Web proxy server
Download as pptx, pdf0 likes1,683 views
A web proxy server functions as a firewall by limiting outside access to client computers and protecting them from hackers. It allows clients connected to the proxy server to access the internet from behind the firewall with minimal effort and without compromising security. The proxy server listens for requests from clients and forwards them to remote internet servers, and also listens for responses to send back to clients. This allows the proxy server to cache frequently requested documents and control internet access at the protocol level.
1 of 9
Downloaded 31 times


Ad
Recommended
Web Proxy Server
Web Proxy ServerMohit Dhankher
╠²
A web proxy server acts as an intermediary between clients and external servers on the internet. It protects clients by filtering traffic and limiting outside access. When a client requests a resource, the proxy server evaluates the request according to its rules before forwarding it to the external server. It then sends the response back to the client. This allows all clients connected to the proxy server to access the internet from behind the firewall with improved security and performance. The proxy server can also cache frequently requested resources to speed up access.Firewall & Proxy Server
Firewall & Proxy ServerLakshyaArora12
╠²
This document discusses firewalls and proxy servers, their relationship, types, hardware and software requirements. It defines a firewall as a device or program that filters network traffic to protect systems. A proxy server acts as an intermediary for requests between a user's device and websites. Hardware firewalls are physical devices that can protect entire networks, while software firewalls run on individual systems. Packet filtering and proxy server firewalls are described in terms of their operation and requirements. The document concludes that firewalls and proxy servers both enhance network security but that a proxy server can be integrated into a firewall system.Proxy server
Proxy serverProxies Rent
╠²
The document explains the function of proxy servers as intermediaries for client requests for resources. It covers various uses for proxies, including privacy protection, bypassing content restrictions, and load balancing, along with details about specific proxies for popular websites. Additionally, it discusses the importance of secure proxies and addresses the issues with free proxies that are often ineffective for certain services.Http Proxy Server
Http Proxy ServerSourav Roy
╠²
This document discusses HTTP proxy servers. It defines a proxy server as a server that acts as an intermediary for requests from clients and acts as a client to the actual servers. An HTTP proxy server specifically handles HTTP requests. It can speed up browsing by caching frequently requested pages. It also anonymizes user requests and reduces load on the internet connection. The document then discusses the software Proxyfire as an example of a "distorting" HTTP proxy server and provides screenshots of its interface. It concludes by listing the hardware and software specifications of the system used.Firewall with proxy server.
Firewall with proxy server.stableproxies
╠²
A proxy server acts as a gateway between users and the internet, improving performance through caching and bandwidth control while enabling anonymous browsing and content filtering. Different types of proxies serve various purposes, including web caching, content filtering, and anonymizing functions, enhancing security by hiding internal clients and blocking harmful content. The document outlines the operational benefits of proxy servers, including reduced latency and network traffic, and their application in both commercial and educational environments.Proxy Servers & Firewalls
Proxy Servers & FirewallsMehdi Poustchi Amin
╠²
Proxy servers and firewalls both act as gateways between internal networks and external networks like the internet. Proxy servers improve performance by caching frequently requested content, control bandwidth usage, and filter requests. Firewalls protect internal networks from external threats by packet filtering, analyzing packets, providing proxy services, and logging and alerting administrators of potential threats. Popular proxy software includes Squid, ISA Server, and WinRoute, while popular firewall software includes ISA Server, Cisco PIX, Norton Internet Security, and ZoneAlarm.seminar on proxyserver
seminar on proxyserverNiraj Barnwal
╠²
A proxy server acts as an intermediary between a client and the server they want to access. It intercepts all requests to the real server to see if it can fulfill the requests itself. If not, it forwards the request to the real server. Proxy servers improve performance by caching frequently requested content and filtering requests according to rules. Common types include HTTP, FTP, and SOCKS proxy servers. Proxy servers have advantages like improved performance and request filtering but also disadvantages like possible security risks, bandwidth usage, and speed issues.Group18_Awesome4some:Proxy server.ppt
Group18_Awesome4some:Proxy server.pptAnitha Selvan
╠²
This document discusses various types of proxy servers including anonymous proxy servers, HTTP proxy servers, FTP proxy servers, caching proxy servers, content filtering proxy servers, reverse proxy servers, and ICAP servers. It provides details on their functions and purposes. Team members on the Awesum4sum project are listed and an index outlines topics covered which include introduction to proxy servers, advantages and disadvantages, and a demonstration on CC Proxy.Proxy
ProxyTriad Square InfoSec
╠²
