Differences to Know Between SSL & TLS certificate .pdf
0 likes42 views
SSL & TLS, Both security protocols are different from each other. In this article, we are going to compare both in detail. LetŌĆÖs dive into it!
1 of 3
Download to read offline

Recommended
Comparative Analysis of Open-SSL Vulnerabilities & Heartbleed Exploit Detection



Comparative Analysis of Open-SSL Vulnerabilities & Heartbleed Exploit DetectionCSCJournals
╠²
Since its introduction in 1994 the Secure Socket Layer (SSL) protocol (later renamed to Transport Layer Security (TLS)) evolved to the de facto standard for securing the transport layer. SSL/TLS can be used for ensuring data confidentiality, integrity and authenticity during transport. A main feature of the protocol is its flexibility. Modes of operation and security aims can easily be configured through different cipher suites. During its evolutionary development process several flaws were found. However, the flexible architecture of SSL/TLS allowed efficient fixes in order to counter the issues. This paper presents an overview on theoretical and practical attacks of the last 20 years.SSL VS TLS.pptx



SSL VS TLS.pptxVignesh kumar
╠²
SILICON CHIPS TAMILAN
Ó«ģÓ«ŻÓ«┐Ó«▓Ó»Ź Ó«ÜÓ»ćÓ«ĄÓ»łÓ«ĢÓ«│Ó»Ź (Squirrel Services)
Hello friends, this is my YouTube channel where I share knowledge about computer hardware, software, networking, server details and Job openings..
NAME : VIGNESH KUMAR
ADDRESS : INDIA , (TAMILNADU).
INSTAGRAM USER NAME : vignesh301992
Ssl and tls



Ssl and tlsRana assad ali
╠²
Transport Layer Security (TLS) is the successor to the Secure Sockets Layer (SSL) protocol. TLS ensures privacy and security between communicating applications and users on the internet by preventing eavesdropping, tampering, and message forgery. It works by having the client and server negotiate a cipher suite and protocol version to use to securely transmit encrypted messages. This establishes a secure channel over an unsecured network like the internet to provide confidentiality, integrity, and authentication of communications.What is TLS/SSL? 



What is TLS/SSL? Shehzad Imran
╠²
This document provides an overview of Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL). It begins with an introduction to TLS/SSL, explaining what they are and their purposes of providing encryption, authentication and integrity verification. It then discusses digital certificates, the TLS/SSL handshake protocol and record protocol. It explains the four upper layer protocols: record, change cipher spec, alert and handshake. It provides details on SSL, TLS, their implementations and applications. The document is intended to explore how TLS works, best practices for its use, and its various applications in securing business computing.Ssl https



Ssl httpsAndrada Boldis
╠²
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that secure internet connections between clients and servers. SSL was originally developed by Netscape in the 1990s to provide HTTPS secure connections for web browsing. It uses public/private key encryption and digital certificates to authenticate servers and establish encrypted connections to securely transmit data over TCP/IP networks like the internet. TLS improved upon SSL by addressing security vulnerabilities and supporting newer encryption algorithms. HTTP (Hypertext Transfer Protocol) is the underlying protocol used to request and transmit web pages and other files over the internet. Combining HTTP with SSL/TLS results in HTTPS, the secure version of HTTP used for encrypted web browsing and transactions.SSL and TLS Theory and Practice 2nd Edition Rolf Oppliger



SSL and TLS Theory and Practice 2nd Edition Rolf Oppligerchizzyejinsu
╠²
SSL and TLS Theory and Practice 2nd Edition Rolf Oppliger
SSL and TLS Theory and Practice 2nd Edition Rolf Oppliger
SSL and TLS Theory and Practice 2nd Edition Rolf OppligerION Santiago: Lock It Up: TLS for Network Operators



ION Santiago: Lock It Up: TLS for Network OperatorsDeploy360 Programme (Internet Society)
╠²
The document discusses the history and evolution of TLS (Transport Layer Security) and SSL (Secure Sockets Layer), their increasing usage across internet applications and services, and efforts by organizations like IETF and Internet Society to promote stronger encryption and the adoption of TLS. It provides an overview of TLS versions and standards development, factors driving increased TLS usage like Snowden revelations, and resources for network operators and developers to help secure communications over the internet using TLS.Sequere socket Layer



Sequere socket LayerRaghavendra Rao
╠²
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that provide secure communication over the internet. They allow for confidentiality, integrity, and authentication between two applications communicating over TCP. SSL/TLS works by encrypting the segments of TCP connections above the transport layer through the use of symmetric and asymmetric cryptography. It establishes a secure channel over an insecure network such as the internet.Introduction to SSL and How to Exploit & Secure



Introduction to SSL and How to Exploit & SecureBrian Ritchie
╠²
The document discusses SSL/TLS, how it works to securely transmit data between endpoints, and potential vulnerabilities. It provides an overview of SSL/TLS protocols and how data is encrypted and transmitted. It then outlines several common endpoint issues that can compromise SSL/TLS, such as inconsistent DNS configurations, self-signed certificates, incomplete certificates, and mixing plain text and encrypted sessions. Exploiting these issues allows man-in-the-middle attacks that can intercept and decrypt encrypted traffic.Transport Layer Security 



Transport Layer Security Ibrahiem Mohammed
╠²
TLS protocol provides transport layer security for internet applications by securing communications between clients and servers. It establishes an encrypted connection through a handshake that negotiates encryption algorithms and authentication, then uses symmetric encryption and message authentication codes to provide confidentiality and integrity for data transfer. TLS has evolved through several versions to strengthen security and address weaknesses in cryptographic algorithms.[Cluj] Turn SSL ON![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
[Cluj] Turn SSL ONOWASP EEE
╠²
This document discusses SSL/TLS protocols and how to set up your own certificate authority (CA) or use Let's Encrypt for free SSL certificates.
It provides a brief history of SSL and TLS protocols, outlines the key differences between versions, and lists common TLS implementations like OpenSSL. It then explains how to set up your own CA by generating root and intermediate certificates and signing server/client certificates.
Finally, it introduces Let's Encrypt as a free and automated CA that aims to promote SSL security. It explains how Let's Encrypt validates domain ownership and issues certificates to ensure communications are private, integrity is maintained, and parties can be trusted.ION Sri Lanka - TLS for Network Operators



ION Sri Lanka - TLS for Network OperatorsDeploy360 Programme (Internet Society)
╠²
This document discusses the increased usage of Transport Layer Security (TLS) across internet applications and networks due to revelations of global surveillance. It outlines responses by organizations like the IETF to strengthen security and privacy of internet protocols by incorporating TLS. These include new working groups to update TLS usage and deprecating insecure versions. As a result, network operators are encouraged to support TLS encrypted traffic and help customers adopt TLS for their services and applications. Challenges in monitoring encrypted traffic and validating certificate authenticity are also addressed.Secure Sockets Layer(SSL)Certificate



Secure Sockets Layer(SSL)CertificateCheapSSLUSA
╠²
In this Pdf,you can know what is SSL Certificate?,How it wroks?,who need SSL Certificate? How you can secure your website in this internet world?
All these Question's solution in giving in this Pdf.TLS - Transport Layer Security



