1 of 22
Downloaded 41 times

















Ad
Recommended
ļ╣äĒŖĖņĮöņØĖ Ļ░£ņØĖĻ░ä ņĀäņ×ÉĒÖöĒÅÉņŗ£ņŖżĒģ£ ņÜöņĢĮ ņäżļ¬ģ
ļ╣äĒŖĖņĮöņØĖ Ļ░£ņØĖĻ░ä ņĀäņ×ÉĒÖöĒÅÉņŗ£ņŖżĒģ£ ņÜöņĢĮ ņäżļ¬ģSeong-Bok Lee
╠²
ņé¼ĒåĀņŗ£ņØś ļ╣äĒŖĖņĮöņØĖ ļģ╝ļ¼Ė ņÜöņĢĮĻ│╝ ļ│┤ņČ® ņäżļ¬ģßäćßģĄßäÉßģ│ßäÅßģ®ßäŗßģĄßå½ ßäćßģĄßäīßģĄßäéßģĄßäēßģ│ ßäĆßģóßäŗßģŁ
ßäćßģĄßäÉßģ│ßäÅßģ®ßäŗßģĄßå½ ßäćßģĄßäīßģĄßäéßģĄßäēßģ│ ßäĆßģóßäŗßģŁJeff Paik
╠²
ļ╣äĒŖĖņĮöņØĖ ļ╣äņ¦ĆļŗłņŖż Ļ░£ņÜöļĖöļĪØņ▓┤ņØĖ Ļ░£ņÜö
ļĖöļĪØņ▓┤ņØĖ Ļ░£ņÜöJeff Paik
╠²
ļĖöļĪØņ▓┤ņØĖņŚÉ ļīĆĒĢ£ ĻĄ¼ļ│äĻ│╝ ņĀĢņØś ļ░Å ļĖöļĪØņ▓┤ņØĖņØä ņØ┤ņÜ®ĒĢśļŖö ņŖżĒāĆĒŖĖņŚģ ņĀĢļ│┤ßäćßģ│ßå»ßäģßģ®ßå©ßäÄßģ”ßäŗßģĄßå½ ßäŗßģźßåĖßäĆßģ© ßäÆßģ¦ßå½ßäÆßģ¬ßå╝
ßäćßģ│ßå»ßäģßģ®ßå©ßäÄßģ”ßäŗßģĄßå½ ßäŗßģźßåĖßäĆßģ© ßäÆßģ¦ßå½ßäÆßģ¬ßå╝Jeff Paik
╠²
ļĖöļĪØņ▓┤ņØĖ ņŚģĻ│ä ĒśäĒÖ®Ļ░ĆņāüĒÖöĒÅÉ ļ╣äĒŖĖņĮöņØĖ, ņĢäņ¦üņØĆ ņä▒Ļ│ĄņĀü, ļ»ĖļלļŖö ļČłĒł¼ļ¬ģ | 2013.08.13
Ļ░ĆņāüĒÖöĒÅÉ ļ╣äĒŖĖņĮöņØĖ, ņĢäņ¦üņØĆ ņä▒Ļ│ĄņĀü, ļ»ĖļלļŖö ļČłĒł¼ļ¬ģ | 2013.08.13Kunwoo Kim
╠²
ļé┤ņ×¼Ļ░Ćņ╣śĻ░Ć ņĀäĒśĆ ņŚåĻ│Ā ņżæņĢÖņØĆĒ¢ēĻ│╝ Ļ░ÖņØĆ Ļ┤Ćļ”¼ņŻ╝ņ▓┤ļÅä ņŚåļŖö Ļ░ĆņāüĒÖöĒÅÉ ļ╣äĒŖĖņĮöņØĖņØ┤ ļåÆņØĆ Ļ░ĆĻ▓®ņŚÉ Ļ▒░ļלļÉśļ®┤ņä£ ņäĖĻ░äņØś Ļ┤Ćņŗ¼ņØä ļüīĻ│Ā ņ׳ļŗż. ļ╣äĒŖĖņĮöņØĖņØ┤ ļ¼┤ņŗ£ ļ¬╗ĒĢĀ ļīĆņāüņ£╝ļĪ£ ļ¢Āņśżļź┤ļ®┤ņä£ ļČłļ▓ĢĻ▒░ļל ņØ┤ņÜ® ļ░®ņ¦Ćļź╝ ņ£äĒĢ£ ņĀĢļČĆ ņ░©ņøÉņØś ļīĆņØæļÅä ļéśĒāĆļéśĻ│Ā ņ׳ļŗż. ļ╣äĒŖĖņĮöņØĖņØĆ ņä▒Ļ│ĄĒĢĀņłśļĪØ ņŚŁņäżņĀüņ£╝ļĪ£ Ļ▒░ļלņłśļŗ©ņ£╝ļĪ£ņä£ ĒÖöĒÅÉ ĻĖ░ļŖźņØ┤ ņĢĮĒÖöļÉĀ ņłśļ░¢ņŚÉ ņŚåļŖö ņĢĮņĀÉļÅä ņ¦ĆļŗłĻ│Ā ņ׳ļŗż.ļ╣äĒŖĖņĮöņØĖ ļäżĒŖĖņøīĒü¼ ĻĖ░ņłĀ ņåīĻ░£ - ņ×äņäØņØś, ņ£żņäØņŻ╝
ļ╣äĒŖĖņĮöņØĖ ļäżĒŖĖņøīĒü¼ ĻĖ░ņłĀ ņåīĻ░£ - ņ×äņäØņØś, ņ£żņäØņŻ╝Seok-ju Yun
╠²
NDC14ļĢī ļ╣äĒŖĖņĮöņØĖņŚÉ ņé¼ņÜ®ļÉ£ ĻĖ░ņłĀ, ņé¼ļĪĆ ņŚ░ĻĄ¼ņŚÉ ļīĆĒĢ┤ ļ░£Ēæ£Ē¢łļŹś ņŖ¼ļØ╝ņØ┤ļō£ ņ×ģļŗłļŗż.3.Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ (4ņ░©ņé░ņŚģĒśüļ¬ģ: Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö)
3.Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ (4ņ░©ņé░ņŚģĒśüļ¬ģ: Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö)doo rip choi
╠²
4ņ░© ņé░ņŚģĒśüļ¬ģņØś ĻĖ░ņłĀļōżņØĆ ņåīĒåĄņØä ņ£äĒĢ£ ņ¦äĒÖö ĻĖ░ņłĀļĪ£ ļ░£ņĀäļÉśņ¢┤ Ļ░ĆĻ│Ā ņ׳ļŗż.
ļ╣äņ”łļŗłņŖż ņśüņŚŁļ¦łļŗż Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄņØ┤ ĒĢäņÜöĒĢśĻ│Ā ņŗĀĻĖ░ņłĀņØä ĒÖ£ņÜ®ĒĢ£
Ļ│ĀĻ░ØņØś ļŗłņ”łņŚÉ ļ¦×ļŖö ņä£ļ╣äņŖż ņŚŁļ¤ēņØä Ļ░ĆņĀĖņĢ╝ ĒĢĀ Ļ▓āņØ┤ļŗż.
Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄņØä ņŻ╝ņĀ£ļĪ£ 3Ļ░£ņØś ņŗ£ļ”¼ņ”ł ļ¼╝ļĪ£ ļ░£Ēæ£ ņ×ÉļŻīļź╝ Ļ│Ąņ£Ā ĒĢ®ļŗłļŗż.
Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö,
1. Ļ│ĀĻ░ØņØä ņØ┤ĒĢ┤ĒĢśļŖö ļ╣ģļŹ░ņØ┤Ēä░
(The big data platform to understand customers.)
2. Ļ│ĀĻ░ØĻ│╝ ņåīĒåĄĒĢśļŖö ņØĖĻ│Ąņ¦ĆļŖź
( Artificial intelligence to communicate with customers)
3. Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ
(Block chain to connect with customer)Bitcoin ĻĖ░ņłĀļČäņäØ - ņĪ░ļé©ņłś
Bitcoin ĻĖ░ņłĀļČäņäØ - ņĪ░ļé©ņłś00heights
╠²
'ļööņ¦ĆĒäĖĒåĄĒÖöņÖĆ ļ╣äĒŖĖņĮöņØĖ' ņäĖļ»Ėļéś ļ░£Ēæ£ ņ×ÉļŻī
ĒĢ£ĻĄŁņĀäņ×ÉĒåĄņŗĀņŚ░ĻĄ¼ņøÉ ņĢöĒśĖĻĖ░ņłĀņŚ░ĻĄ¼ņŗż ņĪ░ļé©ņłś ļ░Ģņé¼
2013.9.19Scale chain ņĀ£ĒÆłņåīĻ░£
Scale chain ņĀ£ĒÆłņåīĻ░£Kangmo Kim
╠²
ScaleChain ņĀ£ĒÆłņåīĻ░£ : 12ņøö 2ņØ╝ ņĀĆļģü 7ņŗ£ ņŖżĒāĆĒŖĖņŚģ ņ¢╝ļØ╝ņØ┤ņ¢ĖņŖż
ļĖöļĪØņ▓┤ņØĖ ņØ┤ĒĢ┤ņÖĆ ĒÖ£ņÜ®
ļĖöļĪØņ▓┤ņØĖ ņØ┤ĒĢ┤ņÖĆ ĒÖ£ņÜ®Seung-Woo Kang
╠²
ļĖöļĪØņ▓┤ņØĖ(Blockchain) Ļ░£ļģÉĻ│╝ ĒÖ£ņÜ® ņé¼ļĪĆ(Use Cases)ņŚÉ ļīĆĒĢ┤ ņĀĢļ”¼ĒĢśņśĆņŖĄļŗłļŗż. ņŗĀļó░(Trust)ļź╝ ĒÖĢļ│┤ĒĢśĻĖ░ ņ£äĒĢ┤ ņé¼ņÜ®ļÉ£ ĻĖ░ņłĀņØä ļ╣äņ£ĀņĀüņ£╝ļĪ£ Ēæ£ĒśäĒĢśļĀż ļģĖļĀźĒĢśņśĆņŖĄļŗłļŗż. ĻĘĖļ”¼Ļ│Ā Ēśäņ×¼ ņ¦äĒ¢ēļÉśĻ│Ā ņ׳ļŖö ņé¼ļĪĆņŚÉ ļīĆĒĢ£ ņ×ÉļŻīļź╝ ņłśņ¦æĒĢśņśĆņŖĄļŗłļŗż. ļ╣äĒŖĖņĮöņØĖĻ│╝ ļĖöļĪØņ▓┤ņØĖ ĒĢĄņŗ¼Ļ░£ļģÉņĀĢļ”¼
ļ╣äĒŖĖņĮöņØĖĻ│╝ ļĖöļĪØņ▓┤ņØĖ ĒĢĄņŗ¼Ļ░£ļģÉņĀĢļ”¼HANSUK KIM
╠²
(ņŖ¼ļØ╝ņØ┤ļō£ ĒÖĢļīĆĒĢ┤ņä£ ļ┤ÉņŻ╝ņäĖņÜö!) ļ╣äĒŖĖņĮöņØĖņØś ĻĘ╝Ļ░äņØä ņØ┤ļŻ©Ļ│Ā ņ׳ļŖö ĻĖ░ņłĀņØĖ
ņ¦ĆĻ░æ,Ļ▒░ļל,P2P,ļĖöļĪØņ▓┤ņØĖ,ņ▒äĻĄ┤ ļō▒ņØś ņŻ╝ņĀ£ļź╝ ĒĢĄņŗ¼ļ¦ī ņÜöņĢĮĒ¢łņŖĄļŗłļŗż
ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀ ņĀüņÜ® ņé¼ļĪĆ
ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀ ņĀüņÜ® ņé¼ļĪĆICON Foundation
╠²
2019.1. Digital Strategy MBA course on Blockchain at aSSIST (a Seoul School of Integrated Sciences & Technologies)ņĀäņ×ÉņāüĻ▒░ļל ļ│┤ņĢł-ļĖöļĪØņ▓┤ņØĖ(Blockchain) ĻĖ░ņłĀ
ņĀäņ×ÉņāüĻ▒░ļל ļ│┤ņĢł-ļĖöļĪØņ▓┤ņØĖ(Blockchain) ĻĖ░ņłĀYechan Ahn
╠²
ņĀäņ×ÉņāüĻ▒░ļל ļ│┤ņĢł-ļĖöļĪØņ▓┤ņØĖ(Blockchain) ĻĖ░ņłĀļ╣äĒŖĖņĮöņØĖņŚÉ Ļ┤ĆĒĢ£ ĻĄÉņ£Īņ×ÉļŻī ņ×ģļŗłļŗż.
