Safeguarding artifact integrity in your Software Supply Chain
0 likes57 views
The document discusses safeguarding artifact integrity within the software supply chain, highlighting vulnerabilities such as compromised source control and bad code injection. It outlines Google's initiatives, including the Open Source Security Foundation and the SLSA framework, to enhance security and integrity in the software supply chain. Key technologies and practices for building secure software artifacts on Google Cloud are also described, emphasizing automated processes and security policies.
1 of 15
Download to read offline









Ad
Recommended
Safeguarding Container Supply Chain - Anshul Patel
Safeguarding Container Supply Chain - Anshul PatelAnshul Patel
╠²
The document outlines a meetup focusing on safeguarding the software supply chain, led by Anshul Patel, a cloud consultant with extensive experience in cloud infrastructure. Key topics include the definition of software supply chain, potential threats, the Software Supply Chain Levels for Software Artifacts (SLSA), and the importance of a Software Bill of Materials (SBOM) for risk management and compliance. It emphasizes the collaboration between Google and the Open Source Security Foundation to establish trust and integrity in the software supply chain.ISACA SV Chapter: Securing Software Supply Chains
ISACA SV Chapter: Securing Software Supply ChainsJim Bugwadia
╠²
The document discusses the importance of securing software supply chains, highlighting the evolution from monolithic applications to modern, highly automated CI/CD environments that face significant security threats. It introduces the SLSA (Supply Chain Levels for Software Artifacts) framework, which outlines different levels of security and compliance, emphasizing the need for provenance and verification in software artifacts. Various OSS tools like Sigstore, In-Toto, and Kyverno are presented as solutions for establishing robust supply chain security practices.Tracy Miranda_DevOps Loop, May 2022.pdf
Tracy Miranda_DevOps Loop, May 2022.pdfVMware Tanzu
╠²
This document proposes a blueprint for securing open source software supply chains. It discusses how software supply chain attacks have increased significantly and open source software is now critical global infrastructure. It recommends following the Supply chain Levels for Software Artifacts (SLSA) framework as an industry standard. SLSA involves documenting the supply chain, generating authenticated provenance for builds, using signatures to prevent tampering, and meeting standards to guarantee auditability. It also recommends using Sigstore for code signing to verify the integrity of software and provide transparency into its origins and changes. The blueprint calls for securing open source supply chains by evaluating projects using SLSA, taking incremental steps to improve, implementing code signing and software bills of materials, and getting help from the openRoom 3 - 2 - Trß║¦n Tuß║źn Anh - Defending Software Supply Chain Security in Bank...
Room 3 - 2 - Trß║¦n Tuß║źn Anh - Defending Software Supply Chain Security in Bank...Vietnam Open Infrastructure User Group
╠²
The document discusses software supply chain security in regulated environments, specifically in banking, led by Tuan Anh Tran from VPBank. It covers key concepts like software integrity, code signing, software bill of materials (SBOM), and the SLSA framework for ensuring security and provenance in software artifacts. It also highlights practical implementation strategies and tools used to enhance security and integrity in the software development process.Oh The Places You'll Sign.pdf
Oh The Places You'll Sign.pdfLibbySchulze
╠²
This document discusses Sigstore, a new standard for signing, verifying, and protecting software. It provides three key pieces - Cosign for signing things, Fulcio for signing with short-lived certificates, and Rekor for verification and monitoring. Sigstore allows signing of software artifacts, documents like SBOMs and attestations, and git commits. Attestations provide signed statements about software, and Sigstore ensures their integrity. Sigstore supports achieving different levels in the SLSA framework for supply chain security. It also aligns with frameworks from NIST and CIS. Tools like Gitsign allow "keyless" signing of git commits to meet requirements for verified history and two-person review.apidays Australia 2023 - Building Trust Brick by Brick, Dasith Wijesiriwarden...
