USENIX NSDI17 Memory Disaggregation
- 1. USENIX NDSI 2017óžæ & Efficient Memory Disaggregation with Infiniswap (University of Michigan) íÆéÓĐż” ¶ÀÁąĐĐŐț·šÈË źbIŒŒĐgŸtșÏŃĐŸżËù ”Ú2»Ű „·„č„Æ„àÏ”ĘÖv»á
- 2. NSDI2017žĆÒȘ ? 14th USENIX Symposium on Networked Systems Design and Implementation ? https://www.usenix.org/conference/nsdi17 ? MARCH 27šC29, 2017, BOSTON, MA ? ͶžćÊę254±ŸĄąńk46±ŸĄą„·„ó„°„ë„»„Ă„·„ç„óĄą„©`„Ω`„Ȁʀ·ĄŁ ? ÖśŽßŐ߀«€é°k±í€”€ì€żœńÄê€ÎNSDIŐÎÄ€ÇÊč€ï€ì€ż„©`„ï©`„É ? SecurityĄąData CenterĄąDistributed SystemsĄąBig Data ? Best Paper Award ? mOS: A Reusable Network stack for Flow Monitoring Middleboxes (KAIST) ? Community Award ? Transparently Compress Hundreds of Petabytes of Image Files for a File- Storage Service (Stanford)
- 3. È˔ĀʞĐÏë ? „Í„Ă„È„ï©`„Ż€Ź„á„€„ó€Ç€Ê€€°k±í€Ź¶à€Ż€ą€êĄą€Ê€ŒNSDI€Ç°k ±í€č€ë€Î€«€ÈËŒ€ï€ì€ë€â€Î€ŹŚ€Ä€«€ą€Ă€żĄŁ ? „»„„ć„ê„Æ„Ł€ÏÈ«13„»„Ă„·„ç„óÖĐĄąŁČ„»„Ă„·„ç„ó€ą€êĄą„»„„ć „ê„Æ„Ł€ÎévĐĀΞ߀€ĄŁ ? ínčú€«€é€Ï4±Ÿ€ÎŐÎÄ(KAIST 3±ŸĄąhêŽóѧУ1±Ÿ)€Źńk€”€ì €Æ€Ș€êĄąŽæÔڞЀŹ€ą€Ă€żĄŁÌŰ€ËKAIST€Ï„ł„ó„č„ż„ó„È€ËŐÎÄ€ò łö€·€Æ€€€ëĄŁ ? SDN: Software Designed Network€Ëév€č€ë°k±í€Ź¶à€Ż€ą€Ă€żĄŁ ? Ëû€Î»áŚh€Ç€ÏÔî}€È€Ê€Ă€Æ€€€ëzmap€Ê€É€òÊč€Ă€żInternetÈ«Ìć €òÏó€Ë€·€żŐ{Ë€ŹNSDI€Ç€ÏÒ»€Ä€â€Ê€«€Ă€ż€ł€È€ŹČ»ËŒŚh
- 4. Efficient Memory Disaggregation with Infiniswap (University of Michigan) ? €ł€ÎŐÎÄ€ËQ€á€żÀíÓÉ
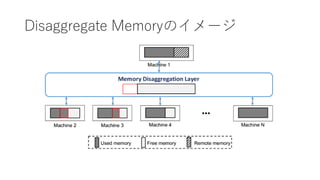
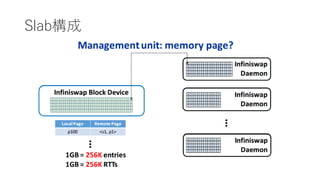
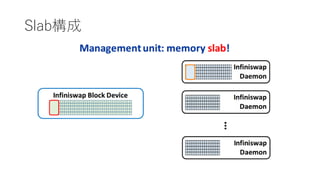
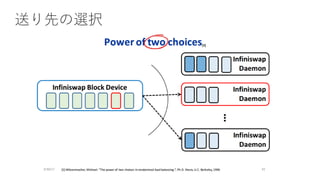
- 5. Infiniswap €ÎžĆÒȘ ? Motivation ? Memory Intensive€Ê„ą„Ś„ê€Ź¶à€€ĄŁ ? „Ç©`„ż„»„ó„ż©`€Ç€Î„á„â„êÀûÓĂ€ÎÆ«€êĄŁ ? RDMA€ò»îÓĂ€·€żDisaggregation Memory ? Challenge ? No application modification, Scalability, Fault-tolerance ? Swap€Î¶țÖŰ»Ż(RDMA or DISK) ? Control Plane (žś„Ț„·„ó€Îdeamon)€ÈData Plane (RDMA)€Î·ÖëxĄŁ ? 4KBÎïÀí„Ú©`„ž€Ë€·€Æ(1GB) slab€Ë€è€ëčÜÀíĄŁ ? decentralized slab placements and evictions. ? power of two random choice.