ļ╣äĒŖĖņĮöņØĖņŚÉ Ļ┤ĆĒĢ£ ĻĄÉņ£Īņ×ÉļŻī ņ×ģļŗłļŗż.Sung Wan Yoon
╠²
ļ╣äĒŖĖņĮöņØĖņŚÉ Ļ┤ĆĒĢ£ ņĀäļ░śņĀüņØĖ ļé┤ņÜ®ņØä ļŗżļŻ©ļŖö ĻĄÉņ£Īņ×ÉļŻī ņ×ģļŗłļŗż.
bithumb.com ĻĘ╝ļ¼┤ ņŗ£ ņ×æņä▒ĒĢ£ ņ×ÉļŻīņ×ģļŗłļŗż.ļČäņé░ĒśĢ ņ╗┤Ēō©Ēīģ Ēöīļ×½ĒÅ╝ [ņŚÉĒģīļ”¼ņøĆ]
ļČäņé░ĒśĢ ņ╗┤Ēō©Ēīģ Ēöīļ×½ĒÅ╝ [ņŚÉĒģīļ”¼ņøĆ]inucreative
╠²
ļČäņé░ĒśĢ ņ╗┤Ēō©Ēīģ Ēöīļ×½ĒÅ╝ [ņŚÉĒģīļ”¼ņøĆ]How Blockchain Works - ļĖöļĪØņ▓┤ņØĖņØś ņøÉļ”¼
How Blockchain Works - ļĖöļĪØņ▓┤ņØĖņØś ņøÉļ”¼SeokWon Kim
╠²
Brief introduction about the ideas of the Blockchain technology.
Written in Korean.
Starts with Hash function, Hashcash, proof-of-work, and how Blockchain adopted and extended the idea.
Bitcoin 2.0(blockchain technology 2)
Bitcoin 2.0(blockchain technology 2)Wooseung Kim
╠²
Introduction to Bitcoin 2.0 or Blockchain 2.0 and Related Topicsļ╣äĒŖĖņĮöņØĖĻ│╝ ļööņ¦ĆĒäĖĒåĄĒÖö - ņØ┤ņŻ╝ņśü
ļ╣äĒŖĖņĮöņØĖĻ│╝ ļööņ¦ĆĒäĖĒåĄĒÖö - ņØ┤ņŻ╝ņśü00heights
╠²
'ļööņ¦ĆĒäĖĒåĄĒÖöņÖĆ ļ╣äĒŖĖņĮöņØĖ' ņäĖļ»Ėļéś ļ░£Ēæ£ ņ×ÉļŻī
ĒĢ£ĻĄŁņĀäņ×ÉĒåĄņŗĀņŚ░ĻĄ¼ņøÉ ņĢöĒśĖĻĖ░ņłĀņŚ░ĻĄ¼ņŗż ņØ┤ņŻ╝ņśü ņäĀņ×ä
2013.9.19141022 ßäæßģĄßå½ßäÉßģ”ßäÅßģ│ ßäåßģĄßäéßģĄ ßäÅßģźßå½ßäæßģźßäģßģźßå½ßäēßģ│ ßäŗßģ▓ßäŗßģ¦ßå╝ßäēßģźßå© ņĮöļ╣Ś ßäāßģóßäæßģŁ
141022 ßäæßģĄßå½ßäÉßģ”ßäÅßģ│ ßäåßģĄßäéßģĄ ßäÅßģźßå½ßäæßģźßäģßģźßå½ßäēßģ│ ßäŗßģ▓ßäŗßģ¦ßå╝ßäēßģźßå© ņĮöļ╣Ś ßäāßģóßäæßģŁStartupAlliance
╠²
2014ļģä 10ņøö 22ņØ╝ ņŖżĒāĆĒŖĖņŚģ ņ¢╝ļØ╝ņØ┤ņ¢ĖņŖżņŚÉņä£ ņŚ┤ļĀĖļŹś ĒĢĆĒģīĒü¼(Fintech) ļ»Ėļŗł ņ╗©ĒŹ╝ļ¤░ņŖżņŚÉņä£ ņ£ĀņśüņäØ ņĮöļ╣Ś(Korbit) ļīĆĒæ£Ļ╗śņä£ ļ░£Ēæ£ĒĢśņŗĀ ņ×ÉļŻīņ×ģļŗłļŗż.More Related Content
What's hot (20)
3.Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ (4ņ░©ņé░ņŚģĒśüļ¬ģ: Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö)
3.Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ (4ņ░©ņé░ņŚģĒśüļ¬ģ: Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö)doo rip choi
╠²
4ņ░© ņé░ņŚģĒśüļ¬ģņØś ĻĖ░ņłĀļōżņØĆ ņåīĒåĄņØä ņ£äĒĢ£ ņ¦äĒÖö ĻĖ░ņłĀļĪ£ ļ░£ņĀäļÉśņ¢┤ Ļ░ĆĻ│Ā ņ׳ļŗż.
ļ╣äņ”łļŗłņŖż ņśüņŚŁļ¦łļŗż Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄņØ┤ ĒĢäņÜöĒĢśĻ│Ā ņŗĀĻĖ░ņłĀņØä ĒÖ£ņÜ®ĒĢ£
Ļ│ĀĻ░ØņØś ļŗłņ”łņŚÉ ļ¦×ļŖö ņä£ļ╣äņŖż ņŚŁļ¤ēņØä Ļ░ĆņĀĖņĢ╝ ĒĢĀ Ļ▓āņØ┤ļŗż.
Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄņØä ņŻ╝ņĀ£ļĪ£ 3Ļ░£ņØś ņŗ£ļ”¼ņ”ł ļ¼╝ļĪ£ ļ░£Ēæ£ ņ×ÉļŻīļź╝ Ļ│Ąņ£Ā ĒĢ®ļŗłļŗż.
Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö,
1. Ļ│ĀĻ░ØņØä ņØ┤ĒĢ┤ĒĢśļŖö ļ╣ģļŹ░ņØ┤Ēä░
(The big data platform to understand customers.)
2. Ļ│ĀĻ░ØĻ│╝ ņåīĒåĄĒĢśļŖö ņØĖĻ│Ąņ¦ĆļŖź
( Artificial intelligence to communicate with customers)
3. Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ
(Block chain to connect with customer)Bitcoin ĻĖ░ņłĀļČäņäØ - ņĪ░ļé©ņłś
Bitcoin ĻĖ░ņłĀļČäņäØ - ņĪ░ļé©ņłś00heights
╠²
'ļööņ¦ĆĒäĖĒåĄĒÖöņÖĆ ļ╣äĒŖĖņĮöņØĖ' ņäĖļ»Ėļéś ļ░£Ēæ£ ņ×ÉļŻī
ĒĢ£ĻĄŁņĀäņ×ÉĒåĄņŗĀņŚ░ĻĄ¼ņøÉ ņĢöĒśĖĻĖ░ņłĀņŚ░ĻĄ¼ņŗż ņĪ░ļé©ņłś ļ░Ģņé¼
2013.9.19Scale chain ņĀ£ĒÆłņåīĻ░£
Scale chain ņĀ£ĒÆłņåīĻ░£Kangmo Kim
╠²
ScaleChain ņĀ£ĒÆłņåīĻ░£ : 12ņøö 2ņØ╝ ņĀĆļģü 7ņŗ£ ņŖżĒāĆĒŖĖņŚģ ņ¢╝ļØ╝ņØ┤ņ¢ĖņŖż
ļĖöļĪØņ▓┤ņØĖ ņØ┤ĒĢ┤ņÖĆ ĒÖ£ņÜ®
ļĖöļĪØņ▓┤ņØĖ ņØ┤ĒĢ┤ņÖĆ ĒÖ£ņÜ®Seung-Woo Kang
╠²
ļĖöļĪØņ▓┤ņØĖ(Blockchain) Ļ░£ļģÉĻ│╝ ĒÖ£ņÜ® ņé¼ļĪĆ(Use Cases)ņŚÉ ļīĆĒĢ┤ ņĀĢļ”¼ĒĢśņśĆņŖĄļŗłļŗż. ņŗĀļó░(Trust)ļź╝ ĒÖĢļ│┤ĒĢśĻĖ░ ņ£äĒĢ┤ ņé¼ņÜ®ļÉ£ ĻĖ░ņłĀņØä ļ╣äņ£ĀņĀüņ£╝ļĪ£ Ēæ£ĒśäĒĢśļĀż ļģĖļĀźĒĢśņśĆņŖĄļŗłļŗż. ĻĘĖļ”¼Ļ│Ā Ēśäņ×¼ ņ¦äĒ¢ēļÉśĻ│Ā ņ׳ļŖö ņé¼ļĪĆņŚÉ ļīĆĒĢ£ ņ×ÉļŻīļź╝ ņłśņ¦æĒĢśņśĆņŖĄļŗłļŗż. ļ╣äĒŖĖņĮöņØĖĻ│╝ ļĖöļĪØņ▓┤ņØĖ ĒĢĄņŗ¼Ļ░£ļģÉņĀĢļ”¼
ļ╣äĒŖĖņĮöņØĖĻ│╝ ļĖöļĪØņ▓┤ņØĖ ĒĢĄņŗ¼Ļ░£ļģÉņĀĢļ”¼HANSUK KIM
╠²
(ņŖ¼ļØ╝ņØ┤ļō£ ĒÖĢļīĆĒĢ┤ņä£ ļ┤ÉņŻ╝ņäĖņÜö!) ļ╣äĒŖĖņĮöņØĖņØś ĻĘ╝Ļ░äņØä ņØ┤ļŻ©Ļ│Ā ņ׳ļŖö ĻĖ░ņłĀņØĖ
ņ¦ĆĻ░æ,Ļ▒░ļל,P2P,ļĖöļĪØņ▓┤ņØĖ,ņ▒äĻĄ┤ ļō▒ņØś ņŻ╝ņĀ£ļź╝ ĒĢĄņŗ¼ļ¦ī ņÜöņĢĮĒ¢łņŖĄļŗłļŗż
ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀ ņĀüņÜ® ņé¼ļĪĆ
ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀ ņĀüņÜ® ņé¼ļĪĆICON Foundation
╠²
2019.1. Digital Strategy MBA course on Blockchain at aSSIST (a Seoul School of Integrated Sciences & Technologies)ņĀäņ×ÉņāüĻ▒░ļל ļ│┤ņĢł-ļĖöļĪØņ▓┤ņØĖ(Blockchain) ĻĖ░ņłĀ
ņĀäņ×ÉņāüĻ▒░ļל ļ│┤ņĢł-ļĖöļĪØņ▓┤ņØĖ(Blockchain) ĻĖ░ņłĀYechan Ahn
╠²
ņĀäņ×ÉņāüĻ▒░ļל ļ│┤ņĢł-ļĖöļĪØņ▓┤ņØĖ(Blockchain) ĻĖ░ņłĀļ╣äĒŖĖņĮöņØĖņŚÉ Ļ┤ĆĒĢ£ ĻĄÉņ£Īņ×ÉļŻī ņ×ģļŗłļŗż.
ļ╣äĒŖĖņĮöņØĖņŚÉ Ļ┤ĆĒĢ£ ĻĄÉņ£Īņ×ÉļŻī ņ×ģļŗłļŗż.Sung Wan Yoon
╠²
ļ╣äĒŖĖņĮöņØĖņŚÉ Ļ┤ĆĒĢ£ ņĀäļ░śņĀüņØĖ ļé┤ņÜ®ņØä ļŗżļŻ©ļŖö ĻĄÉņ£Īņ×ÉļŻī ņ×ģļŗłļŗż.
bithumb.com ĻĘ╝ļ¼┤ ņŗ£ ņ×æņä▒ĒĢ£ ņ×ÉļŻīņ×ģļŗłļŗż.ļČäņé░ĒśĢ ņ╗┤Ēō©Ēīģ Ēöīļ×½ĒÅ╝ [ņŚÉĒģīļ”¼ņøĆ]
ļČäņé░ĒśĢ ņ╗┤Ēō©Ēīģ Ēöīļ×½ĒÅ╝ [ņŚÉĒģīļ”¼ņøĆ]inucreative
╠²
ļČäņé░ĒśĢ ņ╗┤Ēō©Ēīģ Ēöīļ×½ĒÅ╝ [ņŚÉĒģīļ”¼ņøĆ]How Blockchain Works - ļĖöļĪØņ▓┤ņØĖņØś ņøÉļ”¼
How Blockchain Works - ļĖöļĪØņ▓┤ņØĖņØś ņøÉļ”¼SeokWon Kim
╠²
Brief introduction about the ideas of the Blockchain technology.
Written in Korean.
Starts with Hash function, Hashcash, proof-of-work, and how Blockchain adopted and extended the idea.
