Cutting accounts down to scythe
0 likes9,810 views
The document outlines a Python-based framework for user enumeration called 'scythe,' designed for penetration testers to streamline account enumeration tasks. It details features such as modularity, threading, and the ability to handle cookies and CSRF tokens while providing examples of implementation for various sites, particularly WordPress. The framework aims to offer advanced functionality for flexible testing and error handling while generating detailed output and summaries.
1 of 38













![Basic module
<module>
<site>
<name>basic module</name>
<url>
<![CDATA[https://example.com/signup_check/
username=<ACCOUNT>]]>
</url>
<method>GET</method>
<successmatch>taken</successmatch>
</site>
</module>](https://image.slidesharecdn.com/cuttingaccountsdowntoscythe-120928080226-phpapp01/85/Cutting-accounts-down-to-scythe-17-320.jpg)

![<!-- Wordpress.com - Logon user enumeration issue -->
<module>
<site>
<name>Wordpress.com</name>
<url><![CDATA[https://wordpress.com/wp-login.php]]></url>
<method>POST</method>
<postParameters>
<![CDATA [log=<ACCOUNT>&pwd=<RANDOM>redirect_to=http://wordpress.com]]>
</postParameters>
<headers></headers>
<requestCookie>False</requestCookie>
<requestCSRF>False</requestCSRF>
<successmatch>The password you entered for the email or user</successmatch>
<negativematch>Invalid email or username</negativematch>
<errormatch>You have exceeded the login limit</errormatch>
<date>13/09/2012</date>
<version>2</version>
<author>CJR</author>
<category>blogs</category>
</site>
</module>](https://image.slidesharecdn.com/cuttingaccountsdowntoscythe-120928080226-phpapp01/85/Cutting-accounts-down-to-scythe-19-320.jpg)
![<!-- Wordpress.com - Logon user enumeration issue -->
<module>
<site>
<name>Wordpress.com</name>
<url><![CDATA[https://wordpress.com/wp-login.php]]></url>
<method>POST</method>
<postParameters>
<![CDATA [log=<ACCOUNT>&pwd=<RANDOM>redirect_to=http://wordpress.com]]>
</postParameters>
<headers></headers>
<requestCookie>False</requestCookie>
<requestCSRF>False</requestCSRF>
<successmatch>The password you entered for the email or user</successmatch>
<negativematch>Invalid email or username</negativematch>
<errormatch>You have exceeded the login limit</errormatch>
<date>13/09/2012</date>
<version>2</version>
<author>CJR</author>
<category>blogs</category>
</site>
</module>](https://image.slidesharecdn.com/cuttingaccountsdowntoscythe-120928080226-phpapp01/85/Cutting-accounts-down-to-scythe-20-320.jpg)
![<!-- Wordpress.com - Logon user enumeration issue -->
<module>
<site>
<name>Wordpress.com</name>
<url><![CDATA[https://wordpress.com/wp-
login.php]]></url>
<method>POST</method>
<postParameters>
<![CDATA
[log=<ACCOUNT>&pwd=<RANDOM>redirect_to=
http://wordpress.com]]>
</postParameters>](https://image.slidesharecdn.com/cuttingaccountsdowntoscythe-120928080226-phpapp01/85/Cutting-accounts-down-to-scythe-21-320.jpg)










Ad
Recommended
Dev traning 2016 intro to the web
Dev traning 2016 intro to the webSacheen Dhanjie
╠²
This document provides an introduction to the basics of how the World Wide Web works using HTTP requests and responses. It explains the HTTP request-response process, including the different HTTP methods like GET, POST, PUT, and DELETE. It provides examples of requests and responses for each method. It also discusses how to access HTTP data in PHP and provides examples of using requests and responses with Afrihost.WordPress SugarCRM Customer Portal Pro Plugin
WordPress SugarCRM Customer Portal Pro PluginBiztech Store
╠²
The document is a user guide for installing and configuring the Customer Portal Pro plugin compatible with SugarCRM and WordPress. It outlines detailed installation steps for both SugarCRM and WordPress, as well as instructions for plugin activation and configuration settings. Additionally, it provides information on managing user accounts, troubleshooting, and accessing technical support.Cookies
CookiesRamraj Choudhary
╠²
The document describes a project structure for handling cookies in a Java web application. The structure includes an index.html page that collects user input in a form, which is submitted to the CookieExample servlet. This servlet sets two cookies containing the user's first and last name. Control is then redirected to the GetCookie servlet, which retrieves the cookies and displays their values. The project folders, files, and code segments to implement this cookie handling functionality are outlined.Latest Java Setting for MCA Portal(MANUAL)
Latest Java Setting for MCA Portal(MANUAL)GAURAV KR SHARMA
╠²
The document provides instructions for configuring Java settings on a computer to allow for smooth login, form uploads, digital signature usage, and other functions on the MCA21 portal. It outlines setting Java in the Control Panel, Internet Explorer, and system properties, and provides troubleshooting tips for any Java block alerts that may occur.Tools for Open Source Intelligence (OSINT)
Tools for Open Source Intelligence (OSINT)Sudhanshu Chauhan
╠²
This document introduces tools for open source intelligence (OSINT) including Shodan, Recon-ng, FOCA, and Maltego. It provides an overview of each tool, including their purpose and basic usage. Shodan is an internet search engine that allows searching devices connected over the internet. Recon-ng is a web reconnaissance framework for OSINT. FOCA extracts metadata from files. Maltego is an OSINT application that extracts and visually represents relationships in extracted data through entities, transforms, and machines. The document demonstrates features of each tool and provides resources for OSINT.Defense by numbers: Making problems for script kiddies
