Secure Sockets Layer and Transport Layer Security
Download as PPT, PDF0 likes608 views
Transport Layer Security and its predecessor, Secure Sockets Layer, are cryptographic protocols that provide communications security over a computer network.
1 of 27
Downloaded 24 times


























Recommended
Transport Layer Security - Mrinal Wadhwa



Transport Layer Security - Mrinal WadhwaMrinal Wadhwa
╠²
The document summarizes the evolution of the Transport Layer Security (TLS) protocol from versions 1.0 to 1.2. It describes the key components of TLS including the record protocol for fragmenting and transmitting encrypted data, handshake protocol for authentication and key exchange, and cipher suites for encryption algorithms. The TLS protocol provides secure communication over the internet by preventing eavesdropping, tampering, and forgery of messages between client and server applications.Transport layer security (tls)



Transport layer security (tls)Kalpesh Kalekar
╠²
Transport Layer Security (TLS) is the successor to Secure Sockets Layer (SSL) and ensures privacy and security between communicating applications on the internet. TLS encrypts data transmission, works with most browsers and servers, supports flexible encryption algorithms, and is easy to deploy on many systems transparently. It operates directly above TCP and establishes an encrypted connection by negotiating a cipher suite and exchanging certificates and keys between the client and server. Once handshake is complete, both sides can communicate securely until closing the connection. TLS version and cipher suite used can be viewed in browser.Transport Layer Security 



Transport Layer Security Ibrahiem Mohammed
╠²
TLS protocol provides transport layer security for internet applications by securing communications between clients and servers. It establishes an encrypted connection through a handshake that negotiates encryption algorithms and authentication, then uses symmetric encryption and message authentication codes to provide confidentiality and integrity for data transfer. TLS has evolved through several versions to strengthen security and address weaknesses in cryptographic algorithms.Ssl and tls



Ssl and tlsRana assad ali
╠²
Transport Layer Security (TLS) is the successor to the Secure Sockets Layer (SSL) protocol. TLS ensures privacy and security between communicating applications and users on the internet by preventing eavesdropping, tampering, and message forgery. It works by having the client and server negotiate a cipher suite and protocol version to use to securely transmit encrypted messages. This establishes a secure channel over an unsecured network like the internet to provide confidentiality, integrity, and authentication of communications.All you need to know about transport layer security



All you need to know about transport layer securityMaarten Smeets
╠²
Many people think that using HTTPS to offer your site or service to clients makes you secure from eavesdroppers and people trying to manipulate your network traffic. Think again! In this presentation I'll dive into transport layer security. I'll elaborate on what you can achieve with SSL such as authentication, encryption and integrity and how you can achieve it. I'll talk about the client-server handshake, identity and trust, one-way and two-way SSL, keys and keystores and cipher suite choice. By means of several examples, I'll show what it can mean if you make the wrong choices in on premises and cloud scenario's. This presentation is relevant for anyone involved in securing connections between client and server using TLS and people interested in learning more about the topic of TLS in general.What is TLS/SSL? 



What is TLS/SSL? Shehzad Imran
╠²
This document provides an overview of Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL). It begins with an introduction to TLS/SSL, explaining what they are and their purposes of providing encryption, authentication and integrity verification. It then discusses digital certificates, the TLS/SSL handshake protocol and record protocol. It explains the four upper layer protocols: record, change cipher spec, alert and handshake. It provides details on SSL, TLS, their implementations and applications. The document is intended to explore how TLS works, best practices for its use, and its various applications in securing business computing.TLS - Transport Layer Security



TLS - Transport Layer SecurityByronKimani
╠²
TLS (Transport Layer Security) is a cryptographic protocol that provides encryption and security for data sent over the internet. It is used by HTTPS to encrypt communication between web browsers and servers. TLS 1.2, the previous standard, had security flaws in how it exchanged encryption keys. TLS 1.3 improves security by using Diffie-Hellman key exchange so keys are not sent directly over the network. To upgrade a website from HTTP to HTTPS, an SSL certificate must be purchased and installed, all links on the site must be changed to HTTPS, and HTTP traffic should be redirected to HTTPS.SSL/TLS Handshake



SSL/TLS HandshakeArpit Agarwal
╠²
This presentation gives a detailed understanding of SSL/TLS handshake and the basic idea of POODLE attackSSL/TLS



SSL/TLSSirish Kumar
╠²
SSL/TLS is a protocol that provides encryption and authentication for web requests. It evolved from earlier SSL versions into the current TLS standard. During a TLS handshake, the client and server agree on encryption parameters and verify certificates from a certificate authority to establish a secure connection. TLS allows for session resumption to reuse encryption settings for subsequent connections via session identifiers or tickets. However, TLS is still vulnerable to man-in-the-middle and DNS hijacking attacks if certificate authorities are compromised.Introduction to SSL and How to Exploit & Secure



Introduction to SSL and How to Exploit & SecureBrian Ritchie
╠²
The document discusses SSL/TLS, how it works to securely transmit data between endpoints, and potential vulnerabilities. It provides an overview of SSL/TLS protocols and how data is encrypted and transmitted. It then outlines several common endpoint issues that can compromise SSL/TLS, such as inconsistent DNS configurations, self-signed certificates, incomplete certificates, and mixing plain text and encrypted sessions. Exploiting these issues allows man-in-the-middle attacks that can intercept and decrypt encrypted traffic.Transport layer security



Transport layer securityHrudya Balachandran
╠²
TLS is an IETF standard similar to SSL that provides cryptographic security and secure connections between parties through the establishment of a secure session. It aims to securely transmit data via record layer encapsulation and encryption, using techniques like cryptographic computations, MACs, and the generation of secrets through pseudorandom functions and data expansion. TLS supports various cipher suites, certificate types, and alert codes while making some changes compared to SSL in areas like record formatting, PRF usage, and handshake messaging.Transport Layer Security (TLS)