Bitcoin 2.0(blockchain technology 2)
Bitcoin 2.0(blockchain technology 2)Wooseung Kim
╠²
Introduction to Bitcoin 2.0 or Blockchain 2.0 and Related Topics3.Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ (4ņ░©ņé░ņŚģĒśüļ¬ģ: Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö)
3.Ļ│ĀĻ░ØņØä ņŚ░Ļ▓░ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ (4ņ░©ņé░ņŚģĒśüļ¬ģ: Ļ│ĀĻ░ØĻ│╝ņØś ņåīĒåĄ ņŗĀĻĖ░ņłĀņØś ņ¦äĒÖö)doo rip choi
╠²
Viewers also liked (7)
ļ╣äĒŖĖņĮöņØĖĻ│╝ ļööņ¦ĆĒäĖĒåĄĒÖö - ņØ┤ņŻ╝ņśü
ļ╣äĒŖĖņĮöņØĖĻ│╝ ļööņ¦ĆĒäĖĒåĄĒÖö - ņØ┤ņŻ╝ņśü00heights
╠²
'ļööņ¦ĆĒäĖĒåĄĒÖöņÖĆ ļ╣äĒŖĖņĮöņØĖ' ņäĖļ»Ėļéś ļ░£Ēæ£ ņ×ÉļŻī
ĒĢ£ĻĄŁņĀäņ×ÉĒåĄņŗĀņŚ░ĻĄ¼ņøÉ ņĢöĒśĖĻĖ░ņłĀņŚ░ĻĄ¼ņŗż ņØ┤ņŻ╝ņśü ņäĀņ×ä
2013.9.19141022 ßäæßģĄßå½ßäÉßģ”ßäÅßģ│ ßäåßģĄßäéßģĄ ßäÅßģźßå½ßäæßģźßäģßģźßå½ßäēßģ│ ßäŗßģ▓ßäŗßģ¦ßå╝ßäēßģźßå© ņĮöļ╣Ś ßäāßģóßäæßģŁ
141022 ßäæßģĄßå½ßäÉßģ”ßäÅßģ│ ßäåßģĄßäéßģĄ ßäÅßģźßå½ßäæßģźßäģßģźßå½ßäēßģ│ ßäŗßģ▓ßäŗßģ¦ßå╝ßäēßģźßå© ņĮöļ╣Ś ßäāßģóßäæßģŁStartupAlliance
╠²
2014ļģä 10ņøö 22ņØ╝ ņŖżĒāĆĒŖĖņŚģ ņ¢╝ļØ╝ņØ┤ņ¢ĖņŖżņŚÉņä£ ņŚ┤ļĀĖļŹś ĒĢĆĒģīĒü¼(Fintech) ļ»Ėļŗł ņ╗©ĒŹ╝ļ¤░ņŖżņŚÉņä£ ņ£ĀņśüņäØ ņĮöļ╣Ś(Korbit) ļīĆĒæ£Ļ╗śņä£ ļ░£Ēæ£ĒĢśņŗĀ ņ×ÉļŻīņ×ģļŗłļŗż.ßäÉßģ”ßäåßģĪßäÅßģĄßäćßģ®ßäāßģ│ ßäåßģóßäÄßģ”ßäēßģ®ßäĆßģóßäēßģź
ßäÉßģ”ßäåßģĪßäÅßģĄßäćßģ®ßäāßģ│ ßäåßģóßäÄßģ”ßäēßģ®ßäĆßģóßäēßģźCharles Pyo
╠²
650ļ¦ī ļŗżņÜ┤ļĪ£ļō£ņØś ļīĆĒĢ£ļ»╝ĻĄŁ 1ļō▒ Ēéżļ│┤ļō£ ņĢ▒ Ēģīļ¦łĒéżļ│┤ļō£ņØś Ļ┤æĻ│Ā ņĀ£ņĢłņä£ņ×ģļŗłļŗż. ņĀ£ņĢłņĪ░Ļ▒┤ņØĆ ļ¦żņøö Ļ░▒ņŗĀļÉ®ļŗłļŗż.ņĢöĒśĖĒÖöĒÅÉņØś ļ»ĖļלņŚÉ Ļ┤ĆĒĢ£ ļĖīļ”¼ĒĢæ
ņĢöĒśĖĒÖöĒÅÉņØś ļ»ĖļלņŚÉ Ļ┤ĆĒĢ£ ļĖīļ”¼ĒĢæCharles Pyo
╠²
ļ╣äĒŖĖņĮöņØĖ, ņØ┤ļŹöļ”¼ņøĆ, ļ”¼Ēöī ļō▒ ņĢöĒśĖĒÖöĒÅÉ ņŗ£ņןņØś Ēśäņ×¼ņÖĆ ļ»ĖļלņÖĆ Ļ┤ĆĒĢ£ ļĖīļ”¼ĒĢæ ņ×ÉļŻīņ×ģļŗłļŗż.ņĮöņ¢┤ ņØ┤ļŹöļ”¼ņøĆ
ņĮöņ¢┤ ņØ┤ļŹöļ”¼ņøĆ Jay JH Park
╠²
ļ│Ė ļ░£Ēæ£ņ×ÉļŻīņŚÉņä£ļŖö ņØ┤ļŹöļ”¼ņøĆ Ēöīļ×½ĒÅ╝ņØś ņāüņäĖ ņĢäĒéżĒģŹņ│ÉņÖĆ ĻĖ░ļ░ś ĻĖ░ņłĀ, ĻĘĖļ”¼Ļ│Ā ņŖżļ¦łĒŖĖ ņ╗©ĒŖĖļ×ÖĻ│╝ ņØ┤ļź╝ ĻĖ░ļ░śĒĢ£ DappņØś Ļ░£ļ░£ ļ░®ņĢłņŚÉ ļīĆĒĢ┤ ņåīĻ░£ĒĢ£ļŗż. ņØ┤ļŹöļ”¼ņøĆņØĆ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ļ░ś ĻĖ░ņłĀĒĢśņŚÉ ņĢöĒśĖ ĒÖöĒÅÉņØś ņāØņä▒ , ņĀäņåĪ ļō▒ ļØ╝ņØ┤Ēöäņé¼ņØ┤Ēü┤ Ļ┤Ćļ”¼ņÖĖņŚÉ ņŖżļ¦łĒŖĖ ņ╗©ĒŖĖļ×ÖņØä ņ¦ĆņøÉĒĢ£ļŗż. ņŖżļ¦łĒŖĖņ╗©ĒŖĖļ×ÖņØĆ ņä£ļĪ£ ļ¬©ļź┤ļŖö ļŗ╣ņé¼ņ×ÉĻ░äņØś Ļ│äņĢĮņØä ņżĆņłśĒĢśļÅäļĪØ Ļ░ĢņĀ£ĒĢĀ ņłś ņ׳ļŖö ņØæņÜ® ĒöäļĪ£ĻĘĖļשņØ┤ļŗż. ņ╗©ĒŖĖļ×Ö ĒöäļĪ£ĻĘĖļשņØĆ ļ░öņØ┤ĒŖĖņĮöļō£ļĪ£ ņ╗┤ĒīīņØ╝ļÉ£ Ēøä ļĖöļĪØņ▓┤ņØĖņØä ĒåĄĒĢ┤ ļ░░ĒżļÉśĻ│Ā , ļĪ£ņ╗¼ ļĪ£ļō£ņāüņŚÉņä£ ņŗżĒ¢ēļÉśļŖö ņØ╝ņóģņØś ņŚÉņØ┤ņĀäĒŖĖļØ╝ ļ│╝ ņłś ņ׳ļŗż. ņØ┤ļĀćĻ▓ī Ļ░£ļ░öļÉ£ ņŖżļ¦łĒŖĖņ╗©ĒŖĖļ×ÖņØĆ ĻĖ░ņĪ┤ ņø╣ ņØĖĒä░ĒÄśņØ┤ņŖżļź╝ ĒåĄĒĢ┤ ņĀæĻĘ╝ĒĢśĻ│Ā ĒÖ£ņÜ®ĒĢĀ ņłś ņ׳ņ£╝ļ®░ ņØ┤ļĀćĻ▓ī ņŖżļ¦łĒŖĖ ņ╗©ĒŖĖļ×Ö ĻĖ░ļ░śĒĢśņŚÉ Ļ░£ļ░£ļÉ£ ņØæņÜ® ņä£ļ╣äņŖżļź╝ DappņØ┤ļØ╝ ĒĢ£ļŗż. ßäēßģ”ßäēßģ¦ßå½1. block chain as a platform
ßäēßģ”ßäēßģ¦ßå½1. block chain as a platformJay JH Park
╠²
ņØ┤ļŹöļ”¼ņøĆ ņŚ░ĻĄ¼ĒÜī ņĀĢĻĖ░ ļ░£Ēæ£ĒÜī, ņäĖņģś1 - ņØ┤ļŹöļ”¼ņøĆ Ēöīļ×½ĒÅ╝ ņĢäĒéżĒģŹņ│ÉņŚÉ ļīĆĒĢ£ ņāüņäĖ ņäżļ¬ģßäēßģ”ßäēßģ¦ßå½2. ßäŗßģĄßäāßģźßäģßģĄßäŗßģ«ßåĘ ßäÆßģĪßåĖßäŗßģ┤ ßäŗßģĪßå»ßäĆßģ®ßäģßģĄßäīßģ│ßåĘßäĆßģ¬ ßäåßģĪßäŗßģĄßäéßģĄßå╝
ßäēßģ”ßäēßģ¦ßå½2. ßäŗßģĄßäāßģźßäģßģĄßäŗßģ«ßåĘ ßäÆßģĪßåĖßäŗßģ┤ ßäŗßģĪßå»ßäĆßģ®ßäģßģĄßäīßģ│ßåĘßäĆßģ¬ ßäåßģĪßäŗßģĄßäéßģĄßå╝Jay JH Park
╠²
ņØ┤ļŹöļ”¼ņøĆ ņŚ░ĻĄ¼ĒÜī ņĀĢĻĖ░ ļ░£Ēæ£ĒÜī, ņäĖņģś2 - ßäŗßģĄßäāßģźßäģßģĄßäŗßģ«ßåĘ ßäÆßģĪßåĖßäŗßģ┤ ßäŗßģĪßå»ßäĆßģ®ßäģßģĄßäīßģ│ßåĘßäĆßģ¬ ßäåßģĪßäŗßģĄßäéßģĄßå╝141022 ßäæßģĄßå½ßäÉßģ”ßäÅßģ│ ßäåßģĄßäéßģĄ ßäÅßģźßå½ßäæßģźßäģßģźßå½ßäēßģ│ ßäŗßģ▓ßäŗßģ¦ßå╝ßäēßģźßå© ņĮöļ╣Ś ßäāßģóßäæßģŁ
141022 ßäæßģĄßå½ßäÉßģ”ßäÅßģ│ ßäåßģĄßäéßģĄ ßäÅßģźßå½ßäæßģźßäģßģźßå½ßäēßģ│ ßäŗßģ▓ßäŗßģ¦ßå╝ßäēßģźßå© ņĮöļ╣Ś ßäāßģóßäæßģŁStartupAlliance
╠²
ßäēßģ”ßäēßģ¦ßå½2. ßäŗßģĄßäāßģźßäģßģĄßäŗßģ«ßåĘ ßäÆßģĪßåĖßäŗßģ┤ ßäŗßģĪßå»ßäĆßģ®ßäģßģĄßäīßģ│ßåĘßäĆßģ¬ ßäåßģĪßäŗßģĄßäéßģĄßå╝
ßäēßģ”ßäēßģ¦ßå½2. ßäŗßģĄßäāßģźßäģßģĄßäŗßģ«ßåĘ ßäÆßģĪßåĖßäŗßģ┤ ßäŗßģĪßå»ßäĆßģ®ßäģßģĄßäīßģ│ßåĘßäĆßģ¬ ßäåßģĪßäŗßģĄßäéßģĄßå╝Jay JH Park
╠²
Ad
Similar to Bitcoin (20)
[1ņ░©]ņĀäņ×ÉĒÖöĒÅÉņÖĆ ļ╣äĒŖĖņĮöņØĖ(151003)
[1ņ░©]ņĀäņ×ÉĒÖöĒÅÉņÖĆ ļ╣äĒŖĖņĮöņØĖ(151003)Ļ│ĀļĀżļīĆĒĢÖĻĄÉ ņĀĢļ│┤ĻĖ░ņłĀĻ▓ĮņśüĒĢÖĒÜī : ITS
╠²
1ņ░© ļ®öņØĖ ņäĖļ»Ėļéś_ĒĢĆĒģīĒü¼ AņĪ░(ņØ┤ņāüņ£ż,Ļ╣ĆņśüĻĘĀ,ņĀĢĒśäņĀĢ,ņśżņĀĢļ»╝,ĻČīņä▒Ēśä | ņĄ£ņ¦äĒśĖ)
ņĀäņ×ÉĒÖöĒÅÉ_ļ╣äĒŖĖņĮöņØĖ ļČäņäØ(15.10.03)
Ļ│ĀļĀżļīĆĒĢÖĻĄÉ ņĀĢļ│┤ĻĖ░ņłĀĻ▓ĮņśüĒĢÖĒÜī : ITS
Web: http://itsociety.co.kr/
Mail: president@itsociety.co.krļ╣äĒŖĖņĮöņØĖņ£╝ļĪ£ ņØ┤ĒĢ┤ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀ
ļ╣äĒŖĖņĮöņØĖņ£╝ļĪ£ ņØ┤ĒĢ┤ĒĢśļŖö ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀSeong-Bok Lee
╠²
ļ╣äĒŖĖņĮöņØĖņØś ņøÉļ”¼ņÖĆ ņé¼ņÜ® ĻĖ░ņłĀņŚÉ ļīĆĒĢ£ ņØ┤ĒĢ┤ļź╝ ĒåĄĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀņØä ņØ┤ĒĢ┤[ļ▓Ģļ¼┤ļ▓ĢņØĖ ļ»╝Ēøä] Ļ░ĆņāüĒåĄĒÖöŃåŹļĖöļĪØņ▓┤ņØĖņØś ĻĘ£ņĀ£ ļ░Å ņ×ģļ▓ĢļÅÖĒ¢ź
[ļ▓Ģļ¼┤ļ▓ĢņØĖ ļ»╝Ēøä] Ļ░ĆņāüĒåĄĒÖöŃåŹļĖöļĪØņ▓┤ņØĖņØś ĻĘ£ņĀ£ ļ░Å ņ×ģļ▓ĢļÅÖĒ¢źMINWHO Law Group
╠²
Ļ╣ĆĻ▓ĮĒÖś ļ▓Ģļ¼┤ļ▓ĢņØĖ ļ»╝Ēøä ļīĆĒæ£ļ│ĆĒśĖņé¼Ļ░Ć ņ¦Ćļé£ 12ņØ╝, ņ¦ĆļööļäĘņĮöļ”¼ņĢä ņŻ╝ņĄ£ļĪ£ ņŚ┤ļ”░ ņĀ£3ĒÜī ĒīīņØ┤ļéĖņŖż ņØ┤ļģĖļ▓ĀņØ┤ņģś ņ╗©ĒŹ╝ļ¤░ņŖżņŚÉņä£ ļ░£Ēæ£ĒĢ£ ņ×ÉļŻīņ×ģļŗłļŗż. Ļ╣Ć ļ│ĆĒśĖņé¼ļŖö ļ░£Ēæ£ļź╝ ĒåĄĒĢ┤ ņÜ░ļ”¼ļéśļØ╝ņÖĆ ņÖĖĻĄŁņØś Ļ░ĆņāüĒåĄĒÖö ĻĘ£ņĀ£, ļĖöļĪØņ▓┤ņØĖ Ļ┤ĆļĀ© ņ×ģļ▓ĢĒśäĒÖ® ļō▒ņŚÉ ļīĆĒĢ┤ ņāüņäĖĒ׳ ņäżļ¬ģĒĢśņśĆņŖĄļŗłļŗż.[ļ▓Ģļ¼┤ļ▓ĢņØĖļ»╝Ēøä] Ļ░Ćņāüņ×Éņé░ ļ▓ĢņĀü ņåīņåĪņāü ņ¤üņĀÉ
[ļ▓Ģļ¼┤ļ▓ĢņØĖļ»╝Ēøä] Ļ░Ćņāüņ×Éņé░ ļ▓ĢņĀü ņåīņåĪņāü ņ¤üņĀÉMINWHO Law Group
╠²
Ļ░Ćņāüņ×Éņé░ņØä ļæö ļ▓ĢņĀü ļČäņ¤üņØ┤ ņ”ØĻ░ĆĒĢ©ņŚÉ ļö░ļØ╝ Ļ░Ćņāüņ×Éņé░ņØś ļ▓ĢņĀü ņ¦Ćņ£äņÖĆ ņØ┤ņŚÉ ļīĆĒĢ£ ņÜ░ļ”¼ ļ▓ĢņøÉņØś ĒīÉļŗ© ļśÉĒĢ£ ņżæņÜöĒĢ┤ņĪīņŖĄļŗłļŗż.
