Understand Internet Before You Regret.
- 1. INTERNET Understand Internet Before You Regret Only for Education purpose
- 2. INTERNET ’üĄ The internet is a globally connected network system. ’üĄ When most of us think of the internet, we imagine day-to-day activities like 1. Watching a video. 2. Checking the news. 3. Booking a vacation online.
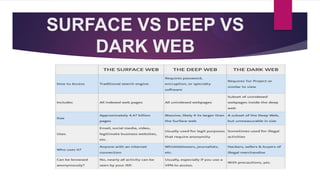
- 3. SURFACE WEB ’üĄ The surface web is the portion of content on the INTERNET that is readily available to the general public and searchable with standard search engines. ’üĄ The Surface Web only consists of 10 percent of the information that is on the internet. ’üĄ Google's index of the surface web contains about 14.5 billion pages.
- 4. DEEP WEB - I ’üĄ Deep Web is a part of the invisible web that a normal user cannot access. ’üĄ Deep Web access only if one has the authorization or login credentials to do so. ’üĄ The data stored in the deep ranges from ’üĄ Personal information (including military data) ’üĄ Financial records. ’üĄ Academic databases. ’üĄ Medical records. ’üĄ Government records.
- 5. DEEP WEB - II ’üĄ You just need a special authorization or access credentials to access the information on the Deep Web. ’üĄ Example: ’üĄ You normally generate a PIN or OTP to access your online banking account ’üĄ It is only once you enter the PIN/OTP that you are able to log into your account. ’üĄ You cannot get into your account by typing ŌĆśSumit ParvatŌĆÖs Banking AccountŌĆÖ on a search engine.
- 6. DARK WEB - I ’üĄ Dark Web an encrypted section of the web that offers complete anonymity as it is not indexed by search engines. ’üĄ It requires the use of an anonymizing browser called Tor to be accessed. ’üĄ The dark web is an instrument to illegal activities like ’üĄ Child pornography ’üĄ The sale of drugs ’üĄ Firearms ’üĄ Stolen credit card numbers.
- 7. ’üĄ What is Available on The Dark Web? ’üĄ Credit card numbers ’üĄ Fake passports ’üĄ Stolen/Hacked Accounts ’üĄ Fake College Degrees ’üĄ Murder for hire/Assassination ’üĄ Plastic Explosives ’üĄ Weapons ’üĄ SWAT-style body armour ’üĄ Hacked Government Data DARK WEB - II
- 8. THE TOR PROJECT ’üĄ Tor is free and open-source software for enabling anonymous communication. ’üĄ the original software project name "The Onion RouterŌĆ£. ’üĄ Tor was developed in the mid-1990s by United States Naval Research Laboratory employees. ’üĄ To exchange sensitive and confidential data anonymously.
- 9. WORKING OF TOR ’üĄ Your data is bundled into an encrypted packet when it enters the Tor network. ’üĄ Tor strips away part of the packet's header. ’üĄ Tor encrypts the rest of the addressing information, called the packet wrapper. ’üĄ The modified and encrypted data packet is then routed through many of these servers, called relays, on the way to its final destination ’üĄ Each relay decrypts only enough of the data packet wrapper to know which relay the data came from, and which relay to send it to next. ’üĄ The relay then rewraps the package in a new wrapper and sends it on.
- 10. SURFACE VS DEEP VS DARK WEB
- 11. THANK YOU !!!