VSLive Las Vegas - The Shift to Rugged DevOps
- 1. 2/13/2020 1 THE SHIFT TO RUGGED DEVOPS SECURITY IN YOUR PIPELINES REN├ēVAN OSNABRUGGE @RENEVO Ren├® van Osnabrugge Xpirit Netherlands @renevo rvanosnabrugge@xpirit.com https://roadtoalm.com 3 4
- 3. 2/13/2020 3 IMPOSSIBLE TO UNDERSTAND IMPOSSIBLE TO IMPLEMENT IMPOSSIBLE TO VALIDATE IMPOSSIBLE TO MAINTAIN THE BATTLE WITH CISO 7 8
- 4. 2/13/2020 4 0 10 20 30 40 50 60 70 80 90 100 Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec SECURITY LEVEL - CURRENT Security Level - Current Audit coming up ! Audit coming up ! THE CLASSIC ŌĆ£SECURITYŌĆØ MODEL 0 10 20 30 40 50 60 70 80 90 100 Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec SECURITY LEVEL - CURRENT Security Level - Current Audit coming up ! Audit coming up ! THE CLASSIC ŌĆ£SECURITYŌĆØ MODEL 9 10
- 6. 2/13/2020 6 CONFIDENTIALITY INTEGRITY AVAILABILITY ŌĆ£COMPLIANCE CHECKING IS THE OPPOSITE OF SECURITY ENGINEERINGŌĆØ James Wicket ŌĆō ŌĆ£The DevOps HandbookŌĆØ 13 15
- 7. 2/13/2020 7 ŌĆ£Health is a state of complete physical, mental and social well-being, and not merely the absence of disease or infirmity.ŌĆØ World Health Organization, 1948 16 17
- 8. 2/13/2020 8 THIS WAS ALL VERY SECURE! Unbreachable walls Indestructible Machines Watchful security guards UNTIL IT WAS NOT! 18 19
- 9. 2/13/2020 9 COMPLIANT SECURE RUGGED ŌĆØFUNDAMENTALLY, IF SOMEBODY WANTS TO GET IN, THEY'RE GETTING INŌĆ”ACCEPT THAT. NUMBER ONE, YOU'RE IN THE FIGHT, WHETHER YOU THOUGHT YOU WERE OR NOT. NUMBER TWO, YOU ALMOST CERTAINLY ARE PENETRATED. WE NEED TO SHIFT FROM PREVENT TO ASSUME BREACH! ŌĆØ Michael Hayden Former Director of NSA & CIA 20 21
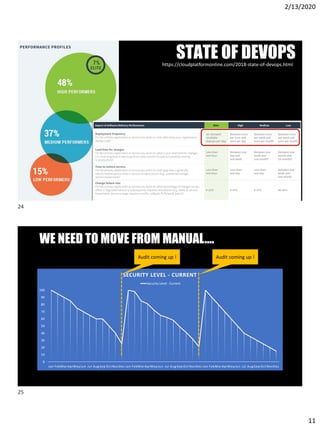
- 11. 2/13/2020 11 STATE OF DEVOPShttps://cloudplatformonline.com/2018-state-of-devops.html 0 10 20 30 40 50 60 70 80 90 100 Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec SECURITY LEVEL - CURRENT Security Level - Current Audit coming up ! Audit coming up ! WE NEED TO MOVE FROM MANUALŌĆ”. 24 25
- 12. 2/13/2020 12 0 10 20 30 40 50 60 70 80 90 100 Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec Jan FebMarAprMayJun Jul AugSep OctNovDec Security Level - Current Desired Audit coming up ! Audit coming up ! ŌĆ”.TO AUTOMATED SECURITY IS THE NEXT SILO TO TEAR DOWN 26 27
- 14. 2/13/2020 14 Make them part of your team! SHIFT LEFT SECURITYYOU BUILD IT YOU RUN IT Make them part of your team! SHIFT LEFT SECURITY 30 31
- 15. 2/13/2020 15 CREATIVE THINKING HACKERS DOŌĆ” NOT PLAY BY THE RULES ALREADY USE CONTINUOUS DELIVERY ARE ALWAYS AHEAD OF YOU USE ALL MEANS POSSIBLE THINK OUT OF THE BOX 32 33
- 16. 2/13/2020 16 HOW DO WE DO THAT? IDENTIFY PREVENT REACT BUILD RUN NOT ORŌĆ”BUT AND! IDENTIFY PREVENT REACT PREVENT BREACH ASSUME BREACH 34 35
- 17. 2/13/2020 17 PREVENT BREACH CODE STORE BUILD DEPLOY RELEASE SECURE PIPELINES SECURE AND COMPLIANT ALL THE WAY 36 37
- 18. 2/13/2020 18 Identity & Access Servers & Containers Firewalls & Network Passwords & Secrets Libraries & Licenses Application Code Build & Delivery Pipelines WHAT NEEDS TO BE SECURE? CODING PHASE ŌĆ£In the coding phase, an idea transforms into codeŌĆØ 38 39
- 19. 2/13/2020 19 CODING PHASE - IDENTIFY ŌĆó Bad coding practicesresulting in Technical Debt ŌĆó Non Deployable code ŌĆó Untested code and therefore unintended consequences ŌĆó Passwords/Secretsetc. exposed in code WE ALL NEED SOME PROTECTION ŌĆ” FROM OURSELVES 40 41
- 21. 2/13/2020 21 CODING PHASE - PREVENT ŌĆó Secure Development Lifecycle (SDL) ŌĆó Compiling / Syntax Checking ŌĆó First stage - Static Code Analysis ŌĆó Ruleset selection is key ! ŌĆó Unit Tests ŌĆó Secure Assets ŌĆó Approvedtemplates ŌĆó Secure shared Packages ŌĆó Credential and Secret Scanning ŌĆó Do we really need secrets? ŌĆó Use of keyvaults 44 45