- 6. Motivation 1 ? Memory Intensive application€Ź¶à€€€ŹĄą
- 7. Motivation 1 ? Memory Intensive application€Ź¶à€€€ŹĄą
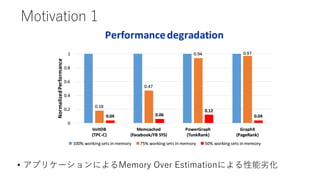
- 8. Motivation 1 ? „ą„Ś„ꄱ©`„·„ç„ó€Ë€è€ëMemory Over Estimation€Ë€è€ëĐÔÄÜÁÓ»Ż
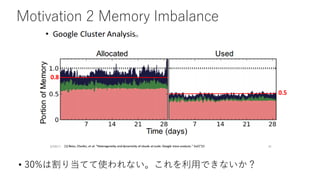
- 9. Motivation 2 Memory Imbalance ? 30%€Ïžî€ê”±€Æ€ÆÊč€ï€ì€Ê€€ĄŁ€ł€ì€òÀûÓÀǀ€Ê€€€«Łż
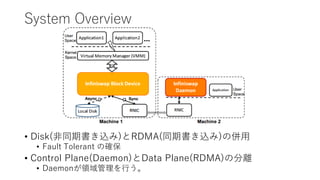
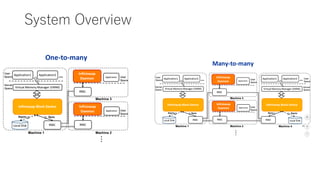
- 12. System Overview ? Disk(·ÇÍŹÆÚű€Țz€ß)€ÈRDMA(ÍŹÆÚű€Țz€ß)€ÎăÓĂ ? Fault Tolerant €ÎŽ_±Ł ? Control Plane(Daemon)€ÈData Plane(RDMA)€Î·Öëx ? Daemon€ŹîIÓòčÜÀí€òĐĐ€ŠĄŁ
- 13. System Overview
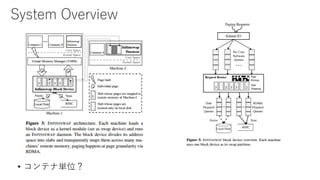
- 15. ł§±ôČčČúččłÉ
- 16. ł§±ôČčČúččłÉ
- 17. ËÍ€êÏÈ€ÎŃĄk
- 18. power of two random choices ? decentralized slab placements and evictions€ÎžÎ ? Michael Mitzenmacher, The Power of Two Choices in Randomized Load Balancing, Ph.D Thesis, 2001. ? https://pdfs.semanticscholar.org/3885/812a092ff0aad3d45c0464660075e98d0231.pdf ? Michael Mitzenmacher, Andrea Richa, Ramesh Sitaraman,The Power of Two Random Choices: A Survey of Techniques and Results, 1996. ? http://www.ic.unicamp.br/~celio/peer2peer/math/mitzenmacher-power-of-two.pdf ? Michael Mitzenmacher, The Power of Two Choices in Randomized Load Balancing, IEEE Trans. Parallel and Distributed Systems, 2001. ? https://www.eecs.harvard.edu/~michaelm/postscripts/tpds2001.pdf
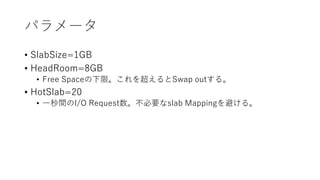
- 19. „Ń„é„á©`„ż ? SlabSize=1GB ? HeadRoom=8GB ? Free Space€ÎÏÂÏȚĄŁ€ł€ì€òłŹ€š€ë€ÈSwap out€č€ëĄŁ ? HotSlab=20 ? Ò»Ăëég€ÎI/O RequestÊꥣȻ±ŰÒȘ€Êslab Mapping€ò±Ü€±€ëĄŁ
