ds
0 likes180 views
This document discusses authentication methods for secure internet banking. It presents two solutions: 1) a short-time password solution based on symmetric cryptography and hardware security modules, and 2) a certificate-based solution using SSL/TLS sessions. Both solutions are classified according to their resistance to offline credential stealing attacks and online channel breaking attacks. While both offer high security against common attacks, the certificate-based solution is presented as a highly attractive alternative for the future given changing legislation and the spread of electronic IDs.
1 of 14











Ad
Recommended
this is test for today
this is test for todayDreamMalar
╠²
This document discusses authentication methods for secure internet banking. It presents two solutions: 1) a short-time password solution that uses symmetric cryptography and a hardware security module, and 2) a certificate-based solution that establishes an SSL/TLS channel without client authentication and uses the client's certificates. Both solutions offer high security against common offline credential stealing and online channel breaking attacks. The certificate solution is attractive for the future due to changing legislation and the spread of electronic IDs.Pay Forum Conference
Pay Forum Conferencehagero
╠²
The document discusses best practices for achieving risk-appropriate authentication. It outlines different authentication options like something you know, have, or are, and matches them to different risk levels from NIST SP 800-63-1. It notes that selecting authentication requires considering who is being authenticated, where, what they will use it for, available endpoints, regulations, budget, and risk. Identity proofing is also important and authentication should use a layered security architecture with adaptive access controls. The document provides an example customer case of a large bank using a versatile authentication platform from Nexus that includes management platforms, OTP tokens, policy enforcement, and an adaptive access manager.Ynamono Hs Lecture
Ynamono Hs Lectureynamoto
╠²
The document discusses using smartcards and biometrics like fingerprints for multi-factor authentication. It outlines the goals of authentication including verifying identity, preventing secrets from leaking, and providing scalability. Passwords are noted as insufficient for these goals. The solution presented is using smartcards to store credentials alongside biometrics like fingerprints for two-factor authentication. An example project that implemented this was a credentialing system for first responders in Illinois.Security Analysis of Mobile Authentication Using QR-Codes
Security Analysis of Mobile Authentication Using QR-Codes csandit
╠²
The paper analyzes the security vulnerabilities in mobile authentication systems using QR codes, highlighting risks such as tampering and counterfeiting due to easy replicability. It discusses the architecture of these systems and proposes recommendations for enhancing security, including blocking screen capture during QR code display and implementing expiring QR codes to mitigate replay attacks. The findings emphasize the need for robust implementation strategies to address threats posed by internal and external attackers.Sms based otp
Sms based otpHai Nguyen
╠²
1. The document analyzes the risks of using SMS-based two-factor authentication for user authentication and transaction authentication.
2. It outlines threats including eavesdropping, man-in-the-middle attacks, SMS delays and losses, lack of coverage, and increasing costs.
3. The document recommends using message authentication codes instead of random numbers or hashes for signatures to protect against attacks. It also suggests verifying transaction data is unchanged when signatures are submitted.Qr code based secure otp distribution scheme for Online banking
Qr code based secure otp distribution scheme for Online bankingSnehith
╠²
This document proposes a new authentication scheme for secure OTP distribution in net banking using QR codes and email. It describes existing OTP distribution methods like text messages and proprietary tokens that have drawbacks like being text-based and increase risk of tampering or identification over long periods. The proposed system generates one-time passwords using a pseudorandom number and timestamp, encrypts it with AES using the user's ATM PIN as the key, converts it to a QR code and distributes it via email. It aims to provide a more secure authentication method compared to existing text-based approaches.Cryptomathic white paper 2fa for banking
Cryptomathic white paper 2fa for bankingHai Nguyen
╠²