Transport Layer Security (TLS)Arun Shukla
╠²
It is an IETF standardization initiative whose goal is to come out with an Internet standard Version of SSL. The presentation discusses all. Happy Learning. :)
Ssl (Secure Sockets Layer)



Ssl (Secure Sockets Layer)Asad Ali
╠²
SSL is an acronym for Secure Sockets Layer. It is a protocol used for authenticating and encrypting web traffic. For web traffic to be authenticated means that your browser is able to verify the identity of the remote server.Transport Layer Security



Transport Layer SecurityChhatra Thapa
╠²
Transport Layer Security (TLS) was designed to provide security at the transport layer and was derived from Secure Sockets Layer (SSL). TLS operates at the transport layer of the internet model and consists of four protocols: the handshake protocol for authentication and key exchange, the change cipher spec protocol for transitioning to the negotiated cryptographic settings, the alert protocol for transmitting error messages, and the record protocol for encapsulation of higher level protocols.SSL overview



SSL overviewTodd Benson (I.T. SPECIALIST and I.T. SECURITY)
╠²
A quick overview of SSL cipher suites, common vulnerabilities associated with them and how to remediate.SSL TLS Protocol



SSL TLS ProtocolDevang Badrakiya
╠²
Brief explanation about TLS and SSL protocol handshake and message exchange process and its describe certificate validation.SSL/TLS Introduction with Practical Examples Including Wireshark Captures



SSL/TLS Introduction with Practical Examples Including Wireshark CapturesJaroslavChmurny
╠²
As some of my colleagues are solving various SSL/TLS problems for one of our customers, I have prepared the above mentioned training for them. The training is divided to three parts:
- Brief Introduction to Public Key Infrastructure (PKI)
- Introduction to SSL/TLS Protocols
- Practical Examples and Hints
The last part primarily consists of hands-on exercises with Wireshark, covering variety of successful and failed SSL/TLS handshakes. The hands-on exercises are based on easily configurable dummy SSL client and server implemented in Java (available at https://github.com/Jardo72/SSL-Sandbox).
SSL/TLS



SSL/TLSDr Anjan Krishnamurthy
╠²
The document discusses SSL/TLS (Secure Sockets Layer/Transport Layer Security), which are cryptographic protocols that provide secure communication over the internet. It covers SSL/TLS concepts like handshaking, encryption, authentication. It also describes JSSE (Java Secure Socket Extension), the Java implementation of SSL/TLS, including its architecture, classes and configuration. The document provides references for further reading on SSL/TLS and JSSE.Secure Socket Layer (SSL)



Secure Socket Layer (SSL)amanchaurasia
╠²
The document presents an overview of Secure Socket Layer (SSL) technology. It discusses how SSL establishes encrypted connections to provide security and integrity. It describes SSL architecture including certificates, hashing, asymmetric and symmetric data transfer, and the SSL handshake process. It also covers encryption algorithms like RC4, AES, Triple DES, and RSA that are used. Finally, it discusses asymmetric key cryptography algorithms like Diffie-Hellman and RSA, as well as symmetric key cryptography and the future scope of encryption standards.Securing TCP connections using SSL



Securing TCP connections using SSLSagar Mali
╠²
Securing TCP connections using SSL
Originally developed by Netscape
Communications to allow secure access of a
browser to a Web server, Secure Sockets
Layer (SSL) has become the accepted
standard for Web security.1 The first version
of SSL was never released because of
problems regarding protection of credit
card transactions on the Web. In 1994,
Netscape created SSLv2, which made it
possible to keep credit card numbers
confidential and also authenticate the Web
server with the use of encryption and digital
certificates. In 1995, Netscape strengthened
the cryptographic algorithms and resolved
many of the security problems in SSLv2
with the release of SSLv3. SSLv3 now
supports more security algorithms
than SSLv2.SSL



SSLtheekuchi
╠²
TLS (Transport Layer Security) is a protocol that provides secure communication over the Internet by addressing issues of privacy, integrity, and authentication. It uses encryption to ensure privacy, message authentication codes to ensure integrity, and X.509 certificates to perform authentication between clients and servers. TLS is commonly used with HTTPS to secure web browsing and can also be used by other applications like email, voice over IP, and file transfer.Secure Socket Layer



Secure Socket LayerPina Parmar
╠²
SSL uses TCP to provide a secure end-to-end service. It consists of two layers - the SSL record protocol and the SSL handshake protocol. The record protocol provides data encryption and integrity checking, while the handshake protocol allows the server and client to authenticate each other and negotiate encryption parameters for the secure connection.SSL Secure socket layer



SSL Secure socket layerAhmed Elnaggar
╠²
The document provides an overview of the Secure Sockets Layer (SSL) protocol. It discusses SSL's goals of providing confidentiality, integrity, and authentication for network communications. It describes the SSL handshake process, where the client and server authenticate each other and negotiate encryption parameters before transmitting application data. It also discusses SSL applications like securing web traffic and online payments. The document concludes that SSL is vital for web security and ensures user confidentiality and integrity.Transport Layer Security



Transport Layer SecurityHuda Seyam
╠²
Added security measures needed we will see TLS (Transport Layer Security)
HTTPS Secure HTTP protocolSecure socket layer



Secure socket layerNishant Pahad
╠²
SSL is a secure protocol that runs above TCP/IP and allows users to encrypt data and authenticate server and client identities securely. It uses public key encryption to generate a shared secret and establish an encrypted connection. The SSL handshake process verifies the server's identity and allows the client and server to agree on encryption algorithms before exchanging data. This helps prevent man-in-the-middle attacks by authenticating servers and encrypting the connection.Ssl in a nutshell



