"Bleeding-In-The-Browser" - Why reverse Heartbleed risk is dangerous to the Enterprise
0 likes1,795 views
This Bleeding-In-The-Browser attack scenario is a highly common scenario that exploits an Android 4.1.1 mobile browser to steal credentials and session cookies using reverse Heartbleed. This presentation illustrates how easily an attacker can steal your Enterprise data with social engineering techniques as well as tips for protecting your Enterprise data from Bleeding-in-the-Browser / client-side Heartbleed.
1 of 7





Recommended
Sso cases Experience



Sso cases ExperienceVu Tran 14
?
This document discusses Single Sign-On (SSO), which allows a user to log in once and gain access to multiple related systems without additional logins. SSO reduces password fatigue and help desk calls by streamlining authentication. The document outlines how SSO works and its benefits, then provides several examples of SSO implementation scenarios across social networks and applications.A Review on Antiphishing Framework



A Review on Antiphishing FrameworkIJAEMSJORNAL
?
Phishing is an attack that deals with social engineering system to illegally get and utilize another person's information for the benefit of authentic site for possess advantage (e.g. Take of client's secret word and Visa precise elements during online correspondence). It is influencing all the significant areas of industry step by step with a considerable measure of abuse of client qualifications. To secure clients against phishing, different hostile to phishing procedures have been suggested that takes after various methodologies like customer side and server side insurance. In this paper we have considered phishing in detail (counting assault process and grouping of phishing assault) and investigated a portion of the current sites to phishing strategies alongside their points of interest and disadvantages.
Phishing attack



Phishing attackRaghav Chhabra
?
Phishing is a hacking technique where criminals create fake websites designed to steal users' personal information, like passwords and financial details. They do this by tricking users into entering information on a fake login page that looks like a real site like Facebook or a bank. To protect against phishing, users should be careful about entering information on unfamiliar sites, check URLs are correct, avoid clicking links in emails, and use antivirus software.Flaws in Oauth 2.0 Can Oauth be used as a Security Server



Flaws in Oauth 2.0 Can Oauth be used as a Security Serverijtsrd
?
1. The document discusses flaws in the OAuth 2.0 protocol related to authentication. It analyzes how an attacker could potentially hijack a user's account by modifying username data contained in authorization tokens.
2. OAuth is intended for authorization but does not fully address authentication. Tokens could allow attackers to log in under another user's identity if the username is changed before token validation.
3. The paper concludes that OAuth needs to provide additional security alerts to users when tokens are generated to prevent unauthorized access using modified tokens. Adding expiration dates to tokens and disallowing local storage on devices would also help address security issues.INTERNET AND ITS APPLICATION RESOURCES



INTERNET AND ITS APPLICATION RESOURCESsushantjuneja1
?
The document provides an overview of the internet and its applications. It discusses how the internet works on a client-server model and uses protocols to transfer data. It describes elements of the world wide web like websites, webpages, hyperlinks, and web browsers. It also covers uses of the internet like connectivity, communication, banking, entertainment and cloud computing. The document discusses advantages and disadvantages of internet use as well as how to create an email account and send/receive emails using Gmail.Phishing



PhishingArpit Patel
?
Student Arpit Patel presented on phishing. Phishing involves tricking users into providing sensitive information like passwords or credit card details through fraudulent websites or emails. The presentation defined phishing, discussed its history and increasing threat levels over time. It covered common phishing techniques, how to identify phishing attempts, and prevention methods like using antivirus software and checking financial statements regularly. The presentation also categorized different types of phishing like deceptive, malware-based, and man-in-the-middle phishing and examined causes and existing/proposed systems to address phishing threats.hotmail, hotmail login, what is hotmail, hotmail sign up, hotmail entrar, new...



hotmail, hotmail login, what is hotmail, hotmail sign up, hotmail entrar, new...Hotmail Support
?
hotmail, hotmail login, what is hotmail, hotmail sign up, hotmail entrar, new hotmail create, register hotmail account, hotmail email createZsun



ZsunHai Nguyen
?
This document summarizes and compares different two-factor authentication systems that can be used to prevent social phishing and man-in-the-browser attacks for internet banking. It analyzes SecureID tokens, mobile phones using the Phoolproof protocol, and mobile phones using the MP-Auth protocol. For each option, it evaluates the usability requirements and costs of deployment, as well as the level of security provided against social phishing and man-in-the-browser attacks. The document concludes SecureID tokens and mobile phones with Phoolproof protocol provide strong protection against social phishing but are still vulnerable to man-in-the-browser attacks.Safe Email Practices



Safe Email PracticesJonathan Slavin
?
This document provides guidance on identifying and preventing the spread of malware through emails. It discusses how malicious emails try to trick recipients through spoofing, phishing links and attachments. Examples are given of common types of malicious emails, like those disguised as package tracking notifications but containing viruses. The document advises users to be wary of emails from unknown senders or containing strange formatting, links or large attachments meant to infect computers. Proper precautions can help safeguard systems from data loss or theft resulting from malware spread through emails.Sip 140208055023-phpapp02



Sip 140208055023-phpapp02mark scott
?
The document discusses various cyber security topics including internet threats, network attacks, phone hacking, and credit/debit card hacking. It provides details on common threats such as email threats, website vulnerabilities, network scanning techniques, mobile malware, and credit card encryption weaknesses. It also offers countermeasures to help protect against these threats, including keeping software updated, using firewalls and antivirus software, input sanitization, and being wary of suspicious links and downloads.Ethical Hacking and Cyber Security



Ethical Hacking and Cyber SecurityNeeraj Negi
?
This document provides an overview of cyber security topics including threats to internet and network security, cyber laws in India, and career opportunities in cyber security. It discusses common internet threats like email threats from phishing and viruses, website threats from SQL injection and cross-site scripting attacks, and network threats from trojans and spyware. Basic steps for securing email and privacy are outlined. Cyber security is important to protect against hackers and online fraud, and India has cyber laws governing internet usage and data protection.Different types of attacks in internet



Different types of attacks in internetRohan Bharadwaj
?
Different types of attacks
Information security
cross site scripting
Denial of service attack
phishing
spoofingPhishing



