobile phone monitoring services, the Linux kernel source code breach, and new malware like Mebromi and Spyeyetrojan. It provides an overview of security tools like OWASP GoatDroid and updates to existing tools. Finally, it lists some security reading materials.Advanced Malware Analysis
Advanced Malware AnalysisPrathan Phongthiproek
╠²
The document discusses security challenges posed by modern malware and web-based attacks. It provides examples of next-generation malware that bypass antivirus detection using techniques like embedding malicious code in Office documents or PDF files. It also discusses how web-based malware has evolved from defacements and DDoS tools to more advanced drive-by download attacks using exploit kits. The document aims to demonstrate malware analysis techniques and how to detect web server backdoors through tools and manual source code reviews. It concludes with a challenge to practice security skills safely.AtlSecCon 2016
AtlSecCon 2016Earl Carter
╠²
The document discusses emerging cybersecurity threats such as exploit kits, ransomware, and phishing scams. It provides an overview of the Angler exploit kit and how it has evolved, targeting vulnerabilities in Adobe Flash, Internet Explorer, and Silverlight. It also examines the CryptoWall ransomware version 4 and how it encrypts files and communicates with command and control servers. Additionally, it analyzes the SamSam ransomware attacks targeting healthcare organizations and the Rombertik malware which uses layers of obfuscation and anti-analysis techniques to propagate via spam and steal user credentials.Ransomware: History, Analysis, & Mitigation
Ransomware: History, Analysis, & MitigationWhiskeyNeon
╠²
The document provides an overview and analysis of ransomware, including its history, technical details, trends, and mitigation techniques. It discusses how ransomware has evolved from early variants like AIDS to modern cryptoware like CryptoLocker and Locky. The document also analyzes the infection process, command and control infrastructure, and outlines strategies organizations can take to help prevent and recover from ransomware attacks, such as backups, patching, and isolation of critical systems.Cyber Espionage Against Georgia (Georbot)
Cyber Espionage Against Georgia (Georbot)DataExchangeAgency
╠²
The document summarizes a cyber espionage attack against the Georgian government discovered in March 2011. Advanced malware was collecting sensitive security documents from Georgian and American systems and uploading them to command and control servers linked to Russian security agencies. The sophisticated malware infected over 390 computers, 70% of which were in Georgia, through compromised Georgian news websites. It was able to fully control infected machines, search for sensitive words, and record audio and video. After extensive analysis of command and control servers and malware files, Georgian authorities determined that the Russian government was behind the attack.G3t R00t at IUT
G3t R00t at IUTNahidul Kibria
╠²
The document outlines various roles in information security, including penetration testers, malware analysts, and forensic analysts, detailing necessary skills and methodologies for each. It emphasizes the importance of community collaboration within OWASP to enhance application security and provides information about tools and resources for security professionals. The document also describes a Capture the Flag (CTF) event aimed at testing participants' skills in computer security, alongside rules and criteria for judging their performance.Hacker Halted 2014 - Post-Exploitation After Having Remote Access
Hacker Halted 2014 - Post-Exploitation After Having Remote AccessEC-Council
╠²
The document details a hacking approach to bypass security measures of high-security remote desktop environments, focusing on malware deployment, privilege escalation, and circumventing application whitelisting. It emphasizes techniques for remote code execution, using simulated user interaction, and methods for bypassing hardware firewalls. The document also provides insights for red teams, blue teams, and policy makers regarding vulnerabilities in security implementations.Recently uploaded (20)
Complete University of Calculus :: 2nd edition
Complete University of Calculus :: 2nd editionShabista Imam
╠²
Master the language of change with the Complete Guidance Book of CalculusŌĆöyour comprehensive resource for understanding the core concepts and applications of differential and integral calculus. Designed for high school, college, and self-study learners, this book takes a clear, intuitive approach to a subject often considered challenging.Decoding Kotlin - Your Guide to Solving the Mysterious in Kotlin - Devoxx PL ...
Decoding Kotlin - Your Guide to Solving the Mysterious in Kotlin - Devoxx PL ...Jo├Żo Esperancinha
╠²
Kotlin can be very handy and easy to use. Kotlin offers the possibility to develop code that is easy to understand, safe, immutable, and thus predictable and follows standards that avoid side effects. I realized that very quickly after I started my Kotlin journey that already amounts to more than 5 years.