Ssl in a nutshellFrank Kelly
╠²
SSL provides encryption and authentication for secure communication over networks. It uses certificates signed by a certificate authority to authenticate servers and establish an encrypted connection. The SSL handshake process involves the client sending a pre-master secret encrypted with the server's public key, both sides then derive encryption keys to encrypt the connection. Debugging SSL issues may require using tools like tcpdump to monitor network traffic or adding debug flags to examine the SSL handshake.secure socket layer



secure socket layerAmar Shah
╠²
SSL and TLS are cryptographic protocols that provide secure communication on the internet. They use public/private key encryption to authenticate servers and establish encrypted connections. While similar, TLS is the standardized successor to SSL. Key differences include TLS using HMAC for integrity checking and having additional alert codes not found in SSL. Both protocols operate at the transport layer and provide data confidentiality, integrity, and server authentication.Secure Socket Layer



Secure Socket LayerAbhishek Gupta
╠²
Secure Socket Layer (SSL) was first proposed and used by Netscape to transmit sensitive data over the internet by encapsulating it in a session on top of the TCP layer. SSL aims to authenticate parties, ensure data integrity, and maintain data privacy. Certain websites can only be accessed through SSL-enabled client software. SSL establishes an association between a client and server by authenticating them and then exchanging and encrypting data using suitable algorithms to keep the information secret. SSL has two layers - the record protocol, which handles data encryption, integrity, and encapsulation, and several subprotocols like the alert, change cipher spec, and handshake protocols, which initiate and negotiate secure sessions.Comparative Analysis of Open-SSL Vulnerabilities & Heartbleed Exploit Detection



Comparative Analysis of Open-SSL Vulnerabilities & Heartbleed Exploit DetectionCSCJournals
╠²
Since its introduction in 1994 the Secure Socket Layer (SSL) protocol (later renamed to Transport Layer Security (TLS)) evolved to the de facto standard for securing the transport layer. SSL/TLS can be used for ensuring data confidentiality, integrity and authenticity during transport. A main feature of the protocol is its flexibility. Modes of operation and security aims can easily be configured through different cipher suites. During its evolutionary development process several flaws were found. However, the flexible architecture of SSL/TLS allowed efficient fixes in order to counter the issues. This paper presents an overview on theoretical and practical attacks of the last 20 years.Sequere socket Layer



Sequere socket LayerRaghavendra Rao
╠²
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that provide secure communication over the internet. They allow for confidentiality, integrity, and authentication between two applications communicating over TCP. SSL/TLS works by encrypting the segments of TCP connections above the transport layer through the use of symmetric and asymmetric cryptography. It establishes a secure channel over an insecure network such as the internet.More Related Content
What's hot (20)
SSL/TLS



SSL/TLSSirish Kumar
╠²
SSL/TLS is a protocol that provides encryption and authentication for web requests. It evolved from earlier SSL versions into the current TLS standard. During a TLS handshake, the client and server agree on encryption parameters and verify certificates from a certificate authority to establish a secure connection. TLS allows for session resumption to reuse encryption settings for subsequent connections via session identifiers or tickets. However, TLS is still vulnerable to man-in-the-middle and DNS hijacking attacks if certificate authorities are compromised.Introduction to SSL and How to Exploit & Secure



Introduction to SSL and How to Exploit & SecureBrian Ritchie
╠²
The document discusses SSL/TLS, how it works to securely transmit data between endpoints, and potential vulnerabilities. It provides an overview of SSL/TLS protocols and how data is encrypted and transmitted. It then outlines several common endpoint issues that can compromise SSL/TLS, such as inconsistent DNS configurations, self-signed certificates, incomplete certificates, and mixing plain text and encrypted sessions. Exploiting these issues allows man-in-the-middle attacks that can intercept and decrypt encrypted traffic.Transport layer security



Transport layer securityHrudya Balachandran
╠²
TLS is an IETF standard similar to SSL that provides cryptographic security and secure connections between parties through the establishment of a secure session. It aims to securely transmit data via record layer encapsulation and encryption, using techniques like cryptographic computations, MACs, and the generation of secrets through pseudorandom functions and data expansion. TLS supports various cipher suites, certificate types, and alert codes while making some changes compared to SSL in areas like record formatting, PRF usage, and handshake messaging.Transport Layer Security (TLS)



Transport Layer Security (TLS)Arun Shukla
╠²
It is an IETF standardization initiative whose goal is to come out with an Internet standard Version of SSL. The presentation discusses all. Happy Learning. :)
Ssl (Secure Sockets Layer)



Ssl (Secure Sockets Layer)Asad Ali
╠²
SSL is an acronym for Secure Sockets Layer. It is a protocol used for authenticating and encrypting web traffic. For web traffic to be authenticated means that your browser is able to verify the identity of the remote server.Transport Layer Security



Transport Layer SecurityChhatra Thapa
╠²
Transport Layer Security (TLS) was designed to provide security at the transport layer and was derived from Secure Sockets Layer (SSL). TLS operates at the transport layer of the internet model and consists of four protocols: the handshake protocol for authentication and key exchange, the change cipher spec protocol for transitioning to the negotiated cryptographic settings, the alert protocol for transmitting error messages, and the record protocol for encapsulation of higher level protocols.SSL overview



SSL overviewTodd Benson (I.T. SPECIALIST and I.T. SECURITY)
╠²
A quick overview of SSL cipher suites, common vulnerabilities associated with them and how to remediate.SSL TLS Protocol