Phishingshivli0769
?
This document summarizes phishing scams and how to protect against them. Phishing involves sending fraudulent emails appearing to come from trusted sources to steal personal information. It has grown into a serious threat, costing billions annually. The document outlines the history of phishing, what scams look like, and tips to identify them such as checking URLs and not clicking links. It also provides information on tools to enhance security on browsers and how reporting phishing helps authorities address the issue.Web Application Security



Web Application SecurityChris Hillman
?
This document discusses web application security from the perspectives of web developers and attackers. It covers common issues web developers face, such as tight deadlines and lack of security standards. It also describes how attackers exploit vulnerabilities like injection attacks and XSS. Recent attacks are presented as examples, such as compromising a power grid operator's website through SQL injection. The document aims to raise awareness of web security challenges.STORED XSS IN DVWA



STORED XSS IN DVWARutvik patel
?
The document discusses cross-site scripting (XSS) vulnerabilities on a DVWA web application. It explains that XSS allows attackers to inject malicious scripts that are executed by users' browsers. There are three types of XSS: stored, reflected, and DOM-based. The demonstration shows how to perform a stored XSS attack by injecting an alert script that is executed when another user views the stored message. It then demonstrates fetching the user's cookies to steal session data.Presentation On CLoudSweeper By Harini Anand



Presentation On CLoudSweeper By Harini AnandHarini Anandakumar
?
This document summarizes a tool called Cloudsweeper that aims to help secure cloud-based storage. It works by scanning a user's Gmail account to identify any credentials or account information stored in plain text that could compromise other accounts if accessed by hackers. Cloudsweeper then provides options to encrypt any found sensitive information, remove it from the account, or estimate how much access to the user's various accounts would be worth to cybercriminals. The tool uses temporary and limited OAuth access to the Gmail account without requiring the user's credentials.SpoofedMe - Intruding Accounts using Social Login Providers 



SpoofedMe - Intruding Accounts using Social Login Providers IBM Security
?
IBM's X-Force Application Security Research Team devised a logical attack that allows a malicious user to intrude into user accounts on a relying website (that is, a website that relies on authentication assertions passed to it by the identity provider) by abusing the social login mechanism.
For more: http://securityintelligence.com/spoofedme-social-login-attack-discovered-by-ibm-x-force-researchers/ Study on Phishing Attacks and Antiphishing Tools



Study on Phishing Attacks and Antiphishing ToolsIRJET Journal
?
This document discusses phishing attacks and anti-phishing tools. It begins by defining phishing as fraudulent attempts to steal users' sensitive information by impersonating trustworthy entities. The document then outlines the common steps in phishing attacks, including planning, setup, attack, collection, fraud, and post-attack actions. It describes different types of phishing attacks and analyzes security issues. The document concludes by describing some popular anti-phishing tools, including Mail-Secure and the Netcraft security toolbar.Phishing: Analysis and Countermeasures



Phishing: Analysis and CountermeasuresIRJET Journal
?
This document discusses phishing attacks and ways to counter them. It begins with an abstract that introduces the topic of email phishing and its growing security problems. The main body is divided into sections that: 1) explain how phishing attacks work and their typical stages, from creating spoofed websites to tricking victims into providing sensitive information; 2) describe different types of phishing scams like spear phishing, whaling, and pharming; 3) outline warning signs that an email may be a phishing attempt, such as coming from an unknown sender or having odd writing; and 4) suggest awareness and technical solutions to help prevent falling victim to phishing.Strategies to handle Phishing attacks



Strategies to handle Phishing attacksSreejith.D. Menon
?
Strategies to handle Phishing attacks - a seminar for ISACA coimbatore chapter. It talks about phishing and strategies to defend phishing.Exploring And Investigating New Dimensions In Phishing



Exploring And Investigating New Dimensions In PhishingMuhammad Haroon CISM PCI QSA ISMS LA CPTS CEH
?
This document summarizes information about phishing attacks, including how they work, common techniques used by phishers, and ways to prevent phishing. It notes that phishing works by deceiving users through fake websites, emails, and URLs that mimic legitimate sites to steal login credentials and private information. Specific phishing methods discussed include visual deception, browser deception, spear phishing, URL redirection flaws, and address bar spoofing. The summary also provides statistics on phishing prevalence and recommendations for technical and user-based defenses against phishing.Phishing with Super Bait



Phishing with Super BaitJeremiah Grossman
?
Phishing with Super Bait
Jeremiah Grossman, Founder and CTO, WhiteHat Security
The use of phishing/cross-site scripting (XSS) hybrid attacks for financial gain is spreading. It?s imperative that security professionals familiarize themselves with these new threats to protect their websites and confidential corporate information.
This isn't just another presentation about phishing scams or cross-site scripting. We?re all very familiar with each of those issues. Instead, we?ll discuss the potential impact when the two are combined to form new attack techniques. Phishers are beginning to exploit these techniques, creating new phishing attacks that are virtually impervious to conventional security measures. Secure sockets layer (SSL), blacklists, token-based authentication, browser same-origin policy, and monitoring / take-down services offer little protection. Even eyeballing the authenticity of a URL is unlikely to help.
By leveraging cross-site scripting, the next level of phishing scams will be launched not from look-alike web pages, but instead from legitimate websites! This presentation will demonstrate how these types of attacks are being achieved. We'll also demonstrate the cutting edge exploits that can effectively turn your browser into spyware with several lines of JavaScript. And, we'll give you the steps you need to take to protect your websites from these attacks.2 secure systems design



2 secure systems designdrewz lin
?
This document summarizes the key aspects of designing secure systems:
1) It discusses various common security threats like defacement, infiltration, phishing, and denial of service attacks.
2) It emphasizes the importance of understanding threats and designing security into systems from the beginning, rather than adding it as an afterthought.
3) Using a simple web server example, it shows how not considering security can leave systems vulnerable if authentication, access controls, and input validation are not implemented properly.Secure client



