Vmug birmingham mar2013 trendmicro
- 1. Giovanni Alberici ŌĆó EMEA Product Marketing Addressing the new security challenges posed by virtualisation & cloud computing
- 2. Stage 1 Consolidation Stage 2 Expansion & Desktop Stage 3 Private > Public Cloud 15% 30% 70% 85% Servers Desktops Cost-efficiency ’ā╝ + Quality of Service ’ā╝ + Business Agility ’ā╝ Data centres are evolving to drive down costs and increase business flexibility The evolving data centre
- 3. Security challenges in the cloud Inter-VM attacks Instant-ON gaps Stage 1 Consolidation Stage 2 Expansion & Desktop Stage 3 Private > Public Cloud Servers Desktops Cost-efficiency ’ā╝ + Quality of Service ’ā╝ + Business Agility ’ā╝ 15% 30% 70% 85% Inter-VM attacks Instant-ON gaps Mixed Trust Level VMs Resource Contention Maintaining Compliance
- 4. Cloned ’ā╗ Challenge: Instant-on Gaps ’ā╝ ’ā╝ ’ā╝ ’ā╝ Dormant Active Reactivated with out dated security ’ā╗ ’ā╗ New, reactivated and cloned VMs can have out-of-date security
- 5. Attacks can spread across VMs Challenge: Inter-VM Attacks / Blind Spots
- 6. Not Patched ’ā╝ ’ā╝ Patched ’ā╝ ’ā╝ ’ā╗ ’ā╗ ’ā╗ Virtualization - patching doesnŌĆÖt go away 8/12/2022 6 Copyright 2012 Trend Micro Inc. ŌĆ£ŌĆ”virtual machine proliferation could soon make it very difficult to maintain compliant environments.ŌĆØ VMware on Patch Management
- 7. Security challenges in the cloud Inter-VM attacks Instant-ON gaps Stage 1 Consolidation Stage 2 Expansion & Desktop Stage 3 Private > Public Cloud Servers Desktops Cost-efficiency ’ā╝ + Quality of Service ’ā╝ + Business Agility ’ā╝ 15% 30% 70% 85% Inter-VM attacks Instant-ON gaps Mixed Trust Level VMs Resource Contention Maintaining Compliance Service Provider (in)Security Multi-tenancy Inter-VM attacks Instant-ON gaps Mixed Trust Level VMs Resource Contention Maintaining Compliance
- 8. Data security challenges in the cloud Encryption rarely used: - Who can see your information? Storage volumes and servers are mobile: - Where is your data? Has it moved? Rogue servers might access data: - Who is attaching to your storage? Audit and alerting modules lacking: - What happened when you werenŌĆÖt looking? Encryption keys tied to vendor: - Are you locked into a single security solution? Who has access to your keys? Storage volumes contain residual data: - Are your storage devices recycled securely? Classification 8/12/2022 9 Name: John Doe SSN: 425-79-0053 Visa #: 4456-8732ŌĆ” Name: John Doe SSN: 425-79-0053 Visa #: 4456-8732ŌĆ”
- 9. Challenges for public cloud Shared Storage Shared Firewall Virtual Servers Shared network inside the firewall Shared firewall ŌĆō Lowest common denominator ŌĆō less fine grained control Multiple customers on one physical server ŌĆō potential for attacks via the hypervisor Shared storage ŌĆō is customer segmentation secure against attack? Easily copied machine images ŌĆō who else has your server? Internet
- 10. Public Cloud: Private Security Shared Storage Shared Firewall Virtual Servers Shared network inside the firewall Shared firewall ŌĆō Lowest common denominator ŌĆō less fine grained control Multiple customers on one physical server ŌĆō potential for attacks via the hypervisor Shared storage ŌĆō is customer segmentation secure against attack? Easily copied machine images ŌĆō who else has your server? DoesnŌĆÖt matter ŌĆō the edge of my virtual machine is protected DoesnŌĆÖt matter ŌĆō treat the LAN as public DoesnŌĆÖt matter ŌĆō treat the LAN as public DoesnŌĆÖt matter ŌĆō They can start my server but only I can unlock my data DoesnŌĆÖt matter ŌĆō My data is encrypted Internet
- 11. Copyright 2013 Trend Micro Inc. Data Center Physical Enabling the Data Center (R)evolution Virtual Private Cloud Public Cloud Deep Security Agent/Agentless Anti-Malware Integrity Monitoring Application Control Log Inspection Firewall Virtual Patching Data Center Ops Security By 2016, 71% of server workloads will be virtualized
- 12. Any Hypervisor Virtualization Security - Agent Based VMware Hypervisor Virtualization Security - Agentless
- 13. Improves system performance 1 Eases security administration 2 Improves security & compliance 3 Advantages of Deep Security for Virtualization Enables workload flexibility 4
- 14. 15 Deep Security Virtual Appliance Improves system performance 1 50% more VDIs 20 ŌĆō 30% more virtual servers
- 15. Deep Security 9 Scan Cache ŌĆó Separate cache for Anti-malware scheduled/on-demand and Integrity Monitoring ŌĆó Up to 20x improvement for Anti-malware scans between VMs ŌĆó Reduce resources and overall on-demand scan time for Anti-malware ŌĆó Reduce overall baseline time for Integrity Monitoring ŌĆó Great benefits for VDI (VMs are linked clones) 8/12/2022 16 Confidential | Copyright 2012 Trend Micro Inc.