A proxy is a third computer that allows communication between two other computers by forwarding requests between them. There are three main types of proxies: forward proxies receive requests from an internal network and send them externally, open proxies forward requests between anywhere on the internet, and reverse proxies receive external requests and send them internally without external users knowing the internal network. Proxies provide security advantages like hiding internal clients, blocking dangerous content, and acting as a single point of access, control and logging.Proxy Servers
Proxy ServersSourav Roy
╠²
A proxy server acts as an intermediary between a client and the internet. It allows enterprises to ensure security, administrative control, and caching services. There are different types of proxy servers such as caching proxies, web proxies, content filtering proxies, and anonymizing proxies. Proxy servers can operate in either a transparent or opaque mode. They provide benefits like security, performance improvements through caching, and load balancing but also have disadvantages like creating single points of failure.Proxy Servers
Proxy ServersSourav Roy
╠²
A proxy server acts as an intermediary between a client device and the internet. It allows clients on a local network indirect access to outside networks like the internet. There are different types of proxy servers that provide advantages like improved security and performance through caching but also have disadvantages like potential slower speeds. Popular proxy server software includes Microsoft ISA Server, Squid, and WinRoute, while common hardware proxies include Cisco PIX and Blue Coat.How a Proxy Server Works
How a Proxy Server WorksMer Joyce
╠²
A proxy server routes web requests through an intermediary server to access sites that may be blocked locally. It works by sending requests from a user's computer to the proxy server instead of directly to the destination website, and then the proxy server forwards the request and sends the response back to the user, providing an indirect channel to access blocked content. The document recommends getting a list of proxy servers from Proxy.org and routes traffic to circumvent blocks, while also mentioning the related topic of Tor for anonymous web browsing.WT - Firewall & Proxy Server
WT - Firewall & Proxy Servervinay arora
╠²
A firewall sits between private and public networks like the Internet to protect computers from unauthorized access. There are different types of firewalls that operate at different layers, including packet filtering firewalls that work at the network layer, circuit-level firewalls that work at the session layer, and application-level firewalls that filter at the application layer. Stateful multilayer firewalls combine aspects of these approaches and can determine if a packet is part of an existing connection. Proxy servers act as intermediaries for client requests to other servers and can filter traffic according to rules.Advantages of proxy server
Advantages of proxy servergreatbury
╠²
The document discusses the advantages and functions of proxy servers, highlighting their role in enhancing web security by acting as intermediaries between users and the internet. Proxy servers help protect user identities by masking IP addresses and filtering malware, while also improving access speed through caching. They serve various purposes, including maintaining system security and enabling anonymous browsing.Proxy servers
Proxy serversKumar
╠²
Proxy servers sit between an internal network and an external network. They act as an intermediary for requests from the internal users to hide their IP addresses and improve security. Proxy servers terminate TCP connections, caching frequently requested files to improve performance, and can filter content to enforce security policies. They provide anonymity and security for internal users while allowing access to external networks and resources.Proxy Server
Proxy Serverguest095022
╠²
The document discusses proxy servers, specifically HTTP and FTP proxy servers. It defines a proxy server as a server that acts as an intermediary for requests from clients to other servers. It describes the main purposes of proxy servers as keeping machines behind it anonymous for security purposes and speeding up access to resources via caching. It also provides details on the mechanisms, types, protocols (HTTP and FTP), and functions of proxy servers.KILLME NOWITSELF
KILLME NOWITSELFShehab Imam
╠²
This document discusses different types of proxy servers and provides information about HTTP proxy servers and the proxy server software Proxyfire. It defines a proxy server as a server that acts as an intermediary between clients and real servers. There are four main types of proxy servers: FTP, HTTP, SOCKS, and SSL. Proxyfire is a proxy server checker that can detect different proxy types like HTTP, SOCKS, and anonymous proxies and classify them. It works by examining inbound traffic rather than just outbound traffic.Proxy Presentation
Proxy Presentationprimeteacher32
╠²
Proxy servers act as intermediaries between internal and external networks, screening traffic and enforcing security policies. They can conceal internal network structure, filter undesirable content, and provide detailed logs. Proxy servers differ from packet filters in that they operate at the application layer and can reconstruct packets with new source IP information to shield internal hosts. Common configurations involve a computer with two network interfaces, one internal and one external. Benefits include concealed clients, blocked URLs and content, and robust logging. Proper configuration of both the proxy server and client software is required.Proxy server
Proxy serverDlovan Salih
╠²
The document explains what a proxy server is, its functionalities, and various types such as anonymous, HTTP, and SSL proxies. It outlines the purposes of using a proxy server, including enhancing internal security, speeding up resource access, and content filtering. The conclusion emphasizes the need for trust in using proxies and mentions an experiment to assess their effectiveness.Proxy Server: A Comprehensive Guide