Secure clientHai Nguyen
?
The document discusses the emerging threat of man-in-the-browser attacks that can modify online transactions without the user's knowledge. These attacks circumvent all existing authentication methods by targeting transactions after authentication. Potential solutions discussed include developing a secure, hardened browser without extensions or scripts that is tightly coupled to cryptography. However, there would be no way for servers to reliably identify use of a secure browser versus an insecure one.Deconstructing A Phishing Scheme



Deconstructing A Phishing SchemeChristopher Duffy
?
This document provides an in-depth breakdown and analysis of a phishing email scheme. It examines various technical aspects of the fraudulent email such as header information, links, and payload in order to understand how the scheme attempted to steal users' personal information. Statistics are also presented on common phishing techniques and the countries most associated with hosting phishing sites. Resources for further information on phishing prevention and response are listed at the end.Online spying tools



Online spying toolsfarazmajeed27
?
Online spying Tools including , cookies, web bugs, spam & spyware , & other hacking methods & also about harming computer etc , its a complete description about Online spying tools , best of luckOnline spying tools



Online spying toolsfarazmajeed27
?
Online spying including : Cookies, web bugs , spam & spyware , it also includes hacking methods & harming computer , a complete package for online spying toolsPhishing: Swiming with the sharks



Phishing: Swiming with the sharksNalneesh Gaur
?
The document discusses phishing attacks and how they work. It describes common phishing techniques like fraudulent links and forms in emails that steal personal information. It also explains how phishing kits are used to launch attacks and how money mules are recruited to launder stolen funds. Technical aspects like address bar spoofing and DNS hijacking are also covered, showing how phishers exploit systems and social engineering to target victims.Mobile Threats: Enterprises Under Attack



Mobile Threats: Enterprises Under AttackLacoon Mobile Security
?
Enterprise mobile devices are increasingly being targeted by advanced persistent threats seeking sensitive corporate data. A joint research study by Lacoon Mobile Security and Check Point found that attackers are developing new techniques like exploiting vulnerabilities in mobile apps and enterprise mobile management systems to infiltrate organizations. The report recommends enterprises strengthen mobile security by implementing mobile threat defense solutions, enforcing strong access controls and policies, and ensuring devices and apps are regularly patched and updated.Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...



Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...Lacoon Mobile Security
?
This document discusses practical attacks against virtual desktop infrastructure (VDI) solutions. It begins with introductions to the presenters and an overview of mobile VDI. It then outlines four threats: 1) using a remote access Trojan to keylog credentials, 2) directly grabbing credentials from an Android device, 3) screen scraping on Android, and 4) man-in-the-middle session hijacking on iOS. It argues that a layered mobile security approach is needed to protect VDI, including device assessment, reducing attack surfaces, threat detection, and risk mitigation.More Related Content
Similar to "Bleeding-In-The-Browser" - Why reverse Heartbleed risk is dangerous to the Enterprise (20)
Safe Email Practices



Safe Email PracticesJonathan Slavin
?
This document provides guidance on identifying and preventing the spread of malware through emails. It discusses how malicious emails try to trick recipients through spoofing, phishing links and attachments. Examples are given of common types of malicious emails, like those disguised as package tracking notifications but containing viruses. The document advises users to be wary of emails from unknown senders or containing strange formatting, links or large attachments meant to infect computers. Proper precautions can help safeguard systems from data loss or theft resulting from malware spread through emails.Sip 140208055023-phpapp02



Sip 140208055023-phpapp02mark scott
?
The document discusses various cyber security topics including internet threats, network attacks, phone hacking, and credit/debit card hacking. It provides details on common threats such as email threats, website vulnerabilities, network scanning techniques, mobile malware, and credit card encryption weaknesses. It also offers countermeasures to help protect against these threats, including keeping software updated, using firewalls and antivirus software, input sanitization, and being wary of suspicious links and downloads.Ethical Hacking and Cyber Security



Ethical Hacking and Cyber SecurityNeeraj Negi
?
This document provides an overview of cyber security topics including threats to internet and network security, cyber laws in India, and career opportunities in cyber security. It discusses common internet threats like email threats from phishing and viruses, website threats from SQL injection and cross-site scripting attacks, and network threats from trojans and spyware. Basic steps for securing email and privacy are outlined. Cyber security is important to protect against hackers and online fraud, and India has cyber laws governing internet usage and data protection.Different types of attacks in internet



Different types of attacks in internetRohan Bharadwaj
?
Different types of attacks
Information security
cross site scripting
Denial of service attack
phishing
spoofingPhishing



Phishingshivli0769
?
This document summarizes phishing scams and how to protect against them. Phishing involves sending fraudulent emails appearing to come from trusted sources to steal personal information. It has grown into a serious threat, costing billions annually. The document outlines the history of phishing, what scams look like, and tips to identify them such as checking URLs and not clicking links. It also provides information on tools to enhance security on browsers and how reporting phishing helps authorities address the issue.Web Application Security



Web Application SecurityChris Hillman
?
This document discusses web application security from the perspectives of web developers and attackers. It covers common issues web developers face, such as tight deadlines and lack of security standards. It also describes how attackers exploit vulnerabilities like injection attacks and XSS. Recent attacks are presented as examples, such as compromising a power grid operator's website through SQL injection. The document aims to raise awareness of web security challenges.STORED XSS IN DVWA



STORED XSS IN DVWARutvik patel
?
The document discusses cross-site scripting (XSS) vulnerabilities on a DVWA web application. It explains that XSS allows attackers to inject malicious scripts that are executed by users' browsers. There are three types of XSS: stored, reflected, and DOM-based. The demonstration shows how to perform a stored XSS attack by injecting an alert script that is executed when another user views the stored message. It then demonstrates fetching the user's cookies to steal session data.Presentation On CLoudSweeper By Harini Anand



Presentation On CLoudSweeper By Harini AnandHarini Anandakumar
?
This document summarizes a tool called Cloudsweeper that aims to help secure cloud-based storage. It works by scanning a user's Gmail account to identify any credentials or account information stored in plain text that could compromise other accounts if accessed by hackers. Cloudsweeper then provides options to encrypt any found sensitive information, remove it from the account, or estimate how much access to the user's various accounts would be worth to cybercriminals. The tool uses temporary and limited OAuth access to the Gmail account without requiring the user's credentials.SpoofedMe - Intruding Accounts using Social Login Providers 



