An Overview of mRATs
0 likes1,067 views
This document provides an overview of mobile remote access trojans (mRATs) and targeted mobile attacks. It discusses how mRATs can snoop on corporate emails and data, eavesdrop, extract contact lists and location information, and infiltrate internal networks. The document describes high-end government/military-grade mRATs, mid-range cybercrime toolkits, and lower-end commercial surveillance toolkits. Real-life statistics from a survey of 650,000 devices within a cellular network of 2 million subscribers in June 2013 showed an infection rate of 1 in 1,000 devices. The document concludes by stating that mobile device management solutions do not address this threat.
1 of 28
Downloaded 15 times




















Ad
Recommended
FaceTime Web 2.0
FaceTime Web 2.0Chris Sparshott
╠²
The document discusses how the internet has become more complex with the rise of unified communications, collaboration tools, and social networking. It notes that information leakage is a top concern for IT professionals. The document also outlines requirements for securely enabling new internet applications, including visibility and control of real-time apps, comprehensive malware protection, and granular policy enforcement. FaceTime's unified security gateway aims to meet these requirements through application identification, inspection, policy enforcement, and archiving capabilities.Fintech Cyber Security Survey Hong Knog 2018
Fintech Cyber Security Survey Hong Knog 2018Entersoft Security
╠²
This survey of over 100 Hong Kong fintech companies in 2017-2018 found that:
- A majority had medium cybersecurity risks with scores over 6000 but below 8000.
- Over 1/3 had not configured SPF and over 3/4 had not configured DKIM or DMARC, leaving them vulnerable to phishing.
- 70% had not set up a privacy policy or terms page on their site, risking noncompliance with GDPR.
- 42% were susceptible to the CRIME SSL vulnerability and under 7% to POODLE, showing risks from outdated encryption.
- Over half had vulnerabilities like lack of XSS protection, WAF, or HTTPS that could enable attacks.Why Organisations Need_Barac
Why Organisations Need_BaracBarac
╠²
Barac, established in 2017, provides an Encrypted Traffic Visibility (ETV) solution that detects malicious activity within encrypted network traffic without decryption. Their method uses AI to analyze metadata from over 200 metrics, achieving high accuracy and minimal false positives, while responding rapidly to threats such as ransomware and malware. Recognized by industry organizations, Barac's innovative platform aims to enhance network security against the rising challenges posed by encryption used by cyber criminals.The Quarantine Report: Cybersecurity Impact Assessment for COVID-19
The Quarantine Report: Cybersecurity Impact Assessment for COVID-19Alex Smirnoff
╠²
The document provides a cybersecurity impact assessment of the COVID-19 outbreak. It finds that while the work from home shift has changed the attack surface, there is no clear evidence of a significant outbreak of cyber attacks. However, cybercriminals are exploiting COVID-19 in social engineering and phishing attacks. VPN and RDP usage has increased to enable remote work but these protocols have ongoing security issues. The document recommends adopting a zero trust approach and improving security awareness as a long term strategy.Amphion Forum 2013: What to Do About Attacks Against MDMs
Amphion Forum 2013: What to Do About Attacks Against MDMsLacoon Mobile Security
╠²
The document discusses popular mobile device management (MDM) solutions and presents methods for attacking them. It begins with an agenda covering personal data, private information, and digital safety. The presentation then outlines how to hack enterprise data on mobile devices in 12 hours for $1000 by infecting a device, installing a backdoor, and bypassing containerization. It also demonstrates commercial mobile surveillance tools and rates of cellular network infection. The document concludes by describing Lacoon's behavior-based mobile security solution to detect and mitigate these kinds of attacks."Bleeding-In-The-Browser" - Why reverse Heartbleed risk is dangerous to the E...
"Bleeding-In-The-Browser" - Why reverse Heartbleed risk is dangerous to the E...Lacoon Mobile Security
╠²
The document outlines the 'bleeding-in-the-browser' attack scenario where an attacker uses phishing emails to lure victims into accessing a malicious HTML page that exploits the Heartbleed vulnerability to capture sensitive data from their browser. The attack operates by opening a hidden tab that logs user credentials while refreshing regularly to extract data from the Android browser heap. To protect against such attacks, the document suggests mapping risks, enabling two-factor authentication, and utilizing specific tracking tools for mobile vulnerabilities.Mobile Threats: Enterprises Under Attack
Mobile Threats: Enterprises Under AttackLacoon Mobile Security
╠²
Enterprise mobile devices are increasingly being targeted by advanced persistent threats seeking sensitive corporate data. A joint research study by Lacoon Mobile Security and Check Point found that attackers are developing new techniques like exploiting vulnerabilities in mobile apps and enterprise mobile management systems to infiltrate organizations. The report recommends enterprises strengthen mobile security by implementing mobile threat defense solutions, enforcing strong access controls and policies, and ensuring devices and apps are regularly patched and updated.Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...
Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...Lacoon Mobile Security
╠²
This document discusses practical attacks against virtual desktop infrastructure (VDI) solutions. It begins with introductions to the presenters and an overview of mobile VDI. It then outlines four threats: 1) using a remote access Trojan to keylog credentials, 2) directly grabbing credentials from an Android device, 3) screen scraping on Android, and 4) man-in-the-middle session hijacking on iOS. It argues that a layered mobile security approach is needed to protect VDI, including device assessment, reducing attack surfaces, threat detection, and risk mitigation.Remote Access Trojans (RATs): The Silent Invaders of Cybersecurity
Remote Access Trojans (RATs): The Silent Invaders of CybersecurityMaryJWilliams2
╠²
Remote Access Trojans (RATs) are sophisticated malware that allow unauthorized remote access and control over systems, posing a significant threat to cybersecurity. They employ various infiltration methods, such as phishing emails and exploiting software vulnerabilities, leading to data theft, system manipulation, and further cyberattacks. A strategic multi-layered defense, user education, and advanced endpoint protection are crucial for preventing and mitigating RAT attacks.Malware on Smartphones and Tablets - The Inconvenient Truth
Malware on Smartphones and Tablets - The Inconvenient TruthAGILLY
╠²
The document discusses the increasing threat of mobile malware on smartphones and tablets, highlighting various malware types and attack vectors for both iOS and Android devices. It emphasizes the security concerns faced by customers and enterprises, particularly in the banking sector, and outlines the role of IBM's Maas360 and Trusteer products in detecting and managing these threats. The document also provides insights on the implications of these threats, urging organizations to adopt a layered security approach for mobile device management.Ms810 assignment viruses and malware affecting moblie devices
Ms810 assignment viruses and malware affecting moblie devicesrebelreg
╠²
Mobile malware attacks increased 185% in 2012, primarily targeting Android devices. Android is vulnerable because it has the largest market share (75%) and allows any developer to post apps to the Google Play Store. It is also slow to fix detected security flaws. Recent malware has stolen SMS messages, call logs, contacts, bank details, and other sensitive data. To protect against malware, organizations should implement security policies while individual users should install antivirus software and avoid suspicious links and WiFi networks. Mobile security risks are expected to rise as users and devices become more prevalent.Pagajdhvdhdhdvhdhdhdhdhhdhdududhjdjdjdjdjdj
PagajdhvdhdhdvhdhdhdhdhhdhdududhjdjdjdjdjdjVAIBHAVSAHU55
╠²
The document summarizes a seminar presentation on remote access trojans (RATs). It defines RATs as malware that allows attackers to remotely control victims' computers without their knowledge. The presentation covers how RATs work, types of RATs, dangers of RATs including data and identity theft, examples of common RATs like Back Orifice and Blackshades, real-world cases of RAT usage, and methods for detecting and preventing RAT infections. The presentation concludes that RATs pose serious risks and detecting them requires multilayered defenses that are continuously updated.Research and discuss an incident where it was discovered that a Remo.pdf
Research and discuss an incident where it was discovered that a Remo.pdffathimafancy
╠²
A remote access trojan (RAT) infiltrated a corporate network by logging keystrokes of the general manager and exploiting vulnerabilities in the Windows operating system. It was detected after the company noticed unauthorized access and poor computer performance, prompting a forensic investigation that revealed extensive malware use. To prevent such incidents, employing virtualization techniques for malware analysis may help identify and mitigate RAT behavior more effectively.Trends in network security feinstein - informatica64
Trends in network security feinstein - informatica64Chema Alonso
╠²
The document summarizes trends in network security seen in 2009, including increases in vulnerabilities in document readers/editors like PDFs that were exploited by "spear phishing" attacks. Malware became more sophisticated with user-friendly banking trojans and rootkits distributed on legitimate websites. The "Aurora" attacks targeted Google and other companies in 2009 using zero-day exploits. The takedown of the Mariposa botnet in late 2009 arrested three individuals operating a commercial botnet kit.Third Annual Mobile Threats Report
Third Annual Mobile Threats ReportJuniper Networks
╠²
The Third Annual Mobile Threats Report from Juniper Networks highlights a dramatic increase in mobile malware, with a 614% rise in samples and concerns regarding the security of Android devices due to its fragmented ecosystem. The report indicates that malware targeting mobile devices is primarily focused on fake install apps, SMS trojans, and spyware, posing significant risks to enterprise data and privacy. Future trends suggest continued vulnerability in Android and rising issues with SMS fraud, necessitating robust security measures for mobile connectivity and device management.Mobile Malware
Mobile MalwareMartin Holovsk├Į
╠²
This document discusses mobile malware and how to protect against it. It begins by defining malware and listing common types. It then provides statistics on the distribution of mobile operating systems and malware detections. The document outlines sources of mobile malware infections and discusses why mobile devices contain sensitive information. It recommends implementing mobile device management to centrally manage devices and deploy security policies. Examples of recent mobile threats are also described. The document concludes by recommending security best practices like using antivirus software, updating devices, and educating users.Malware Applications Development.pptx
Malware Applications Development.pptxFullstackSRM
╠²