Proxy Server: A Comprehensive GuideHTS Hosting
╠²
The document is a comprehensive guide on proxy servers, explaining their functions, types, and uses. It highlights how proxy servers act as intermediaries to enhance security, maintain anonymity, and improve performance for users accessing the internet. Various types of proxy servers, such as anonymous proxies, transparent proxies, and tor onion proxies, are described, each serving distinct purposes in network communication.Linux11 Proxy Server
Linux11 Proxy ServerJainul Musani
╠²
A proxy server sits between a LAN and the internet and allows users on the LAN to access the internet in a secure manner. It accepts requests from users and enables them to browse websites and access other internet services without providing direct connectivity to the internet. Common proxy server software includes Squid, Microsoft Proxy Server, and Apache. Squid is an open source caching proxy that improves performance by caching frequently requested web pages. It can be installed and configured on Linux by editing the squid.conf file to specify settings like the visible hostname and network interface to use.How to set up a proxy server on windows
How to set up a proxy server on windows codeandyou forums
╠²
This document provides step-by-step instructions for setting up a proxy server on Windows using AnalogX proxy server software. It describes downloading and installing AnalogX, configuring the proxy server, establishing the proxy connection, and setting up the proxy in a web browser. The proxy routes internet requests through one source, allowing the administrator to control access from the proxy server.Reverse proxy
Reverse proxyProxies Rent
╠²
A reverse proxy is a type of server that retrieves resources on behalf of a client from multiple servers, masking the origin server's characteristics. It can enhance security, load balancing, and performance by caching content, optimizing loading times, and facilitating tasks like SSL encryption. Additionally, reverse proxies are used for A/B testing and can simplify resource management across multiple web servers sharing a single IP address.Cc proxy
Cc proxyTrã░ß╗Øng Tiß╗ün
╠²
The document is a user manual for CCProxy proxy server software. It provides instructions for installing and configuring the software to share an internet connection on a local area network (LAN). CCProxy can act as an HTTP, FTP, mail, SOCKS and other protocol proxies. It includes features like account management, bandwidth control, web filtering, access logging and monitoring.Introduction to stable proxies.
Introduction to stable proxies.stableproxies
╠²
Proxy servers act as intermediaries for requests from clients to access resources from other servers. They can be used to share an internet connection on a local area network when multiple computers need access. Proxy servers also cache requests to speed up internet surfing for clients and can hide a client's IP address for anonymity and security reasons. Private proxies are exclusively used by one client to hide their public IP address, while shared proxies have multiple users accessing the same server and can transmit large amounts of data in a cost effective manner.Proxy Server
Proxy ServerNetwax Lab
╠²
A proxy server acts as an intermediary between a web browser and the internet, enhancing web performance by caching frequently accessed pages and filtering out harmful content. It provides various functionalities, including request filtering, translation for localization, and anonymous browsing, while also maintaining network security. Different types of proxy servers, such as forward and reverse proxies, serve specific purposes, such as load balancing, caching, and SSL encryption for web servers.Meeting 4 : proxy
Meeting 4 : proxySyaiful Ahdan
╠²
A proxy server acts as an intermediary between clients and servers. It receives requests from clients, then either fulfills them itself if the content is cached, or forwards the requests to the actual servers. Main functions of a proxy server include caching content to improve speed, providing basic firewall protection, and filtering traffic through mechanisms like blacklists, whitelists, and text analysis of web pages. However, maintaining comprehensive and up-to-date lists and effective text analysis at web scale is challenging given the enormous and constantly changing volume of internet content.Kerio Connect 7 Features and Benefits
Kerio Connect 7 Features and BenefitsKerio Technologies
╠²
Kerio Connect is an email server software that provides comprehensive email services like messaging, collaboration, mobile device synchronization, filtering and archiving. It offers ease of administration through a small IT footprint and flexible deployment across Windows, Mac and Linux platforms. New features in Kerio Connect include distributed domain administration, full web administration, CardDAV access, and support for additional mobile platforms like WebOS and Android. It is priced affordably with server licenses starting at $450 and additional users priced at $120 per 5 users.zigbee
zigbeemahamad juber
╠²
This document discusses the design and implementation of a proxy server. A proxy server acts as an intermediary between clients and external servers, caching frequently accessed content to improve performance and providing firewall functionality to enhance security. The implemented proxy server is a multithreaded Java application that handles client requests, checks the cache for content, forwards requests to remote servers if needed, and returns responses while also updating the cache. It functions by having a main daemon thread listen for connections and spawn new threads to handle each client request by communicating with servers and caching content.Proxy http ftp dns email
Proxy http ftp dns emailHeera K S
╠²