ņÜ░ļ”¼ ļ▓ĢņĀ£ļÅä ļśÉĒĢ£ ĒŖ╣ĻĖłļ▓Ģ(ĒŖ╣ņĀĢ ĻĖłņ£ĄĻ▒░ļלņĀĢļ│┤ņØś ļ│┤Ļ│Ā ļ░Å ņØ┤ņÜ® ļō▒ņŚÉ Ļ┤ĆĒĢ£ ļ▓ĢļźĀ)ņØä ņĀ£ņĀĢĒĢśņŚ¼ Ļ░Ćņāüņ×Éņé░ņØä ļæö ļ▓ĢņĀü ĻĖ░ņżĆņØä ļ¦łļĀ©ņĮöņ×É ļģĖļĀźņØä ĻĖ░ņÜĖņØ┤Ļ│Ā ņ׳ņ£╝ļ®░, Ļ░Ćņāüņ×Éņé░ ņé¼ņŚģņ×ÉļŖö ļ▓ĢļĀ╣ņāü ĻĖ░ņżĆņŚÉ ļö░ļØ╝ ņŗĀĻ│Ā ņØśļ¼┤ ļō▒ņØä ļČĆļŗ┤ĒĢśĻ▓ī ļÉ®ļŗłļŗż.
Ļ╣ĆĻ▓ĮĒÖś ļ│ĆĒśĖņé¼ļŖö Ļ░ĢņŚ░ņ×ÉļŻīļź╝ ĒåĄĒĢ┤ Ļ░Ćņāüņ×Éņé░ņØä ļæö ļ▓ĢņĀü ņåīņåĪņŚÉņä£ ņŻ╝ņÜöĒĢśĻ▓ī ļŗżļŻ©ņ¢┤ņ¦ä ņ¤üņĀÉņé¼ĒĢŁĻ│╝ ņÜ░ļ”¼ ļ▓ĢņøÉņØś ĒīÉļŗ© ĻĖ░ņżĆņŚÉ ļīĆĒĢ┤ ņ×ÉņäĖĒ׳ ņäżļ¬ģĒĢśņśĆņŖĄļŗłļŗż. ļ╣äĒŖĖņĮöņØĖ, ĒÖöĒÅÉ ļģ╝ņ¤üņØä ļäśņ¢┤ Ēöīļ×½ĒÅ╝ņ£╝ļĪ£ņä£ņØś ņ×Āņ×¼ļĀź ļČĆņāü ņżæ
ļ╣äĒŖĖņĮöņØĖ, ĒÖöĒÅÉ ļģ╝ņ¤üņØä ļäśņ¢┤ Ēöīļ×½ĒÅ╝ņ£╝ļĪ£ņä£ņØś ņ×Āņ×¼ļĀź ļČĆņāü ņżæKunwoo Kim
╠²
ļ╣äĒŖĖņĮöņØĖņØ┤ ĒÖöĒÅÉļź╝ ļīĆņ▓┤ĒĢĀ ņłś ņ׳ņØäņ¦ĆņŚÉ ļīĆĒĢ£ ĒÜīņØśļĪĀņØ┤ ļČĆĻ░üļÉśļŖö Ļ░ĆņÜ┤ļŹ░ņä£ļÅä ļ╣äĒŖĖņĮöņØĖ ņāØĒā£Ļ│äļŖö ņĀÉņĀÉ ļŹö ĒÖĢļīĆļÉśĻ│Ā ņ׳ļŗż. ļ╣äĒŖĖņĮöņØĖ ĻĖ░ņłĀņØś ņÜöņ▓┤ļŖö ņĀ£3ņØś Ļ│ĄņØĖĻĖ░Ļ┤ĆņØ┤ ņŚåņØ┤ļÅä ļŗ╣ņé¼ņ×ÉĻ░ä ņŗĀļó░ļź╝ ĻĄ¼ņČĢĒĢ£ Ļ▓āņØ┤ļØ╝ ĒĢĀ ņłś ņ׳ļŗż. ļ╣äĒŖĖņĮöņØĖņØĆ ļ░śļō£ņŗ£ ĒÖöĒÅÉĻ░Ć ņĢäļŗłļŹöļØ╝ļÅä ņ×æĻ▓īļŖö ņŗĀņÜ®ņ╣┤ļō£, Ļ│äņóīņØ┤ņ▓┤ļéś PayPal ļō▒Ļ│╝ Ļ░ÖņØĆ ņ¦ĆĻĖēņłśļŗ©ņØś Ļ▓Įņ¤üņ×ÉļĪ£ ņ×Éļ”¼ļ¦żĻ╣ĆĒĢĀ ņłś ņ׳ļŗż. ļśÉĒĢ£ Ļ│ĄņØĖņØĖņ”Øņä£ļź╝ ļīĆņ▓┤ĒĢśļŖö ņØĖņ”Øņŗ£ņŖżĒģ£ņ£╝ļĪ£ ĒÖĢņןļÉĀ ņłśļÅä ņ׳ļŗż. ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀĻ│╝ ņĢöĒśĖĒÖöĒÅÉ Ļ▓ĮņĀ£
ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀĻ│╝ ņĢöĒśĖĒÖöĒÅÉ Ļ▓ĮņĀ£Taehee Kim
╠²
- ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀņŚÉ ļīĆĒĢ┤ ņŗ£Ļ░üņĀüņ£╝ļĪ£ ņēĮĻ▓ī ĒÆĆņØ┤ĒĢśĻ│Āņ×É Ē¢łņ£╝ļ®░, ICOņŚÉ ļīĆĒĢ£ Ļ░£Ļ┤äņĀüņØĖ ņäżļ¬ģĻ│╝ ņĮöņØĖņØś Ļ░ĆĻ▓®ņŚÉ ņśüĒ¢źņØä ļ»Ėņ╣śļŖö ņÜöņåīņŚÉ ļīĆĒĢ┤ Ļ░äļץĒĢ£ ļČäņäØņØä ĒżĒĢ©ĒĢ©
- ļĖöļĪØņ▓┤ņØĖĻ│╝ Ļ░ĆņāüĒÖöĒÅÉļź╝ ĻĄ¼ļČäĒĢĀ ņżä ļ¬©ļź┤ļŖö ļīĆņżæņØä ļīĆņāüņ£╝ļĪ£ ĻĄÉņ£Īņ×ÉļŻīļĪ£ ĒÖ£ņÜ®ĒĢśĻĖ░ ņÜ®ņØ┤ĒĢ©[ļ▓Ģļ¼┤ļ▓ĢņØĖ ļ»╝Ēøä] ņĢöĒśĖĒÖöĒÅÉ┬ĘļĖöļĪØņ▓┤ņØĖņØś ĻĘ£ņĀ£ ļ░Å ņ×ģļ▓ĢļÅÖĒ¢ź
[ļ▓Ģļ¼┤ļ▓ĢņØĖ ļ»╝Ēøä] ņĢöĒśĖĒÖöĒÅÉ┬ĘļĖöļĪØņ▓┤ņØĖņØś ĻĘ£ņĀ£ ļ░Å ņ×ģļ▓ĢļÅÖĒ¢źMINWHO Law Group
╠²
Ļ╣ĆĻ▓ĮĒÖś ļ▓Ģļ¼┤ļ▓ĢņØĖ ļ»╝Ēøä ļīĆĒæ£ļ│ĆĒśĖņé¼ļŖö 2018ļģä 4ņøö 12ņØ╝ ņ╣┤ņØ┤ņŖżĒŖĖ ņĄ£Ļ│ĀĻ▓Įņśüņ×É Ļ│╝ņĀĢņŚÉņä£ 'ņĢöĒśĖĒÖöĒÅÉ┬ĘļĖöļĪØņ▓┤ņØĖņØś ĻĘ£ņĀ£ ļ░Å ņ×ģļ▓ĢļÅÖĒ¢ź'ņŚÉ ļīĆĒĢ┤ Ļ░ĢņØśļź╝ ņŗżņŗ£Ē¢łņŖĄļŗłļŗż.
