Safeguarding Container Supply Chain - Anshul Patel
0 likes19 views
This presentation discuss regarding security of supply chain via SLSA framework and SBOM
1 of 12
Download to read offline









Recommended
Deep dive nella supply chain della nostra infrastruttura cloud



Deep dive nella supply chain della nostra infrastruttura cloudsparkfabrik
╠²
The document discusses software supply chain security and infrastructure as code. It describes how malicious modules and containers could potentially compromise infrastructure. It emphasizes the importance of using tools to detect issues like unauthorized access from modules. The document also discusses using digital signatures, software bills of materials, and initiatives like Sigstore and the OpenSSF to help secure the software supply chain and increase integrity and transparency of artifacts. It provides examples of how infrastructure as code could be exploited and recommends best practices like static analysis and generating signatures and software bills of materials to help prevent issues.Top 10 Software to Detect & Prevent Security Vulnerabilities from BlackHat US...



Top 10 Software to Detect & Prevent Security Vulnerabilities from BlackHat US...Mobodexter
╠²
BlackHat USA 2015 got recently concluded and we head a bunch of news around how BlackHat brought to light various security vulnerabilities in day-to-day life like ZigBee protocol, Device for stealing keyless cars & ATM card skimmers. However the presenters, who are also ethical hackers, also gave a bunch of tools to help software community to detect & prevent security holes in the hardware & software while the product is ready for release. We have reviewed all the presentations from the conference and give you here a list of Top 10 tools/utilities that helps in security vulnerability detection & prevention.
KCD Italy 2023 - Secure Software Supply chain for OCI Artifact on Kubernetes



KCD Italy 2023 - Secure Software Supply chain for OCI Artifact on Kubernetessparkfabrik
╠²
In this talk we will talk about how to ensure the security and quality of the software we deploy on Kubernetes using open-source tools like Sigstore, Kyverno and Syft/Grype.
We will explain what a secure supply chain is, why it is important and how to implement it with these tools. We will also show you how to generate and verify SBOMs (Software Bill of Materials) of your OCI (Open Container Initiative) artifacts. And finally, we will show you some practical examples of how to use these technologies in action.
We hope you enjoy it and find it useful!Enterprise-Grade DevOps Solutions for a Start Up Budget



Enterprise-Grade DevOps Solutions for a Start Up BudgetDevOps.com
╠²
Even though youŌĆÖre a small startup or medium-sized business and just beginning your product journey, it doesnŌĆÖt mean you canŌĆÖt have a robust and scalable DevOps environment like the enterprise experts. It is always a good practice when building a startup or a new company to have a solid foundation and start implementing efficient and scalable solutions early. Join and learn how having a limited budget doesnŌĆÖt mean you canŌĆÖt have enterprise quality tools.Security in open source projects



Security in open source projectsJose Manuel Ortega Candel
╠²
The document discusses security in open source projects. It covers vulnerabilities in dependencies, detecting vulnerabilities in code bases, and improving security. Functionality is often prioritized over security. Various coding flaws are described like buffer overflows. Tools for analyzing dependencies, detecting vulnerabilities statically and dynamically are presented, like OWASP Dependency-Check, Snyk, SonarQube, ZAP. Best practices for open source security include following responsible disclosure policies and auditing code bases regularly.CodeMotion 2023 - Deep dive nella supply chain della nostra infrastruttura cl...



CodeMotion 2023 - Deep dive nella supply chain della nostra infrastruttura cl...sparkfabrik
╠²
In this talk IŌĆÖll explain what is the Software Supply Chain, common threats and mitigations and how they apply to IAC ecosystem too. IŌĆÖll show off security threats using Terraform and its ecosystem and finally iŌĆÖll talk about OCI images talking about digital signatures and SBOM using Sigstore and Syft. IŌĆÖll do a live coding session showing off how to deploy secure OCI images on K8S cluster with security policies built with Kyverno, the session includes also security scanning using the generated SBOM.Safeguarding artifact integrity in your Software Supply Chain



Safeguarding artifact integrity in your Software Supply ChainGiovanni Galloro
╠²
In questo talk descriveremo alcune best practice per migliorare la sicurezza della tua Software Supply Chain, capirai cos'├© il framework SLSA e vedrai esempi di utilizzo degli strumenti di Google che aiutano a risolvere le vulnerabilit├Ā delle dipendenze sia nella fase di sviluppo che in quella di build, attestare l'integrit├Ā del processo di build, configurare gli ambienti di runtime per accettare solo codice attendibile e monitorare continuamente le applicazioni in esecuzione per nuove vulnerabilit├Ā.DevOps-Roadmap



DevOps-RoadmapBnhNguynHuy1
╠²
This document provides a roadmap for learning DevOps skills and technologies. It covers topics such as source code management with Git, programming languages, Linux, networking, servers, containers, orchestration with Kubernetes, infrastructure as code with Terraform, CI/CD, monitoring, cloud providers, Agile methodologies, and automation testing. For each topic, it lists several learning resources like websites, courses, and documentation to gain knowledge in that area. The overall roadmap is intended to help develop the full range of abilities needed for a career in DevOps engineering.Pragmatic Pipeline Security



Pragmatic Pipeline SecurityJames Wickett
╠²
All organizations want to go faster and decrease friction in delivering software. The problem is that InfoSec has historically slowed this down or worse. But, with the rise of CD pipelines and new devsecops tooling, there is an opportunity to reverse this trend and move Security from being a blocker to being an enabler.
This talk will discuss hallmarks of doing security in a software delivery pipeline with an emphasis on being pragmatic. At each phase of the delivery pipeline, you will be armed with philosophy, questions, and tools that will get security up-to-speed with your software delivery cadence.
From DeliveryConf 2020 Drupal Dev Days Vienna 2023 - What is the secure software supply chain and th...



Drupal Dev Days Vienna 2023 - What is the secure software supply chain and th...sparkfabrik
╠²
This document discusses the secure software supply chain and current state of the PHP ecosystem. It begins with introductions and defines a software supply chain as a network involved in creating and delivering a product to consumers. It then discusses threats in modern software supply chains like dependencies and demonstrates building a software bill of materials (SBOM) to analyze dependencies. It also covers recent supply chain attacks on PHP infrastructure and tools like Composer and PEAR. Finally, it recommends mitigations like using signed container images to verify integrity and provenance and generating SBOMs to detect vulnerabilities.Has serverless adoption hit a roadblock?