This document provides an overview of two-factor authentication for banking, including: threats to internet banking like phishing; a range of authentication methods like hardware tokens, SMS codes, and smart cards; and factors to consider in the business case for deployment like customer acceptance, confidence, and cost savings. It aims to help financial institutions understand opportunities for security, business growth, and reduced costs through two-factor authentication.E voting authentication with qr-codes
E voting authentication with qr-codesMd. Hasibur Rashid
╠²
The document proposes an e-voting authentication scheme that uses QR codes and visual cryptography. Voters are issued two "shares" - one containing a QR code with their password, and one stored in a database. To vote, a voter scans the QR code to reveal the password, enters it, and is authenticated. The scheme aims to be highly usable by requiring only a QR code scanner, with no technical background needed. It evaluates the scheme's security against attacks like intercepting transmitted shares or manipulating scanning software.HACBPS: A Hierarchical Access Control- Based Proxy Signature
HACBPS: A Hierarchical Access Control- Based Proxy SignatureIDES Editor
╠²
The document presents a new security scheme called Hierarchical Access Control-based Proxy Signature (HACBPS), which combines hierarchical access control and proxy signature mechanisms to enable users of different security levels to access and sign information securely. In this scheme, upper-level users can delegate their signing rights to lower-level users while ensuring that security keys are well protected and access is properly managed. The authors propose a structured method for key assignment and verification to enhance security and operational efficiency in a hierarchical framework.Iaetsd network security and
Iaetsd network security andIaetsd Iaetsd
╠²
This document discusses network security and cryptography. It begins by introducing network security concepts like secrecy, authentication, nonrepudiation, and integrity. It then discusses cryptography topics such as symmetric and public key encryption. Specific algorithms like RSA are explained. The document also discusses security issues at different layers of the network and summarizes techniques used at each layer.Jips v07 no1_paper17
Jips v07 no1_paper17Hai Nguyen
╠²
1) This research paper proposes a User Authentication Level System (UALS) model for assessing the risk of multi-factor authentication methods.
2) The UALS model defines 5 levels of authentication based on technical requirements from NIST SP800-63, with higher levels incorporating additional authentication factors such as biometric information and hardware tokens.
3) A selection process is described to evaluate transaction risks and vulnerabilities and select the appropriate authentication level, followed by testing to ensure risks are eliminated.E0962833
E0962833IOSR Journals
╠²
This document summarizes and compares different one-time password authentication algorithms. It discusses how one-time passwords avoid vulnerabilities of traditional static passwords by being only valid for a single login session. Different methods for generating and delivering one-time passwords are described, including via text messaging, mobile phone apps, or tokens. The document also discusses advantages and disadvantages of these different one-time password approaches.Toward Better Password Requirements
Toward Better Password RequirementsJim Fenton
╠²
The document summarizes proposed changes to NIST's Digital Authentication Guideline SP 800-63-3 regarding password requirements. Some key changes include increasing the minimum password length to 8 characters, allowing passwords up to 64 characters, accepting all printable ASCII characters and emojis, removing composition rules and knowledge-based authentication questions, and prohibiting password expiration unless compromised. The document encourages participation in the public review process on GitHub to help finalize the updated guidelines.Public key Infrastructure (PKI)
Public key Infrastructure (PKI)Venkatesh Jambulingam
╠²
The document discusses Public Key Infrastructure (PKI), highlighting its role in secure online transactions through the use of digital certificates, encryption methods, and trust services. It explains the components of PKI, including registration and certificate authorities, as well as digital signature processes and certificate-based authentication methods. Overall, the content emphasizes ensuring secure communication and verifying identities in the digital realm.Ricardo Mendez, Technical Director Europe ,Samsung NEXT - Identity, Privacy a...