Defense by numbers: Making problems for script kiddiesChris John Riley
╠²
HTTP status codes can be used defensively to confuse scanners and script kiddies. The document discusses how different browsers interpret various status codes, and this behavior can be leveraged to fingerprint browsers or detect proxy usage. Status codes can also be used to introduce false positives and negatives in vulnerability scanners, or slow them down by returning non-standard codes from all URLs.Defense by numbers: Making Problems for Script Kiddies and Scanner Monkeys
Defense by numbers: Making Problems for Script Kiddies and Scanner MonkeysChris John Riley
╠²
The document discusses the defensive applications of HTTP status codes as a tactic to thwart automated attack tools and scanners. It outlines the categories of status codes and explains their individual meanings, while emphasizing how leveraging these codes can complicate the efforts of attackers and reduce automation effectiveness. The talk ultimately advocates for the creative use of status codes to introduce challenges for scanners, which can slow down or confuse potential attackers.Social Media Monitoring tools as an OSINT platform for intelligence
Social Media Monitoring tools as an OSINT platform for intelligenceE Hacking
╠²
This white paper discusses the application of social media monitoring tools as open source intelligence (OSINT) platforms to enhance the intelligence cycle in counter-terrorism and security sectors. It highlights how such tools improve information collection, processing, and dissemination while addressing challenges related to the vast quantity of data available online. The findings suggest that these tools significantly increase efficiency and relevance in intelligence operations, benefiting various industries including government, defense, and law enforcement.Programming in php
Programming in phprecck
╠²
This document outlines a project to create a basic password protected website using PHP and HTML. It describes creating a login page that asks for a user's name and password, which would be hardcoded. Upon correct login, a protected page would display the user's name, a welcome message, and sample protected content. This page would include a logout link. Bonus features include protecting multiple pages with the same password, allowing name changes, and tracking failed logins. The document provides hosting options for code submissions.BruCon 2011 Lightning talk winner: Web app testing without attack traffic
BruCon 2011 Lightning talk winner: Web app testing without attack trafficAbraham Aranguren
╠²
The document outlines various web application testing techniques that can be performed, many of which do not require permission, except in certain jurisdictions like Spain. It provides guidelines based on the OWASP testing guide, detailing methods for testing vulnerabilities, identifying application entry points, and analyzing the security of session management and user credentials. Additionally, the document emphasizes the importance of ethical considerations in testing practices.I put on my mink and wizard behat - Confoo Canada
I put on my mink and wizard behat - Confoo Canadaxsist10
╠²
This document discusses front end testing using Behat and Mink. It provides an overview of Behat and Mink, how they work together using the Cucumber syntax, and examples of setting up tests to validate features on a website. Context classes are demonstrated which implement step definitions to automate browser interactions and assertions. The challenges of testing JavaScript functionality are also addressed through the use of different browser driver extensions.CNIT 129S: Ch 6: Attacking Authentication
CNIT 129S: Ch 6: Attacking AuthenticationSam Bowne
╠²
Chapter 6 discusses various security vulnerabilities in web application authentication methods, highlighting the risks associated with username and password systems as well as the importance of two-factor authentication. It covers common attack vectors such as brute-force attacks, insecure password reset mechanisms, and information leakage during login processes. Recommendations for securing authentication include strong password policies, proper validation of user inputs, and secure transmission and storage of credentials.Ch 6: Attacking Authentication
Ch 6: Attacking AuthenticationSam Bowne
╠²
This document provides a summary of authentication techniques and common vulnerabilities. It discusses how over 90% of applications use usernames and passwords for authentication. More secure authentication methods like two-factor authentication are also described. The document outlines various authentication protocols like HTTP, SAML, and JWT. It then details common design flaws such as weak passwords, password change vulnerabilities, account recovery issues, and information leakage. Specific attacks like brute force, credential stuffing, and session hijacking are examined. The summary recommends approaches to secure authentication like strong credentials, hashing passwords, multi-factor authentication, and logging authentication events.You Shall Not Pass - Security in Symfony
You Shall Not Pass - Security in SymfonyThe Software House
╠²
The document outlines a development project involving user authentication and idea management features within an application. It includes details about security configurations, custom user providers, authentication tokens, and integration with Facebook Connect for user login. Additionally, it discusses the authorization process, with a focus on the implementation of voter interfaces and success handlers.CNIT 129S - Ch 6a: Attacking Authentication