apidays Australia 2023 - Building Trust Brick by Brick, Dasith Wijesiriwarden...apidays
╠²
The document presents insights from a presentation on modern secure supply chain tools, focusing on threats and workflows within software supply chains. It discusses both consumer and producer-focused tools, emphasizing the importance of transparency, security, and compliance, alongside examples of effective practices such as continuous vulnerability scanning and admission control. Various resources and tools related to software supply chains, like SBOM and provenance, are also highlighted throughout the presentation.KCD Italy 2023 - Secure Software Supply chain for OCI Artifact on Kubernetes
KCD Italy 2023 - Secure Software Supply chain for OCI Artifact on Kubernetessparkfabrik
╠²
The document discusses the importance of securing the software supply chain, particularly in the context of OCI artifacts and Kubernetes, highlighting key areas like digital signatures, software bill of materials (SBOM), and various threats such as dependency confusion and malicious code injection. It emphasizes the need for provenance attestations and integrity checks to ensure authenticity and security against tampering. The document also introduces tools and frameworks like Sigstore and SLSA for enhancing supply chain security and promotes best practices such as signing artifacts and generating SBOMs.OpenSSF.Repository.WG.Presentation.OpenSSF.Repository.WG.Presentation
OpenSSF.Repository.WG.Presentation.OpenSSF.Repository.WG.Presentationkedofef453
╠²
OpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationOpenSSF.Repository.WG.PresentationAll You need to Know about Secure Coding with Open Source Software
All You need to Know about Secure Coding with Open Source SoftwareJavier Perez
╠²
This document provides an overview of secure coding with open source software. It discusses that open source software is now mainstream, used in many modern innovations. It describes what open source software is, the explosive growth of open source, and popular open source libraries and dependencies. The document outlines roles in open source projects and how to contribute. It discusses security considerations like vulnerabilities in open source libraries and the increased risk with reusing libraries. The document provides examples of popular open source projects like Angular.js and their contributions and vulnerabilities. It emphasizes the real risk is not a lack of fixes but the lack of speed in applying fixes. The importance of software composition analysis and vulnerability management for open source is highlighted.(Micro)chips and SLSA: Securing the Software Supply Chain
(Micro)chips and SLSA: Securing the Software Supply ChainRichard Boyd, II
╠²
The document discusses securing the software supply chain, highlighting recent attacks, changing compliance guidelines, and the importance of Software Bill of Materials (SBOMs) and attestations. It emphasizes the need for tamper-proof software supply chains, utilizing standards like SLSA and frameworks such as In-Toto for provenance. The role of Open Policy Agent (OPA) and its Rego policy language in maintaining compliance and governance in software supply chain security is also outlined.Software Supply Chains for DevOps @ InfoQ Live 2021
Software Supply Chains for DevOps @ InfoQ Live 2021Aysylu Greenberg
╠²
The document discusses modern challenges and solutions in software supply chains, particularly in the context of DevOps practices. It highlights the importance of automation, metadata collection, and compliance while managing vulnerabilities and ensuring integrity throughout the software development lifecycle. Key solutions mentioned include tools like Grafeas, Kritis, and In-Toto for continuous security and governance of software supply chains.CodeMotion 2023 - Deep dive nella supply chain della nostra infrastruttura cl...
CodeMotion 2023 - Deep dive nella supply chain della nostra infrastruttura cl...sparkfabrik
╠²
The document explores the security risks associated with the software supply chain in infrastructure as code (IaC), highlighting vulnerabilities exposed by incidents like the SolarWinds attack and Log4j exploit. It emphasizes the importance of using digital signatures, Software Bills of Materials (SBOM), and static analysis tools to mitigate risks while underscoring the need for vigilance in code review and dependency management. Key recommendations include using secure module practices, automated scanning, and ensuring the integrity and authenticity of software artifacts.Deep dive nella supply chain della nostra infrastruttura cloud
Deep dive nella supply chain della nostra infrastruttura cloudsparkfabrik
╠²
The document discusses software supply chain security and infrastructure as code. It describes how malicious modules and containers could potentially compromise infrastructure. It emphasizes the importance of using tools to detect issues like unauthorized access from modules. The document also discusses using digital signatures, software bills of materials, and initiatives like Sigstore and the OpenSSF to help secure the software supply chain and increase integrity and transparency of artifacts. It provides examples of how infrastructure as code could be exploited and recommends best practices like static analysis and generating signatures and software bills of materials to help prevent issues.Synopsys Security Event Israel Presentation: New AppSec Paradigms with Open S...
