WhyNormShield
0 likes170 views
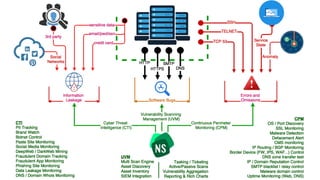
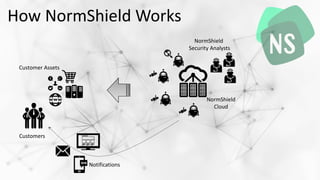
NormShield is a unified vulnerability management and cyber threat intelligence platform that uses 80% automated technology and 20% human intelligence to continuously monitor for vulnerabilities and threats. It aggregates data from open source intelligence, social media, blogs, and underground forums to identify unpatched vulnerabilities, data leaks, malware activities, and insider threats. Given that only 38% of organizations feel prepared for cyberattacks while just 0.1% of employees are security professionals, NormShield provides continuous security scanning to help organizations stay safe from the over 13,000 vulnerabilities published yearly.
1 of 14
Download to read offline





Ad
Recommended
NormShieldBrochure
NormShieldBrochureCandan BOLUKBAS
Ěý
NormShield is a unified vulnerability and cyber intelligence management solution that continuously monitors assets, vulnerabilities, and cyber threats through various tools and feeds. It detects issues and provides notifications and alarms through a centralized dashboard for remediation. Key features include vulnerability scanning, reputation monitoring, fraudulent domain detection, social media tracking, and passive vulnerability alerts.ICION 2016 - Cyber Security Governance
ICION 2016 - Cyber Security GovernanceCharles Lim
Ěý
This document discusses the Honeynet Project and cyber security governance frameworks. It provides an overview of Honeynet, a non-profit focused on computer security research. It then discusses the importance of cyber security governance and introduces the NIST Cybersecurity Framework. The framework consists of five functions (Identify, Protect, Detect, Respond, Recover), categories within each function, and implementation tiers that describe an organization's cybersecurity risk management practices. The document emphasizes that effective cyber security requires leadership and continuous risk management to address evolving threats.Big Data Analytics for Cyber Security: A Quick Overview
Big Data Analytics for Cyber Security: A Quick OverviewFemi Ashaye
Ěý
The document discusses the evolution of cyber security in relation to big data analytics, emphasizing the need for advanced analytical tools to address increased and evolving cyber threats. It highlights the limitations of traditional SIEM systems and advocates for integrating big data analytics to enhance threat detection and response capabilities. The conclusions stress the importance of adopting a more data-centric and agile approach to security intelligence, while also suggesting future investments in security analytics capabilities.Global Cyber Security Outlook - Deloitte (Hotel_Digital_Security_Seminar_Sept...
Global Cyber Security Outlook - Deloitte (Hotel_Digital_Security_Seminar_Sept...XEventsHospitality
Ěý
The document discusses the Hotel Digital Security Seminar held on September 19, 2014, highlighting critical cyber security challenges faced by organizations in India, particularly in the hospitality sector. It outlines trends in corporate espionage, the rise of cyber attacks, and emphasizes the importance of building robust cyber security strategies to protect sensitive information. Additionally, it underscores the need for compliance and proactive measures to mitigate risks associated with modern cyber threats.The role of big data, artificial intelligence and machine learning in cyber i...
The role of big data, artificial intelligence and machine learning in cyber i...Aladdin Dandis
Ěý
The document discusses the role of big data, artificial intelligence, and machine learning in cyber intelligence. It provides definitions of cyber intelligence and distinguishes between raw threat data and true threat intelligence. The document also outlines drivers for adopting AI-based cybersecurity technologies, including accelerating incident detection and response as well as improving risk communication and situational awareness. A cyber intelligence framework is proposed that involves collecting security data from various sources, processing the data using machine learning algorithms, and generating reports and alerts. Challenges with implementing such a framework are also noted.Cyber Security Awareness Month 2017-Wrap-Up
Cyber Security Awareness Month 2017-Wrap-UpChinatu Uzuegbu
Ěý
The Cyber Security Awareness Month 2017 emphasized the increasing threat of cyber crimes and the importance of proactive protection for personal and organizational information assets. The series covered essential concepts, including identifying and classifying information, protection techniques, and regulatory frameworks, encouraging individuals and entities to be aware and take responsibility for their cyber security. It concluded with a call for continuous learning and adherence to standards to enhance cyber resilience.Evidence-Based Security: The New Top Five Controls
Evidence-Based Security: The New Top Five ControlsPriyanka Aash
Ěý
The document summarizes evidence from multiple cybersecurity reports to propose an updated set of top five cybersecurity controls. It analyzes data on the most common attack vectors like phishing and use of stolen credentials. Based on this, the proposed top five controls are: 1) Implementing multifactor authentication and privileged access management, 2) Implementing technical email controls, 3) Training users to spot spearphishing, 4) Managing vulnerabilities well through patching and configuration, and 5) Verifying and locking down external-facing systems and limiting internet access points. The document provides support for these recommendations through statistics and examples from real-world cyber attacks and breaches.2016 - Cyber Security for the Public Sector
2016 - Cyber Security for the Public SectorScott Geye
Ěý
The document discusses cybersecurity topics including 2015-2016 breach reports, vulnerabilities, exploits, malware, cybercrime marketplaces, hacktivism, and cybersecurity resources. It provides an overview of recent cybersecurity trends, including a shift towards directly attacking applications and the monetization of malware. Breaches are shown to most commonly be caused by hacking and involve theft of personal data. The Texas Cybersecurity Framework and resources for local governments to improve cyber defenses are also summarized.NTXISSACSC2 - Top Ten Trends in TRM by Jon Murphy
NTXISSACSC2 - Top Ten Trends in TRM by Jon MurphyNorth Texas Chapter of the ISSA
Ěý
The document outlines the top ten trends in Technology Risk Management (TRM), highlighting the increasing sophistication of cyber threats and the importance of integrating security into organizational processes. It emphasizes the need for proactive measures, including risk assessments and incident response plans, while underscoring that TRM should be a key focus at the board level. Additionally, it provides actionable steps for organizations to enhance their TRM practices.Cyber Threat Intelligence
Cyber Threat IntelligencePrachi Mishra
Ěý
The document discusses cyber threat intelligence and collaborative threat intelligence. It provides an overview of malware trends, requirements for developing threat intelligence capabilities, and principles for managing threat intelligence proactively. The document advocates for a collaborative threat intelligence framework to enable preventative response by identifying and blocking known attackers across multiple organizations through automated and real-time threat information sharing. Standards and tools discussed include IODEF, CIF and how CIF can be used to gather, identify, respond to and mitigate threats based on indicators collected from various sources.Cyber threat intelligence ppt
Cyber threat intelligence pptKumar Gaurav
Ěý
Cyber threat intelligence (CTI) involves collecting, evaluating, and analyzing cyber threat information using expertise and all-source information to provide insight and understanding of complex cyber situations. CTI can include tactical, operational, and strategic intelligence about security events, indicators of compromise, malware behavior, threat actors, and mapping online threats to geopolitical events over short, medium, and long timeframes. Implementing CTI enables organizations to prepare for and respond to existing and unknown threats through evidence-based knowledge and actionable advice beyond just reactive defense measures.Cyber Security Beyond 2020 –
Will We Learn From Our Mistakes?
