1 of 38
Downloaded 35 times


































Ad
Recommended
徹底解説!Project Lambdaのすべて リターンズ[祝Java8Launch #jjug]
徹底解説!Project Lambdaのすべて リターンズ[祝Java8Launch #jjug]bitter_fox
?
祝Java8Launchで発表させていただいた時の資料です.
最新のものはこちらです.
http://www.slideshare.net/bitter_fox/ss-3588249860分て?体験する Stream / Lambda? ハンズオン
60分て?体験する Stream / Lambda? ハンズオンHiroto Yamakawa
?
Java Doでしょう #01(8/23 札幌)
http://javado.connpass.com/event/18278/
磯野ー!関数型言语やろうぜー!
磯野ー!関数型言语やろうぜー!Ra Zon
?
第21回オープンラボ岡山の発表スライド
http://openlab.okaya.ma/wiki.cgi?page=%CA%D9%B6%AF%B2%F1%2F%C2%E8021%B2%F3脆弱性事例に学ぶセキュアコーディング「SSL/TLS証明書検証」編 (JavaDayTokyo2015)
脆弱性事例に学ぶセキュアコーディング「SSL/TLS証明書検証」編 (JavaDayTokyo2015)JPCERT Coordination Center
?
JavaDayTokyo2015 での講演資料です.正规表现リテラルは本当に必要なのか?
正规表现リテラルは本当に必要なのか?kwatch
?
PyConJP2014発表資料。
?正規表現リテラルは、**あれば便利だけどなくても困らない**(ライブラリでカバーできる)ことを説明する。
?Pythonの正規表現が抱える問題点とその解決案を紹介する。Vertex AI Pipelinesで BigQuery MLのワークフローを管理 (ETL ~ デプロイまで)
Vertex AI Pipelinesで BigQuery MLのワークフローを管理 (ETL ~ デプロイまで)幸太朗 岩澤
?
Vertex AI Pipelinesで
BigQuery MLのワークフローを作成しました。機械学習の社会実装勉強会 第12回の発表内容です。
https://machine-learning-workshop.connpass.com/event/250263/Confluenceショートカットキー表 v1
Confluenceショートカットキー表 v1Naho Inuyama
?
Confluence 用のショートカットキー表を作りました。まずは、コミュニティで共有したいと思います。 Mac 上の Chrome で全てのショートカットキーを動作確認していますが、これ使えません!というのがあれば、ご報告お願いします。他製品のショートカットキー表も作成予定です。搁颈诲别谤はいいぞ!
搁颈诲别谤はいいぞ!UnityTechnologiesJapan002
?
JetBrains社の.NET IDEの「Rider」。本セッションでは、Unityゲーム開発と.NET開発におけるRiderの魅力を紹介します。
スピーカー: Ryota MurohoshiForm認証で学ぶSpring Security入門
Form認証で学ぶSpring Security入門Ryosuke Uchitate
?
This document describes how to configure Spring Security for authentication and authorization in a web application. It defines a WebSecurityConfig class that configures HTTP security with roles like OWNER and MANAGER for access control. It also defines a UserDetailsManager service for loading users and a User entity class implementing UserDetails. Tests are shown for security configuration, login, access control and more using Spring Security's test utilities.EchoyaGinhanazeSu_inoka.pptx
EchoyaGinhanazeSu_inoka.pptxkeink
?
Why is echo and gin so fast?
How to create faster HTTP Router in GoConference 2023SQLアンチパターン - ナイーブツリー
SQLアンチパターン - ナイーブツリーke-m kamekoopa
?
社内勉強会資料
追記: 2013-10-31
ついったで指摘( https://twitter.com/akuraru/status/395822183777202176 )を受けたので入れ子集合のノード追加の説明の所を修正しました。狈别谤惫别蝉が开拓する「贰濒颈虫颈谤で滨辞罢」の新世界
狈别谤惫别蝉が开拓する「贰濒颈虫颈谤で滨辞罢」の新世界Hideki Takase
?
Erlang & Elixir Fest 2019で講演しました!
関数型言語ElixirによるIoT開発フレームワーク“Nerves”について,ライブデモをふんだんに交えながら日本の皆さまに共有させていただきました.
https://elixir-fest.jp/
最後にbig news!!があるので,ぜひご覧ください!
https://swest.toppers.jp/keynote/
誤記 P.27:
fukuoka.exでのNerves Trainingは6/7ではなく7/7に開催しますm(_ _)m
講演概要:
Nervesってご存知でしょうか?
