C chap1
- 1. บทที่ 1 ภาษาซีเบื้อง ต้นC Programming C-Programming โดยนางสาวสุชาดา จงจงประเสริฐ รายวิชาการใช้โปรแกรมภาษาซี (3204-2008) วิทยาลัยเทคนิคสิงห์บุรี แห่งที่ 2
- 2. 2 มีอะไรบ้างในบทนี้ 1.1 ความนำาการเขียนโปรแกรม 1.2 ซอฟต์แวร์คืออะไร? 1.3 ภาษาคอมพิวเตอร์ 1.4 โปรแกรมที่เขียนจะทำางาน อย่างไร? 1.5 ไฟล์โปรแกรมที่ได้จากการแปล ภาษา 1.7 ประวัติของภาษาซี 1.8 พัฒนาการของคอมไพเลอร์ภาษา ซี 1.9 ระบบช่วยเหลือของคอมไพเลอร์ C Programming C-Programming
- 3. 3 1.1 ความนำาการเขียน โปรแกรม เราเขียนโปรแกรมไปเพื่ออะไร เพราะว่าในหลักสูตรที่เรียนอยู่บังคับ วิชานี้ เพราะอาจารย์ให้เขียนโปรแกรมส่ง อาทิตย์หน้า เพราะอยากเพิ่มพูนความรู้ด้าน คอมพิวเตอร์ เพราะต้องการเขียนโปรแกรมไว้ใช้ เอง ฯลฯ การเขียนโปรแกรมก็เหมือนการแก้ โจทย์ปัญหา เราจะต้องทราบว่าเรา C Programming C-Programming
- 4. 4 ภาษาคอมพิวเตอร์ โปรแกรมที่รันบนวินโดว์ C/C++, Visual Basic, Delphi โปรแกรมที่ทำางานบนเว็บ PHP, ASP, JAVA, Perl, Tcl, C# โปรแกรมฐานข้อมูล Visual Basic โปรแกรมกราฟิก โปรแกรมเกม โปรแกรมคำานวณ C Programming C-Programming
- 5. 5 1.2 ซอฟต์แวร์คืออะไร ? ซอฟต์แวร์(Software) หรือโปรแกรม คอมพิวเตอร์(Computer Program) คือ โปรแกรมที่ถูกเขียนขึ้นมาจากภาษา คอมพิวเตอร์และถูกแปลงให้เป็น ภาษาเครื่องเพื่อให้คอมพิวเตอร์ ทำางานอย่างใดอย่างหนึ่งตามที่เรา ต้องการ แบ่งออกเป็น 2 ประเภทใหญ่ๆ คือ System software Application software C Programming C-Programming
- 6. 6 System Software เป็นโปรแกรมที่ทำำงำนเกี่ยวกับระบบ คอมพิวเตอร์ มีหน้ำที่ในกำรควบคุม อุปกรณ์ฮำร์ดแวร์ทุกชนิด และจัด ตำรำงกำรทำำงำนทั้งฮำร์ดแวร์และ ซอฟต์แวร์ที่ทำำงำนกับฮำร์ดแวร์ทุก ตัวซึ่งก็คือระบบปฏิบัติกำร(Operating System:OS) นั่นเอง ได้แก่ DOS, Windows, Linux, Mac OS, OS/2 C Programming C-Programming
- 7. 7 Application Software เป็นโปรแกรมที่ถูกสร้ำงขึ้นเพื่อทำำงำน ด้ำนต่ำงๆ ซึ่งก็ถูกเขียนขึ้นจำก โปรแกรมภำษำต่ำงๆ เช่น PowerDVD, Windows Media Player, Winamp, Word, Calculator, SPSS สำมำรถแบ่งออกได้หลำยประเภทดังนี้ โปรแกรมพิมพ์งำน โปรแกรมเกม โปรแกรมยูทิลิตี้ โปรแกรมมัลติมีเดีย โปรแกรมสำำหรับระบบ โปรแกรมภำษำสำำหรับพัฒนำซอฟต์แวร์ C Programming C-Programming
- 8. 8 1.3 ภำษำคอมพิวเตอร์ แบ่งออกเป็น 2 ประเภทใหญ่ๆ คือ ภำษำระดับตำ่ำ ได้แก่ ภำษำเครื่อง และ ภำษำ Assembly ภำษำระดับสูง ได้แก่ Basic, Pascal, Ada, C, Cobol, Fortran และอื่นๆ ควำมแตกต่ำงระหว่ำงภำษำระดับสูงและ ระดับตำ่ำคือ ภำษำระดับตำ่ำ ควบคุม อุปกรณ์ฮำร์ดแวร์คอมพิวเตอร์ได้ดีกว่ำ แต่เขียนยำก และยำวมำก ส่วนภำษำ ระดับสูงเขียนง่ำยเข้ำใจง่ำยกว่ำเพรำะ ใกล้เคียงภำษำมนุษย์ แต่มีข้อจำำกัดใน กำรควบคุมฮำร์ดแวร์ C Programming C-Programming
