Usb forensics BSides London 2015
- 1. Investigating USB Devices On Windows 7 & 8 BSIDES LONDON 2015
- 2. Whoami?
- 3. What you need to know before you start As with any forensic investigation; you really need to know what you are looking for! ŌŚ” What is the scenario? ŌŚ” Are you looking to prove/disprove something? ŌŚ” Do you have any details around the USB device? ŌŚ” What is the end goal? ŌŚ” Proof that IP was stolen? ŌŚ” Illegal content of the device? ŌŚ” Exploratory ? ŌŚ” Additional details? ŌŚ” Computer name? ŌŚ” Time-zone? ŌŚ” User level? ŌŚ” Time since last rebuild? ŌŚ” Any other relevant details about the user?
- 4. Scenario ŌĆóScrooges Crutches Ltd want us to look into Timmy Cratchet ŌĆóA USB stick belonging to Timmy was discovered and has Intellectual Property on it ŌĆóScrooge only uses authorised USB devices ŌĆóTimmyŌĆÖs machine should only have one USB storage device used
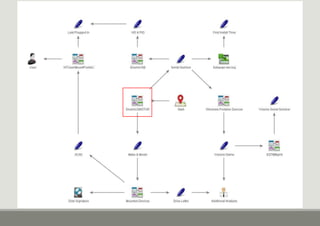
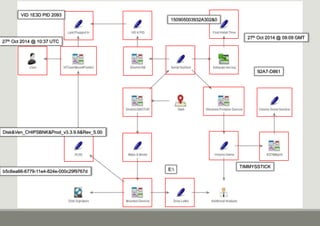
- 6. Identifying the Device Serial Number in the USBSTOR The USBSTOR key contains all of the USB Storage Devices registered on the machine. ŌĆó Located within the SYSTEM hive ŌĆō SYSTEMCurrentControlSetEnumUSBSTOR ŌĆó Each Key may contain more than one device ŌĆō The sub-keys contain the Serial Number of that device ŌĆō All Serial numbers end with either &0 or &1 ŌĆō Serial numbers where the second character is a & are serial number issued by Windows and unique to this machine only
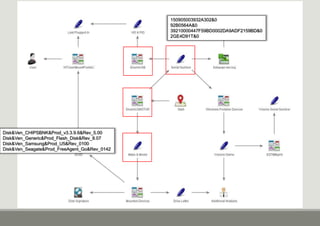
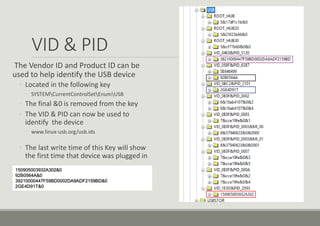
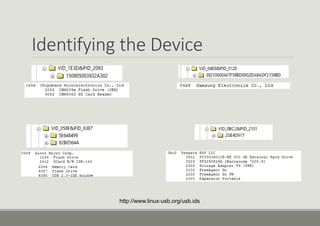
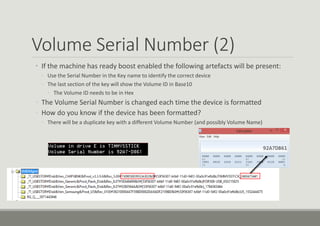
- 8. VID & PID The Vendor ID and Product ID can be used to help identify the USB device ŌŚ” Located in the following key ŌŚ” SYSTEMCurrentControlSetEnumUSB ŌŚ” The final &0 is removed from the key ŌŚ” The VID & PID can now be used to identify the device ŌŚ” www.linux-usb.org/usb.ids ŌŚ” The last write time of this Key will show the first time that device was plugged in 150905003932A302&0 92B0564A&0 39210000447F59BD0002DA9ADF2159BD&0 2GE4D91T&0
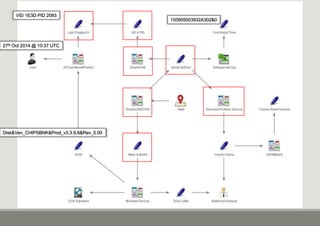
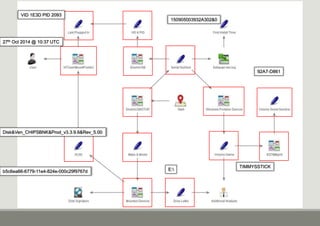
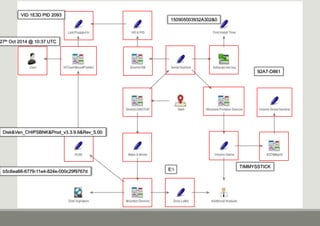
- 10. 150905003932A302&0 Disk&Ven_CHIPSBNK&Prod_v3.3.9.6&Rev_5.00 VID 1E3D PID 2093 27th Oct 2014 @ 10:37 UTC
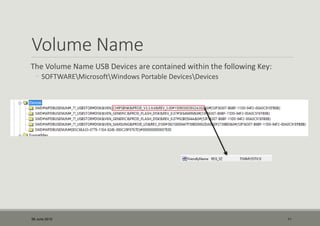
- 11. Volume Name The Volume Name USB Devices are contained within the following Key: ŌŚ” SOFTWAREMicrosoftWindows Portable DevicesDevices 06 June 2015 11
- 12. 150905003932A302&0 Disk&Ven_CHIPSBNK&Prod_v3.3.9.6&Rev_5.00 VID 1E3D PID 2093 TIMMYSSTICK 27th Oct 2014 @ 10:37 UTC
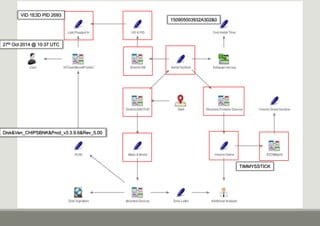
- 13. Volume Serial Number ŌĆó The Volume Serial Number information is stored in the following key ŌŚ” SOFTWAREMicrosoftWindows NTCurrentVersionEMDMgmt ŌŚ” This key was originally designed for use with ReadyBoost (Vista +) ŌŚ” Machines deemed too fast for ReadyBoost will not have any data in this key ŌŚ” Usually if an SSD drive is installed ŌŚ” ReadyBoost also enable SuperPreFetch and Auto Defrag which significantly reduce the lifespan of an SSD ŌŚ” As such if an SSD is present on a Windows 7 system ReadyBoost is disabled ŌŚ” A Windows 8 System will test the performance first
