access-control-basics-murat-kantarcioglu.pdf
- 1. UT DALLAS UT DALLAS Erik Jonsson School of Engineering & Computer Science FEARLESS engineering Access Control Basics Murat Kantarcioglu
- 2. FEARLESS engineering Access Control - basic concepts ŌĆó An access control system regulates the operations that can be executed on data and resources to be protected ŌĆó Its goal is to control operations executed by subjects in order to prevent actions that could damage data and resources ŌĆó Access control is typically provided as part of the operating system and of the database management system (DBMS)
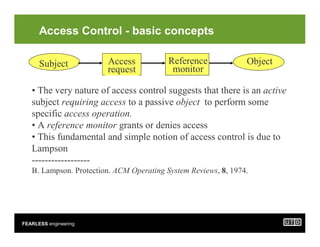
- 3. FEARLESS engineering Access Control - basic concepts Subject Access request Reference monitor Object ŌĆó The very nature of access control suggests that there is an active subject requiring access to a passive object to perform some specific access operation. ŌĆó A reference monitor grants or denies access ŌĆó This fundamental and simple notion of access control is due to Lampson ------------------ B. Lampson. Protection. ACM Operating System Reviews, 8, 1974.
- 4. FEARLESS engineering Access Control Mechanism ŌĆó It is typically a software system implementing the access control function ŌĆó It is usually part of other systems ŌĆó The access control mechanism uses some access control policies to decide whether to grant or deny a subject access to a requested resource ŌĆó We will refer to an access control system as system comprising an access control mechanism and all information required to take access control decisions (for example, access permissions)
- 5. FEARLESS engineering Object ŌĆó Anything that holds data, such as relations, directories, interprocess messages, network packets, I/O devices, or physical media ŌĆó We often refer to objects, controlled by the access control system, as protection objects ŌĆó Note that not all resources managed by a system need to be protected
- 6. FEARLESS engineering Subject ŌĆó An abstraction of any active entity that performs computation in the system ŌĆó Subjects can be classified into: ŌĆō users -- single individuals connecting to the system ŌĆō groups -- sets of users ŌĆō roles -- named collections of privileges / functional entities within the organization ŌĆō processes -- executing programs on behalf of users ŌĆó Relations may exist among the various types of subject
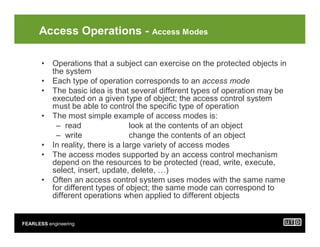
- 7. FEARLESS engineering Access Operations - Access Modes ŌĆó Operations that a subject can exercise on the protected objects in the system ŌĆó Each type of operation corresponds to an access mode ŌĆó The basic idea is that several different types of operation may be executed on a given type of object; the access control system must be able to control the specific type of operation ŌĆó The most simple example of access modes is: ŌĆō read look at the contents of an object ŌĆō write change the contents of an object ŌĆó In reality, there is a large variety of access modes ŌĆó The access modes supported by an access control mechanism depend on the resources to be protected (read, write, execute, select, insert, update, delete, ŌĆ”) ŌĆó Often an access control system uses modes with the same name for different types of object; the same mode can correspond to different operations when applied to different objects
- 8. FEARLESS engineering Access Operations - Access Modes An example ŌĆó Unix operating system ŌĆō Access modes defined for files ŌĆó read: reading from a file ŌĆó write: writing to a file ŌĆó execute: executing a (program) file ŌĆō Access models defined for directories ŌĆó read: list a directory contents ŌĆó write: create or rename a file in a directory ŌĆó execute: search a directory
- 9. FEARLESS engineering Access Operations Access Permissions and Attributes ŌĆó How does the reference monitor decides whether to give access or not? ŌĆó Main approaches: ŌĆō It uses access permissions ŌĆó Typical of discretionary access control (DAC) models ŌĆō It uses information (often referred to as attributes) concerning subjects and objects ŌĆó Typical of multilevel access control (MAC) models ŌĆó More innovative approaches have been developed where access permissions can be also expressed in terms of object and subject attributes and even context parameters
- 10. FEARLESS engineering Access Operations Access Permissions Subject Access request Reference monitor Object Access Permissions Access Control Policies
