VPN_basics_and_necssitated_Technologies.ppt
Download as PPT, PDF0 likes13 views
To Create VPN
1 of 26
Download to read offline

![Traditional Connectivity
[From Gartner Consulting]](https://image.slidesharecdn.com/vpnbasics-240505152446-b2e7c457/85/VPN_basics_and_necssitated_Technologies-ppt-2-320.jpg)






![Tunneling
A virtual point-to-point connection
made through a public network. It
transports
encapsulated datagrams.
Encrypted Inner Datagram
Datagram Header Outer Datagram Data Area
Original Datagram
Data Encapsulation [From Comer]
Two types of end points:
’āś Remote Access
’āś Site-to-Site](https://image.slidesharecdn.com/vpnbasics-240505152446-b2e7c457/85/VPN_basics_and_necssitated_Technologies-ppt-9-320.jpg)

















Recommended
Virtual private network



Virtual private networkSowmia Sathyan
╠²
VPN allows remote access to private networks over public networks like the Internet. It uses encryption and tunneling protocols to securely transmit data. There are three main types of VPN implementations: intranet within an organization, extranet for external access, and remote access for mobile employees. VPN provides benefits like reduced costs, scalability, and flexibility compared to traditional private networks.VPN_ppt.ppt



VPN_ppt.pptKarthikeyan303142
╠²
Virtual private networks (VPNs) allow employees to securely access a company's intranet from remote locations over the public Internet. VPNs use encryption and authentication to ensure privacy and prevent unauthorized access. They provide cost savings over traditional private networks by reducing equipment and maintenance costs while improving scalability. Common VPN types include remote access VPNs for employees and site-to-site VPNs for connecting multiple office locations. Key VPN protocols are PPTP, L2TP, and IPSec. VPNs benefit industries requiring remote access or private network connections and their use is growing as more employees work remotely.Vp npresentation 2



Vp npresentation 2Swarup Kumar Mall
╠²
Virtual private networks (VPNs) use public telecommunication networks like the Internet to provide secure connections between remote locations. VPNs encrypt data packets and transmit them through tunnels, encapsulating one protocol within another, to maintain private networks virtually. This allows remote access and site-to-site connectivity while reducing costs compared to traditional private networks using leased lines.VPN (virtual Private Network)



VPN (virtual Private Network)Chandan Jha
╠²
This document discusses virtual private networks (VPNs). It defines VPNs as private networks that use public telecommunications like the internet instead of leased lines. VPNs allow remote access to company networks and save costs by reducing equipment and maintenance expenses. The document outlines common VPN protocols like PPTP, L2TP, and IPsec. It also discusses VPN implementations, device types, advantages, applications, industries that use VPNs, and the future of VPN technology.Vp npresentation



Vp npresentationRajesh Thakur
╠²
In VPNs, "tunneling" refers to the process of encapsulating VPN packets within regular IP packets in order to transmit them securely over the public Internet or other untrusted networks. This creates a "tunnel" through which the VPN traffic can travel.VPN 



VPN Bhairave Maulekhi
╠²
In VPNs, "tunneling" refers to the process of encapsulating packets from one protocol inside the packets of another protocol. This allows VPNs to work by creating a virtual circuit across the public network to mimic the behavior of a point-to-point private connection.Vp npresentation (1)



Vp npresentation (1)Shreyank Gupta
╠²
In VPNs, "tunneling" refers to the process of encapsulating packets from one protocol inside the packets of another protocol. This allows VPNs to work by creating a "tunnel" between two endpoints and encapsulating all traffic inside that tunnel to maintain privacy and security as it travels over an otherwise public network.Virtual Private Network(VPN)



Virtual Private Network(VPN)Abrish06
╠²
A virtual private network (VPN) allows users to securely send and receive data across shared or public networks as if they are directly connected to a private network. VPNs use authentication and encryption to allow employees to access a company's private network remotely. There are three main types of VPNs: remote access VPNs for employees to connect from various locations, intranet VPNs to connect locations within an organization, and extranet VPNs to securely connect organizations. Common VPN protocols include PPTP, L2TP/IPSec, and OpenVPN. VPNs provide security benefits like authentication, access control, confidentiality and data integrity while allowing remote access and mobility.Virtual private networks (vpn)



Virtual private networks (vpn)Avinash Nath
╠²
1. Virtual Private Networks (VPNs) allow employees to securely access a company's private network from remote locations over the public Internet rather than using a private leased line.
2. VPNs use encryption, authentication, and tunneling protocols to create a secure connection between a user's device and the private network. This allows employees to work remotely while maintaining the security of the private network.
3. There are different types of VPN implementations including intranet VPNs within an organization, extranet VPNs for connections outside an organization, and remote access VPNs for individual employees to connect to the business network remotely. Common protocols used include PPTP, L2TP, and IPsec.Presentation vpn