"Craft and deploy bulletproof embedded software in Elixir"のスローガンのもと,ElixirでIoTデバイスの開発を実現できるフレームワークです.Raspberry PiやBeagleBoneなどを対象として,数十MB程度の省メモリでElixirアプリの駆動を可能とします.mixツールに統合されたビルドシステム,GPIOやI2CなどIoTデバイス制御のための豊富なデバイスドライバ?ライブラリ,NervesHubを介したクラウド経由のセキュアなファームアップデート,Phoenixと連携したリアルタイム通信とデータ可視化と,そのエコシステムの完成度は目を見張るものがあります.本発表では,IoTシステム開発のライブデモを交えながら,Nervesの概要ならびに現状と目指しているところを紹介します.
発表者はLonestar ElixirConf 2019に参加してきました.Nervesのコア開発者からTrainingを直接受講してきて,多くのNerves技術者の発表を聴講して議論してきて,その動向に大いに衝撃を受けました.Austinで得てきたこれらの知見と経験について,日本の全てのElixir技術者の皆さまとこの技術を共有したいと思います.微服務架構 導入經驗分享 吳剛志 - Community Open Camp
微服務架構 導入經驗分享 吳剛志 - Community Open CampAndrew Wu
?
本文件分享了微服務架構的導入經驗,強調了相較於單體式架構的優勢,包括擴展性、故障隔離和資源利用率的提升。通過使用 Windows 容器技術進行系統佈署,實現了更簡化和高效的服務管理,並提出了將傳統 ASP.NET 系統遷移到微服務架構的具體步驟及實際案例。文中也探討了微服務架構在人才發展管理系統中的應用,闡述了建立良好服務邊界和 API 定義的重要性。input type = password autocomplete = off は使ってはいけない
input type = password autocomplete = off は使ってはいけない彰 村地
?
江戸前セキュリティ勉強会(2014/07/5) で発表したライトニング トークのスライドですサイボウズの CI/CD 事情 ?Jenkins おじさんは CircleCI おじさんにしんかした!?
サイボウズの CI/CD 事情 ?Jenkins おじさんは CircleCI おじさんにしんかした!?Jumpei Miyata
?
The document discusses CI/CD tools, specifically Jenkins and CircleCI, highlighting features and performance pricing plans as of November 7, 2018. It also mentions updates regarding CircleCI 2.1 and provides a link to a relevant article. Additionally, it includes engagement with the CI/CD community through an event called 'CI/CD Test Night #1'.Python 3のWebシステムでDDDに入門してみた
Python 3のWebシステムでDDDに入門してみたHiromu Yakura
?
The document discusses dependency injection in Python applications. It covers separating an application into domains, infrastructure, and presentation layers. It also discusses using dependency injection with abstract classes, type annotations, and value objects to decouple components and enable testing. Examples are provided of implementing dependency injection in Python.闯补惫补の进化にともなう运用性の向上はシステム设计にどういう変化をもたらすのか
闯补惫补の进化にともなう运用性の向上はシステム设计にどういう変化をもたらすのかYoshitaka Kawashima
?
Java Day Tokyo 2016 のセッション3-Eの資料です。
Java8, Java9の新機能がシステムの設計にどういう影響があるのかを考えてみました。Vector API - Javaによるベクターコンピューティング
Vector API - JavaによるベクターコンピューティングYuichi Sakuraba
?
Vector API - Javaによるベクターコンピューティング
2020.02.01 ブリ会議資料More Related Content
What's hot (20)
Vertex AI Pipelinesで BigQuery MLのワークフローを管理 (ETL ~ デプロイまで)
Vertex AI Pipelinesで BigQuery MLのワークフローを管理 (ETL ~ デプロイまで)幸太朗 岩澤
?
Vertex AI Pipelinesで
BigQuery MLのワークフローを作成しました。機械学習の社会実装勉強会 第12回の発表内容です。
https://machine-learning-workshop.connpass.com/event/250263/Confluenceショートカットキー表 v1
Confluenceショートカットキー表 v1Naho Inuyama
?
Confluence 用のショートカットキー表を作りました。まずは、コミュニティで共有したいと思います。 Mac 上の Chrome で全てのショートカットキーを動作確認していますが、これ使えません!というのがあれば、ご報告お願いします。他製品のショートカットキー表も作成予定です。搁颈诲别谤はいいぞ!
搁颈诲别谤はいいぞ!UnityTechnologiesJapan002
?
JetBrains社の.NET IDEの「Rider」。本セッションでは、Unityゲーム開発と.NET開発におけるRiderの魅力を紹介します。
スピーカー: Ryota MurohoshiForm認証で学ぶSpring Security入門
Form認証で学ぶSpring Security入門Ryosuke Uchitate
?
This document describes how to configure Spring Security for authentication and authorization in a web application. It defines a WebSecurityConfig class that configures HTTP security with roles like OWNER and MANAGER for access control. It also defines a UserDetailsManager service for loading users and a User entity class implementing UserDetails. Tests are shown for security configuration, login, access control and more using Spring Security's test utilities.EchoyaGinhanazeSu_inoka.pptx
EchoyaGinhanazeSu_inoka.pptxkeink
?