Proxy servers operate as an intermediary between a local network and services available on a larger network like the Internet. They improve performance by caching frequently requested web pages and filtering requests to prevent access to certain sites or protocols. The main types of proxy servers are caching proxy servers, web proxy servers, content-filtering web proxy servers, and anonymizing proxy servers.More Related Content
What's hot (20)
Proxy
ProxyTriad Square InfoSec
╠²
A proxy is a third computer that allows communication between two other computers by forwarding requests between them. There are three main types of proxies: forward proxies receive requests from an internal network and send them externally, open proxies forward requests between anywhere on the internet, and reverse proxies receive external requests and send them internally without external users knowing the internal network. Proxies provide security advantages like hiding internal clients, blocking dangerous content, and acting as a single point of access, control and logging.Proxy Servers
Proxy ServersSourav Roy
╠²
A proxy server acts as an intermediary between a client and the internet. It allows enterprises to ensure security, administrative control, and caching services. There are different types of proxy servers such as caching proxies, web proxies, content filtering proxies, and anonymizing proxies. Proxy servers can operate in either a transparent or opaque mode. They provide benefits like security, performance improvements through caching, and load balancing but also have disadvantages like creating single points of failure.Proxy Servers
Proxy ServersSourav Roy
╠²
A proxy server acts as an intermediary between a client device and the internet. It allows clients on a local network indirect access to outside networks like the internet. There are different types of proxy servers that provide advantages like improved security and performance through caching but also have disadvantages like potential slower speeds. Popular proxy server software includes Microsoft ISA Server, Squid, and WinRoute, while common hardware proxies include Cisco PIX and Blue Coat.How a Proxy Server Works
How a Proxy Server WorksMer Joyce
╠²
A proxy server routes web requests through an intermediary server to access sites that may be blocked locally. It works by sending requests from a user's computer to the proxy server instead of directly to the destination website, and then the proxy server forwards the request and sends the response back to the user, providing an indirect channel to access blocked content. The document recommends getting a list of proxy servers from Proxy.org and routes traffic to circumvent blocks, while also mentioning the related topic of Tor for anonymous web browsing.WT - Firewall & Proxy Server
WT - Firewall & Proxy Servervinay arora
╠²
A firewall sits between private and public networks like the Internet to protect computers from unauthorized access. There are different types of firewalls that operate at different layers, including packet filtering firewalls that work at the network layer, circuit-level firewalls that work at the session layer, and application-level firewalls that filter at the application layer. Stateful multilayer firewalls combine aspects of these approaches and can determine if a packet is part of an existing connection. Proxy servers act as intermediaries for client requests to other servers and can filter traffic according to rules.Advantages of proxy server
Advantages of proxy servergreatbury
╠²
The document discusses the advantages and functions of proxy servers, highlighting their role in enhancing web security by acting as intermediaries between users and the internet. Proxy servers help protect user identities by masking IP addresses and filtering malware, while also improving access speed through caching. They serve various purposes, including maintaining system security and enabling anonymous browsing.Proxy servers
Proxy serversKumar
╠²
Proxy servers sit between an internal network and an external network. They act as an intermediary for requests from the internal users to hide their IP addresses and improve security. Proxy servers terminate TCP connections, caching frequently requested files to improve performance, and can filter content to enforce security policies. They provide anonymity and security for internal users while allowing access to external networks and resources.Proxy Server
Proxy Serverguest095022
╠²
The document discusses proxy servers, specifically HTTP and FTP proxy servers. It defines a proxy server as a server that acts as an intermediary for requests from clients to other servers. It describes the main purposes of proxy servers as keeping machines behind it anonymous for security purposes and speeding up access to resources via caching. It also provides details on the mechanisms, types, protocols (HTTP and FTP), and functions of proxy servers.KILLME NOWITSELF
KILLME NOWITSELFShehab Imam
╠²
This document discusses different types of proxy servers and provides information about HTTP proxy servers and the proxy server software Proxyfire. It defines a proxy server as a server that acts as an intermediary between clients and real servers. There are four main types of proxy servers: FTP, HTTP, SOCKS, and SSL. Proxyfire is a proxy server checker that can detect different proxy types like HTTP, SOCKS, and anonymous proxies and classify them. It works by examining inbound traffic rather than just outbound traffic.Proxy Presentation
Proxy Presentationprimeteacher32
╠²
Proxy servers act as intermediaries between internal and external networks, screening traffic and enforcing security policies. They can conceal internal network structure, filter undesirable content, and provide detailed logs. Proxy servers differ from packet filters in that they operate at the application layer and can reconstruct packets with new source IP information to shield internal hosts. Common configurations involve a computer with two network interfaces, one internal and one external. Benefits include concealed clients, blocked URLs and content, and robust logging. Proper configuration of both the proxy server and client software is required.Proxy server
