Web«∞∂À–‘ƒÐ”≈ªØ 2014
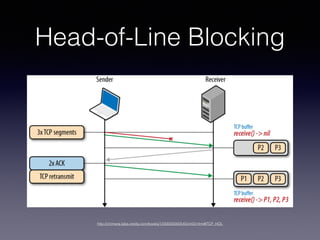
- 3. What happened? ? ¥” ‰?»Î URL µΩ‰Ø¿¿∆˜Ω” ’µƒπ˝≥Ã÷–∑¢?…˙¡À ≤√¥£ø ? ‰Ø¿¿∆˜»Á∫ŒœÚ??Õ¯ø®∑¢ÀÕ ˝æð£ø ? ˝æð»Á∫Œ¥”±æª˙??Õ¯ø®∑¢ÀÕµΩ∑˛ŒÒ∆˜£ø ? ∑˛ŒÒ∆˜Ω” ’µΩ ˝æð∫Ûª·Ω¯?––ƒƒ–©¥¶¿Ì£ø ? ∑˛ŒÒ∆˜∑µªÿ ˝æð∫ۉؿ¿∆˜»Á∫Œ¥¶¿Ì£ø ? ‰Ø¿¿∆˜»Á∫ŒΩ´?“≥?√Ê’πœ÷≥ˆ¿¥£ø
- 4. What happened? ? ¥” ‰?»Î URL µΩ‰Ø¿¿∆˜Ω” ’µƒπ˝≥Ã÷–∑¢?…˙¡À ≤√¥£ø ? ‰Ø¿¿∆˜»Á∫ŒœÚ??Õ¯ø®∑¢ÀÕ ˝æð£ø ? ˝æð»Á∫Œ¥”±æª˙??Õ¯ø®∑¢ÀÕµΩ∑˛ŒÒ∆˜£ø ? ∑˛ŒÒ∆˜Ω” ’µΩ ˝æð∫Ûª·Ω¯?––ƒƒ–©¥¶¿Ì£ø ? ∑˛ŒÒ∆˜∑µªÿ ˝æð∫ۉؿ¿∆˜»Á∫Œ¥¶¿Ì£ø ? ‰Ø¿¿∆˜»Á∫ŒΩ´?“≥?√Ê’πœ÷≥ˆ¿¥£ø
- 5. ?¥Û∏Ÿ ? ˝æ𵃥´ ‰ ? ¥¯øÌ∫Õ—”≥Ÿ ? ??Õ¯¬Á–≠“È ? ª∫¥Ê ? ˝æ𵃉÷»æ ? HTML & CSS ? JavaScript Engine
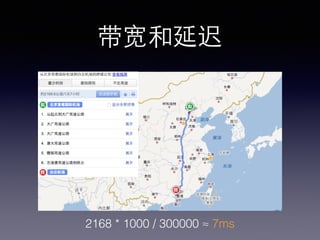
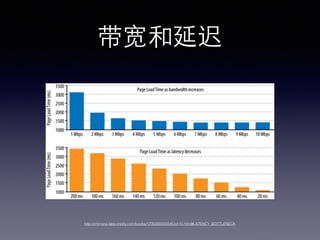
- 6. ¥¯øÌ∫Õ—”≥Ÿ 2168 * 1000 / 300000 °÷ 7ms
- 10. ¥¯øÌ∫Õ—”≥Ÿ ? ¥¯øÌ ≤ª «ƒ«√¥÷ÿ“™ ? —”≥Ÿ ≤≈ «”∞œÏ??Õ¯¬Á–‘ƒÐµƒπÿº¸
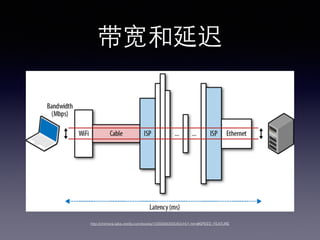
- 11. ??Õ¯¬Á–≠“È ? DNS ? TCP/IP ? HTTP/1.0 & 1.1 ? SPDY
- 12. DNS ? DNS≤È—Ø «?±»Ωœ∫ƒ ±µƒ?“ª∏ˆ≤Ÿ◊˜ ? dig +trace www. @8.8.8.8
- 13. DNS ! ; <<>> DiG 9.8.3-P1 <<>> +trace www. @8.8.8.8 ;; global options: +cmd . 18409 IN NS j.root-servers.net. . 18409 IN NS b.root-servers.net. ;; Received 228 bytes from 8.8.8.8#53(8.8.8.8) in 127 ms ! com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. ;; Received 491 bytes from 202.12.27.33#53(202.12.27.33) in 318 ms ! . 172800 IN NS dns.. . 172800 IN NS ns2.. . 172800 IN NS ns3.. . 172800 IN NS ns4.. . 