Has serverless adoption hit a roadblock?Veselin Pizurica
╠²
The large OŌĆÖReilly survey on serverless adoption indicated that the majority of enterprises have not yet adopted serverless. They have cited the following concerns as main factors: security, the steep learning curve, vendor lock-in, integration/debugging and observability of serverless applications.
In this talk, I will share my views on these concerns and present how Waylay IO has addressed these challenges. Waylay IOŌĆÖs mission is to finally unlock all promised benefits of serverless computation, with an intuitive and developer-friendly low-code platform.Agile Integration Architecture: A Containerized and Decentralized Approach to...



Agile Integration Architecture: A Containerized and Decentralized Approach to...Kim Clark
╠²
Microservices principles are revolutionizing the way applications are built, by enabling a more decoupled and decentralized approach to implementation, creating greater agility, scalability and resilience. These applications still need to be connected to one another, and to existing systems of record. Agile integration architecture brings the benefits of cloud-ready containerization to the integration space. It provides the opportunity to move from the heavily centralized ESB pattern to integration within more empowered and autonomous application teams. We look at the architectural differences in this approach compared to traditional integration, and also at how it enables more decentralized organizational structure better suited to digital transformation. You can read a more detailed paper on this approach at http://ibm.biz/AgileIntegArchPaper. This presentation was recorded for Integration Developer News (http://www.idevnews.com/) and is available here: http://ibm.biz/AgileIntegArchWebinarIoT architecture



IoT architectureSumit Sharma
╠²
How do APIs and IoT relate? The answer is not as simple as merely adding an API on top of a dumb device, but rather about understanding the architectural patterns for implementing an IoT fabric. There are typically two or three trends:
Exposing the device to a management framework
Exposing that management framework to a business centric logic
Exposing that business layer and data to end users.
This last trend is the IoT stack, which involves a new shift in the separation of what stuff happens, where data lives and where the interface lies. For instance, it's a mix of architectural styles between cloud, APIs and native hardware/software configurations.19507334023_NURISMA Z.D._PPT P PRADANA.pptx



19507334023_NURISMA Z.D._PPT P PRADANA.pptxnurismazenitad12
╠²
Cloud computing bukanlah satu bagian dari teknologi seperti microchip atau telepon genggam. Sebaliknya, ini merupakan sebuah sistem yang utamanya terdiri dari tiga layanan: software-as-a-service (SaaS), infrastructure-as-a-service (IaaS), dan platform-as-a-service (PaaS).What is the Secure Supply Chain and the Current State of the PHP Ecosystem



What is the Secure Supply Chain and the Current State of the PHP Ecosystemsparkfabrik
╠²
In this talk IŌĆÖll present the current state of the software supply chain, the big global recent events (SolarWinds, log4shell, codecov, packagist) and the state of the PHP and Drupal ecosystem, the threats and the mitigations that can be applied using tools like Sigstore, Syft, and Grype for digital signatures, SBOM generation, and automatic vulnerability scanning and how to use them for real-world projects to gain unprecedented levels of knowledge of your digital artifacts.
There will be also a demo of the mentioned tools in action to implement a secure supply chain pipeline for your Drupal projects.TechRadarCon 2022 | Have you built your platform yet ?



TechRadarCon 2022 | Have you built your platform yet ?Haggai Philip Zagury
╠²
This document discusses building an internal developer platform to improve the developer experience. It suggests that a platform provides self-service tools for onboarding, documentation, best practices, credentials, and understanding available services. A platform engineer builds and maintains the developer portal and tools. Successful companies like Spotify use platforms like Backstage to standardize processes and resources for developers across teams and clouds. The talk encourages building an incremental, self-service platform to streamline development.Balaji Resume



Balaji ResumeBalaji Ommudali
╠²
I have Over 8+ years of experience as a DevOps Engineer. I came across an interesting position of DevOps Engineering position on your Linked post. Constantly updating my skill set, I am proficient in DevOps Tools like Git, Jenkins Pipeline Automation, AWS, Chef, Ansible, Kubernetes, Terraform, Docker, Shell Scripting,ELK, Jfrog and Prometheus. security_assessment_slides



security_assessment_slidesSteve Arnold
╠²
This document summarizes key information from a presentation on security architecture in the IoT age. It discusses the risks of vulnerabilities being exploited in embedded devices, as seen with Stuxnet. It recommends resources for credible cybersecurity information, including the Information Assurance Support Environment site. The document also summarizes guidance on the Risk Management Framework and Security Technical Implementation Guides.Security & Resiliency of Cloud Native Apps with Weave GitOps & Tetrate Servic...



Security & Resiliency of Cloud Native Apps with Weave GitOps & Tetrate Servic...Weaveworks
╠²
Cloud-native applications are increasingly spanning across hybrid and multi-cloud environments such as on-premise data centers, in the cloud (Amazon EKS, Azure AKS, Google Cloud GKE) and at the edge. Customers need to ensure security and resiliency for their cloud-native applications while managing releases through reliable, consistent deployment and runtime policies.
In this session, weŌĆÖve partnered with Tetrate to showcase how to effectively manage advanced deployments using Weave GitOps. Managing application configurations by different teams across multiple Kubernetes clusters is made possible with Weave GitOps and Tetrate Service Bridge. Using familiar Git workflows, Weave Policy-as-Code enables application engineers to quickly deliver new features safely.
Join us as we demonstrate the scenarios where:
- All changes to application configuration are managed through Git workflows.
- GitOps provides an extra layer of security by removing the need for direct access to Kubernetes clusters.
- Policy-as-Code guarantees security, resilience and coding standards compliance.
- Tetrate Service Bridge provides dynamic configuration of application workloads and failover across multiple Kubernetes clusters.Software Security: In the World of Cloud & CI-CD