Proxy serverDlovan Salih
╠²
The document explains what a proxy server is, its functionalities, and various types such as anonymous, HTTP, and SSL proxies. It outlines the purposes of using a proxy server, including enhancing internal security, speeding up resource access, and content filtering. The conclusion emphasizes the need for trust in using proxies and mentions an experiment to assess their effectiveness.Proxy Server: A Comprehensive Guide
Proxy Server: A Comprehensive GuideHTS Hosting
╠²
The document is a comprehensive guide on proxy servers, explaining their functions, types, and uses. It highlights how proxy servers act as intermediaries to enhance security, maintain anonymity, and improve performance for users accessing the internet. Various types of proxy servers, such as anonymous proxies, transparent proxies, and tor onion proxies, are described, each serving distinct purposes in network communication.Linux11 Proxy Server
Linux11 Proxy ServerJainul Musani
╠²
A proxy server sits between a LAN and the internet and allows users on the LAN to access the internet in a secure manner. It accepts requests from users and enables them to browse websites and access other internet services without providing direct connectivity to the internet. Common proxy server software includes Squid, Microsoft Proxy Server, and Apache. Squid is an open source caching proxy that improves performance by caching frequently requested web pages. It can be installed and configured on Linux by editing the squid.conf file to specify settings like the visible hostname and network interface to use.How to set up a proxy server on windows
How to set up a proxy server on windows codeandyou forums
╠²
This document provides step-by-step instructions for setting up a proxy server on Windows using AnalogX proxy server software. It describes downloading and installing AnalogX, configuring the proxy server, establishing the proxy connection, and setting up the proxy in a web browser. The proxy routes internet requests through one source, allowing the administrator to control access from the proxy server.Reverse proxy
Reverse proxyProxies Rent
╠²
A reverse proxy is a type of server that retrieves resources on behalf of a client from multiple servers, masking the origin server's characteristics. It can enhance security, load balancing, and performance by caching content, optimizing loading times, and facilitating tasks like SSL encryption. Additionally, reverse proxies are used for A/B testing and can simplify resource management across multiple web servers sharing a single IP address.Cc proxy
Cc proxyTrã░ß╗Øng Tiß╗ün
╠²
The document is a user manual for CCProxy proxy server software. It provides instructions for installing and configuring the software to share an internet connection on a local area network (LAN). CCProxy can act as an HTTP, FTP, mail, SOCKS and other protocol proxies. It includes features like account management, bandwidth control, web filtering, access logging and monitoring.Introduction to stable proxies.
Introduction to stable proxies.stableproxies
╠²
Proxy servers act as intermediaries for requests from clients to access resources from other servers. They can be used to share an internet connection on a local area network when multiple computers need access. Proxy servers also cache requests to speed up internet surfing for clients and can hide a client's IP address for anonymity and security reasons. Private proxies are exclusively used by one client to hide their public IP address, while shared proxies have multiple users accessing the same server and can transmit large amounts of data in a cost effective manner.Proxy Server
Proxy ServerNetwax Lab
╠²
A proxy server acts as an intermediary between a web browser and the internet, enhancing web performance by caching frequently accessed pages and filtering out harmful content. It provides various functionalities, including request filtering, translation for localization, and anonymous browsing, while also maintaining network security. Different types of proxy servers, such as forward and reverse proxies, serve specific purposes, such as load balancing, caching, and SSL encryption for web servers.Meeting 4 : proxy
Meeting 4 : proxySyaiful Ahdan
╠²
A proxy server acts as an intermediary between clients and servers. It receives requests from clients, then either fulfills them itself if the content is cached, or forwards the requests to the actual servers. Main functions of a proxy server include caching content to improve speed, providing basic firewall protection, and filtering traffic through mechanisms like blacklists, whitelists, and text analysis of web pages. However, maintaining comprehensive and up-to-date lists and effective text analysis at web scale is challenging given the enormous and constantly changing volume of internet content.Kerio Connect 7 Features and Benefits
Kerio Connect 7 Features and BenefitsKerio Technologies
╠²
Kerio Connect is an email server software that provides comprehensive email services like messaging, collaboration, mobile device synchronization, filtering and archiving. It offers ease of administration through a small IT footprint and flexible deployment across Windows, Mac and Linux platforms. New features in Kerio Connect include distributed domain administration, full web administration, CardDAV access, and support for additional mobile platforms like WebOS and Android. It is priced affordably with server licenses starting at $450 and additional users priced at $120 per 5 users.Similar to Web proxy server (20)
zigbee
zigbeemahamad juber
╠²