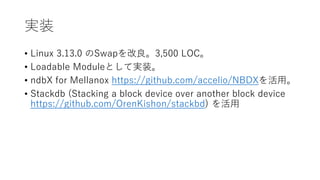
- 20. gŚ° ? Linux 3.13.0 €ÎSwap€òžÄÁŒĄŁ3,500 LOCĄŁ ? Loadable Module€È€·€ÆgŚ°ĄŁ ? ndbX for Mellanox https://github.com/accelio/NBDX€ò»îÓĂĄŁ ? Stackdb (Stacking a block device over another block device https://github.com/OrenKishon/stackbd) €ò»îÓĂ
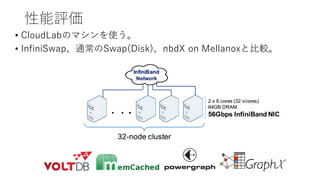
- 21. ĐÔÄÜÆÀę ? CloudLab€Î„Ț„·„ó€òÊ耊ĄŁ ? InfiniSwapĄąÍšłŁ€ÎSwap(Disk)ĄąnbdX on Mellanox€È±ÈĘ^ĄŁ
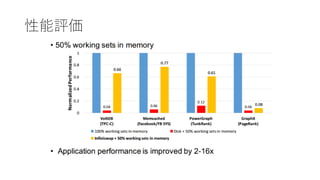
- 22. ĐÔÄÜÆÀę
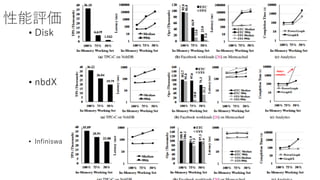
- 23. ĐÔÄÜÆÀę ? Disk ? nbdX ? Infiniswap
- 24. Fault Tolerant€Î„Æ„č„È ? VoltDB(75% memory)ĄąSLAB„Ț„·„óŁ¶Ìš€Î€Š€ÁĄą1Ìš€òÂä€È€· €żöșÏ€ÎĐÔÄÜÁÓ»ŻĄŁ
- 25. Discussion ? Application-aware Design ? „ą„Ś„ê€Źremote memory€òŐJŚR(îl·±€ËÊ耊Hot Table€ÈÊč€ï€Ê€€Cold Table)€·€Æ„Ś„í„°„é„à€·€ż€Û€Š€ŹÔ瀀ĄŁ ? È˔Āʄł„á„ó„ÈŁșLinux€Îmadvise()€ŹÊ耚€Ê€€€«Łż ? OS-Aware Design ? Swap„Ù©`„č€Ë€·€Æ€€€ë€ż€áContext Switch€Î„Ș©`„Đ©`„Ű„Ă„É€ŹńRÂč€Ë €Ê€é€Ê€€ĄŁ
- 26. È˔ĀÊÒÉ ? Remote-memory€òÊ耊€è€êĄąMemory Intensive€ÈCPU Intensive €Î„ą„Ś„ê€ò»ìÔÚ€”€»€ë„脱„ž„ć©`„é€òÊč€Ă€ż€Û€Š€ŹÈ«Ìć”Ā˿ÂÊ”Ä €Ç€ÏŁż ? 1GB Slab€Ë€ą€ë4KB Page€Ź„é„ó„À„à€ËSwap In€”€ì€ż€éżÂÊ”ÄŁż ? Ń}Êę„ą„Ś„ê€Î4KB Page€Ź1GB Slab€Ëžî€ê”±€Æ€é€ì€ë€Î€«Łż ? €ł€ÎöșÏĄąswap in€Ź„ą„Ś„ê°€Ëä€ï€ë€ŹżÂÊ”ÄŁż
- 27. Conclusion ? „œ©`„č„ł©`„ɀϰk±ír€Ë€ÏComing Soon €Ç€·€ż€ŹĄąč«é_€”€ì€Æ €€€Ț€čĄŁ ? https://github.com/Infiniswap/infiniswap ? Ù|ÒÉêŽđ ? Ù|ŁșInfiniswap €ÏLinux€ÎSWAP€òžÄÁŒ€·€Æ€€€ë€ŹĄąHuge Page€Ïê€Ç€€ë€Î€«ĄŁ€ż€·€«ĄąLinux€ÎSWAP€Ç€ÏQ€š€Ê€€ €Ï€ș€À€ŹĄŁ ? »ŰŽđŁșŹFÔÚ€ÎInfiniswap€Ç€âHuge Page€ÏQ€š€Ê€€ĄŁFuture work€ÀĄŁ