Software Security: In the World of Cloud & CI-CDOWASP Delhi
╠²
The document discusses software security in the context of cloud computing and continuous integration/continuous delivery (CI/CD) development processes. It outlines the challenges of managing security for organizations with many cloud products and frequent software changes. The key points are that security needs to be addressed at all stages of the CI/CD pipeline, including selecting secure third-party components, performing static and dynamic analysis during development and testing, and deploying runtime application security tools in production. Taking a holistic CI/CD-based approach helps provide security visibility and input for business decisions around investment and meeting customer demands.SparksCon 2024 - Die Ringe der Macht



SparksCon 2024 - Die Ringe der MachtMarkus Eisele
╠²
Die Wahl der richtigen Entwicklungs- und Betriebsmittel f├╝hlt sich heute oft unm├Čglich an. Endlose Frameworks und Technologien, st├żndiger Druck zum Cloud-Umzug ŌĆō Chaos droht. Markus pr├żsentiert Ihnen die "Ringe der Macht", mit denen Sie Dev, Sec und Ops zu einem schlagkr├żftigen Team vereinen. Lernen Sie, wie Platform Engineering das Entwicklerleben leichter macht und Ihnen die Kontrolle zur├╝ckgibt.Top10 Characteristics of Awesome Apps



Top10 Characteristics of Awesome AppsCasey Lee
╠²
In this talk, you will hear the best practices from analysts at Gartner, engineers at Heroku, and experiences at VSP distilled down into a top ten list of characteristics that applications ought to have to achieve high availability, scalability and flexibility. Target audience includes developers of APIs and web-based applications, the analysts and architects that design them and the infrastructure teams that support them.Cncf checkov and bridgecrew



Cncf checkov and bridgecrewLibbySchulze
╠²
This document discusses a webinar about integrating infrastructure as code (IaC) security into the development lifecycle using Checkov. It notes that nearly half of open source Terraform and CloudFormation templates contain security issues. Checkov is introduced as an open source IaC scanning tool that supports multiple frameworks and cloud providers. The benefits of Checkov include lower remediation times, reduced security incidents, and simplifying compliance. Integrations with DevOps tools and the Cloud Native Application Platform Approach (CNAPP) are also discussed. A demo of Checkov is then shown including using it with VS Code and Azure DevOps.Backstage at CNCF Madison.pptx



Backstage at CNCF Madison.pptxBrandenTimm1
╠²
This document discusses Backstage, an open platform for building developer portals created by Spotify. It summarizes that Backstage unifies all tooling, services, apps, data and docs with a single consistent UI to make sense of a company's entire software ecosystem. It provides speed, chaos control and scalability. Backstage lets developers easily create and manage software, and explore their company's full software ecosystem to enable collaboration.Content Strategy and Developer Engagement for DevPortals



Content Strategy and Developer Engagement for DevPortalsAxway
╠²
║▌║▌▀Żs from Write the Docs Ottawa Meet Up at Shopify HQ in Canada, June 24, 2019
WeŌĆÖll walk through 5 scenarios and concrete ways of reaching a developer community for frictionless and increased engagement.Open Source IoT Project Flogo - Introduction, Overview and Architecture



Open Source IoT Project Flogo - Introduction, Overview and ArchitectureKai W├żhner
╠²
Go-powered Open Source Project Flogo for Lightweight IoT and Edge Integration:
The Internet of Things (IoT) brings up 50 billion devices until 2020, which have to be connected somehow. Challenges include low bandwidth, high latency, non-reliable connectivity and the need for low network costs. Therefore, a gateway at the edge is needed remotely on site of the devices to filter, aggregate and send just relevant data into the cloud or data center.
This session introduces open source project Flogo, which allows developing ultra-lightweight IoT edge applications with a zero-coding web user interface. Coders can also rely just on Go code if they want. It is written in Go programming language and therefore 20-50x more lightweight than similar Java or JavaScript frameworks.
The session focuses on live demos and shows how to develop ultra-lightweight microservices and how to integrate IoT devices using standards such as MQTT, WebSockets, CoaP or REST. The last part of the session compares Project Flogo to other open source IoT projects like Eclipse Kura or Node-RED and cloud offerings such as AWS IoT.
Check out www.flogo.io and https://community.tibco.com/products/project-flogo for more information and community.
Dev{sec}ops



Dev{sec}opsSteven Carlson
╠²
Keeping security top of mind while creating standards for engineering teams following the DevOps culture. This talk was designed to show off how easily it is to automate security scanning and to be the developer advocate by showing the quality of development work. We will cover some high-level topics of DevSecOps and demo some examples DevOps team can implement for free.Open Source Identity and Access management with Keycloak.pdf



Open Source Identity and Access management with Keycloak.pdfAnshul Patel
╠²
My meetup talk provides introduction to keycloak and how it can be
leveraged for identity and access management.Chaos engineering with Litmus Chaos Framework



Chaos engineering with Litmus Chaos FrameworkAnshul Patel
╠²
Chaos engineering introduces failures into systems to test resilience. Litmus Chaos is an open source chaos engineering framework from Mayadata that allows injecting chaos into Kubernetes clusters. It includes a chaos operator, experiments, and engine to run experiments declaratively. Currently it supports experiments for services like OpenEBS, Cassandra, and Kafka.More Related Content
Similar to Safeguarding Container Supply Chain - Anshul Patel (20)
Pragmatic Pipeline Security



Pragmatic Pipeline SecurityJames Wickett
╠²
All organizations want to go faster and decrease friction in delivering software. The problem is that InfoSec has historically slowed this down or worse. But, with the rise of CD pipelines and new devsecops tooling, there is an opportunity to reverse this trend and move Security from being a blocker to being an enabler.
This talk will discuss hallmarks of doing security in a software delivery pipeline with an emphasis on being pragmatic. At each phase of the delivery pipeline, you will be armed with philosophy, questions, and tools that will get security up-to-speed with your software delivery cadence.
From DeliveryConf 2020 Drupal Dev Days Vienna 2023 - What is the secure software supply chain and th...



Drupal Dev Days Vienna 2023 - What is the secure software supply chain and th...sparkfabrik
╠²
This document discusses the secure software supply chain and current state of the PHP ecosystem. It begins with introductions and defines a software supply chain as a network involved in creating and delivering a product to consumers. It then discusses threats in modern software supply chains like dependencies and demonstrates building a software bill of materials (SBOM) to analyze dependencies. It also covers recent supply chain attacks on PHP infrastructure and tools like Composer and PEAR. Finally, it recommends mitigations like using signed container images to verify integrity and provenance and generating SBOMs to detect vulnerabilities.Has serverless adoption hit a roadblock?