Presentation vpnAreeba Gill
╠²
Virtual private networks (VPNs) allow users to securely access an organization's network from remote locations over the public internet. VPNs use encryption and authentication to create a private communications channel between users and the organization's network. There are four main protocols used in VPNs - PPTP, L2TP, IPSec, and SOCKS - with PPTP and L2TP being the most common. VPNs provide benefits like reduced costs, scalability, and flexibility for remote access compared to traditional private networks.Vpn



Vpnsurendrabane
╠²
This document provides an overview of virtual private networks (VPNs). It discusses how VPNs use public networks like the Internet to securely connect remote locations privately. VPNs allow authorized users to access a private network from anywhere for applications like remote access and site-to-site connectivity. The document outlines key VPN concepts, technologies, protocols, functions, examples, advantages in reducing costs, and some challenges in deployment.vpn



vpnvimal0123
╠²
This document discusses virtual private networks (VPNs). It defines a VPN as a private network that uses a public network like the Internet instead of leased lines. VPNs provide secure remote access to corporate resources over the Internet and connect branch office networks to head office networks securely. The document outlines common VPN protocols like PPTP, L2TP, and IPsec. It discusses VPN components such as user authentication, address management, data encryption, and key management. Finally, it highlights benefits of VPNs such as reduced costs and increased flexibility compared to leased lines.Virtual Private Network main



Virtual Private Network mainKanika Gupta
╠²
This document provides an overview of virtual private networks (VPNs). It defines a VPN as using public networks like the Internet to connect private networks securely through authentication and encryption. The document discusses the need for VPNs to reduce costs, improve communication, and ensure security. It covers VPN types, components, protocols, and security measures like firewalls and encryption. Advantages include cost savings and mobility, while disadvantages include security understanding and performance issues outside an organization's control. The future of VPNs is described as widespread use through standardization.csevpnppt-170905123948 (1).pdf



csevpnppt-170905123948 (1).pdfHirazNor
╠²
This document provides an overview of virtual private networks (VPNs). It defines a VPN as a private network that uses public telecommunication networks like the Internet instead of leased lines. It discusses the main types of VPNs including remote access, site-to-site intranet, and site-to-site extranet. The document also covers VPN protocols, security features, devices, advantages like reduced costs, and disadvantages like reliance on internet connectivity. It concludes that VPNs provide a secure and cost-effective private networking solution for many companies.Virtual Private Networks (VPN) ppt



Virtual Private Networks (VPN) pptOECLIB Odisha Electronics Control Library
╠²
Virtual Private Network is a type of private network that uses public telecommunicaton, such as the Internet, instead of leased lines to communicateVpn presentation



Vpn presentationRam Bharosh Raut
╠²
Virtual private networks (VPNs) allow users to securely access an organization's intranet from remote locations using public networks like the internet. VPNs use encryption and tunneling protocols to securely transmit data and authenticate users, providing privacy and access similar to a private network. The main benefits of VPNs are reduced costs compared to dedicated private networks, as VPNs can leverage existing broadband internet connections instead of expensive leased lines. Common VPN protocols include PPTP, L2TP, and IPsec, with "tunneling" referring to the encapsulation of packets within other protocol packets to create and maintain virtual connections.Vpn networks kami



Vpn networks kamikamran_share
╠²
Tunneling in VPNs refers to the process of encapsulating VPN data packets within regular IP packets for transmission through a public network like the Internet. This encapsulation creates a "tunnel" between the VPN endpoints that provides security and allows private network traffic to be carried across a shared infrastructure.Vp npresentation



Vp npresentationPradeep wolf king
╠²
Tunneling in VPNs refers to the process of encapsulating packets from one protocol inside the packets of another protocol. This creates a tunnel between two endpoints that can pass securely over an otherwise untrusted network.Ism



IsmRavi Foods Pvt. Ltd. (DUKES)
╠²
Virtual private networks (VPNs) allow employees to securely access a company's intranet from remote locations over the public Internet. VPNs use encryption and authentication to ensure private and secure connections. There are two main types of VPNs - site-to-site VPNs which connect multiple fixed locations like offices, and remote access VPNs which allow mobile users to connect from outside the network. VPNs provide advantages like reduced costs compared to private lines and increased flexibility and scalability. However, they also present disadvantages like added security risks and performance that depends on public networks outside the company's control. VPNs are commonly used across industries to allow secure data transfer and remote access for employees, customers, and partners.Vp npresentation