- 28. The Design, Implementation, and Deployment of a System to Transparently Compress Hundreds of Petabytes of Image Files for a File-Storage Service (Dropbox, Stanford University) ? Community Award PaperĄŁJPEG„Ő„Ą„€„ë€ò±ŁŽæ€č€ë€Î€ËHuffman Code€«€é parallelized arithmetic code€Ç„č„„ă„ó€·Ö±€·€Æ±ŁŽæ€č€ë„Ő„Ą„€„ë„·„č„Æ„à€Î Lepton€Î°k±íĄŁRżsÂÊ€âCPUĐÔÄÜ€â€è€€ĄŁLepton €Ï2017Äê2Ô€ËDropBox€Ç Êč€ï€ì€ë€è€Š€Ë€Ê€Ă€Æ€Ș€êĄą„œ©`„č„ł©`„É€âč«é_€”€ì€Æ€€€ëĄŁ ? PackJPG, MozJPG, JPEGreen€Ê€ÉîËÆ€ËŃĐŸż€Ï€ą€ë€ŹĄąJPEG€ÎÌŰŐ€òÈĄ€êÖ± €č€ż€á€ËHuffman Code€«€ée€ÎRżs·œ·š€Ç„Ő„Ą„€„ë„·„č„Æ„à€Źê€č€ë€Î€ÏĄą ŒÈŽæ€Î„Ő„©©`„Ț„Ă„È€òČĐ€·€Ä€Ä„·„č„Æ„àÈ€Çê€č€ëĐ€ż€ÊŃĐŸż·œÏò€ÈËŒ€ï€ì €ëĄŁ ? €Ț€żĄąLepton€ÎgŚ°€Ç€Ï„»„„ć„ê„Æ„Ł€òŽ_±Ł€č€ë€Î€ËLinux€ÎSECCOM€òÊč€Ă €Æ€€€ëĄŁ€Ț€żĄąC++€Îthread€Çű€«€ì€Æ€€€ë€ŹĄąDeterministic€òŽ_±Ł€·€Æ€€€ë €Ê€ÉĄą„»„„ć„ê„Á„Ł€äÔÙŹFĐԀˀȚ€ÇŃÔŒ°€·€Æ€Ș€êĄąŃĐŸż€ÎÙ|€Îžß€”€òÊŸ€·€Æ€€ €ëĄŁ
- 29. APUNet: Revitalizing GPU as Packet Processing Accelerator (KAIST) ? „Ń„±„Ă„ÈIÀí€ËGPU€òÊ耊ŃĐŸż(G-Opt[NSDI15])€Ç€Ï„á„â„ê„ł „Ô©`€ÎŰșÉ€Ź€ą€ëĄŁCPU€ÈÍŹ€ž„À„€€Ë€ą€ëIntegrated GPU(AMD Accelerated Processing Unit)€òÊ耊€ł€È€Ç„ą„É„ì „čżŐég€òčČÓĐ€·ĄążÂʔĀËIÀí€č€ëAPUNet€ÎÌá°ž€Ç€ą€ëĄŁ APUNet€ÏNetwork IDS€Ë€âAho-Corasick„Ń„ż©`„ó„Ț„Ă„Á€Îžß ËÙ»Ż€ËÊ耚€ë€È€Î€ł€È€Ç€ą€Ă€żĄŁ ? GPU€ÏÆŐŒ°€č€ë„Ï©`„É„Š„§„ą€Ç€ą€ë€ŹĄą„á„â„ê€Î„ł„Ô©`€ÎŐnî} €òAMD€ÎAPU€òÊč€Ă€Æ„Ń„±„Ă„ÈIÀí€ÈŃÔ€Š„ż©`„Č„Ă„È€òœg€Ă€Æ »îÓĂ€č€ë€Î€ÏÄż€Îž¶€±Ëù€Ź€è€€ĄŁ