Synopsys Security Event Israel Presentation: New AppSec Paradigms with Open S...Synopsys Software Integrity Group
╠²
The document discusses modern application security paradigms in the context of open source and container development, emphasizing the importance of security at every stage from project inception to deployment. It highlights the complexities of open source licensing, the need for robust security practices, and the management of risks associated with vulnerabilities in dependencies. Additionally, it stresses the necessity for thorough inventorying, governance policies, and automation within development operations to mitigate risks and ensure safe practices.Software rotting - DevOpsCon Berlin
Software rotting - DevOpsCon BerlinGiulio Vian
╠²
The document discusses the rapid decay of software and emphasizes the need for improved security approaches due to increasing vulnerabilities and exploitation incidents. It highlights the importance of better tooling, practices, and timely responses to security threats to manage the growing risk in software development. Recommendations include adopting automated patching, thorough regression testing, and standardized source control management practices to enhance security and efficiency.Protecting your organization against attacks via the build system
Protecting your organization against attacks via the build systemLouis Jacomet
╠²
This document discusses supply chain attacks via the software build system and dependencies. It provides examples of real-world attacks where dependencies or build tools were compromised, including the CCleaner and MS Tools attacks. It then outlines various ways a build system and dependencies could be attacked, such as compromising continuous integration infrastructure, dependencies from public repositories, and external services like build caches. Finally, it discusses best practices for securing the build system and dependencies, including signing code, repository filtering, dependency verification, and reproducible builds.The Rocky Cloud Road
The Rocky Cloud RoadGert Drapers
╠²
The document outlines principles for software design and cloud computing, emphasizing simplicity, reliability, and scalability in engineering practices. It promotes self-assembling systems and highlights the importance of efficient operations, including automated deployments and proactive maintenance strategies. Key best practices recommended include designing for failure, loose coupling, and effective versioning to support dynamic service environments.Fluttercon 2024: Showing that you care about security - OpenSSF Scorecards fo...
Fluttercon 2024: Showing that you care about security - OpenSSF Scorecards fo...Chris Swan
╠²
The document outlines the agenda and steps for integrating security scorecards into Dart and Flutter projects, emphasizing the role of OpenSSF and the AllStar tool. It discusses the joys and challenges of managing security across multiple repositories and proposes a streamlined approach for achieving security compliance with minimal effort. Additionally, it encourages using the Scorecard CLI to evaluate security practices in existing repositories.Managing the Software Supply Chain: Policies that Promote Innovation While Op...
Managing the Software Supply Chain: Policies that Promote Innovation While Op...FINOS
╠²
The document discusses the complexities of managing the software supply chain, emphasizing the need for effective governance to optimize security and compliance while promoting innovation. It outlines the risks associated with unknown vulnerabilities and licensing issues in open source and commercial software. The recommendations include establishing an open source review board, conducting scans for compliance, and developing clear policies for managing open source software usage.Best practices for using open source software in the enterprise
Best practices for using open source software in the enterpriseMarcel de Vries
╠²
Marcel de Vries discusses best practices for using open source software in enterprises. He notes that 80% of software is based on open source components and that awareness is key. He demonstrates how to use an artifact repository like Nexus to publish components after builds, scan for licenses and vulnerabilities, and gain insights. While repositories help with transparency and analysis, additional tools and processes are needed for component selection, community engagement, and contribution management to fully address open source usage in enterprises.Open stack
Open stackLuan Cestari
╠²
OpenStack is an open source cloud computing platform that allows users to build private and public clouds. It provides infrastructure as a service (IaaS) and allows users to provision compute, storage, and networking resources on demand in a self-service manner. The document discusses the history and components of OpenStack, including Nova (compute), Swift (object storage), Cinder (block storage), Keystone (identity), Glance (image service), and others. It also covers OpenStack deployment models, supported hypervisors and images, and how to easily install OpenStack using PackStack.Open Source Clouds at VIRTu Alley
Open Source Clouds at VIRTu AlleyDell Cloud Services
╠²
The document discusses various open-source Infrastructure as a Service (IaaS) projects, including OpenNebula, Eucalyptus, CloudStack, and OpenStack, highlighting their missions and histories. It emphasizes the significance of open source in fostering innovation, reducing vendor lock-in, and promoting transparency in cloud computing solutions. The presentation encourages participation in the open-source movement as a path to a collaborative and empowering future in technology.Webinar: End to End Security & Operations with Chainguard and Weave GitOps
Webinar: End to End Security & Operations with Chainguard and Weave GitOpsWeaveworks
╠²
The document details a webinar focused on securing software supply chains through partnerships between Chainguard and Weaveworks, highlighting key topics like identity verification, Git commit signing, and GitOps practices. Experts James Strong and Leo Murillo lead discussions on challenges in software security and the tools available to address them. The session emphasizes the importance of automated processes and continuous delivery in managing cloud-native applications securely."Building Trust: Strengthening Your Software Supply Chain Security", Serhii V...