TLS - Transport Layer SecurityByronKimani
╠²
TLS (Transport Layer Security) is a cryptographic protocol that provides encryption and security for data sent over the internet. It is used by HTTPS to encrypt communication between web browsers and servers. TLS 1.2, the previous standard, had security flaws in how it exchanged encryption keys. TLS 1.3 improves security by using Diffie-Hellman key exchange so keys are not sent directly over the network. To upgrade a website from HTTP to HTTPS, an SSL certificate must be purchased and installed, all links on the site must be changed to HTTPS, and HTTP traffic should be redirected to HTTPS.White paper - Full SSL automation with OneClickSSL



White paper - Full SSL automation with OneClickSSLGlobalSign
╠²
SSL Automation from application to installation
GlobalSign has designed, developed and patented OneClickSSLŌäó, a revolutionary technology that simplifies the process from SSL application to installation with levels of automation previously considered impossible ŌĆō eliminating support fees and minimizing time spent supporting customers.
Learn how the OneClickSSL technology works, the deployment options and use cases and how to generate new revenues with OneClickSSL.#Morecrypto (with tis) - version 2.2



#Morecrypto (with tis) - version 2.2Olle E Johansson
╠²
This document discusses the importance of using more encryption on the Internet to increase privacy and security. It makes the following key points:
1) The Internet has become too easy to monitor as we have built it without sufficient security protections by default. More encryption needs to be implemented across Internet services and protocols to make eavesdropping more difficult.
2) Developers should enable encryption by default for all new Internet protocols. Opportunistic encryption techniques can provide some protections even without full authentication.
3) Individuals can help push for more encryption by requiring encrypted connections when using services and enabling tools like HTTPS Everywhere on their browsers. Transitioning to encrypted connections wherever possible raises the bar for surveillance.SSLtalk



SSLtalkMatthew Aylard
╠²
The document discusses the history and purpose of TLS/SSL, including how it uses asymmetric and symmetric cryptography. It describes how TLS/SSL works, including the handshake and record layers, cipher suites, and public key infrastructure (PKI). It notes that TLS/SSL secures communications between applications and transport layers in the OSI model. Examples of exploits like session hijacking and man-in-the-middle attacks are provided to illustrate the importance of encryption.Secure Sockets Layer and Transport Layer Security



Secure Sockets Layer and Transport Layer SecurityAl Mamun
╠²
Transport Layer Security and its predecessor, Secure Sockets Layer, are cryptographic protocols that provide communications security over a computer network.What is SSL ? The Secure Sockets Layer (SSL) Protocol



What is SSL ? The Secure Sockets Layer (SSL) ProtocolMohammed Adam
╠²
SSL is a protocol that allows clients and servers to securely communicate over the internet. It uses public-key encryption to authenticate servers, optionally authenticate clients, and establish an encrypted connection to securely transmit data. The SSL handshake allows the client and server to negotiate encryption parameters to generate shared secrets and session keys, which are then used to encrypt all further communication during the SSL session. Common implementations of SSL include OpenSSL and Apache-SSL.Report on Heartbleed



Report on HeartbleedShiva Sagar
╠²
Day by day as the complexity in the Internet increasing the vulnerabilities about the security is also increasing. So the knowledge about these flaws has to be spread. So this report discuss about the one of the vulnerability that exists for a long time called ŌĆśHeartbleedŌĆÖ. The purpose of this report is to create awareness about the Heartbleed vulnerability in OpenSSL Library, using which attackers can get access to passwords, private keys or any encrypted data. It explains how Heartbleed works, what code causes data leakage and explains the resolution with code fix. It also explains perform how to perform heartbeat attack.Vulnerabilities of the SSL/TLS Protocol



Vulnerabilities of the SSL/TLS Protocolcsandit
╠²
This paper analyzes vulnerabilities of the SSL/TLS
Handshake
protocol
, which
is
responsible
for
authentication of
the parties in the
communication
and
negotiation of
security parameters
that
will be used
to protect
confidentiality and
integrity of the
data
. It
will
be
analyzed the
attacks
against the implementation of Handshake
protocol, as well as the
attacks against the other
elements
necessary to SSL/TLS protocol to discover security
flaws that were exploited, modes of
attack, the potential consequences, but also studyi
ng methods of defense
.
All versions of the
protocol are going to be the subject of the researc
h but
emphasis will be placed
on the critical
attack that
the most endanger the safety of data.
The goal of
the research
is
to point out the
danger of
existence
of at least
vulnerability
in the SSL/TLS protocol
, which
can be exploited
and
endanger the safety of
the data
that should be protected. VULNERABILITIES OF THE SSL/TLS PROTOCOL



VULNERABILITIES OF THE SSL/TLS PROTOCOLcscpconf
╠²
This paper analyzes vulnerabilities of the SSL/TLS Handshake protocol, which is responsible for authentication of the parties in the communication and negotiation of security parameters that will be used to protect confidentiality and integrity of the data. It will be analyzed the attacks against the implementation of Handshake protocol, as well as the attacks against the other
elements necessary to SSL/TLS protocol to discover security flaws that were exploited, modes of
attack, the potential consequences, but also studying methods of defense. All versions of the
protocol are going to be the subject of the research but emphasis will be placed on the critical attack that the most endanger the safety of data. The goal of the research is to point out the
danger of existence of at least vulnerability in the SSL/TLS protocol, which can be exploited and endanger the safety of the data that should be protected.
Explain how SSL protocol is used to ensure the confidentiality and int.docx



Explain how SSL protocol is used to ensure the confidentiality and int.docxtodd401
╠²
Explain how SSL protocol is used to ensure the confidentiality and integrity of the Internet traffic.
Solution
SSL uses a combination of public-key and symmetric-key encryption to secure a connection between two machines, typically a Web or mail server and a client machine, communicating over the Internet or an internal network.
Using the OSI reference model as context, SSL runs above the TCP/IP protocol, which is responsible for the transport and routing of data over a network, and below higher-level protocols such as HTTP and IMAP, encrypting the data of network connections in the application layer of the Internet Protocol suite. The \"sockets\" part of the term refers to the sockets method of passing data back and forth between a client and a server program in a network, or between program layers in the same computer.
The Transport Layer Security (TLS) protocol evolved from SSL and has largely superseded it, although the terms SSL or SSL/TLS are still commonly used; SSL is often used to refer to what is actually TLS. The combination of SSL/TLS is the most widely deployed security protocol used today and is found in applications such as Web browsers, email and basically any situation where data needs to be securely exchanged over a network, like file transfers, VPN connections, instant messaging and voice over IP.
The SSL protocol includes two sub-protocols: the record protocol and the \"handshake\" protocol. These protocols allow a client to authenticate a server and establish an encrypted SSL connection. In what\'s referred to as the \"initial handshake process,\" a server that supports SSL presents its digital certificate to the client to authenticate the server\'s identity. Server certificates follow the X.509 certificate format that is defined by the Public-Key Cryptography Standards (PKCS). The authentication process uses public-key encryption to validate the digital certificate and confirm that a server is in fact the server it claims to be.
Once the server has been authenticated, the client and server establish cipher settings and a shared key to encrypt the information they exchange during the remainder of the session. This provides data confidentiality and integrity. This whole process is invisible to the user.
For example, if a webpage requires an SSL connection, the URL will change from HTTP to HTTPS and a padlock icon appears in the browser once the server has been authenticated.
The handshake also allows the client to authenticate itself to the server. In this case, after server authentication is successfully completed, the client must present its certificate to the server to authenticate the client\'s identity before the encrypted SSL session can be established.
.ENCRYPTION.pptx