- 30. One Key to Sign Them All Considered Vulnerable: Evaluation of DNSSEC in the Internet (Fraunhofer) ? ŹFÔÚÊč€ï€ì€Æ€€€ë210Íò€ÎDNSSEC€ÎæI€ÎŽàÈőĐÔŐ{ˀΰk±íĄŁ 190Íò€ŹRSA key€Ç€ą€êĄą€ł€Î€Š€Á66Ł„€Ź1024bitÒÔÏÂĄŁ€Ț€żĄą čČÍš€Î„â„ž„ć„é„č€äËŰÊę€âҀĀ«€Ă€Æ€€€ëĄŁ ? „â„ž„ć„é„耏čČÍš€À€ÈCommon Modulus Attack€ŹżÉÄÜ€È€Ê€ëĄŁ ? €ł€Î°k±í€Ź„€„ó„ż©`„Í„Ă„ÈÈ«Ìć€òŐ{Ë€·€żÎšÒ»€Î€â€Î€Ç€ą€Ă€żĄŁ Ëû€ÎÒ»Áś»áŚh€Ç€Ï2,3±Ÿ€ą€ë€Î€Ë€·€ÆĄą„Í„Ă„È„ï©`„Ż€ŹÖśŃÛ€Ê »áŚh€Ë€·€Æ€ÏÉـʀ€ĄŁ
- 31. Enhancing Security and Privacy of Tor's Ecosystem by Using Trusted Execution Environments (KAIST) ? Tor€Ç€Ï„ê„ì©`„Ω`„É€ŹžÄ€¶€ó€”€ì€Æ„Ś„é„€„Đ„·©`€ŹÊŰ€ì€Ê€Ż €Ê€ëŽàÈőĐÔ€Ź€ą€ëĄŁIntel SGX€òÊ耀ĄąTEE: Trusted Execution Environment€Ë€è€ë°ČÈ«€Ê„ê„ì©`„Ω`„ÉÊłö€·Ąą€œ€ì€é€Î€ß€ò Ê耊SGX-Tor€ÎÌá°žĄŁRemote Attestation€ÇÊÔ^€·ĄąłĐŐJ€”€ì €żRelay€Î€ß€òÊ耊ĄŁSGX-Tor €ÎgŚ°€Ç€ÏEnclaveÖĐ€ËSSL Library(OpenSSL), zlib, libevnet€ŹșŹ€Ț€ì€ëĄŁ ? ĐÔÄÜÁÓ»Ż€Ï11.9Ł„ĄŁ ? SGX-Tor€Î„œ©`„č„ł©`„É ? https://github.com/KAIST-INA/SGX-Tor
- 32. Opaque: An Oblivious and Encrypted Distributed Analytics Platform, (UCB) ? SQL€ÎIÀí€Ë Hardware enclave(Intel SGX, AMD memory encryption)€òÊč€Ă€Æ€âAccess pattern leakage€Ź€ą€ëĄŁ„ą„Ż„» „č„Ń„ż©`„ó€òëL€čoblivious relational operators€òŒÓ€š€żSpark SQL€ÎOpaque€ÎÌá°ž€Ç€ą€ëĄŁ ? Opaque€ÎHPĄŁ„œ©`„č„ł©`„É€ą€ê ? https://github.com/ucbrise/opaque
- 33. Bringing IoT to Sports Analytics, (University of Illinois at UrbanašCChampaign) ? ŹFÔڀ΄č„Ę©`„ÄœâŐh€Ï„Ï„€„č„Ô©`„É„«„á„é€òÊč€Ă€ÆÜÛE€òŚ·€Š €ł€È€Ź€Ç€€ë€ŹĄąCČÄ€Źžß€€ĄŁ€ł€Îî}€òœâQ€č€ë€ż€á€ËĄą„Ż „ꄱ„Ă„È€Î„Ü©`„ë€ÎÖĐ€ËŒÓËÙ¶ÈÓĄą„ž„ă„€„íĄąŽĆÁŠÓĄąWiFi€ò Èë€ì€ÆÜÛE€òŚ·€Šiball€Î°k±íĄŁÎ»ÖĂÊłö€ÏŃ}Êę€ÎWiFi„€„ó„Ő„é €òÊ耊ĄŁ ? λÖĂÊłö€ËGPS€Ç€Ï€Ê€ŻĄąWiFi€Ë€è€ë€â€Î€ŹĆdζÉĄŁ€Ț€żĄą „Ő„ê©`„Ő„©©`„ë€Ç€ÏŒÓËÙ¶ÈÓ€ÏŁ°€Ë€Ê€ë€Î€Ç»îÓÀǀ€Ê€Ż€Ê€ë î}€ą€êĄŁ