SSL TLS ProtocolDevang Badrakiya
╠²
Brief explanation about TLS and SSL protocol handshake and message exchange process and its describe certificate validation.SSL/TLS Introduction with Practical Examples Including Wireshark Captures



SSL/TLS Introduction with Practical Examples Including Wireshark CapturesJaroslavChmurny
╠²
As some of my colleagues are solving various SSL/TLS problems for one of our customers, I have prepared the above mentioned training for them. The training is divided to three parts:
- Brief Introduction to Public Key Infrastructure (PKI)
- Introduction to SSL/TLS Protocols
- Practical Examples and Hints
The last part primarily consists of hands-on exercises with Wireshark, covering variety of successful and failed SSL/TLS handshakes. The hands-on exercises are based on easily configurable dummy SSL client and server implemented in Java (available at https://github.com/Jardo72/SSL-Sandbox).
SSL/TLS



SSL/TLSDr Anjan Krishnamurthy
╠²
The document discusses SSL/TLS (Secure Sockets Layer/Transport Layer Security), which are cryptographic protocols that provide secure communication over the internet. It covers SSL/TLS concepts like handshaking, encryption, authentication. It also describes JSSE (Java Secure Socket Extension), the Java implementation of SSL/TLS, including its architecture, classes and configuration. The document provides references for further reading on SSL/TLS and JSSE.Secure Socket Layer (SSL)



Secure Socket Layer (SSL)amanchaurasia
╠²
The document presents an overview of Secure Socket Layer (SSL) technology. It discusses how SSL establishes encrypted connections to provide security and integrity. It describes SSL architecture including certificates, hashing, asymmetric and symmetric data transfer, and the SSL handshake process. It also covers encryption algorithms like RC4, AES, Triple DES, and RSA that are used. Finally, it discusses asymmetric key cryptography algorithms like Diffie-Hellman and RSA, as well as symmetric key cryptography and the future scope of encryption standards.Securing TCP connections using SSL



Securing TCP connections using SSLSagar Mali
╠²
Securing TCP connections using SSL
Originally developed by Netscape
Communications to allow secure access of a
browser to a Web server, Secure Sockets
Layer (SSL) has become the accepted
standard for Web security.1 The first version
of SSL was never released because of
problems regarding protection of credit
card transactions on the Web. In 1994,
Netscape created SSLv2, which made it
possible to keep credit card numbers
confidential and also authenticate the Web
server with the use of encryption and digital
certificates. In 1995, Netscape strengthened
the cryptographic algorithms and resolved
many of the security problems in SSLv2
with the release of SSLv3. SSLv3 now
supports more security algorithms
than SSLv2.SSL



SSLtheekuchi
╠²
TLS (Transport Layer Security) is a protocol that provides secure communication over the Internet by addressing issues of privacy, integrity, and authentication. It uses encryption to ensure privacy, message authentication codes to ensure integrity, and X.509 certificates to perform authentication between clients and servers. TLS is commonly used with HTTPS to secure web browsing and can also be used by other applications like email, voice over IP, and file transfer.Secure Socket Layer



Secure Socket LayerPina Parmar
╠²
SSL uses TCP to provide a secure end-to-end service. It consists of two layers - the SSL record protocol and the SSL handshake protocol. The record protocol provides data encryption and integrity checking, while the handshake protocol allows the server and client to authenticate each other and negotiate encryption parameters for the secure connection.SSL Secure socket layer



SSL Secure socket layerAhmed Elnaggar
╠²
The document provides an overview of the Secure Sockets Layer (SSL) protocol. It discusses SSL's goals of providing confidentiality, integrity, and authentication for network communications. It describes the SSL handshake process, where the client and server authenticate each other and negotiate encryption parameters before transmitting application data. It also discusses SSL applications like securing web traffic and online payments. The document concludes that SSL is vital for web security and ensures user confidentiality and integrity.Transport Layer Security



Transport Layer SecurityHuda Seyam
╠²
Added security measures needed we will see TLS (Transport Layer Security)
HTTPS Secure HTTP protocolSecure socket layer



Secure socket layerNishant Pahad
╠²
SSL is a secure protocol that runs above TCP/IP and allows users to encrypt data and authenticate server and client identities securely. It uses public key encryption to generate a shared secret and establish an encrypted connection. The SSL handshake process verifies the server's identity and allows the client and server to agree on encryption algorithms before exchanging data. This helps prevent man-in-the-middle attacks by authenticating servers and encrypting the connection.Ssl in a nutshell



Ssl in a nutshellFrank Kelly
╠²
SSL provides encryption and authentication for secure communication over networks. It uses certificates signed by a certificate authority to authenticate servers and establish an encrypted connection. The SSL handshake process involves the client sending a pre-master secret encrypted with the server's public key, both sides then derive encryption keys to encrypt the connection. Debugging SSL issues may require using tools like tcpdump to monitor network traffic or adding debug flags to examine the SSL handshake.secure socket layer



secure socket layerAmar Shah
╠²
SSL and TLS are cryptographic protocols that provide secure communication on the internet. They use public/private key encryption to authenticate servers and establish encrypted connections. While similar, TLS is the standardized successor to SSL. Key differences include TLS using HMAC for integrity checking and having additional alert codes not found in SSL. Both protocols operate at the transport layer and provide data confidentiality, integrity, and server authentication.Secure Socket Layer