172800 IN NS ns7.. ;; Received 201 bytes from 192.31.80.30#53(192.31.80.30) in 409 ms ! www.. 1200 IN CNAME www.a.shifen.com. a.shifen.com. 1200 IN NS ns5.a.shifen.com. a.shifen.com. 1200 IN NS ns4.a.shifen.com. a.shifen.com. 1200 IN NS ns3.a.shifen.com. a.shifen.com. 1200 IN NS ns2.a.shifen.com. a.shifen.com. 1200 IN NS ns1.a.shifen.com. ;; Received 228 bytes from 220.181.37.10#53(220.181.37.10) in 30 ms
- 14. DNS ? dig www. @8.8.8.8 ? dig www. @114.114.114.114
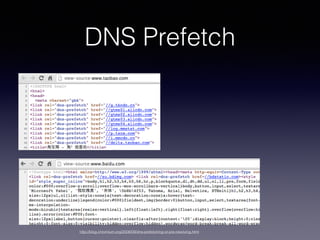
- 15. DNS Cache
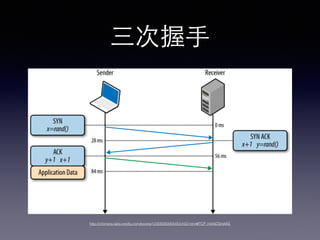
- 17. TCP/IP ? »˝¥ŒŒ’? ÷ ? SYN, SYN ACK, ACK ? ¬˝∆Ù∂Ø∫Õ¡˜¡øøÿ÷∆
- 21. ¿©’π‘ƒ∂¡ ? TCP Fast Open ? SYN ∞¸¥´ ‰ ˝æð£¨ΩµµÕ ~15% ? Building Blocks of TCP ? QUIC£®Quick UDP Internet Connections£© ? 0 - RTT ? ±Ð√‚ HOLB
- 22. HTTP 1.0 & 1.1 ? 1996: RFC1945 ? 1999: RFC2616 ? 2014: RFC7230, RFC7231, RFC7232, RFC7233, RFC7234, RFC7235
- 23. HTTP 1.1 vs 1.0 ? –¬‘ˆµƒ?“ª–©Ãÿ–‘ ? Keep-Alive Connection ? Chunked Encoding Transfer ? Byte Range Requests ? Cache Mechanisms ? Request Pipeline ? °≠°≠
- 24. Keep-Alive Connection $ telnet www. 80 Trying 61.135.169.125... Connected to www.a.shifen.com. Escape character is °Æ^]'. GET / HTTP/1.0 ! HTTP/1.1 200 OK Content-Type: text/html Connection: Close °≠°≠°≠ Connection closed by foreign host. $ telnet www. 80 Trying 61.135.169.125... Connected to www.a.shifen.com. Escape character is °Æ^]'. GET / HTTP/1.1 Host: www. ! HTTP/1.1 200 OK °≠ Content-Type: text/html Transfer-Encoding: chunked Connection: Keep-Alive °≠ ! 3dd6 °≠°≠°≠ 0
- 26. Byte Range Requests wget -c http://www.