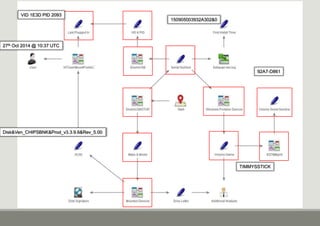
- 14. Volume Serial Number (2) ŌĆó If the machine has ready boost enabled the following artefacts will be present: ŌŚ” Use the Serial Number in the Key name to identify the correct device ŌŚ” The last section of the key will show the Volume ID in Base10 ŌŚ” The Volume ID needs to be in Hex ŌŚ” The Volume Serial Number is changed each time the device is formatted ŌŚ” How do you know if the device has been formatted? ŌŚ” There will be a duplicate key with a different Volume Number (and possibly Volume Name)
- 15. Disk&Ven_CHIPSBNK&Prod_v3.3.9.6&Rev_5.00 VID 1E3D PID 2093 150905003932A302&0 92A7-D861 TIMMYSSTICK 27th Oct 2014 @ 10:37 UTC
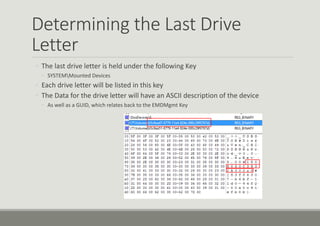
- 16. Determining the Last Drive Letter ŌŚ” The last drive letter is held under the following Key ŌŚ” SYSTEMMounted Devices ŌŚ” Each drive letter will be listed in this key ŌŚ” The Data for the drive letter will have an ASCII description of the device ŌŚ” As well as a GUID, which relates back to the EMDMgmt Key
- 17. Determining the Last Drive Letter ŌŚ” The last drive letter is held under the following Key ŌŚ” SYSTEMMounted Devices ŌŚ” Each drive letter will be listed in this key ŌŚ” The Data for the drive letter will have an ASCII description of the device ŌŚ” As well as a GUID, which relates back to the EMDMgmt Key
- 18. VID 1E3D PID 2093 150905003932A302&0 92A7-D861 TIMMYSSTICK Disk&Ven_CHIPSBNK&Prod_v3.3.9.6&Rev_5.00 b5c6ea66-6779-11e4-824e-000c29f9767d E: 27th Oct 2014 @ 10:37 UTC
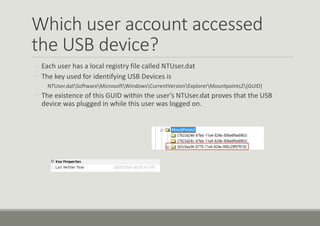
- 19. Which user account accessed the USB device? ŌŚ” Each user has a local registry file called NTUser.dat ŌŚ” The key used for identifying USB Devices is ŌŚ” NTUser.datSoftwareMicrosoftWindowsCurrentVersionExplorerMountpoints2{GUID} ŌŚ” The existence of this GUID within the userŌĆÖs NTUser.dat proves that the USB device was plugged in while this user was logged on.
- 20. VID 1E3D PID 2093 150905003932A302&0 92A7-D861 TIMMYSSTICK Disk&Ven_CHIPSBNK&Prod_v3.3.9.6&Rev_5.00 b5c6ea66-6779-11e4-824e-000c29f9767d E: 27th Oct 2014 @ 10:37 UTC
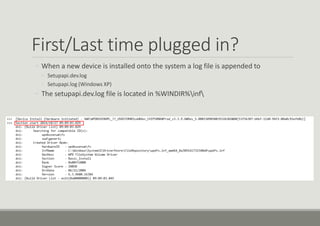
- 21. First/Last time plugged in? ŌŚ” When a new device is installed onto the system a log file is appended to ŌŚ” Setupapi.dev.log ŌŚ” Setupapi.log (Windows XP) ŌŚ” The setupapi.dev.log file is located in %WINDIR%inf
- 22. VID 1E3D PID 2093 92A7-D861 TIMMYSSTICK Disk&Ven_CHIPSBNK&Prod_v3.3.9.6&Rev_5.00 b5c6ea66-6779-11e4-824e-000c29f9767d E: 27th Oct 2014 @ 10:37 UTC 27th Oct 2014 @ 09:09 GMT 150905003932A302&0
- 23. Summary Report A USB Device, a Chipsbank Microelectonics CBM209x, with a serial number 150905003932A302 was plugged at 27th Oct 2014 @ 09:09 GMT for approximately 90 minutes; it was last seen at 27th Oct 2014 @ 10:37 UTC. The device had a Volume Name or ŌĆślabelŌĆÖ of TIMMYSSTICK, it is almost certain that the drive letter used was E: and user TIMMY was the only account to have encountered this device. It is recommended a timeline is created of the machine for those 90 minutes to determine what data, if any, was copied or moved to the device. As a consultant I can do this for youŌĆ”.. ŌĆ”..letŌĆÖs talk day rates
- 25. References & Twitter My Blog ŌŚ” www.HatsOffSecurity.com ŌŚ” And Google Twitter ŌŚ” @Russ_Taylor_