Malware can take many forms and negatively impact mobile devices. The document discusses malware types like ransomware, fileless malware, adware, spyware, Trojans, worms, viruses, rootkits, and keyloggers. It also describes how malware developers create mobile malware through techniques like repackaging common apps, dynamic payload injection, and privilege escalation. Examples of past smartphone malware like Cabir, DroidDream, and Flexispy are provided that underscore the ongoing threat.Net motion wireless-and_frost-sullivan_a-new-mobilty_ps
Net motion wireless-and_frost-sullivan_a-new-mobilty_psAccenture
╠²
The document discusses the rise of mobile field workers and remote work. It explores the evolving security landscape and threats facing remote workers. It then summarizes security solutions like mobile VPNs that can help secure access for remote workers. The document defines mobile VPNs and provides an analysis of the global mobile VPN market, noting that growth will be fueled by increasing wireless device usage and that the top vendors in the space are expected to be Cisco, Juniper, and NetMotion Wireless.Malware
MalwareSetiya Nugroho
╠²
This document provides an overview of malware topics that will be covered in a 4-week lecture series. It defines malware and describes common types including viruses, worms, trojans, ransomware, bots/botnets, adware, spyware, rootkits, and fileless malware. It explains how malware spreads and signs of infection. Methods of malware analysis, detection techniques, and creating a safe analysis environment are outlined. Potential malware sources and 5 cyber threat trends for 2022 are also summarized. The document concludes with 5 case studies examining real-world incidents involving supply chain attacks, account takeovers, out-of-hours attacks, lower barriers to entry for criminals, and new ransomware approaches.Report on Mobile security
Report on Mobile securityKavita Rastogi
╠²
The document discusses mobile security risks and trends. It outlines the anatomy of a mobile attack, including infection vectors, installing backdoors, and exfiltrating data. Key findings include the challenge of BYOD, lack of security in mobile apps, and employees unwittingly introducing threats via personal devices. The OWASP Mobile Top 10 risks framework classifies common vulnerabilities such as improper platform usage, insecure data storage, weak authentication, and code tampering. Overall, the growth of mobile devices and lack of awareness regarding mobile security hygiene has introduced significant risks that organizations must address.Him
HimHimanshu Kumar Paswan
╠²
This document discusses security threats to smartphones from viruses and malware. It begins by explaining how smartphones are essentially pocket computers that can be infected similarly to computers, though through different transmission methods like Bluetooth, MMS, and internet downloads. It then provides examples of some of the first mobile viruses and worms, such as Cabir and ComWar, and how they spread. The document outlines various types of mobile threats including unwanted messaging or information theft. It concludes by offering some protective measures like locking down Bluetooth, password protecting SIM cards, and avoiding phishing attempts or giving out private information over calls or online.Anatomy of a cyber attack
Anatomy of a cyber attackMark Silver
╠²
The document, created by Mark Silver, outlines the anatomy of a cyber attack, detailing the five steps attackers typically follow: reconnaissance, infiltration, malware deployment, data extraction, and cleanup. It emphasizes the importance of understanding these attack steps for organizations and advocates for robust security measures, including risk management and a strong focus on information security at all levels of the organization. The author draws on extensive experience in IT and security, providing insights and engaging references to bolster understanding of cyber threats and defenses.ISACA CACS 2012 - Mobile Device Security and Privacy
ISACA CACS 2012 - Mobile Device Security and PrivacyMichael Davis
╠²
This document discusses trends in social media and mobile security. It notes that mobility and use of personal devices for work is increasing rapidly, bringing new security challenges. Mobile devices face security risks at the network, hardware, operating system and application layers. The document outlines common types of malicious mobile applications and vulnerabilities they may exploit, including monitoring user activity and stealing private data. It emphasizes the importance of securing sensitive data through encryption and access controls on mobile devices and applications. The document recommends organizations form mobility councils to develop mobile security policies and consider mobile device management solutions to help address security risks from increased mobility.cellphone virus and security
cellphone virus and securityAkhil Kumar
╠²
The document discusses threats from mobile malware and viruses and provides strategies for protecting smartphones. It notes that as smartphones have become pocket computers, they are now susceptible to many of the same threats as computers like viruses, worms and trojans. These threats can spread via the internet, Bluetooth, MMS and more. The document then examines some specific examples of early mobile viruses and worms. It concludes by recommending security best practices like using passcodes, enabling auto-lock, being wary of Bluetooth and downloads, and maintaining awareness of social engineering threats.Top 2016 Mobile Security Threats and your Employees
Top 2016 Mobile Security Threats and your EmployeesNeil Kemp
╠²
The document outlines the top mobile security threats of 2016, highlighting that many users do not secure their smartphones, which are vulnerable to hacking, malvertising, and grayware. It emphasizes the risks posed by employees, including internal threats and the misuse of unsecured Wi-Fi, as mobile transactions and data transfers increase. Key threats include mobile web browser hacking, man-in-the-middle attacks, and distributed denial-of-service attacks, particularly within corporate networks and the healthcare sector.White Paper: Defense In Breadth
White Paper: Defense In BreadthCourtland Smith
╠²