Secure Socket LayerAbhishek Gupta
╠²
Secure Socket Layer (SSL) was first proposed and used by Netscape to transmit sensitive data over the internet by encapsulating it in a session on top of the TCP layer. SSL aims to authenticate parties, ensure data integrity, and maintain data privacy. Certain websites can only be accessed through SSL-enabled client software. SSL establishes an association between a client and server by authenticating them and then exchanging and encrypting data using suitable algorithms to keep the information secret. SSL has two layers - the record protocol, which handles data encryption, integrity, and encapsulation, and several subprotocols like the alert, change cipher spec, and handshake protocols, which initiate and negotiate secure sessions.Similar to Secure Sockets Layer and Transport Layer Security (20)
Comparative Analysis of Open-SSL Vulnerabilities & Heartbleed Exploit Detection



Comparative Analysis of Open-SSL Vulnerabilities & Heartbleed Exploit DetectionCSCJournals
╠²
Since its introduction in 1994 the Secure Socket Layer (SSL) protocol (later renamed to Transport Layer Security (TLS)) evolved to the de facto standard for securing the transport layer. SSL/TLS can be used for ensuring data confidentiality, integrity and authenticity during transport. A main feature of the protocol is its flexibility. Modes of operation and security aims can easily be configured through different cipher suites. During its evolutionary development process several flaws were found. However, the flexible architecture of SSL/TLS allowed efficient fixes in order to counter the issues. This paper presents an overview on theoretical and practical attacks of the last 20 years.Sequere socket Layer



Sequere socket LayerRaghavendra Rao
╠²
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that provide secure communication over the internet. They allow for confidentiality, integrity, and authentication between two applications communicating over TCP. SSL/TLS works by encrypting the segments of TCP connections above the transport layer through the use of symmetric and asymmetric cryptography. It establishes a secure channel over an insecure network such as the internet.Differences to Know Between SSL & TLS certificate .pdf



Differences to Know Between SSL & TLS certificate .pdfHost It Smart
╠²
SSL & TLS, Both security protocols are different from each other. In this article, we are going to compare both in detail. LetŌĆÖs dive into it!Secure Sockets Layer(SSL)Certificate



Secure Sockets Layer(SSL)CertificateCheapSSLUSA
╠²
In this Pdf,you can know what is SSL Certificate?,How it wroks?,who need SSL Certificate? How you can secure your website in this internet world?
All these Question's solution in giving in this Pdf.Web security Threats and approaches in Security.pptx



Web security Threats and approaches in Security.pptxVivekanandaGN1
╠²
Web security Threats and approaches in SecuritySSL VS TLS.pptx



SSL VS TLS.pptxVignesh kumar
╠²
SILICON CHIPS TAMILAN
Ó«ģÓ«ŻÓ«┐Ó«▓Ó»Ź Ó«ÜÓ»ćÓ«ĄÓ»łÓ«ĢÓ«│Ó»Ź (Squirrel Services)
Hello friends, this is my YouTube channel where I share knowledge about computer hardware, software, networking, server details and Job openings..
NAME : VIGNESH KUMAR
ADDRESS : INDIA , (TAMILNADU).
INSTAGRAM USER NAME : vignesh301992
Ssl https



Ssl httpsAndrada Boldis
╠²
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that secure internet connections between clients and servers. SSL was originally developed by Netscape in the 1990s to provide HTTPS secure connections for web browsing. It uses public/private key encryption and digital certificates to authenticate servers and establish encrypted connections to securely transmit data over TCP/IP networks like the internet. TLS improved upon SSL by addressing security vulnerabilities and supporting newer encryption algorithms. HTTP (Hypertext Transfer Protocol) is the underlying protocol used to request and transmit web pages and other files over the internet. Combining HTTP with SSL/TLS results in HTTPS, the secure version of HTTP used for encrypted web browsing and transactions.SSLtalk



SSLtalkMatthew Aylard
╠²
The document discusses the history and purpose of TLS/SSL, including how it uses asymmetric and symmetric cryptography. It describes how TLS/SSL works, including the handshake and record layers, cipher suites, and public key infrastructure (PKI). It notes that TLS/SSL secures communications between applications and transport layers in the OSI model. Examples of exploits like session hijacking and man-in-the-middle attacks are provided to illustrate the importance of encryption.Communications Technologies



Communications TechnologiesSarah Jimenez
╠²
The document discusses securing remote access connections by using a virtual private network (VPN) with Windows Server 2012 R2's Routing and Remote Access feature. It will use Extensible Authentication Protocol-Transport Level Security (EAP-TLS) and smartcards for authentication to encrypt traffic and securely connect remote users to the network. The goal is to properly secure these connections to provide end users with secure access to potentially sensitive company data and resources from outside the office.Usage of rc4 cipher in SSL configurations of Sri Lankan financial institutes ...



Usage of rc4 cipher in SSL configurations of Sri Lankan financial institutes ...Tharindu Weerasinghe
╠²
Published @: International Journal of Cyber-Security and Digital Forensics (IJCSDF) 7(2): 111-118
The Society of Digital Information and Wireless Communications (SDIWC), 2018 ISSN: 2305-001Geek Guide: Apache Web Servers and SSL Authentication



Geek Guide: Apache Web Servers and SSL AuthenticationRapidSSLOnline.com
╠²
The document provides an overview of setting up HTTPS on an Apache web server using SSL/TLS encryption. It discusses the basics of SSL/TLS, including how public-key cryptography is used to encrypt communication between a browser and web server. It also covers obtaining and installing an SSL certificate, and configuring Apache so that specific URLs use SSL encryption. The goal is to help readers securely transition an existing HTTP-only site to use HTTPS.Transport Layer Security



Transport Layer SecuritySanjeev Kumar Jaiswal
╠²
Transport Layer Security (TLS) is a protocol that ensures privacy between communicating applications and their users on the Internet. When a server and client communicate, TLS ensures that no third party may eavesdrop or tamper with any message. TLS is the successor to the Secure Sockets Layer (SSL). Study and analysis of some known attacks on transport layer security