- 27. Cache Mechanisms ? Expires ? Cache-Control ? max-age, no-cache, public, private ? Last-Modi?ed ? ETag
- 28. Cache Mechanisms ? Expires ∫Õ Cache-Control ?∂˛—°?“ª ? Ω®“È π?”√Cache-Control£¨±Ð√‚Request Peak ? ÷˜?“≥?√Ê≤ª…Ë÷√£¨ªÚ’þ…Ë÷√≤ªª∫¥Ê Expires: -1 ? Last-Modi?ed ∫Õ ETag ?∂˛—°?“ª ? Ω®“È π?”√ETag£¨∏¸◊º»∑?“ª–©
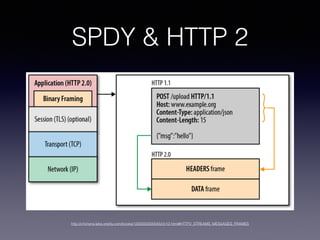
- 31. SPDY & HTTP 2 ? ÷˜“™??ƒøµƒ «ΩµµÕ¥´ ‰µƒ—”≥Ÿ ? HTTP 2 «ª˘”⁄SPDYΩ¯?––—ðªØ ? https://http2.github.io/http2-spec/
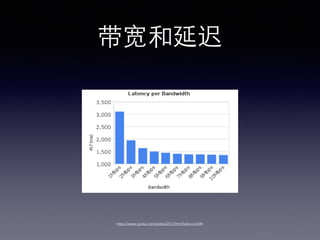
- 32. SPDY & HTTP 2 http://chimera.labs.oreilly.com/books/1230000000545/ch12.html#HTTP2_STREAMS_MESSAGES_FRAMES
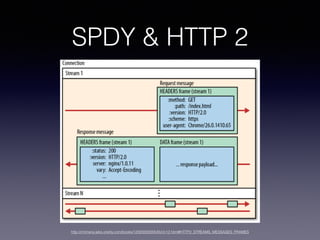
- 33. SPDY & HTTP 2 http://chimera.labs.oreilly.com/books/1230000000545/ch12.html#HTTP2_STREAMS_MESSAGES_FRAMES
- 34. SPDY & HTTP 2 vs HTTP 1 http://stackover?ow.com/questions/10480122/difference-between-http-pipeling-and-http-multiplexing-with-spdy
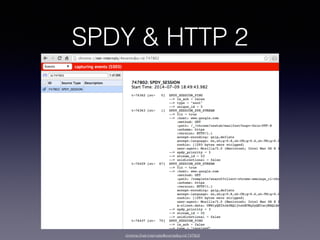
- 35. SPDY & HTTP 2 chrome://net-internals/#events&q=id:747802
- 36. SPDY & HTTP 2
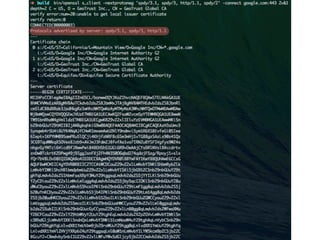
- 37. »Á∫Œ?…˙–ßµƒ£ø ? bin/openssl s_client -nextprotoneg 'spdy/3.1, spdy/3, http/1.1, spdy/2' -connect google.com:443
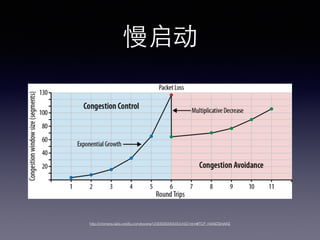
- 39. ˝æ𵃥´ ‰ ? —”≥Ÿ∫Ð÷ÿ“™ ? ºı…ŸDNS≤È—Ø / DNS‘§≤È—Ø / DNSΩ·π˚ª∫¥Ê ? ºı…ŸHTTP«Î«Ûµƒ ˝ ? æ°¡ø π?”√CDN ? ∫œ¿Ìµƒ≈‰÷√∑˛ŒÒ∆˜ª∫¥Ê≤þ¬‘ ? ºı…Ÿ¥´ ‰µƒƒ⁄»ð?¥Û?–° / —πÀı?Œƒ±æ / …æ≥˝?ŒÞ?”√µƒ?Œƒ±æ ? –¬µƒ–≠“È SPDY, QUIC, HTTP 2
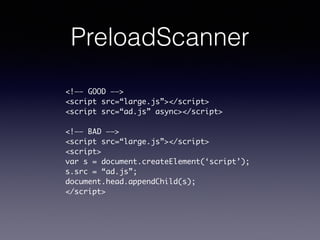
- 40. HTML & CSS ? PreloadScanner ? È–¥?∏þ–ßµƒ CSS selectors ? ±Ð√‚ π?”√ CSS expressions ? ∞—CSS∑≈µΩ?“≥?√Ê∂•≤ø ? √˜»∑Õº?∆¨µƒ≥þ?¥Á ? √˜»∑ƒ⁄»ðµƒ±ý¬Î ? °≠°≠
- 42. PreloadScanner <!°™°™ GOOD °™°™> <script src=/slideshow/web-2014/37087385/°∞large.js°±></script> <script src=°∞ad.js°± async></script> ! <!°™°™ BAD °™°™> <script src=/slideshow/web-2014/37087385/°∞large.js°±></script> <script> var s = document.createElement(°Æscript°Ø); s.src = °∞ad.js°±; document.head.appendChild(s); </script>