This document discusses the design and implementation of a proxy server. A proxy server acts as an intermediary between clients and external servers, caching frequently accessed content to improve performance and providing firewall functionality to enhance security. The implemented proxy server is a multithreaded Java application that handles client requests, checks the cache for content, forwards requests to remote servers if needed, and returns responses while also updating the cache. It functions by having a main daemon thread listen for connections and spawn new threads to handle each client request by communicating with servers and caching content.Proxy http ftp dns email
Proxy http ftp dns emailHeera K S
╠²
Proxy servers operate as an intermediary between a local network and services available on a larger network like the Internet. They improve performance by caching frequently requested web pages and filtering requests to prevent access to certain sites or protocols. The main types of proxy servers are caching proxy servers, web proxy servers, content-filtering web proxy servers, and anonymizing proxy servers.cybersecurity unit 5 basics of cybersecurity
cybersecurity unit 5 basics of cybersecurityJayaMishra170943
╠²
This document discusses proxy servers and anonymizers used in cybersecurity. It begins by defining a proxy server as a server that acts as an intermediary between client requests and servers, protecting the direct connection. Anonymizers are then introduced as proxy servers that limit the data a user reveals while browsing to hide their IP address and location. The document outlines different types of anonymizers like VPNs, proxy servers, and Tor, which routes traffic through nodes to anonymize a user's online activity.Information System Security
Information System Security Elijah Konzo
╠²
1. The document discusses SSH, Telnet, and proxy servers. SSH provides encrypted connections over unsecured networks, while Telnet lacks encryption. Proxies act on behalf of users to access resources, with forward proxies providing external access through a firewall and reverse proxies providing internal access from outside.
2. It provides examples of Linux commands to switch users using SSH, copy a file between accounts using sudo, and set file permissions using chmod and chown.Firewall vpn proxy
Firewall vpn proxySANKET SENAPATI
╠²
A firewall controls incoming and outgoing network traffic to protect devices from attacks. There are three main types: edge firewalls protect individual devices; appliance firewalls are dedicated firewall devices; and network firewalls protect entire networks using routers, bridges, or computer-based software. Firewalls are used to protect networks from probes and attacks, and provide security for less protected devices. Proxies act as intermediaries for network requests, allowing things like caching, filtering, authentication, and load balancing to improve security and performance. Reverse proxies specifically allow external users indirect access to internal servers and websites.Group20 Dynamic Networks
Group20 Dynamic Networkshariprasadnr
╠²
Proxy servers act as an intermediary for requests from clients seeking resources from other servers. There are different types of proxy servers including cache proxies that speed up access and web proxies that allow users to connect to servers and access the internet. Proxy servers aim to provide privacy by hiding clients' IP addresses and allow access around content blocks. FTP and HTTP are protocols for transferring files and web pages respectively using the client-server model, with FTP using separate control and data connections and HTTP using request and response messages. Proxy servers can also be used with FTP and HTTP to add capabilities like caching, authentication, and traffic monitoring.May proxy be_with_you
May proxy be_with_youHimani Singh
╠²
This document provides an extensive overview of different types of web proxies, including forward, reverse, and explicit proxies, as well as their functionalities like SSL termination and traffic filtering. It covers the configurations and operations of these proxies, highlighting the methods for traffic identification and SSL/TLS interception proxies' workings. Additionally, the document discusses the implications of SSL/TLS termination, the importance of certificate trust in secure communications, and the potential risks associated with interception proxies.thesis
thesisVenkata Jaswanth U
╠²
The document describes a dissertation submitted by three students for their Bachelor of Technology degree. It discusses the development of an HTTP proxy server called the Phoenix proxy server. The proxy server aims to provide features like user authentication, access control, caching, quota management, and logging in an efficient manner with simple configuration. The dissertation outlines the implementation approach for each feature and how the proxy server and client would work. It also describes the use of a web interface for proxy management and configuration.Pre Week13
Pre Week13Ryosuke
╠²
A proxy server acts as an intermediary between a client and an external server. When a client makes a request, the proxy server connects to the target server on the client's behalf and returns the information to the client. Proxy servers can cache responses to improve speed for subsequent identical requests from clients. They are often used within corporate networks to filter traffic and protect internal networks from unauthorized external access. However, using an untrusted proxy server poses risks as it can record unencrypted login credentials and browser activity passing through it.Pre Week14
Pre Week14Ryosuke
╠²
A proxy server acts as an intermediary between a client and an external server. When a client makes a request, the proxy server connects to the target server on the client's behalf and returns the information to the client. Proxy servers can cache responses to improve speed for subsequent identical requests from clients. They are often used within corporate networks to filter traffic and protect internal networks from unauthorized external access. However, using an untrusted proxy server poses risks as it can record unencrypted login credentials and browsing activity passing through it.Ce hv6 module 54 proxy server technologies