The document discusses how traditional defense-in-depth security strategies are no longer sufficient due to the expanding attack surface from growing device, network, threat, and vector breadth. As devices become more mobile and networks more complex, attackers have more opportunities. Existing security products also lack the ability to provide comprehensive protection across all devices, locations, and protocols. The document argues that a new "defense-in-breadth" approach is needed using a cloud-based security gateway to regain visibility and control across the entire attack surface.Mobile Protect Pro - Powered by Zimperium
Mobile Protect Pro - Powered by ZimperiumZimperium
╠²
By 2018, 25% of corporate data traffic will bypass security controls as it flows from mobile devices to the cloud, leading to significant digital security risks. By 2020, IT security teams may fail to manage these risks, resulting in major service failures for 60% of digital businesses. The document outlines various threats to mobile enterprise devices, including network-based and app-based vulnerabilities, and discusses the importance of comprehensive mobile security solutions.The Current State of Cybercrime 2013
The Current State of Cybercrime 2013EMC
╠²
The 2013 white paper on cybercrime discusses the evolving landscape of cyber threats, highlighting trends such as the rise of mobile-related cybercrime and the privatization of banking trojans. Cybercriminals are increasingly targeting mobile transactions and exploiting vulnerabilities in mobile apps, while hacktivism is on the rise as individuals and groups use cyber means to express political and social dissent. The RSA Anti-Fraud Command Center anticipates continued growth in these areas, posing significant challenges for organizations trying to protect against these threats.iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation
iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
╠²
The document discusses the threats posed by malicious configuration profiles on iOS devices, detailing how attackers can exploit social engineering tactics to compromise device settings. It highlights the need for advanced security measures, such as Lacoon's MobileFortress, which offers capabilities like jailbreak detection, configuration profile analysis, and man-in-the-middle attack mitigation. The document emphasizes the importance of identifying suspicious traffic and maintaining control over compromised settings through a centralized dashboard.MobileCON 2013 ŌĆō Attacks Aginst MDM Solutions (and What You Can Do About It)
MobileCON 2013 ŌĆō Attacks Aginst MDM Solutions (and What You Can Do About It)Lacoon Mobile Security
╠²
This document summarizes an anatomy of a targeted attack against mobile device management (MDM) solutions and discusses mitigation techniques. It begins with an overview of how the corporate perimeter has collapsed due to bring your own device policies. It then demonstrates how attackers can infect a device, install backdoors to gain administrative privileges, bypass MDM containerization, and exfiltrate information. Current MDM and security solutions fail to adequately protect against these attacks. The document proposes adding behavioral analysis of applications and devices along with vulnerability assessments to better detect threats. It promotes the solutions from Lacoon Mobile Security to help stop these mobile attacks.More Related Content
Similar to An Overview of mRATs (20)
Remote Access Trojans (RATs): The Silent Invaders of Cybersecurity
Remote Access Trojans (RATs): The Silent Invaders of CybersecurityMaryJWilliams2
╠²
Remote Access Trojans (RATs) are sophisticated malware that allow unauthorized remote access and control over systems, posing a significant threat to cybersecurity. They employ various infiltration methods, such as phishing emails and exploiting software vulnerabilities, leading to data theft, system manipulation, and further cyberattacks. A strategic multi-layered defense, user education, and advanced endpoint protection are crucial for preventing and mitigating RAT attacks.Malware on Smartphones and Tablets - The Inconvenient Truth
Malware on Smartphones and Tablets - The Inconvenient TruthAGILLY
╠²
The document discusses the increasing threat of mobile malware on smartphones and tablets, highlighting various malware types and attack vectors for both iOS and Android devices. It emphasizes the security concerns faced by customers and enterprises, particularly in the banking sector, and outlines the role of IBM's Maas360 and Trusteer products in detecting and managing these threats. The document also provides insights on the implications of these threats, urging organizations to adopt a layered security approach for mobile device management.Ms810 assignment viruses and malware affecting moblie devices
Ms810 assignment viruses and malware affecting moblie devicesrebelreg
╠²
Mobile malware attacks increased 185% in 2012, primarily targeting Android devices. Android is vulnerable because it has the largest market share (75%) and allows any developer to post apps to the Google Play Store. It is also slow to fix detected security flaws. Recent malware has stolen SMS messages, call logs, contacts, bank details, and other sensitive data. To protect against malware, organizations should implement security policies while individual users should install antivirus software and avoid suspicious links and WiFi networks. Mobile security risks are expected to rise as users and devices become more prevalent.Pagajdhvdhdhdvhdhdhdhdhhdhdududhjdjdjdjdjdj
PagajdhvdhdhdvhdhdhdhdhhdhdududhjdjdjdjdjdjVAIBHAVSAHU55
╠²
The document summarizes a seminar presentation on remote access trojans (RATs). It defines RATs as malware that allows attackers to remotely control victims' computers without their knowledge. The presentation covers how RATs work, types of RATs, dangers of RATs including data and identity theft, examples of common RATs like Back Orifice and Blackshades, real-world cases of RAT usage, and methods for detecting and preventing RAT infections. The presentation concludes that RATs pose serious risks and detecting them requires multilayered defenses that are continuously updated.Research and discuss an incident where it was discovered that a Remo.pdf