Ļ╣Ć ļ│ĆĒśĖņé¼ļŖö ņĢöĒśĖĒÖöĒÅÉ, ļĖöļĪØņ▓┤ņØĖņØś ņĀäļ░śņĀüņØĖ ļé┤ņÜ®Ļ│╝ Ļ┤ĆļĀ© ļ╣äņ”łļŗłņŖżļź╝ ņ£äĒĢ£ ļ▓ĢņĀ£ļÅäļź╝ ņäżļ¬ģĒĢśĻ│Ā ņé¼ļĪĆļÅä ņåīĻ░£Ē¢łņŖĄļŗłļŗż. ļśÉ ICOņŚÉ ļīĆĒĢ£ ĻĘ£ņĀ£ņÖĆ Ē¢źĒøä ņÜ░ļ”¼ļéśļØ╝ņØś ļ▓ĢņĀ£ļÅä ņĀĢļ╣äļ░®Ē¢źļÅä ņĀ£ņŗ£Ē¢łņŖĄļŗłļŗż.[WeFocus] ļĖöļĪØņ▓┤ņØĖ ĒŖ╣ĒŚł ĒÖĢļ│┤ ņĀäļץ_20180916
[WeFocus] ļĖöļĪØņ▓┤ņØĖ ĒŖ╣ĒŚł ĒÖĢļ│┤ ņĀäļץ_20180916Luke Sunghyun Kim
╠²
- Ļ╣Ćņä▒Ēśä ļ│Ćļ”¼ņé¼
- www.WeFocus.kr
- ņ£äĒżņ╗żņŖż ĒŖ╣ĒŚłļ▓ĢļźĀņé¼ļ¼┤ņåī ļīĆĒæ£ ļ│Ćļ”¼ņé¼(2022.10~)
- ļ│Ćļ”¼ņé¼(2010~), ĻĖ░ņłĀĻ░Ćņ╣śĒÅēĻ░Ćņä£(2015~), ĻĖ░ņłĀĻ▒░ļלņé¼(2019~)
- ņØĖĻ│Ąņ¦ĆļŖź, ļ╣ģļŹ░ņØ┤Ēä░, Ēü┤ļØ╝ņÜ░ļō£, ļĖöļĪØņ▓┤ņØĖ, VR/AR, ļ│┤ņĢł, Web/App/SW/Ēöīļ×½ĒÅ╝ ļō▒ ĻĖ░ņłĀļČäņĢ╝ ņĀäļ¼Ė
- 2021 Ļ│ĀļĀżļīĆĒĢÖĻĄÉ ĻĖ░ņłĀĻ▓ĮņśüņĀäļ¼ĖļīĆĒĢÖņøÉ ĻĖ░ņłĀĻ▓ĮņśüĒĢÖĻ│╝ ņäØņé¼
- 2015 ĒĢ£ĻĄŁļ░®ņåĪĒåĄņŗĀļīĆĒĢÖĻĄÉ ļ▓ĢĒĢÖĻ│╝
- 2011 ĒĢ£ņ¢æļīĆĒĢÖĻĄÉ(ņä£ņÜĖ) ņĀĢļ│┤ĒåĄņŗĀĒĢÖļČĆ
- ļīĆĒĢ£ļ│Ćļ”¼ņé¼ĒÜī ņĀ£7ļīĆ ļīĆņØśņøÉ
- ļ▓ĢņøÉĒ¢ēņĀĢņ▓ś ņĀäļ¼Ėņŗ¼ļ”¼ņ£äņøÉ Ēøäļ│┤ņ×É
- ņĪ░ļŗ¼ņ▓Ł ņÜ░ņłśņĀ£ĒÆł/ĒśüņŗĀņĀ£ĒÆł ņ¦ĆņĀĢ ņŗ¼ņé¼ņ£äņøÉ
- ņĀĢļ│┤ĒåĄņŗĀņé░ņŚģņ¦äĒØźņøÉ, ņĀĢļ│┤ĒåĄņŗĀĻĖ░ĒÜŹĒÅēĻ░ĆņøÉ, ĒĢ£ĻĄŁņØĖĒä░ļäĘņ¦äĒØźņøÉ, ĒĢ£ĻĄŁļ░®ņåĪĒåĄņŗĀņĀäĒīīņ¦äĒØźņøÉ, ĒĢ£ĻĄŁņĮśĒģÉņĖĀņ¦äĒØźņøÉ ļō▒ ĒÅēĻ░Ćņ£äņøÉ
- ņä▒ļé©ņé░ņŚģņ¦äĒØźņøÉ ņ░ĮņŚģļ│┤ņ£Īņä╝Ēä░ ņÜ┤ņśüņ£äņøÉ
- ņżæņåīļ▓żņ▓śĻĖ░ņŚģļČĆ ņä▒ļŖźņØĖņ”Ø(EPC) ĒÅēĻ░Ćņ£äņøÉ, ļ╣äņ”łļŗłņŖżņ¦ĆņøÉļŗ©
- ĻĄŁĻ░ĆĻĖ░ņłĀĒæ£ņżĆņøÉ ņŗĀĻĖ░ņłĀ(NET), ņŗĀņĀ£ĒÆł(NEP) ņØĖņ”Ø ņŗ¼ņé¼ņ£äņøÉ
- ĒĢ£ĻĄŁņé░ņŚģĻĖ░ņłĀĒÅēĻ░ĆĻ┤Ćļ”¼ņøÉ ĻĖ░ņłĀņé¼ņŚģĒÖö ņĮöļööļäżņØ┤Ēä░, IP ņĀäļ¼ĖĻ░Ć, Ēæ£ņżĆņØĖņ”Ø ņĀäļ¼ĖĻ░Ć
- ļīĆĒĢ£ļ│Ćļ”¼ņé¼ĒÜī ņ¦ĆņŗØņ×¼ņé░ ņåīņåĪņŗżļ¼┤ ņŚ░ņłś ņłśļŻī
- ĒĢ£ĻĄŁĒŖ╣ĒŚłņĀĢļ│┤ņøÉ Ēæ£ņżĆĒŖ╣ĒŚł ņĀäļ¼Ėļ│Ćļ”¼ņé¼ ņ¢æņä▒ĻĄÉņ£Ī ņłśļŻī
- ĒĢ£ĻĄŁņ¦ĆņŗØņ×¼ņé░ņĀäļץņøÉ IP-R&DņĀäļץņłśļ”Į ļ░®ļ▓ĢļĪĀ ĻĄÉņ£Ī ņłśļŻī
- ĒĢ£ĻĄŁļ░£ļ¬ģņ¦äĒØźĒÜī IPĻĖłņ£ĄņĀäļ¼ĖĻ░Ć ņ¢æņä▒ĻĄÉņ£Ī ņłśļŻī
- ĒĢ£ĻĄŁņé░ņŚģĻĖ░ņłĀņ¦äĒØźĒśæĒÜī TRIZĒÖ£ņÜ®ĻĄÉņ£Ī ņłśļŻī
- ĒĢ£ĻĄŁļ▓żņ▓śņ║ÉĒö╝ĒāłĒśæĒÜī ļ▓żņ▓śņ║ÉĒö╝Ēāłļ”¼ņŖżĒŖĖ ņĀäļ¼ĖĻ░ĆĻ│╝ņĀĢ ņłśļŻī
- COLUMBIA UNIV., School of International and Public Affairs(SIPA), Fostering Innovation: An Integrated Approach Ļ│╝ņĀĢ ņłśļŻī
- GEORGE WASHINGTON UNIV., Office of Innovation & Entrepreneurship, LEAN INNOVATION Ļ│╝ņĀĢ ņłśļŻī
- HARVARD BUSINESS SCHOOL ONLINE, Entrepreneurship Essentials Ļ│╝ņĀĢ ņłśļŻī[Partner TechForum] ĻĖłņ£Ą ņä£ļ╣äņŖżļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĄ¼ņČĢņé¼ļĪĆ ņåīĻ░£
[Partner TechForum] ĻĖłņ£Ą ņä£ļ╣äņŖżļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĄ¼ņČĢņé¼ļĪĆ ņåīĻ░£Amazon Web Services Korea
╠²
ņŚ░ņé¼: Blocko Ļ╣ĆņČ®ĒśĖ ĒīĆņן[ļ╣äĒŖĖļ▓Āļ”¼ĒīīĒŖĖļäłņŖżļŹ░ņØ┤] ļ╣äĒŖĖļ▓Āļ”¼ ļ╣äņ”łļŗłņŖż ņåöļŻ©ņģś ņåīĻ░£ ņ×ÉļŻī
[ļ╣äĒŖĖļ▓Āļ”¼ĒīīĒŖĖļäłņŖżļŹ░ņØ┤] ļ╣äĒŖĖļ▓Āļ”¼ ļ╣äņ”łļŗłņŖż ņåöļŻ©ņģś ņåīĻ░£ ņ×ÉļŻīBitberry
╠²
[ļ╣äĒŖĖļ▓Āļ”¼ĒīīĒŖĖļäłņŖżļŹ░ņØ┤] ļ╣äĒŖĖļ▓Āļ”¼ ļ╣äņ”łļŗłņŖż ņåöļŻ©ņģś ņåīĻ░£ ņ×ÉļŻīĻ░£ņØĖņĀĢļ│┤ ņäĖļ»Ėļéś(190522) - Session 3 Ļ╣ĆļÅÖĒÖś ļ│ĆĒśĖņé¼
Ļ░£ņØĖņĀĢļ│┤ ņäĖļ»Ėļéś(190522) - Session 3 Ļ╣ĆļÅÖĒÖś ļ│ĆĒśĖņé¼ļ▓Ģļ¼┤ļ▓ĢņØĖ ļööļØ╝ņØ┤ĒŖĖ / D'LIGHT Law Group
╠²
ŌĆś4ņ░©Ēśüļ¬ģ ņŗ£ļīĆņÖĆ Ļ░£ņØĖņĀĢļ│┤ņØś ĻĘ£ņĀ£ ļ░Å ņØ┤ņÜ®ŌĆÖ ņäĖļ»Ėļéś
ļ▓Ģļ¼┤ļ▓ĢņØĖ ļööļØ╝ņØ┤ĒŖĖļŖö 5ņøö 22ņØ╝(ņłś) ņä£ņÜĖ ņä£ņ┤łĻĄ¼ ļō£ļ”╝Ēöīļ¤¼ņŖż Ļ░Ģļé© ņØ┤ļ▓żĒŖĖĒÖĆņŚÉņä£ ļ╣ģļŹ░ņØ┤Ēä░, ņØĖĻ│Ąņ¦ĆļŖź, ļĖöļĪØņ▓┤ņØĖ ļō▒ 4ņ░© ņé░ņŚģĒśüļ¬ģ ņŗ£ļīĆņØś ļŗżņ¢æĒĢ£ ĻĖ░ņłĀ ņśüņŚŁņŚÉņä£ ļ░£ņāØĒĢśļŖö Ļ░£ņØĖņĀĢļ│┤ ņØ┤ņŖłļź╝ ļģ╝ņØśĒĢśļŖö ņäĖļ»Ėļéśļź╝ Ļ░£ņĄ£ĒĢśņśĆņŖĄļŗłļŗż.
ņØ┤ļ▓ł ņäĖļ»ĖļéśļŖö ļ▓Ģļ¼┤ļ▓ĢņØĖ ļööļØ╝ņØ┤ĒŖĖ, ZDNet Korea Ļ░Ć Ļ│ĄļÅÖņŻ╝ņĄ£ĒĢśĻ│Ā ĒĢ£ĻĄŁņØĖĒä░ļäĘņ¦äĒØźņøÉ, ĒĢ£ĒÖö ļō£ļ”╝Ēöīļ¤¼ņŖżĻ░Ć ĒøäņøÉĒĢśļŖö ņäĖļ»ĖļéśļĪ£ņä£ ļ╣ģļŹ░ņØ┤Ēä░, ņØĖĻ│Ąņ¦ĆļŖź, ļĖöļĪØņ▓┤ņØĖ ļō▒ 4ņ░© ņé░ņŚģĒśüļ¬ģ ņŗ£ļīĆņØś ĒĢĄņŗ¼ ĻĖ░ņłĀ ļ░Å Ļ░£ņØĖņĀĢļ│┤ ļ│┤ĒśĖ ņØ┤ņŖłņŚÉ Ļ┤Ćņŗ¼ņ׳ļŖö ņé¼ļ×īņØ┤ļ®┤ ļłäĻĄ¼ļéś ņ░ĖĻ░ĆĒĢĀ ņłś ņ׳ļŖö Ē¢ēņé¼ņśĆņŖĄļŗłļŗż.
ņäĖļ»ĖļéśņØś ĒöäļĪ£ĻĘĖļשņØĆ ļ©╝ņĀĆ ĒĢ£ĻĄŁņØĖĒä░ļäĘņ¦äĒØźņøÉ(KISA)ņØś ĻČīĒśäņżĆ Ļ░£ņØĖņĀĢļ│┤ļ│┤ĒśĖļ│ĖļČĆņןņØ┤ ŌĆś4ņ░©Ēśüļ¬ģ ņŗ£ļīĆņØś Ļ░£ņØĖņĀĢļ│┤ļ│┤ĒśĖ ņĀĢņ▒ģļ░®Ē¢źņØ┤ļØ╝ļŖö ņŻ╝ņĀ£ņØś Keynote SpeechļĪ£ ņŗ£ņ×æļÉśņŚłĻ│Ā, ņ£żņäØļ╣ł ņśżĒöłļĖöļĪØņ▓┤ņØĖĒżļ¤╝ ļīĆĒæ£ņØ┤ņ×É ļööļØ╝ņØ┤ĒŖĖņØś ņłśņäØņŚ░ĻĄ¼ņøÉņØ┤ ŌĆśĻĖ░ņłĀņØś ņ£ĄĒĢ®ņŗ£ļīĆ(-ļ╣ģļŹ░ņØ┤Ēä░, AI ĻĘĖļ”¼Ļ│Ā ļĖöļĪØņ▓┤ņØĖ)ŌĆÖ ņØä ĒĢ£Ēś£ņäĀ ļ│ĆĒśĖņé¼Ļ░Ć ŌĆśļ╣ģļŹ░ņØ┤Ēä░ ĒÖ£ņÜ®Ļ│╝ Ļ░£ņØĖņĀĢļ│┤ņØś ļ▓ĢņĀü ņØ┤ņŖłŌĆÖ ņŚÉ ļīĆĒĢ┤ņä£ ņĢīņĢä ļ│┤ņĢśņŖĄļŗłļŗż. ņØ┤ņ¢┤ņä£ Ļ╣ĆļÅÖĒÖś ļ│ĆĒśĖņé¼Ļ░Ć ŌĆśļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀĻ│╝ Ļ░£ņØĖņĀĢļ│┤ņØś ļ│┤ĒśĖŌĆÖ ņŚÉ ļīĆĒĢ┤ņä£ ļģ╝ņØśĒĢśņśĆĻ│Ā, ĒĢ£ĻĄŁņØĖĒä░ļäĘņ¦äĒØźņøÉ(KISA)ņØś ņĄ£Ļ┤æĒؼ Ļ░£ņØĖņĀĢļ│┤ņĀĢņ▒ģļŗ©ņןņØ┤ ŌĆśEU GDPR ņŗ£Ē¢ē 1ļģäņØś ĒÜīĻ│ĀņÖĆ ņĀäļ¦ØŌĆÖ ņŚÉ ļīĆĒĢ┤ņä£ ņé┤ĒÄ┤ļ│┤ņĢśņŖĄļŗłļŗż. ļ¦łņ¦Ćļ¦ēņ£╝ļĪ£ ĒÖ®Ēś£ņ¦ä ļ│ĆĒśĖņé¼Ļ░Ć ŌĆś4ņ░©Ēśüļ¬ģ ņŗ£ļīĆņØś Ļ░£ņØĖņĀĢļ│┤ ĒÖ£ņÜ® Best PracticeŌĆÖ ļØ╝ļŖö ņŻ╝ņĀ£ļĪ£ Ļ░ĢņŚ░ņØä ņ¦äĒ¢ēĒĢśņśĆņŖĄļŗłļŗż.