Vp npresentationAyano Midakso
╠²
Tunneling in VPNs refers to the process of encapsulating packets inside packets of a different protocol to create and maintain the virtual circuit between the VPN endpoints. This allows data to be securely transmitted across an untrusted network like the public internet.VIRTUAL PRIVATE NETWORKS BY SAIKIRAN PANJALA



VIRTUAL PRIVATE NETWORKS BY SAIKIRAN PANJALASaikiran Panjala
╠²
Virtual private networks (VPNs) allow for secure data transmission over public networks like the Internet. VPNs create virtual tunnels between devices to securely transmit encrypted data. There are three main types of VPNs: remote-access VPNs for remote users, intranet-based site-to-site VPNs to connect locations within a company, and extranet-based site-to-site VPNs to connect companies. VPNs use protocols like IPsec and SSL to encrypt data and tunneling protocols to transmit data securely between devices.Insights of vpn



Insights of vpnHarshika Rana
╠²
This content has been created mainly for the students who would like to understand the basics of the VPN and its 5W1HShradhamaheshwari vpn



Shradhamaheshwari vpnShradha Maheshwari
╠²
Virtual private networks (VPNs) allow secure connections over public networks like the Internet instead of expensive leased lines. There are three main types of VPNs: trusted VPNs rely on a single provider's network for security; secure VPNs encrypt and authenticate all traffic between agreed parties; and hybrid VPNs combine secure VPN technologies running over trusted VPN technologies. VPNs use technologies like IPSec, SSL/TLS, and PPTP to provide critical functions of authentication, access control, confidentiality, and data integrity. They are commonly used by industries for remote access, site-to-site connectivity between offices, and access to networks for business partners and customers.Virtual Private Network



Virtual Private NetworkRajan Kumar
╠²
A dynamic virtual private network (DVPN) allows secure connections between remote users and private networks through virtual connections over public networks like the internet. It provides enhanced security, can accommodate changing user communities dynamically, and maintains integrity over user access rights and data security over time regardless of technological changes. Key features include distributed access control, application independence, access control based on authenticated user identities, and support for user groups. DVPNs establish trust in open network environments through flexible yet finely-controlled security.Virtual Private Network



Virtual Private NetworkRicha Singh
╠²
A virtual private network gives secure access to LAN resources over a shared network infrastructure such as the internet. It can be conceptualized as creating a tunnel from one location to another, with Encrypted data traveling through the tunnel before being decrypted at its destination.
More Related Content
Similar to VPN_basics_and_necssitated_Technologies.ppt (20)
Virtual private networks (vpn)



Virtual private networks (vpn)Avinash Nath
╠²
1. Virtual Private Networks (VPNs) allow employees to securely access a company's private network from remote locations over the public Internet rather than using a private leased line.
2. VPNs use encryption, authentication, and tunneling protocols to create a secure connection between a user's device and the private network. This allows employees to work remotely while maintaining the security of the private network.
3. There are different types of VPN implementations including intranet VPNs within an organization, extranet VPNs for connections outside an organization, and remote access VPNs for individual employees to connect to the business network remotely. Common protocols used include PPTP, L2TP, and IPsec.Presentation vpn



Presentation vpnAreeba Gill
╠²
Virtual private networks (VPNs) allow users to securely access an organization's network from remote locations over the public internet. VPNs use encryption and authentication to create a private communications channel between users and the organization's network. There are four main protocols used in VPNs - PPTP, L2TP, IPSec, and SOCKS - with PPTP and L2TP being the most common. VPNs provide benefits like reduced costs, scalability, and flexibility for remote access compared to traditional private networks.Vpn



Vpnsurendrabane
╠²
This document provides an overview of virtual private networks (VPNs). It discusses how VPNs use public networks like the Internet to securely connect remote locations privately. VPNs allow authorized users to access a private network from anywhere for applications like remote access and site-to-site connectivity. The document outlines key VPN concepts, technologies, protocols, functions, examples, advantages in reducing costs, and some challenges in deployment.vpn



vpnvimal0123
╠²
This document discusses virtual private networks (VPNs). It defines a VPN as a private network that uses a public network like the Internet instead of leased lines. VPNs provide secure remote access to corporate resources over the Internet and connect branch office networks to head office networks securely. The document outlines common VPN protocols like PPTP, L2TP, and IPsec. It discusses VPN components such as user authentication, address management, data encryption, and key management. Finally, it highlights benefits of VPNs such as reduced costs and increased flexibility compared to leased lines.Virtual Private Network main