- 16. Anti-malware Scan Performance 8/12/2022 17 Confidential | Copyright 2012 Trend Micro Inc. 1st AM scan 2nd AM scan (cached) Scan time ~ 20x faster Significant DSVA CPU Reduction Huge IO Volume Reduction
- 17. 18 ŌĆó Visibility into virtual and cloud environments ŌĆō vCenter, Active Directory, vCloud, Amazon (AWS) ŌĆó Automation & Recommendation ŌĆō Identify unique security controls required ŌĆō OS, applications, patch-levels, vulnerabilities ŌĆō Automatically deploy and activate security policies ŌĆō Example: SAP server requires 28 controls Provisioning Infrastructure vCenter, AD, vCloud and AWS Virtual Appliance Public Cloud Deep Security ŌĆó Scalable ŌĆó Redundant SAP Exchange Servers Oracle Web Server Web Server 73 controls 8 controls 28 controls 19 controls 15 controls Linux Server Eases security administration 2
- 18. 8/12/2022 19 Confidential | Copyright 2012 Trend Micro Inc.
- 19. Global threat intelligence from the cloud ŌĆ” collects 6TB worth of data for analysis ŌĆ” analyses 1.15B new threat samples ŌĆ” identifies 90,000 new threats ŌĆ” blocks 200M threats EVERY 24 HOURS 20 Improves security & compliance 3
- 20. Patch Management is a Growing Challenge Critical ŌĆ£Software FlawŌĆØ Vulnerabilities in 2012 Common Vulnerabilities & Exposures (ŌĆ£CVEŌĆØ): Score 7-10 1,764 Almost 7 critical vulnerabilities everyday! 8/12/2022 21 Confidential | Copyright 2013 Trend Micro Inc. ŌĆ£Due to the increasing volume of public vulnerability reports, the Common Vulnerabilities and Exposures (CVE) project will change the syntax of its standard vulnerability identifiers so that CVE can track more than 10,000 vulnerabilities in a single year.ŌĆØ http://cve.mitre.org/news/index.html 2012 saw 26% increase in # of vulnerabilities disclosed NSS Labs
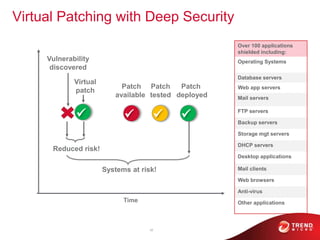
- 21. 22 Virtual Patching with Deep Security Time Vulnerability discovered Over 100 applications shielded including: Operating Systems Database servers Web app servers Mail servers FTP servers Backup servers Storage mgt servers DHCP servers Desktop applications Mail clients Web browsers Anti-virus Other applications ’ā╝ Patch available ’ā╝ Patch tested ’ā╝ Patch deployed Systems at risk! Reduced risk! Virtual patch ’ā╝
- 22. Compliance with Deep Security 23 IDS / IPS Web Application Protection Application Control Firewall Deep Packet Inspection Integrity Monitoring Log Inspection Anti-Malware 5 Protection Modules Defence In Depth Addressing 7 PCI requirements and 20+ sub-controls including: ’āŠ (1.) Network Segmentation ’āŠ (1.x) Firewall ’āŠ (5.x) Anti-Malware ’āŠ (6.1) Virtual Patching ’āŠ (6.6) Web App. Protection ’āŠ (10.6) Daily Log Review ’āŠ (11.4) IDS / IPS ’āŠ (11.5) Integrity Monitoring PCI-DSS Compliance
- 23. Physical Database Storage Virtual Web Server Mail Server Web Server Enterprise Providers Deep Security Web Access Enables workload flexibility 4
- 24. Physical Virtual Cloud Manageability Glut of security products Less security Higher TCO Reduce Complexity One Security Model is Possible across Physical, Virtual, and Cloud Environments Integrated Security: Single Management Console Performance & Threats Traditional security degrades performance New VM-based threats Increase Efficiency Visibility & Threats Less visibility More external risks Deliver Agility
- 25. Thank You! 8/12/2022 26 Confidential | Copyright 2012 Trend Micro Inc.