"Building Trust: Strengthening Your Software Supply Chain Security", Serhii V...Fwdays
╠²
The talk focuses on developing and integrating automation tools to enhance Supply Chain security. It addresses reproducible security practices with tools like Renovate and Wiz, as well as GitLab and JFrog Artifactory, to enforce consistent security scans seamlessly within existing workflows.
We will cover centralized artifact management for improved oversight and consistency. Furthermore, we will discuss the seamless integration of security scans into deployment tooling, featuring automatic deployment blocks for vulnerabilities and a controlled override option for flexibility.
The talk also examines tactics to keep the source code secure and up to date. We will explore the integration of runtime monitoring systems with detection capabilities and SLAs to manage and resolve issues on time.Vulnerability Alert Fatigue and Malicious Code Attacks Meetup 11012024.pdf
Vulnerability Alert Fatigue and Malicious Code Attacks Meetup 11012024.pdflior mazor
╠²
The document discusses the rising threat of software supply chain attacks, highlighting various attack types and the importance of securing dependencies in software development. It details the challenges posed by these attacks, such as vulnerabilities in third-party code, and introduces frameworks like SLSA to improve security measures. Additionally, it emphasizes best practices for development teams to mitigate risks associated with open-source dependencies and enhance overall security.stackconf 2024 | How to hack and defend (your) open source by Roman Zhukov.pdf
stackconf 2024 | How to hack and defend (your) open source by Roman Zhukov.pdfNETWAYS
╠²
The document discusses the importance of securing open-source software and provides guidance on risk assessment and best practices for secure sourcing, development, and maintenance. It emphasizes the use of various frameworks and tools for evaluating software and mitigating risks, such as dependency confusion and supply chain vulnerabilities. Key strategies include maintaining repositories, leveraging automation for vulnerability detection, and implementing robust secret management and security measures.DevOps Service | Mindtree
DevOps Service | MindtreeAnikeyRoy
╠²
GitLab is a popular DevOps platform that provides an ecosystem for code management, release management, and continuous integration and delivery (CI/CD) pipelines. This document discusses implementing DevOps using the GitLab ecosystem, including its tools, branching strategies, and designing a GitLab-based DevOps implementation. It provides an overview of the key GitLab tools and interfaces for users, and describes best practices for areas like source code management, continuous integration, monitoring, and security.A question of trust - understanding Open Source risks
A question of trust - understanding Open Source risksTim Mackey
╠²
The document discusses the security risks associated with open source software, particularly within the context of containerization. It highlights the necessity for security-driven development practices, awareness of vulnerabilities, and the importance of managing open source components and dependencies. The document also outlines a maturity model for evaluating the security practices related to open source usage, stressing the need for automation and integration with developer tools to improve governance and risk management.Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
╠²
║▌║▌▀Ż deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.More Related Content
Similar to Safeguarding artifact integrity in your Software Supply Chain (20)
All You need to Know about Secure Coding with Open Source Software
All You need to Know about Secure Coding with Open Source SoftwareJavier Perez
╠²
This document provides an overview of secure coding with open source software. It discusses that open source software is now mainstream, used in many modern innovations. It describes what open source software is, the explosive growth of open source, and popular open source libraries and dependencies. The document outlines roles in open source projects and how to contribute. It discusses security considerations like vulnerabilities in open source libraries and the increased risk with reusing libraries. The document provides examples of popular open source projects like Angular.js and their contributions and vulnerabilities. It emphasizes the real risk is not a lack of fixes but the lack of speed in applying fixes. The importance of software composition analysis and vulnerability management for open source is highlighted.(Micro)chips and SLSA: Securing the Software Supply Chain
(Micro)chips and SLSA: Securing the Software Supply ChainRichard Boyd, II
╠²
The document discusses securing the software supply chain, highlighting recent attacks, changing compliance guidelines, and the importance of Software Bill of Materials (SBOMs) and attestations. It emphasizes the need for tamper-proof software supply chains, utilizing standards like SLSA and frameworks such as In-Toto for provenance. The role of Open Policy Agent (OPA) and its Rego policy language in maintaining compliance and governance in software supply chain security is also outlined.Software Supply Chains for DevOps @ InfoQ Live 2021
Software Supply Chains for DevOps @ InfoQ Live 2021Aysylu Greenberg
╠²
The document discusses modern challenges and solutions in software supply chains, particularly in the context of DevOps practices. It highlights the importance of automation, metadata collection, and compliance while managing vulnerabilities and ensuring integrity throughout the software development lifecycle. Key solutions mentioned include tools like Grafeas, Kritis, and In-Toto for continuous security and governance of software supply chains.CodeMotion 2023 - Deep dive nella supply chain della nostra infrastruttura cl...