Study and analysis of some known attacks on transport layer securityNazmul Hossain Rakib
╠²
This paper is focused on study on some practically feasible attacks and threats against TLS based connection. The reader can also get an idea on SSL Strip attack presented here based on an experiment in a testbed environment. There are also some other attacks on TLS protocol such as BEAST, Padding Oracle Attack, STARTTLS command injection attack, Theft of RSA Private Keys, Triple Handshake etc. which are also discussed here descriptively. This study summarizes the common known attacks following RFC 7457 and their existence, appliance and remedies for the TLS activated server. ION Sri Lanka - TLS for Network Operators



ION Sri Lanka - TLS for Network OperatorsDeploy360 Programme (Internet Society)
╠²
This document discusses the increased usage of Transport Layer Security (TLS) across internet applications and networks due to revelations of global surveillance. It outlines responses by organizations like the IETF to strengthen security and privacy of internet protocols by incorporating TLS. These include new working groups to update TLS usage and deprecating insecure versions. As a result, network operators are encouraged to support TLS encrypted traffic and help customers adopt TLS for their services and applications. Challenges in monitoring encrypted traffic and validating certificate authenticity are also addressed.Unit 6



Unit 6Vinod Kumar Gorrepati
╠²
The document discusses web security considerations and threats. It provides 3 levels at which security can be implemented - at the IP level using IPSec, at the transport level using SSL/TLS, and at the application level using protocols like SET. SSL/TLS works by establishing an encrypted channel between the client and server for secure communication. It uses handshake, change cipher spec, and alert protocols for negotiation and management of the secure session. Common web security threats include eavesdropping, message modification, denial of service attacks, and impersonation which can be mitigated using encryption, authentication and other cryptographic techniques.BSET_Lecture_Crypto and SSL_Overview_FINAL



BSET_Lecture_Crypto and SSL_Overview_FINALGlenn Haley
╠²
This document provides an overview of cryptography and the SSL/TLS protocol. It begins with an introduction to symmetric and asymmetric cryptography. It then discusses how SSL/TLS uses both types of cryptography to provide data encryption, server authentication, and optional client authentication over unsecured networks. The document outlines the SSL/TLS handshake process and record layer format. It explains how SSL/TLS enables secure communication for applications like HTTPS. It also notes that SSL/TLS performance can be improved with hardware offloading due to its computational demands. Related books on cryptography and SSL/TLS are listed for additional reference.SSL and TLS Theory and Practice 2nd Edition Rolf Oppliger



SSL and TLS Theory and Practice 2nd Edition Rolf Oppligerchizzyejinsu
╠²
SSL and TLS Theory and Practice 2nd Edition Rolf Oppliger
SSL and TLS Theory and Practice 2nd Edition Rolf Oppliger
SSL and TLS Theory and Practice 2nd Edition Rolf OppligerHTTPS, Here and Now



HTTPS, Here and NowPhilippe De Ryck
╠²
The tools at our disposal today for deploying HTTPS are tremendously powerful, and easy to use. Initiatives like Let's Encrypt offer certificates, and new security policies like HSTS and HPKP allow you to protect against extremely powerful attacks. HTTPS, Here and Now!
This was an invited talk at the ICT Security Happening, organized by the VDAB Competence Center in Leuven.ION Santiago: Lock It Up: TLS for Network Operators



ION Santiago: Lock It Up: TLS for Network OperatorsDeploy360 Programme (Internet Society)
╠²
The document discusses the history and evolution of TLS (Transport Layer Security) and SSL (Secure Sockets Layer), their increasing usage across internet applications and services, and efforts by organizations like IETF and Internet Society to promote stronger encryption and the adoption of TLS. It provides an overview of TLS versions and standards development, factors driving increased TLS usage like Snowden revelations, and resources for network operators and developers to help secure communications over the internet using TLS.Usage of rc4 cipher in SSL configurations of Sri Lankan financial institutes ...



Usage of rc4 cipher in SSL configurations of Sri Lankan financial institutes ...Tharindu Weerasinghe
╠²
More from Al Mamun (9)
Bus Management System



Bus Management SystemAl Mamun
╠²
This is a bus management system slide. Here you will get the total process of bus management system to make a software.Computer Printer



Computer PrinterAl Mamun
╠²
A printer is a piece of hardware for a computer. It allows a user to print items on paper, such as letters and pictures. Mostly a printer prints under the control of a computer. Many can also work as a copying machine or with a digital camera to print directly without using a computer.World Wide Web (WWW)



World Wide Web (WWW)Al Mamun
╠²
The World Wide Web is an information space where documents and other web resources are identified by Uniform Resource Locators, interlinked by hypertext links, and can be accessed via the Internet.Web Engineering 



Web Engineering Al Mamun
╠²
Web engineering focuses on the methodologies, techniques, and tools that are the foundation of Web application development and which support their design, development, evolution, and evaluation.Uses of internet for learning vocabulary



Uses of internet for learning vocabularyAl Mamun
╠²
Vocabulary learning is usually dealt with when learners come across new words while doing reading or listening tasks in class. Different techniques have been adopted by second language learners in order to learn vocabulary. Real world applications of matrices



Real world applications of matricesAl Mamun
╠²
Graphic Uses of Matrix Mathematics. Graphic software uses matrix mathematics to process linear transformations to render images. A square matrix, one with exactly as many rows as columns, can represent a linear transformation of a geometric object.Producer consumer problem operating system



Producer consumer problem operating systemAl Mamun
╠²
In computing, the producerŌĆōconsumer problem (also known as the bounded-buffer problem) is a classic example of a multi-process synchronization problem. The problem describes two processes, the producer and the consumer, who share a common, fixed-size buffer used as a queue.Design cycles of pattern recognition