Cyber Security Beyond 2020 –
Will We Learn From Our Mistakes?Raffael Marty
Ěý
The document discusses the urgent need for a paradigm shift in cybersecurity to escape the persistent cat-and-mouse game between defense and attack. It emphasizes the importance of integrating security platforms, focusing on human behavior, and adapting to new attack surfaces driven by digital transformation. The document also highlights the challenges posed by insider threats, alert overload, and evolving technologies, advocating for a risk-based approach to enhance security effectiveness.A Strategy for Addressing Cyber Security Challenges
A Strategy for Addressing Cyber Security Challenges Cybersecurity Education and Research Centre
Ěý
The document discusses the growing challenges of cybersecurity faced by individuals, businesses, and governments, emphasizing the complexity of the threat landscape, including cyber crimes costing significant financial losses. It outlines strategies to address these challenges through education, research, policy development, and collaboration among various stakeholders to enhance cybersecurity readiness. The importance of building capacity, supporting cybersecurity education and research, and integrating security into existing curricula is highlighted as essential for a robust national response to cyber threats.Threat intelligence in security
Threat intelligence in securityOsama Ellahi
Ěý
Threat intelligence involves understanding and preparing for cyber threats targeting an organization, utilizing various tools, techniques, and frameworks to mitigate risks. Key steps include staying updated on new threats and sharing encountered malware with global response teams, such as CERT. The document discusses types of security incidents, including DDoS attacks, ransomware infections, and unauthorized data exposure.The Hacker Playbook: How to Think like a Cybercriminal to Reduce Risk
The Hacker Playbook: How to Think like a Cybercriminal to Reduce RiskBeyondTrust
Ěý
The document details Cqure Consulting's offerings, which include high-quality penetration testing, incident response, and extensive security training aimed at building a responsible security culture in organizations. It emphasizes the need for skilled cybersecurity professionals and outlines twelve critical skills for effective threat protection and incident response. Additionally, it highlights the risks associated with insider threats and external hacking, advocating for privileged access management and vulnerability management to mitigate these risks.Webinar cybersecurity presentation-6-2018 (final)
Webinar cybersecurity presentation-6-2018 (final)AT-NET Services, Inc. - Charleston Division
Ěý
This document provides an overview of cyber security threats for non-technical executives. It discusses who may target a company's data such as hackers, criminals, and terrorists. It outlines common methods of attack like phishing, ransomware, and malware. The document also considers what data is most valuable to an organization to assess potential damage from attacks. Finally, it recommends actions for protection including implementing security baselines, training, and balancing cyber risks with other business risks.Ponemon Report: Cyber Security Incident Response: Are we as prepared as we th...
Ponemon Report: Cyber Security Incident Response: Are we as prepared as we th...Lancope, Inc.
Ěý
The document summarizes the findings of a survey conducted by Ponemon Institute on the state of cyber incident response programs. Some key findings from the survey include: organizations are ill-prepared to respond to cyber threats, cybersecurity budgets dedicate a low percentage to incident response preparedness, and network audit trails are seen as the most effective tool for detecting security breaches. The document recommends that organizations build dedicated incident response teams, assess team readiness, use metrics to measure effectiveness, and foster information sharing.Cybersecurity: How to Use What We Already Know
Cybersecurity: How to Use What We Already Knowjxyz
Ěý
This document discusses the challenges of cybersecurity and how to leverage research for practical solutions in software security. It highlights the need for policy-agnostic programming and explores ways to motivate stakeholders to invest in security measures. Key recommendations include connecting researchers with industry, implementing technical solutions, and fostering a culture that prioritizes security.CYBERSECURITY - Best Practices,Concepts & Case Study (Mindmap)
CYBERSECURITY - Best Practices,Concepts & Case Study (Mindmap)WAJAHAT IQBAL
Ěý
The document outlines key practices, frameworks, and standards within the cybersecurity domain aimed at protecting various entities from global cyber threats. It details the cybersecurity lifecycle, common attack vectors, and tactics employed by cybercriminals, including a categorization of well-known cybersecurity risks and vulnerabilities. Additionally, it emphasizes the need for comprehensive security strategies and incident management processes to enhance organizational cybersecurity posture.Cyber Security for Non-Technical Executives (SC GMIS) Columbia, SC
Cyber Security for Non-Technical Executives (SC GMIS) Columbia, SCAT-NET Services, Inc. - Charleston Division
Ěý
This document outlines cyber security principles, roles, and risks for non-technical executives, focusing on understanding and managing cyber security threats. It emphasizes the importance of confidentiality, integrity, and availability while providing a roadmap for planning and responding to cyber incidents. Additionally, it discusses the NIST framework for managing cybersecurity-related risks, covering implementation phases, risk evaluation, and incident response strategies.Breaking down the cyber security framework closing critical it security gaps
Breaking down the cyber security framework closing critical it security gapsIBM Security
Ěý
The IBM and Deloitte joint webinar discusses key cybersecurity challenges, including critical IT security gaps and the cybersecurity framework. Key points include the rise in cyber threats, the impact of the U.S. President's executive order on information sharing and privacy, and the identification of critical infrastructure at risk. The presentation emphasizes the need for organizations to respond proactively to evolving threats while enhancing their security measures and cybersecurity frameworks.Cybersecurity Training
Cybersecurity TrainingWindstoneHealth
Ěý
This document provides an overview of cybersecurity training for Windstone Health Services employees in 2021. It defines cybersecurity and why it is important, discusses common cybersecurity threats like malware, phishing, and denial of service attacks. It also outlines responsibilities for both employees and the company, including maintaining secure passwords, updating software, and employing firewalls and encryption. The overall message is that cyberattacks are a serious risk and all entities must work together to protect systems, be wary of suspicious activities, and keep security protocols up to date.Career Guidance on Cybersecurity by Mohammed Adam
Career Guidance on Cybersecurity by Mohammed AdamMohammed Adam
Ěý
The document provides a comprehensive overview of career guidance in cybersecurity, including definitions, the demand for professionals, various fields and roles, and essential training resources. It discusses the importance of certifications, training initiatives for veterans, and networking opportunities, along with strategies for resume preparation in the cybersecurity job market. Overall, it serves as a resource for both beginners and experienced individuals looking to advance their careers in cybersecurity.eSentinel webinar with Netpluz & Straits Interactive on Cyber Security & PDPA...