CodeMotion 2023 - Deep dive nella supply chain della nostra infrastruttura cl...sparkfabrik
╠²
The document explores the security risks associated with the software supply chain in infrastructure as code (IaC), highlighting vulnerabilities exposed by incidents like the SolarWinds attack and Log4j exploit. It emphasizes the importance of using digital signatures, Software Bills of Materials (SBOM), and static analysis tools to mitigate risks while underscoring the need for vigilance in code review and dependency management. Key recommendations include using secure module practices, automated scanning, and ensuring the integrity and authenticity of software artifacts.Deep dive nella supply chain della nostra infrastruttura cloud
Deep dive nella supply chain della nostra infrastruttura cloudsparkfabrik
╠²
The document discusses software supply chain security and infrastructure as code. It describes how malicious modules and containers could potentially compromise infrastructure. It emphasizes the importance of using tools to detect issues like unauthorized access from modules. The document also discusses using digital signatures, software bills of materials, and initiatives like Sigstore and the OpenSSF to help secure the software supply chain and increase integrity and transparency of artifacts. It provides examples of how infrastructure as code could be exploited and recommends best practices like static analysis and generating signatures and software bills of materials to help prevent issues.Synopsys Security Event Israel Presentation: New AppSec Paradigms with Open S...
Synopsys Security Event Israel Presentation: New AppSec Paradigms with Open S...Synopsys Software Integrity Group
╠²
The document discusses modern application security paradigms in the context of open source and container development, emphasizing the importance of security at every stage from project inception to deployment. It highlights the complexities of open source licensing, the need for robust security practices, and the management of risks associated with vulnerabilities in dependencies. Additionally, it stresses the necessity for thorough inventorying, governance policies, and automation within development operations to mitigate risks and ensure safe practices.Software rotting - DevOpsCon Berlin
Software rotting - DevOpsCon BerlinGiulio Vian
╠²
The document discusses the rapid decay of software and emphasizes the need for improved security approaches due to increasing vulnerabilities and exploitation incidents. It highlights the importance of better tooling, practices, and timely responses to security threats to manage the growing risk in software development. Recommendations include adopting automated patching, thorough regression testing, and standardized source control management practices to enhance security and efficiency.Protecting your organization against attacks via the build system
Protecting your organization against attacks via the build systemLouis Jacomet
╠²
This document discusses supply chain attacks via the software build system and dependencies. It provides examples of real-world attacks where dependencies or build tools were compromised, including the CCleaner and MS Tools attacks. It then outlines various ways a build system and dependencies could be attacked, such as compromising continuous integration infrastructure, dependencies from public repositories, and external services like build caches. Finally, it discusses best practices for securing the build system and dependencies, including signing code, repository filtering, dependency verification, and reproducible builds.The Rocky Cloud Road
The Rocky Cloud RoadGert Drapers
╠²
The document outlines principles for software design and cloud computing, emphasizing simplicity, reliability, and scalability in engineering practices. It promotes self-assembling systems and highlights the importance of efficient operations, including automated deployments and proactive maintenance strategies. Key best practices recommended include designing for failure, loose coupling, and effective versioning to support dynamic service environments.Fluttercon 2024: Showing that you care about security - OpenSSF Scorecards fo...
Fluttercon 2024: Showing that you care about security - OpenSSF Scorecards fo...Chris Swan
╠²
The document outlines the agenda and steps for integrating security scorecards into Dart and Flutter projects, emphasizing the role of OpenSSF and the AllStar tool. It discusses the joys and challenges of managing security across multiple repositories and proposes a streamlined approach for achieving security compliance with minimal effort. Additionally, it encourages using the Scorecard CLI to evaluate security practices in existing repositories.Managing the Software Supply Chain: Policies that Promote Innovation While Op...