Why is echo and gin so fast?
How to create faster HTTP Router in GoConference 2023SQLアンチパターン - ナイーブツリー
SQLアンチパターン - ナイーブツリーke-m kamekoopa
?
社内勉強会資料
追記: 2013-10-31
ついったで指摘( https://twitter.com/akuraru/status/395822183777202176 )を受けたので入れ子集合のノード追加の説明の所を修正しました。狈别谤惫别蝉が开拓する「贰濒颈虫颈谤で滨辞罢」の新世界
狈别谤惫别蝉が开拓する「贰濒颈虫颈谤で滨辞罢」の新世界Hideki Takase
?
Erlang & Elixir Fest 2019で講演しました!
関数型言語ElixirによるIoT開発フレームワーク“Nerves”について,ライブデモをふんだんに交えながら日本の皆さまに共有させていただきました.
https://elixir-fest.jp/
最後にbig news!!があるので,ぜひご覧ください!
https://swest.toppers.jp/keynote/
誤記 P.27:
fukuoka.exでのNerves Trainingは6/7ではなく7/7に開催しますm(_ _)m
講演概要:
Nervesってご存知でしょうか?
"Craft and deploy bulletproof embedded software in Elixir"のスローガンのもと,ElixirでIoTデバイスの開発を実現できるフレームワークです.Raspberry PiやBeagleBoneなどを対象として,数十MB程度の省メモリでElixirアプリの駆動を可能とします.mixツールに統合されたビルドシステム,GPIOやI2CなどIoTデバイス制御のための豊富なデバイスドライバ?ライブラリ,NervesHubを介したクラウド経由のセキュアなファームアップデート,Phoenixと連携したリアルタイム通信とデータ可視化と,そのエコシステムの完成度は目を見張るものがあります.本発表では,IoTシステム開発のライブデモを交えながら,Nervesの概要ならびに現状と目指しているところを紹介します.
発表者はLonestar ElixirConf 2019に参加してきました.Nervesのコア開発者からTrainingを直接受講してきて,多くのNerves技術者の発表を聴講して議論してきて,その動向に大いに衝撃を受けました.Austinで得てきたこれらの知見と経験について,日本の全てのElixir技術者の皆さまとこの技術を共有したいと思います.微服務架構 導入經驗分享 吳剛志 - Community Open Camp
微服務架構 導入經驗分享 吳剛志 - Community Open CampAndrew Wu
?
本文件分享了微服務架構的導入經驗,強調了相較於單體式架構的優勢,包括擴展性、故障隔離和資源利用率的提升。通過使用 Windows 容器技術進行系統佈署,實現了更簡化和高效的服務管理,並提出了將傳統 ASP.NET 系統遷移到微服務架構的具體步驟及實際案例。文中也探討了微服務架構在人才發展管理系統中的應用,闡述了建立良好服務邊界和 API 定義的重要性。input type = password autocomplete = off は使ってはいけない
input type = password autocomplete = off は使ってはいけない彰 村地
?
江戸前セキュリティ勉強会(2014/07/5) で発表したライトニング トークのスライドですサイボウズの CI/CD 事情 ?Jenkins おじさんは CircleCI おじさんにしんかした!?
サイボウズの CI/CD 事情 ?Jenkins おじさんは CircleCI おじさんにしんかした!?Jumpei Miyata
?
The document discusses CI/CD tools, specifically Jenkins and CircleCI, highlighting features and performance pricing plans as of November 7, 2018. It also mentions updates regarding CircleCI 2.1 and provides a link to a relevant article. Additionally, it includes engagement with the CI/CD community through an event called 'CI/CD Test Night #1'.Python 3のWebシステムでDDDに入門してみた
Python 3のWebシステムでDDDに入門してみたHiromu Yakura
?
The document discusses dependency injection in Python applications. It covers separating an application into domains, infrastructure, and presentation layers. It also discusses using dependency injection with abstract classes, type annotations, and value objects to decouple components and enable testing. Examples are provided of implementing dependency injection in Python.闯补惫补の进化にともなう运用性の向上はシステム设计にどういう変化をもたらすのか
闯补惫补の进化にともなう运用性の向上はシステム设计にどういう変化をもたらすのかYoshitaka Kawashima
?
Java Day Tokyo 2016 のセッション3-Eの資料です。
Java8, Java9の新機能がシステムの設計にどういう影響があるのかを考えてみました。More from Yuichi Sakuraba (20)
Vector API - Javaによるベクターコンピューティング
Vector API - JavaによるベクターコンピューティングYuichi Sakuraba
?