eSentinel webinar with Netpluz & Straits Interactive on Cyber Security & PDPA...Netpluz Asia Pte Ltd
Ěý
- 360° Managed Cybersecurity is an integrated platform that provides comprehensive cybersecurity protection through features like attack prevention, threat detection, security assessments, and a security operations center.
- Small and medium enterprises are increasingly targeted by cyberattacks, with many lacking preparedness for risks associated with remote working.
- The platform addresses security challenges across multiple attack vectors and provides visibility through a single pane of glass with customizable policies, alerts, and monthly reporting.Challenges in implementating cyber security
Challenges in implementating cyber securityInderjeet Singh
Ěý
This document discusses several challenges in implementing cyber security including the information security model, risk management, and survivability. It outlines various opportunities for intrusion such as rapidly adopted networks and exploitable vulnerabilities. The document also discusses internal and external intruders as well as the information security model. Risk is defined and risk management processes are outlined including risk assessment. The concept of survivability and an approach using multiple layers of protection for critical assets is presented.Solving the Asset Management Challenge for Cybersecurity (It’s About Time)
Solving the Asset Management Challenge for Cybersecurity (It’s About Time)Enterprise Management Associates
Ěý
The document discusses the critical role of asset management in enhancing cybersecurity, highlighting ongoing challenges and specific use cases. It emphasizes the need for a comprehensive asset inventory and offers a simple approach for organizations to address coverage gaps and policy enforcement. The document includes insights on industry regulations, asset discovery, endpoint protection, and incident response while promoting a trial for the proposed solution.Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...
Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...BCM Institute
Ěý
The document discusses the significant cybersecurity challenges and financial impacts faced by enterprises in Southeast Asia due to malware and data breaches, amounting to $230 billion in 2014. It emphasizes the importance of a strong security culture starting from top management, risk assessment, and employing certified security personnel to strengthen cyber resilience. Additionally, it outlines frameworks such as the National Infocomm Competency Framework (NICF) and compliance with standards like DoD 8140 to enhance cybersecurity education and skill development.How COVID-19 Changed The Cyber Security Worldwide? — Cyberroot Risk Advisory
How COVID-19 Changed The Cyber Security Worldwide? — Cyberroot Risk AdvisoryCR Group
Ěý
The COVID-19 pandemic has drastically altered global cybersecurity, leading to a 63% increase in phishing, malware, and ransomware attacks as cybercriminals exploit the crisis. With the shift to remote work, companies and individuals face heightened vulnerabilities, necessitating robust cybersecurity measures, employee training, and strong network practices. Organizations must prioritize data protection and adapt to new threats while navigating both cybersecurity challenges and public health concerns.publication
publicationMary Clare Imbo
Ěý
This document reviews the impact of African traditional termite control methods on biodiversity conservation. It discusses how termites are an important part of African ecosystems but some species are also agricultural pests. Traditional control methods used by African communities include physical barriers and plant-based pesticides. These methods are considered more environmentally friendly than chemical pesticides. However, their effectiveness has not been scientifically proven. The review examines the benefits of traditional methods for biodiversity preservation compared to conventional chemical control.Clash royale startingRolaxWAR29
Ěý
Esta presentacion contiene algo de lo mas relevante sobre clash royale.
espero que les guste
gracias.More Related Content
What's hot (20)
NTXISSACSC2 - Top Ten Trends in TRM by Jon Murphy
NTXISSACSC2 - Top Ten Trends in TRM by Jon MurphyNorth Texas Chapter of the ISSA
Ěý
The document outlines the top ten trends in Technology Risk Management (TRM), highlighting the increasing sophistication of cyber threats and the importance of integrating security into organizational processes. It emphasizes the need for proactive measures, including risk assessments and incident response plans, while underscoring that TRM should be a key focus at the board level. Additionally, it provides actionable steps for organizations to enhance their TRM practices.Cyber Threat Intelligence
Cyber Threat IntelligencePrachi Mishra
Ěý
The document discusses cyber threat intelligence and collaborative threat intelligence. It provides an overview of malware trends, requirements for developing threat intelligence capabilities, and principles for managing threat intelligence proactively. The document advocates for a collaborative threat intelligence framework to enable preventative response by identifying and blocking known attackers across multiple organizations through automated and real-time threat information sharing. Standards and tools discussed include IODEF, CIF and how CIF can be used to gather, identify, respond to and mitigate threats based on indicators collected from various sources.Cyber threat intelligence ppt
Cyber threat intelligence pptKumar Gaurav
Ěý
Cyber threat intelligence (CTI) involves collecting, evaluating, and analyzing cyber threat information using expertise and all-source information to provide insight and understanding of complex cyber situations. CTI can include tactical, operational, and strategic intelligence about security events, indicators of compromise, malware behavior, threat actors, and mapping online threats to geopolitical events over short, medium, and long timeframes. Implementing CTI enables organizations to prepare for and respond to existing and unknown threats through evidence-based knowledge and actionable advice beyond just reactive defense measures.Cyber Security Beyond 2020 –
Will We Learn From Our Mistakes?