Ricardo Mendez, Technical Director Europe ,Samsung NEXT - Identity, Privacy a...Techsylvania
╠²
Ricardo J. M├®ndez discusses identity, privacy, and processing data at the edge. He provides a conceptual 7-layer model for digital identity and discusses how characteristics can identify people even without facts. While edge processing can enhance privacy, it does not guarantee it. M├®ndez argues that companies pinky-swearing not to abuse data is not enough and that people will not leave platforms due to scandals. To improve privacy, systems must give compelling reasons for people to use them and address fears of impermanence.ipas implicit password authentication system ieee 2011
ipas implicit password authentication system ieee 2011prasanna9
╠²
This document summarizes a proposed authentication system called the Implicit Password Authentication System (IPAS). IPAS aims to address weaknesses in existing authentication schemes like passwords, tokens, biometrics and graphical passwords. It proposes using a set of questions and answers during registration that are then implicitly embedded into images by the server during authentication. The server randomly selects questions and images, requiring the user to demonstrate knowledge of their prior answers without directly reproducing them. The system is intended for mobile banking but could generalize to other client-server environments.wed
wedDreamMalar
╠²
The document discusses authentication methods for secure internet banking. It presents two challenge response authentication solutions: one based on short-time passwords and one based on certificates. It describes attacks on authentication like offline credential stealing and online channel breaking. Both proposed solutions offer high security against common attacks and the certificate-based solution is attractive for the future given changing legislation and spread of electronic IDs.dfsd
dfsdDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining the objectives, describing common attacks on authentication like offline credential stealing and online channel breaking. It then details how each solution works, providing security against such attacks through symmetric cryptography and hardware security modules for short-time passwords and SSL/TLS sessions and browser certificates for the certificate-based approach. The document concludes that while both solutions offer high security now, certificate-based e-IDs may become a more attractive long-term solution.this is test for download option
this is test for download optionDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining the objectives, describing common attacks on authentication like offline credential stealing and online channel breaking. It then details how each solution works to resist these attacks, with the short-time password solution using hardware security modules and the certificate solution employing SSL/TLS sessions. The document concludes that while both solutions offer high security against current attacks, certificate-based authentication may be more attractive and valuable in the future due to changing legislation and widespread use of electronic IDs.the
theDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining the objectives, describing common attacks on authentication like offline credential stealing and online channel breaking. It then details how each solution works and compares their resistance to such attacks through a taxonomy. Both solutions offer high security but certificates may become more attractive over time as e-IDs spread due to changing legislation.de
deDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining objectives like understanding network security services and awareness of vulnerabilities. It then describes current authentication threats and the two solutions. The short-time password solution uses hardware security modules while the certificate-based solution establishes an SSL/TLS channel. Both solutions offer high security against common attacks like offline credential stealing and online channel breaking. The certificate solution is concluded to be highly attractive for the future given changing legislation and spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using symmetric cryptography and hardware security modules, and the other based on certificate-based authentication using SSL/TLS. It discusses common attacks on authentication like offline credential stealing and online channel breaking. Both proposed solutions offer strong security against these attacks. While highly secure now, the certificate-based solution is presented as being highly attractive and valuable for the future as electronic IDs become more widespread and legislation changes.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and the spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and potential widespread use of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using a hardware security module, and the other based on certificates. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong protection against these common attacks by requiring additional hardware like smart cards. The certificate-based solution establishes an initial SSL/TLS channel before accessing credentials stored on the smart card within the browser. While secure now, the solutions may need to evolve to address more sophisticated future attacks as internet banking grows in importance.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and the spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using symmetric cryptography and hardware security modules, and the other based on certificate-based authentication using SSL/TLS. It discusses common attacks on authentication like offline credential stealing and online channel breaking. Both proposed solutions offer strong security against these attacks. While highly secure now, the certificate-based solution is presented as being more attractive and valuable for the future with changing legislation and widespread use of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and the spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and potential widespread use of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using a hardware security module, and the other based on certificates. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong protection against these common attacks, with the certificate-based solution being highly attractive for the future as electronic IDs become more widely used among customers.More Related Content
What's hot (8)
HACBPS: A Hierarchical Access Control- Based Proxy Signature
HACBPS: A Hierarchical Access Control- Based Proxy SignatureIDES Editor
╠²
The document presents a new security scheme called Hierarchical Access Control-based Proxy Signature (HACBPS), which combines hierarchical access control and proxy signature mechanisms to enable users of different security levels to access and sign information securely. In this scheme, upper-level users can delegate their signing rights to lower-level users while ensuring that security keys are well protected and access is properly managed. The authors propose a structured method for key assignment and verification to enhance security and operational efficiency in a hierarchical framework.Iaetsd network security and
Iaetsd network security andIaetsd Iaetsd
╠²
This document discusses network security and cryptography. It begins by introducing network security concepts like secrecy, authentication, nonrepudiation, and integrity. It then discusses cryptography topics such as symmetric and public key encryption. Specific algorithms like RSA are explained. The document also discusses security issues at different layers of the network and summarizes techniques used at each layer.Jips v07 no1_paper17
Jips v07 no1_paper17Hai Nguyen
╠²
1) This research paper proposes a User Authentication Level System (UALS) model for assessing the risk of multi-factor authentication methods.