Ce hv6 module 54 proxy server technologiesVi Tính Hoàng Nam
╠²
This document provides an overview of proxy server technologies. It defines what a proxy server is and its basic functions. It then discusses different types of proxy servers and several proxy server tools, including WinGate, UserGate, SafeSquid, AllegroSurf, ezProxy, and AnalogX Proxy. The document aims to familiarize readers with proxy servers, their roles, types and some common tools.Unit 5 - Designing Internet Systems and Servers - IT
Unit 5 - Designing Internet Systems and Servers - ITDeepraj Bhujel
╠²
This document discusses various concepts related to designing internet systems and servers. It covers network architecture principles, components of internet architecture like routers and clients, and building blocks like addressing and routing. It also discusses server concepts like web, mail, proxy and RADIUS servers. It provides details on load balancing and the use of proxy server arrays for load balancing.Apache httpd 2.4 Reverse Proxy
Apache httpd 2.4 Reverse ProxyJim Jagielski
╠²
Jim Jagielski discusses improvements to Apache HTTP Server 2.4 including enhanced performance, support for asynchronous I/O, additional multi-processing modules, and improved functionality for reverse proxy servers. Key enhancements to Apache's reverse proxy module mod_proxy include support for additional protocols like FastCGI and SCGI, improved load balancing capabilities, and an embedded administration interface.Web technology
Web technologySelvin Josy Bai Somu
╠²
The document outlines key concepts related to web communication, server technologies, and web design, highlighting the role of HTML, HTTP, and various available scripting languages. It details the client-server model, secure data transmission, and the importance of web servers in hosting websites along with protocols for data transfer. Additionally, it explains the differences between static and dynamic web pages, and the use of various scripting languages like JavaScript and PHP in creating interactive web applications.WebTechnology Powerpointpresentation.pdf
WebTechnology Powerpointpresentation.pdfkrishkiran2408
╠²
The document covers essential aspects of web communication, server technologies, and web design, including the importance of protocols like TCP/IP and HTTP. It discusses web page types, scripting languages, and security measures like HTTPS and SSL for secure data transmission. Additionally, it highlights the roles of web servers, data centers, and the functioning of DNS in resolving domain names to IP addresses.Using aphace-as-proxy-server
Using aphace-as-proxy-serverHARRY CHAN PUTRA
╠²
Apache can function as both a forward and reverse proxy server. To configure it as a proxy, enable the proxy module, turn on proxy requests, and specify which clients can access the proxy. The proxy caches frequently accessed pages to improve performance and reduce bandwidth. It also provides security, access control, and logging of internet traffic on the network.Uses of proxies
Uses of proxiesProxies Rent
╠²
The document discusses various types of proxy servers, including transparent, anonymous, distorting, and high anonymity proxies, each offering different levels of anonymity and caching capabilities. It highlights the functions of web proxies, such as speeding up resource access, logging usage, preventing data loss, and filtering content. Users are advised to use proxy servers with caution and seek permission, as their usage may be illegal in certain jurisdictions.Unit v
Unit v APARNA P
╠²
This document provides an overview of the World Wide Web (WWW) and the Hypertext Transfer Protocol (HTTP). It discusses the architecture of the WWW including web clients, servers, and documents. It describes the Uniform Resource Locator (URL) format and explains static, dynamic, and active web documents. The document then focuses on HTTP, describing request and response message formats, methods, status codes, headers, cookies, caching with proxy servers, and HTTP security with SSL.Smuggling TCP traffic through HTTP
Smuggling TCP traffic through HTTPDávid Halász
╠²
This document discusses smuggling TCP traffic through HTTP by leveraging HTTP upgrades. It proposes a new project called Purr that implements a TCP "smuggling" server in Ruby using Rack and a client-side proxy. Purr aims to allow anything TCP-based to be tunneled through HTTP, controlled by a browser extension using native messaging and accessible from web apps via a JS library. The incomplete implementation has a server and basic client-side proxy functionality, but more work is needed for distribution, libraries, HTTPS support, and testing.Web application development ( basics )
Web application development ( basics )Chirag Nag
╠²
The document provides an introduction to web application development basics. It discusses how the world wide web is based on clients (web browsers) and servers. Web browsers allow users to access and navigate the internet, while web servers watch for and respond to requests from browsers by finding and sending back requested documents. The document also describes how browsers communicate with servers using protocols like HTTP and how dynamic web pages are generated through CGI scripts or server-side scripting languages.Ad
Web proxy server
- 1. WEB PROXY SERVER A Presentation on Proxy Server Vikas Reddy Merugu
- 2. WEB PROXY SERVER ÔÇó It is a specialized HTTP Server. ÔÇó Functions as a firewall. ÔÇó Protects client computers from Hackers by limiting outside access to clients. ÔÇó Allows all clients connected to Web Proxy Server to access Internet from behind ÔÇ£firewall.ÔÇØ ÔÇó Client computer(s) are allowed access past firewall with minimum effort and without compromising security.