Cyber Security Beyond 2020 –
Will We Learn From Our Mistakes?Raffael Marty
Ěý
The document discusses the urgent need for a paradigm shift in cybersecurity to escape the persistent cat-and-mouse game between defense and attack. It emphasizes the importance of integrating security platforms, focusing on human behavior, and adapting to new attack surfaces driven by digital transformation. The document also highlights the challenges posed by insider threats, alert overload, and evolving technologies, advocating for a risk-based approach to enhance security effectiveness.A Strategy for Addressing Cyber Security Challenges
A Strategy for Addressing Cyber Security Challenges Cybersecurity Education and Research Centre
Ěý
The document discusses the growing challenges of cybersecurity faced by individuals, businesses, and governments, emphasizing the complexity of the threat landscape, including cyber crimes costing significant financial losses. It outlines strategies to address these challenges through education, research, policy development, and collaboration among various stakeholders to enhance cybersecurity readiness. The importance of building capacity, supporting cybersecurity education and research, and integrating security into existing curricula is highlighted as essential for a robust national response to cyber threats.Threat intelligence in security
Threat intelligence in securityOsama Ellahi
Ěý
Threat intelligence involves understanding and preparing for cyber threats targeting an organization, utilizing various tools, techniques, and frameworks to mitigate risks. Key steps include staying updated on new threats and sharing encountered malware with global response teams, such as CERT. The document discusses types of security incidents, including DDoS attacks, ransomware infections, and unauthorized data exposure.The Hacker Playbook: How to Think like a Cybercriminal to Reduce Risk
The Hacker Playbook: How to Think like a Cybercriminal to Reduce RiskBeyondTrust
Ěý
The document details Cqure Consulting's offerings, which include high-quality penetration testing, incident response, and extensive security training aimed at building a responsible security culture in organizations. It emphasizes the need for skilled cybersecurity professionals and outlines twelve critical skills for effective threat protection and incident response. Additionally, it highlights the risks associated with insider threats and external hacking, advocating for privileged access management and vulnerability management to mitigate these risks.Webinar cybersecurity presentation-6-2018 (final)
Webinar cybersecurity presentation-6-2018 (final)AT-NET Services, Inc. - Charleston Division
Ěý
This document provides an overview of cyber security threats for non-technical executives. It discusses who may target a company's data such as hackers, criminals, and terrorists. It outlines common methods of attack like phishing, ransomware, and malware. The document also considers what data is most valuable to an organization to assess potential damage from attacks. Finally, it recommends actions for protection including implementing security baselines, training, and balancing cyber risks with other business risks.Ponemon Report: Cyber Security Incident Response: Are we as prepared as we th...
Ponemon Report: Cyber Security Incident Response: Are we as prepared as we th...Lancope, Inc.
Ěý
The document summarizes the findings of a survey conducted by Ponemon Institute on the state of cyber incident response programs. Some key findings from the survey include: organizations are ill-prepared to respond to cyber threats, cybersecurity budgets dedicate a low percentage to incident response preparedness, and network audit trails are seen as the most effective tool for detecting security breaches. The document recommends that organizations build dedicated incident response teams, assess team readiness, use metrics to measure effectiveness, and foster information sharing.Cybersecurity: How to Use What We Already Know
Cybersecurity: How to Use What We Already Knowjxyz
Ěý
This document discusses the challenges of cybersecurity and how to leverage research for practical solutions in software security. It highlights the need for policy-agnostic programming and explores ways to motivate stakeholders to invest in security measures. Key recommendations include connecting researchers with industry, implementing technical solutions, and fostering a culture that prioritizes security.CYBERSECURITY - Best Practices,Concepts & Case Study (Mindmap)
CYBERSECURITY - Best Practices,Concepts & Case Study (Mindmap)WAJAHAT IQBAL
Ěý
The document outlines key practices, frameworks, and standards within the cybersecurity domain aimed at protecting various entities from global cyber threats. It details the cybersecurity lifecycle, common attack vectors, and tactics employed by cybercriminals, including a categorization of well-known cybersecurity risks and vulnerabilities. Additionally, it emphasizes the need for comprehensive security strategies and incident management processes to enhance organizational cybersecurity posture.Cyber Security for Non-Technical Executives (SC GMIS) Columbia, SC
Cyber Security for Non-Technical Executives (SC GMIS) Columbia, SCAT-NET Services, Inc. - Charleston Division
Ěý
This document outlines cyber security principles, roles, and risks for non-technical executives, focusing on understanding and managing cyber security threats. It emphasizes the importance of confidentiality, integrity, and availability while providing a roadmap for planning and responding to cyber incidents. Additionally, it discusses the NIST framework for managing cybersecurity-related risks, covering implementation phases, risk evaluation, and incident response strategies.Breaking down the cyber security framework closing critical it security gaps
Breaking down the cyber security framework closing critical it security gapsIBM Security
Ěý
The IBM and Deloitte joint webinar discusses key cybersecurity challenges, including critical IT security gaps and the cybersecurity framework. Key points include the rise in cyber threats, the impact of the U.S. President's executive order on information sharing and privacy, and the identification of critical infrastructure at risk. The presentation emphasizes the need for organizations to respond proactively to evolving threats while enhancing their security measures and cybersecurity frameworks.Cybersecurity Training
Cybersecurity TrainingWindstoneHealth
Ěý
This document provides an overview of cybersecurity training for Windstone Health Services employees in 2021. It defines cybersecurity and why it is important, discusses common cybersecurity threats like malware, phishing, and denial of service attacks. It also outlines responsibilities for both employees and the company, including maintaining secure passwords, updating software, and employing firewalls and encryption. The overall message is that cyberattacks are a serious risk and all entities must work together to protect systems, be wary of suspicious activities, and keep security protocols up to date.Career Guidance on Cybersecurity by Mohammed Adam
Career Guidance on Cybersecurity by Mohammed AdamMohammed Adam
Ěý
The document provides a comprehensive overview of career guidance in cybersecurity, including definitions, the demand for professionals, various fields and roles, and essential training resources. It discusses the importance of certifications, training initiatives for veterans, and networking opportunities, along with strategies for resume preparation in the cybersecurity job market. Overall, it serves as a resource for both beginners and experienced individuals looking to advance their careers in cybersecurity.eSentinel webinar with Netpluz & Straits Interactive on Cyber Security & PDPA...