ENCRYPTION.pptxabbu03oct
╠²
Encryption is a technique used to protect data and transmissions by encoding them in a way that only authorized parties can access. There are two main types: symmetric encryption uses a single secret key for encryption and decryption, while asymmetric encryption uses two keys - a public key to encrypt and a private key to decrypt. Symmetric encryption is faster but less secure as it relies on secure key exchange, while asymmetric encryption uses separate keys and is more secure though computationally slower. Digital certificates verify the identity of websites, machines, or devices and are issued by certificate authorities to facilitate secure transactions online.OpenSSL



OpenSSLTimbal Mayank
╠²
SSL and certificates exist to provide encryption and identification for secure communication between web servers and clients. OpenSSL is a cryptography library and toolkit that implements the SSL and TLS protocols, providing encryption through different ciphers and algorithms. It is widely used by over 60% of web servers to generate private keys, certificate signing requests, and perform encryption and decryption as well as manage certificates.secure socket layer



secure socket layerAmar Shah
╠²
SSL and TLS are cryptographic protocols that provide secure communication on the internet. They use public/private key encryption to authenticate servers and establish encrypted connections. While similar, TLS is the standardized successor to SSL. Key differences include TLS using HMAC for integrity checking and having additional alert codes not found in SSL. Both protocols operate at the transport layer and provide data confidentiality, integrity, and server authentication.Details about the SSL Certificate



Details about the SSL CertificateCheapSSLUSA
╠²
In this Pdf,you can know about the SSL certificate.
Who use SSL Certificate?
How it works.?
all this questions solution is in this pdf.Web Design Creating User-Friendly and Visually Engaging Websites - April 2025...



Web Design Creating User-Friendly and Visually Engaging Websites - April 2025...TheoRuby
╠²
Website design for small business owners looking at wordpress and elementor pro and covering all areas of design including UX and storytelling!
Dehydrated Fruits and Vegetables Market: Healthy Convenience & Long Shelf Life



Dehydrated Fruits and Vegetables Market: Healthy Convenience & Long Shelf Lifechanderdeepseoexpert
╠²
Explore the Dehydrated Fruits and Vegetables Market, driven by growing demand for healthy, convenient, and shelf-stable food options. Ideal for snacks, ready meals, and emergency supplies, these products offer nutritional value and extended storage life. Key trends include clean-label products, innovative drying technologies, and rising health consciousness among consumers worldwide.More Related Content
Similar to Differences to Know Between SSL & TLS certificate .pdf (20)
Introduction to SSL and How to Exploit & Secure



Introduction to SSL and How to Exploit & SecureBrian Ritchie
╠²
The document discusses SSL/TLS, how it works to securely transmit data between endpoints, and potential vulnerabilities. It provides an overview of SSL/TLS protocols and how data is encrypted and transmitted. It then outlines several common endpoint issues that can compromise SSL/TLS, such as inconsistent DNS configurations, self-signed certificates, incomplete certificates, and mixing plain text and encrypted sessions. Exploiting these issues allows man-in-the-middle attacks that can intercept and decrypt encrypted traffic.Transport Layer Security 



Transport Layer Security Ibrahiem Mohammed
╠²
TLS protocol provides transport layer security for internet applications by securing communications between clients and servers. It establishes an encrypted connection through a handshake that negotiates encryption algorithms and authentication, then uses symmetric encryption and message authentication codes to provide confidentiality and integrity for data transfer. TLS has evolved through several versions to strengthen security and address weaknesses in cryptographic algorithms.[Cluj] Turn SSL ON![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
[Cluj] Turn SSL ONOWASP EEE
╠²
This document discusses SSL/TLS protocols and how to set up your own certificate authority (CA) or use Let's Encrypt for free SSL certificates.
It provides a brief history of SSL and TLS protocols, outlines the key differences between versions, and lists common TLS implementations like OpenSSL. It then explains how to set up your own CA by generating root and intermediate certificates and signing server/client certificates.
Finally, it introduces Let's Encrypt as a free and automated CA that aims to promote SSL security. It explains how Let's Encrypt validates domain ownership and issues certificates to ensure communications are private, integrity is maintained, and parties can be trusted.ION Sri Lanka - TLS for Network Operators



ION Sri Lanka - TLS for Network OperatorsDeploy360 Programme (Internet Society)
╠²
This document discusses the increased usage of Transport Layer Security (TLS) across internet applications and networks due to revelations of global surveillance. It outlines responses by organizations like the IETF to strengthen security and privacy of internet protocols by incorporating TLS. These include new working groups to update TLS usage and deprecating insecure versions. As a result, network operators are encouraged to support TLS encrypted traffic and help customers adopt TLS for their services and applications. Challenges in monitoring encrypted traffic and validating certificate authenticity are also addressed.Secure Sockets Layer(SSL)Certificate



Secure Sockets Layer(SSL)CertificateCheapSSLUSA
╠²
In this Pdf,you can know what is SSL Certificate?,How it wroks?,who need SSL Certificate? How you can secure your website in this internet world?
All these Question's solution in giving in this Pdf.TLS - Transport Layer Security



TLS - Transport Layer SecurityByronKimani
╠²
TLS (Transport Layer Security) is a cryptographic protocol that provides encryption and security for data sent over the internet. It is used by HTTPS to encrypt communication between web browsers and servers. TLS 1.2, the previous standard, had security flaws in how it exchanged encryption keys. TLS 1.3 improves security by using Diffie-Hellman key exchange so keys are not sent directly over the network. To upgrade a website from HTTP to HTTPS, an SSL certificate must be purchased and installed, all links on the site must be changed to HTTPS, and HTTP traffic should be redirected to HTTPS.White paper - Full SSL automation with OneClickSSL



White paper - Full SSL automation with OneClickSSLGlobalSign
╠²
SSL Automation from application to installation
GlobalSign has designed, developed and patented OneClickSSLŌäó, a revolutionary technology that simplifies the process from SSL application to installation with levels of automation previously considered impossible ŌĆō eliminating support fees and minimizing time spent supporting customers.
Learn how the OneClickSSL technology works, the deployment options and use cases and how to generate new revenues with OneClickSSL.#Morecrypto (with tis) - version 2.2



#Morecrypto (with tis) - version 2.2Olle E Johansson
╠²
This document discusses the importance of using more encryption on the Internet to increase privacy and security. It makes the following key points:
1) The Internet has become too easy to monitor as we have built it without sufficient security protections by default. More encryption needs to be implemented across Internet services and protocols to make eavesdropping more difficult.
2) Developers should enable encryption by default for all new Internet protocols. Opportunistic encryption techniques can provide some protections even without full authentication.
3) Individuals can help push for more encryption by requiring encrypted connections when using services and enabling tools like HTTPS Everywhere on their browsers. Transitioning to encrypted connections wherever possible raises the bar for surveillance.SSLtalk



SSLtalkMatthew Aylard
╠²
The document discusses the history and purpose of TLS/SSL, including how it uses asymmetric and symmetric cryptography. It describes how TLS/SSL works, including the handshake and record layers, cipher suites, and public key infrastructure (PKI). It notes that TLS/SSL secures communications between applications and transport layers in the OSI model. Examples of exploits like session hijacking and man-in-the-middle attacks are provided to illustrate the importance of encryption.Secure Sockets Layer and Transport Layer Security