2) The UALS model defines 5 levels of authentication based on technical requirements from NIST SP800-63, with higher levels incorporating additional authentication factors such as biometric information and hardware tokens.
3) A selection process is described to evaluate transaction risks and vulnerabilities and select the appropriate authentication level, followed by testing to ensure risks are eliminated.E0962833
E0962833IOSR Journals
╠²
This document summarizes and compares different one-time password authentication algorithms. It discusses how one-time passwords avoid vulnerabilities of traditional static passwords by being only valid for a single login session. Different methods for generating and delivering one-time passwords are described, including via text messaging, mobile phone apps, or tokens. The document also discusses advantages and disadvantages of these different one-time password approaches.Toward Better Password Requirements
Toward Better Password RequirementsJim Fenton
╠²
The document summarizes proposed changes to NIST's Digital Authentication Guideline SP 800-63-3 regarding password requirements. Some key changes include increasing the minimum password length to 8 characters, allowing passwords up to 64 characters, accepting all printable ASCII characters and emojis, removing composition rules and knowledge-based authentication questions, and prohibiting password expiration unless compromised. The document encourages participation in the public review process on GitHub to help finalize the updated guidelines.Public key Infrastructure (PKI)
Public key Infrastructure (PKI)Venkatesh Jambulingam
╠²
The document discusses Public Key Infrastructure (PKI), highlighting its role in secure online transactions through the use of digital certificates, encryption methods, and trust services. It explains the components of PKI, including registration and certificate authorities, as well as digital signature processes and certificate-based authentication methods. Overall, the content emphasizes ensuring secure communication and verifying identities in the digital realm.Ricardo Mendez, Technical Director Europe ,Samsung NEXT - Identity, Privacy a...
Ricardo Mendez, Technical Director Europe ,Samsung NEXT - Identity, Privacy a...Techsylvania
╠²
Ricardo J. M├®ndez discusses identity, privacy, and processing data at the edge. He provides a conceptual 7-layer model for digital identity and discusses how characteristics can identify people even without facts. While edge processing can enhance privacy, it does not guarantee it. M├®ndez argues that companies pinky-swearing not to abuse data is not enough and that people will not leave platforms due to scandals. To improve privacy, systems must give compelling reasons for people to use them and address fears of impermanence.ipas implicit password authentication system ieee 2011
ipas implicit password authentication system ieee 2011prasanna9
╠²
This document summarizes a proposed authentication system called the Implicit Password Authentication System (IPAS). IPAS aims to address weaknesses in existing authentication schemes like passwords, tokens, biometrics and graphical passwords. It proposes using a set of questions and answers during registration that are then implicitly embedded into images by the server during authentication. The server randomly selects questions and images, requiring the user to demonstrate knowledge of their prior answers without directly reproducing them. The system is intended for mobile banking but could generalize to other client-server environments.Similar to ds (20)
wed
wedDreamMalar
╠²
The document discusses authentication methods for secure internet banking. It presents two challenge response authentication solutions: one based on short-time passwords and one based on certificates. It describes attacks on authentication like offline credential stealing and online channel breaking. Both proposed solutions offer high security against common attacks and the certificate-based solution is attractive for the future given changing legislation and spread of electronic IDs.dfsd
dfsdDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining the objectives, describing common attacks on authentication like offline credential stealing and online channel breaking. It then details how each solution works, providing security against such attacks through symmetric cryptography and hardware security modules for short-time passwords and SSL/TLS sessions and browser certificates for the certificate-based approach. The document concludes that while both solutions offer high security now, certificate-based e-IDs may become a more attractive long-term solution.this is test for download option
this is test for download optionDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining the objectives, describing common attacks on authentication like offline credential stealing and online channel breaking. It then details how each solution works to resist these attacks, with the short-time password solution using hardware security modules and the certificate solution employing SSL/TLS sessions. The document concludes that while both solutions offer high security against current attacks, certificate-based authentication may be more attractive and valuable in the future due to changing legislation and widespread use of electronic IDs.the
theDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining the objectives, describing common attacks on authentication like offline credential stealing and online channel breaking. It then details how each solution works and compares their resistance to such attacks through a taxonomy. Both solutions offer high security but certificates may become more attractive over time as e-IDs spread due to changing legislation.de
deDreamMalar
╠²
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining objectives like understanding network security services and awareness of vulnerabilities. It then describes current authentication threats and the two solutions. The short-time password solution uses hardware security modules while the certificate-based solution establishes an SSL/TLS channel. Both solutions offer high security against common attacks like offline credential stealing and online channel breaking. The certificate solution is concluded to be highly attractive for the future given changing legislation and spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using symmetric cryptography and hardware security modules, and the other based on certificate-based authentication using SSL/TLS. It discusses common attacks on authentication like offline credential stealing and online channel breaking. Both proposed solutions offer strong security against these attacks. While highly secure now, the certificate-based solution is presented as being highly attractive and valuable for the future as electronic IDs become more widespread and legislation changes.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and the spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and potential widespread use of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using a hardware security module, and the other based on certificates. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong protection against these common attacks by requiring additional hardware like smart cards. The certificate-based solution establishes an initial SSL/TLS channel before accessing credentials stored on the smart card within the browser. While secure now, the solutions may need to evolve to address more sophisticated future attacks as internet banking grows in importance.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and the spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using symmetric cryptography and hardware security modules, and the other based on certificate-based authentication using SSL/TLS. It discusses common attacks on authentication like offline credential stealing and online channel breaking. Both proposed solutions offer strong security against these attacks. While highly secure now, the certificate-based solution is presented as being more attractive and valuable for the future with changing legislation and widespread use of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and the spread of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and potential widespread use of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using a hardware security module, and the other based on certificates. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong protection against these common attacks, with the certificate-based solution being highly attractive for the future as electronic IDs become more widely used among customers.NetworkSecurity.ppt
NetworkSecurity.pptjameschloejames
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using a hardware security module, and the other based on certificates. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong protection against these common attacks. While secure now, the certificate-based solution is presented as a highly attractive option for the future as electronic IDs become more widely used among customers.sample.ppt
sample.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and potential widespread use of electronic IDs.PPT
PPTBhavani Testone
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using a hardware security module, and the other based on certificates. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong protection against these common attacks, with the certificate-based solution being highly attractive for the future as electronic IDs become more widely used among customers.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using a hardware security module, and the other based on certificates. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong protection against these common attacks. While secure now, the certificate-based solution is presented as a highly attractive option for the future as electronic IDs become more widely used among customers.NetworkSecurity.ppt
NetworkSecurity.pptBhavani Testone
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and potential widespread use of electronic IDs.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document presents two solutions for secure internet banking authentication - one based on short-time passwords using hardware security modules, and the other based on certificate-based authentication using smart cards. It discusses current authentication threats like offline credential stealing and online channel breaking attacks. Both proposed solutions offer strong security against these common attacks, with the certificate-based solution being highly attractive for the future due to changing legislation and potential widespread use of electronic IDs.Ad