eSentinel webinar with Netpluz & Straits Interactive on Cyber Security & PDPA...Netpluz Asia Pte Ltd
Ěý
- 360° Managed Cybersecurity is an integrated platform that provides comprehensive cybersecurity protection through features like attack prevention, threat detection, security assessments, and a security operations center.
- Small and medium enterprises are increasingly targeted by cyberattacks, with many lacking preparedness for risks associated with remote working.
- The platform addresses security challenges across multiple attack vectors and provides visibility through a single pane of glass with customizable policies, alerts, and monthly reporting.Challenges in implementating cyber security
Challenges in implementating cyber securityInderjeet Singh
Ěý
This document discusses several challenges in implementing cyber security including the information security model, risk management, and survivability. It outlines various opportunities for intrusion such as rapidly adopted networks and exploitable vulnerabilities. The document also discusses internal and external intruders as well as the information security model. Risk is defined and risk management processes are outlined including risk assessment. The concept of survivability and an approach using multiple layers of protection for critical assets is presented.Solving the Asset Management Challenge for Cybersecurity (It’s About Time)
Solving the Asset Management Challenge for Cybersecurity (It’s About Time)Enterprise Management Associates
Ěý
The document discusses the critical role of asset management in enhancing cybersecurity, highlighting ongoing challenges and specific use cases. It emphasizes the need for a comprehensive asset inventory and offers a simple approach for organizations to address coverage gaps and policy enforcement. The document includes insights on industry regulations, asset discovery, endpoint protection, and incident response while promoting a trial for the proposed solution.Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...
Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...BCM Institute
Ěý
The document discusses the significant cybersecurity challenges and financial impacts faced by enterprises in Southeast Asia due to malware and data breaches, amounting to $230 billion in 2014. It emphasizes the importance of a strong security culture starting from top management, risk assessment, and employing certified security personnel to strengthen cyber resilience. Additionally, it outlines frameworks such as the National Infocomm Competency Framework (NICF) and compliance with standards like DoD 8140 to enhance cybersecurity education and skill development.How COVID-19 Changed The Cyber Security Worldwide? — Cyberroot Risk Advisory
How COVID-19 Changed The Cyber Security Worldwide? — Cyberroot Risk AdvisoryCR Group
Ěý
The COVID-19 pandemic has drastically altered global cybersecurity, leading to a 63% increase in phishing, malware, and ransomware attacks as cybercriminals exploit the crisis. With the shift to remote work, companies and individuals face heightened vulnerabilities, necessitating robust cybersecurity measures, employee training, and strong network practices. Organizations must prioritize data protection and adapt to new threats while navigating both cybersecurity challenges and public health concerns.Cyber Security for Non-Technical Executives (SC GMIS) Columbia, SC
Cyber Security for Non-Technical Executives (SC GMIS) Columbia, SCAT-NET Services, Inc. - Charleston Division
Ěý
eSentinel webinar with Netpluz & Straits Interactive on Cyber Security & PDPA...
eSentinel webinar with Netpluz & Straits Interactive on Cyber Security & PDPA...Netpluz Asia Pte Ltd
Ěý
Solving the Asset Management Challenge for Cybersecurity (It’s About Time)
Solving the Asset Management Challenge for Cybersecurity (It’s About Time)Enterprise Management Associates
Ěý
Viewers also liked (10)
publication
publicationMary Clare Imbo
Ěý
This document reviews the impact of African traditional termite control methods on biodiversity conservation. It discusses how termites are an important part of African ecosystems but some species are also agricultural pests. Traditional control methods used by African communities include physical barriers and plant-based pesticides. These methods are considered more environmentally friendly than chemical pesticides. However, their effectiveness has not been scientifically proven. The review examines the benefits of traditional methods for biodiversity preservation compared to conventional chemical control.Clash royale startingRolaxWAR29
Ěý
Esta presentacion contiene algo de lo mas relevante sobre clash royale.