- 34. Clipper: A Low-Latency Online Prediction Serving System (USB) ? ŹFÔÚ€ÎMachine Learning€ÏGoogle TensorFlow€Î€è€Š€ËÓÀΠ„Ï©`„É„Š„§„ą€òÊč€Ă€ÆĐÔÄÜÏòÉÏ€òí€Ă€Æ€€€ë€ŹĄą€ł€Î€è€Š€Ê ÓĂ»Ż€Ïäžü€Źëy€·€€ĄŁűÓÀˀč€ëŒŒĐg€ż€á€ËLayered Architecture€òńÓĂ€·€żClipper€ÎÌá°žĄŁSpark, Tensor Flow, Caffe€Î„š„󄞄󀏳éÏ󻯀”€ì€ëModel Abstraction Layer €È€œ €ì€ò»îÓĂ€č€ë„ą„Ś„ê€òłéÏ󻯀·€żModel selection layer€ÇłÉ €”€ì€ëĄŁModel Abstraction Layer€ÏŃ}Êę€Î„š„ó„ž„ó€òĆäÏ€ËÖĂ €Ż€ł€È€Ź€Ç€€ëĄŁ ? Clipper€Î„œ©`„č€ÏÒ»€«ÔÂáá€Ëč«é_€”€ì€ë€œ€Š€ÀĄŁŹFÔÚč«é_g€ßĄŁ ? https://github.com/ucbrise/clipper
- 35. Gaia: Geo-Distributed Machine Learning Approaching LAN Speeds (CMU, ETH) ? ÊÀœçÖĐ€ËÉą€é€Đ€Ă€ż„Ç©`„ż„»„󄿀òMachine Learning€ÇÊ耚€ë €è€Š€Ë€č€ëGeo-distributed ML system€ÎGaia€ÎÌá°žĄŁ Parameter server€Çžś„Ç©`„ż„»„󄿀òŐ{Őû€č€ëĄŁ„ì„€„Æ„ó„·€ò ëL€č€ż€á€Ë„Ç©`„żÜËÍĄąÍŹÆڀʀɀÎ耷ò€·ĄąLAN€Ëœü€€ĐÔÄÜ€ò ß_łÉĄŁ












![APUNet: Revitalizing GPU as Packet
Processing Accelerator (KAIST)
? „Ń„±„Ă„ÈIÀí€ËGPU€òÊ耊ŃĐŸż(G-Opt[NSDI15])€Ç€Ï„á„â„ê„ł
„Ô©`€ÎŰșÉ€Ź€ą€ëĄŁCPU€ÈÍŹ€ž„À„€€Ë€ą€ëIntegrated
GPU(AMD Accelerated Processing Unit)€òÊ耊€ł€È€Ç„ą„É„ì
„čżŐég€òčČÓĐ€·ĄążÂʔĀËIÀí€č€ëAPUNet€ÎÌá°ž€Ç€ą€ëĄŁ
APUNet€ÏNetwork IDS€Ë€âAho-Corasick„Ń„ż©`„ó„Ț„Ă„Á€Îžß
ËÙ»Ż€ËÊ耚€ë€È€Î€ł€È€Ç€ą€Ă€żĄŁ
? GPU€ÏÆŐŒ°€č€ë„Ï©`„É„Š„§„ą€Ç€ą€ë€ŹĄą„á„â„ê€Î„ł„Ô©`€ÎŐnî}
€òAMD€ÎAPU€òÊč€Ă€Æ„Ń„±„Ă„ÈIÀí€ÈŃÔ€Š„ż©`„Č„Ă„È€òœg€Ă€Æ
»îÓĂ€č€ë€Î€ÏÄż€Îž¶€±Ëù€Ź€è€€ĄŁ](https://image.slidesharecdn.com/usenix-nsdi17-memorydisaggregation-170606224304/85/USENIX-NSDI17-Memory-Disaggregation-29-320.jpg)