This is the third version of this presentation focused on more detail explaining inline, crossinline, tailrec and as a bonus a quick run through unnamed classes.Fundamentals of Digital Design_Class_12th April.pptx
Fundamentals of Digital Design_Class_12th April.pptxdrdebarshi1993
╠²
Boolean Algebra and Combinational Logic CircuitTesla-Stock-Analysis-and-Forecast.pptx (1).pptx
Tesla-Stock-Analysis-and-Forecast.pptx (1).pptxmoonsony54
╠²
this is data science ppt for tesla stock (linear regression)Rapid Prototyping for XR: Lecture 1 Introduction to Prototyping
Rapid Prototyping for XR: Lecture 1 Introduction to PrototypingMark Billinghurst
╠²
Lecture 1 of a course on Rapid Prototyping for XR taught by Mark Billinghurst at Oulu University on June 9th, 2025. This lecture presents an Introduction to Prototyping. (Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...ketan09101
╠²
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental practice in DevOps that streamlines software development and deployment.Complete guidance book of Asp.Net Web API
Complete guidance book of Asp.Net Web APIShabista Imam
╠²
Unlock the full potential of modern web development with the Complete Guidance Book of ASP.NET Web APIŌĆöyour all-in-one resource for mastering RESTful services using MicrosoftŌĆÖs powerful ASP.NET Core framework. This book takes you on a step-by-step journey from beginner to expert, covering everything from routing and controllers to security, performance optimization, and real-world architecture.International Journal of Advanced Information Technology (IJAIT)
International Journal of Advanced Information Technology (IJAIT)ijait
╠²
International journal of advanced Information technology (IJAIT) is a bi monthly open access peer-
reviewed journal, will act as a major forum for the presentation of innovative ideas, approaches,
developments, and research projects in the area advanced information technology applications and
services. It will also serve to facilitate the exchange of information between researchers and industry
professionals to discuss the latest issues and advancement in the area of advanced IT. Core areas of
advanced IT and multi-disciplinary and its applications will be covered during the conferences.Tally.ERP 9 at a Glance.book - Tally Solutions .pdf
Tally.ERP 9 at a Glance.book - Tally Solutions .pdfShabista Imam
╠²
Tally.ERP 9 at a Glance.book, a fully completed guidance to learn tally erp 9.0ElysiumPro Company Profile 2025-2026.pdf
ElysiumPro Company Profile 2025-2026.pdfinfo751436
╠²
Description
ElysiumPro | IEEE Final Year Projects | Best Internship Training | Inplant Training in Madurai
Best Final Year project training center
Address:
First Floor, A Block, 'Elysium Campus, 229, Church Rd, Vaigai Colony, Madurai, Tamil Nadu 625020
Plus Code:
W4CX+56 Madurai, Tamil Nadu
+91 9944793398
info@elysiumpro.in
Elysium Group of Companies established ElysiumPro in 2001. Since its inception, it has been the most sought-after destination for final year project development and research papers among the students. Our commitment to providing quality project training & documentation to students has always been exceptional. We deliver the final year engineering projects and technical documents that provide extra edge and industry exposure to land prestigious jobs and reputed institutions for higher studies. Students from all over the country avail of our services for their final year projects. On average, we develop 5000+ projects and research papers per year on varied advanced domains. Python, JAVA, PHP, Android, Matlab, LabView, VLSI, SIMULINK, Power electronics, Power System, Antenna, Machine Learning, Deep Learning, Data Science, Artificial Intelligence, data Mining, Big Data, Cloud Computing, IoT,
Hours of Operation: -
Sunday 10am-1pm
Monday 7.30am-8pm
Tuesday 7.30am-8pm
Wednesday 7.30am-8pm
Thursday 7.30am-8pm
Friday 7.30am-8pm
Saturday 7.30am-8pm
Web Site:
https://elysiumpro.in/
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Youtube Geotagged Video:
https://youtu.be/QULY6XfuMyo
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
║▌║▌▀Żshow Images (Google Photos):
https://photos.app.goo.gl/hVwQJtkeptA1JZKd9
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
GBP Listing:
https://goo.gl/maps/6d6hko6TsDYyeDrz9
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Serving Areas:
https://www.google.com/maps/d/edit?mid=1-fsZogBiEAcjGP_aDyI0UKKIcwVUWfo&usp=sharing
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google Site:
https://elysiumpro-project-center.business.site
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google Sheet: https://docs.google.com/spreadsheets/d/1uXA07zxrUx2FCnBZWH80PpBZQrrX-2q1UBBe_0k3Yeo
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google Document: https://docs.google.com/document/d/1BU4ZHW_41XJm2lvTq9pWYUpZILAEmF9dWEw7-DBbWoE
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google ║▌║▌▀Żs: https://docs.google.com/presentation/d/1uF8q6ueJWcAnhKTQsZxLE0Bo9PwgRNwCeuGV_ZgbSyU
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*Cadastral Maps
Cadastral MapsGoogle
╠²
Preparation of cadastral maps based by Engineer Dungo Tizazu from Dire Dawa University A Cluster-Based Trusted Secure Multipath Routing Protocol for Mobile Ad Hoc N...