Secure Sockets Layer and Transport Layer SecurityAl Mamun
╠²
Transport Layer Security and its predecessor, Secure Sockets Layer, are cryptographic protocols that provide communications security over a computer network.What is SSL ? The Secure Sockets Layer (SSL) Protocol



What is SSL ? The Secure Sockets Layer (SSL) ProtocolMohammed Adam
╠²
SSL is a protocol that allows clients and servers to securely communicate over the internet. It uses public-key encryption to authenticate servers, optionally authenticate clients, and establish an encrypted connection to securely transmit data. The SSL handshake allows the client and server to negotiate encryption parameters to generate shared secrets and session keys, which are then used to encrypt all further communication during the SSL session. Common implementations of SSL include OpenSSL and Apache-SSL.Report on Heartbleed



Report on HeartbleedShiva Sagar
╠²
Day by day as the complexity in the Internet increasing the vulnerabilities about the security is also increasing. So the knowledge about these flaws has to be spread. So this report discuss about the one of the vulnerability that exists for a long time called ŌĆśHeartbleedŌĆÖ. The purpose of this report is to create awareness about the Heartbleed vulnerability in OpenSSL Library, using which attackers can get access to passwords, private keys or any encrypted data. It explains how Heartbleed works, what code causes data leakage and explains the resolution with code fix. It also explains perform how to perform heartbeat attack.Vulnerabilities of the SSL/TLS Protocol



Vulnerabilities of the SSL/TLS Protocolcsandit
╠²
This paper analyzes vulnerabilities of the SSL/TLS
Handshake
protocol
, which
is
responsible
for
authentication of
the parties in the
communication
and
negotiation of
security parameters
that
will be used
to protect
confidentiality and
integrity of the
data
. It
will
be
analyzed the
attacks
against the implementation of Handshake
protocol, as well as the
attacks against the other
elements
necessary to SSL/TLS protocol to discover security
flaws that were exploited, modes of
attack, the potential consequences, but also studyi
ng methods of defense
.
All versions of the
protocol are going to be the subject of the researc
h but
emphasis will be placed
on the critical
attack that
the most endanger the safety of data.
The goal of
the research
is
to point out the
danger of
existence
of at least
vulnerability
in the SSL/TLS protocol
, which
can be exploited
and
endanger the safety of
the data
that should be protected. VULNERABILITIES OF THE SSL/TLS PROTOCOL



VULNERABILITIES OF THE SSL/TLS PROTOCOLcscpconf
╠²
This paper analyzes vulnerabilities of the SSL/TLS Handshake protocol, which is responsible for authentication of the parties in the communication and negotiation of security parameters that will be used to protect confidentiality and integrity of the data. It will be analyzed the attacks against the implementation of Handshake protocol, as well as the attacks against the other
elements necessary to SSL/TLS protocol to discover security flaws that were exploited, modes of
attack, the potential consequences, but also studying methods of defense. All versions of the
protocol are going to be the subject of the research but emphasis will be placed on the critical attack that the most endanger the safety of data. The goal of the research is to point out the
danger of existence of at least vulnerability in the SSL/TLS protocol, which can be exploited and endanger the safety of the data that should be protected.
Explain how SSL protocol is used to ensure the confidentiality and int.docx



Explain how SSL protocol is used to ensure the confidentiality and int.docxtodd401
╠²
Explain how SSL protocol is used to ensure the confidentiality and integrity of the Internet traffic.
Solution
SSL uses a combination of public-key and symmetric-key encryption to secure a connection between two machines, typically a Web or mail server and a client machine, communicating over the Internet or an internal network.
Using the OSI reference model as context, SSL runs above the TCP/IP protocol, which is responsible for the transport and routing of data over a network, and below higher-level protocols such as HTTP and IMAP, encrypting the data of network connections in the application layer of the Internet Protocol suite. The \"sockets\" part of the term refers to the sockets method of passing data back and forth between a client and a server program in a network, or between program layers in the same computer.
The Transport Layer Security (TLS) protocol evolved from SSL and has largely superseded it, although the terms SSL or SSL/TLS are still commonly used; SSL is often used to refer to what is actually TLS. The combination of SSL/TLS is the most widely deployed security protocol used today and is found in applications such as Web browsers, email and basically any situation where data needs to be securely exchanged over a network, like file transfers, VPN connections, instant messaging and voice over IP.
The SSL protocol includes two sub-protocols: the record protocol and the \"handshake\" protocol. These protocols allow a client to authenticate a server and establish an encrypted SSL connection. In what\'s referred to as the \"initial handshake process,\" a server that supports SSL presents its digital certificate to the client to authenticate the server\'s identity. Server certificates follow the X.509 certificate format that is defined by the Public-Key Cryptography Standards (PKCS). The authentication process uses public-key encryption to validate the digital certificate and confirm that a server is in fact the server it claims to be.
Once the server has been authenticated, the client and server establish cipher settings and a shared key to encrypt the information they exchange during the remainder of the session. This provides data confidentiality and integrity. This whole process is invisible to the user.
For example, if a webpage requires an SSL connection, the URL will change from HTTP to HTTPS and a padlock icon appears in the browser once the server has been authenticated.
The handshake also allows the client to authenticate itself to the server. In this case, after server authentication is successfully completed, the client must present its certificate to the server to authenticate the client\'s identity before the encrypted SSL session can be established.
.ENCRYPTION.pptx



ENCRYPTION.pptxabbu03oct
╠²
Encryption is a technique used to protect data and transmissions by encoding them in a way that only authorized parties can access. There are two main types: symmetric encryption uses a single secret key for encryption and decryption, while asymmetric encryption uses two keys - a public key to encrypt and a private key to decrypt. Symmetric encryption is faster but less secure as it relies on secure key exchange, while asymmetric encryption uses separate keys and is more secure though computationally slower. Digital certificates verify the identity of websites, machines, or devices and are issued by certificate authorities to facilitate secure transactions online.OpenSSL



OpenSSLTimbal Mayank
╠²
SSL and certificates exist to provide encryption and identification for secure communication between web servers and clients. OpenSSL is a cryptography library and toolkit that implements the SSL and TLS protocols, providing encryption through different ciphers and algorithms. It is widely used by over 60% of web servers to generate private keys, certificate signing requests, and perform encryption and decryption as well as manage certificates.secure socket layer



secure socket layerAmar Shah
╠²
SSL and TLS are cryptographic protocols that provide secure communication on the internet. They use public/private key encryption to authenticate servers and establish encrypted connections. While similar, TLS is the standardized successor to SSL. Key differences include TLS using HMAC for integrity checking and having additional alert codes not found in SSL. Both protocols operate at the transport layer and provide data confidentiality, integrity, and server authentication.Details about the SSL Certificate



Details about the SSL CertificateCheapSSLUSA
╠²
In this Pdf,you can know about the SSL certificate.
Who use SSL Certificate?
How it works.?
all this questions solution is in this pdf.Recently uploaded (20)
Web Design Creating User-Friendly and Visually Engaging Websites - April 2025...