Vector API - Javaによるベクターコンピューティング
2020.02.01 ブリ会議資料Project Loom + Project Panama
Project Loom + Project PanamaYuichi Sakuraba
?
JVM Language Summit Reporting Seminar Material
JVM Language Summit 報告会資料Oracle Code One 報告会 Java SE Update
Oracle Code One 報告会 Java SE UpdateYuichi Sakuraba
?
This short document discusses getting the process ID (PID) in Panama. It mentions including the unistd.h header file and linking with the unistd.jar library to use the getpid function, as well as potentially needing the libc.so shared object for it to work properly.Oracle Code One 報告会 Java SE Update
Oracle Code One 報告会 Java SE UpdateYuichi Sakuraba
?
2018.11.24 関西ジャバユーザーグループ
Oracle Code One 報告会 Java SE Update
まだJavaの進化が遅いと思っている人はいませんよねWhat's New in Java
What's New in JavaYuichi Sakuraba
?
The document repeatedly discusses the concept of "Japanthink" but provides no further context or details about what Japanthink refers to. It consists solely of the word "Japanthink" printed multiple times.Migration Guide to Java SE 10, and also Java SE 11
Migration Guide to Java SE 10, and also Java SE 11Yuichi Sakuraba
?
Java Day Tokyo 2018 JSE-5
Java SE 10、そしてJava SE 11への移行ガイド
Migration Guide to Java SE 10, and also Java SE 11Moving to Module: Issues & Solutions
Moving to Module: Issues & SolutionsYuichi Sakuraba
?
Project Jigsaw introduces a modular system to Java to address issues with non-modular code. It divides the Java platform API into named modules that clearly define dependencies and exported packages. This avoids issues with classes from sun.* and com.sun.* packages being inaccessible or the huge size of rt.jar. The module system allows modular and non-modular code to coexist through automatic modules and the unnamed module. Tools like jdeps and jlink are provided to help with adoption and management of modules.Project Jigsawと、ちょっとだけVector API
Project Jigsawと、ちょっとだけVector APIYuichi Sakuraba
?
2017.12.02 Javaコミュ@福岡 JavaOne報告会
「Project Jigsawと、ちょっとだけVector API」資料Java SEの現在、過去 そして未来Yuichi Sakuraba
?
El documento describe un proyecto llamado Valhalla que consiste en una lista de puntos con coordenadas x e y. La lista contiene cabeceras y puntos con valores numéricos para x e y.Introduction of Project Jigsaw
Introduction of Project JigsawYuichi Sakuraba
?
Introduction of Project Jigsaw
20 May 2017 Japan Java User Group "Cross Community Conference" MaterialAd
Recently uploaded (7)
PGConf.dev 2025 参加レポート (JPUG総会併設セミナー2025 発表資料)
PGConf.dev 2025 参加レポート (JPUG総会併設セミナー2025 発表資料)NTT DATA Technology & Innovation
?
PGConf.dev 2025 参加レポート
(JPUG総会併設セミナー2025 発表資料)
2025年6月14日(土)
NTTデータ
OSSビジネス推進室
貞弘 泰輔、池田 凛太郎Protect Your IoT Data with UbiBot's Private Platform.pptx
Protect Your IoT Data with UbiBot's Private Platform.pptxユビボット 株式会社
?
Our on-premise IoT platform offers a secure and scalable solution for businesses, with features such as real-time monitoring, customizable alerts and open API support, and can be deployed on your own servers to ensure complete data privacy and control.Ad
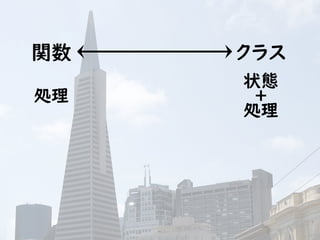
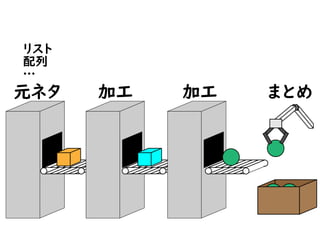
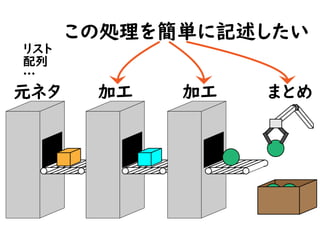
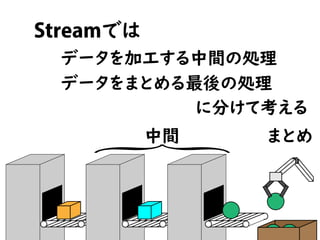
今こそStream API入門
- 6. イテレータは 2 種類 外部イテレータ 内部イテレータ 繰り返しの制御を自分で記述 繰り返しはライブラリまかせ for文 拡張for文 Iteratorクラス Stream API