SpoofedMe - Intruding Accounts using Social Login Providers IBM Security
?
IBM's X-Force Application Security Research Team devised a logical attack that allows a malicious user to intrude into user accounts on a relying website (that is, a website that relies on authentication assertions passed to it by the identity provider) by abusing the social login mechanism.
For more: http://securityintelligence.com/spoofedme-social-login-attack-discovered-by-ibm-x-force-researchers/ Study on Phishing Attacks and Antiphishing Tools



Study on Phishing Attacks and Antiphishing ToolsIRJET Journal
?
This document discusses phishing attacks and anti-phishing tools. It begins by defining phishing as fraudulent attempts to steal users' sensitive information by impersonating trustworthy entities. The document then outlines the common steps in phishing attacks, including planning, setup, attack, collection, fraud, and post-attack actions. It describes different types of phishing attacks and analyzes security issues. The document concludes by describing some popular anti-phishing tools, including Mail-Secure and the Netcraft security toolbar.Phishing: Analysis and Countermeasures



Phishing: Analysis and CountermeasuresIRJET Journal
?
This document discusses phishing attacks and ways to counter them. It begins with an abstract that introduces the topic of email phishing and its growing security problems. The main body is divided into sections that: 1) explain how phishing attacks work and their typical stages, from creating spoofed websites to tricking victims into providing sensitive information; 2) describe different types of phishing scams like spear phishing, whaling, and pharming; 3) outline warning signs that an email may be a phishing attempt, such as coming from an unknown sender or having odd writing; and 4) suggest awareness and technical solutions to help prevent falling victim to phishing.Strategies to handle Phishing attacks



Strategies to handle Phishing attacksSreejith.D. Menon
?
Strategies to handle Phishing attacks - a seminar for ISACA coimbatore chapter. It talks about phishing and strategies to defend phishing.Exploring And Investigating New Dimensions In Phishing



Exploring And Investigating New Dimensions In PhishingMuhammad Haroon CISM PCI QSA ISMS LA CPTS CEH
?
This document summarizes information about phishing attacks, including how they work, common techniques used by phishers, and ways to prevent phishing. It notes that phishing works by deceiving users through fake websites, emails, and URLs that mimic legitimate sites to steal login credentials and private information. Specific phishing methods discussed include visual deception, browser deception, spear phishing, URL redirection flaws, and address bar spoofing. The summary also provides statistics on phishing prevalence and recommendations for technical and user-based defenses against phishing.Phishing with Super Bait



Phishing with Super BaitJeremiah Grossman
?
Phishing with Super Bait
Jeremiah Grossman, Founder and CTO, WhiteHat Security
The use of phishing/cross-site scripting (XSS) hybrid attacks for financial gain is spreading. It?s imperative that security professionals familiarize themselves with these new threats to protect their websites and confidential corporate information.
This isn't just another presentation about phishing scams or cross-site scripting. We?re all very familiar with each of those issues. Instead, we?ll discuss the potential impact when the two are combined to form new attack techniques. Phishers are beginning to exploit these techniques, creating new phishing attacks that are virtually impervious to conventional security measures. Secure sockets layer (SSL), blacklists, token-based authentication, browser same-origin policy, and monitoring / take-down services offer little protection. Even eyeballing the authenticity of a URL is unlikely to help.
By leveraging cross-site scripting, the next level of phishing scams will be launched not from look-alike web pages, but instead from legitimate websites! This presentation will demonstrate how these types of attacks are being achieved. We'll also demonstrate the cutting edge exploits that can effectively turn your browser into spyware with several lines of JavaScript. And, we'll give you the steps you need to take to protect your websites from these attacks.2 secure systems design



2 secure systems designdrewz lin
?
This document summarizes the key aspects of designing secure systems:
1) It discusses various common security threats like defacement, infiltration, phishing, and denial of service attacks.
2) It emphasizes the importance of understanding threats and designing security into systems from the beginning, rather than adding it as an afterthought.
3) Using a simple web server example, it shows how not considering security can leave systems vulnerable if authentication, access controls, and input validation are not implemented properly.Secure client



Secure clientHai Nguyen
?
The document discusses the emerging threat of man-in-the-browser attacks that can modify online transactions without the user's knowledge. These attacks circumvent all existing authentication methods by targeting transactions after authentication. Potential solutions discussed include developing a secure, hardened browser without extensions or scripts that is tightly coupled to cryptography. However, there would be no way for servers to reliably identify use of a secure browser versus an insecure one.Deconstructing A Phishing Scheme



Deconstructing A Phishing SchemeChristopher Duffy
?
This document provides an in-depth breakdown and analysis of a phishing email scheme. It examines various technical aspects of the fraudulent email such as header information, links, and payload in order to understand how the scheme attempted to steal users' personal information. Statistics are also presented on common phishing techniques and the countries most associated with hosting phishing sites. Resources for further information on phishing prevention and response are listed at the end.Online spying tools



Online spying toolsfarazmajeed27
?
Online spying Tools including , cookies, web bugs, spam & spyware , & other hacking methods & also about harming computer etc , its a complete description about Online spying tools , best of luckOnline spying tools



Online spying toolsfarazmajeed27
?
Online spying including : Cookies, web bugs , spam & spyware , it also includes hacking methods & harming computer , a complete package for online spying toolsPhishing: Swiming with the sharks



Phishing: Swiming with the sharksNalneesh Gaur
?
The document discusses phishing attacks and how they work. It describes common phishing techniques like fraudulent links and forms in emails that steal personal information. It also explains how phishing kits are used to launch attacks and how money mules are recruited to launder stolen funds. Technical aspects like address bar spoofing and DNS hijacking are also covered, showing how phishers exploit systems and social engineering to target victims.Exploring And Investigating New Dimensions In Phishing



Exploring And Investigating New Dimensions In PhishingMuhammad Haroon CISM PCI QSA ISMS LA CPTS CEH
?
More from Lacoon Mobile Security (11)
Mobile Threats: Enterprises Under Attack



Mobile Threats: Enterprises Under AttackLacoon Mobile Security
?
Enterprise mobile devices are increasingly being targeted by advanced persistent threats seeking sensitive corporate data. A joint research study by Lacoon Mobile Security and Check Point found that attackers are developing new techniques like exploiting vulnerabilities in mobile apps and enterprise mobile management systems to infiltrate organizations. The report recommends enterprises strengthen mobile security by implementing mobile threat defense solutions, enforcing strong access controls and policies, and ensuring devices and apps are regularly patched and updated.Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...



Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...Lacoon Mobile Security
?
This document discusses practical attacks against virtual desktop infrastructure (VDI) solutions. It begins with introductions to the presenters and an overview of mobile VDI. It then outlines four threats: 1) using a remote access Trojan to keylog credentials, 2) directly grabbing credentials from an Android device, 3) screen scraping on Android, and 4) man-in-the-middle session hijacking on iOS. It argues that a layered mobile security approach is needed to protect VDI, including device assessment, reducing attack surfaces, threat detection, and risk mitigation.iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation



iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
?
A profile is an extremely sensitive optional configuration file which allows to re-define different system functionality parameters such as mobile carrier settings, Mobile Device Management (MDM) settings and networking settings. Through social engineering techniques such as email phishing or a fake URL, an attacker can convince a user to install a malicious profile and compromise the device settings to silently route network traffic from the device to a remote proxy over SSL using a self-signed certificate.
The impact:
Once the attacker has re-routed all traffic from the mobile device to their own server, they can begin to install other malicious apps and decrypt SSL communications.Amphion Forum 2013: What to Do About Attacks Against MDMs



Amphion Forum 2013: What to Do About Attacks Against MDMsLacoon Mobile Security
?
The document discusses popular mobile device management (MDM) solutions and presents methods for attacking them. It begins with an agenda covering personal data, private information, and digital safety. The presentation then outlines how to hack enterprise data on mobile devices in 12 hours for $1000 by infecting a device, installing a backdoor, and bypassing containerization. It also demonstrates commercial mobile surveillance tools and rates of cellular network infection. The document concludes by describing Lacoon's behavior-based mobile security solution to detect and mitigate these kinds of attacks.An Overview of mRATs



An Overview of mRATsLacoon Mobile Security
?
This document provides an overview of mobile remote access trojans (mRATs) and targeted mobile attacks. It discusses how mRATs can snoop on corporate emails and data, eavesdrop, extract contact lists and location information, and infiltrate internal networks. The document describes high-end government/military-grade mRATs, mid-range cybercrime toolkits, and lower-end commercial surveillance toolkits. Real-life statistics from a survey of 650,000 devices within a cellular network of 2 million subscribers in June 2013 showed an infection rate of 1 in 1,000 devices. The document concludes by stating that mobile device management solutions do not address this threat.MobileCON 2013 ¨C Attacks Aginst MDM Solutions (and What You Can Do About It)



MobileCON 2013 ¨C Attacks Aginst MDM Solutions (and What You Can Do About It)Lacoon Mobile Security
?
This document summarizes an anatomy of a targeted attack against mobile device management (MDM) solutions and discusses mitigation techniques. It begins with an overview of how the corporate perimeter has collapsed due to bring your own device policies. It then demonstrates how attackers can infect a device, install backdoors to gain administrative privileges, bypass MDM containerization, and exfiltrate information. Current MDM and security solutions fail to adequately protect against these attacks. The document proposes adding behavioral analysis of applications and devices along with vulnerability assessments to better detect threats. It promotes the solutions from Lacoon Mobile Security to help stop these mobile attacks.IPExpo 2013 - Anatomy of a Targeted Attack Against MDM Solutions



IPExpo 2013 - Anatomy of a Targeted Attack Against MDM SolutionsLacoon Mobile Security
?
This document summarizes a presentation about targeted attacks against mobile device management (MDM) solutions. It discusses how the corporate perimeter has collapsed with bring-your-own-device policies. Mobile devices are attractive targets for threats like snooping on data and tracking locations. The presentation demonstrates how mobile malware can bypass MDM solutions by infecting devices, installing backdoors, and exfiltrating information despite containerization efforts. Current security solutions like MDM, wrappers, and network access control fail to fully protect against these attacks. Behavioral analysis of applications and devices, along with threat intelligence and vulnerability research, can help detection. The document promotes Lacoon Mobile Security as a solution to these mobile security issues.How Mobile Malware Bypasses Secure Containers



How Mobile Malware Bypasses Secure ContainersLacoon Mobile Security
?
The document discusses how mobile malware can bypass secure containers on mobile devices. It describes the mobile application sandbox security model and how containers and wrappers aim to secure storage, memory and device functionality. However, it explains that malware can break these containers through various attacks. It outlines a three step process for malware infection: 1) infecting the device, 2) installing a backdoor, and 3) bypassing containerization. Finally, it introduces a behavioral-based malware detection solution called Lacoon Mobile Security that uses virtual execution, identification of malicious behaviors and detection of command and control activity to block mobile threats.BlackHat USA 2013 - Practical Attacks against Mobile Device Management Solutions



BlackHat USA 2013 - Practical Attacks against Mobile Device Management SolutionsLacoon Mobile Security
?
This document summarizes a presentation about practical attacks against mobile device management (MDM) solutions. It outlines four steps an attacker can take to bypass MDM on Android devices: (1) infect the device, (2) install a backdoor by rooting it, (3) bypass containerization, and (4) exfiltrate information. It also describes how an attacker can jailbreak iOS devices to install a backdoor and bypass containerization. Finally, it recommends mitigation techniques for MDM like following a layered defense-in-depth approach and using an adaptive multi-layer model.Anatomy of a Targeted Attack against Mobile Device Management (MDM)



Anatomy of a Targeted Attack against Mobile Device Management (MDM)Lacoon Mobile Security
?
In this engaging session, we demonstrate a live attack technique aimed at bypassing a popular MDM solution with an email encryption offering. Further, we show how the mobile surveillance software effectively renders the encryption feature useless. This demonstration includes a mobile spyware version which directly accesses the MDM¡¯s memory storage, retrieves the plain-text emails and sends them on to a remote server. Finally, we present mitigation techniques to solve against this problem.
Differentiate between mass consumer-oriented mobile attacks and targeted mobile cyber-attacks
Recognise the shortcoming of MDM as a wholesome security solution
Enhance mobile attack mitigation techniques through mobile activity visibilityBlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)



BlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)Lacoon Mobile Security
?
Spyphones are surveillance tools surreptitiously planted on a user¡¯s handheld device. While malicious mobile applications, mainly phone fraud applications distributed through common application channels, target the typical consumer, spyphones are nation states tool of attacks. Why? Once installed, the software stealthy gathers information such as text messages (SMS), geo-location information, emails and even surround-recordings.
How are these mobile cyber-espionage attacks carried out? In this engaging session, we present novel proof-of-concept attack techniques - both on Android and iOS devices - which bypass traditional mobile malware detection measures- and even circumvent common Mobile Device Management (MDM) features, such as encryption.Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...



Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...Lacoon Mobile Security
?
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation



iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
?
MobileCON 2013 ¨C Attacks Aginst MDM Solutions (and What You Can Do About It)



MobileCON 2013 ¨C Attacks Aginst MDM Solutions (and What You Can Do About It)Lacoon Mobile Security
?
BlackHat USA 2013 - Practical Attacks against Mobile Device Management Solutions



BlackHat USA 2013 - Practical Attacks against Mobile Device Management SolutionsLacoon Mobile Security
?
BlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)



BlackHat Europe 2013 - Practical Attacks against Mobile Device Management (MDM)Lacoon Mobile Security
?
Recently uploaded (20)
World Information Architecture Day 2025 - UX at a Crossroads



World Information Architecture Day 2025 - UX at a CrossroadsJoshua Randall
?
User Experience stands at a crossroads: will we live up to our potential to design a better world? or will we be co-opted by ¡°product management¡± or another business buzzword?
Looking backwards, this talk will show how UX has repeatedly failed to create a better world, drawing on industry data from Nielsen Norman Group, Baymard, MeasuringU, WebAIM, and others.
Looking forwards, this talk will argue that UX must resist hype, say no more often and collaborate less often (you read that right), and become a true profession ¡ª in order to be able to design a better world.Wondershare Dr.Fone Crack Free Download 2025



Wondershare Dr.Fone Crack Free Download 2025maharajput103
?
copy & paste ? ???? https://filedownloadx.com/download-link/
Wondershare Dr.Fone Crack is a comprehensive mobile phone management and recovery software designed to help users recover lost data, repair system issues, and manage mobile devices. It supports both Android and iOS platforms, offering a wide range of features aimed at restoring files, repairing software problems, and backing up or transferring data.How Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...



How Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...ScyllaDB
?
This talk shares how Discord scaled their message search infrastructure using Rust, Kubernetes, and a multi-cluster Elasticsearch architecture to achieve better performance, operability, and reliability, while also enabling new search features for Discord users.THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
?
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.Unlocking DevOps Secuirty :Vault & Keylock



Unlocking DevOps Secuirty :Vault & KeylockHusseinMalikMammadli
?
DevOps i? t?hl¨¹k?sizliyi sizi maraqland?r?r? ?st?r developer, ist?r t?hl¨¹k?sizlik m¨¹h?ndisi, ist?rs? d? DevOps h?v?skar? olun, bu t?dbir ??b?k?l??m?k, bilikl?rinizi b?l¨¹?m?k v? DevSecOps sah?sind? ?n son t?cr¨¹b?l?ri ?yr?nm?k ¨¹?¨¹n m¨¹k?mm?l f¨¹rs?tdir!
Bu workshopda DevOps infrastrukturlar?n?n t?hl¨¹k?sizliyini nec? art?rmaq bar?d? dan??acay?q. DevOps sisteml?ri qurulark?n avtomatla?d?r?lm??, y¨¹ks?k ?l?atan v? etibarl? olmas? il? yana??, h?m d? t?hl¨¹k?sizlik m?s?l?l?ri n?z?r? al?nmal?d?r. Bu s?b?bd?n, DevOps komandolar?n?n t?hl¨¹k?sizliy? y?n?lmi? praktikalara riay?t etm?si vacibdir.Transform Your Future with Front-End Development Training



Transform Your Future with Front-End Development TrainingVtechlabs
?
Kickstart your career in web development with our front-end web development course in Vadodara. Learn HTML, CSS, JavaScript, React, and more through hands-on projects and expert mentorship. Our front-end development course with placement includes real-world training, mock interviews, and job assistance to help you secure top roles like Front-End Developer, UI/UX Developer, and Web Designer.
Join VtechLabs today and build a successful career in the booming IT industry!DealBook of Ukraine: 2025 edition | AVentures Capital



DealBook of Ukraine: 2025 edition | AVentures CapitalYevgen Sysoyev
?
The DealBook is our annual overview of the Ukrainian tech investment industry. This edition comprehensively covers the full year 2024 and the first deals of 2025. DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)Tsuyoshi Hirayama
?
DAO UTokyo 2025
–|¾©´óѧÇéˆóѧh ¥Ö¥í¥Ã¥¯¥Á¥§©`¥óÑо¿¥¤¥Ë¥·¥¢¥Æ¥£¥Ö
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (ƽɽÒã)The Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.A Framework for Model-Driven Digital Twin Engineering



A Framework for Model-Driven Digital Twin EngineeringDaniel Lehner
?
ºÝºÝߣs from my PhD Defense at Johannes Kepler University, held on Janurary 10, 2025.
The full thesis is available here: https://epub.jku.at/urn/urn:nbn:at:at-ubl:1-83896What Makes "Deep Research"? A Dive into AI Agents



What Makes "Deep Research"? A Dive into AI AgentsZilliz
?
About this webinar:
Unless you live under a rock, you will have heard about OpenAI¡¯s release of Deep Research on Feb 2, 2025. This new product promises to revolutionize how we answer questions requiring the synthesis of large amounts of diverse information. But how does this technology work, and why is Deep Research a noticeable improvement over previous attempts? In this webinar, we will examine the concepts underpinning modern agents using our basic clone, Deep Searcher, as an example.
Topics covered:
Tool use
Structured output
Reflection
Reasoning models
Planning
Types of agentic memoryUiPath Agentic Automation Capabilities and Opportunities