espero que les guste
gracias.Applied Project Final Defense Final
Applied Project Final Defense FinalJacob Dicus
Ěý
This document discusses a research project exploring the role of Graduate Assistants (GAs) at the Kimmel Student Involvement Center at Southern Illinois University Edwardsville. The research aims to address issues around leadership succession and knowledge sharing when GAs turnover regularly. A literature review covers concepts of organizational identification, how groups develop identities, and bona fide group theory. The research methodology will involve qualitative interviews with GAs, students, and faculty to understand how GAs influence groups and can improve knowledge transfer during leadership changes. The goal is to create an operations manual to foster consistency during GA transitions.CSIRT_16_Jun
CSIRT_16_JunCandan BOLUKBAS
Ěý
As attacks have become more sophisticated, the need for Computer Security Incident Response Teams (CSIRTs) has grown to address challenges like botnets, distributed denial-of-service (DDoS) attacks, insider threats, and advanced persistent threats (APTs). The presentation discusses best practices for creating a CSIRT, including obtaining management support, determining a strategic plan, designing a vision, implementation, and evaluating effectiveness. It also covers Security Operations Centers (SOCs), their mission to prevent, monitor, detect, respond to, and report on cybersecurity incidents, and best practices for establishing an SOC.±Ę°ů±đ˛ő±đ˛ÔłŮ˛ął¦ľ±Ăł˛Ô1euniceortiz1429
Ěý
El documento resume las caracterĂsticas y desafĂos de la vida de los niños con necesidades especiales, en particular del sĂndrome de Down. Los niños con necesidades especiales enfrentan más obstáculos en actividades cotidianas y necesitan apoyo de cuidadores. Aquellos con sĂndrome de Down presentan rasgos fĂsicos distintivos y problemas de salud comunes como defectos cardĂacos y auditivos. No existe cura para el sĂndrome de Down.EvasionTechniques
EvasionTechniquesCandan BOLUKBAS
Ěý
This document discusses various techniques for evading antivirus, firewalls, and intrusion prevention systems (IPS). It begins with techniques for antivirus evasion using tools like msfvenom, veil-evasion, shellter, and unicorn to obfuscate payloads. Next it discusses firewall and IPS evasion techniques like stage encoding/encryption, zombie scanning, tunneling over protocols like ICMP, DNS, and using a custom Tor configuration. The document provides examples and links to demonstrate these evasion techniques.Dependency Breaking Techniques
Dependency Breaking Techniqueshyun soomyung
Ěý
The document discusses 24 dependency breaking techniques for testing legacy code. Some key techniques include: adapt parameter to break dependencies on parameter classes; break out method object to separate logic into new classes; extract and override methods, factories, and getters to inject test logic; introduce instance delegators and static setters to test static methods; and subclass and override methods to break dependencies in object-oriented languages. The techniques aim to separate dependencies but may reduce readability and introduce errors if misused. Legacy code refactoring is challenging, so imperfect techniques are better than no alternatives.Chapt7 slides
Chapt7 slidesEngr Razaque
Ěý
Resource leveling is a process where the project manager schedules resources to activities to accomplish work within scheduled start and finish dates. There are three approaches to level resources: utilizing slack, shifting the project finish date, or smoothing. A work package describes tasks for an activity and is assigned to a work package manager responsible for on-time completion.Scalable Web Architecture and Distributed Systems
Scalable Web Architecture and Distributed Systemshyun soomyung
Ěý
Scalable web architectures distribute resources across multiple servers to improve availability, performance, reliability, and scalability. Key principles for designing scalable systems include availability, performance, reliability, scalability, manageability, and cost. These principles sometimes conflict and require tradeoffs. To improve scalability, services can be split and data distributed across partitions or shards. Caches, proxies, indexes, load balancers, and queues help optimize data access and manage asynchronous operations in distributed systems.Linux 4.x Tracing: Performance Analysis with bcc/BPF
Linux 4.x Tracing: Performance Analysis with bcc/BPFBrendan Gregg
Ěý
The document discusses advanced Linux tracing techniques and tools using BPF (Berkeley Packet Filter) and its enhanced versions (eBPF) for performance analysis. It offers insights into tracing methods, the evolution of BPF, key tools included in the BCC (BPF Compiler Collection), and various command examples for performance diagnostics. The document emphasizes the importance of upgrading to newer Linux versions to leverage these tracing capabilities effectively.Ad
Similar to WhyNormShield (20)
NormShield Cyber Threat & Vulnerability Orchestration Overview
NormShield Cyber Threat & Vulnerability Orchestration OverviewNormShield, Inc.
Ěý
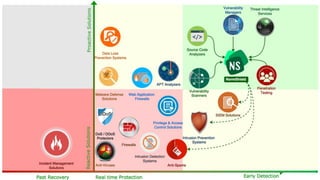
The document discusses the Normshield cloud platform, which offers automated cyber security operations and reporting to help organizations manage cyber threats and vulnerabilities effectively. It emphasizes the importance of continuous monitoring, prioritized risk assessment, and eliminating false positives to improve response times and security. Furthermore, the platform includes tools for vulnerability management, threat intelligence, and enhanced executive visibility through its risk scorecard feature.NormShield 2018 Cyber Security Risk Brief
NormShield 2018 Cyber Security Risk BriefNormShield
Ěý
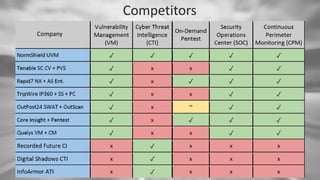
The document presents a comprehensive cyber risk assessment scoring and insights for organizations across multiple industries, highlighting the need for improved cyber security measures. It categorizes organizations' grades across five key areas: credential management, patch management, IP reputation, SSL strength, and DNS security, with most organizations receiving a C or lower, indicating urgent action is required. The document also provides actionable steps to enhance security in each category and emphasizes that beginners can exploit many vulnerabilities.HOW TO MEASURE WHAT HACKERS KNOW ABOUT YOU
HOW TO MEASURE WHAT HACKERS KNOW ABOUT YOUNormShield
Ěý
The document discusses the need for companies to measure their cyber security posture using comprehensive methods rather than relying solely on traditional penetration tests. It highlights the importance of independent security ratings, like those provided by Normshield, to offer an objective assessment of vulnerabilities, thereby helping organizations prioritize and improve their defenses. By utilizing open-source intelligence and monitoring tools, companies can gain insights into their cyber risks and enhance communication between technical teams and executives.Be More Secure than your Competition: MePush Cyber Security for Small Business
Be More Secure than your Competition: MePush Cyber Security for Small BusinessArt Ocain
Ěý
The document provides guidance on improving cybersecurity through basic training and awareness. It discusses how people are often the biggest vulnerability and outlines common social engineering tactics like playing on emotions, creating a sense of urgency, and using hyperlinks or attachments in emails. It recommends continuous education and emphasizes that antivirus alone is not sufficient, and that email filtering and training are important defenses against phishing attacks. Additional resources are provided to help test for phishing vulnerabilities and check if email addresses have been involved in data breaches. Physical security controls and separating financial duties are also recommended to reduce fraud risks.2017 Cyber Risk Grades by Industry: Normshield Executive Presentation