- 22. 2/13/2020 22 CREDENTIAL SCANNING DEMO STORING PHASE ŌĆ£In the storing phase you make ŌĆ£yourŌĆØ code ŌĆ£ourŌĆØ code and ensure it is safeŌĆØ 46 47
- 23. 2/13/2020 23 STORING PHASE - IDENTIFY ŌĆó Everything from Coding phase ! ŌĆó Unknown committers to Git Repository ŌĆó Suspicious code is committed to the code repository ŌĆó Code is deployed without 4-eyes principle ŌĆó Code contains secrets/passwordsetc. STORING PHASE - PREVENT ŌĆó Protect Git Repo to ensure ŌĆ£pusherŌĆØ is known ŌĆó Use Pull Requests and protect the master branch ŌĆó Run Continuous IntegrationBuilds ŌĆó Enforce 4-eyes on every code change ŌĆó Enforce CI checks on every code change ŌĆó Static Code Analysis ŌĆó CredScans ŌĆó Compiling Syntax Checking ŌĆó Unit Tests 48 49
- 24. 2/13/2020 24 BUILD PHASE ŌĆ£In the build phase we transform the product from code and script into an immutable and versioned packageŌĆØ BUILD PHASE - IDENTIFY ŌĆó Package can be unintentionallymodified ŌĆó Code can contain vulnerabilities/ Technical Debt ŌĆó Code can contain secrets ŌĆó Code is untested/unstable ŌĆó Unauthorized modification of build process ŌĆó Code can use unsecure libraries ŌĆó Code can use unlicensed / wrongly licensed libraries 50 51
- 26. 2/13/2020 26 Components 80 ŌĆō 90 % Original Code 10-20% (max) YOUR CODE VS. THEIR CODE COPYLEFT GPL LGPL AGPL Permissive Restrictive ANDTHENTHEREISLICENSING 54 55
- 27. 2/13/2020 27 BUILD PHASE - PREVENT ŌĆó Build activities from Storing Phase ŌĆó Second stage - Static Code Analysis ŌĆó Vulnerabilityand dependency scanning ŌĆó License Scanning ŌĆó Securely storing the Build Artifact ŌĆó Protectingthe Build History DEPENDENCY MANAGEMENT DEMO 56 57
- 28. 2/13/2020 28 DEPLOY / RELEASE PHASE ŌĆ£THIS IS THE PHASE WHERE THE ARTIFACTS MOVE FROM YOUR ŌĆ£PROTECTEDŌĆØ ENVIRONMENT INTO THE OPENŌĆØ DEPLOY / RELEASE PHASE - IDENTIFY ŌĆó Unauthorized change in the release steps ŌĆó Target environment accessible by multiple process ŌĆó Deployed application has obvious vulnerabilities ŌĆó Deployed application has unexpected consequences on availability etc. ŌĆó Secrets are exposed during deployment process 58 59
- 29. 2/13/2020 29 DEPLOY / RELEASE PHASE - PREVENT ŌĆó Run Dynamic Security Tests on Infrastructure ŌĆó Run Tests that require a deployed application ŌĆó Monitor key metrics after deployment ŌĆó Set up secure Endpointsto target environment ŌĆó Secret Management in the pipeline ŌĆó Build in a mechanism to separate functional from technical release ŌĆó Enforce 4 eyes-principle on the release pipeline RELEASE GATES DEMO 60 61
- 30. 2/13/2020 30 ASSUME BREACH / RUN IDENTIFY PREVENT REACT PREVENT BREACH ASSUME BREACH Monitor REACT MTTR Baselines Pipelines Alerts Continuous Delivery You build it / You run it Post Mortem Share Experience Rebuilt Everything as Code DETECT RESPOND RECOVER 62 63
- 31. 2/13/2020 31 Monitor Detect Fix Bleeding Scan & Fix Locally Embed in Pipeline Set new Baseline Continuous Assurance DEMO DETECT , RESPOND, RECOVER 64 65
- 33. 2/13/2020 33 RED TEAM vs. BLUE TEAM Red Team Model real-world attacks Identify gaps in security story Demonstrable impact Blue Team Exercises ability to detect & respond Enhances situational awareness Measures readiness & impact AND COMPLIANCY? 69 70
- 34. 2/13/2020 34 COMPLIANT BY DEFAULT 1 2 3 AVAILABILITY INTEGRITY CONFIDENTIALITY 71 72
- 35. 2/13/2020 35 Ren├® van Osnabrugge Xpirit Netherlands @renevo rvanosnabrugge@xpirit.com https://roadtoalm.com Ren├® van Osnabrugge Xpirit Netherlands @renevo rvanosnabrugge@xpirit.com https://roadtoalm.com Attributions Pictures: https://unsplash.com / https://www.flickr.com/photos/wocintechchat Gifs: https://giphy.com Music: https://open.spotify.com/user/rvanosnabrugge/playlist/ 0BWgsNPM5iwgk8ZGlMHeoY?si=l9-tV8FTR8S1J7AbKBz-KA Video: https://www.youtube.com/watch?v=47u3n1kX0wE Thanks: Geert, Marcel, Alex, Jasper, Xpirit 73 74