Research and discuss an incident where it was discovered that a Remo.pdffathimafancy
╠²
A remote access trojan (RAT) infiltrated a corporate network by logging keystrokes of the general manager and exploiting vulnerabilities in the Windows operating system. It was detected after the company noticed unauthorized access and poor computer performance, prompting a forensic investigation that revealed extensive malware use. To prevent such incidents, employing virtualization techniques for malware analysis may help identify and mitigate RAT behavior more effectively.Trends in network security feinstein - informatica64
Trends in network security feinstein - informatica64Chema Alonso
╠²
The document summarizes trends in network security seen in 2009, including increases in vulnerabilities in document readers/editors like PDFs that were exploited by "spear phishing" attacks. Malware became more sophisticated with user-friendly banking trojans and rootkits distributed on legitimate websites. The "Aurora" attacks targeted Google and other companies in 2009 using zero-day exploits. The takedown of the Mariposa botnet in late 2009 arrested three individuals operating a commercial botnet kit.Third Annual Mobile Threats Report
Third Annual Mobile Threats ReportJuniper Networks
╠²
The Third Annual Mobile Threats Report from Juniper Networks highlights a dramatic increase in mobile malware, with a 614% rise in samples and concerns regarding the security of Android devices due to its fragmented ecosystem. The report indicates that malware targeting mobile devices is primarily focused on fake install apps, SMS trojans, and spyware, posing significant risks to enterprise data and privacy. Future trends suggest continued vulnerability in Android and rising issues with SMS fraud, necessitating robust security measures for mobile connectivity and device management.Mobile Malware
Mobile MalwareMartin Holovsk├Į
╠²
This document discusses mobile malware and how to protect against it. It begins by defining malware and listing common types. It then provides statistics on the distribution of mobile operating systems and malware detections. The document outlines sources of mobile malware infections and discusses why mobile devices contain sensitive information. It recommends implementing mobile device management to centrally manage devices and deploy security policies. Examples of recent mobile threats are also described. The document concludes by recommending security best practices like using antivirus software, updating devices, and educating users.Malware Applications Development.pptx
Malware Applications Development.pptxFullstackSRM
╠²
Malware can take many forms and negatively impact mobile devices. The document discusses malware types like ransomware, fileless malware, adware, spyware, Trojans, worms, viruses, rootkits, and keyloggers. It also describes how malware developers create mobile malware through techniques like repackaging common apps, dynamic payload injection, and privilege escalation. Examples of past smartphone malware like Cabir, DroidDream, and Flexispy are provided that underscore the ongoing threat.Net motion wireless-and_frost-sullivan_a-new-mobilty_ps
Net motion wireless-and_frost-sullivan_a-new-mobilty_psAccenture
╠²
The document discusses the rise of mobile field workers and remote work. It explores the evolving security landscape and threats facing remote workers. It then summarizes security solutions like mobile VPNs that can help secure access for remote workers. The document defines mobile VPNs and provides an analysis of the global mobile VPN market, noting that growth will be fueled by increasing wireless device usage and that the top vendors in the space are expected to be Cisco, Juniper, and NetMotion Wireless.Malware
MalwareSetiya Nugroho
╠²
This document provides an overview of malware topics that will be covered in a 4-week lecture series. It defines malware and describes common types including viruses, worms, trojans, ransomware, bots/botnets, adware, spyware, rootkits, and fileless malware. It explains how malware spreads and signs of infection. Methods of malware analysis, detection techniques, and creating a safe analysis environment are outlined. Potential malware sources and 5 cyber threat trends for 2022 are also summarized. The document concludes with 5 case studies examining real-world incidents involving supply chain attacks, account takeovers, out-of-hours attacks, lower barriers to entry for criminals, and new ransomware approaches.Report on Mobile security
Report on Mobile securityKavita Rastogi
╠²
The document discusses mobile security risks and trends. It outlines the anatomy of a mobile attack, including infection vectors, installing backdoors, and exfiltrating data. Key findings include the challenge of BYOD, lack of security in mobile apps, and employees unwittingly introducing threats via personal devices. The OWASP Mobile Top 10 risks framework classifies common vulnerabilities such as improper platform usage, insecure data storage, weak authentication, and code tampering. Overall, the growth of mobile devices and lack of awareness regarding mobile security hygiene has introduced significant risks that organizations must address.Him
HimHimanshu Kumar Paswan
╠²
This document discusses security threats to smartphones from viruses and malware. It begins by explaining how smartphones are essentially pocket computers that can be infected similarly to computers, though through different transmission methods like Bluetooth, MMS, and internet downloads. It then provides examples of some of the first mobile viruses and worms, such as Cabir and ComWar, and how they spread. The document outlines various types of mobile threats including unwanted messaging or information theft. It concludes by offering some protective measures like locking down Bluetooth, password protecting SIM cards, and avoiding phishing attempts or giving out private information over calls or online.Anatomy of a cyber attack
Anatomy of a cyber attackMark Silver
╠²