- 9. 9 1.4 โปรแกรมที่เขียนขึ้นจะ ทำำงำนได้อย่ำงไร ? โปรแกรมที่เขียนขึ้นมำ ไม่ว่ำจะเขียน โดยใช้อิดิเตอร์(editor) อะไรก็ตำม จะได้ ซอร์สโค้ด(source code) ซึ่งจะเก็บในรูป แฟ้มข้อมูล ซึ่งจะมีนำมสกุลแตกต่ำงกัน ไปดังนี้ C Programming ภำษำ นำมสกุล ตัวอย่ำง C++ C Pascal Perl PHP Java .c .cpp .pas .pl .php .java hello.c hello.cpp hello.pas hello.pl hello.php hello.java C-Programming
- 10. 10 กระบวนกำรแปลโปรแกรมC Programming ---- ---- ---- ---- ---- ---- ซอร์สโค้ด กระบวนกำรแปลโปรแกรมโปรแกรมที่สำมำรพทำำงำนได โดยไม่ต้องมี source code C-Programming
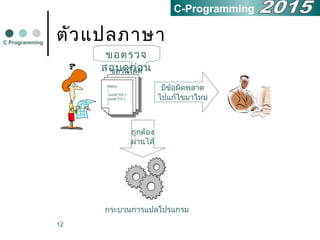
- 11. 11 ตัวแปลภาษา คอมไพเลอร์(compiler) คอมไพเลอร์จะอ่านโปรแกรม ทั้งหมดก่อน เมื่อเจอข้อผิดพลาดก็ จะแจ้งให้แก้ไข แต่ถ้าไม่พบข้อผิด พลาดใดๆ ในโปรแกรม ก็จะแปลให้ เป็นโปรแกรมที่พร้อมจะทำางานดังรูป C Programming C-Programming
- 14. 14 1.5 ไฟล์โปรแกรมที่ได้จาก การแปลภาษา เมื่อเขียนโปรแกรมเสร็จ ผ่าน การแปลภาษาแล้วผลที่ได้ก็จะ เป็นไฟล์โปรแกรมที่สามารถนำา ไปใช้ได้เลย โดยอาจก๊อปปี้ลง ดิสก์ไปเปิดที่เครื่องอื่นๆ ได้ ซึ่ง จะเป็นไฟล์โปรแกรมแยกจากตัว ซอร์สโค้ดที่เราเขียน ไฟล์โปรแกรมที่ได้นั้นเป็นไฟล์ แบบเลขฐานสอง หรือ C Programming C-Programming
- 15. 15 1.6 ประวัติของภาษาซี C มีต้นกำาเนิดมาจากภาษาคอมพิวเตอร์ ยูนิกซ์(UNIX) นำาเอาภาษาเครื่องมาใช้ในการพัฒนา โปรแกรมอื่นๆ และพัฒนาเป็นระบบ ปฏิบัติการ(OS) และได้สร้างภาษาบี(B) ขึ้นมา เพื่อช่วยให้การเขียนโปรแกรม ทำาได้ง่ายขึ้น ต่อมา Dennis Ritchie จาก Bell Lab ได้นำาภาษานี้มาพัฒนา ต่อและใช้ชื่อว่า C เพราะเป็นภาษาต่อ จาก B ในยุคนั้นจะทำางานบนยูนิกซ์ เป็นส่วนมาก C Programming C-Programming
- 16. 16 จากภาษา C สู่ C++ ภาษา C ได้มีการพัฒนาต่อโดยใช้ แนวคิดโปรแกรมเชิงวัตถุ หรือ OOP(Object Oriented Programming) “ ”เกิดภาษาใหม่เรียกว่า ซี พลัส พลัส (C++) ภาษาซียังเป็นต้นฉบับให้กับอีกหลายๆ ภาษาในปัจจุบันเช่น Java, C# (อ่านว่า ซีชาร์ป) C# คือภาษาที่ออกแบบมาเพื่อทำางาน บนแพลตฟอร์ม .NET C Programming C-Programming
- 17. 17 1.7 พัฒนาการของคอมไพ เลอร์ภาษา C DOS >> Turbo C Windows >> Microsoft Visual C++ Borland C++ Borland C++ Builder Symantec C/C++ C Programming C-Programming
- 18. 18 1.8 ระบบช่วยเหลือของคอม ไพเลอร์ภาษา C เมื่อติดตั้งคอมไพเลอร์ภาษา C แล้วจะ มีระบบช่วยเหลือมาให้ด้วย Visual C++ จะมีระบบช่วยเหลือที่ชื่อ MSDN(Microsoft Developer Network) C Programming C-Programming
- 19. 19 1.9 สรุป คอมไพเลอร์ภาษา C ที่ในปัจจุบันมี หลายตัว แต่มีพื้นฐานมาจากมาตรฐาน เดียวกันคือ ANSI C ซึ่งจะเป็น มาตรฐานของการเขียนโปรแกรม ภาษา C บนยูนิกซ์ Linux หรือ Windows โดยใช้คอมไพเลอร์ Visual C++, Borland C++, GNU C/C++ ภาษาซีเป็นพื้นฐานของภาษา C++, Java, C# C Programming C-Programming