CNIT 129S - Ch 6a: Attacking AuthenticationSam Bowne
╠²
Chapter 6 of CNIT 129S discusses various vulnerabilities in web application authentication systems, highlighting the prevalence of username and password combinations, the importance of two-factor authentication, and common attack vectors like brute-force attacks and account enumeration. It addresses flaws in password reset mechanisms, session management, and credential storage, advocating for best practices in securing user credentials, such as using secure hashing methods and enforcing strong password regulations. Additionally, the chapter emphasizes the need for logging and monitoring authentication events to detect and respond to security incidents effectively.Penetration Testing Report
Penetration Testing ReportAman Srivastava
╠²
The document details a penetration testing assessment of the website certifiedhacker.com, revealing various vulnerabilities including Cross-Site Scripting (XSS) and HTML forms lacking CSRF protection, which could lead to unauthorized actions by attackers. It highlights the server's infrastructure, the operational technologies in use, and notes that despite some minor vulnerabilities, the overall website security appears to be fairly robust. Additionally, the testing uncovered a directory listing and recommended implementing strict security measures for embedded external content and missing HTTP headers.Robot framework - SAST V├żst Q3
Robot framework - SAST V├żst Q3Anders Arnholm
╠²
Robot Framework is an open-source test automation framework implemented in Python, designed for automated acceptance testing that aligns with user needs and requirements. It supports keyword-driven syntax, data-driven tests, and allows easy integration with various test environments and tools. Its extensible libraries and compatibility with data formats make it suitable for agile development projects and automated testing processes.Integrated security testing public
Integrated security testing publicMorgan Roman
╠²
This document discusses how to use existing integration tests to find security vulnerabilities. It begins by defining Selenium and integration testing. It then outlines how, after reviewing the presentation, one can make existing tests find security bugs without false positives through minimal changes. The presenter discusses their experience as a tester and penetration tester. They provide an example workflow for trying to find XSS vulnerabilities and how to modify tests to add payloads at different points. The document discusses how tests can be used to find issues like XSS, SQL injection, Angular injection, authorization bugs, and more. It emphasizes trying to break tests with payloads rather than expecting them to succeed.Codeception Testing Framework -- English #phpkansai
Codeception Testing Framework -- English #phpkansaiFlorent Batard
╠²
The document discusses introducing Codeception, a PHP testing framework. It begins with an agenda that includes a presentation on Codeception, different test types, a demonstration, and best practices. It then introduces the speaker, Florent Batard, who is a security engineer and web developer from France. He explains why testing is important for reducing assumptions and validating that code runs as expected. The bulk of the document then focuses on Codeception, explaining what it is, how it works, the different types of tests it supports including acceptance, functional, and unit tests, and how to install and use it. Code examples are provided and it concludes with referencing materials and opening the floor for questions.Enabling agile devliery through enabling BDD in PHP projects
Enabling agile devliery through enabling BDD in PHP projectsKonstantin Kudryashov
╠²
The document discusses the significance of Behavior Driven Development (BDD) for enhancing agile processes in PHP projects, led by a BDD expert and creator of various tools like Behat. It emphasizes the role of BDD in improving requirements analysis, design, development, and testing, while also detailing how techniques like StoryBDD help clarify business needs and ensure alignment with client expectations through structured narratives and scenarios. The presentation also addresses the practical implementation of BDD in software development, including feedback loops and examples of feature specifications.Python Code Camp for Professionals 4/4
Python Code Camp for Professionals 4/4DEVCON
╠²
The document outlines the process of building a Python web application using MongoDB, highlighting the speed and ease of use compared to SQL databases. It provides code snippets for setting up the connection, performing basic CRUD operations using the 'pymongo' library, and creating API endpoints with the 'Bottle' framework. Additionally, it covers implementing templates for dynamic HTML content and presents examples of common return types for web APIs.I put on my mink and wizard behat
I put on my mink and wizard behatxsist10
╠²
The document discusses the implementation of front-end testing using frameworks such as Behat and Mink, including workflows for unit tests, integration tests, and user authentication scenarios. It emphasizes the importance of collaboration among team members, code coverage for user stories, and various web driver configurations for testing. Additionally, it contains practical examples, configuration setups, and advanced usage of hooks for improved testing processes.WordPress Acceptance Testing, Solved!
