Component of system unit.ppt
- 1. Components of System Unit Course Instructor: Fariha Sabahat 1
- 2. The System Unit ŌĆó What is the system unit? ’āś Case that contains electronic components of the computer used to process data ’é¦ Sometimes called the chassis 2
- 3. The System Unit ŌĆó What are common components inside the system unit? ’āś Memory ’āś Adapter cards ’é¦ Sound card ’é¦ Modem card ’é¦ Video card ’é¦ Network card ’āś Ports ’āś Drive bays ’āś Power supply power supply ports drive bays processor memory sound card video card modem card network card ’āś Processor 3
- 4. 4
- 5. The System Unit ŌĆó What is the motherboard? ’āś Main circuit board in system unit ’āś Contains adapter cards, processor chips, and memory chips ’āś Also called system board processor chip adapter cards memory chips memory slots motherboard Expansion slots for adapter cards 5
- 6. The Motherboard and CPU ŌĆó The motherboard is the main circuit board of a microcomputer. It contains the central processing unit (CPU), the Basic Input/Output System (BIOS), memory, mass storage interfaces, serial and parallel ports, expansion slots, and all the controllers for standard peripheral devices like the keyboard, disk drive and display screen. 6
- 7. The System Unit ŌĆó What is a chip? dual inline packages (DIP) holds memory chips pin grid array (PGA) package holds processor chips ’āś Small piece of semi-conducting material on which integrated circuits are etched ’é¦ Integrated circuits contain many microscopic pathways capable of carrying electrical current ’āś Chips are packaged so they can be attached to a circuit board 7
- 8. Processor Control Unit Arithmetic Logic Unit (ALU) Arithmetic Logic Unit (ALU) Processor What is the central processing unit (CPU)? Input Devices Storage Devices Output Devices ’āś Interprets and carries out basic instructions that operate a computer Memory Data Information Instructions Data Information Instructions Data Information Control Unit ’é¦ Control unit directs and coordinates operations in computer ’é¦ Arithmetic logic unit (ALU) performs arithmetic, comparison, and logical operations ’āś Also called the processor 8
- 9. Processing Sequence Two crucial aspects are related with Processors & Processing 1. Machine Cycles ŌĆó Control unit and memory working together to perform all instructions on computer ŌĆó Two cycles ŌĆō Instruction Cycle (Fetch instruction and translate them) ŌĆō Fetch ŌĆō Decode ŌĆō Execution Cycle (Process and Produce(store) results) ŌĆō Execute ŌĆō Store 9
- 10. Processing Sequence 2. Registers ŌĆó To execute machine cycles, the control unit needs temporary storage spaces called ŌĆ£RegistersŌĆØ ŌĆó Part of Processor not Storage or Memory devices ŌĆó These are faster than the main memory ŌĆó Their purpose is to hold most frequent instructions carried out by processors and therefore they eventually speeds us the execution process 10
- 11. Stores location from where instruction was fetched Processor Stores instruction while it is being decoded ŌĆó What is a register? Stores data while ALU computes it Stores results of calculation ’āś Temporary high-speed storage area that holds data and instructions 11
- 12. 12
- 13. Processor Control Unit Memory ALU Processor What is a machine cycle? Step 1. Fetch Obtain program instruction or data item from memory Step 2. Decode Translate instruction into commands Step 4. Store Write result to memory Step 3. Execute Carry out command ’āś Four operations of the CPU comprise a machine cycle 13
- 14. 14
- 15. Processor ŌĆó What is pipelining? ’āś CPU begins fetching second instruction before completing machine cycle for first instruction ’āś Results in faster processing 15
- 16. Processor What is the system clock? FLOPS Floating Point Operations per second Pace of system clock is clock speed Most clock speeds are in the gigahertz (GHz) range (1 GHz = one billion ticks of system clock per second) Processor speed can also be measured in millions of instructions per second (MIPS) ’āś Controls timing of all computer operations ’āś Generates regular electronic pulses, or ticks, that set operating pace of components of system unit ’āś Each tick is a clock cycle (million to billion times in 1 sec) 16
- 17. Chip-for chip upgrade replace the chip Processor ŌĆó What are the types of processor upgrades? Piggyback upgrade stack new chip on top of old one Daughterboard upgrade chip is on adapter card that plugs into motherboard 17
- 18. Processor What is a zero-insertion force (ZIF) socket? Step 2. Insert the chip. Step 1. Lift the lever on the socket. lever Step 3. Push the lever down. lever ’āś Allows you to install and remove chips with no force 18
- 19. Processor What is parallel processing? Control Processor Processor 1 Memory Processor 2 Memory Processor 3 Memory Processor 4 Memory Results combined ’āś Using multiple processors simultaneously to execute a program faster ’āś Requires special software to divide problem and bring results together ’āś SIMD v/s MIMD 19