- 3. HOW DOES IT WORKS ? ÔÇó Web Proxy Server listens for any request from clients. ÔÇó All requests are forwarded to remote internet servers outside firewall. ÔÇó Also listens for responses or request from outside the firewall (external servers) and sends to them to internal client computers. ÔÇó Usually, all clients with a subnet use the same proxy server. ÔÇó This makes it possible for the proxy server to cache documents that are requested by one or more clients (repeatedly).
- 4. CONTINUE  For clients using a web proxy server, it is as if they are getting responses directly from a remote server.  Clients without a Domain Name Service can still access the Web  All that is needed is the proxy servers IP address.  Most Web Proxy Servers are implemented on a per-access method basis.  It can allow or deny internet requests according to the protocol used.  For Example: A proxy server can allow calls to FTP while but deny calls to HTTP servers.
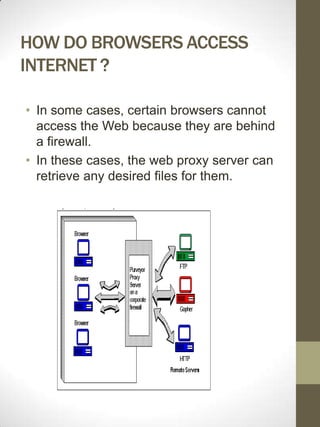
- 5. HOW DO BROWSERS ACCESS INTERNET ? ÔÇó In some cases, certain browsers cannot access the Web because they are behind a firewall. ÔÇó In these cases, the web proxy server can retrieve any desired files for them.
- 6. CONTROLLING ACCESS TO INTERNET ÔÇó Web proxy server makes it possible to filter client ÔÇ£transactionsÔÇØ at the protocol level. ÔÇó Controls access to services for individual methods, hosts, as well as domains. ÔÇó For Example, web proxy servers allows administrators to: ÔÇó Decide which requests to grant permission to and which ones to turn down. ÔÇó Specify the URL(s) masks of locations that you donÔÇÖt want the proxy server to serve. ÔÇó Specify which protocols clients can use the services based on their IP address.
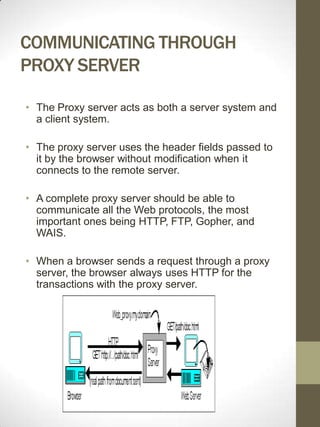
- 7. COMMUNICATING THROUGH PROXY SERVER ÔÇó The Proxy server acts as both a server system and a client system. ÔÇó The proxy server uses the header fields passed to it by the browser without modification when it connects to the remote server. ÔÇó A complete proxy server should be able to communicate all the Web protocols, the most important ones being HTTP, FTP, Gopher, and WAIS. ÔÇó When a browser sends a request through a proxy server, the browser always uses HTTP for the transactions with the proxy server.
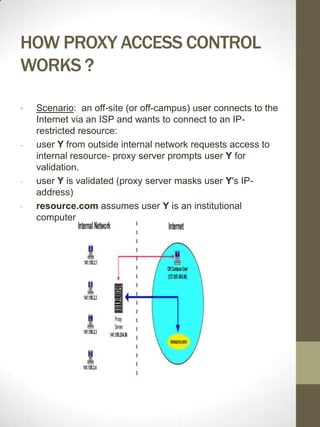
- 8. HOW PROXY ACCESS CONTROL WORKS ? ÔÇó Scenario: an off-site (or off-campus) user connects to the Internet via an ISP and wants to connect to an IP- restricted resource: - user Y from outside internal network requests access to internal resource- proxy server prompts user Y for validation. - user Y is validated (proxy server masks user Y's IP- address) - resource.com assumes user Y is an institutional computer
- 9. Thank you for your kind attention