WordPress Acceptance Testing, Solved!Taylor Lovett
╠²
The document outlines the benefits and functionalities of WP Acceptance, a toolkit designed for automated acceptance testing in WordPress development. It emphasizes the importance of consistent testing environments among engineering teams and provides instructions for setting up tests, environment snapshots, and continuous integration. Additionally, it includes examples, debugging options, and links to extensive documentation for effective usage.Course_Presentation cyber --------------.pptx
Course_Presentation cyber --------------.pptxssuser020436
╠²
This document provides an agenda for a web application penetration testing course. The course aims to share cybersecurity knowledge in Arabic and focus on practical application. It will cover Linux basics, Burp Suite, common web vulnerabilities at easy and medium levels, and advanced topics like XSS and CSRF. Students will learn how to find data leaks, analyze protocols and network traffic, exploit vulnerabilities, and earn money through bug bounty programs.Romulus OWASP
Romulus OWASPGrupo Gesfor I+D+i
╠²
This document provides an overview of the Open Web Application Security Project (OWASP). It discusses OWASP's mission to improve application security and lists some of its key projects, including the OWASP Top Ten, a list of the most critical web application security flaws. It also summarizes several common security testing techniques like information gathering, authentication testing, session management testing, and input validation testing. Tools are mentioned for each technique.Web Bugs
Web BugsDr Rushi Raval
╠²
This document provides an overview of unusual web application security bugs and exploitation techniques discussed by Alex Kuznetsov, including exploiting logged out XSS vulnerabilities, CSRF protected XSS, XSS via HTTP headers, file upload issues, PHP oddities, SQL injection encoding attacks, and more obscure bugs involving cookies, timing attacks, and cookie policies. The talk outlines new and creative ways to bypass input validation and achieve remote code execution or sensitive data disclosure on vulnerable sites.Unusual Web Bugs
Unusual Web Bugsamiable_indian
╠²
The document summarizes various techniques for exploiting vulnerabilities in web applications, including exploiting logged out XSS vulnerabilities, CSRF protected XSS, XSS via HTTP headers, file upload issues, and encoding tricks for SQL injection. It discusses using techniques like browser password managers, session fixation, persistent data stores, and Flash to circumvent protections.CNIT 129: 6. Attacking Authentication
CNIT 129: 6. Attacking AuthenticationSam Bowne
╠²
Chapter 6 of 'Securing Web Applications' discusses various authentication attack vectors and their defenses, highlighting that over 90% of applications use username and password authentication. It emphasizes the need for stronger methods like two-factor authentication, secure credential storage, and validated password change functionalities to mitigate risks such as brute-force attacks, username enumeration, and insecure transmission of credentials. The chapter also outlines best practices for securing authentication processes, including the implementation of multi-stage logins, proper logging of events, and protecting user data from vulnerabilities.UserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40
╠²
VMwareŌĆÖs pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include ScopesŌĆöand Datacenter is now officially part of the equation. In this session, weŌĆÖll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. YouŌĆÖll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiencyŌĆöall without migrating to the cloud. WeŌĆÖll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.More Related Content
Similar to Cutting accounts down to scythe (20)
Programming in php
Programming in phprecck
╠²
This document outlines a project to create a basic password protected website using PHP and HTML. It describes creating a login page that asks for a user's name and password, which would be hardcoded. Upon correct login, a protected page would display the user's name, a welcome message, and sample protected content. This page would include a logout link. Bonus features include protecting multiple pages with the same password, allowing name changes, and tracking failed logins. The document provides hosting options for code submissions.BruCon 2011 Lightning talk winner: Web app testing without attack traffic
BruCon 2011 Lightning talk winner: Web app testing without attack trafficAbraham Aranguren