- 43. È–¥?∏þ–ßµƒ CSS selectors ? Avoid a universal key selector. ? Make your rules as speci?c as possible. ? Remove redundant quali?ers. ? Avoid using descendant selectors, especially those that specify redundant ancestors. ? Use class selectors instead of descendant selectors. https://developers.google.com/speed/docs/best-practices/rendering#UseEf?cientCSSSelectors
- 44. ±Ð√‚ π?”√ CSS expressions ? »Áπ˚ø…ƒÐµƒª∞£¨ π?”√±Í◊ºµƒ CSS Ù–‘ ? »Áπ˚?ŒÞ∑®±Ð√‚£¨æ°¡ø?”√ JavaScript ¿¥ÕÍ≥…À˘–˵ƒ π¶ƒÐ
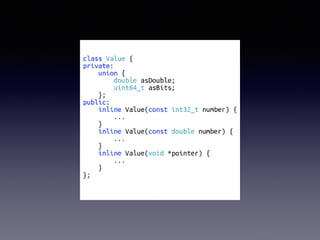
- 45. JavaScript Engine ? JIT Optimization ? Optimization killers
- 46. JIT Optimization ? Small Integers ? Hidden Class ? Inline Cache ? Type Interface ? ...
- 47. WTF?
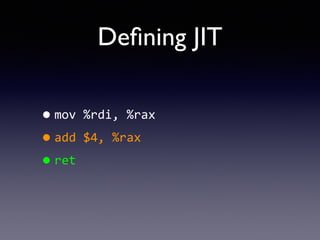
- 48. De?ning JIT ?Finding ?a ?way ?to ?generate ?native ? code ? ?Then ?execute ?the ?native ?code
- 49. De?ning JIT ! ?unsigned ?char[] ?code ?= ?{ ? ? ? ?0x48, ?0x89, ?0xf8 ? ? ? ?0x48, ?0x83, ?0xc0, ?0x04 ? ? ? ?0xc3 };
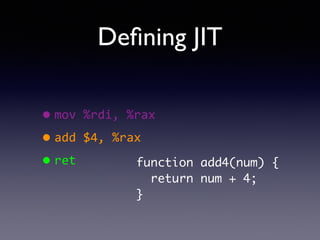
- 50. De?ning JIT ?mov ?%rdi, ?%rax ? ?add ?$4, ?%rax ? ?ret
- 51. De?ning JIT ?mov ?%rdi, ?%rax ? ?add ?$4, ?%rax ? ?ret function add4(num) { return num + 4; }
- 54. Value Representation ? Tagged pointer ? NaN Boxing Avoid Pointer Dereference
- 55. Tagged pointer ? Pointer vs Integer
- 56. sizeof( void * ) ? 32bit ? 64bit
- 57. Aligned pointer ? pointer ?% ?8 ?== ?0 ? ? pointer ?% ?4 ?== ?0
- 58. Tagged pointer ? 1010 1111 0101 0011 1100 0000 0000 0000 ? 1010 1111 0101 0011 1100 0000 0000 0000 1010 1111 0101 0011 1100 0000 0000 0000
- 59. Tagged pointer int31 ?iiiiiiii|iiiiiiii|iiiiiiii|iiiiiii1 ? ?Range: ?[0, ?2^31]
- 60. Tagged Pointer ? int32 & double will over?ow