- 20. Data Representation How do computers represent data? ’é¦ Recognize only two discrete states: on or off ’é¦ Use a binary system to recognize two states ’é¦ Use Number system with two unique digits: 0 and 1, called bits (short for binary digits) ’āś Most computers are digital 20
- 21. Data Representation What is a byte? ’āś Eight bits grouped together as a unit ’āś Provides enough different combinations of 0s and 1s to represent 256 individual characters ’é¦ Numbers ’é¦ Uppercase and lowercase letters ’é¦ Punctuation marks ’āś Encoding 21
- 22. Data Representation What are three popular coding systems to represent data? ’āś ASCIIŌĆöAmerican Standard Code for Information Interchange ’āś EBCDICŌĆöExtended Binary Coded Decimal Interchange Code ’āś UnicodeŌĆöcoding scheme capable of representing all worldŌĆÖs languages ASCII Symbol EBCDIC 00110000 0 11110000 00110001 1 11110001 00110010 2 11110010 00110011 3 11110011 22
- 23. Data Representation How is a letter converted to binary form and back? Step 1. The user presses the capital letter D (shift+D key) on the keyboard. Step 2. An electronic signal for the capital letter D is sent to the system unit. Step 3. The signal for the capital letter D is converted to its ASCII binary code (01000100) and is stored in memory for processing. Step 4. After processing, the binary code for the capital letter D is converted to an image, and displayed on the output device. 23
- 24. Memory What is memory? ’āś Electronic components that store instructions, data, and results ’āś Consists of one or more chips on motherboard or other circuit board ’āś Each byte stored in unique location called an address, similar to seats on a passenger train Seat #2B4 Seat #2B3 24
- 25. Memory How is memory measured? Term Abbreviation Approximate Size Kilobyte KB or K 1 thousand bytes Megabyte MB 1 million bytes Gigabyte GB 1 billion bytes Terabyte TB 1 trillion bytes ’āś By number of bytes available for storage 25
- 26. Memory What is random access memory (RAM)? The more RAM a computer has, the faster it responds Also called main memory or primary storage Most RAM is volatile, it is lost when computerŌĆÖs power is turned off Memory chips that can be read from and written to by processor 26
- 27. Memory How do program instructions transfer in and out of RAM? Step 1. When you start the computer, certain operating system files are loaded into RAM from the hard disk. The operating system displays the user interface on the screen. Operating system instructions Web browser instructions Word processing program instructions Operating system interface Web browser window Word processing program window RAM RAM Web browser program instructions are removed from RAM Web browser window no longer is displayed on desktop Step 2. When you start a Web browser, the programŌĆÖs instructions are loaded into RAM from the hard disk. The Web browser window is displayed on the screen. Step 3. When you start a word processing program, the programŌĆÖs instructions are loaded into RAM from the hard disk. The word processing program, along with the Web Browser and certain operating system instructions are in RAM. The word processing program window is displayed on the screen. Step 4. When you quit a program, such as the Web browser, its program instructions are removed from RAM. The Web browser no longer is displayed on the screen. 27
- 28. Faster variations of DRAM are SDRAM and RDRAM Used for special applications such as cache Most common type Faster and more reliable than DRAM chips Memory What are two basic types of RAM chips? Dynamic RAM (DRAM) ŌĆó Future: Magnetoresistive RAM (MRAM) Static RAM (SRAM) 28
- 29. Memory ŌĆó Where does memory reside? ’āś Resides on small circuit board called memory module ’āś Memory slots on motherboard hold memory modules memory chip memory slot dual inline memory module 29
- 30. Memory How much RAM does an application require? ’āś Software package typically indicates RAM requirements ’āś For optimal performance, you need more than minimum specifications System Requirements Windows┬« XP Home Edition/Professional ŌĆó Intel Pentium processor at 233MHZ or higher ŌĆó AMD K6 (Athlon Duron Family processor at 233MHZ or higher ŌĆó 64 MB of RAM 30
- 31. Memory How much RAM do you need? ’āś Depends on type of applications you intend to run on your computer RAM Use 128 to 256 MB 256 to 1 GB 1 GB and up ŌĆó Home and business users managing personal finance ŌĆó Using standard application software such as word processing ŌĆó Using educational or entertainment CD-ROMs ŌĆó Communicating with others on the Web ŌĆó Users requiring more advanced multimedia capabilities ŌĆó Running number-intensive accounting, financial, or spreadsheet programs ŌĆó Using voice recognition ŌĆó Working with videos, music, and digital imaging ŌĆó Creating Web sites ŌĆó Participating in video conferences ŌĆó Playing Internet games ŌĆó Power users creating professional Web sites ŌĆó Running sophisticated CAD, 3D design, or other graphics-intensive software 31