Virtual Private Network mainKanika Gupta
╠²
This document provides an overview of virtual private networks (VPNs). It defines a VPN as using public networks like the Internet to connect private networks securely through authentication and encryption. The document discusses the need for VPNs to reduce costs, improve communication, and ensure security. It covers VPN types, components, protocols, and security measures like firewalls and encryption. Advantages include cost savings and mobility, while disadvantages include security understanding and performance issues outside an organization's control. The future of VPNs is described as widespread use through standardization.csevpnppt-170905123948 (1).pdf



csevpnppt-170905123948 (1).pdfHirazNor
╠²
This document provides an overview of virtual private networks (VPNs). It defines a VPN as a private network that uses public telecommunication networks like the Internet instead of leased lines. It discusses the main types of VPNs including remote access, site-to-site intranet, and site-to-site extranet. The document also covers VPN protocols, security features, devices, advantages like reduced costs, and disadvantages like reliance on internet connectivity. It concludes that VPNs provide a secure and cost-effective private networking solution for many companies.Virtual Private Networks (VPN) ppt



Virtual Private Networks (VPN) pptOECLIB Odisha Electronics Control Library
╠²
Virtual Private Network is a type of private network that uses public telecommunicaton, such as the Internet, instead of leased lines to communicateVpn presentation



Vpn presentationRam Bharosh Raut
╠²
Virtual private networks (VPNs) allow users to securely access an organization's intranet from remote locations using public networks like the internet. VPNs use encryption and tunneling protocols to securely transmit data and authenticate users, providing privacy and access similar to a private network. The main benefits of VPNs are reduced costs compared to dedicated private networks, as VPNs can leverage existing broadband internet connections instead of expensive leased lines. Common VPN protocols include PPTP, L2TP, and IPsec, with "tunneling" referring to the encapsulation of packets within other protocol packets to create and maintain virtual connections.Vpn networks kami



Vpn networks kamikamran_share
╠²
Tunneling in VPNs refers to the process of encapsulating VPN data packets within regular IP packets for transmission through a public network like the Internet. This encapsulation creates a "tunnel" between the VPN endpoints that provides security and allows private network traffic to be carried across a shared infrastructure.Vp npresentation



Vp npresentationPradeep wolf king
╠²
Tunneling in VPNs refers to the process of encapsulating packets from one protocol inside the packets of another protocol. This creates a tunnel between two endpoints that can pass securely over an otherwise untrusted network.Ism



IsmRavi Foods Pvt. Ltd. (DUKES)
╠²
Virtual private networks (VPNs) allow employees to securely access a company's intranet from remote locations over the public Internet. VPNs use encryption and authentication to ensure private and secure connections. There are two main types of VPNs - site-to-site VPNs which connect multiple fixed locations like offices, and remote access VPNs which allow mobile users to connect from outside the network. VPNs provide advantages like reduced costs compared to private lines and increased flexibility and scalability. However, they also present disadvantages like added security risks and performance that depends on public networks outside the company's control. VPNs are commonly used across industries to allow secure data transfer and remote access for employees, customers, and partners.Vp npresentation



Vp npresentationAyano Midakso
╠²
Tunneling in VPNs refers to the process of encapsulating packets inside packets of a different protocol to create and maintain the virtual circuit between the VPN endpoints. This allows data to be securely transmitted across an untrusted network like the public internet.VIRTUAL PRIVATE NETWORKS BY SAIKIRAN PANJALA



VIRTUAL PRIVATE NETWORKS BY SAIKIRAN PANJALASaikiran Panjala
╠²
Virtual private networks (VPNs) allow for secure data transmission over public networks like the Internet. VPNs create virtual tunnels between devices to securely transmit encrypted data. There are three main types of VPNs: remote-access VPNs for remote users, intranet-based site-to-site VPNs to connect locations within a company, and extranet-based site-to-site VPNs to connect companies. VPNs use protocols like IPsec and SSL to encrypt data and tunneling protocols to transmit data securely between devices.Insights of vpn



Insights of vpnHarshika Rana
╠²
This content has been created mainly for the students who would like to understand the basics of the VPN and its 5W1HShradhamaheshwari vpn



Shradhamaheshwari vpnShradha Maheshwari
╠²
Virtual private networks (VPNs) allow secure connections over public networks like the Internet instead of expensive leased lines. There are three main types of VPNs: trusted VPNs rely on a single provider's network for security; secure VPNs encrypt and authenticate all traffic between agreed parties; and hybrid VPNs combine secure VPN technologies running over trusted VPN technologies. VPNs use technologies like IPSec, SSL/TLS, and PPTP to provide critical functions of authentication, access control, confidentiality, and data integrity. They are commonly used by industries for remote access, site-to-site connectivity between offices, and access to networks for business partners and customers.Virtual Private Network