Web Design Creating User-Friendly and Visually Engaging Websites - April 2025...TheoRuby
╠²
Website design for small business owners looking at wordpress and elementor pro and covering all areas of design including UX and storytelling!
Dehydrated Fruits and Vegetables Market: Healthy Convenience & Long Shelf Life



Dehydrated Fruits and Vegetables Market: Healthy Convenience & Long Shelf Lifechanderdeepseoexpert
╠²
Explore the Dehydrated Fruits and Vegetables Market, driven by growing demand for healthy, convenient, and shelf-stable food options. Ideal for snacks, ready meals, and emergency supplies, these products offer nutritional value and extended storage life. Key trends include clean-label products, innovative drying technologies, and rising health consciousness among consumers worldwide.Solaris Resources Presentation - Corporate April 2025.pdf



Solaris Resources Presentation - Corporate April 2025.pdfpchambers2
╠²
Solaris Resources Corporate PresentationSupply Chain Management decision making .pptx



Supply Chain Management decision making .pptxWezaWeza1
╠²
Supply Chain Management decision making .pptxąÆąĖą║ą╗ąĖą║ąĖ ą┐čĆąŠą│čĆą░ą╝ąĮąŠą│ąŠ čéą░ ą┐ąŠčĆčéč乥ą╗čīąĮąŠą│ąŠ ą╝ąĄąĮąĄą┤ąČą╝ąĄąĮčéčā: čÅą║ čŚčģ ą┤ąŠą╗ą░čéąĖ | ąÆąĄą▒č¢ąĮą░čĆ