╠²
The document outlines various web application testing techniques that can be performed, many of which do not require permission, except in certain jurisdictions like Spain. It provides guidelines based on the OWASP testing guide, detailing methods for testing vulnerabilities, identifying application entry points, and analyzing the security of session management and user credentials. Additionally, the document emphasizes the importance of ethical considerations in testing practices.I put on my mink and wizard behat - Confoo Canada
I put on my mink and wizard behat - Confoo Canadaxsist10
╠²
This document discusses front end testing using Behat and Mink. It provides an overview of Behat and Mink, how they work together using the Cucumber syntax, and examples of setting up tests to validate features on a website. Context classes are demonstrated which implement step definitions to automate browser interactions and assertions. The challenges of testing JavaScript functionality are also addressed through the use of different browser driver extensions.CNIT 129S: Ch 6: Attacking Authentication
CNIT 129S: Ch 6: Attacking AuthenticationSam Bowne
╠²
Chapter 6 discusses various security vulnerabilities in web application authentication methods, highlighting the risks associated with username and password systems as well as the importance of two-factor authentication. It covers common attack vectors such as brute-force attacks, insecure password reset mechanisms, and information leakage during login processes. Recommendations for securing authentication include strong password policies, proper validation of user inputs, and secure transmission and storage of credentials.Ch 6: Attacking Authentication
Ch 6: Attacking AuthenticationSam Bowne
╠²
This document provides a summary of authentication techniques and common vulnerabilities. It discusses how over 90% of applications use usernames and passwords for authentication. More secure authentication methods like two-factor authentication are also described. The document outlines various authentication protocols like HTTP, SAML, and JWT. It then details common design flaws such as weak passwords, password change vulnerabilities, account recovery issues, and information leakage. Specific attacks like brute force, credential stuffing, and session hijacking are examined. The summary recommends approaches to secure authentication like strong credentials, hashing passwords, multi-factor authentication, and logging authentication events.You Shall Not Pass - Security in Symfony
You Shall Not Pass - Security in SymfonyThe Software House
╠²
The document outlines a development project involving user authentication and idea management features within an application. It includes details about security configurations, custom user providers, authentication tokens, and integration with Facebook Connect for user login. Additionally, it discusses the authorization process, with a focus on the implementation of voter interfaces and success handlers.CNIT 129S - Ch 6a: Attacking Authentication
CNIT 129S - Ch 6a: Attacking AuthenticationSam Bowne
╠²
Chapter 6 of CNIT 129S discusses various vulnerabilities in web application authentication systems, highlighting the prevalence of username and password combinations, the importance of two-factor authentication, and common attack vectors like brute-force attacks and account enumeration. It addresses flaws in password reset mechanisms, session management, and credential storage, advocating for best practices in securing user credentials, such as using secure hashing methods and enforcing strong password regulations. Additionally, the chapter emphasizes the need for logging and monitoring authentication events to detect and respond to security incidents effectively.Penetration Testing Report
Penetration Testing ReportAman Srivastava
╠²
The document details a penetration testing assessment of the website certifiedhacker.com, revealing various vulnerabilities including Cross-Site Scripting (XSS) and HTML forms lacking CSRF protection, which could lead to unauthorized actions by attackers. It highlights the server's infrastructure, the operational technologies in use, and notes that despite some minor vulnerabilities, the overall website security appears to be fairly robust. Additionally, the testing uncovered a directory listing and recommended implementing strict security measures for embedded external content and missing HTTP headers.Robot framework - SAST V├żst Q3
Robot framework - SAST V├żst Q3Anders Arnholm
╠²