Has serverless adoption hit a roadblock?Veselin Pizurica
╠²
The large OŌĆÖReilly survey on serverless adoption indicated that the majority of enterprises have not yet adopted serverless. They have cited the following concerns as main factors: security, the steep learning curve, vendor lock-in, integration/debugging and observability of serverless applications.
In this talk, I will share my views on these concerns and present how Waylay IO has addressed these challenges. Waylay IOŌĆÖs mission is to finally unlock all promised benefits of serverless computation, with an intuitive and developer-friendly low-code platform.Agile Integration Architecture: A Containerized and Decentralized Approach to...



Agile Integration Architecture: A Containerized and Decentralized Approach to...Kim Clark
╠²
Microservices principles are revolutionizing the way applications are built, by enabling a more decoupled and decentralized approach to implementation, creating greater agility, scalability and resilience. These applications still need to be connected to one another, and to existing systems of record. Agile integration architecture brings the benefits of cloud-ready containerization to the integration space. It provides the opportunity to move from the heavily centralized ESB pattern to integration within more empowered and autonomous application teams. We look at the architectural differences in this approach compared to traditional integration, and also at how it enables more decentralized organizational structure better suited to digital transformation. You can read a more detailed paper on this approach at http://ibm.biz/AgileIntegArchPaper. This presentation was recorded for Integration Developer News (http://www.idevnews.com/) and is available here: http://ibm.biz/AgileIntegArchWebinarIoT architecture



IoT architectureSumit Sharma
╠²
How do APIs and IoT relate? The answer is not as simple as merely adding an API on top of a dumb device, but rather about understanding the architectural patterns for implementing an IoT fabric. There are typically two or three trends:
Exposing the device to a management framework
Exposing that management framework to a business centric logic
Exposing that business layer and data to end users.
This last trend is the IoT stack, which involves a new shift in the separation of what stuff happens, where data lives and where the interface lies. For instance, it's a mix of architectural styles between cloud, APIs and native hardware/software configurations.19507334023_NURISMA Z.D._PPT P PRADANA.pptx



19507334023_NURISMA Z.D._PPT P PRADANA.pptxnurismazenitad12
╠²
Cloud computing bukanlah satu bagian dari teknologi seperti microchip atau telepon genggam. Sebaliknya, ini merupakan sebuah sistem yang utamanya terdiri dari tiga layanan: software-as-a-service (SaaS), infrastructure-as-a-service (IaaS), dan platform-as-a-service (PaaS).What is the Secure Supply Chain and the Current State of the PHP Ecosystem



What is the Secure Supply Chain and the Current State of the PHP Ecosystemsparkfabrik
╠²
In this talk IŌĆÖll present the current state of the software supply chain, the big global recent events (SolarWinds, log4shell, codecov, packagist) and the state of the PHP and Drupal ecosystem, the threats and the mitigations that can be applied using tools like Sigstore, Syft, and Grype for digital signatures, SBOM generation, and automatic vulnerability scanning and how to use them for real-world projects to gain unprecedented levels of knowledge of your digital artifacts.
There will be also a demo of the mentioned tools in action to implement a secure supply chain pipeline for your Drupal projects.TechRadarCon 2022 | Have you built your platform yet ?



TechRadarCon 2022 | Have you built your platform yet ?Haggai Philip Zagury
╠²
This document discusses building an internal developer platform to improve the developer experience. It suggests that a platform provides self-service tools for onboarding, documentation, best practices, credentials, and understanding available services. A platform engineer builds and maintains the developer portal and tools. Successful companies like Spotify use platforms like Backstage to standardize processes and resources for developers across teams and clouds. The talk encourages building an incremental, self-service platform to streamline development.Balaji Resume



Balaji ResumeBalaji Ommudali
╠²
I have Over 8+ years of experience as a DevOps Engineer. I came across an interesting position of DevOps Engineering position on your Linked post. Constantly updating my skill set, I am proficient in DevOps Tools like Git, Jenkins Pipeline Automation, AWS, Chef, Ansible, Kubernetes, Terraform, Docker, Shell Scripting,ELK, Jfrog and Prometheus. security_assessment_slides



security_assessment_slidesSteve Arnold
╠²
This document summarizes key information from a presentation on security architecture in the IoT age. It discusses the risks of vulnerabilities being exploited in embedded devices, as seen with Stuxnet. It recommends resources for credible cybersecurity information, including the Information Assurance Support Environment site. The document also summarizes guidance on the Risk Management Framework and Security Technical Implementation Guides.Security & Resiliency of Cloud Native Apps with Weave GitOps & Tetrate Servic...



Security & Resiliency of Cloud Native Apps with Weave GitOps & Tetrate Servic...Weaveworks
╠²
Cloud-native applications are increasingly spanning across hybrid and multi-cloud environments such as on-premise data centers, in the cloud (Amazon EKS, Azure AKS, Google Cloud GKE) and at the edge. Customers need to ensure security and resiliency for their cloud-native applications while managing releases through reliable, consistent deployment and runtime policies.
In this session, weŌĆÖve partnered with Tetrate to showcase how to effectively manage advanced deployments using Weave GitOps. Managing application configurations by different teams across multiple Kubernetes clusters is made possible with Weave GitOps and Tetrate Service Bridge. Using familiar Git workflows, Weave Policy-as-Code enables application engineers to quickly deliver new features safely.
Join us as we demonstrate the scenarios where:
- All changes to application configuration are managed through Git workflows.
- GitOps provides an extra layer of security by removing the need for direct access to Kubernetes clusters.
- Policy-as-Code guarantees security, resilience and coding standards compliance.
- Tetrate Service Bridge provides dynamic configuration of application workloads and failover across multiple Kubernetes clusters.Software Security: In the World of Cloud & CI-CD