Editor's Notes
- The data centre is evolving. This is a depiction of a customerŌĆÖs typical virtualization journey from physical to cloud via virtualization.In stage 1, orgs have begun virtualization all of their low hanging fruit ŌĆō web servers, file and print servers, some app servers, and begun to realize the hardware consolidation and operational management benefits that result in lower CAPX and OPEX costs.In stage 2, they have begun virtualizing more of their tier 1 apps and mission critical servers now. They are also leveraging some of the more advanced capabilities of virtualization such as automatic live migration, disaster recovery and software fault tolerance. Many stage 2 orgs have also started deploying virtual desktops as well.Benefits in stage 2 are even more cost efficiencies plus also higher QoS from the higher level virtualization capabilities.
- Next weŌĆÖll cover instant-on gaps. [click]Unlike a physical machine, when a virtual machine is offline, it is still available to any application that can access the virtual machine storage over the network, and is therefore susceptible to malware infection. However, dormant or offline VMs do not have the ability to run an antimalware scan agent. [click]Also when dormant VMs are reactivated, they may have out-of-date security. [click]One of the benefits of virtualization is the ease at which VMs can be cloned. However, if a VM with out-of-date security is cloned the new VM will have out-of-date security as well. New VMs must have a configured security agent and updated pattern files to be effectively protected. [click]Again the solution is a dedicated security virtual appliance that can ensure that guest VMs on the same host have up-to-date security if accessed or reactivated, and can make sure that newly provisioned VMs also have current security. This security virtual appliance should include layered protection that integrates multiple technologies such as antivirus, integrity monitoring, intrusion detection and prevention, virtual patching, and more. .
- IŌĆÖd now like to highlight a couple of additional virtualization challenges. The next one weŌĆÖll discuss today is inter-VM attacks and blind spots. [click]When a threat penetrates a virtual machine, the threat can then spread to other virtual machines on the same host. Traditional security such as hardware-based firewalls might protect the host, but not the guest virtual machines. And cross-VM communication might not leave the host to be routed through other forms of security, creating a blind spot. [click]For the solution, protection must be applied on an individual virtual machine level, not host level, to ensure security. And integration with the virtualization platform, such as VMware, provide the ability to communicate with the guest virtual machines. Also, virtual patching ensures that VMs stay secure until patches can be deployed.
- Patching is one of the most significant pain points for every IT department, and it also needs to be addressed in virtual datacenters. Patch cycles, virtual machine proliferation could soon make it very difficult to maintain compliant environments. http://www.vmware.com/virtualization/advantages/virtualization-management/patching.html VMware vCenter Update Manager lets you:Reduce the risks associated with patching hosts by allowing fast rollbacks to a pre-patch stage Eliminate application downtime related to VMware ESX host patching Increase IT administrator productivity with unique automation capabilities Increase flexibility by allowing delayed reboot of virtual machines VMware vCenter Update Manager is a fully integrated module of VMware vCenter Server. It does not require a complex installation or additional infrastructure.
- In stage 3, organizations have started leveraging private and public clouds. The IT dept has transformed itself into acting as a service provider with charge-back type processes where consumers of IT are in effect renting computing space and time from IT. Benefits are further cost efficiencies, QoS and faster business agility.As orgs considered their move to stage 3, security was top of mind ŌĆō IDC survey data shows that it is the #1 issue why orgs will not move to the cloud.