A Cluster-Based Trusted Secure Multipath Routing Protocol for Mobile Ad Hoc N...IJCNCJournal
╠²
Mobile Ad Hoc Network (MANET) is a self-organizing and flexible system. MANET systems manage sensitive data from many distinct applications in various domains. Its dynamic nature increases its vulnerability to numerous types of security threats. Many of the present approaches using indirect approaches provide false approximations of trust degrees. It is significantly required a good routing system that meets Quality of Service (QoS) standards and enhances network performance. In this paper purposed cluster-based trustworthy safe multipath routing (CTSMP-Routing) for mobile ad hoc networks (MANETs). Load balancing challenge is addressed by using a modified proportional topology optimization (MPTO) approach using geographical data related to network nodes. The Enhanced Seeker Search Optimization (ESSO) approach is used to compute trust degrees after the clustering phase considering numerous network constraints including node mobility, received signal strength, energy consumption, and cooperation rate. Assumed to be the service node, the node showing the highest degree of trust manages inter-cluster routing. We have developed a hybrid soft computing approach termed the multi-layer deep recurrent neural network (ML-DRNN) to enhance the optimal path-finding process. This method selects, among many routes between source and destination nodes, the best one quickly. The outcomes of this paper demonstrate that CTSMP-Routing provides effective protection against several attack paths within the MANET environment and displays better performance in regard to quality of service (QoS) requirements.Decoding Kotlin - Your Guide to Solving the Mysterious in Kotlin - Devoxx PL ...
Decoding Kotlin - Your Guide to Solving the Mysterious in Kotlin - Devoxx PL ...Jo├Żo Esperancinha
╠²
Ad
TS/NOFORN
- 1. MARIONMARSCHALEK@PINKFLAWDMARION@CYPHORT.COMBCC0 7607 2FFA BCA8 9048 D648 D169 73AF F372 F2CA
- 2. Welcome to the keynote circuit ŌĆōI thought thatŌĆśs where old people like me go to die? ;) -Halvar Flake, Oct.14 2014
- 7. http://www.fanpop.com/ SOPHISTICATEDWEAPONRY WITH SUPERPOWERS
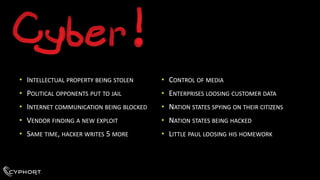
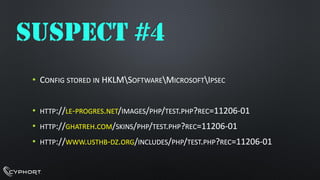
- 12. SUSPECT #1 ŌĆóFILESIZE:192512ŌĆóCOMPILETIME: 2010:05:06 ŌĆóC&C: CALLIENTEFEVER.INFOŌĆóHTTP ACCEPT-LANGUAGE: FR
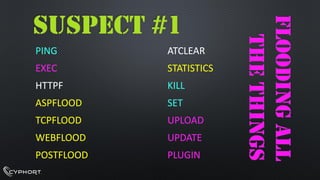
- 14. PING EXEC HTTPFASPFLOODTCPFLOODWEBFLOODPOSTFLOODATCLEAR STATISTICSKILLSET UPLOAD UPDATE PLUGIN SUSPECT #1 FLOODING ALL THE THINGS
- 15. SUSPECT #1
- 16. OMG!!