Robot Framework is an open-source test automation framework implemented in Python, designed for automated acceptance testing that aligns with user needs and requirements. It supports keyword-driven syntax, data-driven tests, and allows easy integration with various test environments and tools. Its extensible libraries and compatibility with data formats make it suitable for agile development projects and automated testing processes.Integrated security testing public
Integrated security testing publicMorgan Roman
╠²
This document discusses how to use existing integration tests to find security vulnerabilities. It begins by defining Selenium and integration testing. It then outlines how, after reviewing the presentation, one can make existing tests find security bugs without false positives through minimal changes. The presenter discusses their experience as a tester and penetration tester. They provide an example workflow for trying to find XSS vulnerabilities and how to modify tests to add payloads at different points. The document discusses how tests can be used to find issues like XSS, SQL injection, Angular injection, authorization bugs, and more. It emphasizes trying to break tests with payloads rather than expecting them to succeed.Codeception Testing Framework -- English #phpkansai
Codeception Testing Framework -- English #phpkansaiFlorent Batard
╠²
The document discusses introducing Codeception, a PHP testing framework. It begins with an agenda that includes a presentation on Codeception, different test types, a demonstration, and best practices. It then introduces the speaker, Florent Batard, who is a security engineer and web developer from France. He explains why testing is important for reducing assumptions and validating that code runs as expected. The bulk of the document then focuses on Codeception, explaining what it is, how it works, the different types of tests it supports including acceptance, functional, and unit tests, and how to install and use it. Code examples are provided and it concludes with referencing materials and opening the floor for questions.Enabling agile devliery through enabling BDD in PHP projects
Enabling agile devliery through enabling BDD in PHP projectsKonstantin Kudryashov
╠²
The document discusses the significance of Behavior Driven Development (BDD) for enhancing agile processes in PHP projects, led by a BDD expert and creator of various tools like Behat. It emphasizes the role of BDD in improving requirements analysis, design, development, and testing, while also detailing how techniques like StoryBDD help clarify business needs and ensure alignment with client expectations through structured narratives and scenarios. The presentation also addresses the practical implementation of BDD in software development, including feedback loops and examples of feature specifications.Python Code Camp for Professionals 4/4
Python Code Camp for Professionals 4/4DEVCON
╠²
The document outlines the process of building a Python web application using MongoDB, highlighting the speed and ease of use compared to SQL databases. It provides code snippets for setting up the connection, performing basic CRUD operations using the 'pymongo' library, and creating API endpoints with the 'Bottle' framework. Additionally, it covers implementing templates for dynamic HTML content and presents examples of common return types for web APIs.I put on my mink and wizard behat
I put on my mink and wizard behatxsist10
╠²
The document discusses the implementation of front-end testing using frameworks such as Behat and Mink, including workflows for unit tests, integration tests, and user authentication scenarios. It emphasizes the importance of collaboration among team members, code coverage for user stories, and various web driver configurations for testing. Additionally, it contains practical examples, configuration setups, and advanced usage of hooks for improved testing processes.WordPress Acceptance Testing, Solved!
WordPress Acceptance Testing, Solved!Taylor Lovett
╠²
The document outlines the benefits and functionalities of WP Acceptance, a toolkit designed for automated acceptance testing in WordPress development. It emphasizes the importance of consistent testing environments among engineering teams and provides instructions for setting up tests, environment snapshots, and continuous integration. Additionally, it includes examples, debugging options, and links to extensive documentation for effective usage.Course_Presentation cyber --------------.pptx
Course_Presentation cyber --------------.pptxssuser020436
╠²