[ņäĖļ»Ėļéś ļ░£Ēæ£ņ×ÉļŻī]
Keynote Speech _ 4ņ░©Ēśüļ¬ģ ņŗ£ļīĆņØś Ļ░£ņØĖņĀĢļ│┤ļ│┤ĒśĖ ņĀĢņ▒ģļ░®Ē¢ź _ ĻČīĒśäņżĆ Ļ░£ņØĖņĀĢļ│┤ļ│┤ĒśĖļ│ĖļČĆņן(ĒĢ£ĻĄŁņØĖĒä░ļäĘņ¦äĒØźņøÉ)
Session 1 _ ĻĖ░ņłĀņØś ņ£ĄĒĢ® ņŗ£ļīĆ-ļ╣ģļŹ░ņØ┤Ēä░, AI ĻĘĖļ”¼Ļ│Ā ļĖöļĪØņ▓┤ņØĖ _ ņ£żņäØļ╣ł ņłśņäØņŚ░ĻĄ¼ņøÉ
Session 2 _ ļ╣ģļŹ░ņØ┤Ēä░ ĒÖ£ņÜ®Ļ│╝ Ļ░£ņØĖņĀĢļ│┤ņØś ļ▓ĢņĀü ņØ┤ņŖł _ ĒĢ£Ēś£ņäĀ ļ│ĆĒśĖņé¼
Session 3 _ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņłĀĻ│╝ Ļ░£ņØĖņĀĢļ│┤ņØś ļ│┤ĒśĖ _ Ļ╣ĆļÅÖĒÖś ļ│ĆĒśĖņé¼
Session 4 _ EU GDPR ņŗ£Ē¢ē 1ļģäņØś ĒÜīĻ│ĀņÖĆ ņĀäļ¦Ø _ ņĄ£Ļ┤æĒؼ Ļ░£ņØĖņĀĢļ│┤ņĀĢņ▒ģļŗ©ņן(ĒĢ£ĻĄŁņØĖĒä░ļäĘņ¦äĒØźņøÉ)
Session 5 _ 4ņ░©Ēśüļ¬ģ ņŗ£ļīĆņØś Ļ░£ņØĖņĀĢļ│┤ ĒÖ£ņÜ® Best Practice _ ĒÖ®Ēś£ņ¦ä ļ│ĆĒśĖņé¼Blockchain Basic Concept Theory (Beginner Version) / ņ┤łļ│┤ņ×Éļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņ┤ł Ļ░£ļģÉ ņØ┤ļĪĀ
Blockchain Basic Concept Theory (Beginner Version) / ņ┤łļ│┤ņ×Éļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņ┤ł Ļ░£ļģÉ ņØ┤ļĪĀMinwoo Kim
╠²
Document Title: Blockchain Basic Concept Theory (Beginner Version) / ņ┤łļ│┤ņ×Éļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņ┤ł Ļ░£ļģÉ ņØ┤ļĪĀ
#1 ņĀĆņ×É ņåīĻ░£
#2 ļĖöļĪØņ▓┤ņØĖ ņåīĻ░£
#3 ļĖöļĪØ ņåīĻ░£
#4 ļĖöļĪØņ▓┤ņØĖņØś ĻĄ¼ņĪ░ ņåīĻ░£
#5 ļĖöļĪØĒĢ┤ņŗ£ ņåīĻ░£
#6 ļĖöļĪØņ▓┤ņØĖņØś ņóģļźś
#7 ņ×æņŚģņ”Øļ¬ģ ņåīĻ░£
#8 ņ¦ĆļČäņ”Øļ¬ģ ņåīĻ░£
#9 ļĖöļĪØņ▓┤ņØĖ ļÅÖņ×æļ░®ņŗØ
#10 Swiftļź╝ ņØ┤ņÜ®ĒĢ£ Ļ░äļŗ©ĒĢ£ ļĖöļĪØņ▓┤ņØĖ ņøÉļ”¼ ĻĄ¼ĒśäĒĢśĻĖ░
#11 P2P ņåīĻ░£
#12 ļ╣äĒŖĖņĮöņØĖ ņåīĻ░£
#13 ņĢīĒŖĖņĮöņØĖ ņåīĻ░£
========================================>
ļ¼Ėņä£ņŚÉ ļīĆĒĢ£ ņ¦łļ¼Ė ņé¼ĒĢŁ ļ░Å ņśżĒāłņ×É ļ░£Ļ▓¼ ņŗ£ ļ▓łĻ▒░ļĪŁļŹöļØ╝ļÅä ļ¼ĖņØśĒĢ┤ņŻ╝ņŗ£ļ®┤ Ļ░Éņé¼ĒĢśĻ▓ĀņŖĄļŗłļŗż.
E-mail: escapelazy@gmail.com / kimminwoo0807@uos.ac.kr
LinkedIn: https://www.linkedin.com/in/%EB%AF%BC%EC%9A%B0-%EA%B9%80-50a344151/
20181219 digital token regualtion re exchange & ico ted koo
20181219 digital token regualtion re exchange & ico ted koo TEK & LAW, LLP
╠²
ļ»ĖĻĄŁ ĒĢśņøÉņŚÉņä£ ņĢöĒśĖĒÖöĒÅÉļź╝ ļööņ¦ĆĒäĖ ĒåĀĒü░ņ£╝ļĪ£ ļ¬ģļ¬ģĒĢśĻ│Ā, ņ”ØĻČīļ▓Ģ ņĀüņÜ®ņØä ļ░░ņĀ£ĒĢśļŖö ļ▓ĢņĢłņØ┤ ņĀ£ņČ£ļÉśņŚłņŖĄļŗłļŗż.
ņĀ£Ļ░Ć ņ¦Ćļé£ 11.6. ĻĄŁĒÜīņŚÉņä£ ļ»╝ļ│æļæÉ ņØśņøÉ ņŻ╝ņĄ£ļĪ£ Ļ░£ņĄ£ĒĢ£ ņäĖļ»ĖļéśņŚÉņä£ ļ░£Ēæ£ĒĢ£ ņ×ÉļŻīļź╝ ļ│┤ļé┤ļō£ļ”Įļŗłļŗż.
Ļ░£ņÜöļŖö
- Ēü¼ļ”ĮĒåĀļź╝ ļööņ¦ĆĒäĖ ĒåĀĒü░ņ£╝ļĪ£ ļ¬ģļ¬ģ
- ļ╣äņ”ØĻČīĒśĢ ĒåĀĒü░ņØĆ ļööņ¦ĆĒäĖ ņ×Éņé░ņØ┤ļ»ĆļĪ£ Ļ▒░ļלņåīņŚÉ ĒŖ╣ļ│äĒĢ£ ĻĘ£ņĀ£ ĒĢäņÜö ņŚåņØī
- ņ”ØĻČīĒśĢ ĒåĀĒü░ Ļ▒░ļלņåīļŖö ņĀäĻĖłļ▓Ģņāü ļō▒ļĪØņĀ£ ĻĘ£ņĀĢ
- ĒåĀĒü░ ņäĀĒīÉļ¦ż(ICO)ļŖö ņĀäĻĖłļ▓Ģņāü ļō▒ļĪØņĀ£ ĻĘ£ņĀĢ. ļŗżļ¦ī, ņä£ļ╣äņŖż ņČ£ņŗ£ Ēøä ĒåĀĒü░ĒīÉļ¦żļŖö ņŗżļ¼╝Ļ▒░ļלņØ┤ļ»ĆļĪ£ ĻĘ£ņĀ£ ļČłĒĢäņÜö.190320 [ict convergence 2019] blockchain financing
190320 [ict convergence 2019] blockchain financingEunseong Kang
╠²
ļĖöļĪØņ▓┤ņØĖņØĆ ĻĘ╝ļ│ĖņĀüņ£╝ļĪ£ ļŗżņłśņØś ļģĖļō£ņŚÉ Ļ░ÖņØĆ ļé┤ņÜ®ņØä ĻĖ░ļĪØĒĢ©ņ£╝ļĪ£ņŹ© ļ¼┤Ļ▓░ņä▒, Ļ░ĆņÜ®ņä▒, Ēł¼ļ¬ģņä▒ņØä ļ│┤ņןĒĢśĻ│Ā ņØ┤ļź╝ ĻĖ░ļ░śņ£╝ļĪ£ ņŗĀļó░ļź╝ ņāØņä▒ĒĢśļŖö ĻĖ░ņłĀņØ┤ĻĖ░ ļĢīļ¼ĖņŚÉ ļŗ©ņ£ä ĒŖĖļ×£ņףņģś ļŗ╣ ņåīņÜöļÉśļŖö ņ╗┤Ēō©Ēīģ ĒīīņøīņÖĆ ņĀĆņןĻ│ĄĻ░äņØ┤ ļ¦ÄņØĆ ŌĆśļ╣äņŗ╝ŌĆÖĻĖ░ņłĀņØ┤ļŗż. ļö░ļØ╝ņä£ ņØ┤ļź╝ ĒÖ£ņÜ®ĒĢśļŖö ņØæņÜ® ņŚŁņŗ£ ņØ┤ņŚÉ ņĀüĒĢ®ĒĢ┤ņĢ╝ ĒĢ£ļŗż. ĻĖ░ņĪ┤ ĻĄŁĻ░ĆņÖĆ ĻĖłņ£ĄĻĖ░Ļ┤ĆņØś ŌĆśņŗĀļó░ņä▒ŌĆÖņØä ĻĘ╝Ļ▒░ļĪ£ ĒĢ£ ņŗĀņÜ®ņ░ĮņĪ░ļŖö 2008ļģä ĻĖłņ£Ąņ£äĻĖ░ņŚÉņä£ ļ¼ĖņĀ£ļź╝ ļō£ļ¤¼ļāłĻ│Ā ņ¦ĆņåŹņĀüņØĖ ĒåĄĒÖöļ¤ē ņ”ØĻ░Ćļź╝ ĒåĄĒĢ£ ņØĖĒöīļĀłņØ┤ņģśņØĆ ĒĢ£ ņé¼ĒÜīņØś ļČĆļź╝ ņāüņ£ä 10%ņØś ņé¼ļ×īļōżņŚÉĻ▓ī ņĀÉņĀÉ ņ¦æņżæņŗ£ĒéżļŖö ņåīļōØ(ņ×Éņé░) ļČłĒÅēļō▒ņØä ņŗ¼ĒÖöņŗ£ņ╝£ ņÖöļŗż. ĒĢ£ĻĄŁ ņĀ£1ĒśĖ ICO ĒöäļĪ£ņĀØĒŖĖņØĖ ļ│┤ņŖżņĮöņØĖ(BOScoin) ĒöäļĪ£ņĀØĒŖĖļŖö ļĖöļĪØņ▓┤ņØĖņØ┤ ņĀ£Ļ│ĄĒĢśļŖö ņŗĀļó░ņÖĆ 1ņØĖ 1Ēæ£ņØś ļ»╝ņŻ╝ņĀü Ļ▒░ļ▓äļäīņŖżļź╝ ĻĖ░ļ░śņ£╝ļĪ£ ŌĆśĻ│ĄĻ│ĄĻĖłņ£ĄŌĆÖ(Public Financing) ņé¼ņŚģņØä ņłśĒ¢ēĒĢ£ļŗż. ņØ┤ ĒöäļĪ£ņĀØĒŖĖļŖö, ņé¼ņŚģņŚÉļŖö ņ£ĀļŖźĒĢśņ¦Ćļ¦ī Ēśäņŗż ĻĖłņ£ĄņŚÉņä£ Ēś£ĒāØņØä ļ░øĻĖ░ ņ¢┤ļĀżņÜ┤ ĻĖ░ņŚģļōżĻ│╝ ņŗĀņøÉĒÖĢņØĖ(KYC)ņØä ĒåĄĻ│╝ĒĢ£ ļ│┤ņŖżņĮöņØĖ ņØśĒÜī ļ®żļ▓äļōżņØ┤ ĒśæļĀźĒĢśņŚ¼ ļ│┤ņŖżņĮöņØĖ ĻĖłņ£ĄņØä ļ░£ņāØņŗ£ĒéżĻ│Ā, ļ│┤ņŖżņĮöņØĖ Ļ▓░ņĀ£ļź╝ ĒåĄĒĢ┤ ĻĖĆļĪ£ļ▓ī Ļ▓ĮņĀ£ ņāØĒā£Ļ│äļź╝ ņØ┤ļŻĖņ£╝ļĪ£ņŹ© ĻĖ░ņŚģĻ│╝ ļ®żļ▓äļōżņØ┤ ņ£ł-ņ£łĒĢśļŖö ĒśæļĀźļ¬©ļŹĖņØ┤ ļÉĀ Ļ▓āņØ┤ļŗż.ßäćßģ│ßå»ßäģßģ®ßå©ßäÄßģ”ßäŗßģĄßå½ßäĆßģ¬ ßäŗßģĪßåĘßäÆßģ®ßäÆßģ¬ßäæßģ© ßäĆßģ│ßäģßģĄßäĆßģ® ßäŗßģĪßå©ßäēßģźßå╝ßäÅßģ®ßäāßģ│
ßäćßģ│ßå»ßäģßģ®ßå©ßäÄßģ”ßäŗßģĄßå½ßäĆßģ¬ ßäŗßģĪßåĘßäÆßģ®ßäÆßģ¬ßäæßģ© ßäĆßģ│ßäģßģĄßäĆßģ® ßäŗßģĪßå©ßäēßģźßå╝ßäÅßģ®ßäāßģ│Jeong-woo Park
╠²
ļČĆņĀ£: ņĢäņ¦üļÅä ļ╣äĒŖĖņĮöņØĖ ļ¦łņĀĆ ņל ļ¬©ļź┤Ļ▓ĀļŖö ļĖöļĪØņ▓┤ņØĖ, ņĢöĒśĖĒÖöĒÅÉ ņ┤łņ┤łļ│┤ IT, ļ│┤ņĢłņØĖņØä ņ£äĒĢ£ ļÅäņøĆ ņ×ÉļŻī
[Partner TechForum] ĻĖłņ£Ą ņä£ļ╣äņŖżļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĄ¼ņČĢņé¼ļĪĆ ņåīĻ░£
[Partner TechForum] ĻĖłņ£Ą ņä£ļ╣äņŖżļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĄ¼ņČĢņé¼ļĪĆ ņåīĻ░£Amazon Web Services Korea
╠²
Ļ░£ņØĖņĀĢļ│┤ ņäĖļ»Ėļéś(190522) - Session 3 Ļ╣ĆļÅÖĒÖś ļ│ĆĒśĖņé¼
Ļ░£ņØĖņĀĢļ│┤ ņäĖļ»Ėļéś(190522) - Session 3 Ļ╣ĆļÅÖĒÖś ļ│ĆĒśĖņé¼ļ▓Ģļ¼┤ļ▓ĢņØĖ ļööļØ╝ņØ┤ĒŖĖ / D'LIGHT Law Group
╠²
Blockchain Basic Concept Theory (Beginner Version) / ņ┤łļ│┤ņ×Éļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņ┤ł Ļ░£ļģÉ ņØ┤ļĪĀ
Blockchain Basic Concept Theory (Beginner Version) / ņ┤łļ│┤ņ×Éļź╝ ņ£äĒĢ£ ļĖöļĪØņ▓┤ņØĖ ĻĖ░ņ┤ł Ļ░£ļģÉ ņØ┤ļĪĀMinwoo Kim
╠²
ßäćßģ│ßå»ßäģßģ®ßå©ßäÄßģ”ßäŗßģĄßå½ßäĆßģ¬ ßäŗßģĪßåĘßäÆßģ®ßäÆßģ¬ßäæßģ© ßäĆßģ│ßäģßģĄßäĆßģ® ßäŗßģĪßå©ßäēßģźßå╝ßäÅßģ®ßäāßģ│
ßäćßģ│ßå»ßäģßģ®ßå©ßäÄßģ”ßäŗßģĄßå½ßäĆßģ¬ ßäŗßģĪßåĘßäÆßģ®ßäÆßģ¬ßäæßģ© ßäĆßģ│ßäģßģĄßäĆßģ® ßäŗßģĪßå©ßäēßģźßå╝ßäÅßģ®ßäāßģ│Jeong-woo Park
╠²
Ad
More from Jongmyoung Kim (20)
REST
RESTJongmyoung Kim
╠²
REST (REpresentational State Transfer) is a web service architecture that uses HTTP requests to GET, POST, PUT, PATCH, and DELETE data in a stateless manner. It focuses on resources instead of remote procedures. REST examples show making GET requests to retrieve XML data from a URI and using RESTful principles like addressability, connectedness, statelessness, and a homogeneous interface with standard HTTP methods.iTunes media server for ubuntu
iTunes media server for ubuntuJongmyoung Kim
╠²
This document discusses media server options for Ubuntu, including iTunes Media Server which uses Digital Audio Access Protocol (DAAP) and the mt-daap and FirePlay clients. It also mentions the Media Player Daemon (MPD) as an alternative media server that includes an MPD server and clients that can control streaming.Open source for upload
Open source for uploadJongmyoung Kim
╠²
This document discusses implementing a file upload feature using open source technologies. It describes using HTML forms to upload files and a PHP script to handle the upload. It then recommends using the open source Plupload library to add multiple file selection, client-side validation, and progress bars. The Plupload library allows uploading files to a PHP script which can then store the files in a database.ßäÄßģ▒ßäŗßģźßåĖßäÅßģóßåĘßäæßģ│ ßäÉßģ│ßå©ßäĆßģĪßå╝ - ßäĆßģĄßäŗßģźßåĖßäŗßģ┤ ßäēßģźßäćßģĄßäēßģ│ ßäĆßģóßäćßģĪßå» ßäæßģ│ßäģßģ®ßäīßģ”ßå©ßäÉßģ│