Software Security: In the World of Cloud & CI-CDOWASP Delhi
╠²
The document discusses software security in the context of cloud computing and continuous integration/continuous delivery (CI/CD) development processes. It outlines the challenges of managing security for organizations with many cloud products and frequent software changes. The key points are that security needs to be addressed at all stages of the CI/CD pipeline, including selecting secure third-party components, performing static and dynamic analysis during development and testing, and deploying runtime application security tools in production. Taking a holistic CI/CD-based approach helps provide security visibility and input for business decisions around investment and meeting customer demands.SparksCon 2024 - Die Ringe der Macht



SparksCon 2024 - Die Ringe der MachtMarkus Eisele
╠²
Die Wahl der richtigen Entwicklungs- und Betriebsmittel f├╝hlt sich heute oft unm├Čglich an. Endlose Frameworks und Technologien, st├żndiger Druck zum Cloud-Umzug ŌĆō Chaos droht. Markus pr├żsentiert Ihnen die "Ringe der Macht", mit denen Sie Dev, Sec und Ops zu einem schlagkr├żftigen Team vereinen. Lernen Sie, wie Platform Engineering das Entwicklerleben leichter macht und Ihnen die Kontrolle zur├╝ckgibt.Top10 Characteristics of Awesome Apps



Top10 Characteristics of Awesome AppsCasey Lee
╠²
In this talk, you will hear the best practices from analysts at Gartner, engineers at Heroku, and experiences at VSP distilled down into a top ten list of characteristics that applications ought to have to achieve high availability, scalability and flexibility. Target audience includes developers of APIs and web-based applications, the analysts and architects that design them and the infrastructure teams that support them.Cncf checkov and bridgecrew



Cncf checkov and bridgecrewLibbySchulze
╠²
This document discusses a webinar about integrating infrastructure as code (IaC) security into the development lifecycle using Checkov. It notes that nearly half of open source Terraform and CloudFormation templates contain security issues. Checkov is introduced as an open source IaC scanning tool that supports multiple frameworks and cloud providers. The benefits of Checkov include lower remediation times, reduced security incidents, and simplifying compliance. Integrations with DevOps tools and the Cloud Native Application Platform Approach (CNAPP) are also discussed. A demo of Checkov is then shown including using it with VS Code and Azure DevOps.Backstage at CNCF Madison.pptx



Backstage at CNCF Madison.pptxBrandenTimm1
╠²
This document discusses Backstage, an open platform for building developer portals created by Spotify. It summarizes that Backstage unifies all tooling, services, apps, data and docs with a single consistent UI to make sense of a company's entire software ecosystem. It provides speed, chaos control and scalability. Backstage lets developers easily create and manage software, and explore their company's full software ecosystem to enable collaboration.Content Strategy and Developer Engagement for DevPortals



Content Strategy and Developer Engagement for DevPortalsAxway
╠²
║▌║▌▀Żs from Write the Docs Ottawa Meet Up at Shopify HQ in Canada, June 24, 2019
WeŌĆÖll walk through 5 scenarios and concrete ways of reaching a developer community for frictionless and increased engagement.Open Source IoT Project Flogo - Introduction, Overview and Architecture



Open Source IoT Project Flogo - Introduction, Overview and ArchitectureKai W├żhner
╠²
Go-powered Open Source Project Flogo for Lightweight IoT and Edge Integration:
The Internet of Things (IoT) brings up 50 billion devices until 2020, which have to be connected somehow. Challenges include low bandwidth, high latency, non-reliable connectivity and the need for low network costs. Therefore, a gateway at the edge is needed remotely on site of the devices to filter, aggregate and send just relevant data into the cloud or data center.
This session introduces open source project Flogo, which allows developing ultra-lightweight IoT edge applications with a zero-coding web user interface. Coders can also rely just on Go code if they want. It is written in Go programming language and therefore 20-50x more lightweight than similar Java or JavaScript frameworks.
The session focuses on live demos and shows how to develop ultra-lightweight microservices and how to integrate IoT devices using standards such as MQTT, WebSockets, CoaP or REST. The last part of the session compares Project Flogo to other open source IoT projects like Eclipse Kura or Node-RED and cloud offerings such as AWS IoT.
Check out www.flogo.io and https://community.tibco.com/products/project-flogo for more information and community.
Dev{sec}ops



Dev{sec}opsSteven Carlson
╠²
Keeping security top of mind while creating standards for engineering teams following the DevOps culture. This talk was designed to show off how easily it is to automate security scanning and to be the developer advocate by showing the quality of development work. We will cover some high-level topics of DevSecOps and demo some examples DevOps team can implement for free.More from Anshul Patel (12)
Open Source Identity and Access management with Keycloak.pdf



Open Source Identity and Access management with Keycloak.pdfAnshul Patel
╠²
My meetup talk provides introduction to keycloak and how it can be
leveraged for identity and access management.Chaos engineering with Litmus Chaos Framework



Chaos engineering with Litmus Chaos FrameworkAnshul Patel
╠²
Chaos engineering introduces failures into systems to test resilience. Litmus Chaos is an open source chaos engineering framework from Mayadata that allows injecting chaos into Kubernetes clusters. It includes a chaos operator, experiments, and engine to run experiments declaratively. Currently it supports experiments for services like OpenEBS, Cassandra, and Kafka.Docker Fundamentals



Docker FundamentalsAnshul Patel
╠²
The document provides an overview of Docker fundamentals, including what Docker is, its architecture, common operations, and advantages. It begins by explaining that Docker is a container technology that packages code and dependencies together. Containers run atop the same OS kernel and utilize fewer system resources than virtual machines. The document then describes Docker's client-server architecture and underlying technologies like namespaces and cgroups that enable isolation. It also outlines common Docker commands and explains that Dockerfiles define container configurations.Chaos Engineering with Gremlin Platform



Chaos Engineering with Gremlin PlatformAnshul Patel
╠²
Chaos Engineering is a practice of experimenting on a system to evaluate its resilience by intentionally introducing failures. Gremlin is a failure/resiliency as a service platform that can safely simulate real world outages through various failure vectors at the infrastructure and application layers. It has a client-server architecture with clients installed in the infrastructure or applications to communicate with the Gremlin platform. Gremlin supports failure injection scenarios that can be triggered on demand or scheduled, and stores results and history.Chaos Engineering



