We Really Don\'t Know Clouds at All: Challenges to Privacy Compliance
- 1. We Really Don’t Know Clouds at All: Challenges to Privacy Compliance David Elder Stikeman Elliott 2nd Cloud Computing Law Federated Press Ottawa 21 June 2011 STIKEMAN ELLIOTT LLP www.stikeman.com
- 2. Outline  On clouds  Legal framework for privacy in canada  Key privacy obligations  Cloud challenges  The sky is not falling SLIDE 1 STIKEMAN ELLIOTT LLP
- 3. What is Cloud Computing?  “Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.” National Institute of Standards and Technology SLIDE 2 STIKEMAN ELLIOTT LLP
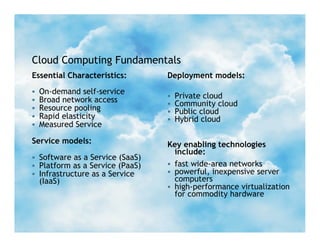
- 4. Cloud Computing Fundamentals Essential Characteristics: Deployment models:  On-demand self-service  Broad network access  Private cloud  Community cloud  Resource pooling  Public cloud  Rapid elasticity  Hybrid cloud  Measured Service Service models: Key enabling technologies include:  Software as a Service (SaaS)  Platform as a Service (PaaS)  fast wide-area networks  Infrastructure as a Service  powerful, inexpensive server (IaaS) computers  high-performance virtualization for commodity hardware SLIDE 3 STIKEMAN ELLIOTT LLP
- 5. Legislative Framework  Patchwork?  Mix of Federal and Provincial Regimes Private Sector Health Sector Public Sector Employees © TinyApartmentCrafts SLIDE 4 STIKEMAN ELLIOTT LLP
- 6. Private Sector Privacy  Provincial: B.C.: Personal Information Protection Act Alberta: Personal Information Protection Act Québec: An Act Respecting the Protection of Personal Information in the Private Sector  Federal: Personal Information Protection and Electronic Documents Act SLIDE 5 STIKEMAN ELLIOTT LLP
- 7. Private Sector Privacy Federal Personal Information Protection and Electronic Documents Act  Applies to collection, use and disclosure of personal information by: – Private sector federal works & undertakings, including their employees – Private sector organizations, in course of commercial activities, when:  Transferred across provincial borders  Collected, used or disclosed in province without “substantially similar” legislation SLIDE 6 STIKEMAN ELLIOTT LLP
- 8. Private Sector Privacy Provincial B.C.: Personal Information Protection Act Alberta: Personal Information Protection Act Québec: An Act Respecting the Protection of Personal Information in the Private Sector  Apply to collection, use and disclosure of personal information by all private sector organizations in the Province – Not just in course of commercial activities – Including employee personal information – N/A to interprovincial transfers and federal undertakings SLIDE 7 STIKEMAN ELLIOTT LLP
- 9. Health Sector Privacy  Provincial: British Columbia: Personal Information Protection Act Alberta: Health Information Act Saskatchewan: Health Information Protection Act Manitoba: Personal Health Information Act Ontario: Personal Health Information Protection Act New Brunswick: Personal Health Information Privacy and Access Act Nova Scotia: Personal Health Information Act* Newfoundland & Labrador: Personal Health Information Act  Federal: Personal Information Protection and Electronic Documents Act SLIDE 8 STIKEMAN ELLIOTT LLP
- 10. Health Sector Privacy Provincial health sector privacy laws generally apply to:  Personal health information, held by  Health Information Custodians: persons or organizations with custody or control of PHI in performing duties, including: – Health care practitioners – Hospitals and long-term care facilities – Community health centres – Pharmacies – Laboratories, etc. SLIDE 9 STIKEMAN ELLIOTT LLP
