About rootkit
- 2. 22000-00-00 Contents Classification of ROOTKITs Type II ROOTKITs Type III ROOTKITs Next Generation ROOTKITs
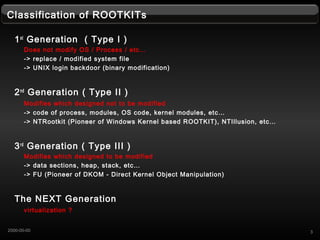
- 3. Classification of ROOTKITs 1st Generation ( Type I ) Does not modify OS / Process / etcˇ -> replace / modified system file -> UNIX login backdoor (binary modification) 2nd Generation ( Type II ) Modifies which designed not to be modified -> code of process, modules, OS code, kernel modules, etcˇ -> NTRootkit (Pioneer of Windows Kernel based ROOTKIT), NTIllusion, etcˇ 3rd Generation ( Type III ) Modifies which designed to be modified -> data sections, heap, stack, etcˇ -> FU (Pioneer of DKOM - Direct Kernel Object Manipulation) The NEXT Generation virtualization ? 32000-00-00
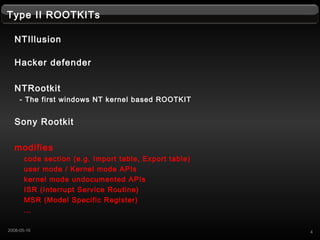
- 4. Type II ROOTKITs NTIllusion Hacker defender NTRootkit - The first windows NT kernel based ROOTKIT Sony Rootkit modifies code section (e.g. Import table, Export table) user mode / Kernel mode APIs kernel mode undocumented APIs ISR (Interrupt Service Routine) MSR (Model Specific Register) ˇ 42008-05-16
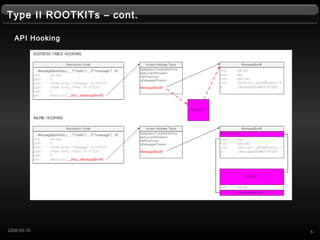
- 5. Type II ROOTKITs ¨C cont. API Hooking 52008-05-16
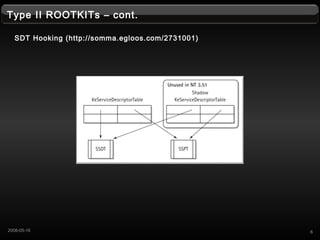
- 6. Type II ROOTKITs ¨C cont. SDT Hooking (http://somma.egloos.com/2731001) 62008-05-16
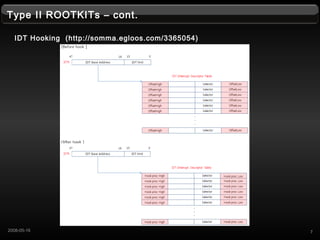
- 7. Type II ROOTKITs ¨C cont. IDT Hooking (http://somma.egloos.com/3365054) 72008-05-16
- 8. Type II ROOTKITs ¨C cont. DEMO - API Hooking (Ring 3) (CheatEngine) - Code Injection (Ring 3) (WinMine.exe hacking) - SDT hooking (Ring 0) (FxLoader / bkdp.sys) - IDT hooking (Ring 0) (SDFP ¨C app.exe / template.sys ¨C real machine) 82008-05-16
- 9. Type III ROOTKITs FU - The first ROOTKIT introduce DKOM (Direct Kernel Object Manipulation) He4Hook - RAW IRP hooking on File system driver PHIDE2 Layered driver (Filter driver) modifies data sections IRP handlers kernel objects that allocated and managed dynamically ˇ 92008-05-16
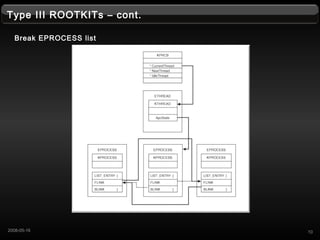
- 10. Type III ROOTKITs ¨C cont. Break EPROCESS list 102008-05-16
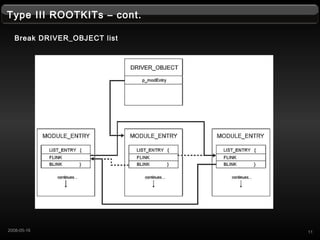
- 11. Type III ROOTKITs ¨C cont. Break DRIVER_OBJECT list 112008-05-16
- 12. Type III ROOTKITs ¨C cont. DEMO - FU rootkit - jeng_2 SDT hook & DKOM example 122008-05-16
- 13. Fighting ROOTKITs Check IAT (Import Address Table) Check inline hooks Check System Service Dispatch Table (ntoskrnl.exe) Check Shadow table (win32k.sys) Check DriverˇŻs IRP handler Check MSR ( MSR_SYSENTER ) ˇ how ? ECD (Explicit Compromise Detection) Cross View Based Detection use DKOM to find out ROOTKITs - dump PspCidTable - trace OS Scheduler data base, etcˇ Virtual Machine Monitor (http://northsecuritylabs.com/products.aspx ) 132008-05-16
- 14. Fighting ROOTKITs ¨C cont. DEMO - API Hook detection and API Hook removal hook_shield PlgnPETest.dll - Finding process FU hided by DKOM technique dump PspCidTable 142008-05-16
- 15. Next Generation ROOTKITs DEMO - Hypervisor based rootkit 152008-05-16