Virtual Private NetworkRajan Kumar
╠²
A dynamic virtual private network (DVPN) allows secure connections between remote users and private networks through virtual connections over public networks like the internet. It provides enhanced security, can accommodate changing user communities dynamically, and maintains integrity over user access rights and data security over time regardless of technological changes. Key features include distributed access control, application independence, access control based on authenticated user identities, and support for user groups. DVPNs establish trust in open network environments through flexible yet finely-controlled security.Virtual Private Network



Virtual Private NetworkRicha Singh
╠²
A virtual private network gives secure access to LAN resources over a shared network infrastructure such as the internet. It can be conceptualized as creating a tunnel from one location to another, with Encrypted data traveling through the tunnel before being decrypted at its destination.
More from shabdrang (9)
1. VoIP.ppt



1. VoIP.pptshabdrang
╠²
This document discusses the requirements and considerations for implementing voice over IP (VoIP) networks. It covers topics like the impact of packet loss, delay and jitter on voice quality in an IP network. It also addresses the need for consistent throughput, reliability, and different types of gateways. Additional sections provide details on encapsulating voice in IP packets, major VoIP protocols like RTP and RTCP, and calculating bandwidth requirements.1. IP Internetwork.pptx



1. IP Internetwork.pptxshabdrang
╠²
This document discusses how VoIP systems work, including:
1) Soft switches translate phone numbers to IP addresses and know the current location and IP address of endpoints on the network.
2) Common VoIP protocols like H.323 and SIP are used to connect hardware and support real-time video, audio, and data applications. However, a lack of standardization can cause compatibility issues.
3) VoIP offers advantages over traditional phone systems like lower costs, mobility via internet connections, and reduced bandwidth requirements.Maths wise teaching guide 6



Maths wise teaching guide 6shabdrang
╠²
This teaching guide provides lesson plans for teaching mathematics from sets to information handling. Each lesson includes starter activities, the main lesson content from the textbook, practice activities, individual work, homework, and recapitulation. The lessons progress from introductory to more advanced topics and include examples, exercises from the textbook, and assessment worksheets. The guide is meant to help teachers systematically divide the course content over the entire year and ensure all topics are well taught.Ch21



Ch21shabdrang
╠²
This document discusses key concepts about electric charge including:
- Charges of the same sign repel and opposite charges attract based on Coulomb's law.
- Conductors allow free movement of charge carriers like electrons, while insulators do not.
- Charge is quantized and can only exist in integer multiples of the elementary charge carried by protons and electrons.
- Charge is conserved in interactions and transformations at both the macro and microscopic level.Obe sheet



Obe sheetshabdrang
╠²
This document contains:
1. Student performance data from the course EEE351 Principles of Communication Systems, including student registration numbers, names, marks obtained on assignments, sessions exams, terminal exam and overall total marks.
2. The maximum marks for different assessment categories and their weightage towards the final grade.
3. A table with 28 student records listing their details and marks.
4. The class average and passing percentage for different course learning outcomes.5. lec5 curl of a vector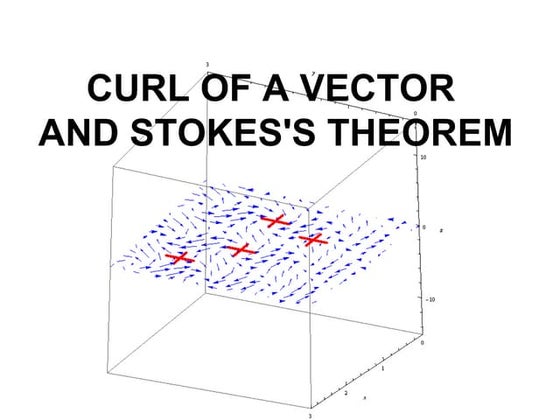



5. lec5 curl of a vectorshabdrang
╠²
1. The document discusses vector calculus concepts including the gradient, divergence, curl, and theorems relating integrals.
2. It defines the curl of a vector field A as the maximum circulation of A per unit area and provides expressions for curl in Cartesian, cylindrical and spherical coordinates.
3. Stokes's theorem is described as relating a line integral around a closed path to a surface integral of the curl over the enclosed surface, allowing transformation between different integral types.Basics of solar



Basics of solarshabdrang
╠²
Solar energy can be harnessed through both solar thermal and solar photovoltaic (PV) systems. Solar thermal systems use sunlight to heat water or spaces for uses like cooking and water heating. PV systems convert sunlight directly into electricity using solar panels made of silicon cells. Both types of systems provide environmental benefits over fossil fuels and can offset utility costs. Students can experiment with designing solar collectors and exploring factors that affect their efficiency.Recently uploaded (20)
PresentWEFWEFWERWERWERWERREWREWation.pptx