- 32. Memory What is cache? ’é¦ L1 cache built into processor ’é¦ L2 cache slower but has larger capacity ’é¦ L2 advanced transfer cache is faster, built directly on processor chip ’é¦ L3 cache is separate from processor chip on motherboard (L3 is only on computers that use L2 advanced transfer cache) ’é¦ 256 KB of L2 for Personal computers ’é¦ 2 MB of L2 for Servers ’āś Helps speed computer processes by storing frequently used instructions and data ’āś Also called memory cache 32
- 33. Memory What is read-only memory (ROM)? Memory chips that store permanent data and instructions Nonvolatile memory, it is not lost when computerŌĆÖs power is turned off Three types: Firmware Manufactured with permanently written data, instructions, or information EEPROM (electrically erasable programmable read-only memory)ŌĆö Type of PROM containing microcode programmer can erase PROM (programmable read-only memory)ŌĆö Blank ROM chip onto which a programmer can write permanently 33
- 34. Memory What is flash memory? Step 1. Purchase and download MP3 music tracks from a Web site. With one end of a special cable connected to the system unit, connect the other end into the MP3 player. Step 2. Instruct the computer to copy the MP3 music track to the flash memory chip in the MP3 player. Step 3. Plug the headphones into the MP3 player, push a button on the MP3 player, and listen to the music through the headphones. MP3 Player Flash memory chip Flash memory card From computer To headphones ’āś Nonvolatile memory that can be erased electronically and reprogrammed ’āś Used with PDAs, digital cameras, digital cellular phones, music players, digital voice recorders, printers, Internet receivers, and pagers 34
- 35. Memory What is CMOS? Uses battery power to retain information when other power is turned off Stores date, time, and computerŌĆÖs startup information Complementary metal-oxide semiconductor memory Used in some RAM chips, flash memory chips, and other types of memory chips 35
- 36. Memory What is access time? ’āś Amount of time it takes processor to read data from memory ’āś Measured in nanoseconds (ns), one billionth of a second ’āś It takes 1/10 of a second to blink your eye; a computer can perform up to 10 million operations in same amount of time Term Speed Millisecond One-thousandth of a second Microsecond One-millionth of a second Nanosecond One-billionth of a second Picosecond One-trillionth of a second 36
- 37. Expansion Slots and Adapter Cards What is an adapter card? Types of Adapter Cards ’āś Enhances system unit or provides connections to external devices called peripherals ’āś Also called an expansion card 37
- 38. VGASound Card 38
- 39. Expansion Slots and Adapter Cards What is an expansion slot? ’āś An opening, or socket, on the motherboard that can hold an adapter card ’āś With Plug and Play, the computer automatically configures cards and other devices as you install them 39
- 40. PCMCIA (PC Card) ŌĆó Personal Computer Memory Card International Association ŌĆó Found on notebook computers 40
- 41. Expansion Slots and Adapter Cards What are PC cards and flash memory cards? ’āś A PC card adds memory, storage, sound, fax/modem, communications, and other capabilities to notebook computers ’āś A flash memory card allows users to transfer data from mobile devices to desktop computers ’é¦ Hot plugging allows you to insert and remove cards while computer is running 41
- 42. Ports and Connectors What are ports and connectors? ’āś Port connects external devices to system unit ’āś Connector joins cable to peripheral ’é¦ Available in one of two genders: male and female 42
- 43. Ports and Connectors What are different types of connectors? 43
- 44. Ports and Connectors What is a serial port? ’āś Transmits one bit of data at a time ’āś Connects slow-speed devices, such as mouse, keyboard, modem 44
- 45. 45
- 46. Ports and Connectors What is a parallel port? ’āś Connects devices that can transfer more than one bit at a time, such as a printer 46
- 47. Third USB device connects to second USB device, and so on Second USB device connects to first USB device First USB device connects to USB port on computer Single USB port can be used to attach multiple peripherals in a daisy chain PCs typically have four to eight USB ports on front or back of the system unit Ports and Connectors What are USB ports? USB (universal serial bus) port can connect up to 127 different peripherals together with a single connector type 47
- 48. Ports and Connectors What are special-purpose ports? ’é¦ FireWire port ’é¦ MIDI (Musical Instrument Digital Interface) port ’é¦ SCSI (small computer system interface) port ’é¦ IrDA (Infrared Data Association) port ’é¦ Bluetooth port ’āś Allow users to attach specialized peripherals (digital video cameras, color printers, scanners, and disk drives) or transmit data to wireless devices 48
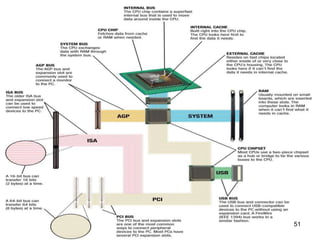
- 49. Buses What is a bus? ’āś Channel that allows devices inside computer to communicate with each other ’é¦ System bus connects processor and RAM ’é¦ Bus width determines number of bits transmitted at one time ’é¦ Word size is the number of bits processor can interpret and execute at a given time 49
- 50. Buses What is an expansion bus? ’āś Allows processor to communicate with peripherals 50
- 51. 51