Dark Knight- UCAV
- 1. Stealth Unmanned Combat Air Vehicle Dark Knight Jaydeep Deshpande
- 2. Dark Knight âĒ Aircraft âĒ Unmanned âĒ Stealth
- 3. Stealth
- 4. Stealth ï Concealing your identity from your enemy ï Low observable technology ï It is a combination of technologies that attempt to greatly reduce the distances at which a person or vehicle can be detected.
- 5. Elements of Stealth ï Reduction in Radar Cross Section 1. Stealthy Plan-form 2. Radar Absorbent Material Coating (RAM) 3. Reflection ï Reduction in Heat Signature 1. Use of highly specialized alloys and ceramics 2. Surface coatings ï Electronic Noise reduction 1. Reducing Electronic noise emission (Radars, Electronic Warfare Suit)
- 6. Plan-form RAM coating Reflection- The Hopeless Diamond Reduced Heat Signature
- 7. Unmanned Air Vehicle ï Pilotless ï Takes instructions from ground control ï Complete flight path can be pre-programmed ï Very high endurance ï Higher survivability
- 8. Global Hawk Reaper
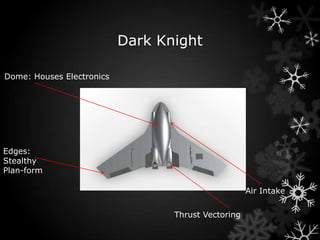
- 9. Dark Knight ï Stealthy Plan-form ï Shielded Engine Blades ï Surface coatings (RAM + Friction reducing) ï Reduced Heat Signature ï Thrust Vectored Engine Nozzles
- 10. Dark Knight Dome: Houses Electronics Edges: Stealthy Plan-form Air Intake Thrust Vectoring
- 11. Dark Knight All moving Vertical Stabilizers Well Hidden Engine Blades Housing for external Weapons
- 12. Thank you