Managing the Software Supply Chain: Policies that Promote Innovation While Op...FINOS
╠²
The document discusses the complexities of managing the software supply chain, emphasizing the need for effective governance to optimize security and compliance while promoting innovation. It outlines the risks associated with unknown vulnerabilities and licensing issues in open source and commercial software. The recommendations include establishing an open source review board, conducting scans for compliance, and developing clear policies for managing open source software usage.Best practices for using open source software in the enterprise
Best practices for using open source software in the enterpriseMarcel de Vries
╠²
Marcel de Vries discusses best practices for using open source software in enterprises. He notes that 80% of software is based on open source components and that awareness is key. He demonstrates how to use an artifact repository like Nexus to publish components after builds, scan for licenses and vulnerabilities, and gain insights. While repositories help with transparency and analysis, additional tools and processes are needed for component selection, community engagement, and contribution management to fully address open source usage in enterprises.Open stack
Open stackLuan Cestari
╠²
OpenStack is an open source cloud computing platform that allows users to build private and public clouds. It provides infrastructure as a service (IaaS) and allows users to provision compute, storage, and networking resources on demand in a self-service manner. The document discusses the history and components of OpenStack, including Nova (compute), Swift (object storage), Cinder (block storage), Keystone (identity), Glance (image service), and others. It also covers OpenStack deployment models, supported hypervisors and images, and how to easily install OpenStack using PackStack.Open Source Clouds at VIRTu Alley
Open Source Clouds at VIRTu AlleyDell Cloud Services
╠²
The document discusses various open-source Infrastructure as a Service (IaaS) projects, including OpenNebula, Eucalyptus, CloudStack, and OpenStack, highlighting their missions and histories. It emphasizes the significance of open source in fostering innovation, reducing vendor lock-in, and promoting transparency in cloud computing solutions. The presentation encourages participation in the open-source movement as a path to a collaborative and empowering future in technology.Webinar: End to End Security & Operations with Chainguard and Weave GitOps
Webinar: End to End Security & Operations with Chainguard and Weave GitOpsWeaveworks
╠²
The document details a webinar focused on securing software supply chains through partnerships between Chainguard and Weaveworks, highlighting key topics like identity verification, Git commit signing, and GitOps practices. Experts James Strong and Leo Murillo lead discussions on challenges in software security and the tools available to address them. The session emphasizes the importance of automated processes and continuous delivery in managing cloud-native applications securely."Building Trust: Strengthening Your Software Supply Chain Security", Serhii V...
"Building Trust: Strengthening Your Software Supply Chain Security", Serhii V...Fwdays
╠²
The talk focuses on developing and integrating automation tools to enhance Supply Chain security. It addresses reproducible security practices with tools like Renovate and Wiz, as well as GitLab and JFrog Artifactory, to enforce consistent security scans seamlessly within existing workflows.
We will cover centralized artifact management for improved oversight and consistency. Furthermore, we will discuss the seamless integration of security scans into deployment tooling, featuring automatic deployment blocks for vulnerabilities and a controlled override option for flexibility.