PresentWEFWEFWERWERWERWERREWREWation.pptxtoxicsuprit
╠²
ewfweqrwqerwrwqrwqr qwr qw r qwrqwrqwrqw rqwrqwr qwrq wr wqr qwrfdwqf qw f qwf qw r qw f qw f qwf qw fqw r q2wr q3 32 r qwf qw f as f werweqt we fr ewf we fw qe fw egew g we g ewg ew ewg weg w eg we g ewg we g ewewOdoo Project Management .pdf



Odoo Project Management .pdfdela33martin33
╠²
SDLC Corp delivers a powerful Odoo Project Management solution, offering seamless Odoo project module implementation, automation, and customization. Our Odoo project management software optimizes workflows, enhances collaboration, and ensures efficient project execution for business growth and scalability.Amazon Sidewalk: A Global Wake-Up Call for the Telecom Industry



Amazon Sidewalk: A Global Wake-Up Call for the Telecom IndustryDavid Swift
╠²
ØŚöØŚ║ØŚ«ØśćØŚ╝ØŚ╗ ØŚ»ØśéØŚČØŚ╣Øśü ØŚöØŚ║ØŚ▓ØŚ┐ØŚČØŚ░ØŚ«ŌĆÖØśĆ ØŚ╣ØŚ«ØŚ┐ØŚ┤ØŚ▓ØśĆØśü ØŚ£ØŚ╝ØŚ¦ ØŚ╗ØŚ▓ØśüØśäØŚ╝ØŚ┐ØŚĖŌĆöand nobody noticed. ØŚĪØŚ╝Øśü ØŚ▓ØśāØŚ▓ØŚ╗ ØśüØŚĄØŚ▓ ØśüØŚ▓ØŚ╣ØŚ░ØŚ╝ØśĆ.
No spectrum auctions.
No cell towers.
No billion-dollar rollouts.
Here's the story... Amazon has quietly launched the largest IoT network in the United States, covering over 90% of the population. This network, known as Amazon Sidewalk, bypasses traditional telecom infrastructure, leverages consumer devices, and utilizes unlicensed spectrum to deliver pervasive, low-bandwidth connectivity. This white paper explores the global implications of Amazon's approach, outlines strategic risks and opportunities for telecom operators, and provides actionable insights for future-proofing telco business models in the face of tech-driven disruption.Complete Nmap Scanning Commands CheatSheet by Hackopedia Utkarsh Thakur



Complete Nmap Scanning Commands CheatSheet by Hackopedia Utkarsh ThakurHackopedia Utkarsh Thakur
╠²
Complete Nmap Scanning Commands CheatSheet by Hackopedia Utkarsh Thakur, ETHICAL HACKING , HACKOPEDIA Generative artificial intelligence in EU Grant Writing



Generative artificial intelligence in EU Grant WritingPeter Trkman
╠²
The presentation "AI in EU Grant Writing" by Dr. Peter Trkman and Dr. Luka Tomat focuses on the integration of generative artificial intelligence (GenAI) tools into the process of writing grant applications, particularly in the context of EU-funded projects. It was delivered as part of a workshop held at the University of Ljubljana and is based on the authorsŌĆÖ extensive experienceŌĆöover 80 workshops since late 2023.
The presentation begins by clarifying what GenAI is and what it is not. It explains how large language models (LLMs) work, including tokenization, vector embedding, and self-attention mechanisms. It introduces major LLMs such as GPT-4, Claude, Grok, Gemini, and others, along with an extensive list of tools built on top of these models.
The core of the presentation is practical. It explores how GenAI can assist in the preparation of grant applications, from generating project summaries and activity plans to producing ethics statements and evaluation responses. Concrete examples are given from Erasmus+ mobility forms, national project applications, and fictional debates using actual EU evaluation criteria.
The authors explain that GenAI is most useful for tasks requiring large volumes of content, knowledge synthesis, translation to various audiences, second opinions, and early drafting. However, they emphasize that it should not be used when accuracy is paramount or when ethical implications are significant. Instead, it is best seen as a complementary tool that boosts productivity, especially for those less experienced in writing.
The presentation includes broader reflections on how GenAI is reshaping research practices and the labor market, with references to studies showing that GenAI often outperforms human analysts in certain tasks and that its emotional support capabilities rival those of trained therapists.
Specific tools for grant writing are introduced, such as DeepRFP, Grantable, and GrantedAI, along with general tools like ChatGPT, Copilot, and Perplexity. The presenters also advocate for long-term structural change in the grant systemŌĆöstreamlining processes to eliminate the need for GenAI use altogether. Until then, they argue, one must ŌĆ£play the gameŌĆØ and use these tools effectively while maintaining academic integrity.
The closing message is clear: while GenAI tools offer powerful support, responsible use and a focus on substance over form remain essential. Peter and Luka invite further contact for tailored workshops and note that all content is based on their personal experience and research, not confidential material.Mdf Board manufacturer in india.........