UiPath Agentic Automation Capabilities and OpportunitiesDianaGray10
?
Learn what UiPath Agentic Automation capabilities are and how you can empower your agents with dynamic decision making. In this session we will cover these topics:
What do we mean by Agents
Components of Agents
Agentic Automation capabilities
What Agentic automation delivers and AI Tools
Identifying Agent opportunities
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.Cloud of everything Tech of the 21 century in Aviation



Cloud of everything Tech of the 21 century in AviationAssem mousa
?
AI, Block chain, Digital Currency, Cloud, Cloud of Things, Tactile Internet, Digital Twins, IOT, AR, VR, MR, U commerce, data and robotics."
TrustArc Webinar - Building your DPIA/PIA Program: Best Practices & Tips



TrustArc Webinar - Building your DPIA/PIA Program: Best Practices & TipsTrustArc
?
Understanding DPIA/PIAs and how to implement them can be the key to embedding privacy in the heart of your organization as well as achieving compliance with multiple data protection / privacy laws, such as GDPR and CCPA. Indeed, the GDPR mandates Privacy by Design and requires documented Data Protection Impact Assessments (DPIAs) for high risk processing and the EU AI Act requires an assessment of fundamental rights.
How can you build this into a sustainable program across your business? What are the similarities and differences between PIAs and DPIAs? What are the best practices for integrating PIAs/DPIAs into your data privacy processes?
Whether you're refining your compliance framework or looking to enhance your PIA/DPIA execution, this session will provide actionable insights and strategies to ensure your organization meets the highest standards of data protection.
Join our panel of privacy experts as we explore:
- DPIA & PIA best practices
- Key regulatory requirements for conducting PIAs and DPIAs
- How to identify and mitigate data privacy risks through comprehensive assessments
- Strategies for ensuring documentation and compliance are robust and defensible
- Real-world case studies that highlight common pitfalls and practical solutionsField Device Management Market Report 2030 - TechSci Research



Field Device Management Market Report 2030 - TechSci ResearchVipin Mishra
?
The Global Field Device Management (FDM) Market is expected to experience significant growth in the forecast period from 2026 to 2030, driven by the integration of advanced technologies aimed at improving industrial operations.
? According to TechSci Research, the Global Field Device Management Market was valued at USD 1,506.34 million in 2023 and is anticipated to grow at a CAGR of 6.72% through 2030. FDM plays a vital role in the centralized oversight and optimization of industrial field devices, including sensors, actuators, and controllers.
Key tasks managed under FDM include:
Configuration
Monitoring
Diagnostics
Maintenance
Performance optimization
FDM solutions offer a comprehensive platform for real-time data collection, analysis, and decision-making, enabling:
Proactive maintenance
Predictive analytics
Remote monitoring
By streamlining operations and ensuring compliance, FDM enhances operational efficiency, reduces downtime, and improves asset reliability, ultimately leading to greater performance in industrial processes. FDM¡¯s emphasis on predictive maintenance is particularly important in ensuring the long-term sustainability and success of industrial operations.
For more information, explore the full report: https://shorturl.at/EJnzR
Major companies operating in Global?Field Device Management Market are:
General Electric Co
Siemens AG
ABB Ltd
Emerson Electric Co
Aveva Group Ltd
Schneider Electric SE
STMicroelectronics Inc
Techno Systems Inc
Semiconductor Components Industries LLC
International Business Machines Corporation (IBM)
#FieldDeviceManagement #IndustrialAutomation #PredictiveMaintenance #TechInnovation #IndustrialEfficiency #RemoteMonitoring #TechAdvancements #MarketGrowth #OperationalExcellence #SensorsAndActuators[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
[Webinar] Scaling Made Simple: Getting Started with No-Code Web AppsSafe Software
?
Ready to simplify workflow sharing across your organization without diving into complex coding? With FME Flow Apps, you can build no-code web apps that make your data work harder for you ¡ª fast.
In this webinar, we¡¯ll show you how to:
Build and deploy Workspace Apps to create an intuitive user interface for self-serve data processing and validation.
Automate processes using Automation Apps. Learn to create a no-code web app to kick off workflows tailored to your needs, trigger multiple workspaces and external actions, and use conditional filtering within automations to control your workflows.
Create a centralized portal with Gallery Apps to share a collection of no-code web apps across your organization.
Through real-world examples and practical demos, you¡¯ll learn how to transform your workflows into intuitive, self-serve solutions that empower your team and save you time. We can¡¯t wait to show you what¡¯s possible!UiPath Automation Developer Associate Training Series 2025 - Session 2



UiPath Automation Developer Associate Training Series 2025 - Session 2DianaGray10
?
In session 2, we will introduce you to Data manipulation in UiPath Studio.
Topics covered:
Data Manipulation
What is Data Manipulation
Strings
Lists
Dictionaries
RegEx Builder
Date and Time
Required Self-Paced Learning for this session:
Data Manipulation with Strings in UiPath Studio (v2022.10) 2 modules - 1h 30m - https://academy.uipath.com/courses/data-manipulation-with-strings-in-studio
Data Manipulation with Lists and Dictionaries in UiPath Studio (v2022.10) 2 modules - 1h - https:/academy.uipath.com/courses/data-manipulation-with-lists-and-dictionaries-in-studio
Data Manipulation with Data Tables in UiPath Studio (v2022.10) 2 modules - 1h 30m - https:/academy.uipath.com/courses/data-manipulation-with-data-tables-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Revolutionizing-Government-Communication-The-OSWAN-Success-Story