The talk also examines tactics to keep the source code secure and up to date. We will explore the integration of runtime monitoring systems with detection capabilities and SLAs to manage and resolve issues on time.Vulnerability Alert Fatigue and Malicious Code Attacks Meetup 11012024.pdf
Vulnerability Alert Fatigue and Malicious Code Attacks Meetup 11012024.pdflior mazor
╠²
The document discusses the rising threat of software supply chain attacks, highlighting various attack types and the importance of securing dependencies in software development. It details the challenges posed by these attacks, such as vulnerabilities in third-party code, and introduces frameworks like SLSA to improve security measures. Additionally, it emphasizes best practices for development teams to mitigate risks associated with open-source dependencies and enhance overall security.stackconf 2024 | How to hack and defend (your) open source by Roman Zhukov.pdf
stackconf 2024 | How to hack and defend (your) open source by Roman Zhukov.pdfNETWAYS
╠²
The document discusses the importance of securing open-source software and provides guidance on risk assessment and best practices for secure sourcing, development, and maintenance. It emphasizes the use of various frameworks and tools for evaluating software and mitigating risks, such as dependency confusion and supply chain vulnerabilities. Key strategies include maintaining repositories, leveraging automation for vulnerability detection, and implementing robust secret management and security measures.DevOps Service | Mindtree
DevOps Service | MindtreeAnikeyRoy
╠²
GitLab is a popular DevOps platform that provides an ecosystem for code management, release management, and continuous integration and delivery (CI/CD) pipelines. This document discusses implementing DevOps using the GitLab ecosystem, including its tools, branching strategies, and designing a GitLab-based DevOps implementation. It provides an overview of the key GitLab tools and interfaces for users, and describes best practices for areas like source code management, continuous integration, monitoring, and security.A question of trust - understanding Open Source risks
A question of trust - understanding Open Source risksTim Mackey
╠²
The document discusses the security risks associated with open source software, particularly within the context of containerization. It highlights the necessity for security-driven development practices, awareness of vulnerabilities, and the importance of managing open source components and dependencies. The document also outlines a maturity model for evaluating the security practices related to open source usage, stressing the need for automation and integration with developer tools to improve governance and risk management.Synopsys Security Event Israel Presentation: New AppSec Paradigms with Open S...
Synopsys Security Event Israel Presentation: New AppSec Paradigms with Open S...Synopsys Software Integrity Group
╠²
Recently uploaded (20)
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
╠²
║▌║▌▀Ż deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.OpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
╠²
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash
╠²
Lessons Learned from Developing Secure AI WorkflowsAI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
╠²
AI VIDEO MAGAZINE - r/aivideo community newsletter ŌĆō Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
╠²
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnŌĆÖt yielding any results, so I expanded my search to second-hand dealer sitesŌĆöonly to realise that periodically checking each one was going to be tedious. ThatŌĆÖs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformŌĆÖs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IŌĆÖll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canŌĆÖt buy a car for youŌĆöyetŌĆöit can certainly help you find the one youŌĆÖre after!FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: Targeting Trust: The Future of Identity in the WorkforceFIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
╠²
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionMuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
╠²
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...
Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...janeliewang985
╠²
the slides of the MP selection approach CMPSTech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
╠²
A presentation at Internetware 2025.Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik
╠²
A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdf
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdfbiswajitbanerjee38
╠²
Russia is one of the most aggressive nations when it comes to state coordinated cyberattacksŌĆŖŌĆöŌĆŖand Ukraine has been at the center of their crosshairs for 3 years. This report, provided the State Service of Special Communications and Information Protection of Ukraine contains an incredible amount of cybersecurity insights, showcasing the coordinated aggressive cyberwarfare campaigns of Russia against Ukraine.
It brings to the forefront that understanding your adversary, especially an aggressive nation state, is important for cyber defense. Knowing their motivations, capabilities, and tactics becomes an advantage when allocating resources for maximum impact.
Intelligence shows Russia is on a cyber rampage, leveraging FSB, SVR, and GRU resources to professionally target UkraineŌĆÖs critical infrastructures, military, and international diplomacy support efforts.
The number of total incidents against Ukraine, originating from Russia, has steadily increased from 1350 in 2021 to 4315 in 2024, but the number of actual critical incidents has been managed down from a high of 1048 in 2022 to a mere 59 in 2024ŌĆŖŌĆöŌĆŖshowcasing how the rapid detection and response to cyberattacks has been impacted by UkraineŌĆÖs improved cyber resilience.
Even against a much larger adversary, Ukraine is showcasing outstanding cybersecurity, enabled by strong strategies and sound tactics. There are lessons to learn for any enterprise that could potentially be targeted by aggressive nation states.