- 17. SUSPECTS #[2-4] ŌĆóFILESIZE: 184320 ŌĆóCODESIZE: 139264 ŌĆóCOMPILETIME: 2010:02:16 18:05:54+01:00 ŌĆóFILESIZE: 184320 ŌĆóCODESIZE: 139264 ŌĆóCOMPILETIME: 2010:03:11 17:55:03+01:00 ŌĆóFILESIZE: 792064 ŌĆóCODESIZE: 583680 ŌĆóCOMPILETIME: 2011:10:2520:28:39+01:00
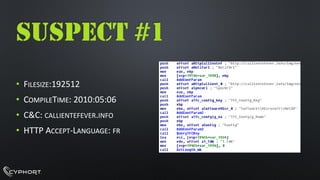
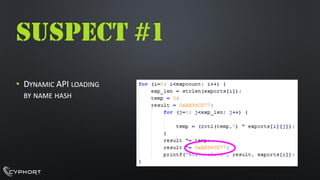
- 18. SUSPECT #4 ŌĆóFILESIZE: 792064 ŌĆóCOMPILETIME: 2011:10:2520:28:39+01:00ŌĆóAPI NAMEHASHINGKEYAB34CD77HŌĆóHTTP://1.9.32.11/BUNNY/TEST.PHP?REC=NVISTAANTI-ANALYSIS| THREADS& FILES| CPU DATA| C&C COMMANDS| LUA
- 19. Not funny.
- 20. AV PRODUCTENUMERATIONFIREWALLPRODUCTENUMERATIONSANDBOXCHECK"KLAVME", "MYAPP", "TESTAPP", "AFYJEVMV.EXEŌĆ£, TIMINGCONDITIONSUSPECT #4SELECT * FROM ANTIVIRUSPRODUCTSELECT * FROM FIREWALLPRODUCT
- 21. SUSPECT #4Big BossWorker2Worker1Worker0Worker3MainThreadPerfMon CommandParsing ScriptExecution Manage Worker ThreadsFileMan/Inet
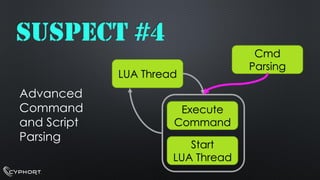
- 23. LUA ThreadCmd ParsingExecute CommandStart LUA ThreadSUSPECT #4 Advanced Command and Script Parsing
- 24. SUSPECT #4 Advanced Command and Script Parsing4 WORKERTHREADSEXECUTINGLUA SCRIPTSLUA 5.1 + C/INVOKECODECALLBACKFROMLUA TOC++
- 26. Vulnerability Summary for CVE-2011-4369 Original release date: 12/16/2011 Last revised: 01/29/2013 Source: US-CERT/NIST http://blog.9bplus.com/analyzing-cve-2011-4369-part-one/
- 27. SUSPECT #5 ŌĆóFILESIZE: 966144 ŌĆóCODESIZE: 128512 ŌĆóCOMPILETIME: 2011:10:2519:28:00+01:00 ŌĆóDROPPERFORSUSPECT#4 ŌĆóSAMEC&CSASSUSPECT#4
- 28. ACRORD32INFO.EXE Location Remote Host Port Number Oakville, Canada 69.90.160.65 80 Montr├®al,Canada 70.38.107.13 80 Montr├®al,Canada 70.38.12.10 80 http://www.threatexpert.com/report.aspx?md5=c40e3ee23cf95d992b7cd0b7c01b8599SUSPECT #5
- 29. SRSLY?
- 32. SWISS CHEESE ATTRIBUTIONŌĆóPROJECTNAMEDBUNNY, VERSION2.3.2ŌĆóDDOS BOTNETOPERATORSŌĆóACCEPT-LANGUAGE: FRŌĆóC&C SERVERSHOSTEDINCANADAŌĆóC&C DOMAINSRESEMBLEFRENCH/IRANIANWEBSITESŌĆóAUTHORNOENGLISHNATIVE-SPEAKER... ŌĆóLUA? MUSTBEFLAME
- 33. Wars not make one great.
- 39. Viperis a binary management and analysis frameworkdedicated to malware and exploit researchers. http://viper.li/
- 40. ACKNOWLEDGEMENTSŌĆóMR. WHITE, MR. ORANGE, MR. BLONDE& MR. PINKŌĆóMORGANMARQUIS-BOIREŌĆóINBARRAZŌĆóNICOLASBRULEZŌĆó@EMERGENCYKITTENS
- 41. Thank you! Marion Marschalek @pinkflawd marion@cyphort.com http://karmadecay.com/