This document provides an agenda for a web application penetration testing course. The course aims to share cybersecurity knowledge in Arabic and focus on practical application. It will cover Linux basics, Burp Suite, common web vulnerabilities at easy and medium levels, and advanced topics like XSS and CSRF. Students will learn how to find data leaks, analyze protocols and network traffic, exploit vulnerabilities, and earn money through bug bounty programs.Romulus OWASP
Romulus OWASPGrupo Gesfor I+D+i
╠²
This document provides an overview of the Open Web Application Security Project (OWASP). It discusses OWASP's mission to improve application security and lists some of its key projects, including the OWASP Top Ten, a list of the most critical web application security flaws. It also summarizes several common security testing techniques like information gathering, authentication testing, session management testing, and input validation testing. Tools are mentioned for each technique.Web Bugs
Web BugsDr Rushi Raval
╠²
This document provides an overview of unusual web application security bugs and exploitation techniques discussed by Alex Kuznetsov, including exploiting logged out XSS vulnerabilities, CSRF protected XSS, XSS via HTTP headers, file upload issues, PHP oddities, SQL injection encoding attacks, and more obscure bugs involving cookies, timing attacks, and cookie policies. The talk outlines new and creative ways to bypass input validation and achieve remote code execution or sensitive data disclosure on vulnerable sites.Unusual Web Bugs
Unusual Web Bugsamiable_indian
╠²
The document summarizes various techniques for exploiting vulnerabilities in web applications, including exploiting logged out XSS vulnerabilities, CSRF protected XSS, XSS via HTTP headers, file upload issues, and encoding tricks for SQL injection. It discusses using techniques like browser password managers, session fixation, persistent data stores, and Flash to circumvent protections.CNIT 129: 6. Attacking Authentication
CNIT 129: 6. Attacking AuthenticationSam Bowne
╠²
Chapter 6 of 'Securing Web Applications' discusses various authentication attack vectors and their defenses, highlighting that over 90% of applications use username and password authentication. It emphasizes the need for stronger methods like two-factor authentication, secure credential storage, and validated password change functionalities to mitigate risks such as brute-force attacks, username enumeration, and insecure transmission of credentials. The chapter also outlines best practices for securing authentication processes, including the implementation of multi-stage logins, proper logging of events, and protecting user data from vulnerabilities.Recently uploaded (20)
UserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40
╠²
VMwareŌĆÖs pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include ScopesŌĆöand Datacenter is now officially part of the equation. In this session, weŌĆÖll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. YouŌĆÖll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiencyŌĆöall without migrating to the cloud. WeŌĆÖll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.Mastering AI Workflows with FME by Mark Do╠łring
Mastering AI Workflows with FME by Mark Do╠łringSafe Software
╠²
Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FMEŌĆÖs powerful tools for training, optimization, and seamless integrationAI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
╠²
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike."How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.The Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu
╠²
A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash
╠²
10 Key Challenges for AI within the EU Data Protection FrameworkAI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash
╠²
Cracking the Code - Unveiling Synergies Between Open Source Security and AIUsing the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the SameSecurity Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
╠²
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik
╠²
A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
╠²
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
¤æŗ Introducing Data Contracts: An agreement between data producers and consumers
¤ōØ Data Contracts key components: Understanding a contract and its purpose
¤¦æŌĆŹ¤Ä© Writing your first contract: How to create your own contracts in OpenMetadata
¤”Š An OpenMetadata MCP Server update!
Ō×Ģ And More!Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash
╠²