Definitely worth the read!FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptx
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptxFIDO Alliance
╠²
FIDO Seminar: Authentication for a Billion Consumers - AmazonCapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptx
FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: New Data: Passkey Adoption in the WorkforceFIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance
╠²
FIDO Seminar: Evolving Landscape of Post-Quantum CryptographyCoordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the SameAd
Safeguarding artifact integrity in your Software Supply Chain
- 1. Safeguarding artifact integrity in your software supply chain Giovanni Galloro - EMEA CE Specialist - Application Modernization - Google Cloud @ggalloro
- 2. The need to secure the software supply chain
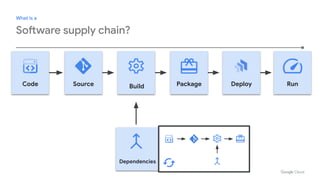
- 3. What is a Software supply chain? Source Build Package Run Dependencies Code Deploy
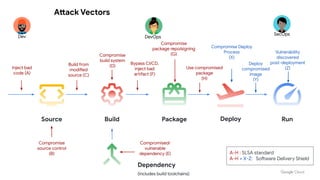
- 5. Source Build Package Run Dependency (includes build toolchains) Inject bad code (A) Compromise source control (B) Build from modified source (C) Compromise build system (D) Compromised/ vulnerable dependency (E) Bypass CI/CD, inject bad artifact (F) Compromise package repo/signing (G) Use compromised package (H) Attack Vectors DevOps SecOps Dev Deploy Compromise Deploy Process (X) Deploy compromised image (Y) Vulnerability discovered post-deployment (Z) A-H : SLSA standard A-H + X-Z: Software Delivery Shield
- 6. What is Google doing in the community
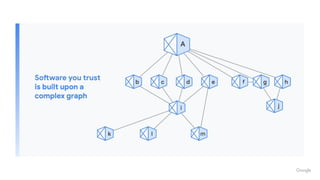
- 7. Making the chain stronger: Google open source efforts ŌŚÅ Open Source Security Foundation ŌĆō We co-founded Open Source Security Foundation in 2019, a cross-industry forum on supply chain security. ŌŚÅ Supply-chain Levels for Software Artifacts (SLSA) ŌĆō SLSA is an end-to-end framework for supply chain integrity. It is an open-source equivalent of many of the processes we have been implementing internally at Google. SLSA provides an auditable provenance of what was built and how. ŌŚÅ OpenSSF Scorecards ŌĆō Scorecards use evaluation metrics like well-defined security policy, code review process, and continuous test coverage with fuzzing and static code analysis tools to provide a risk score for open-source projects. ŌŚÅ Open Source Insights - provides a transitive dependency graph so you can see your dependencies and their dependencies, all down the dependency tree ŌŚÅ Grafeas & Kritis - Open metadata standard for software artifacts and admission controller to enforce security policies at deployment.
- 8. SLSA Levels Automation & Provenance Build must be fully scripted/automated and generate provenance Version Control & Signed Provenance Requires using version control and hosted build service that generates authenticated provenance Non-falsifiable, Ephemeral Builds are fully trustworthy, with identity attestations of underlying build infrastructure/hardware. Ephemeral builds leave nothing behind. Hermetic Builds, Review All build inputs/dependencies are specified upfront with no internet egress during the build. Two-party reviews. Measure integrity levels for build, source and dependencies See: slsa.dev
- 9. Safeguarding artifact integrity on GCP
- 10. Operate Cloud Logging & Monitoring Package Artifact Registry Scanning Artifact Analysis Source Cloud Source Repositories Build Cloud Build IDE Cloud Code Deploy Cloud Deploy Runtime Kubernetes Engine Firebase Cloud Functions Cloud Run Anthos Sw Supply Chain on GCP
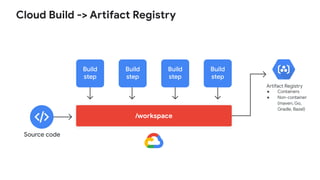
- 12. Cloud Build -> Artifact Registry /workspace Build step Build step Build step Build step Source code Artifact Registry ŌŚÅ Containers ŌŚÅ Non-container (maven, Go, Gradle, Bazel)
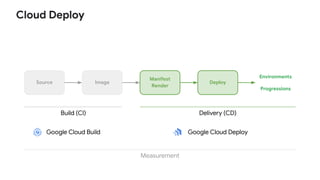
- 13. Source Image Manifest Render Deploy Environments Progressions Build (CI) Delivery (CD) Measurement Cloud Deploy Google Cloud Deploy Google Cloud Build
- 14. Binary authorization Cloud Build Triggered & Automatic Scan Container Analysis Image metadata Artifact Registry Kubernetes Engine Cloud Code Google Cloud Deploy Software Delivery Shield Cloud Run Continuous scanning with Container Analysis Admission control Cloud Workstations Assured OSS Source Control API API
- 15. Questions ?