More from DreamMalar (20)
example.pdf
example.pdfDreamMalar
╠²
The document provides instructions for submitting papers to the ENTCS (Electronic Notes in Theoretical Computer Science) macro package. It details replacing files, including frontmatter like the title and author names, and using environments like theorems. It also discusses formatting requirements like using Type 1 fonts and producing PDF files using tools like dvips, ps2pdf, and pdfLaTeX.example.pdf
example.pdfDreamMalar
╠²
The document provides instructions for submitting papers to the ENTCS (Electronic Notes in Theoretical Computer Science) macro package. It explains that the paper must be formatted using either the entcsmacro.sty or prentcsmacro.sty style files. It also provides information on formatting the frontmatter, using environments like theorems and lemmas, adding references, and producing a PDF file.tag
tagDreamMalar
╠²
This test document contains sample formatting including bold, italic, and underlined text. It also includes an unordered list with 4 items and a table with 3 rows and 3 columns. The document demonstrates a page break and contains a paragraph with a footnote.tag
tagDreamMalar
╠²
This test document contains sample formatting including bold, italic, and underlined text. It also includes an unordered list with 4 items and a table with 3 rows and 3 columns. The document demonstrates a page break and contains a paragraph with a footnote.example.pdf
example.pdfDreamMalar
╠²
The document provides instructions for submitting papers to the ENTCS (Electronic Notes in Theoretical Computer Science) macro package. It explains that the paper must be formatted using either the entcsmacro.sty or prentcsmacro.sty style files. It also provides information on formatting the frontmatter, using environments like theorems and lemmas, adding references, and producing a PDF file.LAtest Doc
LAtest DocDreamMalar
╠²
This document provides tips for creating effective PowerPoint slides by avoiding common pitfalls. It addresses how to structure slides with outlines and bullet points, use fonts and colors that are easy to read, include graphs and charts to visualize data, check for spelling and grammar errors, and conclude with a clear summary and invitation for questions. Key recommendations include using a large font size, limiting each slide to 4-5 main points, choosing high contrast colors, including descriptive titles on all visuals, and proofreading for clarity and correctness.NetworkSecurity.ppt
NetworkSecurity.pptDreamMalar
╠²
The document proposes two solutions for secure internet banking authentication - one based on short-time passwords using smart cards and symmetric cryptography, and the other based on digital certificates. It discusses attacks on authentication like offline credential stealing and online channel breaking. The short-time password solution involves the user copying a response from their smart card to a bank login form. The certificate-based solution establishes an SSL/TLS channel without client authentication initially and then uses the smart card certificates for authentication. Both solutions offer high security against common attacks but certificate-based authentication may be more attractive long-term as e-IDs spread.Sample.ppt
Sample.pptDreamMalar
╠²
This document provides information about the HelloPT application, which allows users to control PowerPoint presentations from an iPhone or iPod touch. HelloPT allows users to view slides, navigate between slides, and use the screen as a digital whiteboard. It also displays notes entered in PowerPoint files. To use HelloPT, it must be installed on a Windows server along with PowerPoint 2000/2003/2007/2010. The application works for iPhone/iPod touch devices running iOS 2.2.1 or higher.not from widget
not from widgetDreamMalar
╠²
This document provides tips for creating effective PowerPoint slides and avoiding pitfalls of bad slides. It covers topics like outlines, slide structure, fonts, color, backgrounds, graphs, spelling and grammar. For slide structure, it recommends using point form, including 4-5 points per slide, and showing one point at a time. For fonts, it suggests using a large, easy-to-read font like Arial. For color, it advises using contrasting font/background colors and being consistent. For graphs, it says to include titles and use graphs over tables when possible. It also stresses proofreading for errors.Document.docx.docx
Document.docx.docxDreamMalar
╠²
This document tests the compatibility of document formatting and elements across different word processing applications. It contains various formatting styles, layouts, and elements like headings, bullets, tables, images, and drawings. The document is originally created in Microsoft Word 2007 in DOCX format. When opened in other applications, it checks if the original styles, layouts, and elements are preserved or changed/lost in formatting and display. The document acts as a prototype to see how well different applications maintain compatibility when opening a file created in another application.PDF2.pdf
PDF2.pdfDreamMalar
╠²