ąÆąĖą║ą╗ąĖą║ąĖ ą┐čĆąŠą│čĆą░ą╝ąĮąŠą│ąŠ čéą░ ą┐ąŠčĆčéč乥ą╗čīąĮąŠą│ąŠ ą╝ąĄąĮąĄą┤ąČą╝ąĄąĮčéčā: čÅą║ čŚčģ ą┤ąŠą╗ą░čéąĖ | ąÆąĄą▒č¢ąĮą░čĆE-5
╠²
ąĢč乥ą║čéąĖą▓ąĮąĄ čāą┐čĆą░ą▓ą╗č¢ąĮąĮčÅ ą┐čĆąŠą│čĆą░ą╝ą░ą╝ąĖ čéą░ ą┐ąŠčĆčéč乥ą╗ąĄą╝ ą┐čĆąŠčöą║čéč¢ą▓ ŌĆō ą║ą╗čÄčć ą┤ąŠ čüčéą░ą▒č¢ą╗čīąĮąŠčüčéč¢ čéą░ ąĘčĆąŠčüčéą░ąĮąĮčÅ ą▒č¢ąĘąĮąĄčüčā. ą¤čĆąŠč鹥 ą▓ čāą╝ąŠą▓ą░čģ čüčéčĆč¢ą╝ą║ąĖčģ ąĘą╝č¢ąĮ č¢ ąŠą▒ą╝ąĄąČąĄąĮąĖčģ čĆąĄčüčāčĆčüč¢ą▓ čåąĄą╣ ą┐čĆąŠčåąĄčü čüčéą░čö ą┤ąĄą┤ą░ą╗č¢ čüą║ą╗ą░ą┤ąĮč¢čłąĖą╝. ąÜąĄčĆč¢ą▓ąĮąĖą║ą░ą╝ ąĮąĄąŠą▒čģč¢ą┤ąĮąŠ ą▓čĆą░čģąŠą▓čāą▓ą░čéąĖ ą▒ąĄąĘą╗č¢čć čäą░ą║č鹊čĆč¢ą▓: čüčéčĆą░č鹥ą│č¢čćąĮč¢ ą┐čĆč¢ąŠčĆąĖč鹥čéąĖ, čĆąĖąĘąĖą║ąĖ, čäč¢ąĮą░ąĮčüąŠą▓č¢ ąŠą▒ą╝ąĄąČąĄąĮąĮčÅ čéą░ ą┐ąŠčéčĆąĄą▒ąĖ ą║ąŠą╝ą░ąĮą┤ąĖ.
ąóąŠą╝čā ą╝ąĖ čüčéą▓ąŠčĆąĖą╗ąĖ čåąĄą╣ ą▓ąĄą▒č¢ąĮą░čĆ, čēąŠą▒ ą┤ąŠą┐ąŠą╝ąŠą│čéąĖ ą║ąĄčĆč¢ą▓ąĮąĖą║ą░ą╝ ą┐čĆąŠą│čĆą░ą╝ č¢ ą┐ąŠčĆčéč乥ą╗č¢ą▓ ą┐čĆąŠčöą║čéč¢ą▓ ą┤ąŠą╗ą░čéąĖ ą║ą╗čÄč湊ą▓č¢ ą▓ąĖą║ą╗ąĖą║ąĖ, ąŠą┐čéąĖą╝č¢ąĘčāą▓ą░čéąĖ čāą┐čĆą░ą▓ą╗č¢ąĮčüčīą║č¢ ą┐čĆąŠčåąĄčüąĖ čéą░ ąĘąĮą░čģąŠą┤ąĖčéąĖ ąĄč乥ą║čéąĖą▓ąĮč¢ čĆč¢čłąĄąĮąĮčÅ ąĮą░ ąŠčüąĮąŠą▓č¢ čĆąĄą░ą╗čīąĮąĖčģ ą║ąĄą╣čüč¢ą▓.
ą¤č¢ą┤ čćą░čü ą▓ąĄą▒č¢ąĮą░čĆčā čĆąŠąĘą│ą╗čÅąĮčāą╗ąĖ ąĮą░ą╣ą┐ąŠčłąĖčĆąĄąĮč¢čłč¢ čéčĆčāą┤ąĮąŠčēč¢, ąĮą░ ąŠčüąĮąŠą▓č¢ ą░ąĮą░ą╗č¢ąĘčā ą┐čĆą░ą║čéąĖčćąĮąĖčģ ą║ąĄą╣čüč¢ą▓ čéą░ ą┐čĆąĄą┤čüčéą░ą▓ąĖą╝ąŠ ą┐ąĄčĆąĄą▓č¢čĆąĄąĮč¢ ą┐č¢ą┤čģąŠą┤ąĖ, čÅą║č¢ ą┤ąŠąĘą▓ąŠą╗čÅčéčī ą┐č¢ą┤ą▓ąĖčēąĖčéąĖ ąĄč乥ą║čéąĖą▓ąĮč¢čüčéčī čāą┐čĆą░ą▓ą╗č¢ąĮąĮčÅ.
ą®ąŠ čĆąŠąĘč¢ą▒čĆą░ą╗ąĖ ąĮą░ ą▓ąĄą▒č¢ąĮą░čĆč¢?
¤ōī ą×čüąĮąŠą▓ąĮč¢ čéčĆčāą┤ąĮąŠčēč¢ ą┐čĆąŠą│čĆą░ą╝ąĮąŠą│ąŠ čéą░ ą┐ąŠčĆčéč乥ą╗čīąĮąŠą│ąŠ ą╝ąĄąĮąĄą┤ąČą╝ąĄąĮčéčā: ąĮąĄą▓ąĖąĘąĮą░č湥ąĮč¢čüčéčī, ą┐čĆč¢ąŠčĆąĖč鹥čéąĖ, ąŠą▒ą╝ąĄąČąĄąĮč¢ čĆąĄčüčāčĆčüąĖ č鹊čēąŠ
¤ōī ąĀąĄą░ą╗čīąĮč¢ ą║ąĄą╣čüąĖ ąĘ ą▒č¢ąĘąĮąĄčü-ą┐čĆą░ą║čéąĖą║ąĖ: ą░ąĮą░ą╗č¢ąĘ ą┐ąŠą╝ąĖą╗ąŠą║ č¢ čāčüą┐č¢čłąĮąĖčģ čĆč¢čłąĄąĮčī
¤ōī ąåąĮčüčéčĆčāą╝ąĄąĮčéąĖ čéą░ ą╝ąĄč鹊ą┤ąĖą║ąĖ, čēąŠ ą┤ąŠą┐ąŠą╝ą░ą│ą░čÄčéčī ą┐ąŠą║čĆą░čēąĖčéąĖ čāą┐čĆą░ą▓ą╗č¢ąĮąĮčÅ ą┐čĆąŠą│čĆą░ą╝ą░ą╝ąĖ čéą░ ą┐ąŠčĆčéč乥ą╗čÅą╝ąĖ
ąÆąĄą▒č¢ąĮą░čĆ ą▒čāą┤ąĄ ą║ąŠčĆąĖčüąĮąĖą╝ ą┤ą╗čÅ ą║ąĄčĆč¢ą▓ąĮąĖą║č¢ą▓ ą┐čĆąŠą│čĆą░ą╝ č¢ ą┐ąŠčĆčéč乥ą╗č¢ą▓, ą┐čĆąŠčöą║čéąĮąĖčģ ą╝ąĄąĮąĄą┤ąČąĄčĆč¢ą▓, ą╗č¢ą┤ąĄčĆč¢ą▓ ą║ąŠą╝ą░ąĮą┤ čéą░ čüčéčĆą░č鹥ą│č¢čćąĮąĖčģ čāą┐čĆą░ą▓ą╗č¢ąĮčåč¢ą▓, čÅą║č¢ ą┐čĆą░ą│ąĮčāčéčī ą┐č¢ą┤ą▓ąĖčēąĖčéąĖ ąĄč乥ą║čéąĖą▓ąĮč¢čüčéčī čüą▓ąŠčöčŚ čĆąŠą▒ąŠčéąĖ.
¤ōī ąĪą┐č¢ą║ąĄčĆą║ą░:
ą£ą░čĆč¢čÅ ą©ą▓ąĄčåčī
Senior Director | EPAM Systems
Director, Head of Consulting and Process Management, PMO @Intellias
PM & Agile mentor, ICAgile Authorized instructor
ą¤ąŠąĮą░ą┤ 12 čĆąŠą║č¢ą▓ ą┤ąŠčüą▓č¢ą┤čā ą▓ ąåąó-č¢ąĮą┤čāčüčéčĆč¢čŚ, ąĘ ąĮąĖčģ 9+ čĆąŠą║č¢ą▓ ą▓ čāą┐čĆą░ą▓ą╗č¢ąĮąĮč¢ ą┐čĆąŠčöą║čéą░ą╝ąĖ, ą┐ąŠčĆčéč乥ą╗čÅą╝ąĖ čéą░ ą┐čĆąŠą│čĆą░ą╝ą░ą╝ąĖ
ąóą░ ą▓ąČąĄ ą┐ąŠąĮą░ą┤ 8 čĆąŠą║č¢ą▓ ąĮą░ą▓čćą░čö čéą░ ą║ąŠąĮčüčāą╗čīčéčāčö ąĘ č鹥ą╝ čāą┐čĆą░ą▓ą╗č¢ąĮąĮčÅ ą┐čĆąŠčöą║čéą░ą╝ąĖ čéą░ Agile
ą£ą░čö ą┤ąŠčüą▓č¢ą┤ čāą┐čĆą░ą▓ą╗č¢ąĮąĮčÅ ąĮą░ čĆč¢ąĘąĮąĖčģ ą┐ąŠąĘąĖčåč¢čÅčģ, ąĘąŠą║čĆąĄą╝ą░ Project/Program/Portfolio/Delivery Manager, ą░ čéą░ą║ąŠąČ PMO Expert/Consultant. ą¤čĆąŠą┤ąĄą╝ąŠąĮčüčéčĆčāą▓ą░ą╗ą░ čāčüą┐č¢čłąĮąĄ ąĘčĆąŠčüčéą░ąĮąĮčÅ ą┐ąŠčĆčéč乊ą╗č¢ąŠ ą┐čĆąŠčöą║čéč¢ą▓ ąĮą░ ą┐ąŠčüą░ą┤č¢ Delivery Director, ąĘą░ą▒ąĄąĘą┐ąĄčćčāčÄčćąĖ ą▓ąĖčüąŠą║čā čÅą║č¢čüčéčī ą▓ąĖą║ąŠąĮą░ąĮąĮčÅ ą▓ čéč¢čüąĮč¢ą╣ čüą┐č¢ą▓ą┐čĆą░čåč¢ ąĘ ą║ąŠą╝ą░ąĮą┤ąŠčÄ čéą░ ą┐čĆąŠčÅą▓ą╗čÅčÄčćąĖ č¢ąĮąĮąŠą▓ą░čåč¢ą╣ąĮč¢čüčéčī čéą░ ą┐čĆąŠą░ą║čéąĖą▓ąĮč¢čüčéčī čā čĆąŠąĘčĆąŠą▒čåč¢ čĆč¢čłąĄąĮčī.
ąŚą░čģąŠą┐ą╗čÄčöčéčīčüčÅ ą▓čüč¢ą╝ą░ ą░čüą┐ąĄą║čéą░ą╝ąĖ čüą▓ąŠčöčŚ čĆąŠą▒ąŠčéąĖ ŌĆō ą▓č¢ą┤ ą║ąĄčĆčāą▓ą░ąĮąĮčÅ ą┤ąĖąĮą░ą╝č¢čćąĮąĖą╝ąĖ ą┐čĆąŠčöą║čéą░ą╝ąĖ čĆą░ąĘąŠą╝ č¢ąĘ ą║ąŠą╝ą░ąĮą┤ąŠčÄ čéą░ čüą┐č¢ą▓ą┐čĆą░čåč¢ ąĘ čéą░ą╗ą░ąĮąŠą▓ąĖčéąĖą╝ąĖ čäą░čģč¢ą▓čåčÅą╝ąĖ ą┤ąŠ ą┐ąŠčüčéč¢ą╣ąĮąŠą│ąŠ ą▓č¢ą┤čüč鹥ąČąĄąĮąĮčÅ č鹥čģąĮąŠą╗ąŠą│č¢čćąĮąĖčģ č鹥ąĮą┤ąĄąĮčåč¢ą╣ č¢ ą┐ą░čĆčéąĮąĄčĆčüčéą▓ą░ ąĘ ą║ą╗č¢čöąĮčéą░ą╝ąĖ ą┤ą╗čÅ ą┤ąŠčüčÅą│ąĮąĄąĮąĮčÅ čŚčģąĮčīąŠą│ąŠ čāčüą┐č¢čģčā.Selec Controls Pvt. Ltd. Line Card FY2025-26.pdf



