UMA Trusted Claims
- 1. Extending UMA Protocol to support Trusted Claims (tClaims) Newcastle University Domenico Catalano and the Smart Team 13th July, 2011 1 V.3 Wednesday, July 13, 2011
- 2. Who I am âĒ Domenico Catalano âĒ Senior Sales Consultant @Oracle Italy + Sun âĒ Identity & Security Architect âĒ Leadership team member (UX) @Kantara UMA WG 2 Wednesday, July 13, 2011
- 3. Agenda âĒ UMA Conceptual model âĒ tClaims Requirements Analysis âĒ OpenID Connect âĒ UMA/OpenID Connect Integration approach âĒ User Interaction âĒ Trust Model consideration âĒ Q&A 3 Wednesday, July 13, 2011
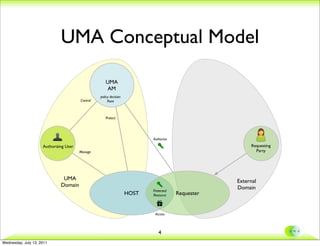
- 4. UMA Conceptual Model UMA AM policy decision Control Point Protect Authorize Authorizing User Requesting Manage Party UMA External Domain Domain Protected HOST Resource Requester Access 4 Wednesday, July 13, 2011
- 5. UMA Trusted Claims âĒ UMA Trusted Claims approach is designed to support Claims-based Access Control. âĒ In a Claim-based Access Control, the decision to grant access to a protected resource is made based on Subjectâs information, such as name, age, email address, role, location, or credit score, etc. Claims Trusted Claims Trusted usted C laims 5 Wednesday, July 13, 2011
- 6. tClaims example scenarios âĒ Enterprise class scenario âĢ Accessing Personal Loan Special Program âĒ Social/web class scenario âĢ Sharing photo with âbob@gmail.comâ 6 Wednesday, July 13, 2011
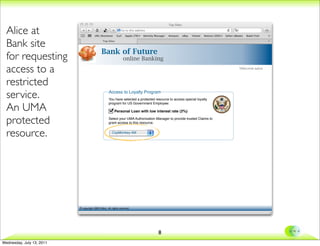
- 7. Accessing Personal Loan special program Enterprise Class Scenario âĒ Bank online service provides an User- Managed Claims access control to restrict and personalize access to special program/ service (i.e. personal loan with low interest rate) to users which have determinate employment (i.e. government employee), and have an high credit score. 7 Wednesday, July 13, 2011
- 8. Alice at Bank site Bank of Future for requesting 10.0 online Banking access to a Welcome aalice restricted service. Access to Loyalty Program You have selected a protected resource to access special loyalty An UMA program for US Government Employee: Personal Loan with low interest rate (2%) protected Select your UMA Authorization Manager to provide trusted Claims to grant access to this resource. resource. CopMonkey AM ÂĐ copyright 2009 CMInc. All rights reserved. 8 Wednesday, July 13, 2011
- 9. Sharing Photo with âbob@gmail.com Social/web Class Scenario âĒ Alice wants share a photo gallery with bob if Bob has an account email âbob@gmail.comâ and he is 18 years old. 9 Wednesday, July 13, 2011
- 10. Alice deïŽnes claims-based authorization policy, using In- App widget 10 Wednesday, July 13, 2011
- 11. Requirements Analysis âĒ Authorizing User (Resource Owner) needs a claims- based access control to restrict access to own resources based on Requesting Partyâs Identity attributes. âĒ Identity attributes must issued by a Trusted Third Party (TTP) and veriïŽable by a Claims Requester. âĒ Claims may be logically aggregated to provide a collection of attributes from different Attribute Providers (Claims Host). 11 Wednesday, July 13, 2011
- 12. OpenID Connect âĒ OpenID Connect provides authentication, authorization, and attribute transmission capability. It allows third party attested claims from distributed sources. âĒ This speciïŽcation is largely compliant with OAuth 2.0 draft 15. OpenID Connect Core 1.0 - draft 04 12 Wednesday, July 13, 2011