ßäÄßģ▒ßäŗßģźßåĖßäÅßģóßåĘßäæßģ│ ßäÉßģ│ßå©ßäĆßģĪßå╝ - ßäĆßģĄßäŗßģźßåĖßäŗßģ┤ ßäēßģźßäćßģĄßäēßģ│ ßäĆßģóßäćßģĪßå» ßäæßģ│ßäģßģ®ßäīßģ”ßå©ßäÉßģ│Jongmyoung Kim
╠²
Ļ▓Įļ»╝ļīĆĒĢÖĻĄÉ ņØĖĒä░ļäĘņĀĢļ│┤Ļ│╝ - ņĘ©ņŚģņ║ĀĒöä ĒŖ╣Ļ░ĢTTS SystemņØä ņØ┤ņÜ®ĒĢ£ ĻĄÉņ£ĪņÜ® ņåīĒöäĒŖĖņø©ņ¢┤ Ļ░£ļ░£
TTS SystemņØä ņØ┤ņÜ®ĒĢ£ ĻĄÉņ£ĪņÜ® ņåīĒöäĒŖĖņø©ņ¢┤ Ļ░£ļ░£Jongmyoung Kim
╠²
2001ļģä ņĀ£ņ×æļÉ£ Learn Up ĒöäļĪ£ĻĘĖļשņØś ņĀ£ņ×æ ļ░£Ēæ£ ņ×ÉļŻīņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch19
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch19Jongmyoung Kim
╠²
This document discusses computer security and threats. It covers authentication through passwords, program threats like trojan horses and trap doors, system threats such as worms and viruses. It also discusses threat monitoring through audit logs and scans, and encryption techniques like public-key encryption. The goal is to protect systems from unauthorized access, malicious modification, and accidental inconsistencies.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch21
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch21Jongmyoung Kim
╠²
This document provides an overview of the Linux operating system, including its history, design principles, and key components. It began in 1991 as a small kernel developed by Linus Torvalds and has grown through collaboration over the Internet. The core Linux kernel is original but can run existing UNIX software. Major versions have added support for new hardware, file systems, networking, and multiprocessing. Key components include the Linux kernel, system libraries, and system utilities. The kernel uses loadable modules and supports process management and scheduling.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch18
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch18Jongmyoung Kim
╠²
This document discusses protection in operating systems. It covers the goals of protection, domains of protection, access matrices, implementation of access matrices, revocation of access rights, capability-based systems, and language-based protection. The key aspects are that protection ensures each object is only accessed by allowed processes, domains define access rights to objects, access matrices represent access permissions, and capabilities and access control lists are approaches to implementing and revoking access rights.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch20
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch20Jongmyoung Kim
╠²
The document provides an overview of the Unix operating system, including its history, design principles, interfaces, and key components. It was originally developed in 1969 at Bell Labs and incorporated features from Multics. The C programming language was developed to support Unix. Key aspects include its process management, memory management using paging and swapping, file system storing files in blocks and fragments, and user interface through command line shells.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch17
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch17Jongmyoung Kim
╠²
This document summarizes key aspects of distributed file systems (DFS), including their structure, naming and transparency, remote file access using caching, stateful versus stateless service models, file replication, and examples like the Sun Network File System (NFS). A DFS manages dispersed storage across a network, using caching to improve performance of remote file access and dealing with issues of consistency between cached and server copies. NFS provides a specific implementation of a DFS that integrates remote directories transparently and uses stateless remote procedure calls along with caching for efficiency.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch14
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch14Jongmyoung Kim
╠²
This document discusses network structures and communication. It describes different types of network topologies including fully connected, partially connected, tree-structured, star, ring, and bus networks. It also describes different network types like local area networks (LANs) and wide area networks (WANs). Additionally, it discusses important aspects of network communication like naming and addressing, routing strategies, connection strategies, contention, and design strategies using a layered approach.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch13
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch13Jongmyoung Kim
╠²
This document discusses secondary storage devices used by operating systems, including disk structure, disk scheduling algorithms, disk management, swap space management, and tertiary storage devices. It provides details on disk addressing, mapping, scheduling algorithms like FCFS, SSTF, SCAN and C-SCAN. It also summarizes disk reliability techniques, stable storage implementation, removable media like floppy disks, tapes, optical disks and their applications. Hierarchical storage management and performance factors like speed, reliability and cost of different storage devices are also overviewed.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch16
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch16Jongmyoung Kim
╠²
This document discusses various techniques for distributed coordination including event ordering, mutual exclusion, atomicity, concurrency control, deadlock handling, election algorithms, and reaching agreement. It provides details on implementing happened-before relations for event ordering, centralized and distributed approaches for mutual exclusion, using two-phase commit for atomicity, locking protocols and timestamp ordering for concurrency control, deadlock prevention and detection methods, and election algorithms for determining where to restart a coordinator process.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch12
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch12Jongmyoung Kim
╠²
This document discusses input/output (I/O) systems. It describes I/O hardware, including devices, ports, buses and controllers. It explains how I/O requests are handled using techniques like polling, interrupts and direct memory access. It also discusses the role of the operating system kernel in managing I/O through subsystems that interface with applications, transform requests, handle buffers and errors. The performance of I/O systems is also covered.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch11
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch11Jongmyoung Kim