Chaos EngineeringAnshul Patel
╠²
This document provides an overview of chaos engineering, including what it is, how it differs from testing, how to design chaos experiments, and what chaos lambda is. Specifically, it explains that chaos engineering involves intentionally introducing failures into systems to test their resilience and identify weaknesses, unlike testing which checks for known issues. It also outlines the steps to design chaos experiments and describes chaos lambda as an open source tool from the BBC to simulate EC2 instance failures in auto scaling groups.Introduction to docker_notary_v1.0.0



Introduction to docker_notary_v1.0.0Anshul Patel
╠²
This document provides an introduction to Docker Notary service. It explains that Notary provides trust for digital content by signing and verifying updates. It ensures the integrity and freshness of software and protects against threats like compromised keys or spoofed updates. The key components of Notary include clients, servers, signers and databases. Notary is integrated with Docker Content Trust to sign images when they are pushed to repositories, establishing trust for users interacting with those images.Linux Operating System Fundamentals



Linux Operating System FundamentalsAnshul Patel
╠²
This document provides an overview of key Linux operating system fundamentals including: the Linux boot process; systemctl for managing services; process and memory management; filesystems; package management; kernel parameters; and shells. It outlines several common Linux directories and filesystem concepts. The document also describes process types in Linux and different types of memory. It discusses mounting, unmounting, and formatting filesystems as well as inodes. Linux package management topics such as repositories, installing, removing, updating, and listing packages are covered. Finally, it briefly discusses shells, shell profiles, environment variables, and popular shell types in Linux.Building CLI Applications with Golang



Building CLI Applications with GolangAnshul Patel
╠²
The document discusses developing command line interface (CLI) applications with Golang. It notes that Golang is well-suited for CLI apps due to its cross-platform compilation, ability to statically link dependencies into a single binary, and comparable execution performance to C/C++. Popular CLI frameworks for Golang include Cobra, urfave/cli, docopt/docopt.go, and mitchellh/cli. The document outlines common CLI structures like subcommands, flags, and arguments, and benefits of using a CLI framework like generating help documentation and POSIX compliant flags.Linux kit meetup_v1.0.0



Linux kit meetup_v1.0.0Anshul Patel
╠²
LinuxKit is a toolkit for building secure, portable, and lean container-based operating systems. It builds the entire OS using containers, with all OS services contained within pluggable containers. The OS is built declaratively using Moby tools and a YAML configuration file to specify components like the kernel, initialization services, long-running processes, files to copy, and trusted components. This approach creates immutable, cryptographically verified OS images with minimal components and privileges for improved security and reliability.Cloud Computing Security



Cloud Computing SecurityAnshul Patel
╠²
This document discusses security considerations for cloud computing instances, networking, and storage. It recommends using bastion servers for CLI access with key-based authentication over secure protocols. For instances, it suggests using LTS OS releases, security patches, and HIDS for critical hosts. Networking advice includes using subnets for applications, public subnets only for public-facing systems, and private subnets with NAT for non-public systems. The document also recommends encrypting sensitive stored data with role-based access controls and logging, and storing authentication materials securely.Meetup on Apache Zookeeper



Meetup on Apache ZookeeperAnshul Patel
╠²
Zookeeper is a distributed coordination service that provides naming, configuration, synchronization, and group services. It allows distributed processes to coordinate with each other through a shared hierarchical namespace of data registers called znodes. Zookeeper follows a leader-elected consensus protocol to guarantee atomic broadcast of state updates from the leader to followers. It uses a hierarchical namespace of znodes similar to a file system to store configuration data and other application-defined metadata. Zookeeper provides services like leader election, group membership, synchronization, and configuration management that are essential for distributed systems.AWS ECS Meetup Talentica



AWS ECS Meetup TalenticaAnshul Patel
╠²
This document discusses Docker containers and Amazon ECS container management. It defines what Docker containers are, why they are used, and why a container cluster management system is needed. It then explains what Amazon ECS is, including its key components like clusters, instances, tasks, and services. It describes how ECS manages the lifecycle of containers across a cluster of EC2 instances and provides high scalability and availability. Finally, it covers some advantages of ECS, challenges to consider, and default resource limits.Recently uploaded (20)
Inside Freshworks' Migration from Cassandra to ScyllaDB by Premkumar Patturaj



Inside Freshworks' Migration from Cassandra to ScyllaDB by Premkumar PatturajScyllaDB
╠²
Freshworks migrated from Cassandra to ScyllaDB to handle growing audit log data efficiently. Cassandra required frequent scaling, complex repairs, and had non-linear scaling. ScyllaDB reduced costs with fewer machines and improved operations. Using Zero Downtime Migration (ZDM), they bulk-migrated data, performed dual writes, and validated consistency.Understanding Traditional AI with Custom Vision & MuleSoft.pptx



Understanding Traditional AI with Custom Vision & MuleSoft.pptxshyamraj55
╠²
Understanding Traditional AI with Custom Vision & MuleSoft.pptx | ### ║▌║▌▀Ż Deck Description:
This presentation features Atul, a Senior Solution Architect at NTT DATA, sharing his journey into traditional AI using Azure's Custom Vision tool. He discusses how AI mimics human thinking and reasoning, differentiates between predictive and generative AI, and demonstrates a real-world use case. The session covers the step-by-step process of creating and training an AI model for image classification and object detectionŌĆöspecifically, an ad display that adapts based on the viewer's gender. Atulavan highlights the ease of implementation without deep software or programming expertise. The presentation concludes with a Q&A session addressing technical and privacy concerns.Early Adopter's Guide to AI Moderation (Preview)



Early Adopter's Guide to AI Moderation (Preview)nick896721
╠²
Early Adopter's Guide to AI Moderation preview by User Interviews.Computational Photography: How Technology is Changing Way We Capture the World



Computational Photography: How Technology is Changing Way We Capture the WorldHusseinMalikMammadli
╠²
¤ōĖ Computational Photography (Computer Vision/Image): How Technology is Changing the Way We Capture the World
He├¦ d├╝┼¤├╝nm├╝s├╝n├╝zm├╝, m├╝asir smartfonlar v╔Ö kameralar nec╔Ö bu q╔Öd╔Ör g├Čz╔Öl g├Čr├╝nt├╝l╔Ör yarad─▒r? Bunun sirri Computational Fotoqrafiyas─▒nda(Computer Vision/Imaging) gizlidirŌĆö┼¤╔Ökill╔Öri ├¦╔Ökm╔Ö v╔Ö emal etm╔Ö ├╝sulumuzu t╔Ökmill╔Ö┼¤dir╔Ön, komp├╝ter elmi il╔Ö fotoqrafiyan─▒n inqilabi birl╔Ö┼¤m╔Ösi.UiPath Automation Developer Associate Training Series 2025 - Session 2