Mdf Board manufacturer in india.........veerseo13
╠²
E3 MDF Manufacturing Facility in Kashipur, Uttarakhand, sets new industry standards with state-of-the-art European machinery for wood chipping, fiber refinement, and continuous pressing. Our advanced system produces 300 cubic meters daily, supplemented by multi-daylight presses generating 250 cubic meters. This allows us to achieve an impressive total of 550 cubic meters of high-quality MDF boards daily. We are committed to delivering excellence, ensuring that every board meets with the highest quality standards of strength, durability and finish. Choose E3 MDF boards for your projects, and experience the perfect blend of innovation, quality, and reliability. Trust us as your MDF board manufacturer to elevate your projects to new heights.BGP Best Practices, presented by Imtiaz Sajid



BGP Best Practices, presented by Imtiaz SajidAPNIC
╠²
Imtiaz Sajid, Network Analyst / Technical Trainer at APNIC, delivered a remote presentation on 'BGP Best Practices' for MMNOG 7 held Yangon, Myanmar from 19 to 22 March 2025. The Evolution of Home Security from Cameras to Smart Systems.pdf



The Evolution of Home Security from Cameras to Smart Systems.pdfInternet Bundle Now
╠²
Explore how Home Security Cameras evolved into intelligent, connected systems. Internet Bundle Now breaks down the rise of Home Security Services.
Epochalypse 2038 - Remediating the 32-bit Timestamp Risk at Global Scale (Pub...



Epochalypse 2038 - Remediating the 32-bit Timestamp Risk at Global Scale (Pub...treyka
╠²
Epochalypse 2038 - Remediating the 32-bit Timestamp Risk at Global Scale (Public Briefing v1.0 2025-03-31).pdfIETF 122: draft-ietf-regext-rdap-rir-search-16



IETF 122: draft-ietf-regext-rdap-rir-search-16APNIC
╠²
Tom Harrison, Registry Product and Delivery Manager at APNIC, presented updates on the draft regext-rdap-rir-search functionality at IETF 122 held in Bangkok Thailand from 15 to 21 March 2025.║▌║▌▀Żs: Eco Economic Epochs World Game's Great Redesign .pdf



║▌║▌▀Żs: Eco Economic Epochs World Game's Great Redesign .pdfSteven McGee
╠²
SLIDES: The Great Redesign of The World Game (s) Eco Economic Epochs pdf
intellectual property DeFi foundation technology via an adaptive procedural template tech frameworkMeasuring ECN, presented by Geoff Huston at IETF 122



Measuring ECN, presented by Geoff Huston at IETF 122APNIC
╠²
APNIC Chief Scientist, Geoff Huston, presented on 'Measuring ECN' at IETF 122 held in Bangkok, Thailand from 15 to 21 March 2025.The-Power-of-Digital-Marketing-Fueling-Business-Growth.pdf



The-Power-of-Digital-Marketing-Fueling-Business-Growth.pdfmakelinkak002
╠²
Transform your business by merging software development with digital marketing services, utilising cloud solutions for scalability, efficiency, and innovation with Makelink Innovation.
Expert Odoo support services (1).pdf