Design cycles of pattern recognitionAl Mamun
╠²
Pattern recognition and classification is the act of taking in raw data and using a set of properties and features take an action on the data.CPU Cache Memory



CPU Cache MemoryAl Mamun
╠²
Cache memory is a very high speed memory that is placed between the CPU and main memory, to operate at the speed of the CPU. It is used to reduce the average time to access data from the main memory. Recently uploaded (20)
Odoo Project Management .pdf



Odoo Project Management .pdfdela33martin33
╠²
SDLC Corp delivers a powerful Odoo Project Management solution, offering seamless Odoo project module implementation, automation, and customization. Our Odoo project management software optimizes workflows, enhances collaboration, and ensures efficient project execution for business growth and scalability.Odoo Service Provider .pdf



Odoo Service Provider .pdfdela33martin33
╠²
Partner with SDLC Corp, a trusted sted Odoo Service Provider, for tailored Odoo ERP solutions. Our expert services enhance business efficiency through seamless implementation and migration, offering personalized Odoo consultancy services to optimize workflows and support informed decision-making.Microsoft Azure: Empowering the Future of Cloud Technology



Microsoft Azure: Empowering the Future of Cloud Technologycyberpoint678
╠²
Microsoft Azure is a leading cloud computing platform offering scalable solutions for businesses and developers. It provides services like AI, analytics, security, and hybrid cloud capabilities. Azure enables seamless app deployment, data management, and machine learning, ensuring reliability and innovation. With global infrastructure and advanced tools, Azure accelerates digital transformation for enterprises of all sizes.
For More: https://cyberpoint.com.au/it-services/cloud-computing-overview/microsoft-azure/BGP Best Practices, presented by Imtiaz Sajid



BGP Best Practices, presented by Imtiaz SajidAPNIC
╠²
Imtiaz Sajid, Network Analyst / Technical Trainer at APNIC, delivered a remote presentation on 'BGP Best Practices' for MMNOG 7 held Yangon, Myanmar from 19 to 22 March 2025. Electrical Control Panels for Water Treatment Plants_ Controlling Water Flow ...



Electrical Control Panels for Water Treatment Plants_ Controlling Water Flow ...Balaji Switchgears
╠²
This document explores the critical role of electrical control panels in water treatment plants, focusing on their design, functionality, and importance in managing water flow and purification processes. It covers key components, automation technologies, and safety measures, providing valuable insights into optimizing water treatment operations through effective control systems.The Evolution of Home Security from Cameras to Smart Systems.pdf



The Evolution of Home Security from Cameras to Smart Systems.pdfInternet Bundle Now
╠²
Explore how Home Security Cameras evolved into intelligent, connected systems. Internet Bundle Now breaks down the rise of Home Security Services.
¤öź SITUS GACOR TERPERCAYA - KAJIAN4D! ¤öź



¤öź SITUS GACOR TERPERCAYA - KAJIAN4D! ¤öźKAJIAN4D
╠²
¤öź SITUS GACOR TERPERCAYA - KAJIAN4D! ¤öź
¤Æ░ BONUS MELIMPAH UNTUK MEMBER BARU & SETIA! ¤Æ░
Ō£ģ Bonus New Member 50% (Pragmatic)
Ō£ģ Bonus New Member 20% (PG Soft)
Ō£ģ Bonus Deposit 10%
Ō£ģ Bonus Lucky Spin 500K
ŌÜĪ DEPOSIT KILAT HITUNGAN DETIK! ŌÜĪ
¤ÆĖ Proses cepat & aman dengan sistem QRIS!
¤ÜĆ DAFTAR SEKARANG & RAIH KEMENANGANMU! ¤ÜĆ
¤öŹ GOOGLE: KAJIAN4D
¤ōī Mainkan game favoritmu dan nikmati keseruannya bersama KAJIAN4D!Complete Nmap Scanning Commands CheatSheet by Hackopedia Utkarsh Thakur



Complete Nmap Scanning Commands CheatSheet by Hackopedia Utkarsh ThakurHackopedia Utkarsh Thakur
╠²
Complete Nmap Scanning Commands CheatSheet by Hackopedia Utkarsh Thakur, ETHICAL HACKING , HACKOPEDIA PresentWEFWEFWERWERWERWERREWREWation.pptx



PresentWEFWEFWERWERWERWERREWREWation.pptxtoxicsuprit
╠²
ewfweqrwqerwrwqrwqr qwr qw r qwrqwrqwrqw rqwrqwr qwrq wr wqr qwrfdwqf qw f qwf qw r qw f qw f qwf qw fqw r q2wr q3 32 r qwf qw f as f werweqt we fr ewf we fw qe fw egew g we g ewg ew ewg weg w eg we g ewg we g ewewExpert Odoo support services (1).pdf



Expert Odoo support services (1).pdfdela33martin33
╠²
SDLC Corp offers Odoo Support Service, ensuring seamless business operations with expert assistance. Our Odoo ERP Support Services ance performance, while Odoo Technical Support resolves issues enhance efficiently, optimizing workflows, improving system reliability, and boosting productivity for long-term success.Shopify Store Setup_ Database Management for Large Stores.pdf



Shopify Store Setup_ Database Management for Large Stores.pdfCartCoders
╠²
Discover expert Shopify store setup services with CartCoders. Tailored to meet your unique business needs, our team ensures your online store launches smoothly with all necessary features. Maximize your e-commerce potential with our professional support and guidance.IETF 122: draft-ietf-regext-rdap-rir-search-16