- 11. Key Privacy Obligations Security  Personal info must be protected by security safeguards appropriate to the sensitivity of the information  Nature of safeguards will vary according to sensitivity, quantity, distribution, format, method of storage  Should include physical, organizational, technological measures  See PIPA Advisory #8: Implementing Reasonable Safeguards http://www.oipc.ab.ca/ims/client/upload/PIPA_Advisory_8_Reasonable_Safeguards20 07.pdf  See Securing Personal Information: A Self-Assessment Tool for Organizations: http://priv.gc.ca/resource/tool-outil/security- securite/english/AssessRisks.asp?formAction=ShowPrintedAssess&methods=full SLIDE 10 STIKEMAN ELLIOTT LLP
- 12. Key Privacy Obligations Limiting Use, Disclosure and Retention  Personal info to be used solely for purposes for which collected  Personal info to be retained only as long as necessary to fulfil purposes for which collected, then returned, deleted or destroyed Access & Accuracy  Upon request, individual has right of access to their personal information, including how used and disclosed  Inaccurate or incomplete info must be corrected SLIDE 11 STIKEMAN ELLIOTT LLP
- 13. Key Privacy Obligations Accountability  Organization responsible for personal info it collects  Still responsible for personal info transferred to third parties for processing Breach Notification  Requirement or expectation to notify Privacy Commissioner, affected individual Consent  Knowledge and consent required for the collection, use and disclosure of personal information SLIDE 12 STIKEMAN ELLIOTT LLP
- 14. The Dark Side of the Cloud  Out of your control, vision obscured  Multiple and unknown locations, jurisdictions  Focus on low cost, efficiency may mean – One-size fits all service, reluctance to customize – Security as a secondary focus?  Co-mingling in community, public, hybrid cloud may mean potential – Cross-info, segregation problems – auditability? – Exposure to other’s vulnerabilities – Delays where breaches SLIDE 13 STIKEMAN ELLIOTT LLP
- 15. Key Privacy Obligations & Challenges Obligations Cloud Challenges Security  Tendency to one-size-fits all  Security safeguards appropriate  Cloud makes security decisions - to sensitivity of personal info not you  Cloud unaware of sensitivity of info Breach Notification  Need to be advised of cloud  Advise Privacy Commissioner(s), breach individuals/customers  How to define what notifiable  Need cooperation, up-to-minute details  Could be many cloud users affected SLIDE 14 STIKEMAN ELLIOTT LLP
- 16. Key Privacy Obligations & Challenges Obligations Cloud Challenges: Limiting Use, Disclosure,  Uncertainty won’t be Retention mined/used for other purposes  To be used solely for identified  Uncertainty of retention purpose periods, foreign requirements?  To be retained only as long as  Right to destroy, delete, have necessary to fulfil purposes, returned then returned or destroyed Access & Accuracy  Ensure individual will have  Right of access access  Right to correct  Ensure can quickly correct incomplete or inaccurate data SLIDE 15 STIKEMAN ELLIOTT LLP
- 17. Key Privacy Obligations & Challenges Obligations Cloud Challenges: Accountability  How to maintain control, visibility?  Organization responsible for personal info it collects, even  Difficult to audit if widely when transferred to 3rd parties dispersed, co-mingled Consent  Can be need for explicit consent to storage/processing  Knowledge and consent outside Canada, due to foreign required for the collection, use legal jurisdictions and disclosure of personal information  Consent to cloud itself? SLIDE 16 STIKEMAN ELLIOTT LLP
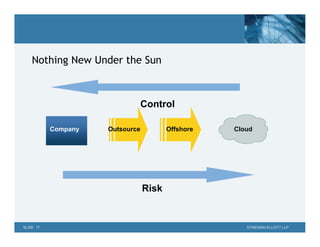
- 18. Nothing New Under the Sun Control Company Outsource Offshore Cloud Risk SLIDE 17 STIKEMAN ELLIOTT LLP
- 19. I Can See Clearly Now  Not for everyone  Choose your provider very carefully  Where located?  Pick your cloud  Bake key terms, levels, guarantees into contract: – Security practices and requirements – Breach/investigation response/CIRT – Audit – Liability, indemnity – Subcontracting control SLIDE 18 STIKEMAN ELLIOTT LLP
- 20. Questions & Answers David Elder delder@stikeman.com STIKEMAN ELLIOTT LLP www.stikeman.com