Revolutionizing-Government-Communication-The-OSWAN-Success-Storyssuser52ad5e
?
? ????? ??????? ????? ?
???????? ??????????? is proud to be a part of the ?????? ????? ???? ???? ??????? (?????) success story! By delivering seamless, secure, and high-speed connectivity, OSWAN has revolutionized e-?????????? ?? ??????, enabling efficient communication between government departments and enhancing citizen services.
Through our innovative solutions, ???????? ?????????? has contributed to making governance smarter, faster, and more transparent. This milestone reflects our commitment to driving digital transformation and empowering communities.
? ?????????? ??????, ?????????? ??????????!
"Bleeding-In-The-Browser" - Why reverse Heartbleed risk is dangerous to the Enterprise
- 1. Bleeding-In-The-Browser -? Attack flow scenario ¨C Illustration of how an attacker can steal your Enterprise data -? Tips for protecting your Enterprise data from Bleeding-in-the-Browser / client-side Heartbleed 1
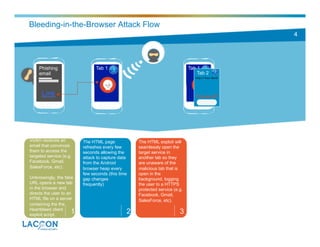
- 2. Tab 1 2 Victim receives an email that convinces them to access the targeted service (e.g. Facebook, Gmail, SalesForce, etc). Unknowingly, the fake URL opens a new tab in the browser and directs the user to an HTML file on a server containing the the Heartbleed client exploit script. Bleeding-in-the-Browser Attack Flow The HTML page refreshes every few seconds allowing the attack to capture data from the Android browser heap every few seconds (this time gap changes frequently) The HTML exploit will seamlessly open the target service in another tab so they are unaware of the malicious tab that is open in the background, logging the user to a HTTPS protected service (e.g. Facebook, Gmail, SalesForce, etc). During the login process, the malicious tab will refresh and cause additional data to arrive from the client's Android browser heap. 1 The attacker can now begin to extract data such as cookies, username, passwords and other credentials. 2 3 4 5 Phishing email Link
- 3. Tab 1 3 Victim receives an email that convinces them to access the targeted service (e.g. Facebook, Gmail, SalesForce, etc). Unknowingly, the fake URL opens a new tab in the browser and directs the user to an HTML file on a server containing the the Heartbleed client exploit script. Bleeding-in-the-Browser Attack Flow The HTML page refreshes every few seconds allowing the attack to capture data from the Android browser heap every few seconds (this time gap changes frequently) The HTML exploit will seamlessly open the target service in another tab so they are unaware of the malicious tab that is open in the background, logging the user to a HTTPS protected service (e.g. Facebook, Gmail, SalesForce, etc). During the login process, the malicious tab will refresh and cause additional data to arrive from the client's Android browser heap. 1 The attacker can now begin to extract data such as cookies, username, passwords and other credentials. 2 3 4 5 Phishing email Link
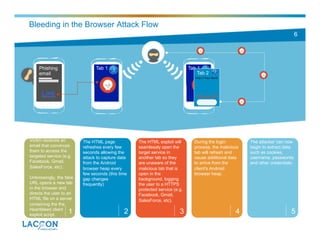
- 4. Tab 1 4 Victim receives an email that convinces them to access the targeted service (e.g. Facebook, Gmail, SalesForce, etc). Unknowingly, the fake URL opens a new tab in the browser and directs the user to an HTML file on a server containing the the Heartbleed client exploit script. Bleeding-in-the-Browser Attack Flow The HTML page refreshes every few seconds allowing the attack to capture data from the Android browser heap every few seconds (this time gap changes frequently) The HTML exploit will seamlessly open the target service in another tab so they are unaware of the malicious tab that is open in the background, logging the user to a HTTPS protected service (e.g. Facebook, Gmail, SalesForce, etc). During the login process, the malicious tab will refresh and cause additional data to arrive from the client's Android browser heap. 1 The attacker can now begin to extract data such as cookies, username, passwords and other credentials. 2 3 4 5 Phishing email Link Tab 1 Tab 2
- 5. Tab 1 5 Victim receives an email that convinces them to access the targeted service (e.g. Facebook, Gmail, SalesForce, etc). Unknowingly, the fake URL opens a new tab in the browser and directs the user to an HTML file on a server containing the the Heartbleed client exploit script. Bleeding-in-the-Browser Attack Flow The HTML page refreshes every few seconds allowing the attack to capture data from the Android browser heap every few seconds (this time gap changes frequently) The HTML exploit will seamlessly open the target service in another tab so they are unaware of the malicious tab that is open in the background, logging the user to a HTTPS protected service (e.g. Facebook, Gmail, SalesForce, etc). During the login process, the malicious tab will refresh and cause additional data to arrive from the client's Android browser heap. 1 The attacker can now begin to extract data such as cookies, username, passwords and other credentials. 2 3 4 5 Phishing email Link Tab 1 Tab 2
- 6. Tab 1 6 Victim receives an email that convinces them to access the targeted service (e.g. Facebook, Gmail, SalesForce, etc). Unknowingly, the fake URL opens a new tab in the browser and directs the user to an HTML file on a server containing the the Heartbleed client exploit script. Bleeding in the Browser Attack Flow The HTML page refreshes every few seconds allowing the attack to capture data from the Android browser heap every few seconds (this time gap changes frequently) The HTML exploit will seamlessly open the target service in another tab so they are unaware of the malicious tab that is open in the background, logging the user to a HTTPS protected service (e.g. Facebook, Gmail, SalesForce, etc). During the login process, the malicious tab will refresh and cause additional data to arrive from the client's Android browser heap. 1 The attacker can now begin to extract data such as cookies, username, passwords and other credentials. 2 3 4 5 Phishing email Link Tab 1 Tab 2
- 7. 7 Protect Your Enterprise Data from Bleeding-in-the-Browser We Advise our Enterprise Customers to: ¡ì?? Map the risk across your enterprise¡¯s mobile devices and identify vulnerable devices. An on-line Heartbleed mobile device tester is available here: http://www.lacoon.com/?p=7998 For a free enterprise account, contact us at info@lacoon.com ¡ì?? If you¡¯ve identified vulnerable devices, enable two-factor authentication on critical services as SalesForce, Google Apps, Office365, etc. ¡ì?? Use Lacoon MobileFortress to track the vulnerability status in your mobile environment and provide on-demand exploit mitigation.