- 13. OpenID Connect protocol overview âĒ OpenID Connect protocol in abstract follows the following steps: 1. The Client sends a request to the Serverâs End-User Authorization Endpoint. 2. The Server authenticates the user and obtains appropriate authorization. 3. The Server responds with access_token and a few other variables. 4. The Client sends a request with access_token to the Userinfo Endpoint. 5. Userinfo Endpoint returns the additional user supported by the Server. 13 Wednesday, July 13, 2011
- 14. UMA Conceptual Model UMA AM policy decision Control Point Protect Authorize Authorizing User Requesting Manage Party UMA External Domain Domain Protected HOST Resource Requester Access 14 Wednesday, July 13, 2011
- 15. UMA Conceptual Model with tClaims OpenID UMA Claims 1. Request Client 3. Access_token Connect AM AS policy decision Control Point 5. Userinfo 2. AuthN AuthZ 4. Request Userinfo Protect Protect Authorize UserInfo Authorizing User EndPoint Requesting Manage Party SSO UMA OpenID Domain Domain Protected HOST Resource Requester Access 15 Wednesday, July 13, 2011
- 16. UMA/OpenID Connect Integration approach UserInfo EndPoint Claims Claims Provider Protected Resource UMA Claims AuthZ OpenID Authorization Client Server Identity Provider Manager OpenID RP OpenID Connect SSO AuthN AuthZ Requesting Party 16 Wednesday, July 13, 2011
- 17. User eXperience 17 Wednesday, July 13, 2011
- 18. Scenario âĒ Sharing Photo with âbob@gmail.comâ âĢ Host In-App Fast Sharing settings. âĢ Requesting Party requests direct access to Protected Resource. âĢ OpenID Connect interaction. 18 Wednesday, July 13, 2011
- 19. Alice at Host Site Protected Resource by CopMonkey AM in-App Fast AuthZ Settings for sharing 19 Wednesday, July 13, 2011
- 20. Alice deïŽnes claims-based authorization policy, using In- App widget 20 Wednesday, July 13, 2011
- 21. Protected Resource is ready for sharing under authZ policy 21 Wednesday, July 13, 2011
- 22. Alice shares the Protected Photo4Sharing resource 10.0 online photo Service through twitter Home Photo Gallery Places Share Settings Hello Alice Alice twitter Photo View Resource Sharing Photo4Sharing: Places:Venice:Bridge at Places> Venice> Bridge Edit CopMonkey Protected http://photo4sharing.com/AB112FFD Resource 22 hours ago reply CopMonkey In-App Claim- based authorization Tweet text goes here. URL keep it under 140 characters photo4sharing.com/AB112FFD http://bit.ly/ds5c6z 22 hours ago reply Share Never thought I'd say this, but sign out of twitter.com, now! There's a nice new homepage to check out. http://bit.ly/ds5c6z 22 hours ago reply homepage to check out. http://bit.ly/ds5c6z 22 hours ago reply ÂĐ copyright 2009 CMInc. All rights reserved. 22 Wednesday, July 13, 2011
- 23. Bob attempts to access to protected resource. Bob is redirect to AM to convey claims 23 Wednesday, July 13, 2011
- 24. CopMonkey authenticates Bob through OpenID, in order to initialize OpenID Connect protocol 24 Wednesday, July 13, 2011
- 25. Bob is redirect to IdPâs authorization service to grant claims. 25 Wednesday, July 13, 2011
- 26. Bob gets access to the protected resource 26 Wednesday, July 13, 2011
- 27. Trust Model Consideration Bootstrapping Trust Claims Provider AuthN IdP AuthN IdP Subject Subject Subject Self Registration AfïŽliate Registration AfïŽliate Registration LoA CertiïŽcation UMA UMA UMA AM AM AM Trusted Self Registration AfïŽliate Registration AfïŽliate Registration Framework Host Introduction Host Introduction Host Introduction Host Host Host TFP A B C Self-Registration AfïŽliate or SSO AfïŽliate or SSO with Trusted Framework 27 Wednesday, July 13, 2011
- 28. Thanks 28 Wednesday, July 13, 2011