This document provides an overview of the Centers for Disease Control and Prevention's (CDC) use of Facebook and other social media platforms. It discusses CDC's strategy of using social media to disseminate public health information to diverse audiences. It highlights CDC's Facebook page which has over 54,000 fans, and the "i know" campaign page which focuses on HIV prevention among young African Americans. The document also outlines CDC's social media best practices around compliance, accessibility, and interaction with users.1934015245 Software TestingA.pdf
1934015245 Software TestingA.pdfDreamMalar
╠²
This document provides guidelines and information for preparing a resume for software testing interviews. It includes a sample resume on the accompanying CD and discusses including an objective, experience, projects, education, and limiting the resume to 4-5 pages. The document also provides an organizational hierarchy for software development roles to help candidates understand the levels and requirements of different positions.Ad
ds
- 1. SECURE INTERNET BANKING AUTHENTICATION AAR T H I K AN N AP P AN D H IV Y AA.R M AH A L AK S H M I.S
- 2. Network Security c tion Offline cr trod u edential In Attacks on Onl Sho ine authentication rt t cha ime pwd nn el Abstract nomy bjec tives k t axo o At tac Conclusion sol ution based f icate Certi 2
- 3. PRESENTATION OBJECTIVES ’é¦ Understand network security services ’é¦ Be aware of vulnerabilities and threats ’é¦ Realize why network security is necessary ’é¦ Highly attractive solution for valuable and secure future. 3
- 4. ABSTRACT ’é¦The authors present two challenge response Internet banking authentication solutions ’é¦ one based on short-time passwords ’é¦ and one on certificates ’é¦attacks on authentication ’é¦transaction-signing option 4
- 5. INTRODUCTION ’é¦ The Internet is an integral part of our daily lives, and the proportion of people who expect to be able to manage their bank accounts anywhere, anytime is constantly growing ’é¦ This article describes current Authentication threats and two proposed solutions as well as how these solutions can be extended in the face of more complex future attacks 5
- 6. ATTACKS ON AUTHENTICATION ’é¦ Internet banking systems must authenticate users before granting them access to particular services. ’é¦ successful authentication eventually enables users to access their private information. We can classify all Internet banking authentication methods according to their resistance to two types of common attacks ’āś offline credential-stealing attacks ’āś online channel-breaking attacks 6
- 7. Offline credential-stealing attacks ’é¦ Security precautions can help users protect themselves from malicious software. ’é¦ For example-- installing and maintaining a firewall and up-to date antivirus software, regularly applying operating system and browser patches 7
- 8. Online channel-breaking attack ’é¦ The intruder noticeably intercepts messages between the client PC and the banking server by masquerading as the server to the client and vice versa ’é¦ Online channel-breaking attacks donŌĆÖt necessarily compromise the userŌĆÖs credentials but the sessionŌĆÖs credentials and therefore typically require the user-initiated banking 8 session to work properly.
- 9. AN ATTACK TAXONOMY Taxonomy of Internet banking authentication methods. Methods are classified according to their resistance against offline 9 credential-stealing and online channel-breaking attacks.
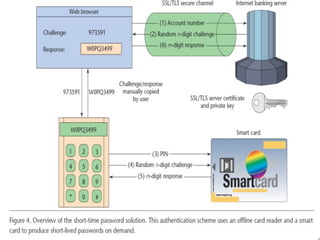
- 10. SHORT-TIME PASSWORD SOLUTION ’é¦ It uses symmetric cryptography in combination with a hardware security module . User authentication works as follows: 4. The user connects to the Internet banking 5. The user claims his or her identity by entering an account number in the bankŌĆÖs login form 6. The user opens his or her smart card by entering the corresponding PIN in the reader before entering the given challenge. 7. The user manually copies the shown response to the bankŌĆÖs login form to be checked by the bankŌĆÖs authentication server. 10
- 11. The Need for Web Security 11
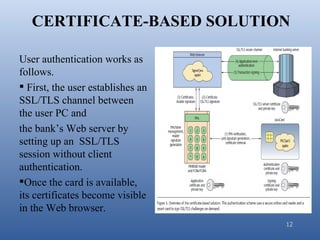
- 12. CERTIFICATE-BASED SOLUTION User authentication works as follows. ’é¦ First, the user establishes an SSL/TLS channel between the user PC and the bankŌĆÖs Web server by setting up an SSL/TLS session without client authentication. ’é¦Once the card is available, its certificates become visible in the Web browser. 12
- 13. Conclusion ’é¦Internet banking has turned into an arms race between financial institutions and public network attackers. ’é¦Both solutions offer high security against common attacks. ’é¦However, changing legislation and the eventually spread of e-IDs among customers makes this solution a highly attractive and valuable alternative for the future. 13
- 14. THANK YOU Network security!!!!!!!! 14
Editor's Notes
- #6: This sub-section addresses why Internet security is a problem and how it came to be that we are depending on an infrastructure with fundamental vulnerabilities. updated 2000-08-07
- #14: Confidentiality Integrity Authentication Ensures that the origin of a message is correctly identified, with an assurance that the identity is not false Nonrepudiation Neither the sender nor the receiver of a message is able to deny the transmission Access Control Availability