UiPath Automation Developer Associate Training Series 2025 - Session 2DianaGray10
╠²
In session 2, we will introduce you to Data manipulation in UiPath Studio.
Topics covered:
Data Manipulation
What is Data Manipulation
Strings
Lists
Dictionaries
RegEx Builder
Date and Time
Required Self-Paced Learning for this session:
Data Manipulation with Strings in UiPath Studio (v2022.10) 2 modules - 1h 30m - https://academy.uipath.com/courses/data-manipulation-with-strings-in-studio
Data Manipulation with Lists and Dictionaries in UiPath Studio (v2022.10) 2 modules - 1h - https:/academy.uipath.com/courses/data-manipulation-with-lists-and-dictionaries-in-studio
Data Manipulation with Data Tables in UiPath Studio (v2022.10) 2 modules - 1h 30m - https:/academy.uipath.com/courses/data-manipulation-with-data-tables-in-studio
Ōüē’ĖÅ For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. A Framework for Model-Driven Digital Twin Engineering



A Framework for Model-Driven Digital Twin EngineeringDaniel Lehner
╠²
║▌║▌▀Żs from my PhD Defense at Johannes Kepler University, held on Janurary 10, 2025.
The full thesis is available here: https://epub.jku.at/urn/urn:nbn:at:at-ubl:1-83896Backstage Software Templates for Java Developers



Backstage Software Templates for Java DevelopersMarkus Eisele
╠²
As a Java developer you might have a hard time accepting the limitations that you feel being introduced into your development cycles. Let's look at the positives and learn everything important to know to turn Backstag's software templates into a helpful tool you can use to elevate the platform experience for all developers.Unlock AI Creativity: Image Generation with DALL┬ĘE



Unlock AI Creativity: Image Generation with DALL┬ĘEExpeed Software
╠²
Discover the power of AI image generation with DALL┬ĘE, an advanced AI model that transforms text prompts into stunning, high-quality visuals. This presentation explores how artificial intelligence is revolutionizing digital creativity, from graphic design to content creation and marketing. Learn about the technology behind DALL┬ĘE, its real-world applications, and how businesses can leverage AI-generated art for innovation. Whether you're a designer, developer, or marketer, this guide will help you unlock new creative possibilities with AI-driven image synthesis.UiPath Agentic Automation Capabilities and Opportunities



UiPath Agentic Automation Capabilities and OpportunitiesDianaGray10
╠²
Learn what UiPath Agentic Automation capabilities are and how you can empower your agents with dynamic decision making. In this session we will cover these topics:
What do we mean by Agents
Components of Agents
Agentic Automation capabilities
What Agentic automation delivers and AI Tools
Identifying Agent opportunities
ŌØō If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.Revolutionizing-Government-Communication-The-OSWAN-Success-Story



Revolutionizing-Government-Communication-The-OSWAN-Success-Storyssuser52ad5e
╠²
¤īÉ ØŚóØŚ”ØŚ¬ØŚöØŚĪ ØŚ”ØśéØŚ░ØŚ░ØŚ▓ØśĆØśĆ ØŚ”ØśüØŚ╝ØŚ┐Øśå ¤ÜĆ
ØŚóØŚ║ØŚ╗ØŚČØŚ╣ØŚČØŚ╗ØŚĖ ØŚ¦ØŚ▓ØŚ░ØŚĄØŚ╗ØŚ╝ØŚ╣ØŚ╝ØŚ┤Øśå╠² is proud to be a part of the ØŚóØŚ▒ØŚČØśĆØŚĄØŚ« ØŚ”ØśüØŚ«ØśüØŚ▓ ØŚ¬ØŚČØŚ▒ØŚ▓ ØŚöØŚ┐ØŚ▓ØŚ« ØŚĪØŚ▓ØśüØśäØŚ╝ØŚ┐ØŚĖ (ØŚóØŚ”ØŚ¬ØŚöØŚĪ) success story! By delivering seamless, secure, and high-speed connectivity, OSWAN has revolutionized e-ØŚÜØŚ╝ØśāØŚ▓ØŚ┐ØŚ╗ØŚ«ØŚ╗ØŚ░ØŚ▓ ØŚČØŚ╗ ØŚóØŚ▒ØŚČØśĆØŚĄØŚ«, enabling efficient communication between government departments and enhancing citizen services.
Through our innovative solutions, ØŚóØŚ║ØŚ╗ØŚČØŚ╣ØŚČØŚ╗ØŚĖ ØŚ¦ØŚ▓ØŚ░ØŚĄØŚ╗ØŚ╝ØŚ╣ØŚ╝ØŚ┤Øśå has contributed to making governance smarter, faster, and more transparent. This milestone reflects our commitment to driving digital transformation and empowering communities.
¤ōĪ ØŚ¢ØŚ╝ØŚ╗ØŚ╗ØŚ▓ØŚ░ØśüØŚČØŚ╗ØŚ┤ ØŚóØŚ▒ØŚČØśĆØŚĄØŚ«, ØŚśØŚ║ØŚĮØŚ╝ØśäØŚ▓ØŚ┐ØŚČØŚ╗ØŚ┤ ØŚÜØŚ╝ØśāØŚ▓ØŚ┐ØŚ╗ØŚ«ØŚ╗ØŚ░ØŚ▓!
MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
╠²
MIND Revenue Release Quarter 4 2024 - Finacial PresentationThe Future of Repair: Transparent and Incremental by Botond Dénes



The Future of Repair: Transparent and Incremental by Botond DénesScyllaDB
╠²
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.Both Feet on the Ground - Generative Artificial Intelligence