Selec Controls Pvt. Ltd. Line Card FY2025-26.pdfSelec Controls
╠²
Selec Controls is leading the nation with Innovative Solutions!
¤īŹ Global Presence: Sales Subsidiaries in Europe, Australia, and the USA.
¤īÉ Exports to 75+ Countries.
¤ÅŁ Manufacturing 4 Million Products Annually in India.
¤ö¦ Highly Automated Inhouse Manufacturing Processes with 14 SMT Lines.
¤Åó Facilities spread over 1.80 Lakh sq. ft. area.
¤ÜĆ Commitment to Quality & Customer-Centric Solutions.
Proudly Contributing to nation-building by nurturing the engineering ecosystem in India!
Discover cutting-edge solutions with Selec Controls. Check out our Line card to know more.
Selec Controls Pvt. Ltd. is an Indian manufacturer and a global supplier of high-quality, innovative products for Electrical Measurement, Power Quality, Industrial Automation, Process Control, Solar, and Electrical Protection & control. It is best known for innovation and the excellent value its products give to customers.
Since its foundation, Selec has become the market leader for Timers, Counters, and Temperature Controllers in India and has been offering a wide range of products like Digital Panel Meters, Relays, Current Transformers, APFCs, PID/Temperature Controllers, Process Indicators, Timers, Counters, Time Totalizers, and PLCs, Power Supplies that are CE and UL certified.
Along the way, we've expanded into new technologies like EMS - IoT for energy management and MiBRX, our patented micro-modular PLC solution. Recently, we've introduced indigenously developed products, including Advanced Static VAr Generator, Static Voltage Regulators, Solar On-grid Inverters, Wi-Fi Enabled multifunction meters, Humidity controllers, and universal PID controllers.
Let us discover cutting-edge solutions with Selec Controls. Your partner for innovation and excellence!Viktor Svystunov: Your Team Can Do More (UA)



Viktor Svystunov: Your Team Can Do More (UA)Lviv Startup Club
╠²
Viktor Svystunov: Your Team Can Do More (UA)
UA Online PMDay 2025 Spring
Website ŌĆō https://pmday.org/online
Youtube ŌĆō https://www.youtube.com/startuplviv
FB ŌĆō https://www.facebook.com/pmdayconferencecompany/organization/personal branding guide



company/organization/personal branding guideShahnewazAhmed7
╠²
This is a sample brand guide. Any person or company looking for a sample brand guide can use this sample as guideline. However no one can not completely copy this.TNR Gold Shotgun Gold Project Presentation



TNR Gold Shotgun Gold Project PresentationKirill Klip
╠²
Gold in the USA, the Alaskan Elephant Country: TNR Gold Shotgun Gold Project Presentation Vietnam retail store (Modern Trade) trend 2025



Vietnam retail store (Modern Trade) trend 2025A2Z Marketing
╠²
Kh├Īm ph├Ī to├Ān cß║Żnh xu hŲ░ß╗øng k├¬nh b├Īn lß║╗ hiß╗ćn ─æß║Īi tß║Īi Viß╗ćt Nam 2025 qua sß╗æ liß╗ću mß╗øi nhß║źt: t─āng trŲ░ß╗¤ng, chuyß╗ān dß╗ŗch & chiß║┐n lŲ░ß╗Żc thŲ░ŲĪng hiß╗ću.Tax Credits Turn Tax Season into Saving Season.pdf



Tax Credits Turn Tax Season into Saving Season.pdfTax Goddess
╠²
Think tax season is just about paying more? Think again.
Most Americans are missing out on thousands in tax savings simply because they donŌĆÖt know which credits they qualify for. The reality? The IRS offers numerous tax credits designed to support families, workers, students, and even eco-conscious consumersŌĆöand unlike deductions, credits reduce your tax bill dollar-for-dollar.
In this comprehensive guide, youŌĆÖll uncover how to take full advantage of credits like:
Ō£ģ Earned Income Tax Credit (EITC): Up to $7,430 for low-to-moderate income earners. Yet, 1 in 5 eligible taxpayers never claim it.
Ō£ģ Child Tax Credit: Receive up to $2,000 per child under 17ŌĆöa financial boost for over 40 million families each year.
Ō£ģ Education Credits: Whether youŌĆÖre a college student or lifelong learner, you could get up to $2,500 back through the American Opportunity or Lifetime Learning Credit.
Ō£ģ Clean Energy & EV Credits: Thinking green? Solar installation could earn you a 30% credit, while purchasing an electric vehicle may qualify you for up to $7,500.
But it doesnŌĆÖt stop thereŌĆöstrategically planning your purchases, tracking your expenses, and scheduling a mid-year tax checkup can maximize your savings. With the right knowledge, tax season becomes a season of opportunity.
DonŌĆÖt wait until April. Start planning smarter today.
Visit taxgoddess.com and learn how to claim every dollar you deserve.Large language models in business - conceptual changes and examples



Large language models in business - conceptual changes and examplesPeter Trkman
╠²
This presentation, titled ŌĆ£Large Language Models ŌĆō Generative AI as a Game Changer in the Business WorldŌĆØ by Peter Trkman, is an insightful and multifaceted exploration of how generative artificial intelligence (GAI), particularly large language models (LLMs), are transforming business practices, professional roles, and communication.
The presentation starts with a personal introduction, balancing professional credibility and a touch of humor to humanize the presenter. It then frames GAI not as a future concept but as a present reality, demonstrating through examples how easily and quickly contentŌĆöranging from blog posts to CEO speechesŌĆöcan be generated with minimal effort.
Several concrete examples illustrate how AI tools can write, code, analyze, and visualize, making tasks faster and more efficient. These examples are not generic; they are tailored, practical, and created in seconds, reinforcing the message that the AI revolution isnŌĆÖt upcomingŌĆöitŌĆÖs already here. Notably, the slides highlight AI's role in financial reporting, mutual fund advising, and internal corporate communication, each with full examples showing how GAI adds value.
An important conceptual shift is emphasized: content creation is no longer a differentiator because AI makes it cheap and easy. The real challenge becomes recognizing where human creativity, empathy, and judgment are still irreplaceableŌĆöwhat the presentation calls the ŌĆ£power of human steps in a digital world.ŌĆØ
The slides also include elements of comedy, including stand-up routines about the speaker, reinforcing the idea that humor, personality, and emotion are still human domains where AI struggles.
Throughout, the message is not alarmist but strategic. The presentation encourages participants to:
Recognize the limits of AI (ŌĆ£What GAI wonŌĆÖt doŌĆØ),
Focus on sectors and processes most affected by AI (e.g., content creation, customer interaction),
Develop AI-compatible and AI-optimized processes and texts (like AIO vs SEO),
Cultivate critical human skills such as communication, creativity, and empathy,
Avoid hype unless it has marketing value.
The conclusion stresses the need for authenticity in communicationŌĆöemphasizing that while GAI can generate professional-looking content, real impact comes from short, heartfelt, human messages. The final takeaway is a philosophical yet practical appeal: use AI for efficiency, but donŌĆÖt lose sight of humanity, especially in meaningful interactions.
In sum, this presentation is both a practical guide and a conceptual reflection on how to navigate the present and future shaped by generative AI. It provides a balanced, humorous, and deeply insightful roadmap for professionals and organizations aiming to leverage LLMs meaningfully and ethically.Picture Archiving and Communication System (PACS) Market Size & Insights (202...