The document, created by Mark Silver, outlines the anatomy of a cyber attack, detailing the five steps attackers typically follow: reconnaissance, infiltration, malware deployment, data extraction, and cleanup. It emphasizes the importance of understanding these attack steps for organizations and advocates for robust security measures, including risk management and a strong focus on information security at all levels of the organization. The author draws on extensive experience in IT and security, providing insights and engaging references to bolster understanding of cyber threats and defenses.ISACA CACS 2012 - Mobile Device Security and Privacy
ISACA CACS 2012 - Mobile Device Security and PrivacyMichael Davis
╠²
This document discusses trends in social media and mobile security. It notes that mobility and use of personal devices for work is increasing rapidly, bringing new security challenges. Mobile devices face security risks at the network, hardware, operating system and application layers. The document outlines common types of malicious mobile applications and vulnerabilities they may exploit, including monitoring user activity and stealing private data. It emphasizes the importance of securing sensitive data through encryption and access controls on mobile devices and applications. The document recommends organizations form mobility councils to develop mobile security policies and consider mobile device management solutions to help address security risks from increased mobility.cellphone virus and security
cellphone virus and securityAkhil Kumar
╠²
The document discusses threats from mobile malware and viruses and provides strategies for protecting smartphones. It notes that as smartphones have become pocket computers, they are now susceptible to many of the same threats as computers like viruses, worms and trojans. These threats can spread via the internet, Bluetooth, MMS and more. The document then examines some specific examples of early mobile viruses and worms. It concludes by recommending security best practices like using passcodes, enabling auto-lock, being wary of Bluetooth and downloads, and maintaining awareness of social engineering threats.Top 2016 Mobile Security Threats and your Employees
Top 2016 Mobile Security Threats and your EmployeesNeil Kemp
╠²
The document outlines the top mobile security threats of 2016, highlighting that many users do not secure their smartphones, which are vulnerable to hacking, malvertising, and grayware. It emphasizes the risks posed by employees, including internal threats and the misuse of unsecured Wi-Fi, as mobile transactions and data transfers increase. Key threats include mobile web browser hacking, man-in-the-middle attacks, and distributed denial-of-service attacks, particularly within corporate networks and the healthcare sector.White Paper: Defense In Breadth
White Paper: Defense In BreadthCourtland Smith
╠²
The document discusses how traditional defense-in-depth security strategies are no longer sufficient due to the expanding attack surface from growing device, network, threat, and vector breadth. As devices become more mobile and networks more complex, attackers have more opportunities. Existing security products also lack the ability to provide comprehensive protection across all devices, locations, and protocols. The document argues that a new "defense-in-breadth" approach is needed using a cloud-based security gateway to regain visibility and control across the entire attack surface.Mobile Protect Pro - Powered by Zimperium
Mobile Protect Pro - Powered by ZimperiumZimperium
╠²
By 2018, 25% of corporate data traffic will bypass security controls as it flows from mobile devices to the cloud, leading to significant digital security risks. By 2020, IT security teams may fail to manage these risks, resulting in major service failures for 60% of digital businesses. The document outlines various threats to mobile enterprise devices, including network-based and app-based vulnerabilities, and discusses the importance of comprehensive mobile security solutions.The Current State of Cybercrime 2013
The Current State of Cybercrime 2013EMC
╠²
The 2013 white paper on cybercrime discusses the evolving landscape of cyber threats, highlighting trends such as the rise of mobile-related cybercrime and the privatization of banking trojans. Cybercriminals are increasingly targeting mobile transactions and exploiting vulnerabilities in mobile apps, while hacktivism is on the rise as individuals and groups use cyber means to express political and social dissent. The RSA Anti-Fraud Command Center anticipates continued growth in these areas, posing significant challenges for organizations trying to protect against these threats.More from Lacoon Mobile Security (7)
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation
iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
╠²
The document discusses the threats posed by malicious configuration profiles on iOS devices, detailing how attackers can exploit social engineering tactics to compromise device settings. It highlights the need for advanced security measures, such as Lacoon's MobileFortress, which offers capabilities like jailbreak detection, configuration profile analysis, and man-in-the-middle attack mitigation. The document emphasizes the importance of identifying suspicious traffic and maintaining control over compromised settings through a centralized dashboard.MobileCON 2013 ŌĆō Attacks Aginst MDM Solutions (and What You Can Do About It)
MobileCON 2013 ŌĆō Attacks Aginst MDM Solutions (and What You Can Do About It)Lacoon Mobile Security
╠²
This document summarizes an anatomy of a targeted attack against mobile device management (MDM) solutions and discusses mitigation techniques. It begins with an overview of how the corporate perimeter has collapsed due to bring your own device policies. It then demonstrates how attackers can infect a device, install backdoors to gain administrative privileges, bypass MDM containerization, and exfiltrate information. Current MDM and security solutions fail to adequately protect against these attacks. The document proposes adding behavioral analysis of applications and devices along with vulnerability assessments to better detect threats. It promotes the solutions from Lacoon Mobile Security to help stop these mobile attacks.IPExpo 2013 - Anatomy of a Targeted Attack Against MDM Solutions