Oh, the Possibilities - Balancing Innovation and Risk with Generative AICluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...
Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...janeliewang985
╠²
the slides of the MP selection approach CMPS9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.Ad
Cutting accounts down to scythe
- 1. Cutting accounts down to SCYTHE! Chris John Riley
- 3. ŌĆ£THE WISEST MAN, IS HE WHO KNOWS, THAT HE KNOWS NOTHINGŌĆØ SOCRATES: APOLOGY, 21D
- 5. 1) What 2) Why 3) How 4) QŌĆÖs
- 6. WHAT?
- 7. FRAMEWORK FOR USER ENUMERATION
- 9. What ’é¦Written in Python ’é¦Threaded ’é¦Modular ’é¦Description files (XML) ’é¦Easy to use ’é¦Hopefully!
- 10. WHY?
- 13. Why ’é¦Speed up account enumeration ’é¦ POC Examples ’é¦Offer advanced features ’é¦ Cookie support ’é¦ CSRF token collection ’é¦ Wait / Retries ’é¦ Threading
- 14. HOW?
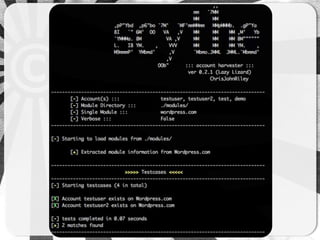
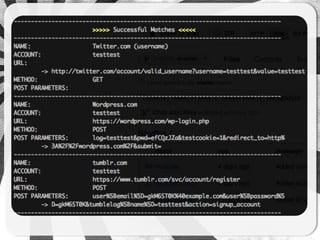
- 15. IT ALL STARTS WITH A MODULE
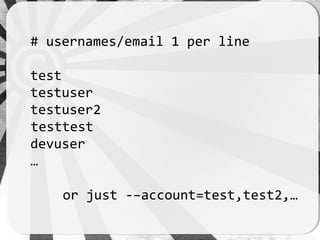
- 16. BASIC
- 17. Basic module <module> <site> <name>basic module</name> <url> <![CDATA[https://example.com/signup_check/ username=<ACCOUNT>]]> </url> <method>GET</method> <successmatch>taken</successmatch> </site> </module>
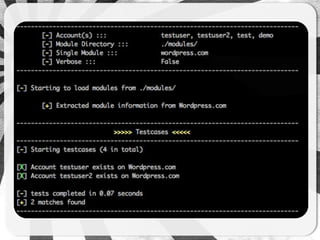
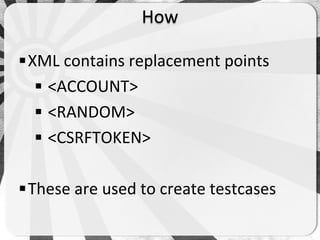
- 18. ADVANCED
- 19. <!-- Wordpress.com - Logon user enumeration issue --> <module> <site> <name>Wordpress.com</name> <url><![CDATA[https://wordpress.com/wp-login.php]]></url> <method>POST</method> <postParameters> <![CDATA [log=<ACCOUNT>&pwd=<RANDOM>redirect_to=http://wordpress.com]]> </postParameters> <headers></headers> <requestCookie>False</requestCookie> <requestCSRF>False</requestCSRF> <successmatch>The password you entered for the email or user</successmatch> <negativematch>Invalid email or username</negativematch> <errormatch>You have exceeded the login limit</errormatch> <date>13/09/2012</date> <version>2</version> <author>CJR</author> <category>blogs</category> </site> </module>
- 20. <!-- Wordpress.com - Logon user enumeration issue --> <module> <site> <name>Wordpress.com</name> <url><![CDATA[https://wordpress.com/wp-login.php]]></url> <method>POST</method> <postParameters> <![CDATA [log=<ACCOUNT>&pwd=<RANDOM>redirect_to=http://wordpress.com]]> </postParameters> <headers></headers> <requestCookie>False</requestCookie> <requestCSRF>False</requestCSRF> <successmatch>The password you entered for the email or user</successmatch> <negativematch>Invalid email or username</negativematch> <errormatch>You have exceeded the login limit</errormatch> <date>13/09/2012</date> <version>2</version> <author>CJR</author> <category>blogs</category> </site> </module>
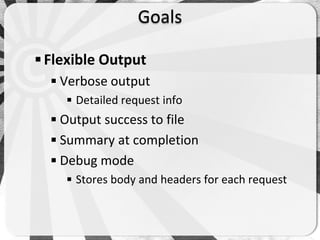
- 21. <!-- Wordpress.com - Logon user enumeration issue --> <module> <site> <name>Wordpress.com</name> <url><![CDATA[https://wordpress.com/wp- login.php]]></url> <method>POST</method> <postParameters> <![CDATA [log=<ACCOUNT>&pwd=<RANDOM>redirect_to= http://wordpress.com]]> </postParameters>
- 22. <headers></headers> <requestCookie>False</requestCookie> <requestCSRF>False</requestCSRF> <successmatch>The password you entered for the email or user</successmatch> <negativematch>Invalid email or username</negativematch> <errormatch>You have exceeded the login limit</errormatch> <date>13/09/2012</date> <version>2</version> <author>CJR</author> <category>blogs</category> </site> </module>
- 23. ADD A LIST OF USERNAMES / EMAILS
- 24. # usernames/email 1 per line test testuser testuser2 testtest devuser ŌĆ” or just -ŌĆōaccount=test,test2,ŌĆ”
- 25. MIX AND LEAVE TO RUN FOR A FEW MINUTES
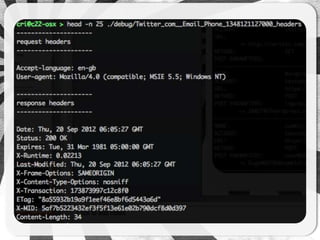
- 28. How ’é¦ XML contains replacement points ’é¦ <ACCOUNT> ’é¦ <RANDOM> ’é¦ <CSRFTOKEN> ’é¦ These are used to create testcases
- 29. GOALS
- 30. Goals ’é¦ Flexible Running ’é¦ Single module (targeted) ’é¦ --single wordpress.com ’é¦ Category of modules ’é¦ --category=blogs ’é¦ Single account ’é¦ --account=test ’é¦ Filename containing accounts ’é¦ --accountfile=accounts.txt
- 31. Goals ’é¦ Flexible Handling ’é¦ Error detection ’é¦ Retry on error (<errorcode>) ’é¦ -- retries and --retrytime ’é¦ Handles cookies and CSRF tokens ’é¦ <CSRF_URL> ’é¦ <CSRF_regex> to extract token ’é¦ Insert into request using <CSRFTOKEN>
- 32. Goals ’é¦ Flexible Output ’é¦ Verbose output ’é¦ Detailed request info ’é¦ Output success to file ’é¦ Summary at completion ’é¦ Debug mode ’é¦ Stores body and headers for each request
- 36. Questions?
- 37. GO FORTH AND ENUMERATE ALL THE THINGS!
- 38. Thanks for coming http://c22.cc contact@c22.cc