╠²
This document discusses key aspects of file systems including file concepts, directory structures, access methods, allocation methods, and file system performance and recovery. It covers topics such as file attributes, operations, types, structures, tree-structured and graph-based directories, protection methods, free space management, efficiency techniques, and consistency checking. The goal is to provide an overview of file system interfaces and how different components are organized and managed.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch10
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch10Jongmyoung Kim
╠²
Virtual memory allows a program's logical address space to be larger than physical memory by swapping pages in and out of memory as needed. Demand paging brings pages into memory only when they are referenced. When a page is not in memory and is referenced, a page fault occurs which causes the OS to locate a free frame, swap in the page, and update tables. Page replacement algorithms like FIFO and LRU are used to determine which page to swap out when there is no free frame. Thrashing can occur if working set size is larger than physical memory.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch22
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ Ch22Jongmyoung Kim
╠²
Windows NT is a 32-bit preemptive multitasking operating system that uses a microkernel architecture. It has several key goals including portability, security, POSIX compliance, extensibility, and compatibility with MS-DOS and Windows applications. The document discusses Windows NT's history, design principles, system components including the kernel, executive subsystems, virtual memory manager, process manager, file system, and networking. It provides details on how Windows NT achieves reliability, performance, and international support through its layered architecture and object-oriented design.ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ - Ch09
ņÜ┤ņśüņ▓┤ņĀ£ļĪĀ - Ch09Jongmyoung Kim
╠²
This document discusses various memory management techniques including paging, segmentation, and swapping. Paging divides memory into fixed-size blocks called frames and logical memory into blocks called pages. It uses a page table to map logical to physical addresses. Segmentation divides programs into segments and uses segment tables to map logical segments to physical frames. Swapping temporarily moves processes out of memory to disk to allow other processes to run.Web app service project
Web app service projectJongmyoung Kim
╠²
ĻĖ░ņŚģņŚÉņä£ņØś ņø╣ / ņĢ▒ Ļ░£ļ░£ Ļ│ĄņĀĢņŚÉļīĆĒĢ£ ņäżļ¬ģ ņ×ÉļŻīņ×äßäÄßģ▒ßäŗßģźßåĖßäÅßģóßåĘßäæßģ│ ßäÉßģ│ßå©ßäĆßģĪßå╝ - ßäĆßģĄßäŗßģźßåĖßäŗßģ┤ ßäēßģźßäćßģĄßäēßģ│ ßäĆßģóßäćßģĪßå» ßäæßģ│ßäģßģ®ßäīßģ”ßå©ßäÉßģ│
ßäÄßģ▒ßäŗßģźßåĖßäÅßģóßåĘßäæßģ│ ßäÉßģ│ßå©ßäĆßģĪßå╝ - ßäĆßģĄßäŗßģźßåĖßäŗßģ┤ ßäēßģźßäćßģĄßäēßģ│ ßäĆßģóßäćßģĪßå» ßäæßģ│ßäģßģ®ßäīßģ”ßå©ßäÉßģ│Jongmyoung Kim
╠²
Bitcoin
- 4. What is Bitcoin? Satoshi Nakamoto (2009) Digital Monay No center processor Method of transaction - Distribute Database on Peer to Peer Network Public-Key Cryptosystem anonymity and disclosure
- 5. What is Bitcoin? ņ¦ĆĻ░æņŚÉ Ļ░üĻ░üņØś Ļ│Āņ£Ā ņŻ╝ņåīĻ░Ć ļČĆņŚ¼ ņŻ╝ņåīļź╝ ĻĖ░ļ░śņ£╝ļĪ£ ļ╣äĒŖĖņĮöņØĖ Ļ▒░ļל ļ░£ļŗ© - ļ╣äĒŖĖņĮöņØĖņØĆ 1998ļģä ņø©ņØ┤ļö░ņØ┤Ļ░Ć ņé¼ņØ┤ļ▓äĒÄæĒü¼ ļ®öņØ╝ļ¦ü ļ”¼ņŖżĒŖĖņŚÉ ņś¼ļ”░ ņĢöĒśĖĒåĄĒÖö(cryptocurrency)ļ×Ć ĻĄ¼ņāüņØä ņĄ£ņ┤łļĪ£ ĻĄ¼Ēśä
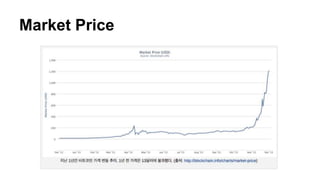
- 7. Market Price
- 8. ļ╣äĒŖĖņĮöņØĖ Ļ░ĆĻ▓®ņØ┤ ĻĖēņāüņŖ╣ĒĢ£ ņØ┤ņ£Ā 1. ļ╣äĒŖĖņĮöņØĖņ£╝ļĪ£ ļ¦łņĢĮ Ļ▒░ļלĒĢśļŖö ņé¼ņØ┤ĒŖĖļź╝ FBIĻ░Ć ĒÅÉņćäĒĢśļ®┤ņä£ Ļ┤Ćņŗ¼ ĻĖēļō▒ 2. ņżæĻĄŁ Ļ▒░ļīĆ ņ×ÉĻĖłņØś ļ¦łļĢģĒĢ£ Ēł¼ņ×Éņ▓śĻ░Ć ņŚåļŗż 3. Ēü░ Ēł¼ņ×Éņ×ÉļōżņØ┤ Ēł¼ņ×Éļź╝ ņŗ£ņ×æĒ¢łļŗż 4. ļ╣äĒŖĖņĮöņØĖ Ļ┤ĆļĀ© ĻĖ░ņŚģņØ┤ ļ▓żņ▓śņ║ÉĒö╝ĒäĖļōżņØś Ēł¼ņ×Éļź╝ ļ░øĻ│Ā ņ׳ļŗż 5. Ļ│Ąņ¦£ļĪ£ ņ║Éņä£ ņō░ļŹś ņé¼ļ×īļōżņØ┤ ĻĄ¼ņ×ģĒĢ┤ņä£ ļ¬©ņ£╝ĻĖ░ ņŗ£ņ×æĒ¢łļŗż 6. ņØ╝ļČĆ ĻĄŁĻ░ĆņŚÉņä£ ļ╣äĒŖĖņĮöņØĖņØä ņØĖņĀĢĒĢśĻĖ░ ņŗ£ņ×æĒ¢łļŗż - ņ║Éļéśļŗż, ļÅģņØ╝, ļäżļŹ£ļ×Ćļō£ ļō▒
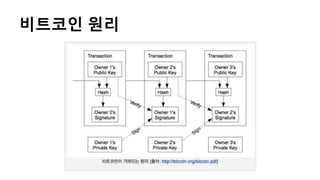
- 9. ļ╣äĒŖĖņĮöņØĖ ļŹö ĒīīĒŚżņ╣śĻĖ░ RSA ņĢöĒśĖĒÖö ĻĖ░ņłĀņØ┤ ņĀüņÜ®ļÉ£ ņłśĒĢÖ ļ╣äĒŖĖņĮöņØĖ ņåīņ£Āņ×Éļ¦ī Private Key ņåīņ£Ā (Ļ│ĄņØĖņØĖņ”Øņä£ņÖĆ ņ£Āņé¼) Ļ▒░ļל ņŗ£ ĒĢ£ ņŻ╝ņåīņŚÉņä£ ļŗżļźĖ ņŻ╝ņåīļĪ£ ņĮöņØĖņØä ļ│┤ļé┤ļ®┤ ļÉ£ ļŗż - ņŻ╝ņåī ņśł ) 1MyhygBUrT6aakgRFDs8ECgoJMqVo9u5n2 ņŻ╝ņåīļŖö ņ×äņØś ņāØņä▒ņØ┤ Ļ░ĆļŖźĒĢśĻ│Ā ņåīņ£Āņ×ÉņŚÉ ļīĆĒĢ£ ņĀĢļ│┤Ļ░Ć ĒżĒĢ©ļÉśņ¦Ć ņĢŖļŖöļŗż -> ņØĄļ¬ģņä▒ ļ│┤ņןņ£╝ļĪ£ ļ▓öņŻäņŚÉ ņĢģņÜ®ļÉĀ ņåīņ¦ĆĻ░Ć ļåÆļŗż ņżæņĢÖņØĆĒ¢ēņØ┤ ņŚåļŗż ļ╣äĒŖĖņĮöņØĖ Ļ▒░ļל ļ░£ņāØ ņŗ£ ĻĘĖ ļé┤ņŚŁņØ┤ ņĀä ņäĖĻ│äļĪ£ ņĀäĒīīļÉśļ®░ ļŗżļźĖ ņé¼ļ×īļōżņØ┤ ņ£ĀĒÜ©ĒĢ£ Ļ▒░ ļלļØ╝ļŖö Ļ▓āņØä ņ”Øļ¬ģĒĢ┤ņżĆļŗż. -> Ļ░£ņØĖņŗĀņÜ®ĒÅēĻ░Ćņé¼ņÖĆ ņØ╝ļČĆ ņ£Āņé¼
- 10. ļ╣äĒŖĖņĮöņØĖ ļŹö ĒīīĒŚżņ╣śĻĖ░ 2 Ļ▒░ļל ļé┤ņŚŁņØĆ ŌĆ£Block ChainŌĆØņØ┤ļØ╝ļŖö Ļ││ņŚÉ ļ│┤Ļ┤ĆļÉ£ļŗż ņØ┤Ļ││ņŚÉņä£ ņØ┤ņżæ Ļ▓░ņĀ£(ņĢģņØśņĀüņ£╝ļĪ£ ņŚ¼ļ¤¼Ļ││ņŚÉ ņĀäņåĪ)ļź╝ ņ▓┤Ēü¼ĒĢĀ ņłś ņ׳ļŗż
- 13. ļ╣äĒŖĖņĮöņØĖ ļŹö ĒīīĒŚżņ╣śĻĖ░ 3 ļĖöļĪØņ▓┤ņØĖņØä ĒÖĢņØĖĒĢśļŖöļŹ░ ņłśĒĢÖņĀü Ļ│äņé░Ļ│╝ Ļ│Āņä▒ļŖź ĒĢśļō£ņø©ņ¢┤Ļ░Ć ĒĢäņÜöĒĢśļŗż ņØ┤ļź╝ ĒÖĢņØĖĒĢ┤ņżĆ ļ│┤ņāüņ£╝ļĪ£ ļ╣äĒŖĖņĮöņØĖņØä ņŻ╝ļÅäļĪØ ņĢīĻ│Āļ”¼ņ”śļÉśņ¢┤ ņ׳ļŗż ņØ┤ļĀćĻ▓ī ļ╣äĒŖĖņĮöņØĖņØä ņ¢╗ļŖö Ļ▓āņØä ŌĆ£bitcoin miningŌĆØļØ╝ ĒĢ£ļŗż
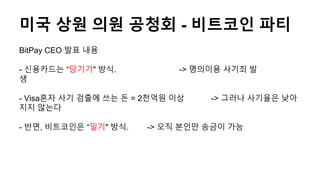
- 16. ļ»ĖĻĄŁ ņāüņøÉ ņØśņøÉ Ļ│Ąņ▓ŁĒÜī - ļ╣äĒŖĖņĮöņØĖ ĒīīĒŗ░ BitPay CEO ļ░£Ēæ£ ļé┤ņÜ® - ņŗĀņÜ®ņ╣┤ļō£ļŖö ŌĆ£ļŗ╣ĻĖ░ĻĖ░" ļ░®ņŗØ. -> ļ¬ģņØśņØ┤ņÜ® ņé¼ĻĖ░ņŻä ļ░£ ņāØ - VisaĒś╝ņ×É ņé¼ĻĖ░ Ļ▓ĆņČ£ņŚÉ ņō░ļŖö ļÅł = 2ņ▓£ņ¢ĄņøÉ ņØ┤ņāü -> ĻĘĖļ¤¼ļéś ņé¼ĻĖ░ņ£©ņØĆ ļé«ņĢä ņ¦Ćņ¦Ć ņĢŖļŖöļŗż - ļ░śļ®┤, ļ╣äĒŖĖņĮöņØĖņØĆ ŌĆ£ļ░ĆĻĖ░" ļ░®ņŗØ. -> ņśżņ¦ü ļ│ĖņØĖļ¦ī ņåĪĻĖłņØ┤ Ļ░ĆļŖź
- 17. ļ╣äĒŖĖņĮöņØĖņØś ĒĢ£Ļ│ä ĒåĄņĀ£ ļ░øņ¦Ć ņĢŖņØīņØ┤ ĒĢ£Ļ│äĻ░Ć ļÉĀ ņłś ņ׳ļŗż -> ļ»╝Ļ░ÉĒĢ£ Ļ░Ćņ╣ś ļ│ĆļÅÖņ£╝ļĪ£ ņØĖĒĢ£ Ļ│ĄĒÖ® Ļ░ĆļŖźņä▒ ĒŖĖļלņףņģś ņåīņÜö ņŗ£Ļ░äņØ┤ ļäłļ¼┤ ĻĖĖļŗż (Ļ▒░ļלļŗ╣ 10~20ļČä) - ĻĄŁĻ░ĆĻ░ä Ļ▒░ļלļĪ£ļŖö ņ¦¦ņØĆ ņŗ£Ļ░äņØ┤ļéś, ņŖżĒāĆļ▓ģņŖż ņ╗żĒö╝ĒĢ£ņ×ö ņé¼ļŖöļŹ░ļŖö ĻĖ┤ ņŗ£Ļ░äņ×ä ļ╣äĒŖĖņĮöņØĖņØĆ ņ×āņ¢┤ļ▓äļ”¼Ļ▒░ļéś ļÅäļææļ¦×ņ£╝ļ®┤ ļüØ (ņØĄļ¬ģņä▒ņØś ļ░śĻ▓®) Ļ░£ņØĖĻ░ä ļ¼╝ĒÆł ĻĄ¼ļ¦ż ņŗ£ ņĢłņĀäĻ▒░ļל ļČłĻ░Ć ņżæĻĄŁņØś ļ╣äĒŖĖņĮöņØĖ ņĀĢņ▒ģ ļ│ĆĒÖöļĪ£ ļööĒöīļĀłņØ┤ņģś ņ£äĒŚś
- 18. ņĀĢļ”¼ ņĀäņ▓┤ ņ¢æņØ┤ ņ£ĀĒĢ£ĒĢśņŚ¼ ĻĖł,ņØĆĻ│╝ Ļ░ÖņØĆ Ļ░ĆĻ▓® ļ│ĆļÅÖ ņä▒ Ē¢ź ņŗżņ▓┤Ļ░Ć Ļ░ĆņāüņØ┤ļ»ĆļĪ£ ņØ╝ņóģņØś ĒīīņāØņāüĒÆł ņĢäņ¦ü Ļ│ĄņŗĀļĀźņØ┤ ņŚåņ¢┤ Ēł¼ņ×ÉļīĆņāüņ£╝ļĪ£ļ¦ī ņĘ©ĻĖē ĒĢäņÜö
- 19. NEXT SECTION Bitcoin Mining Machanism - SHA-256 (SHA2) - Try Hashcrach " ņŚ¼ļ│┤ņäĖņÜö , ņäĖĻ│ä ! 0 "= > 1312af178c253f84028d480a6adc1e25e81caa44c749ec81976192e2ec934c64 " ņĢłļģĢĒĢśņäĖņÜö, ņäĖĻ│ä ! 1 "= > e9afc424b79e4f6ab42d99c81156d3a17228d6e1eef4139be78e948a9332a7d8 " ņŚ¼ļ│┤ņäĖņÜö , ņäĖĻ│ä ! 2 "= > ae37343a357a8297591625e7134cbea22f5928be8ca2a32aa475cf05fd4266b7 ...
- 20. Calculations
- 21. Code