IPExpo 2013 - Anatomy of a Targeted Attack Against MDM SolutionsLacoon Mobile Security
╠²
This document summarizes a presentation about targeted attacks against mobile device management (MDM) solutions. It discusses how the corporate perimeter has collapsed with bring-your-own-device policies. Mobile devices are attractive targets for threats like snooping on data and tracking locations. The presentation demonstrates how mobile malware can bypass MDM solutions by infecting devices, installing backdoors, and exfiltrating information despite containerization efforts. Current security solutions like MDM, wrappers, and network access control fail to fully protect against these attacks. Behavioral analysis of applications and devices, along with threat intelligence and vulnerability research, can help detection. The document promotes Lacoon Mobile Security as a solution to these mobile security issues.How Mobile Malware Bypasses Secure Containers
How Mobile Malware Bypasses Secure ContainersLacoon Mobile Security
╠²
The document discusses how mobile malware can bypass secure containers on mobile devices. It describes the mobile application sandbox security model and how containers and wrappers aim to secure storage, memory and device functionality. However, it explains that malware can break these containers through various attacks. It outlines a three step process for malware infection: 1) infecting the device, 2) installing a backdoor, and 3) bypassing containerization. Finally, it introduces a behavioral-based malware detection solution called Lacoon Mobile Security that uses virtual execution, identification of malicious behaviors and detection of command and control activity to block mobile threats.BlackHat USA 2013 - Practical Attacks against Mobile Device Management Solutions
BlackHat USA 2013 - Practical Attacks against Mobile Device Management SolutionsLacoon Mobile Security
╠²
This document summarizes a presentation about practical attacks against mobile device management (MDM) solutions. It outlines four steps an attacker can take to bypass MDM on Android devices: (1) infect the device, (2) install a backdoor by rooting it, (3) bypass containerization, and (4) exfiltrate information. It also describes how an attacker can jailbreak iOS devices to install a backdoor and bypass containerization. Finally, it recommends mitigation techniques for MDM like following a layered defense-in-depth approach and using an adaptive multi-layer model.Anatomy of a Targeted Attack against Mobile Device Management (MDM)
Anatomy of a Targeted Attack against Mobile Device Management (MDM)Lacoon Mobile Security
╠²
The document discusses the anatomy of targeted attacks against Mobile Device Management (MDM) solutions, focusing on the methods used to bypass these security measures. It details steps for infecting devices, establishing backdoors, and overcoming containerization protections, alongside mitigation techniques. The document highlights a specific incident involving an Android trojan used in an attack on Tibetan activists through spear phishing and email hacking.BlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)
BlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)Lacoon Mobile Security
╠²
The document discusses the vulnerabilities of Mobile Device Management (MDM) systems and the rise of spyphones, emphasizing that secure containers are not entirely secure against sophisticated attacks. It highlights the prevalence of mobile malware and the effectiveness of low-end spy tools that can compromise both personal and corporate data. The conclusion advocates for a multi-layered security approach, noting that while MDM can separate business and personal data, it cannot guarantee absolute security.iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation
iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
╠²
MobileCON 2013 ŌĆō Attacks Aginst MDM Solutions (and What You Can Do About It)
MobileCON 2013 ŌĆō Attacks Aginst MDM Solutions (and What You Can Do About It)Lacoon Mobile Security
╠²
BlackHat USA 2013 - Practical Attacks against Mobile Device Management Solutions
BlackHat USA 2013 - Practical Attacks against Mobile Device Management SolutionsLacoon Mobile Security
╠²
BlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)
BlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)Lacoon Mobile Security
╠²
Ad
Recently uploaded (20)
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash
╠²
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and PrivacyAI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
╠²
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens
╠²
Hi, IŌĆÖm Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as IŌĆÖve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobsŌĆ” WeŌĆÖll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is ŌĆ£Fifth ElementŌĆØ. It wowed me with futuristic predictions when I was a kid and IŌĆÖm impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldnŌĆÖt be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we donŌĆÖt know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didnŌĆÖt steal jobsŌĆöthey transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani
╠²
Salesforce Summer '25 Release Frenchgathering.pptx.pdfGenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowOh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash
╠²
Oh, the Possibilities - Balancing Innovation and Risk with Generative AIUserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40
╠²
VMwareŌĆÖs pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include ScopesŌĆöand Datacenter is now officially part of the equation. In this session, weŌĆÖll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. YouŌĆÖll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiencyŌĆöall without migrating to the cloud. WeŌĆÖll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
╠²
║▌║▌▀Ż deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
╠²
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.AI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
╠²
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike." How to survive with 1 billion vectors and not sell a kidney: our low-cost c...