Expert Odoo support services (1).pdfdela33martin33
╠²
SDLC Corp offers Odoo Support Service, ensuring seamless business operations with expert assistance. Our Odoo ERP Support Services ance performance, while Odoo Technical Support resolves issues enhance efficiently, optimizing workflows, improving system reliability, and boosting productivity for long-term success.VPN_basics_and_necssitated_Technologies.ppt
- 2. Traditional Connectivity [From Gartner Consulting]
- 3. What is VPN? ’āś Virtual Private Network is a type of private network that uses public telecommunication, such as the Internet, instead of leased lines to communicate. ’āś Became popular as more employees worked in remote locations. ’āś Terminologies to understand how VPNs work.
- 4. Private Networks vs. Virtual Private Networks ’āś Employees can access the network (Intranet) from remote locations. ’āś Secured networks. ’āś The Internet is used as the backbone for VPNs ’āś Saves cost tremendously from reduction of equipment and maintenance costs. ’āś Scalability
- 5. Remote Access Virtual Private Network (From Gartner Consulting)
- 6. Brief Overview of How it Works ’āś Two connections ŌĆō one is made to the Internet and the second is made to the VPN. ’āś Datagrams ŌĆō contains data, destination and source information. ’āś Firewalls ŌĆō VPNs allow authorized users to pass through the firewalls. ’āś Protocols ŌĆō protocols create the VPN tunnels.
- 7. Four Critical Functions ’āśAuthentication ŌĆō validates that the data was sent from the sender. ’āśAccess control ŌĆō limiting unauthorized users from accessing the network. ’āśConfidentiality ŌĆō preventing the data to be read or copied as the data is being transported. ’āśData Integrity ŌĆō ensuring that the data has not been altered
- 8. Encryption ’āśEncryption -- is a method of ŌĆ£scramblingŌĆØ data before transmitting it onto the Internet. ’āśPublic Key Encryption Technique ’āśDigital signature ŌĆō for authentication
- 9. Tunneling A virtual point-to-point connection made through a public network. It transports encapsulated datagrams. Encrypted Inner Datagram Datagram Header Outer Datagram Data Area Original Datagram Data Encapsulation [From Comer] Two types of end points: ’āś Remote Access ’āś Site-to-Site
- 10. Four Protocols used in VPN ’āśPPTP -- Point-to-Point Tunneling Protocol ’āśL2TP -- Layer 2 Tunneling Protocol ’āśIPsec -- Internet Protocol Security ’āśSOCKS ŌĆō is not used as much as the ones above
- 11. VPN Encapsulation of Packets
- 12. Types of Implementations ’āśWhat does ŌĆ£implementationŌĆØ mean in VPNs? ’āś3 types ’āś Intranet ŌĆō Within an organization ’āś Extranet ŌĆō Outside an organization ’āś Remote Access ŌĆō Employee to Business
- 13. Virtual Private Networks (VPN) Basic Architecture
- 14. Device Types What it means 3 types ’ü« Hardware ’ü« Firewall ’ü« Software
- 15. Device Types: Hardware Usually a VPN type of router Pros ŌĆó Highest network throughput ŌĆó Plug and Play ŌĆó Dual-purpose Cons ŌĆó Cost ŌĆó Lack of flexibility
- 16. Device Types: Firewall More security? Pros ŌĆó ŌĆ£HardenŌĆØ Operating System ŌĆó Tri-purpose ŌĆó Cost-effective Cons ŌĆó Still relatively costly
- 17. Device Types: Software Ideal for 2 end points not in same org. Great when different firewalls implemented Pros ŌĆó Flexible ŌĆó Low relative cost Cons ŌĆó Lack of efficiency ŌĆó More labor training required ŌĆó Lower productivity; higher labor costs
- 19. Advantages: Cost Savings ’āśEliminating the need for expensive long- distance leased lines ’āśReducing the long-distance telephone charges for remote access. ’āśTransferring the support burden to the service providers ’āśOperational costs
- 20. Advantages: Scalability ’āśFlexibility of growth ’āśEfficiency with broadband technology
- 21. Disadvantages ’āś VPNs require an in-depth understanding of public network security issues and proper deployment of precautions ’āś Availability and performance depends on factors largely outside of their control ’āś Immature standards ’āś VPNs need to accommodate protocols other than IP and existing internal network technology
- 22. Applications: Site-to-Site VPNs Large-scale encryption between multiple fixed sites such as remote offices and central offices Network traffic is sent over the branch office Internet connection This saves the company hardware and management expenses
- 24. Applications: Remote Access ’āś Encrypted connections between mobile or remote users and their corporate networks ’āś Remote user can make a local call to an ISP, as opposed to a long distance call to the corporate remote access server. ’āś Ideal for a telecommuter or mobile sales people. ’āś VPN allows mobile workers & telecommuters to take advantage of broadband connectivity. i.e. DSL, Cable
- 25. Industries That May Use a VPN ’āś Healthcare: enables the transferring of confidential patient information within the medical facilities & health care provider ’āś Manufacturing: allow suppliers to view inventory & allow clients to purchase online safely ’āś Retail: able to securely transfer sales data or customer info between stores & the headquarters ’āś Banking/Financial: enables account information to be transferred safely within departments & branches ’āś General Business: communication between remote employees can be securely exchanged
- 26. Where Do We See VPNs Going in the Future? ’āś VPNs are continually being enhanced. Example: Equant NV ’āś As the VPN market becomes larger, more applications will be created along with more VPN providers and new VPN types. ’āś Networks are expected to converge to create an integrated VPN ’āś Improved protocols are expected, which will also improve VPNs. ’āś Managed Security Service providers