2017 Cyber Risk Grades by Industry: Normshield Executive PresentationNormShield, Inc.
Ěý
The 2017 Cyber Security Risk Brief reveals that 217 organizations averaged a C- grade in cybersecurity across five categories, highlighting urgent vulnerabilities in credential management, vulnerabilities, IP/domain reputation, SSL strength, and DNS security. Nearly 75% of users employ duplicate passwords, and over 10% of respondents had critical issues, mainly due to outdated web servers and applications. Recommendations include regular password changes, continuous monitoring of cyber data leaks, and implementing strong security measures to protect against both novice and experienced hackers.Vulnerability Management: What You Need to Know to Prioritize Risk
Vulnerability Management: What You Need to Know to Prioritize RiskAlienVault
Ěý
The document discusses the importance of vulnerability management, highlighting trends in threat detection and the challenges of patching vulnerabilities. It emphasizes a proactive approach that includes regular network assessments, the use of threat intelligence, and continuous monitoring. Recommendations include thinking like an attacker, unifying security controls, and recognizing that vulnerability management is an ongoing process.Trending it security threats in the public sector
Trending it security threats in the public sectorCore Security
Ěý
The document discusses current cybersecurity challenges in the public sector, emphasizing issues such as network vulnerabilities, password theft, and the overload faced by security teams. It highlights the importance of implementing proactive measures, including penetration testing and vulnerability management, while embracing new technologies and resources. The need for a shift towards an intelligent defense model is underscored to better address the increasing cybersecurity threats.Steel Point Solutions IAS Track 3 "Sustaining a Cyber Workforce" by L.T. Hawkins
Steel Point Solutions IAS Track 3 "Sustaining a Cyber Workforce" by L.T. Hawkinslthawkins
Ěý
The document outlines the importance of sustaining a cyber workforce for small business government contractors, presented by Likia T. Hawkins. It emphasizes the increasing threats and challenges faced due to cybercrime, which costs businesses billions annually, and highlights the necessity for a well-educated and trained workforce, as well as effective cybersecurity strategies. Resources, practices, and cultural elements are provided to help organizations integrate cybersecurity into their operations, ensuring the protection of sensitive data and compliance with regulations.Symantec cyber-resilience
Symantec cyber-resilienceSymantec
Ěý
The document discusses the need for organizations to adopt a strategy of cyber resilience in response to the growing threats posed by the digital environment. It emphasizes that while complete risk elimination is impossible, cyber resilience involves managing security through a multi-layered approach across people, processes, and technology. This can help organizations better prepare for, detect, respond to, and recover from cyber attacks in order to minimize potential damage and disruption. Symantec is presented as uniquely qualified to help organizations achieve cyber resilience through its security solutions, intelligence capabilities, scale, expertise and infrastructure.Netwealth educational webinar: Peace of mind in a digital world
Netwealth educational webinar: Peace of mind in a digital worldnetwealthInvest
Ěý
The document discusses cyber security issues for financial advisors. It notes that 45% of advisors experienced a cyber incident in the past year, which on average costs $275,000 per incident. The document provides definitions and explanations of common cyber threats like malware, ransomware, social engineering, and botnets. It also defines common cyber security terms and controls. The document shares results of a cyber security survey of financial advisors which found that over half do not feel prepared for a cyber attack and most lack confidence in staff security practices. It emphasizes the new mandatory data breach notification laws and educating clients on security best practices.Rethinking Cyber-Security: 7 Key Strategies for the Challenges that Lie Ahead
Rethinking Cyber-Security: 7 Key Strategies for the Challenges that Lie AheadOpenDNS
Ěý
The document outlines the evolving threat landscape in cybersecurity, emphasizing the need for a holistic approach that goes beyond traditional preventative techniques. It highlights the ineffectiveness of current security measures against sophisticated attacks and urges organizations to adopt a multi-tiered strategy that includes risk analysis and proactive education. Key recommendations include improving coverage and visibility, quick detection and containment, and aligning security investments with organizational vulnerabilities.Best practices for_implementing_security_awareness_training
Best practices for_implementing_security_awareness_trainingwardell henley
Ěý
- Security professionals are most concerned about data breaches, phishing, spearphishing, and ransomware attacks. These threats can be addressed through effective security awareness training.
- The vast majority of surveyed organizations had experienced security incidents like phishing attacks delivering malware, targeted email attacks, or data breaches in the past year.
- Over 90% of organizations report that phishing and spearphishing attempts reaching end users have increased or stayed the same over the past 12 months, indicating ongoing threats.VIPRE --Responding to Cyberattacks
VIPRE --Responding to CyberattacksAbhishek Sood
Ěý
- The document summarizes the findings of a survey that found many organizations are ill-prepared to respond to cyberattacks due to a lack of incident response plans, reliance on manual processes, infrequent patching, and other issues.
- While IT managers understand cybersecurity risks, over half do not have an incident response plan and 55% rely on manual processes to respond to attacks. Only a quarter apply patches weekly.
- Managed service providers (MSPs) generally have stronger security practices than in-house IT managers, including more frequent patching, remote access to security tools, and documented response plans. However, MSPs also fear business shutdown from an attack.
- The document recommends organizations prioritize patching, investCybersecurity 101 final
Cybersecurity 101 finalKemper Brown, Jr.