" How to survive with 1 billion vectors and not sell a kidney: our low-cost c...Fwdays
╠²
Let's talk about our history. How we started the project with a small vector database of less than 2 million records. Later, we received a request for +100 million records, then another +100... And so gradually we reached almost 1 billion. Standard tools were quickly running out of steam - we were running into performance, index size, and very limited resources. After a long series of trials and errors, we built our own low-cost cluster, which today stably processes thousands of queries to more than 1B vectors.Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...Josef Weingand
╠²
IBM LTO10Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
╠²
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of Deepfakes"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
╠²
AI VIDEO MAGAZINE - r/aivideo community newsletter ŌĆō Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -OpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
╠²
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.Ad
An Overview of mRATs
- 1. An Overview of Mobile Remote Access Trojans (mRATs) and Targeted Mobile Attacks
- 2. Agenda ŌŚÅŌĆ» The Collapse of the Corporate Perimeter ŌŚÅŌĆ» Mobile Remote Access Trojans (mRATs) What do they do? What types are there? ŌŚÅŌĆ» Real-Life mRAT statistics ŌŚÅŌĆ» Infection vectors ŌŚÅŌĆ» Follow up videos
- 3. The Collapse Of The Corporate Perimeter
- 4. The Collapse Of The Corporate Perimeter
- 5. The Collapse Of The Corporate Perimeter ŌĆ£More than 60% of organizations enable BYODŌĆØ Gartner, Inc. October 2012
- 6. The Collapse Of The Corporate Perimeter
- 8. mRAT Capabilities Snooping on corporate emails and application data
- 9. mRAT Capabilities Snooping on corporate emails and application data Eavesdropping
- 10. mRAT Capabilities Snooping on corporate emails and application data Eavesdropping Extracting contact lists, call &text logs
- 11. mRAT Capabilities Snooping on corporate emails and application data Eavesdropping Extracting contact lists, call &text logs Tracking location
- 12. mRAT Capabilities Snooping on corporate emails and application data Eavesdropping Extracting contact lists, call &text logs Tracking location Infiltrating internal LANs
- 13. TYPES OF mRATS
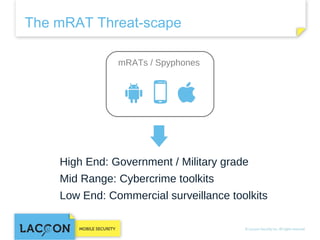
- 14. The mRAT Threat-scape mRATs / Spyphones High End: Government / Military grade Mid Range: Cybercrime toolkits Low End: Commercial surveillance toolkits
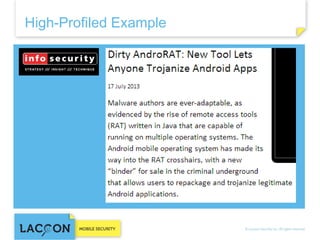
- 15. HIGH END: GOV / MIL mRATs High End Mid Range Low End
- 17. MID: CYBERCRIME TOOLKITS High End Mid Range Low End
- 19. LOWER END: COMMERCIAL SURVEILLANCE TOOLKITS High End Mid Range Low End
- 20. Commercial mobile surveillance tools
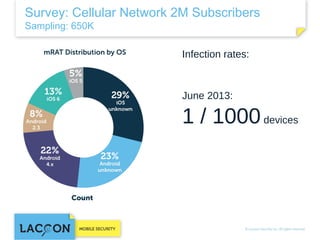
- 22. Survey: Cellular Network 2M Subscribers Sampling: 650K Infection rates: June 2013: 1 / 1000 devices
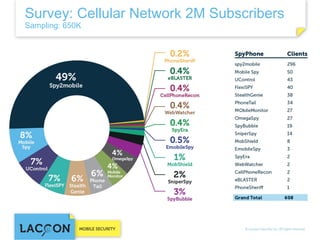
- 23. Survey: Cellular Network 2M Subscribers Sampling: 650K
- 25. Infection Vectors For more Information: Coming soonŌĆ” ŌĆ£Cyber-Threats to Android-Based DevicesŌĆØ ŌĆ£Cyber-Threats to iOS-Based DevicesŌĆØ Lacoon Mobile Security YouTube Channel
- 26. MOBILE DEVICE MANAGEMENT (MDM) SOLUTIONS DO NOT ADDRESS THIS THREAT
- 27. An Anatomy of an Attack against MDMs For more Information: ŌĆ£Bypassing Secure Containers on MobileŌĆØ Lacoon Mobile Security YouTube Channel
- 28. Thank You. @LacoonSecurity Lacoon Mobile Security info@lacoon.com
Editor's Notes
- #25: Infection of mobile devices can be done remotely ŌĆō such as via receiving an email containing the malware, or locally ŌĆō for example, through the usage of a USB cable.