Both Feet on the Ground - Generative Artificial IntelligencePete Nieminen
╠²
High-level presentation for executives and board professionals about Generative AI, its current uses and governance models.[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
[Webinar] Scaling Made Simple: Getting Started with No-Code Web AppsSafe Software
╠²
Ready to simplify workflow sharing across your organization without diving into complex coding? With FME Flow Apps, you can build no-code web apps that make your data work harder for you ŌĆö fast.
In this webinar, weŌĆÖll show you how to:
Build and deploy Workspace Apps to create an intuitive user interface for self-serve data processing and validation.
Automate processes using Automation Apps. Learn to create a no-code web app to kick off workflows tailored to your needs, trigger multiple workspaces and external actions, and use conditional filtering within automations to control your workflows.
Create a centralized portal with Gallery Apps to share a collection of no-code web apps across your organization.
Through real-world examples and practical demos, youŌĆÖll learn how to transform your workflows into intuitive, self-serve solutions that empower your team and save you time. We canŌĆÖt wait to show you whatŌĆÖs possible!Technology use over time and its impact on consumers and businesses.pptx



Technology use over time and its impact on consumers and businesses.pptxkaylagaze
╠²
In this presentation, I explore how technology has changed consumer behaviour and its impact on consumers and businesses. I will focus on internet access, digital devices, how customers search for information and what they buy online, video consumption, and lastly consumer trends.UiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
╠²
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
Ōüē’ĖÅ For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Cloud of everything Tech of the 21 century in Aviation



Cloud of everything Tech of the 21 century in AviationAssem mousa
╠²
AI, Block chain, Digital Currency, Cloud, Cloud of Things, Tactile Internet, Digital Twins, IOT, AR, VR, MR, U commerce, data and robotics."
Future-Proof Your Career with AI Options



Future-Proof Your Career with AI OptionsDianaGray10
╠²
Learn about the difference between automation, AI and agentic and ways you can harness these to further your career. In this session you will learn:
Introduction to automation, AI, agentic
Trends in the marketplace
Take advantage of UiPath training and certification
In demand skills needed to strategically position yourself to stay ahead
ŌØō If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.Computational Photography: How Technology is Changing Way We Capture the World



Computational Photography: How Technology is Changing Way We Capture the WorldHusseinMalikMammadli
╠²
Safeguarding Container Supply Chain - Anshul Patel
- 1. Safeguarding Container Supply Chain Docker Meetup Ahmedabad - August 31, 2024 Anshul Patel
- 2. Who am I? Anshul Patel Cloud Consultant at Toptal Decade of experience in architecting, implementing, and optimizing cloud infrastructure, site-reliability, and operations to maximize the business value. Previously worked at Adani, Woven by Toyota, Infostretch(now Apexon), Talentica, Amdocs, Elitecore(now Sterlite Tech) https://anshulpatel.in
- 3. Agenda ŌŚÅ What is Software Supply Chain? ŌŚÅ Supply Chain Threats ŌŚÅ What is Supply Chain levels for Software Artifacts (SLSA)? ŌŚÅ How SLSA establishes trust? ŌŚÅ SLSA Levels ŌŚÅ What is Software Bill of Materials(SBOM)? ŌŚÅ Why SBOM? ŌŚÅ Questions?
- 4. What is Software Supply Chain? ŌŚÅ Software supply chain is how organizations publish their artifacts ŌŚÅ Modern Software Applications are no longer completely built from custom code ŌŚÅ Modern Software Applications are 85% dependent on Open Source, third party libraries Technical Source Code Con’¼ügurations Dependencies Build Environment Packages Functional People Process Policy Vendors What are parts of Software Supply Chain?
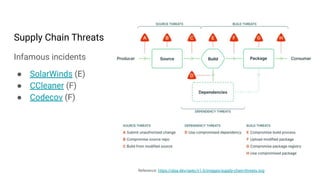
- 5. Supply Chain Threats Infamous incidents ŌŚÅ SolarWinds (E) ŌŚÅ CCleaner (F) ŌŚÅ Codecov (F) Reference: https://slsa.dev/spec/v1.0/images/supply-chain-threats.svg
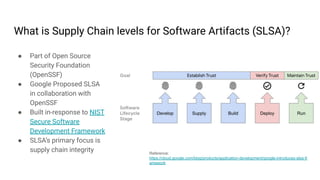
- 6. What is Supply Chain levels for Software Artifacts (SLSA)? ŌŚÅ Part of Open Source Security Foundation (OpenSSF) ŌŚÅ Google Proposed SLSA in collaboration with OpenSSF ŌŚÅ Built in-response to NIST Secure Software Development Framework ŌŚÅ SLSAŌĆÖs primary focus is supply chain integrity Reference: https://cloud.google.com/blog/products/application-development/google-introduces-slsa-fr amework
- 7. How SLSA establishes trust?
- 8. How SLSA establishes trust? Reference: https://www.sigstore.dev/how-it-works
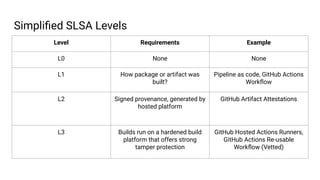
- 9. Simpli’¼üed SLSA Levels Level Requirements Example L0 None None L1 How package or artifact was built? Pipeline as code, GitHub Actions Work’¼éow L2 Signed provenance, generated by hosted platform GitHub Artifact Attestations L3 Builds run on a hardened build platform that offers strong tamper protection GitHub Hosted Actions Runners, GitHub Actions Re-usable Work’¼éow (Vetted)
- 10. What is Software Bill of Materials (SBOM)? ŌŚÅ Concept is derived from manufacturing domain where bill of materials lists items within the manufactured product ŌŚÅ In Software Industry ŌŚŗ Lists open source and third party components ŌŚŗ Lists the version of components ŌŚŗ Lists the license information of components ŌŚÅ Modern Software Composition Analysis tools can produce SBOM ŌŚŗ For e.g. Trivy, Syft ŌŚÅ Popular SBOM formats ŌŚŗ SPDX, developed by The Linux Foundation ŌŚŗ CycloneDX, developed by the Open Worldwide Application Security Project (OWASP)
- 11. Why SBOM? ŌŚÅ Identify vulnerabilities ŌŚÅ License compliance ŌŚÅ Mitigate software supply chain risks ŌŚÅ Qualify vendors ŌŚÅ Risk Management
- 12. Questions? ’¼ün