Ěý
The document outlines essential cybersecurity measures for medical practices facing an evolving threat landscape, emphasizing the importance of annual HIPAA security assessments, security awareness training, and robust data backup solutions. It highlights the prevalence of cybersecurity threats, particularly the risks posed by employee actions, such as falling for phishing attacks. In the event of a breach, it provides a structured response plan, including documentation, contacting IT professionals, and adhering to HIPAA breach notification requirements.Prevent Data Breach for your company with Vulnerability Assessment
Prevent Data Breach for your company with Vulnerability Assessment Cyber Octet Private Limited
Ěý
The document outlines the process of vulnerability assessment, which identifies and prioritizes system vulnerabilities to protect against unauthorized access and data breaches. It details various types of assessments used in different sectors, tools for conducting these assessments, and highlights the services offered by Cyber Octet, a cybersecurity provider in Ahmedabad. Additionally, it provides contact information for inquiries regarding their services.Cybersecurity: Take Back Control
Cybersecurity: Take Back ControlICF
Ěý
Organizations must enhance their cybersecurity by implementing vigilant network monitoring and continuous vulnerability assessments to understand their network's security posture. Key strategies include using a security information and event management system, preparing for incident response, and knowing valuable information at risk. Additionally, engaging professional support and sharing forensics with law enforcement are essential steps to mitigate the damage from potential cyberattacks.Scot Secure 2015
Scot Secure 2015Ray Bugg
Ěý
The document discusses the evolving landscape of cybersecurity threats and outlines key challenges such as cost, operational efficiency, and the emergence of advanced persistent threats. It emphasizes the importance of a structured approach to mitigation, detection, and remediation of security threats, with a focus on collaboration among stakeholders and continuous monitoring. Additionally, it highlights the significance of protecting networks and developing cyber resilience in organizations through strategic planning and risk management.Let's TOC: Navigate the Cybersecurity Conversation with Dominique Singer
Let's TOC: Navigate the Cybersecurity Conversation with Dominique SingerSaraPia5
Ěý
The document discusses the challenges of cybersecurity, emphasizing the need for a strong risk management framework. It outlines essential steps for identifying and mitigating risks, highlights discrepancies in organizational confidence in cyber resilience, and addresses common mistakes in risk management. Overall, it calls for improved alignment between security measures and business objectives to enhance cybersecurity effectiveness.Cyber threat forecast 2018..
Cyber threat forecast 2018..Bolaji James Bankole CCSS,CEH,MCSA,MCSE,MCP,CCNA,
Ěý
This document provides a cyber threat forecast for 2018. It discusses several types of cyber attacks that are expected to increase in 2018, including ransomware attacks, mobile app attacks, network-based attacks on hospitals, identity theft, proof of concept attacks targeting medical devices, attacks on cryptocurrencies, cyber espionage by countries like Russia and North Korea, attacks on cloud infrastructure, and cyber bullying. It also mentions the enforcement of new GDPR regulations in Europe and increased international collaboration between cybercrime fighters. The purpose is to educate organizations on cybersecurity risks and the need to implement effective cyber resilience plans.CHIME LEAD Fourm Houston - "Creating an Effective Cyber Security Strategy: Ke...
CHIME LEAD Fourm Houston - "Creating an Effective Cyber Security Strategy: Ke...Health IT Conference – iHT2
Ěý
The document outlines a forum on creating effective cybersecurity strategies, discussing key attributes and challenges faced by medical center hospital systems. It highlights the importance of regular security audits, managing external and internal access, and the need for ongoing education and compliance to mitigate cyber risks. Case studies from two health networks illustrate the development of robust security measures and the evolution of their cybersecurity programs.CHIME LEAD Fourm Houston - "Creating an Effective Cyber Security Strategy: Ke...
CHIME LEAD Fourm Houston - "Creating an Effective Cyber Security Strategy: Ke...Health IT Conference – iHT2
Ěý
Ad
WhyNormShield
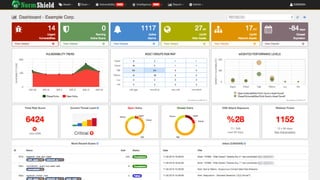
- 1. NormShield Unified Vulnerability Management & Cyber Threat Intelligence
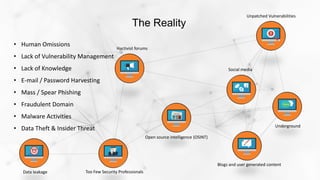
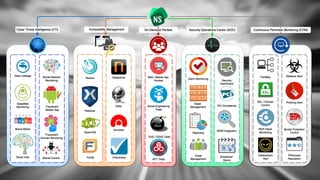
- 3. Open source intelligence (OSINT) Social media Unpatched Vulnerabilities Blogs and user generated content Hactivist forums Too Few Security Professionals Underground Data leakage • Human Omissions • Lack of Vulnerability Management • Lack of Knowledge • E-mail / Password Harvesting • Mass / Spear Phishing • Fraudulent Domain • Malware Activities • Data Theft & Insider Threat The Reality
- 4. 13,073 Vulnerabilities published last year 38%Believes their organization is prepared for a sophisticated cyber attack. 0.1% Ratio of cyber security professionals over company employees 91%Annual increase in job postings for cyber security professionals Is Being Safe Easy? Source: http://www.isaca.org/Knowledge-Center/Blog/Lists/Posts/Post.aspx?ID=503
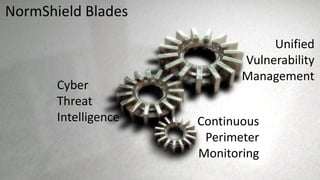
- 5. a new approach to Cyber Security NormShield 80% Automated Technology, 20% Human Intelligence Offensive & Defensive Unified Vulnerability Management 360° Continuous Security Monitoring
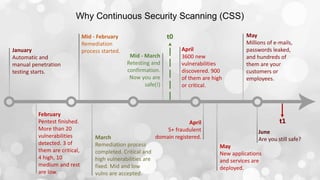
- 6. Why Continuous Security Scanning (CSS) January Automatic and manual penetration testing starts. February Pentest finished. More than 20 vulnerabilities detected. 3 of them are critical, 4 high, 10 medium and rest are low. March Remediation process completed. Critical and high vulnerabilities are fixed. Mid and low vulns are accepted. Mid - March Retesting and confirmation. Now you are safe(!) April 3600 new vulnerabilities discovered. 900 of them are high or critical. April 5+ fraudulent domain registered. May Millions of e-mails, passwords leaked, and hundreds of them are your customers or employees. May New applications and services are deployed. June Are you still safe? t0 t1 Mid - February Remediation process started.