- 61. Tagged pointer pointer ?pppppppp|pppppppp|pppppppp|ppppppT0 ? ?Range: ?[0, ?2^31]
- 62. NaN Boxing
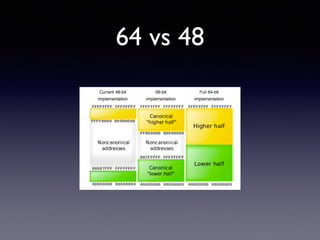
- 63. 64 vs 48
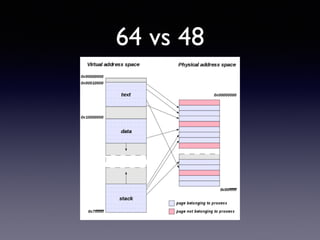
- 65. 64 vs 48
- 66. NaN Boxing
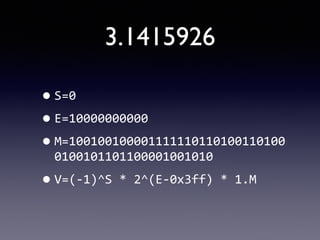
- 67. 3.1415926 ?S=0 ? ?E=10000000000 ? ?M=100100100001111110110100110100 0100101101100001001010 ? ?V=(-?©\1)^S ?* ?2^(E-?©\0x3ff) ?* ?1.M
- 69. The end
- 70. Optimization killers ? with ? debugger ? arguments ? for-in ? °≠
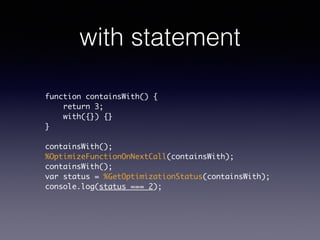
- 71. with statement function containsWith() { return 3; with({}) {} } ! containsWith(); %OptimizeFunctionOnNextCall(containsWith); containsWith(); var status = %GetOptimizationStatus(containsWith); console.log(status === 2);
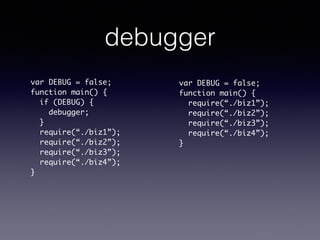
- 72. debugger var DEBUG = false; function main() { if (DEBUG) { debugger; } require(°∞./biz1°±); require(°∞./biz2°±); require(°∞./biz3°±); require(°∞./biz4°±); } var DEBUG = false; function main() { require(°∞./biz1°±); require(°∞./biz2°±); require(°∞./biz3°±); require(°∞./biz4°±); }
- 73. arguments function fn1(a, b) { b = b || 10; return a + b; } ! function fn2() { var args = [].slice.call( arguments); } function fn3(a, opt_b) { var b = opt_b || 10; return a + b; } ! function fn4() { var args = []; for(var i = 0; i < arguments.length; i ++ ){ args[i] = arguments[i]; } }
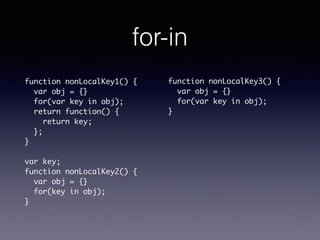
- 74. for-in function nonLocalKey1() { var obj = {} for(var key in obj); return function() { return key; }; } ! var key; function nonLocalKey2() { var obj = {} for(key in obj); } function nonLocalKey3() { var obj = {} for(var key in obj); }
- 75. ˝æ𵃉÷»æ ? HTML & CSS ? √ª”– ≤√¥Ãÿ ‚◊¢“‚µƒƒ⁄»ð ? øÿ÷∆¥˙¬ÎµƒÃª˝£¨—°‘Ò∫œ¿ÌµƒHTMLΩ·ππ ? JavaScript Engine ? JS“˝«Êµƒ–‘ƒÐ‘Ω¿¥‘Ω∫√ ? Make it happy!