- 11. FEARLESS engineering Access Permissions ŌĆó Access permissions, also called authorizations, are expressed in terms of subjects, objects, and access modes ŌĆó From a conceptual point of view an access permission is a tuple <s, o, a> where ŌĆō s is a subject ŌĆō o is an object ŌĆō a is an access mode It states that subject s has the permission to execute operation a on object o We also say that s has access right a on object o ŌĆó Example: the access permission <Bob, Read, F1> states that Bob has the permission to read file F1
- 12. FEARLESS engineering Access Permissions ŌĆó Subjects, objects, and access modes can be organized into hierarchies ŌĆó The semantics of the hierarchy depends on the domain ŌĆó The use of hierarchies has two important advantages: ŌĆō It reduces the number of permissions that need to be entered into the access control system, thus reducing administration costs ŌĆō Combined with negative authorizations (to be discussed later on), it supports the specification of exceptions
- 13. FEARLESS engineering Object Hierarchy object component object PART-OF directory file
- 14. FEARLESS engineering Role Hierarchy senior role junior role technical manager programmer
- 15. FEARLESS engineering Group Hierarchy group group member GROUP MEMBERSHIP University CS Dept Suppose that the group CS department has 200 members and the University group 5000 members; suppose we have the policy that the department calendar can be read to all members of the University and written only by the members of CS; these policies can be encoded into two access permissions of the form: <University, calendar, Read> <CS Dept, calendar, Write>
- 16. FEARLESS engineering Access Mode Hierarchy mode implied mode SUBSUMPTION write read
- 17. FEARLESS engineering Groups and Negative Permissions ŌĆó Groups can be seen as an intermediate level between users and objects ŌĆó An example of an ideal world where all access permissions are mediated by groups g1 g2 s1 s2 s3 s4 s5 Users Groups Objects o1 o2 o3 o4 o5 o6
- 18. FEARLESS engineering Groups and Negative Permissions ŌĆó Often access control policies have special cases where is proves convenient to give some user a permission for an object directly or deny a user a permission that it would normally derive from its membership in some group ŌĆó A negative permission specifies an operation that a subject is not allowed to perform ŌĆó Representing negative permissions requires extending our simple tuple model with an additional component: <s, o, a, sign> where sign ├Ä{+, -}
- 19. FEARLESS engineering Groups and Negative Permissions An example in which not all access permissions are mediated through groups Users Groups Objects g1 s1 s2 s3 o1 o2 o3 o4 o5
- 20. FEARLESS engineering Ownership and Administration ŌĆó A key question when dealing with access control is who specifies which subjects can access which objects for which operations ŌĆó In the case of permissions, this means specifying which are the subjects that can enter permissions
- 21. FEARLESS engineering Ownership and Administration Two basic options ŌĆó Discretionary approach ŌĆō the owner of a resource decrees who is allowed to have access ŌĆō But then: who is the owner of a resource? ŌĆó Mandatory approach ŌĆō a system-wide policy decrees who is allowed to have access
- 22. FEARLESS engineering Access Control Structures The most well known access control structures for DAC models are based on the notion of Access Control Matrix. Let: - S be a set of subjects - O be a set of objects - A be a set of access modes An access control matrix M on S, O, and A is defined as M = (Mso)s ŌłŖ S, o ŌłŖ O with Mso ŌŖé A The entry Mso specifies the set of access operations subject s can perform on object o.
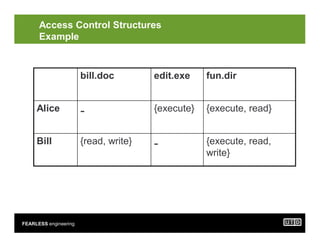
- 23. FEARLESS engineering Access Control Structures Example {execute, read, write} - {read, write} Bill {execute, read} {execute} - Alice fun.dir edit.exe bill.doc
- 24. FEARLESS engineering Access Control Structures Access Control Lists and Capabilities ŌĆó Directly implementing access control matrices is quite inefficient, because in most cases these matrices are sparse ŌĆó Therefore two main implementations have been developed ŌĆō Access control lists ŌĆó Used in DBMS and Operating Systems ŌĆō Capabilities
- 25. FEARLESS engineering Basic Operations in Access Control ŌĆó Grant permissions ŌĆō Inserting values in the matrixŌĆÖs entries ŌĆó Revoke permissions ŌĆō Remove values from the matrixŌĆÖs entries ŌĆó Check permissions ŌĆō Verifying whether the entry related to a subject s and an object o contains a given access mode