Picture Archiving and Communication System (PACS) Market Size & Insights (202...janewatson684
╠²
The global picture archiving and communication system (PACS) market size attained a value of USD 5.29 Billion in 2024. The market is anticipated to grow at a CAGR of 5.70% during the forecast period of 2025-2034 to attain a value of USD 9.21 Billion by 2034.AlaskaSilver Corporate Presentation Apr 28 2025.pdf



AlaskaSilver Corporate Presentation Apr 28 2025.pdfWestern Alaska Minerals Corp.
╠²
Alaska Silver: Developing Critical Minerals & High-Grade Silver Resources
Alaska Silver is advancing a prolific 8-km mineral corridor hosting two significant deposits. Our flagship high-grade silver deposit at Waterpump Creek, which contains gallium (the U.S. #1 critical mineral), and the historic Illinois Creek mine anchor our 100% owned carbonate replacement system across an expansive, underexplored landscape.
Waterpump Creek: 75 Moz @ 980 g/t AgEq (Inferred), open for expansion north and south
Illinois Creek: 525 Koz AuEq - 373 Koz @ 1.3 g/t AuEq (Indicated), 152 Koz @ 1.44 g/t AuEq (Inferred)
2024 "Warm Springs" Discovery: First copper, gold, and Waterpump Creek-grade silver intercepts 0.8 miles from Illinois Creek
2025 Focus: Targeting additional high-grade silver discoveries at Waterpump Creek South and initiating studies on gallium recovery potential.Entrepreneurship: Practicum on Business Plan.ppt



Entrepreneurship: Practicum on Business Plan.pptTribhuvan University
╠²
Dr. Gopal Thapa's ppt based on practicum on business plan especially for Tribhuvan University BBA studentsNetwork Detection and Response (NDR): The Future of Intelligent Cybersecurity



Network Detection and Response (NDR): The Future of Intelligent CybersecurityGauriKale30
╠²
Network Detection and Response (NDR) uses AI and behavioral analytics to detect, analyze, and respond to threats in real time, ensuring comprehensive and automated network security.PARISH SURVEY 2024-25 at St. Agatha-St. James



PARISH SURVEY 2024-25 at St. Agatha-St. Jamesssuser1525f2
╠²
PARISH SURVEY 2024-25 at St. Agatha-St. JamesDehydrated Fruits and Vegetables Market: Healthy Convenience & Long Shelf Life



Dehydrated Fruits and Vegetables Market: Healthy Convenience & Long Shelf Lifechanderdeepseoexpert
╠²
ąÆąĖą║ą╗ąĖą║ąĖ ą┐čĆąŠą│čĆą░ą╝ąĮąŠą│ąŠ čéą░ ą┐ąŠčĆčéč乥ą╗čīąĮąŠą│ąŠ ą╝ąĄąĮąĄą┤ąČą╝ąĄąĮčéčā: čÅą║ čŚčģ ą┤ąŠą╗ą░čéąĖ | ąÆąĄą▒č¢ąĮą░čĆ



ąÆąĖą║ą╗ąĖą║ąĖ ą┐čĆąŠą│čĆą░ą╝ąĮąŠą│ąŠ čéą░ ą┐ąŠčĆčéč乥ą╗čīąĮąŠą│ąŠ ą╝ąĄąĮąĄą┤ąČą╝ąĄąĮčéčā: čÅą║ čŚčģ ą┤ąŠą╗ą░čéąĖ | ąÆąĄą▒č¢ąĮą░čĆE-5
╠²
Differences to Know Between SSL & TLS certificate .pdf
- 1. Differences to Know Between SSL & TLS Certificates Have you ever wondered what the difference is between TLS and SSL? or Are they just the same thing with different names? Both TLS and SSL are cryptographic protocols that authenticate data transfer between servers, systems, applications, and users. But they still have differences. Just like a cappuccino is different from Espresso, they may come from the same coffee bean, but there are differences we must respect. Their work is similar; they both encrypt the data exchanged between a web server and a user, but they are still different from each other on many levels. SSL was a first-of-its-kind cryptographic protocol, whereas TLS is relatively new and more of an upgraded version of SSL.
- 2. We need SSL/TLS certificates to ensure security from Cybercrimes, which have become a very common threat on the internet. The risk of data theft is the highest when its exchanged through client and server systems. SSL/TLS certificates tackle this issue by ensuring a secure exchange. LetŌĆÖs learn more about SSL and TLS certificates. What is SSL? SSL was first developed by Netscape in the year 1994; its main function was to ensure secure communication between client and server systems on the web. Eventually, it was standardized by IETF (the Internet Engineering Task Force) as a protocol. Since then, two versions of SSL have been rolled out by Netscape, which fixed the flaws of the first version. Currently, SSL 3.0 is in use. SSL is a cryptographic protocol that uses explicit connections to establish secure communication between a web server and a client. Also Read: 9 Types Of SSL Certificates ŌĆō Make The Right Choice What is TLS? TLS stands for Transport Layer Security. It is a successor to SSL 3.0 and was first released in 1999 by the Internet Engineering Task Force. TSL v1.1 was released in 2008; it added protection against CBC (Cipher Block chaining) attacks. TSL v1.0 and TLS v1.1 were deprecated by Google, Apple, Microsoft, and Mozilla in 2020. TLS v1.2 was rolled out in 2008. It included some additional features. The latest version of TLS was released in August 2018. It has major features which differentiate it from and makes it better than its previous versions. It is also a cryptographic protocol. It provides secure communication between the web server and the client through implicit connections. It is the successor of the SSL protocol.
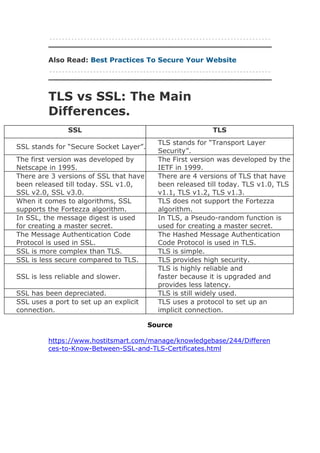
- 3. Also Read: Best Practices To Secure Your Website TLS vs SSL: The Main Differences. Source https://www.hostitsmart.com/manage/knowledgebase/244/Differen ces-to-Know-Between-SSL-and-TLS-Certificates.html SSL TLS SSL stands for ŌĆ£Secure Socket LayerŌĆØ. TLS stands for ŌĆ£Transport Layer SecurityŌĆØ. The first version was developed by Netscape in 1995. The First version was developed by the IETF in 1999. There are 3 versions of SSL that have been released till today. SSL v1.0, SSL v2.0, SSL v3.0. There are 4 versions of TLS that have been released till today. TLS v1.0, TLS v1.1, TLS v1.2, TLS v1.3. When it comes to algorithms, SSL supports the Fortezza algorithm. TLS does not support the Fortezza algorithm. In SSL, the message digest is used for creating a master secret. In TLS, a Pseudo-random function is used for creating a master secret. The Message Authentication Code Protocol is used in SSL. The Hashed Message Authentication Code Protocol is used in TLS. SSL is more complex than TLS. TLS is simple. SSL is less secure compared to TLS. TLS provides high security. SSL is less reliable and slower. TLS is highly reliable and faster because it is upgraded and provides less latency. SSL has been depreciated. TLS is still widely used. SSL uses a port to set up an explicit connection. TLS uses a protocol to set up an implicit connection.