IETF 122: draft-ietf-regext-rdap-rir-search-16APNIC
╠²
Tom Harrison, Registry Product and Delivery Manager at APNIC, presented updates on the draft regext-rdap-rir-search functionality at IETF 122 held in Bangkok Thailand from 15 to 21 March 2025.Generative artificial intelligence in EU Grant Writing



Generative artificial intelligence in EU Grant WritingPeter Trkman
╠²
The presentation "AI in EU Grant Writing" by Dr. Peter Trkman and Dr. Luka Tomat focuses on the integration of generative artificial intelligence (GenAI) tools into the process of writing grant applications, particularly in the context of EU-funded projects. It was delivered as part of a workshop held at the University of Ljubljana and is based on the authorsŌĆÖ extensive experienceŌĆöover 80 workshops since late 2023.
The presentation begins by clarifying what GenAI is and what it is not. It explains how large language models (LLMs) work, including tokenization, vector embedding, and self-attention mechanisms. It introduces major LLMs such as GPT-4, Claude, Grok, Gemini, and others, along with an extensive list of tools built on top of these models.
The core of the presentation is practical. It explores how GenAI can assist in the preparation of grant applications, from generating project summaries and activity plans to producing ethics statements and evaluation responses. Concrete examples are given from Erasmus+ mobility forms, national project applications, and fictional debates using actual EU evaluation criteria.
The authors explain that GenAI is most useful for tasks requiring large volumes of content, knowledge synthesis, translation to various audiences, second opinions, and early drafting. However, they emphasize that it should not be used when accuracy is paramount or when ethical implications are significant. Instead, it is best seen as a complementary tool that boosts productivity, especially for those less experienced in writing.
The presentation includes broader reflections on how GenAI is reshaping research practices and the labor market, with references to studies showing that GenAI often outperforms human analysts in certain tasks and that its emotional support capabilities rival those of trained therapists.
Specific tools for grant writing are introduced, such as DeepRFP, Grantable, and GrantedAI, along with general tools like ChatGPT, Copilot, and Perplexity. The presenters also advocate for long-term structural change in the grant systemŌĆöstreamlining processes to eliminate the need for GenAI use altogether. Until then, they argue, one must ŌĆ£play the gameŌĆØ and use these tools effectively while maintaining academic integrity.
The closing message is clear: while GenAI tools offer powerful support, responsible use and a focus on substance over form remain essential. Peter and Luka invite further contact for tailored workshops and note that all content is based on their personal experience and research, not confidential material.Hire Odoo Consultant .pdf



Hire Odoo Consultant .pdfdela33martin33
╠²
SDLC Corp provides expert Odoo consulting services, helping businesses streamline operations, customize ERP solutions, and enhance efficiency. Our Odoo consultants specialize in implementation, integration, and support, ensuring seamless Odoo services that optimize workflows, boost productivity, and drive business growth.Odoo demo .pdf



Odoo demo .pdfdela33martin33
╠²
SDLC Corp offers comprehensive and personalized Odoo Demo services, helping businesses explore the full potential of Odoo ERP Our Odoo experts provide hands-on demos of core Odoo modules such as CRM, Sales, Inventory, Accounting, and more. As a trusted Odoo partner, we ensure you experience real-time workflows and tailored functionalities. From customization to integration, we help you make informed decisions with an interactive Odoo demo that highlights efficiency, automation, and business growth opportunities.Epochalypse 2038 - Remediating the 32-bit Timestamp Risk at Global Scale (Pub...



Epochalypse 2038 - Remediating the 32-bit Timestamp Risk at Global Scale (Pub...treyka
╠²
Epochalypse 2038 - Remediating the 32-bit Timestamp Risk at Global Scale (Public Briefing v1.0 2025-03-31).pdfElectrical Control Panels for Water Treatment Plants_ Controlling Water Flow ...



Electrical Control Panels for Water Treatment Plants_ Controlling Water Flow ...Balaji Switchgears
╠²
Secure Sockets Layer and Transport Layer Security
- 2. Reality!!! 2
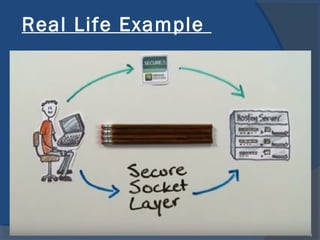
- 3. Outline ’é× Web Security ’é× SSL/TLS ’é× SSL/ TLS Encryption ’é× Why SSL exists? ’é× SSL/TLS Architecture ’é× Real Life Example ’é× Summary ’é× References 3
- 4. Web security ’é× Web is now widely used by businesses, government firms and individuals. ’é× Confidentiality : Anyone can see content ’é× Integrity : Someone might alter content ’é× Authentication : Not clear who you are talking with 4
- 10. Web security 10
- 12. SSL/ TLS ’é× Secure Sockets Layer (SSL) ’éŚ Developed by Netscape Corporation ’éŚ Versions 1, 2, and 3 (released in 1996) ’é× Transport Layer Security (TLS) ’éŚ Successor of SSL ’éŚ IETF standards track protocol, based on SSL 3.0 ’éŚ TLS and SSL encrypt the segments of network connections at the Transport Layer end-to-end. ’éŚ 12
- 13. SSL/ TLS 13
- 25. 25 Summary ’é× SSL/TLS addresses the need for security in Internet communications ’éŚPrivacy - conventional encryption ’éŚIntegrity - Message Authentication Codes ’éŚAuthentication - certificates August 16, 2016 NITTTR, Chandigarh
- 26. References ’é× https://images.google.com/ ’é× https://www.youtube.com/watch?v=O1oP_DNL0uo ’é× https://www.youtube.com/watch?v=rROgWTfA5qE 26
- 27. August 16, 2016 27NITTTR, Chandigarh