- 76. π´Àæƒ⁄µƒ?“ª–©∆Ωî ? http://uaq. ? http://webspeed. ? http://speedup. ? http://yunjiasu. ? http://bcs-console.bae.
- 78. Q & A
- 79. References
- 80. References
- 81. References
- 82. References ? https://developers.google.com/speed/docs/best-practices/rendering ? https://developers.google.com/speed/articles/spdy-for-mobile ? https://docs.google.com/spreadsheet/ccc? key=0As3TLupYw2RedG50WW9hNldQaERDTlFHMEc2S2FBTXc#gid=4 ? https://www.igvita.com/ ? https://www.igvita.com/slides/2012/html5devconf/#52 ? http://httparchive.org/trends.php#bytesTotal&reqTotal ? http://http2.github.io/ ? https://github.com/h5bp/server-con?gs ? https://igrigorik.github.io/resource-hints/ ? http://nikic.github.io/2012/02/02/Pointer-magic-for-ef?cient-dynamic-value-representations.html ? °≠°≠
















![Keep-Alive Connection
$ telnet www. 80
Trying 61.135.169.125...
Connected to www.a.shifen.com.
Escape character is °Æ^]'.
GET / HTTP/1.0
!
HTTP/1.1 200 OK
Content-Type: text/html
Connection: Close
°≠°≠°≠
Connection closed by foreign host.
$ telnet www. 80
Trying 61.135.169.125...
Connected to www.a.shifen.com.
Escape character is °Æ^]'.
GET / HTTP/1.1
Host: www.
!
HTTP/1.1 200 OK
°≠
Content-Type: text/html
Transfer-Encoding: chunked
Connection: Keep-Alive
°≠
!
3dd6
°≠°≠°≠
0](https://image.slidesharecdn.com/web-2014-140717081956-phpapp01/85/Web-2014-24-320.jpg)















![De?ning JIT
!
?unsigned
?char[]
?code
?=
?{
?
?
?
?0x48,
?0x89,
?0xf8
?
?
?
?0x48,
?0x83,
?0xc0,
?0x04
?
?
?
?0xc3
};](https://image.slidesharecdn.com/web-2014-140717081956-phpapp01/85/Web-2014-49-320.jpg)






![Tagged pointer int31
?iiiiiiii|iiiiiiii|iiiiiiii|iiiiiii1
?
?Range:
?[0,
?2^31]](https://image.slidesharecdn.com/web-2014-140717081956-phpapp01/85/Web-2014-59-320.jpg)

![Tagged pointer pointer
?pppppppp|pppppppp|pppppppp|ppppppT0
?
?Range:
?[0,
?2^31]](https://image.slidesharecdn.com/web-2014-140717081956-phpapp01/85/Web-2014-61-320.jpg)



![arguments
function fn1(a, b) {
b = b || 10;
return a + b;
}
!
function fn2() {
var args = [].slice.call(
arguments);
}
function fn3(a, opt_b) {
var b = opt_b || 10;
return a + b;
}
!
function fn4() {
var args = [];
for(var i = 0;
i < arguments.length;
i ++ ){
args[i] = arguments[i];
}
}](https://image.slidesharecdn.com/web-2014-140717081956-phpapp01/85/Web-2014-73-320.jpg)