- To address the risks of evolving your data center, we have a single platform and administration that secures your physical, virtual and cloud environments.Our solution is open, automated and highly scalable, fitting your existing infrastructure, seamlessly integrating with key applications like VMWare or cloud environments like Amazon Web Services.Like our end user protection solution, this solution is plug-and-play in nature ŌĆō allowing you to extend and grow your solution as your business needs change.Block and remove malicious software with Anti-Malware.Protect against known and zero-day vulnerabilities with Intrusion Prevention. This provides you with ŌĆ£virtual patchingŌĆØ -- protecting you before you patch.Achieve segmentation of systems and reduce the attack surface with a host-based Firewall.Identify expected and unexpected (malicious) system changes with Integrity Monitoring.Gain additional visibility and correlation of system and application events with Log Inspection. This can be integrated with your existing SIEM for further insight.Protect sensitive data, particularly when using cloud service providers with Encryption.<click>And just like our other solutions, it is powered by our Smart Protection Network, protecting against real-world threats faster.Our Cloud and Data Center Solution protects you on your journey to the cloud ŌĆō now and in the future.
- LetŌĆÖs look at the example here:LetŌĆÖs imagine a VMware ESX host with 15 virtual servers running on it, each of which has a locally installed security agent providing e.g. AM, Web Threat Protection, FW, DPI, IM. So whatŌĆÖs the problem with this approach? Simultaneous scanning, updates, network traffic analysis and so on lead to increased resource usage on each VM, and a cumulative resource impact on the ESX host which can be disastrous and lead to outages of the host and ŌĆō therefore ŌĆō all of the VMs running on that host. This is turn can result in a combination of the following:Less VMs per ESX hostReduced security on each VMNo security on each VMSo how does Deep Security solve this problem? Deep SecurityŌĆÖs agentless protection abilities mean you can drastically increase the amount of VMs per ESX host ŌĆō all without reducing the security posture of the VM. Which means one thing for VMware customers ŌĆō increased ROI (and security!) in their virtual infrastructure.Savings on improved VM density:VDI: 50% more VDIsVirtual servers: 20 ŌĆō 30% more virtual serversSavings during initial deployment:Where Deep Security saves significant setup time is when customers need to install multiple separate point security solutions ŌĆō for example, for separate solutions such as anti-virus, host firewall, host IPS, and integrity monitoring. By providing these technologies in a single integrated virtual appliance, Deep Security reduces overall setup time relative to other market alternatives that deploy multiple agent-based solutions.Savings in on going management:Faster deployment on new VMsVirtual patching
- Datacenter extension into the cloud ŌĆō Workloads like Web or mail. Challenges with visibility and policy with the workloads and extension of networkDS ŌĆō Allowing visibility into physical, virtual, cloud assetsBeing able to assign and enforce security policies across these workloads.
- Each of these platforms has unique security concerns. With physical machines, the manageability of various security solutions can be an issue.There can be a glut of security productsŌĆöeither through excessive layering or overly specialized products. This increases hardware and software costs. Also, management across the different products can be difficult ŌĆō causing security gaps. And collectively these issues create a higher Total Cost of Ownership.The solution is to reduce complexity by consolidating security vendors and correlating protection.[click]With virtualization, the risks pertain to both performance and threats specific to virtual environments. There is a concern that security will reduce performance, which reduces the ROI of a virtual infrastructure. Also there are unique virtual machine attacks, such as inter-VM threats. Here the solution is increased efficiencyŌĆösecurity that optimizes performance while also defending against traditional as well as virtualization-specific threats. [click]With cloud services, the risks pertain to less visibility and cloud-specific threats. Companies are concerned about having less visibility into their applications and data. And they are concerned about increased external threats, especially in multi-tenant environments.For the cloud, businesses need security that allows them to use the cloud to deliver IT agility. Data must be able to safely migrate from on-premise data centers to private clouds to public clouds so organizations can make the best use of resources. [click]As weŌĆÖll see later, all of these concerns can be addressed. And through protection that is provided in an integrated security solution all managed through one console. With cross-platform security, youŌĆÖll stay protected as your data center and virtual or cloud deployments evolve, allowing you to leverage the benefits of each platform while defending against the threats unique to each environment.